Non-Functional Requirements Analysis
VerifiedAdded on 2020/05/28
|15
|2960
|83
AI Summary
This assignment investigates the crucial nature of non-functional requirements in software development. It analyzes various approaches to elicit and model these requirements, highlighting their influence on software quality attributes such as security, performance, usability, and maintainability. The text delves into research papers and real-world examples to provide a comprehensive understanding of the challenges and best practices associated with handling non-functional requirements throughout the Software Development Life Cycle (SDLC).
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: OBJECT AND DATA MODELLING
Elaboration phase: A Case Study of James Healthcare Centre (JHC)
Name of the Student:
Name of the University:
Elaboration phase: A Case Study of James Healthcare Centre (JHC)
Name of the Student:
Name of the University:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1OBJECT AND DATA MODELLING
Table of Contents
1. Functional and Non-Functional Requirements................................................................2
1.1 Functional Requirements...........................................................................................2
1.2 Non-Functional Requirements...................................................................................4
2. Identification of Use Cases and Use Case Diagram:.......................................................6
3. Domain Model Class Diagram:.......................................................................................7
4. Event Based Partition System:.........................................................................................8
5. SDLC Phases:..................................................................................................................8
Bibliography......................................................................................................................12
Table of Contents
1. Functional and Non-Functional Requirements................................................................2
1.1 Functional Requirements...........................................................................................2
1.2 Non-Functional Requirements...................................................................................4
2. Identification of Use Cases and Use Case Diagram:.......................................................6
3. Domain Model Class Diagram:.......................................................................................7
4. Event Based Partition System:.........................................................................................8
5. SDLC Phases:..................................................................................................................8
Bibliography......................................................................................................................12

2OBJECT AND DATA MODELLING
1. Functional and Non-Functional Requirements
1.1 Functional Requirements
The functional requirements that have been identified for JHC's (James Healthcare
Centre) new information system are listed as below:
Electronic Medical Records (EMR): It is referred to the documentation that is
associated with the data of patients to be stored in the information system. The information
system will hold personal information of the patient along with the record of their treatment
information. The tests, diagnosed diseases along with other information related to health
conditions will be stored within the EMR. The storing of such information related to patients will
facilitate monitoring of data over the time. This module in the system will help to keep track of
the certain parameters on the health of a patient such as blood pressure at a regular interval.
Database: The database acts as the backend platform for any system which is required
for storage of information. The database for the new information system will comprise every
record starting from EMR to payroll of the employee. There will be a centralized database
associated with the system so that it can be accessed by the every user according to their
predefined roles and authorization. There will be implementation of methods like verification
and validation for checking the accuracy and reliability of the data that is being input prior to
storing in the database. The encryption of the database is also required for increasing the security
of the information residing in the database.
Clinical Decision Support System (CDSS): It is referred to as the application that can
be used to analyze data such that healthcare providers can make decisions. The decisions will
relate to the clinical procedures that must be followed in context to the present health conditions
1. Functional and Non-Functional Requirements
1.1 Functional Requirements
The functional requirements that have been identified for JHC's (James Healthcare
Centre) new information system are listed as below:
Electronic Medical Records (EMR): It is referred to the documentation that is
associated with the data of patients to be stored in the information system. The information
system will hold personal information of the patient along with the record of their treatment
information. The tests, diagnosed diseases along with other information related to health
conditions will be stored within the EMR. The storing of such information related to patients will
facilitate monitoring of data over the time. This module in the system will help to keep track of
the certain parameters on the health of a patient such as blood pressure at a regular interval.
Database: The database acts as the backend platform for any system which is required
for storage of information. The database for the new information system will comprise every
record starting from EMR to payroll of the employee. There will be a centralized database
associated with the system so that it can be accessed by the every user according to their
predefined roles and authorization. There will be implementation of methods like verification
and validation for checking the accuracy and reliability of the data that is being input prior to
storing in the database. The encryption of the database is also required for increasing the security
of the information residing in the database.
