Computing Architecture Assignment: AI, Networking, and Social Media
VerifiedAdded on 2020/04/01
|12
|3787
|451
Homework Assignment
AI Summary
This assignment explores various aspects of computing architecture, starting with the contributions of key individuals like John McCarthy, the father of AI, and Linus Torvalds, the developer of Linux. It then delves into the evolution of networks, from NSFNET to modern internet infrastructure, and examines Layer 2 protocols like Token Ring. The assignment further investigates the impact of hackers, exemplified by Kevin Mitnick, and concludes with a look at future networking technologies such as the Web of Things and the history of social media platforms like Twitter. Each week focuses on a specific topic, providing summaries of relevant resources and highlighting their significance in the context of computing architecture and its ongoing evolution. The assignment covers a wide array of topics, from the foundational elements of computing to the emerging trends shaping our digital landscape.
Student Name
Student Number
Tasks
Week 1
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title: John McCarthy: Computer scientist and the father of AI
Reference: Childs, M., 2017. John McCarthy: Computer scientist known as the father of AI.
[online] The Independent.
Available at: http://www.independent.co.uk/news/obituaries/john-mccarthy-computer-scientist-
known-as-the-father-of-ai-6255307.html
[Accessed 26 Sep. 2017].
Summary:
Student Number
Tasks
Week 1
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title: John McCarthy: Computer scientist and the father of AI
Reference: Childs, M., 2017. John McCarthy: Computer scientist known as the father of AI.
[online] The Independent.
Available at: http://www.independent.co.uk/news/obituaries/john-mccarthy-computer-scientist-
known-as-the-father-of-ai-6255307.html
[Accessed 26 Sep. 2017].
Summary:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
The article discusses the role of an individual in development of modern computer
architecture. The article describes the contribution of John Mccarthy in development
of a programming language called LISP that forms the basis of Artificial intelligence.
I chose this article as it describes in brief the different contribution of this computer
scientists in the field of science and computers. McCarthy developed and invested the
LISP programming language, which is still considered as a backbone of modern
technology.
Perhaps the most interesting aspect of this article is that, it gives the insight about the
fact that McCarthy coined the term artificial intelligence. Furthermore, he was
responsible for developing the time sharing process. He further researched in the field
of human level artificial Intelligence and reasoning using the common sense.
McCarthy shared his works and ideas with masses. The concept of time sharing in
networking enabled the users in sharing the data by linking to a main or the central
computer. The various works and contribution of Mccarthy helped in the evolution of
internet as well. I found this article useful as it not only discusses the contribution of
Mccarthy in developing modern computer architecture, but also gives a detailed idea
and insight about his works in the field of computing. McCarthy should be credited
for laying the foundation of cloud computing by discovering the use and effectiveness
of time sharing and networking. Cloud computing is one of the integral parts of
modern world and for this; a bit of credit goes to McCarthy as well.
Week 2
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONEsuch individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title : Development of Linux
and Reference: Operating-system.org.,2017. History of the Linux Kernel. [online] Available
at:
http://www.operating-system.org/betriebssystem/_english/bs-linux.htm
[Accessed 26 Sep. 2017].
Summary:
The article discusses the contribution of Linus Torvalds in development of Linux
operating system, which is one of the most widely used operating systems of the
recent times. The article in an interesting way reveals the dedication and strong will of
Torvalds in development of an operating system. I chose this article as it summarises
quite specifically the life of Torvalds and his idea behind the development of a whole
operating system, with an initial aim of modifying an already developed operating
system.
Linus as a student used MINIX operating system in his university. The article discusses how Linus
found the terminal emulator program of MINIX unacceptable and hence embarked on modifying some
of its features. He started programming his own drivers for further accessing the internet and upload or
download files over internet. The source code of MINIX was open source and any modification on the
source code was bound to license terms. Therefore, Linus started developing the system from the
scratch and developed a more advanced operating system than MINIX. Perhaps the most interesting
aspect of this article is that, it properly conveyed the dedication of Linus in development of the linux
operating system. As this operating system had some features of MINIX, it was named as Linux.
architecture. The article describes the contribution of John Mccarthy in development
of a programming language called LISP that forms the basis of Artificial intelligence.
