Cybersecurity Threats and Countermeasures
VerifiedAdded on 2020/02/24
|13
|3436
|93
AI Summary
This assignment delves into the multifaceted world of cybersecurity threats, examining various types such as malware, spyware, phishing, and social engineering. It analyzes the vulnerabilities posed by both external actors like hackers and internal threats originating from employees or disgruntled individuals. The document highlights the impact of these threats on individuals, organizations, and critical infrastructure. Furthermore, it explores a range of countermeasures and best practices for mitigating cybersecurity risks, including firewalls, antivirus software, multi-factor authentication, security awareness training, and incident response planning.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: IT Risk Management 1
IT Risk Management
Name
Date
IT Risk Management
Name
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT Risk Management 2
Contents
Illustration of VIC Government Security Risks...........................................................................................3
ICT risks and security concerns for the VIC public sector data...................................................................4
Classification of Risks.................................................................................................................................5
Comparative Analysis of Deliberate and Accidental Threats......................................................................7
Challenges the VIC government will face in deciding whether ICT security should be handled internally
or outsource.................................................................................................................................................9
Risk and Uncertainty.................................................................................................................................11
Different approaches VIC government can use for risk control.................................................................11
References.................................................................................................................................................13
Contents
Illustration of VIC Government Security Risks...........................................................................................3
ICT risks and security concerns for the VIC public sector data...................................................................4
Classification of Risks.................................................................................................................................5
Comparative Analysis of Deliberate and Accidental Threats......................................................................7
Challenges the VIC government will face in deciding whether ICT security should be handled internally
or outsource.................................................................................................................................................9
Risk and Uncertainty.................................................................................................................................11
Different approaches VIC government can use for risk control.................................................................11
References.................................................................................................................................................13
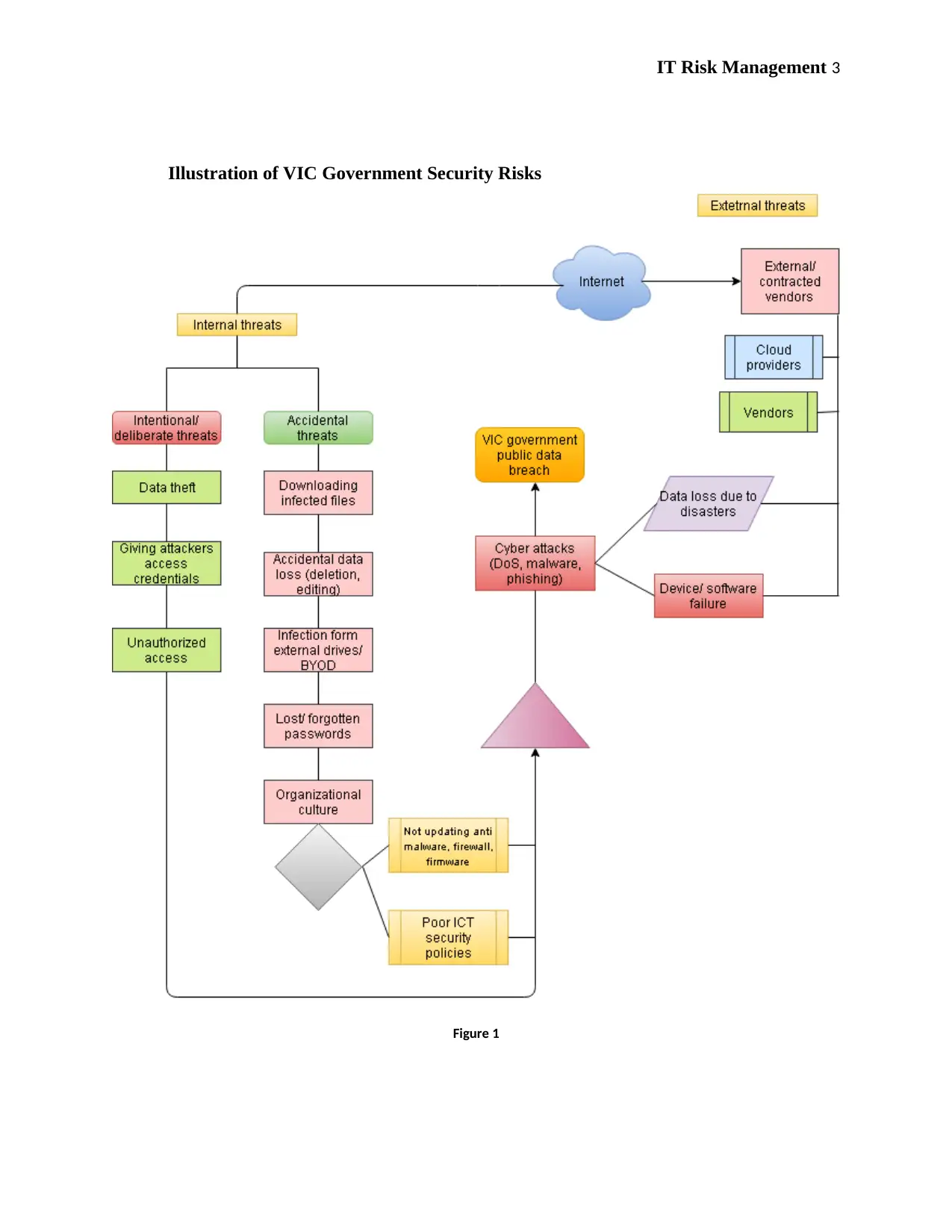
IT Risk Management 3
Illustration of VIC Government Security Risks
Figure 1
Illustration of VIC Government Security Risks
Figure 1

IT Risk Management 4
ICT risks and security concerns for the VIC public sector data
Based on figure I above, there are two main categories of threats to the VIC government
public sector data, based on the Victoria Protective Data Security Framework; internal threats
and external threats. The internal threats are further subdivided into employee risks/ threats,
where the employees are the cause of security risks. Employee risks can further be subdivided
into intentional/ malicious threats and unintentional threats. The intentional threats/ risks include
malicious theft of information for monetary gain or just malice where a staff member
intentionally steals and shares sensitive information with malicious third parties. This may also
be achieved by staff leaving backdoors for attackers to access the VIC public sector information
without authorized access, such as by not implementing strong security policies in access points
such as on routes and external access. Unauthorized access to information or editing information
deliberately, such as overwriting or deletion of public sector data is another form of intentional
security risks. Unintended internal risks from staff/ employees include accidental deletion,
overwriting, or editing of information, or failure to save edited information, causing malware
infection by using external storage devices that are infected, or exposing the VIC public sector
data by exposing access credentials.