Clinical Decision Support System (CDSS): It is referred to as the application that can
be used to analyze data such that healthcare providers can make decisions. The decisions will
relate to the clinical procedures that must be followed in context to the present health conditions

3OBJECT AND DATA MODELLING
of the patient. This module will be aggregated as a part of decision support system in the new
information system. The existing employees such as nurses, physicians along with other
healthcare professionals in JHC (James Healthcare Centre) will be able to utilize the CDSS so as
to prepare a diagnosis and reviewing that for enhancing the required outcome. Different
protocols will be used by CDSS for utilizing the data of patients with the help of an interface
engine. The system will display only the information that is authorized according to the user
access level.
Data Mining: This is an essential concept related to big data sets or large databases in
context to the any information system. The mining of data will be processed by information
system of the organization so as to evaluate the medical history of patients and associated
clinical research that is relevant for the present context. Data mining will be used by the
organization for recognition of possible events ranging from symptoms identified for diseases to
the application of medicinal drugs.
Computerized physician order entry (CPOE): It is considered as the process for
entering the order for medicines required by the medical professionals. The organization will be
able to eliminate the issues that often occur due to unrecognizable handwriting.
Billing: The system must be implemented with functionality such that it will
automatically calculate the amount that have to be paid by the patient. There will be automatic
generation of bill on behalf of the medicinal services provide to a patient as a discharge
procedure. The bill will reflect the entire breakdown and the costs that have been incurred for
each treatment process carried out on the patient.
of the patient. This module will be aggregated as a part of decision support system in the new
information system. The existing employees such as nurses, physicians along with other
healthcare professionals in JHC (James Healthcare Centre) will be able to utilize the CDSS so as
to prepare a diagnosis and reviewing that for enhancing the required outcome. Different
protocols will be used by CDSS for utilizing the data of patients with the help of an interface
engine. The system will display only the information that is authorized according to the user
access level.
Data Mining: This is an essential concept related to big data sets or large databases in
context to the any information system. The mining of data will be processed by information
system of the organization so as to evaluate the medical history of patients and associated
clinical research that is relevant for the present context. Data mining will be used by the
organization for recognition of possible events ranging from symptoms identified for diseases to
the application of medicinal drugs.
Computerized physician order entry (CPOE): It is considered as the process for
entering the order for medicines required by the medical professionals. The organization will be
able to eliminate the issues that often occur due to unrecognizable handwriting.
Billing: The system must be implemented with functionality such that it will
automatically calculate the amount that have to be paid by the patient. There will be automatic
generation of bill on behalf of the medicinal services provide to a patient as a discharge
procedure. The bill will reflect the entire breakdown and the costs that have been incurred for
each treatment process carried out on the patient.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4OBJECT AND DATA MODELLING
Tracking of Attendance: The system will also store the information related to
attendance of the employees in the organization. The system must be able to display the stored
information as per request of end-user to generate reports.
Audit: The system must have the capability to perform audits based on the stored data
and generation of audit reports in a well-designed and presentable format for stakeholders
associated with the organization. The internal controls used for the development of the
information system should be analyzed for creation of an audit planning and the responsibility,
authority and accountability should be defined. The analysis of the risk also important and it
should be divided into internet risk, control risk and detection risk. The audit is performed after
establishment of the internal review and gathering evidence for supporting the findings in the
audit.
Payroll: The system must have the provision to process information related to the salary
of staffs along with other expense and benefits offered by the organization.
Appointment: The system should support the process of online appointment so that the
patient can schedule their visit for medical checkup as per own convenience.
1.2 Non-Functional Requirements
The non-functional requirements that have been identified for JHC's (James Healthcare
Centre) new information system are listed as below:
Security: Security is an essential feature that have to be implemented in almost any
information system to ensure safety of the stored data. In the new information system of JHC,
there will be records on personal information of patient’s hence proper security measures have to
be implemented. The system must be able to protect sensitive information from external threats
Tracking of Attendance: The system will also store the information related to
attendance of the employees in the organization. The system must be able to display the stored
information as per request of end-user to generate reports.
Audit: The system must have the capability to perform audits based on the stored data
and generation of audit reports in a well-designed and presentable format for stakeholders
associated with the organization. The internal controls used for the development of the
information system should be analyzed for creation of an audit planning and the responsibility,
authority and accountability should be defined. The analysis of the risk also important and it
should be divided into internet risk, control risk and detection risk. The audit is performed after
establishment of the internal review and gathering evidence for supporting the findings in the
audit.
Payroll: The system must have the provision to process information related to the salary
of staffs along with other expense and benefits offered by the organization.