I chose this article as it describes in brief the different contribution of this computer
scientists in the field of science and computers. McCarthy developed and invested the
LISP programming language, which is still considered as a backbone of modern
technology.
Perhaps the most interesting aspect of this article is that, it gives the insight about the
fact that McCarthy coined the term artificial intelligence. Furthermore, he was
responsible for developing the time sharing process. He further researched in the field
of human level artificial Intelligence and reasoning using the common sense.
McCarthy shared his works and ideas with masses. The concept of time sharing in
networking enabled the users in sharing the data by linking to a main or the central
computer. The various works and contribution of Mccarthy helped in the evolution of
internet as well. I found this article useful as it not only discusses the contribution of
Mccarthy in developing modern computer architecture, but also gives a detailed idea
and insight about his works in the field of computing. McCarthy should be credited
for laying the foundation of cloud computing by discovering the use and effectiveness
of time sharing and networking. Cloud computing is one of the integral parts of
modern world and for this; a bit of credit goes to McCarthy as well.
Week 2
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONEsuch individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title : Development of Linux
and Reference: Operating-system.org.,2017. History of the Linux Kernel. [online] Available
at:
http://www.operating-system.org/betriebssystem/_english/bs-linux.htm
[Accessed 26 Sep. 2017].
Summary:
The article discusses the contribution of Linus Torvalds in development of Linux
operating system, which is one of the most widely used operating systems of the
recent times. The article in an interesting way reveals the dedication and strong will of
Torvalds in development of an operating system. I chose this article as it summarises
quite specifically the life of Torvalds and his idea behind the development of a whole
operating system, with an initial aim of modifying an already developed operating
system.
Linus as a student used MINIX operating system in his university. The article discusses how Linus
found the terminal emulator program of MINIX unacceptable and hence embarked on modifying some
of its features. He started programming his own drivers for further accessing the internet and upload or
download files over internet. The source code of MINIX was open source and any modification on the
source code was bound to license terms. Therefore, Linus started developing the system from the
scratch and developed a more advanced operating system than MINIX. Perhaps the most interesting
aspect of this article is that, it properly conveyed the dedication of Linus in development of the linux
operating system. As this operating system had some features of MINIX, it was named as Linux.
Although Linux had some features of MINIX, it was developed from scratch. The Linux operating
system is one of the most widely used operating systems. I found this article helpful as it provided a
clear idea of the then development of Linux operating system by Linus Torvalds.
system is one of the most widely used operating systems. I found this article helpful as it provided a
clear idea of the then development of Linux operating system by Linus Torvalds.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Week 3
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONEof the networks that led to the development of the
modern Internet.
Title: NSFNET -- National Science Foundation Network
and Reference: .com.,2017. NSFNET, National Science Foundation Network. [online]
Available at:
https://www.livinginternet.com/i/ii_nsfnet.htm
[Accessed 26 Sep. 2017].
Summary:
The article discusses the evolution of modern network from earlier networks. One
such network is national science foundation network. The national Science
Foundation built this network in order to establish a connection among the
supercomputers. I chose this article as it discusses in brief the different aspect and the
gradual evolution of this network that led the foundation of modern internet as well.
The major aim of developing this network was replacing the ARPNET in connecting
the supercomputers of science departments in the universities.
Perhaps the most interesting aspect of this article is that, it describes the evolution of
the NFSNET from a network with a speed as slow as 56kbps to a speed of 1.5mbps.
Although the network was built for research purposes, the demand for making the
network public increased considerably. This resulted in allowing the commercial use
of this network as well. With growth on NFSNET in commercial network, the traffic
increased in the network to 12 billion packets.
I found this article useful as it discusses the entire scenario of development of
NFSNET replacing the ARPNET, which formed the basis of the modern computer
internet. The main idea behind development of the NFSNET to establish connection
among the supercomputers but its extensive popularity and ease of access made it one
of the most popular networks. NFSNET was dissolved in the year 1995 going back to
its core usage as a network to be used for research purposes only. Nevertheless, this
network formed the backbone of the modern computer internet.