Inability to follow set ICT security policies either due to ignorance or lack of such
policies is also another unintended internal risk. Another source of internal risks includes
organizational culture that is due to several factors of omission and commission. These include
poor security policies such as failure to use strong passwords, not updating/ patching software
regularly, and inability to constantly review and update security policies and threats, and
noncompliance. Other factors/ causes for risks due to organizational culture include hiring ICT
staff that do not meet the standards (are unqualified) and using external vendors without vetting.
Cultural issues also include lack of clear policies such as restricting access to specific
information, failure to encrypt information, poor setup for data bases and backups, and inability
to undertake sensitization initiatives on ICT risks to educate users/ employees. Because there is
increased use of the internet, there are other external risks that include cyber-attacks, loss of data
due to disasters, and risks of data loss/ theft due to external service providers, such as cloud
service providers or software/ device providers and vendors whose products fail, or have
ICT risks and security concerns for the VIC public sector data
Based on figure I above, there are two main categories of threats to the VIC government
public sector data, based on the Victoria Protective Data Security Framework; internal threats
and external threats. The internal threats are further subdivided into employee risks/ threats,
where the employees are the cause of security risks. Employee risks can further be subdivided
into intentional/ malicious threats and unintentional threats. The intentional threats/ risks include
malicious theft of information for monetary gain or just malice where a staff member
intentionally steals and shares sensitive information with malicious third parties. This may also
be achieved by staff leaving backdoors for attackers to access the VIC public sector information
without authorized access, such as by not implementing strong security policies in access points
such as on routes and external access. Unauthorized access to information or editing information
deliberately, such as overwriting or deletion of public sector data is another form of intentional
security risks. Unintended internal risks from staff/ employees include accidental deletion,
overwriting, or editing of information, or failure to save edited information, causing malware
infection by using external storage devices that are infected, or exposing the VIC public sector
data by exposing access credentials.
Inability to follow set ICT security policies either due to ignorance or lack of such
policies is also another unintended internal risk. Another source of internal risks includes
organizational culture that is due to several factors of omission and commission. These include
poor security policies such as failure to use strong passwords, not updating/ patching software
regularly, and inability to constantly review and update security policies and threats, and
noncompliance. Other factors/ causes for risks due to organizational culture include hiring ICT
staff that do not meet the standards (are unqualified) and using external vendors without vetting.
