Assignment on Cyber Security PDF
14 Pages3121 Words81 Views
Added on 2021-05-30
Assignment on Cyber Security PDF
Added on 2021-05-30
ShareRelated Documents
AssignmentCyber Security

Contents1.Introduction...................................................................................................................................22.Risks Identification........................................................................................................................23.Risks Strategy................................................................................................................................4Conceptual Framework:.....................................................................................................................4Process of risk management strategy.................................................................................................54.Risks evaluation and Assessment..................................................................................................75.Risks Mitigation plan.....................................................................................................................86.Discussion...................................................................................................................................117.Conclusion...................................................................................................................................128.References:..................................................................................................................................12

Title: Risk assessment and risk management strategy associated with cloud infrastructure1.IntroductionEvery organization is looking forward to transform their traditional business tactics with the ICT technology. The Cloud computing technology is the emerging trend for developing digitization in the organization. The platform of cloud computing provides new innovation, scalability, flexibility, reliability, of information for improving the working tactics of the enterprise. The advantages of using cloud computing technology are managing abstraction of resources, managing scalability and flexibility of the business process, improving instant provision mechanism for innovation, sharing of hardware, software, network resources, providing on-demand service, managing virtualization of the business processes and resources, and others. The cloud computing environment helps in managing effective relationship between different business units of the enterprise with the inclusion of software as a service model, infrastructure as a service model, and platform as a service model. With the increasing growth of digitization, the security is the major concern associated with the preservation of the confidential information of the organization. The identification and mitigation of the risks is the important part of the business process for achieving success in the undertaking project. In this paper, we are looking forward to analyse the risks identification and management of cloud computing infrastructure. 2.Risks IdentificationThe adoption of cloud computing architecture helps in transforming traditional business tactics with the digital environment. The following table shows the risks identified which are associated with the cloud computing infrastructure:Risks IdentificationDescriptionSecurity associated with physical assetsThe hardware, software, and network resources uploaded on the cloud platform are associated with the security risks. The third party can get unauthorised access of using the devicesIdentification security risksThe user can get unauthorised access by using false identitySecurity issues related with application managementThe third party can get unauthorised access of using the business applications. The security is the major concern associated with the application available on the cloud.Security issues related toThe security issues related with the data leakages of the

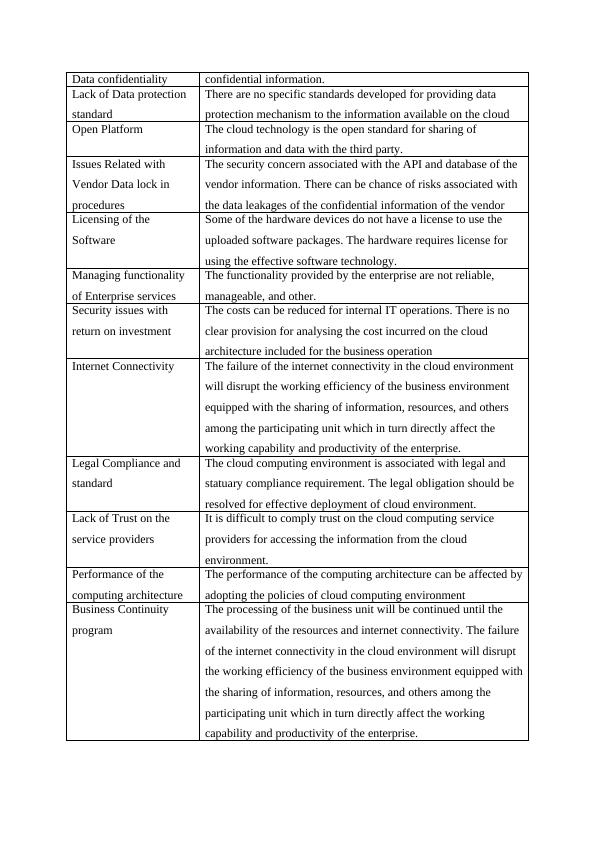
Data confidentialityconfidential information. Lack of Data protection standardThere are no specific standards developed for providing data protection mechanism to the information available on the cloudOpen PlatformThe cloud technology is the open standard for sharing of information and data with the third party.Issues Related with Vendor Data lock in proceduresThe security concern associated with the API and database of the vendor information. There can be chance of risks associated with the data leakages of the confidential information of the vendorLicensing of the SoftwareSome of the hardware devices do not have a license to use the uploaded software packages. The hardware requires license for using the effective software technology.Managing functionality of Enterprise services The functionality provided by the enterprise are not reliable, manageable, and other. Security issues with return on investmentThe costs can be reduced for internal IT operations. There is no clear provision for analysing the cost incurred on the cloud architecture included for the business operationInternet ConnectivityThe failure of the internet connectivity in the cloud environment will disrupt the working efficiency of the business environment equipped with the sharing of information, resources, and others among the participating unit which in turn directly affect the working capability and productivity of the enterprise. Legal Compliance and standardThe cloud computing environment is associated with legal and statuary compliance requirement. The legal obligation should be resolved for effective deployment of cloud environment. Lack of Trust on the service providersIt is difficult to comply trust on the cloud computing service providers for accessing the information from the cloud environment. Performance of the computing architecture The performance of the computing architecture can be affected byadopting the policies of cloud computing environment Business Continuity programThe processing of the business unit will be continued until the availability of the resources and internet connectivity. The failure of the internet connectivity in the cloud environment will disrupt the working efficiency of the business environment equipped withthe sharing of information, resources, and others among the participating unit which in turn directly affect the working capability and productivity of the enterprise.
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Cloud Computing Security PDFlg...
|13
|3038
|39
IT Risks Associated with Cloud Computing and a Case Study of Data Breach Attack on Svitzerlg...
|6
|1455
|81
Cloud Privacy and Securitylg...
|21
|6371
|142
Information Security Assignment | Security and Privacylg...
|9
|2067
|44
Cloud Security and Risklg...
|19
|5365
|373
Data Security in Cloud Computinglg...
|14
|2815
|29
