Cyber Crime Trends Research Paper 2022
VerifiedAdded on 2022/09/06
|10
|3676
|38
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: CYBER CRIME TRENDS
0
Trends in Cyber Crime
IT Write Up
(Student Details: )
1/2/2020
0
Trends in Cyber Crime
IT Write Up
(Student Details: )
1/2/2020
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CYBER CRIME
1
Contents
CO4515 Trends in Cybercrime..................................................................................................2
I. Abstract...................................................................................................................................2
II. Introduction...........................................................................................................................2
III. Analysis of the related works...............................................................................................2
Introduction to cybercrime.....................................................................................................2
Spams and Cybercrime..........................................................................................................1
Detection of email spams.......................................................................................................2
IV. Discussion............................................................................................................................2
Mitigation of email spams......................................................................................................2
Effects of cybercrime through spams.................................................................................2
Prevention of cybercrime...................................................................................................3
Mitigation techniques.........................................................................................................3
Future recommendations....................................................................................................4
V. Conclusion.............................................................................................................................4
References..................................................................................................................................5
1
Contents
CO4515 Trends in Cybercrime..................................................................................................2
I. Abstract...................................................................................................................................2
II. Introduction...........................................................................................................................2
III. Analysis of the related works...............................................................................................2
Introduction to cybercrime.....................................................................................................2
Spams and Cybercrime..........................................................................................................1
Detection of email spams.......................................................................................................2
IV. Discussion............................................................................................................................2
Mitigation of email spams......................................................................................................2
Effects of cybercrime through spams.................................................................................2
Prevention of cybercrime...................................................................................................3
Mitigation techniques.........................................................................................................3
Future recommendations....................................................................................................4
V. Conclusion.............................................................................................................................4
References..................................................................................................................................5

CYBER CRIME
2
CO4515 Trends in Cybercrime
I. Abstract
This research paper is focused on studying
trends in cybercrime while from the
perspective of security. To do so, a
theoretical study on how to effectively
mitigate email spams will take place. The
research question of this paper is focused
on ‘researching about email spam for
cybercrime so that mitigation can be
done’. Researching about email spams is
essential because cybercriminals are
currently utilizing more scalable and
advanced tools for breaching modern
users’ privacy and thereby they are getting
achievements in the field of cybercrimes.
In this era, cybercriminals are operating
online for targeting cryptocurrencies while
leveraging phishing as well as rest social
engineering attacks. Moreover,
cybercrimes are constantly increasing due
to tweaking age-old scams for the digital
age. Thus the aforementioned reasons are
clearly given the motivation of writing this
research paper. The purpose of this paper
is to explore different trends in cybercrime
while specifically talking about email
spams. In this way, the research study is a
great contribution towards the whole
information technology field while
mitigating the cybercrime causes and
effects effectively.
II. Introduction
The research report is focused to explore
the real nature of different groups who are
engaged in the modern cyber-crimes.
While doing so, the study will outline the
definition as well as the scope of
cybercrime, empirical and theoretical
challenges for addressing these
cybercrimes. With the help of some
known examples and scenarios, different
types, as well as trends of cyber-crimes,
will be explored in this paper. The research
question of this paper
is focused on ‘researching about email
spam for cybercrime so that mitigation can
be done’. Specifically, spams and
cybercrime is the main topic for writing
this research paper while exploring email
spams in detail. Detailed analysis and
discussion will take place in the context of
cybercrime trends 1. In general, with the
advent of the modern age, information
technology has been grown at a quick
speed which has given rise to an evolving
class to cybercrimes and thereby
cyberthreats 2. In this way, these
cybercrimes are affecting enterprises and
individuals in the last few years; hence the
paper will majorly explore the ways to
mitigate email spams in an effective
manner.
III. Analysis of the related works
Introduction to cybercrime
In this digital age, cybercrime is falling
into 2 main categories including attacks
and financial. In this context, the first
cybercrime is attacks that are against a
computer software and hardware from
cyberthreats like malware, viruses,
network intrusion as well as botnets 3.
2
CO4515 Trends in Cybercrime
I. Abstract
This research paper is focused on studying
trends in cybercrime while from the
perspective of security. To do so, a
theoretical study on how to effectively
mitigate email spams will take place. The
research question of this paper is focused
on ‘researching about email spam for
cybercrime so that mitigation can be
done’. Researching about email spams is
essential because cybercriminals are
currently utilizing more scalable and
advanced tools for breaching modern
users’ privacy and thereby they are getting
achievements in the field of cybercrimes.
In this era, cybercriminals are operating
online for targeting cryptocurrencies while
leveraging phishing as well as rest social
engineering attacks. Moreover,
cybercrimes are constantly increasing due
to tweaking age-old scams for the digital
age. Thus the aforementioned reasons are
clearly given the motivation of writing this
research paper. The purpose of this paper
is to explore different trends in cybercrime
while specifically talking about email
spams. In this way, the research study is a
great contribution towards the whole
information technology field while
mitigating the cybercrime causes and
effects effectively.
II. Introduction
The research report is focused to explore
the real nature of different groups who are
engaged in the modern cyber-crimes.