Cultural issues also include lack of clear policies such as restricting access to specific
information, failure to encrypt information, poor setup for data bases and backups, and inability
to undertake sensitization initiatives on ICT risks to educate users/ employees. Because there is
increased use of the internet, there are other external risks that include cyber-attacks, loss of data
due to disasters, and risks of data loss/ theft due to external service providers, such as cloud
service providers or software/ device providers and vendors whose products fail, or have
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
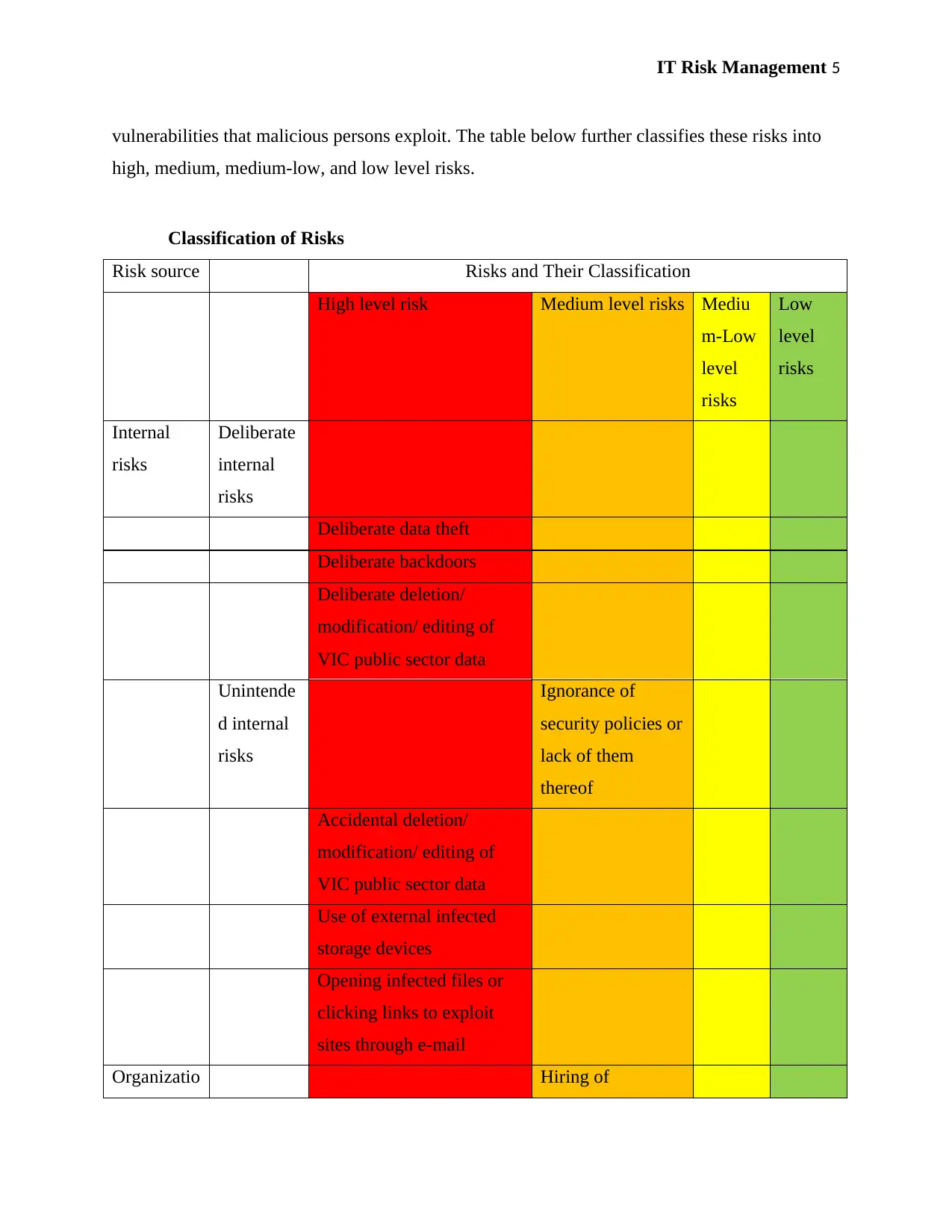
IT Risk Management 5
vulnerabilities that malicious persons exploit. The table below further classifies these risks into
high, medium, medium-low, and low level risks.
Classification of Risks
Risk source Risks and Their Classification
High level risk Medium level risks Mediu
m-Low
level
risks
Low
level
risks
Internal
risks
Deliberate
internal
risks
Deliberate data theft
Deliberate backdoors
Deliberate deletion/
modification/ editing of
VIC public sector data
Unintende
d internal
risks
Ignorance of
security policies or
lack of them
thereof
Accidental deletion/
modification/ editing of
VIC public sector data
Use of external infected
storage devices
Opening infected files or
clicking links to exploit
sites through e-mail
Organizatio Hiring of
vulnerabilities that malicious persons exploit. The table below further classifies these risks into
high, medium, medium-low, and low level risks.
Classification of Risks
Risk source Risks and Their Classification
High level risk Medium level risks Mediu
m-Low
level
risks
Low
level
risks
Internal
risks
Deliberate
internal
risks
Deliberate data theft
Deliberate backdoors
Deliberate deletion/
modification/ editing of
VIC public sector data
Unintende
d internal
risks
Ignorance of
security policies or
lack of them
thereof
Accidental deletion/
modification/ editing of
VIC public sector data
Use of external infected
storage devices
Opening infected files or
clicking links to exploit
sites through e-mail
Organizatio Hiring of
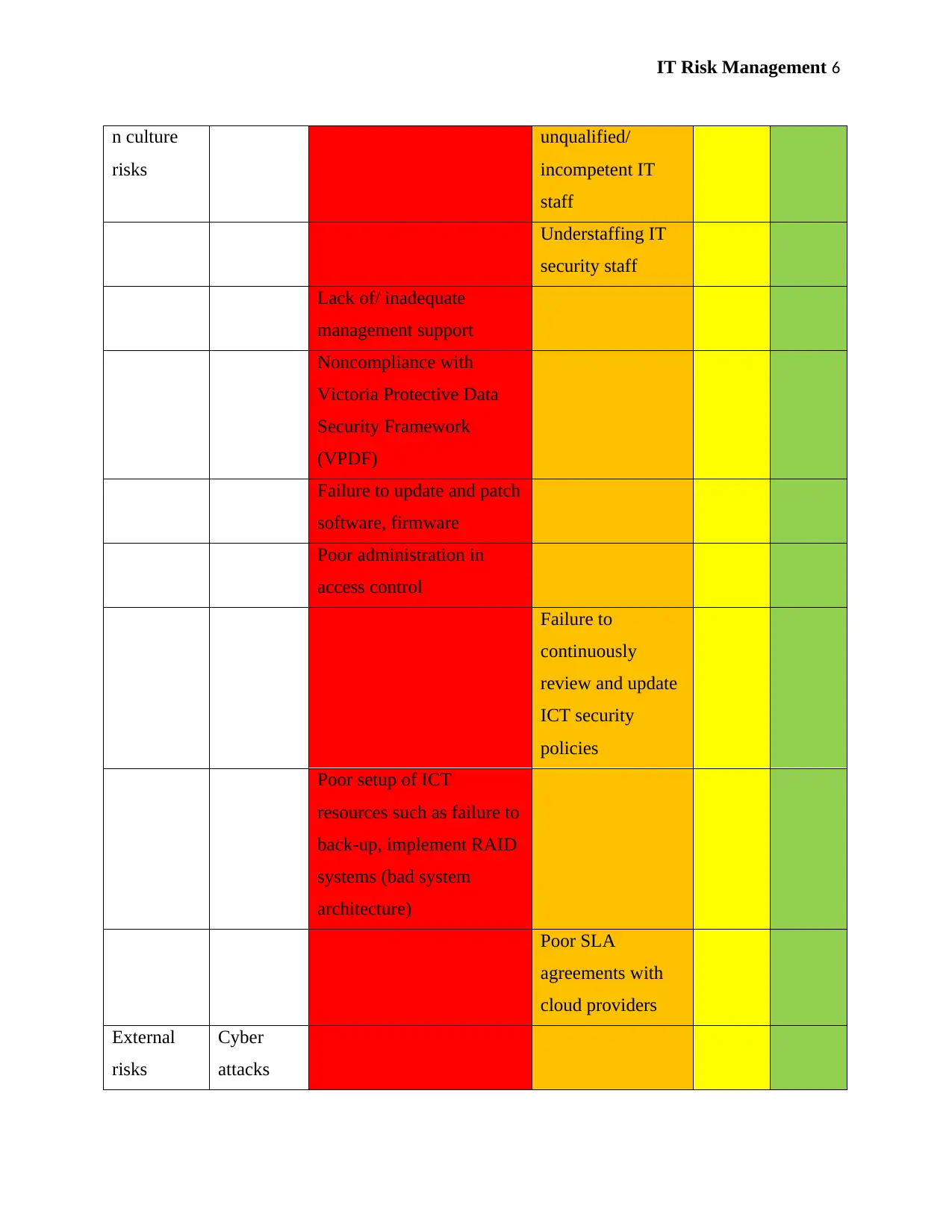
IT Risk Management 6
n culture
risks
unqualified/
incompetent IT
staff
Understaffing IT
security staff