Week 4
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
Title: IEEE 802.5 Token Ring
Reference: Ecomputernotes.com.,2017. IEEE 802.5 Token Ring. [online] Available at:
http://ecomputernotes.com/computernetworkingnotes/communication-networks/what-is-ieee-
8025-protocol
[Accessed 26 Sep. 2017].
Summary:
The article discusses one of the layer two data link protocol, the token ring protocol. The article
discusses the functionality and working principal of token rings, which is a layer twoo protocol of data
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONEof the networks that led to the development of the
modern Internet.
Title: NSFNET -- National Science Foundation Network
and Reference: .com.,2017. NSFNET, National Science Foundation Network. [online]
Available at:
https://www.livinginternet.com/i/ii_nsfnet.htm
[Accessed 26 Sep. 2017].
Summary:
The article discusses the evolution of modern network from earlier networks. One
such network is national science foundation network. The national Science
Foundation built this network in order to establish a connection among the
supercomputers. I chose this article as it discusses in brief the different aspect and the
gradual evolution of this network that led the foundation of modern internet as well.
The major aim of developing this network was replacing the ARPNET in connecting
the supercomputers of science departments in the universities.
Perhaps the most interesting aspect of this article is that, it describes the evolution of
the NFSNET from a network with a speed as slow as 56kbps to a speed of 1.5mbps.
Although the network was built for research purposes, the demand for making the
network public increased considerably. This resulted in allowing the commercial use
of this network as well. With growth on NFSNET in commercial network, the traffic
increased in the network to 12 billion packets.
I found this article useful as it discusses the entire scenario of development of
NFSNET replacing the ARPNET, which formed the basis of the modern computer
internet. The main idea behind development of the NFSNET to establish connection
among the supercomputers but its extensive popularity and ease of access made it one
of the most popular networks. NFSNET was dissolved in the year 1995 going back to
its core usage as a network to be used for research purposes only. Nevertheless, this
network formed the backbone of the modern computer internet.
Week 4
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
Title: IEEE 802.5 Token Ring
Reference: Ecomputernotes.com.,2017. IEEE 802.5 Token Ring. [online] Available at:
http://ecomputernotes.com/computernetworkingnotes/communication-networks/what-is-ieee-
8025-protocol
[Accessed 26 Sep. 2017].
Summary:
The article discusses one of the layer two data link protocol, the token ring protocol. The article
discusses the functionality and working principal of token rings, which is a layer twoo protocol of data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

link in OSI model.
I chose this article as it discusses in brief the working principal of token rings. Token
rings is a standard local area network protocol, that is used for transmission of
information among the interconnected device with the lead of a token. Among a
network of interconnected devices, the node containing the token is only allowed to
transfer data into the network. This helps in preventing the collision of messages in a
network and that is the advantage of token ring protocol.
Perhaps the most interesting aspect of this article is that, it describes in brief the entire
working principal of a token ring network and its associated advantages. The collision
in the network is prevented as the node containing the token is allowed to transfer a
message. This also implies that the network will be able to transfer one message at a
time. Implementation of token ring is complex and is costly as well. Therefore as an
alternative and cost effective solution, Ethernet is mostly used nowadays. Another
major disadvantage of token ring protocol is that, it can hold a specific data for a
particular amount of time after which the data is lost if the transaction is not
completed.
I found this article useful as it clearly indicated the pros and cons of using token ring
protocol in a network.
Week 5
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title: Hacker for the Hell of It: The Adventures of Kevin Mitnick
and Reference: Gots, J.,2017. Hacker for the Hell of It: The Adventures of Kevin Mitnick.
[online] Big Think. Available at:
http://bigthink.com/think-tank/hacker-for-the-hell-of-it-the-adventures-of-kevin-mitnick
[Accessed 26 Sep. 2017].
Summary:
The article summarises about a famous hacker Kevin Mitnick. Kevin Mitnick is world famous hacker
who never spent a dime of other people’s money. I chose this article as it discusses the adventures of
Kevin Mitnick, the world famous hacker. He was one of the most wanted hackers of time.