Appointment: The system should support the process of online appointment so that the
patient can schedule their visit for medical checkup as per own convenience.
1.2 Non-Functional Requirements
The non-functional requirements that have been identified for JHC's (James Healthcare
Centre) new information system are listed as below:
Security: Security is an essential feature that have to be implemented in almost any
information system to ensure safety of the stored data. In the new information system of JHC,
there will be records on personal information of patient’s hence proper security measures have to
be implemented. The system must be able to protect sensitive information from external threats

5OBJECT AND DATA MODELLING
or unauthorized access. The increase in the cyber-attacks have raised as a major concern related
to information systems so the organization can implement third party security applications. There
will be application of various protocols on the system of end-users for preventing exploitation
attacks.
Availability: This feature is significant in context to the new information system as there
is a requirement that the system must be accessible 24x7 for business processes. The downtime
of the system will result into disruption of all the business process that are running within the
organization. There is a requirement to develop an IT team with specialized persons for
maintaining the system and retain the functionality.
Usability: It is referred to as the feature that will ensure suitable interaction of end users
with the system. The system must be easily accessible and have an easy to use interface so that
the users are able to easily operate the system. The system will display different interfaces for
different users according to predefined roles and authorization level. The development team for
the system will conduct feedback analysis by gathering data on the design of the user interface so
as to make it simpler for the end users.
Scalability: This term relates to the capability of the system in context to management of
resources. The management of resources is an essential element for savings on cost incurred due
to the information system. The system must be able to provide provisions for making decisions
on how to reduce the utilization of resources for running the business processes.
or unauthorized access. The increase in the cyber-attacks have raised as a major concern related
to information systems so the organization can implement third party security applications. There
will be application of various protocols on the system of end-users for preventing exploitation
attacks.
Availability: This feature is significant in context to the new information system as there