Lack of/ inadequate
management support
Noncompliance with
Victoria Protective Data
Security Framework
(VPDF)
Failure to update and patch
software, firmware
Poor administration in
access control
Failure to
continuously
review and update
ICT security
policies
Poor setup of ICT
resources such as failure to
back-up, implement RAID
systems (bad system
architecture)
Poor SLA
agreements with
cloud providers
External
risks
Cyber
attacks
n culture
risks
unqualified/
incompetent IT
staff
Understaffing IT
security staff
Lack of/ inadequate
management support
Noncompliance with
Victoria Protective Data
Security Framework
(VPDF)
Failure to update and patch
software, firmware
Poor administration in
access control
Failure to
continuously
review and update
ICT security
policies
Poor setup of ICT
resources such as failure to
back-up, implement RAID
systems (bad system
architecture)
Poor SLA
agreements with
cloud providers
External
risks
Cyber
attacks

IT Risk Management 7
Malware, DoS, DDoS,
viruses
Phishin
g
Data loss
Data loss due to disasters
such as fires, unreadable
data
Comparative Analysis of Deliberate and Accidental Threats
Deliberate threats include intentional threats and risks to the VIC public sector data
accruing from deliberate and intentional actions that pose risks to data. Such risks are usually due
to human intervention/ mediation. For instance, one of the biggest deliberate threats to data is
theft of such data either out of malice or for financial gain in which a staffer deliberately exposes
or gives confidential public sector data to third parties with malicious intent, such as hackers or
scammers. This can also happen when a disgruntled staff member, such as a fired/ demoted
employee providers malicious entities with passwords for accessing confidential public sector
data. This can happen where staff steals data from internal servers or from the cloud storage
servers for which they have access. This is a very high level risk, since security policies can be
overridden by such actions/ threats. These attacks carry huge risks because there is a high
potential for sensitive data being exposed to the public, or personal details being stolen and sold
for financial gain, with few options for detection of such actions (Rowe, Akman, Smith &
Tomison, 2013).