The article strategically discusses the motive, addiction and curiosity in launching an
attack. It was believed that he had the power to start a nuclear war simply by
whistling into a telephone.
Perhaps the most interesting aspect of the article is that inspite of having the access to
credit cards, social security numbers and proprietary software, Kevin never spent a
dime on other people’s money. Kevin had compromised the databases, computers
network and different computer systems. Even the hacker community considered
Kevin as a threat because he never dime on other people’s money. Furthermore, he
had not stolen the money of any common people or users. With his excellent identity
changing skills, Kevin was able to hide from FBI for a long time. He was in prison for
five years.
Kevin by his careful research, earning insider jargon and impersonating the personnel
of phone company he was able to get the top secret phone numbers that helped him to
tap the phone lines and make long distance calls.
I chose this article as it gave a clear idea of this hacker and made us aware of his interesting
I chose this article as it discusses in brief the working principal of token rings. Token
rings is a standard local area network protocol, that is used for transmission of
information among the interconnected device with the lead of a token. Among a
network of interconnected devices, the node containing the token is only allowed to
transfer data into the network. This helps in preventing the collision of messages in a
network and that is the advantage of token ring protocol.
Perhaps the most interesting aspect of this article is that, it describes in brief the entire
working principal of a token ring network and its associated advantages. The collision
in the network is prevented as the node containing the token is allowed to transfer a
message. This also implies that the network will be able to transfer one message at a
time. Implementation of token ring is complex and is costly as well. Therefore as an
alternative and cost effective solution, Ethernet is mostly used nowadays. Another
major disadvantage of token ring protocol is that, it can hold a specific data for a
particular amount of time after which the data is lost if the transaction is not
completed.
I found this article useful as it clearly indicated the pros and cons of using token ring
protocol in a network.
Week 5
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title: Hacker for the Hell of It: The Adventures of Kevin Mitnick
and Reference: Gots, J.,2017. Hacker for the Hell of It: The Adventures of Kevin Mitnick.
[online] Big Think. Available at:
http://bigthink.com/think-tank/hacker-for-the-hell-of-it-the-adventures-of-kevin-mitnick
[Accessed 26 Sep. 2017].
Summary:
The article summarises about a famous hacker Kevin Mitnick. Kevin Mitnick is world famous hacker
who never spent a dime of other people’s money. I chose this article as it discusses the adventures of
Kevin Mitnick, the world famous hacker. He was one of the most wanted hackers of time.
The article strategically discusses the motive, addiction and curiosity in launching an
attack. It was believed that he had the power to start a nuclear war simply by
whistling into a telephone.
Perhaps the most interesting aspect of the article is that inspite of having the access to
credit cards, social security numbers and proprietary software, Kevin never spent a
dime on other people’s money. Kevin had compromised the databases, computers
network and different computer systems. Even the hacker community considered
Kevin as a threat because he never dime on other people’s money. Furthermore, he
had not stolen the money of any common people or users. With his excellent identity
changing skills, Kevin was able to hide from FBI for a long time. He was in prison for
five years.
Kevin by his careful research, earning insider jargon and impersonating the personnel
of phone company he was able to get the top secret phone numbers that helped him to
tap the phone lines and make long distance calls.
I chose this article as it gave a clear idea of this hacker and made us aware of his interesting

personality. It gives an overview of the life and adventures of this imfamous hacker.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 6
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title: What is the Web of Things?
Reference: Guinard, D., 2017. What is the Web of Things? – Web of Things. [online]
Webofthings.org. Available at:
https://webofthings.org/2017/04/08/what-is-the-web-of-things/
[Accessed 21 Sep. 2017].
Summary:
The article discusses about of the future network technologies. One of the
future networking technology is web of things. I chose this article as it clearly
describes this future technology and the impact it may have in future.
Web of things is an advanced version of internet of things that helps in
connecting all the physical devices to a single network. This eliminates the
hassle of installing different applications for controlling the different devices as
it is done in case of internet of things.
Perhaps the most interesting aspect of this article is that, that it describes such
a technology that can help in controlling all the different physical devices,
people interact with using a single interface. This will make the management of
the devices easier and hassle free. This technology has a high possibility of
becoming a dominant technology in near future as it will offer varied
advantages and benefits.