is a requirement that the system must be accessible 24x7 for business processes. The downtime
of the system will result into disruption of all the business process that are running within the
organization. There is a requirement to develop an IT team with specialized persons for
maintaining the system and retain the functionality.
Usability: It is referred to as the feature that will ensure suitable interaction of end users
with the system. The system must be easily accessible and have an easy to use interface so that
the users are able to easily operate the system. The system will display different interfaces for
different users according to predefined roles and authorization level. The development team for
the system will conduct feedback analysis by gathering data on the design of the user interface so
as to make it simpler for the end users.
Scalability: This term relates to the capability of the system in context to management of
resources. The management of resources is an essential element for savings on cost incurred due
to the information system. The system must be able to provide provisions for making decisions
on how to reduce the utilization of resources for running the business processes.
6OBJECT AND DATA MODELLING
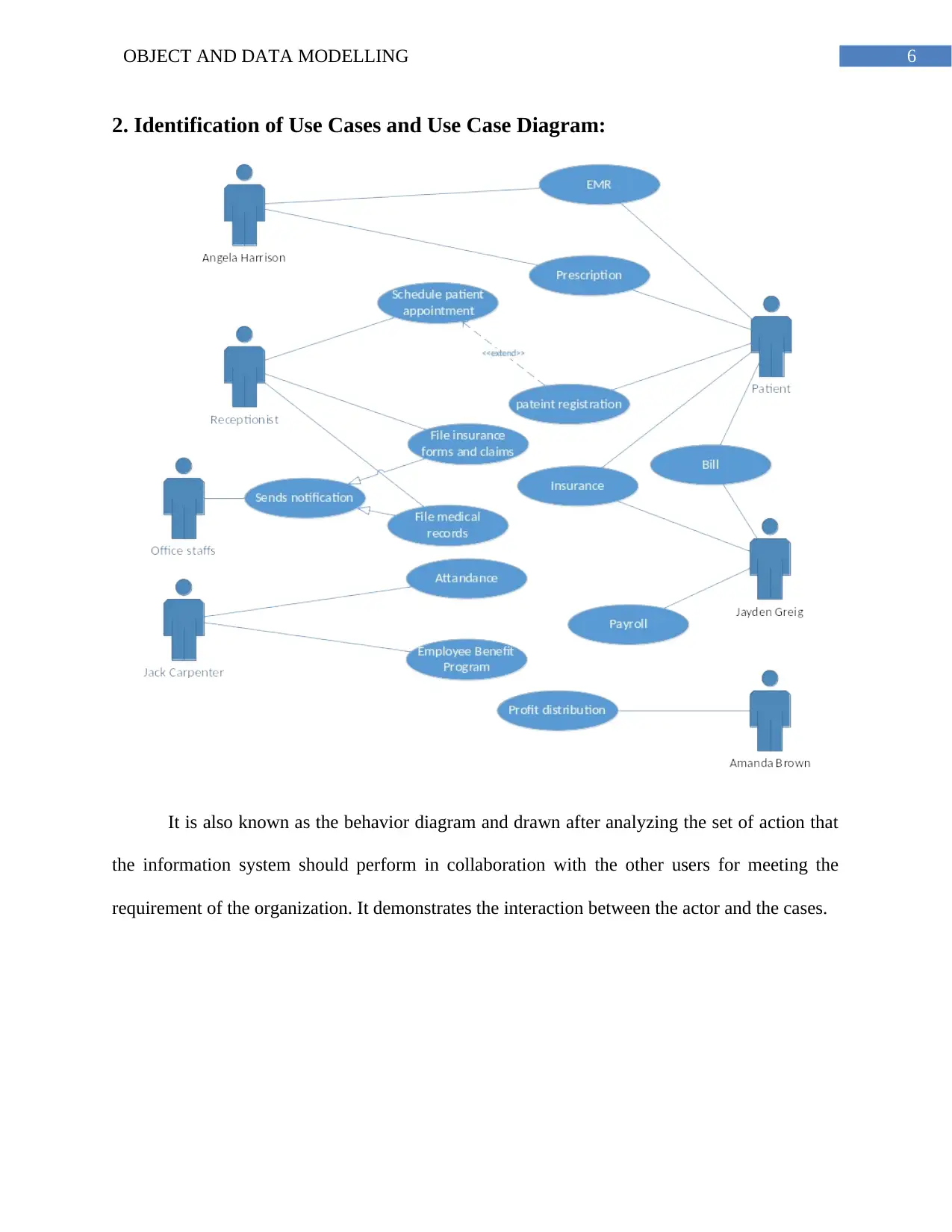
2. Identification of Use Cases and Use Case Diagram:
It is also known as the behavior diagram and drawn after analyzing the set of action that
the information system should perform in collaboration with the other users for meeting the
requirement of the organization. It demonstrates the interaction between the actor and the cases.
2. Identification of Use Cases and Use Case Diagram:
It is also known as the behavior diagram and drawn after analyzing the set of action that
the information system should perform in collaboration with the other users for meeting the
requirement of the organization. It demonstrates the interaction between the actor and the cases.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7OBJECT AND DATA MODELLING
3. Domain Model Class Diagram:
The above diagram is created by analyzing the classes and identification of its member, it
acts as a static diagram for the development team for the identification of the structure of the
hospital and relationship of the staffs, patients and the other members of the organization.
3. Domain Model Class Diagram:
The above diagram is created by analyzing the classes and identification of its member, it
acts as a static diagram for the development team for the identification of the structure of the
hospital and relationship of the staffs, patients and the other members of the organization.