Deliberate threats can also be external in which malicious entities use various tools to
access and misuse/ exploit the VIC public sector data. Such exploits are undertaken through
phishing, malware attacks; for instance, sending files/ links containing malware to staff e-mail
accounts that then gives the hackers access to the public sector data. These are done using
malware such as ransom-ware, worms, viruses, or Trojans that either gain access to the public
Malware, DoS, DDoS,
viruses
Phishin
g
Data loss
Data loss due to disasters
such as fires, unreadable
data
Comparative Analysis of Deliberate and Accidental Threats
Deliberate threats include intentional threats and risks to the VIC public sector data
accruing from deliberate and intentional actions that pose risks to data. Such risks are usually due
to human intervention/ mediation. For instance, one of the biggest deliberate threats to data is
theft of such data either out of malice or for financial gain in which a staffer deliberately exposes
or gives confidential public sector data to third parties with malicious intent, such as hackers or
scammers. This can also happen when a disgruntled staff member, such as a fired/ demoted
employee providers malicious entities with passwords for accessing confidential public sector
data. This can happen where staff steals data from internal servers or from the cloud storage
servers for which they have access. This is a very high level risk, since security policies can be
overridden by such actions/ threats. These attacks carry huge risks because there is a high
potential for sensitive data being exposed to the public, or personal details being stolen and sold
for financial gain, with few options for detection of such actions (Rowe, Akman, Smith &
Tomison, 2013).
Deliberate threats can also be external in which malicious entities use various tools to
access and misuse/ exploit the VIC public sector data. Such exploits are undertaken through
phishing, malware attacks; for instance, sending files/ links containing malware to staff e-mail
accounts that then gives the hackers access to the public sector data. These are done using
malware such as ransom-ware, worms, viruses, or Trojans that either gain access to the public
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management 8
sector data and steals and sends the information over the network, or denies the users access to
this data. Such attacks can also result in theft and loss of access to crucial data where the
attackers demand ransom, as happened in the UK when the National health Services (NHS)
computer systems were attacked by a deadly ransom-ware (‘Fox News,’ 2017), or permanent
deletion of information, such as the attack on Aramco, the Saudi Arabia petroleum company
where all its data stored in computers and servers were permanently deleted in a matter of
minutes (Perlroth, 2012).
Such deliberate attacks can also lead to data loss, as happened in Australia and other
countries where a malware propagated itself over networks, attacking office and home computers
and encrypting files such that users could not access them (Griffith, 2017). Such deliberate risks
are the most dangerous, with their risk level being very high and high risks. The reason why they
are very high or high risk threats is because of the potential/ possible level of damage, as well as
the difficulty in controlling/ preventing them. While cyber-attacks can be prevented/ mitigated
through such security measures as implementing strong firewalls and using network analysis
tools that are regularly patched and updated, along with networks isolation use of antimalware
software, malware attacks have become even more sophisticated (Bakhtiyari & Ismail,2012).
Malware have become sophisticated and stealthy by confusing detection tools, such as through
multiple stage loading, environmental awareness, obfuscation of internal data, and time based
evasion techniques (Mazurczyk & Caviglione, 2015). Such deliberate attacks, either internal or
undertaken by external entities are very destructive; hence their classification as being either
very high or high risk attacks (Choo, 2011).
Accidental threats also pose huge risks to data security; while such actions are
unintended, the consequences can also be massive. For instance, when a user accidentally deletes
or overwrites, or edits but fails to save sensitive data such as that stored in the cloud; such data
may not be recoverable, or have a steep price for recovery. Third party vendors, contractors, and
even staff with privileged access to certain data have caused breaches to data by accident. The
vast majority of data breaches such as network openings or malware invasion have been caused
by innocent accidents, such as when a user accidentally overwrites data (Durbin, 2016). While
such innocent accidents can lead to the loss of data, modern public (and private)organizations
employ measures where data is backed up in real time; such mistakes and errors can also be
sector data and steals and sends the information over the network, or denies the users access to
this data. Such attacks can also result in theft and loss of access to crucial data where the
attackers demand ransom, as happened in the UK when the National health Services (NHS)
computer systems were attacked by a deadly ransom-ware (‘Fox News,’ 2017), or permanent
deletion of information, such as the attack on Aramco, the Saudi Arabia petroleum company
where all its data stored in computers and servers were permanently deleted in a matter of
minutes (Perlroth, 2012).
Such deliberate attacks can also lead to data loss, as happened in Australia and other
countries where a malware propagated itself over networks, attacking office and home computers
and encrypting files such that users could not access them (Griffith, 2017). Such deliberate risks
are the most dangerous, with their risk level being very high and high risks. The reason why they
are very high or high risk threats is because of the potential/ possible level of damage, as well as
the difficulty in controlling/ preventing them. While cyber-attacks can be prevented/ mitigated
through such security measures as implementing strong firewalls and using network analysis
tools that are regularly patched and updated, along with networks isolation use of antimalware
software, malware attacks have become even more sophisticated (Bakhtiyari & Ismail,2012).
Malware have become sophisticated and stealthy by confusing detection tools, such as through
multiple stage loading, environmental awareness, obfuscation of internal data, and time based
evasion techniques (Mazurczyk & Caviglione, 2015). Such deliberate attacks, either internal or
undertaken by external entities are very destructive; hence their classification as being either
very high or high risk attacks (Choo, 2011).