I found this article useful as it described and defined the technology of web of
things, which is very probable of becoming a dominant technology in near
future. The article also discusses about the different layers of web of things
architecture such as compose, share, find and access. The article clearly
illustrates the different layers of the web of things and its working principal.
The web of things is a refined form of internet of things and can definitely
replace the IOT in near future.
Week 7
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title: The Real History of Twitter, In Brief
Reference: Lifewire., 2017. The History of Twitter You Didn't Know. [online] Available at:
https://www.lifewire.com/history-of-twitter-3288854
[Accessed 26 Sep. 2017].
Summary:
The article discusses the development of a famous social networking site twitter. I
chose this article as it clearly describes the contribution and efforts of the founder in
development of twitter.
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title: What is the Web of Things?
Reference: Guinard, D., 2017. What is the Web of Things? – Web of Things. [online]
Webofthings.org. Available at:
https://webofthings.org/2017/04/08/what-is-the-web-of-things/
[Accessed 21 Sep. 2017].
Summary:
The article discusses about of the future network technologies. One of the
future networking technology is web of things. I chose this article as it clearly
describes this future technology and the impact it may have in future.
Web of things is an advanced version of internet of things that helps in
connecting all the physical devices to a single network. This eliminates the
hassle of installing different applications for controlling the different devices as
it is done in case of internet of things.
Perhaps the most interesting aspect of this article is that, that it describes such
a technology that can help in controlling all the different physical devices,
people interact with using a single interface. This will make the management of
the devices easier and hassle free. This technology has a high possibility of
becoming a dominant technology in near future as it will offer varied
advantages and benefits.
I found this article useful as it described and defined the technology of web of
things, which is very probable of becoming a dominant technology in near
future. The article also discusses about the different layers of web of things
architecture such as compose, share, find and access. The article clearly
illustrates the different layers of the web of things and its working principal.
The web of things is a refined form of internet of things and can definitely
replace the IOT in near future.
Week 7
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title: The Real History of Twitter, In Brief
Reference: Lifewire., 2017. The History of Twitter You Didn't Know. [online] Available at:
https://www.lifewire.com/history-of-twitter-3288854
[Accessed 26 Sep. 2017].
Summary:
The article discusses the development of a famous social networking site twitter. I
chose this article as it clearly describes the contribution and efforts of the founder in
development of twitter.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The idea behing development of the twitter was to develop a platform for keeping a
tab of friends with the help of status updates. The platform developed was much
similar to that of normal texting.
Perhaps the most interesting aspect of the this article is that, the previous name of
twitter was twtrr as it was a trend of that time to drop vowels from the name of the
company. The character limit of twitter was set to 140 as the character limit in sms
was 160.
This simple idea lead to the development of one of the largest social media platform,
which is now used by millions of users. Research data says that twitter, at present has
almost 200 million active users. Furthermore, the development of twitter helped in
saving a somewhat dying company.
I found this article useful and it explained in brief, the idea and the process of
development of this famous social media platform. The name twitter was derived
from the name of the photo sharing site Flicker. Millions of people nowadays use
twitter to keep in touch with their loved ones and know about the whereabouts of their
friends. Thus, development of twitter was indeed successful in achieving its goal and
objectives.
Week 8
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title: How Netflix Uses Analytics To Select Movies, Create Content, and Make Multimillion
Dollar Decisions
Reference: Kissmetrics, 2017,. How Netflix Uses Analytics To Select Movies, Create Content,
& Make Multimillion Dollar Decisions. [online] Available at: https://blog.kissmetrics.com/how-
netflix-uses-analytics/
[Accessed 26 Sep. 2017].
Summary:
The article describes the use of mass data collection and data mining in a business.
Netflix is one such platform that uses extensive data mining in increasing the business
processes. I chose this article as it clearly describes the how Netflix uses data mining
in improving its business decisions. The use of data mining helps in increasing the
accuracy of business decisions and processes.
Netflix is one of the largest online TV streaming platform with a million of customers
and therefore it becomes essential for Netflix to understand the preferences of its
users.