8OBJECT AND DATA MODELLING
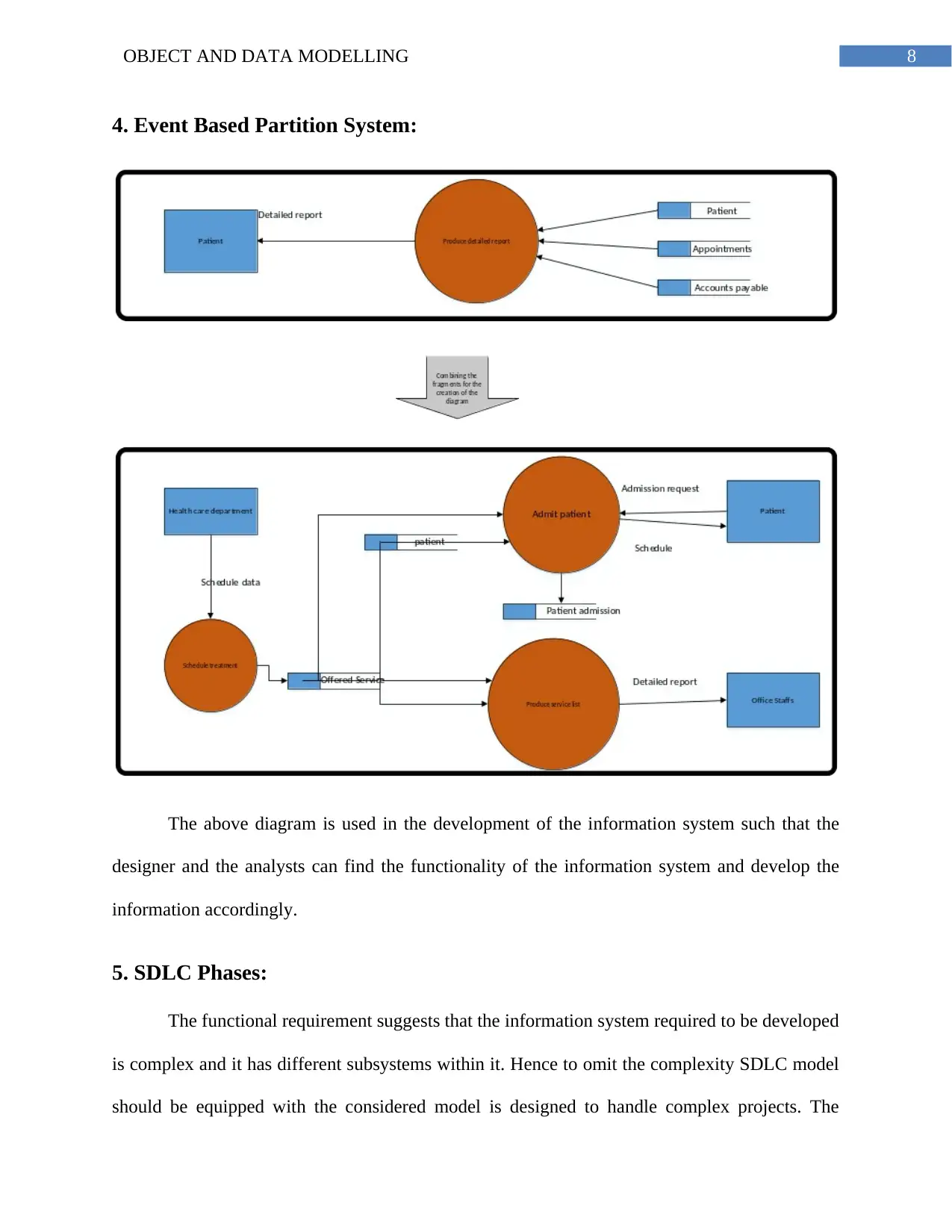
4. Event Based Partition System:
The above diagram is used in the development of the information system such that the
designer and the analysts can find the functionality of the information system and develop the
information accordingly.
5. SDLC Phases:
The functional requirement suggests that the information system required to be developed
is complex and it has different subsystems within it. Hence to omit the complexity SDLC model
should be equipped with the considered model is designed to handle complex projects. The
4. Event Based Partition System:
The above diagram is used in the development of the information system such that the
designer and the analysts can find the functionality of the information system and develop the
information accordingly.
5. SDLC Phases:
The functional requirement suggests that the information system required to be developed
is complex and it has different subsystems within it. Hence to omit the complexity SDLC model
should be equipped with the considered model is designed to handle complex projects. The

9OBJECT AND DATA MODELLING
model follows a realistic approach towards development of the information system. The agile
methodology is selected for the development of the healthcare information system because the
agile approach is highly flexible and it can adopt the changes in the information system during
the phases of development. The model is also designed to encourage cross-training and team
efforts. Non-functional requirement demands usability can be achieved by the partial work
solution as it is beneficial in gathering end-user’s feedback (GUPTA & LAXMI, 2015). When
compared with other models, the subject requires lesser effort in planning the project hence,
enabling the team (project) to manage the processes more accurately and comfortably. The agile
model offers flexibility to the developers which is required in the considered project.