Accidental threats also pose huge risks to data security; while such actions are
unintended, the consequences can also be massive. For instance, when a user accidentally deletes
or overwrites, or edits but fails to save sensitive data such as that stored in the cloud; such data
may not be recoverable, or have a steep price for recovery. Third party vendors, contractors, and
even staff with privileged access to certain data have caused breaches to data by accident. The
vast majority of data breaches such as network openings or malware invasion have been caused
by innocent accidents, such as when a user accidentally overwrites data (Durbin, 2016). While
such innocent accidents can lead to the loss of data, modern public (and private)organizations
employ measures where data is backed up in real time; such mistakes and errors can also be

IT Risk Management 9
rectified through instant data recover, for instance, for accidentally deleted data, or data
reconstruction and editing (Rashmi et al., 2015). However, the problem becomes exacerbated
when employee or vendor mistakes open doors for external entities such as hackers; this can
happen by vendors not updating or patching their software and firmware, or when an employee
opens a mail with malware embedded in them, or clicks links to malicious sites that then initiate
attacks that, for instance, erase data and lead to theft of data. In such cases, there is a confluence
of both accidental mistakes and external cyber threats that amplify the effect of the accidental
threats. In retrospect, therefore, accidental threats are ranked as medium to high; given that some
accidents can be rectified (medium threats) while some accidents can open doors to more serious
risks and threats to public sector data, such as malware attacks or identity theft (Rasmi et al.,
2015).
Challenges the VIC government will face in deciding whether ICT security should
be handled internally or outsource
ICT security for public sector data is highly critical; being a government agency, the VIC
government will most definitely be attacked, either through internal or external risks. The
challenge is in whether security should be handled in-house or be outsourced to professionals.
While outsourcing security has its benefits; there are also several challenges. Existing laws may
prevent, or hinder access to personal information by third parties. Outsourcing essentially implies
that aspects of data management, such as processing or storage/ backups are done by external
third party organizations (Libicki, 2000). Under the Australian Privacy Act, an entity such as the
VIC government is the holder the public sector data for its citizens; and so it is obliged to ensure
this data and information remains private, even if such data management, such as storage is
outsourced to third parties, but it’s the VIC government with express authority and right to deal
with the information. For instance, storing public information in the cloud, a service offered by
third parties may allow the vendors including human resource) software vendors to have access
to the VIC public sector information data bases through shared storage of log-in ID. Further, the
third party to which the security is outsourced may make mistakes or lead to data security
breaches, through acts of omission or commission; the VIC government will still remain liable
for such data breaches.
rectified through instant data recover, for instance, for accidentally deleted data, or data
reconstruction and editing (Rashmi et al., 2015). However, the problem becomes exacerbated
when employee or vendor mistakes open doors for external entities such as hackers; this can
happen by vendors not updating or patching their software and firmware, or when an employee
opens a mail with malware embedded in them, or clicks links to malicious sites that then initiate
attacks that, for instance, erase data and lead to theft of data. In such cases, there is a confluence
of both accidental mistakes and external cyber threats that amplify the effect of the accidental
threats. In retrospect, therefore, accidental threats are ranked as medium to high; given that some
accidents can be rectified (medium threats) while some accidents can open doors to more serious
risks and threats to public sector data, such as malware attacks or identity theft (Rasmi et al.,
2015).
Challenges the VIC government will face in deciding whether ICT security should
be handled internally or outsource
ICT security for public sector data is highly critical; being a government agency, the VIC
government will most definitely be attacked, either through internal or external risks. The
challenge is in whether security should be handled in-house or be outsourced to professionals.
While outsourcing security has its benefits; there are also several challenges. Existing laws may
prevent, or hinder access to personal information by third parties. Outsourcing essentially implies
that aspects of data management, such as processing or storage/ backups are done by external
third party organizations (Libicki, 2000). Under the Australian Privacy Act, an entity such as the
VIC government is the holder the public sector data for its citizens; and so it is obliged to ensure
this data and information remains private, even if such data management, such as storage is
outsourced to third parties, but it’s the VIC government with express authority and right to deal
with the information. For instance, storing public information in the cloud, a service offered by
third parties may allow the vendors including human resource) software vendors to have access
to the VIC public sector information data bases through shared storage of log-in ID. Further, the
third party to which the security is outsourced may make mistakes or lead to data security
breaches, through acts of omission or commission; the VIC government will still remain liable
for such data breaches.

IT Risk Management 10
Outsourcing security, a concept termed ISO (information security outsourcing) has the
challenge of creating complexities, in environments that are less secure, while the organization is
still supposed to be responsible for such data. ISO is a concept that has still not been adopted
significantly, with research showing that 59% of firms outsource some aspects of their
information security, such as penetration testing. However, just 13% of organizations have
reported, according to the same research, to have adopted full ISO. When many vendors are
involved, there are added complexities although some risks (pertaining to security) are reduced.
Outsourcing requires an elaborate ICT security framework to evaluate risks pertaining to
information integrity, confidentiality, and availability where many different vendors are to be
evaluated. This approach also creates a new security model that must be evaluated. Looking at
the other aspect of in-house security management; the risk profile and analysis show that internal
threats are exacerbated by cultural issues, such as lax security measures. Generally, public
organizations tend to be more lax on ICT security compared to private organizations. Further, a
systematic cultural issue can be multiplied at different levels of the organization, further
enhancing the threat of both internal and external ICT security threats.