Perhaps the most interesting aspect of this article is that, it describes how the data
mining can be used for knowing the preferences of the customer, which in turn help in
improving the business decisions.
The data Netflix collect in the process of data mining includes the data of pause,
rewind date of watching and so on. These data help in improving the business needs
and process that further helps in improving the experiences of the customers and helps
in obtaining the customer feedback in a proper way. It uses proper algorithmic
methods in sorting the data that can be used for increasing the business processes.
I found this article useful as it clearly described the process of data mining and the use
of the same in improving the business decisions and helped in further growth of the
business more strategically.
tab of friends with the help of status updates. The platform developed was much
similar to that of normal texting.
Perhaps the most interesting aspect of the this article is that, the previous name of
twitter was twtrr as it was a trend of that time to drop vowels from the name of the
company. The character limit of twitter was set to 140 as the character limit in sms
was 160.
This simple idea lead to the development of one of the largest social media platform,
which is now used by millions of users. Research data says that twitter, at present has
almost 200 million active users. Furthermore, the development of twitter helped in
saving a somewhat dying company.
I found this article useful and it explained in brief, the idea and the process of
development of this famous social media platform. The name twitter was derived
from the name of the photo sharing site Flicker. Millions of people nowadays use
twitter to keep in touch with their loved ones and know about the whereabouts of their
friends. Thus, development of twitter was indeed successful in achieving its goal and
objectives.
Week 8
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title: How Netflix Uses Analytics To Select Movies, Create Content, and Make Multimillion
Dollar Decisions
Reference: Kissmetrics, 2017,. How Netflix Uses Analytics To Select Movies, Create Content,
& Make Multimillion Dollar Decisions. [online] Available at: https://blog.kissmetrics.com/how-
netflix-uses-analytics/
[Accessed 26 Sep. 2017].
Summary:
The article describes the use of mass data collection and data mining in a business.
Netflix is one such platform that uses extensive data mining in increasing the business
processes. I chose this article as it clearly describes the how Netflix uses data mining
in improving its business decisions. The use of data mining helps in increasing the
accuracy of business decisions and processes.
Netflix is one of the largest online TV streaming platform with a million of customers
and therefore it becomes essential for Netflix to understand the preferences of its
users.
Perhaps the most interesting aspect of this article is that, it describes how the data
mining can be used for knowing the preferences of the customer, which in turn help in
improving the business decisions.
The data Netflix collect in the process of data mining includes the data of pause,
rewind date of watching and so on. These data help in improving the business needs
and process that further helps in improving the experiences of the customers and helps
in obtaining the customer feedback in a proper way. It uses proper algorithmic
methods in sorting the data that can be used for increasing the business processes.
I found this article useful as it clearly described the process of data mining and the use
of the same in improving the business decisions and helped in further growth of the
business more strategically.

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 9
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title: 5 Things You Can Learn From The Story Of WhatsApp
Reference: Medium., 2017, 5 Things You Can Learn From The Story Of WhatsApp – The
Story Of Grip – Medium. [online] Available at: https://medium.com/the-story-of-grip/5-things-
every-founder-can-learn-from-the-story-of-whatsapp-b6496bc4f54d
[Accessed 26 Sep. 2017].
Summary:
The article discusses the success of Watsapp founder Jan Koum in development of the
famous mobile application WatsApp. I chose this article as it discusses in brief the
idea behind the development of this application and its success stories.
WatsApp is used by the millions of users for communicating with the friends and
family. Jan Koum developed watsapp with an idea of developing a platform of
sending notifications to the friends. The developments of this app however, brought a
revolution in the field of messaging, as texting was never been so simple and easy.
Perhaps the most interesting aspect of this article is that it describes how a simple idea
lead to the development of the most famous mobile application. It has reached this
success as using watsapp is simple and easy and this is another reason for the
increasing populariy of this app.
The founder of Jan Koum was responsible was rejected a job at facebook at one point
of time, later facebook bought watsapp in the year 2015.
The communication in Watsapp is protected by standard encryption methods that is
another feature of this famous mobile application.