Construction iterations, end game, pre-project planning, production, project initiation and
retirement are the phases of the agile model. Insight into the phases mentioned above with
consideration to the JHC system development are stated as follows:
Pre-project Planning: Pre-project planning or iteration-1 consists of project’s success,
business process opportunities and feasibility assessment. JHC can build a better future for
themselves by implementing IT infrastructure accurately and by enhancing the system processes
as it already has a very well-built customer base. JHC can improve their customer satisfaction
level as the system will be enabled with the capability of handling the request of the patients
quickly and easily (Jamro, 2015). This phase will also assist the organization to build a further
stronger customer base by attracting new customers. JHC’s stakeholders are hoping for a better
environment at the healthcare Centre where their requests process is quick, and the departmental
communication is effective. Implementation of the information system is the most suited strategy
for the subject of the paper in the current situation (Alshamrani & Bahattab, 2015). Business
process execution will also get cost-efficient after the implementation of the system. The
model follows a realistic approach towards development of the information system. The agile
methodology is selected for the development of the healthcare information system because the
agile approach is highly flexible and it can adopt the changes in the information system during
the phases of development. The model is also designed to encourage cross-training and team
efforts. Non-functional requirement demands usability can be achieved by the partial work
solution as it is beneficial in gathering end-user’s feedback (GUPTA & LAXMI, 2015). When
compared with other models, the subject requires lesser effort in planning the project hence,
enabling the team (project) to manage the processes more accurately and comfortably. The agile
model offers flexibility to the developers which is required in the considered project.
Construction iterations, end game, pre-project planning, production, project initiation and
retirement are the phases of the agile model. Insight into the phases mentioned above with
consideration to the JHC system development are stated as follows:
Pre-project Planning: Pre-project planning or iteration-1 consists of project’s success,
business process opportunities and feasibility assessment. JHC can build a better future for
themselves by implementing IT infrastructure accurately and by enhancing the system processes
as it already has a very well-built customer base. JHC can improve their customer satisfaction
level as the system will be enabled with the capability of handling the request of the patients
quickly and easily (Jamro, 2015). This phase will also assist the organization to build a further
stronger customer base by attracting new customers. JHC’s stakeholders are hoping for a better
environment at the healthcare Centre where their requests process is quick, and the departmental
communication is effective. Implementation of the information system is the most suited strategy
for the subject of the paper in the current situation (Alshamrani & Bahattab, 2015). Business
process execution will also get cost-efficient after the implementation of the system. The
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10OBJECT AND DATA MODELLING
goodwill of the organization will also get a boost after the implementation. The discussion above
can be emphasized to state that implementing the system is viable for the subject when
considered socially, economically and technologically.
Project Initiation: The fund for the project will be sanctioned after a meeting between
the project team manager and the sponsors along with the stakeholders of the firm. A detailed
discussion of various factors involved in the project and the validity of the project will be done
during the meeting. A decision on the members of the team will also be made by the manager
(project) with Jack Carpenter’s involvement (Karim, Saba & Albuolayan, 2017). After receiving
the permission to proceed with the project Jayden Greig will be approached to develop the
required environment and purchasing of the needed equipment. The project manager will be
burdened with estimating the budget.
Construction Iterations: The project team will develop high standard applications
within this phase. Based on the working application, feedbacks from the end-users will be
received. The next step will be to develop the application taking the basis of the data identified
by the designers and the analysts. The system developers will pursue the development of the
application (Sharma & Misra, 2017). The application will receive an upgrade based on the
feedback received and hence ensure the quality of the system. Excessive manner testing of the
developed application will also be pursued in the ongoing phase. Emily Cox will head the
evaluation process for the end-users feedbacks.
Transition: Deployment of the project is done during this phase. After receiving all the
feedback from the users that have been implemented in the system, the team will proceed with
the final testing of the system. This phase also serves the purpose of end-users training and
developing documents to assist the end-user in accessing the system (Summers, Joshi & Morkos,
goodwill of the organization will also get a boost after the implementation. The discussion above
can be emphasized to state that implementing the system is viable for the subject when
considered socially, economically and technologically.
Project Initiation: The fund for the project will be sanctioned after a meeting between
the project team manager and the sponsors along with the stakeholders of the firm. A detailed
discussion of various factors involved in the project and the validity of the project will be done
during the meeting. A decision on the members of the team will also be made by the manager
(project) with Jack Carpenter’s involvement (Karim, Saba & Albuolayan, 2017). After receiving
the permission to proceed with the project Jayden Greig will be approached to develop the
required environment and purchasing of the needed equipment. The project manager will be
burdened with estimating the budget.