Because governments are not premier ICT service businesses, there is a tendency to have
unsuitable internal security policies or gaps in implementing the outlined security policies. The
best approach, therefore would be to adopt ISO but with a new security and risk profile
assessment or use a hybrid model between outsourcing some security aspects, such as encryption
and before-incident analysis of all threats before they reach the governments’ actual servers. The
VIC government can also institute better security protocols such as restricted access and other
measures including updating and patching anti malware and network devices firmware, while
ensuring only authorized persons can access data. ISO becomes feasible when combined with
cloud computing to improve security and business process continuity in case of a disaster where
data is lost; the VIC government can continue offering services through the cloud restoration and
backup platform. Further, the risk profile shows that vendor threats are medium to high, but
internal threats are high or very high.
Outsourcing security, a concept termed ISO (information security outsourcing) has the
challenge of creating complexities, in environments that are less secure, while the organization is
still supposed to be responsible for such data. ISO is a concept that has still not been adopted
significantly, with research showing that 59% of firms outsource some aspects of their
information security, such as penetration testing. However, just 13% of organizations have
reported, according to the same research, to have adopted full ISO. When many vendors are
involved, there are added complexities although some risks (pertaining to security) are reduced.
Outsourcing requires an elaborate ICT security framework to evaluate risks pertaining to
information integrity, confidentiality, and availability where many different vendors are to be
evaluated. This approach also creates a new security model that must be evaluated. Looking at
the other aspect of in-house security management; the risk profile and analysis show that internal
threats are exacerbated by cultural issues, such as lax security measures. Generally, public
organizations tend to be more lax on ICT security compared to private organizations. Further, a
systematic cultural issue can be multiplied at different levels of the organization, further
enhancing the threat of both internal and external ICT security threats.
Because governments are not premier ICT service businesses, there is a tendency to have
unsuitable internal security policies or gaps in implementing the outlined security policies. The
best approach, therefore would be to adopt ISO but with a new security and risk profile
assessment or use a hybrid model between outsourcing some security aspects, such as encryption
and before-incident analysis of all threats before they reach the governments’ actual servers. The
VIC government can also institute better security protocols such as restricted access and other
measures including updating and patching anti malware and network devices firmware, while
ensuring only authorized persons can access data. ISO becomes feasible when combined with
cloud computing to improve security and business process continuity in case of a disaster where
data is lost; the VIC government can continue offering services through the cloud restoration and
backup platform. Further, the risk profile shows that vendor threats are medium to high, but
internal threats are high or very high.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT Risk Management 11
Risk and Uncertainty
Risk refers to the potential to either gain or lose value; since risk is a probability, it can be given
a value to make it quantitative, for example, the probability of suffering a cyber-attack for Vic
government is once every four months. The risk helps to create a risk profile that can then be
used to hierarchically classify risks, and then deal with them based on the risk level (Lloyd,
2008). Uncertainty, on the other hand, is a qualitative and merely perceptive, it is the level of
doubt over something, for instance, the margin of error for measuring a security risk. It does not
have a straightforward description, although it is always present; for example, whether the VIC
government should adopt ISO or depend on in-house ICT security measures; there is uncertainty
on data security if it adopted ISO.
Different approaches VIC government can use for risk control
The VIC government can use a hybrid and integrated approach to ICT risk control in handling
public data; the risk management profile should begin internally before some aspects can be
outsourced. Internally, the government should implement the VPSF in Toto. The first line of
defense is to undertake a comprehensive security and risk analysis and then, using the VPSF
framework, develop a security policy that is updated regularly. The security policy should ensure
that access to information is restricted and on a need-to-use basis. For sensitive information or
those stored in the cloud, and for certain actions, such as modifying, deleting, or transferring
data, and the user must be authenticated using a two-step log-in process involving mobile
(Almutairi et al., 2012). For cloud applications, there must be strong APIs that are designed to
automatically log out when there is no activity for a given period. VIC should also implement
regulations for restricted area IT rooms to control access using biometrics (Akhgar & Arabnia,
2014).
Users must have strong password authentication and administrators must constantly
monitor logging activity, with actions such as downloading databases being restricted. The
network devices such as wireless access points must have strong encrypted passwords and data
should be sent in encrypted format. The VIC government should adopt a hybrid cloud and
virtualization to back up its data in case of data loss, in multiple geographical locations with
providers (Stair & Reynolds, 2015). Further, the government must use basic security measures
Risk and Uncertainty
Risk refers to the potential to either gain or lose value; since risk is a probability, it can be given
a value to make it quantitative, for example, the probability of suffering a cyber-attack for Vic
government is once every four months. The risk helps to create a risk profile that can then be
used to hierarchically classify risks, and then deal with them based on the risk level (Lloyd,
2008). Uncertainty, on the other hand, is a qualitative and merely perceptive, it is the level of
doubt over something, for instance, the margin of error for measuring a security risk. It does not
have a straightforward description, although it is always present; for example, whether the VIC
government should adopt ISO or depend on in-house ICT security measures; there is uncertainty
on data security if it adopted ISO.