I found this article useful as described in a strategic way, the development of this
famous mobile application by Jan Koum and his idea for improving the process of
text messages. Therefore, it can be concluded that Jan Koum indeed brought a
revolution in the landscape of
Text messaging.
Week 10
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title: ERP Failure: Hershey
Reference: Pemeco.com. ,2017,. A Case Study on Hershey's ERP Implementation Failure–
Driving successful enterprise software projects. [online] Available at:
https://www.pemeco.com/a-case-study-on-hersheys-erp-implementation-failure-the-
importance-of-testing-and-scheduling/
[Accessed 26 Sep. 2017].
Summary:
The article discuses a scenario, where the use of information security has brought a
negative impact in the life of people. The article deals with the ERP failure of
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title: 5 Things You Can Learn From The Story Of WhatsApp
Reference: Medium., 2017, 5 Things You Can Learn From The Story Of WhatsApp – The
Story Of Grip – Medium. [online] Available at: https://medium.com/the-story-of-grip/5-things-
every-founder-can-learn-from-the-story-of-whatsapp-b6496bc4f54d
[Accessed 26 Sep. 2017].
Summary:
The article discusses the success of Watsapp founder Jan Koum in development of the
famous mobile application WatsApp. I chose this article as it discusses in brief the
idea behind the development of this application and its success stories.
WatsApp is used by the millions of users for communicating with the friends and
family. Jan Koum developed watsapp with an idea of developing a platform of
sending notifications to the friends. The developments of this app however, brought a
revolution in the field of messaging, as texting was never been so simple and easy.
Perhaps the most interesting aspect of this article is that it describes how a simple idea
lead to the development of the most famous mobile application. It has reached this
success as using watsapp is simple and easy and this is another reason for the
increasing populariy of this app.
The founder of Jan Koum was responsible was rejected a job at facebook at one point
of time, later facebook bought watsapp in the year 2015.
The communication in Watsapp is protected by standard encryption methods that is
another feature of this famous mobile application.
I found this article useful as described in a strategic way, the development of this
famous mobile application by Jan Koum and his idea for improving the process of
text messages. Therefore, it can be concluded that Jan Koum indeed brought a
revolution in the landscape of
Text messaging.
Week 10
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title: ERP Failure: Hershey
Reference: Pemeco.com. ,2017,. A Case Study on Hershey's ERP Implementation Failure–
Driving successful enterprise software projects. [online] Available at:
https://www.pemeco.com/a-case-study-on-hersheys-erp-implementation-failure-the-
importance-of-testing-and-scheduling/
[Accessed 26 Sep. 2017].
Summary:
The article discuses a scenario, where the use of information security has brought a
negative impact in the life of people. The article deals with the ERP failure of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Hershey that resulted in a severe loss of the company. I chose this article as it defined
in a structural way the life and processes or the scenario that led to the failure of the
implementation ERP in the organization.
Perhaps the most interesting aspect of this article is that, it discusses the process of failure of the ERP
in Hershey during their busiest business times. This resulted in the loss of the quarterly profit of the
organization by 19% and decline in the stock price by as huge as 8%. The ERP was to be implemented
for integrating the operational works of the organization but the development of the software in a
constricted time resulted in the failure of the system haulting the entire business process. This resulted
in the failure of order processing worth $100. This proves that the improper implementation of a
technology or a software may lead to a negative effect for humans. I found this article useful as it
clearly described the negative effect of information technology on humans. The major reason behind
the failure of this technology is that the development phase of the software skipped many testing
phases that resulted in the software failing to perform in the busiest time of the business.
in a structural way the life and processes or the scenario that led to the failure of the
implementation ERP in the organization.
Perhaps the most interesting aspect of this article is that, it discusses the process of failure of the ERP
in Hershey during their busiest business times. This resulted in the loss of the quarterly profit of the
organization by 19% and decline in the stock price by as huge as 8%. The ERP was to be implemented
for integrating the operational works of the organization but the development of the software in a
constricted time resulted in the failure of the system haulting the entire business process. This resulted
in the failure of order processing worth $100. This proves that the improper implementation of a
technology or a software may lead to a negative effect for humans. I found this article useful as it
clearly described the negative effect of information technology on humans. The major reason behind
the failure of this technology is that the development phase of the software skipped many testing
phases that resulted in the software failing to perform in the busiest time of the business.