Construction Iterations: The project team will develop high standard applications
within this phase. Based on the working application, feedbacks from the end-users will be
received. The next step will be to develop the application taking the basis of the data identified
by the designers and the analysts. The system developers will pursue the development of the
application (Sharma & Misra, 2017). The application will receive an upgrade based on the
feedback received and hence ensure the quality of the system. Excessive manner testing of the
developed application will also be pursued in the ongoing phase. Emily Cox will head the
evaluation process for the end-users feedbacks.
Transition: Deployment of the project is done during this phase. After receiving all the
feedback from the users that have been implemented in the system, the team will proceed with
the final testing of the system. This phase also serves the purpose of end-users training and
developing documents to assist the end-user in accessing the system (Summers, Joshi & Morkos,

11OBJECT AND DATA MODELLING
2014). The users are engaged in the testing phase and their feedback are documented for
application of any improvement in the developed information system.
Production: The purpose of this phase is to keep a check on the operations after the
deployment of the system in the organization. If any error is found in the product it is resolved
for increasing the security of the information system and deliver a quality software application.
Retirement: This phases server the purpose of retiring the older systems and on occasions
the operational system. At the retirement phase of the project the functionality and the features
are analyzed for replacing it with a new information system.
2014). The users are engaged in the testing phase and their feedback are documented for
application of any improvement in the developed information system.
Production: The purpose of this phase is to keep a check on the operations after the
deployment of the system in the organization. If any error is found in the product it is resolved
for increasing the security of the information system and deliver a quality software application.
Retirement: This phases server the purpose of retiring the older systems and on occasions
the operational system. At the retirement phase of the project the functionality and the features
are analyzed for replacing it with a new information system.

12OBJECT AND DATA MODELLING
Bibliography
Adams, K. (2015). Non-functional requirements in systems analysis and design (Vol. 28).
Springer.
Alshamrani, A., & Bahattab, A. (2015). A comparison between three SDLC models waterfall
model, spiral model, and Incremental/Iterative model. International Journal of Computer
Science Issues (IJCSI), 12(1), 106.
Coronel, C., & Morris, S. (2016). Database systems: design, implementation, & management.
Cengage Learning.
Eckhardt, J., Vogelsang, A., & Fernández, D. M. (2016, May). Are" Non-functional"
Requirements really Non-functional? An Investigation of Non-functional Requirements
in Practice. In Software Engineering (ICSE), 2016 IEEE/ACM 38th International
Conference on (pp. 832-842). IEEE.
GUPTA, R. S., & LAXMI, V. (2015). Software Development Life Cycle (SDLC)
Implementationin Information Technology & Management. International Journal of
Recent Advances in Information Technology & Management, 1(1).
Hasan, M. M., Loucopoulos, P., & Nikolaidou, M. (2014). Classification and qualitative analysis
of non-functional requirements approaches. In Enterprise, Business-Process and
Information Systems Modeling (pp. 348-362). Springer, Berlin, Heidelberg.
Jamro, M. (2015). SysML Modeling of Functional and Non-functional Requirements for IEC
61131-3 Control Systems. In Progress in Automation, Robotics and Measuring
Techniques(pp. 91-100). Springer International Publishing.
Bibliography
Adams, K. (2015). Non-functional requirements in systems analysis and design (Vol. 28).
Springer.
Alshamrani, A., & Bahattab, A. (2015). A comparison between three SDLC models waterfall
model, spiral model, and Incremental/Iterative model. International Journal of Computer
Science Issues (IJCSI), 12(1), 106.
Coronel, C., & Morris, S. (2016). Database systems: design, implementation, & management.
Cengage Learning.
Eckhardt, J., Vogelsang, A., & Fernández, D. M. (2016, May). Are" Non-functional"
Requirements really Non-functional? An Investigation of Non-functional Requirements
in Practice. In Software Engineering (ICSE), 2016 IEEE/ACM 38th International
Conference on (pp. 832-842). IEEE.
GUPTA, R. S., & LAXMI, V. (2015). Software Development Life Cycle (SDLC)
Implementationin Information Technology & Management. International Journal of
Recent Advances in Information Technology & Management, 1(1).