Different approaches VIC government can use for risk control
The VIC government can use a hybrid and integrated approach to ICT risk control in handling
public data; the risk management profile should begin internally before some aspects can be
outsourced. Internally, the government should implement the VPSF in Toto. The first line of
defense is to undertake a comprehensive security and risk analysis and then, using the VPSF
framework, develop a security policy that is updated regularly. The security policy should ensure
that access to information is restricted and on a need-to-use basis. For sensitive information or
those stored in the cloud, and for certain actions, such as modifying, deleting, or transferring
data, and the user must be authenticated using a two-step log-in process involving mobile
(Almutairi et al., 2012). For cloud applications, there must be strong APIs that are designed to
automatically log out when there is no activity for a given period. VIC should also implement
regulations for restricted area IT rooms to control access using biometrics (Akhgar & Arabnia,
2014).
Users must have strong password authentication and administrators must constantly
monitor logging activity, with actions such as downloading databases being restricted. The
network devices such as wireless access points must have strong encrypted passwords and data
should be sent in encrypted format. The VIC government should adopt a hybrid cloud and
virtualization to back up its data in case of data loss, in multiple geographical locations with
providers (Stair & Reynolds, 2015). Further, the government must use basic security measures

IT Risk Management 12
including physical and software firewalls, network analysis and monitors, antimalware, all which
must be updated regularly; same for firmware patches (Brown, 2014). The VIC government an
outsource security monitoring for the network where a company like RedTM uses a virtual version
of its ICT system to monitor malware and give warnings. The system works in a way that if a
malware targets VIC government, it first enters the virtual machines, where it can exploit
thinking those are the actual physical datacenters and RED will identify such malicious activity
and give warnings.
including physical and software firewalls, network analysis and monitors, antimalware, all which
must be updated regularly; same for firmware patches (Brown, 2014). The VIC government an
outsource security monitoring for the network where a company like RedTM uses a virtual version
of its ICT system to monitor malware and give warnings. The system works in a way that if a
malware targets VIC government, it first enters the virtual machines, where it can exploit
thinking those are the actual physical datacenters and RED will identify such malicious activity
and give warnings.

IT Risk Management 13
References
Akhgar, B., & Arabnia, H. (2014). Emerging trends in ICT security. Amsterdam ; Boston :
Morgan Kaufmann/Elsevier,
Almutairi, A., Sarfraz, M., Basalamah, S., Aref, W., & Ghafoor, A. (January 01, 2012). A
Distributed Access Control Architecture for Cloud Computing. IEEE Software, 29, 2, 36-
44.
Bakhtiyari, S. A., & Ismail, Z. (January 01, 2012). A Tree Model for Identification of Threats as
the First Stage of Risk Assessment in HIS. Journal of Information Security, 3, 2, 169-
176.
Brown, B. C. (2014). How to Stop E-Mail Spam, Spyware, Malware, Computer Viruses, and
Hackers from Ruining Your Computer or Network. Atlantic Publishing Group Inc.
Choo, R. (2010). Cyber threat landscape faced by financial and insurance industry. Canberra:
Australian Institute of Criminology.
Durbin, S. (2016). Insiders are today’s biggest security threat. [online] Recode. Available at:
https://www.recode.net/2016/5/24/11756584/cyber-attack-data-breach-insider-threat-
steve-durbin [Accessed 28 Aug. 2017].
'Fox News' (2017). 'Ransomware' cyberattack cripples hospitals across England. [online] Fox
News. Available at: http://www.foxnews.com/health/2017/05/12/uk-hospitals-turn-away-
patients-after-ransomware-attack.html [Accessed 28 Aug. 2017].
Griffith, C. (2017). Hackers on top. [online] Theaustralian.com.au. Available at:
References
Akhgar, B., & Arabnia, H. (2014). Emerging trends in ICT security. Amsterdam ; Boston :
Morgan Kaufmann/Elsevier,
Almutairi, A., Sarfraz, M., Basalamah, S., Aref, W., & Ghafoor, A. (January 01, 2012). A
Distributed Access Control Architecture for Cloud Computing. IEEE Software, 29, 2, 36-
44.
Bakhtiyari, S. A., & Ismail, Z. (January 01, 2012). A Tree Model for Identification of Threats as
the First Stage of Risk Assessment in HIS. Journal of Information Security, 3, 2, 169-
176.
Brown, B. C. (2014). How to Stop E-Mail Spam, Spyware, Malware, Computer Viruses, and
Hackers from Ruining Your Computer or Network. Atlantic Publishing Group Inc.
Choo, R. (2010). Cyber threat landscape faced by financial and insurance industry. Canberra:
Australian Institute of Criminology.
Durbin, S. (2016). Insiders are today’s biggest security threat. [online] Recode. Available at:
https://www.recode.net/2016/5/24/11756584/cyber-attack-data-breach-insider-threat-
steve-durbin [Accessed 28 Aug. 2017].
'Fox News' (2017). 'Ransomware' cyberattack cripples hospitals across England. [online] Fox
News. Available at: http://www.foxnews.com/health/2017/05/12/uk-hospitals-turn-away-
patients-after-ransomware-attack.html [Accessed 28 Aug. 2017].
Griffith, C. (2017). Hackers on top. [online] Theaustralian.com.au. Available at:
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