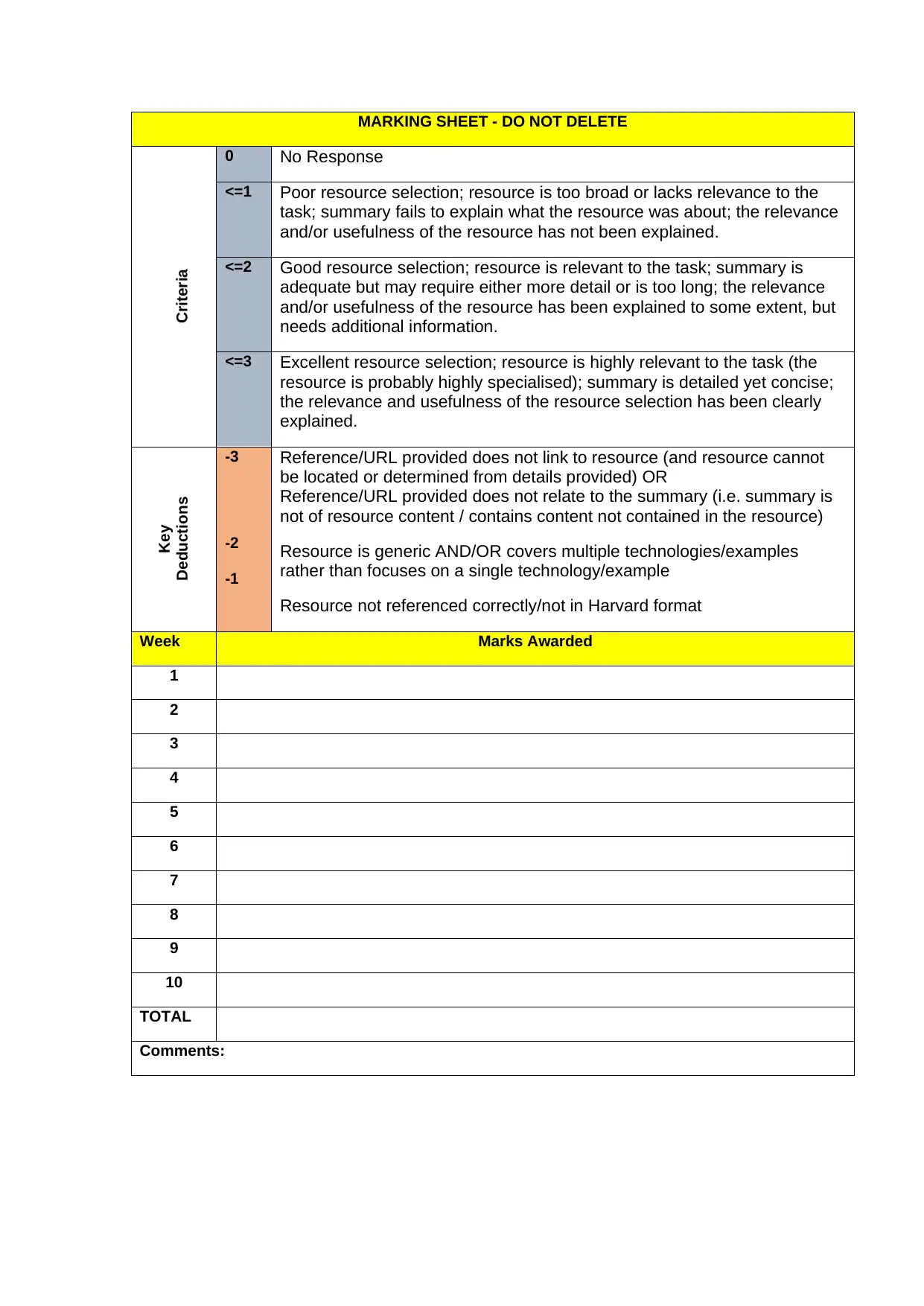
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