Hasan, M. M., Loucopoulos, P., & Nikolaidou, M. (2014). Classification and qualitative analysis
of non-functional requirements approaches. In Enterprise, Business-Process and
Information Systems Modeling (pp. 348-362). Springer, Berlin, Heidelberg.
Jamro, M. (2015). SysML Modeling of Functional and Non-functional Requirements for IEC
61131-3 Control Systems. In Progress in Automation, Robotics and Measuring
Techniques(pp. 91-100). Springer International Publishing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13OBJECT AND DATA MODELLING
Karim, N. S. A., Albuolayan, A., Saba, T., & Rehman, A. (2016). The practice of secure
software development in SDLC: an investigation through existing model and a case
study. Security and Communication Networks, 9(18), 5333-5345.
Karim, N. S. A., Saba, T., & Albuolayan, A. (2017). Analysis of software security model in
scenario of Software Development Life Cycle (SDLC). Journal of Engineering
Technology (ISSN: 0747-9964), 6(2), 304-316.
Khan, F., Jan, S. R., Tahir, M., Khan, S., & Ullah, F. (2016). Survey: Dealing Non-Functional
Requirements at Architecture Level. VFAST Transactions on Software Engineering, 9(2),
7-13.
Mc Hugh, M., McCaffery, F., Casey, V., & Pikkarainen, M. (2017). Integrating agile practices
with a medical device software development lifecycle.
Rahman, M., & Ripon, S. (2014). Elicitation and modeling non-functional requirements-a POS
case study. arXiv preprint arXiv:1403.1936.
Raturi, A., Penzenstadler, B., Tomlinson, B., & Richardson, D. (2014, June). Developing a
sustainability non-functional requirements framework. In Proceedings of the 3rd
International Workshop on Green and Sustainable Software(pp. 1-8). ACM.
Sharma, A., & Misra, P. K. (2017). Aspects of Enhancing Security in Software Development
Life Cycle. Advances in Computational Sciences and Technology, 10(2), 203-210.
Silva, A., Pinheiro, P. R., Albuquerque, A., & Barroso, J. (2016). Approach to Define a Non-
Functional Requirements Elicitation Guide Using a Customer Language. In SEKE (pp.
575-578).
Karim, N. S. A., Albuolayan, A., Saba, T., & Rehman, A. (2016). The practice of secure
software development in SDLC: an investigation through existing model and a case
study. Security and Communication Networks, 9(18), 5333-5345.
Karim, N. S. A., Saba, T., & Albuolayan, A. (2017). Analysis of software security model in
scenario of Software Development Life Cycle (SDLC). Journal of Engineering
Technology (ISSN: 0747-9964), 6(2), 304-316.
Khan, F., Jan, S. R., Tahir, M., Khan, S., & Ullah, F. (2016). Survey: Dealing Non-Functional
Requirements at Architecture Level. VFAST Transactions on Software Engineering, 9(2),
7-13.
Mc Hugh, M., McCaffery, F., Casey, V., & Pikkarainen, M. (2017). Integrating agile practices
with a medical device software development lifecycle.
Rahman, M., & Ripon, S. (2014). Elicitation and modeling non-functional requirements-a POS
case study. arXiv preprint arXiv:1403.1936.
Raturi, A., Penzenstadler, B., Tomlinson, B., & Richardson, D. (2014, June). Developing a
sustainability non-functional requirements framework. In Proceedings of the 3rd
International Workshop on Green and Sustainable Software(pp. 1-8). ACM.
Sharma, A., & Misra, P. K. (2017). Aspects of Enhancing Security in Software Development
Life Cycle. Advances in Computational Sciences and Technology, 10(2), 203-210.
Silva, A., Pinheiro, P. R., Albuquerque, A., & Barroso, J. (2016). Approach to Define a Non-
Functional Requirements Elicitation Guide Using a Customer Language. In SEKE (pp.
575-578).

14OBJECT AND DATA MODELLING
Summers, J. D., Joshi, S., & Morkos, B. (2014, August). Requirements evolution: Relating
functional and non-functional requirement change on student project success.
In International Design Engineering Technical Conferences and Computers and
Information in Engineering Conference.
Summers, J. D., Joshi, S., & Morkos, B. (2014, August). Requirements evolution: Relating
functional and non-functional requirement change on student project success.
In International Design Engineering Technical Conferences and Computers and
Information in Engineering Conference.
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