While doing so, the study will outline the
definition as well as the scope of
cybercrime, empirical and theoretical
challenges for addressing these
cybercrimes. With the help of some
known examples and scenarios, different
types, as well as trends of cyber-crimes,
will be explored in this paper. The research
question of this paper
is focused on ‘researching about email
spam for cybercrime so that mitigation can
be done’. Specifically, spams and
cybercrime is the main topic for writing
this research paper while exploring email
spams in detail. Detailed analysis and
discussion will take place in the context of
cybercrime trends 1. In general, with the
advent of the modern age, information
technology has been grown at a quick
speed which has given rise to an evolving
class to cybercrimes and thereby
cyberthreats 2. In this way, these
cybercrimes are affecting enterprises and
individuals in the last few years; hence the
paper will majorly explore the ways to
mitigate email spams in an effective
manner.
III. Analysis of the related works
Introduction to cybercrime
In this digital age, cybercrime is falling
into 2 main categories including attacks
and financial. In this context, the first
cybercrime is attacks that are against a
computer software and hardware from
cyberthreats like malware, viruses,
network intrusion as well as botnets 3.

CYBER CRIME
3
Later then, cybercrime can also be related
to finance which can include phishing,
theft of financial info and identity fraud 4.
From the definition perspective,
cybercrime is known as a net crime as well
as computer crime, which refers to any
criminal activity that contains a computer
or a network, either in the commissioning
of the crime or the target 5.
In the context of the current state of
cybercrime, it has been found in a recent
cybercrime survey, 3 out of 4 respondents
often detected a security breach event in
the past few years. It means security
deficiencies in modern organizations are
found due to most of the susceptible
cybercrime as follows:
Lack of thorough employee
awareness training and security
Insider risk and threats which are
not effectively addressed
Unplanned and reactive
cybersecurity expenditure
Lack of understanding of risks
related to supply-chain 2.
Apart from these challenges, recent
cybercrimes are increasing at a high rate
which is a matter to be addressed soon. It
is worth knowing that recent cybercrimes
are not restricted to the desktop alone, as
mobile devices are also getting proliferated
during past years. In this way, cybercrimes
are continuously increasing in the form of
phishing scams, malware and viruses 6.
For example, a recent cybercrime survey
revealed that 72% of the whole
applications for the operating system have
been regarded as unwanted, suspicious or
malicious as Trojans are making up the
majority of the threats 7.
Source: 1
Spams and Cybercrime
Spam can be defined as junk or email
which can easily create cybercrime. It has
been found that spam emails are always
vigilant while responding or receiving
emails. It is necessary to make sure that
the spam filter is switched on to optimize
the whole risks 8. In this context, the
majority of the emails are sent on a daily
basis as unsolicited junk mail. There are
some key examples of spams in this digital
age:
Hoax charity appeals
Hoax virus warnings
Getting so many rich as well as
quick work from home schemes
Advertise related to gambling,
dating, pornography, and online
pharmacies
Chain emails which are
encouraging an individual to
forward them to several contacts
from their contacts list 9.
In this context, when spam is used for
conducting cybercrime then it is important
to know how spammers actually get
personal email addresses 3. There are so
many ways through which spammers get
an email addressed to do cybercrime. For
instance, spammers usually use automated
software for generating such email
addresses. In this way, they can spread
3
Later then, cybercrime can also be related
to finance which can include phishing,
theft of financial info and identity fraud 4.
From the definition perspective,
cybercrime is known as a net crime as well
as computer crime, which refers to any
criminal activity that contains a computer
or a network, either in the commissioning
of the crime or the target 5.
In the context of the current state of
cybercrime, it has been found in a recent
cybercrime survey, 3 out of 4 respondents
often detected a security breach event in
the past few years. It means security
deficiencies in modern organizations are
found due to most of the susceptible
cybercrime as follows:
Lack of thorough employee
awareness training and security
Insider risk and threats which are
not effectively addressed
Unplanned and reactive
cybersecurity expenditure
Lack of understanding of risks
related to supply-chain 2.
Apart from these challenges, recent
cybercrimes are increasing at a high rate
which is a matter to be addressed soon. It
is worth knowing that recent cybercrimes
are not restricted to the desktop alone, as
mobile devices are also getting proliferated
during past years. In this way, cybercrimes
are continuously increasing in the form of
phishing scams, malware and viruses 6.
For example, a recent cybercrime survey
revealed that 72% of the whole
applications for the operating system have
been regarded as unwanted, suspicious or
malicious as Trojans are making up the
majority of the threats 7.
Source: 1
Spams and Cybercrime
Spam can be defined as junk or email
which can easily create cybercrime. It has
been found that spam emails are always
vigilant while responding or receiving
emails. It is necessary to make sure that
the spam filter is switched on to optimize
the whole risks 8. In this context, the
majority of the emails are sent on a daily
basis as unsolicited junk mail. There are
some key examples of spams in this digital
age:
Hoax charity appeals
Hoax virus warnings
Getting so many rich as well as
quick work from home schemes
Advertise related to gambling,
dating, pornography, and online
pharmacies
Chain emails which are
encouraging an individual to
forward them to several contacts
from their contacts list 9.
In this context, when spam is used for
conducting cybercrime then it is important
to know how spammers actually get
personal email addresses 3. There are so
many ways through which spammers get
an email addressed to do cybercrime. For
instance, spammers usually use automated
software for generating such email
addresses. In this way, they can spread
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
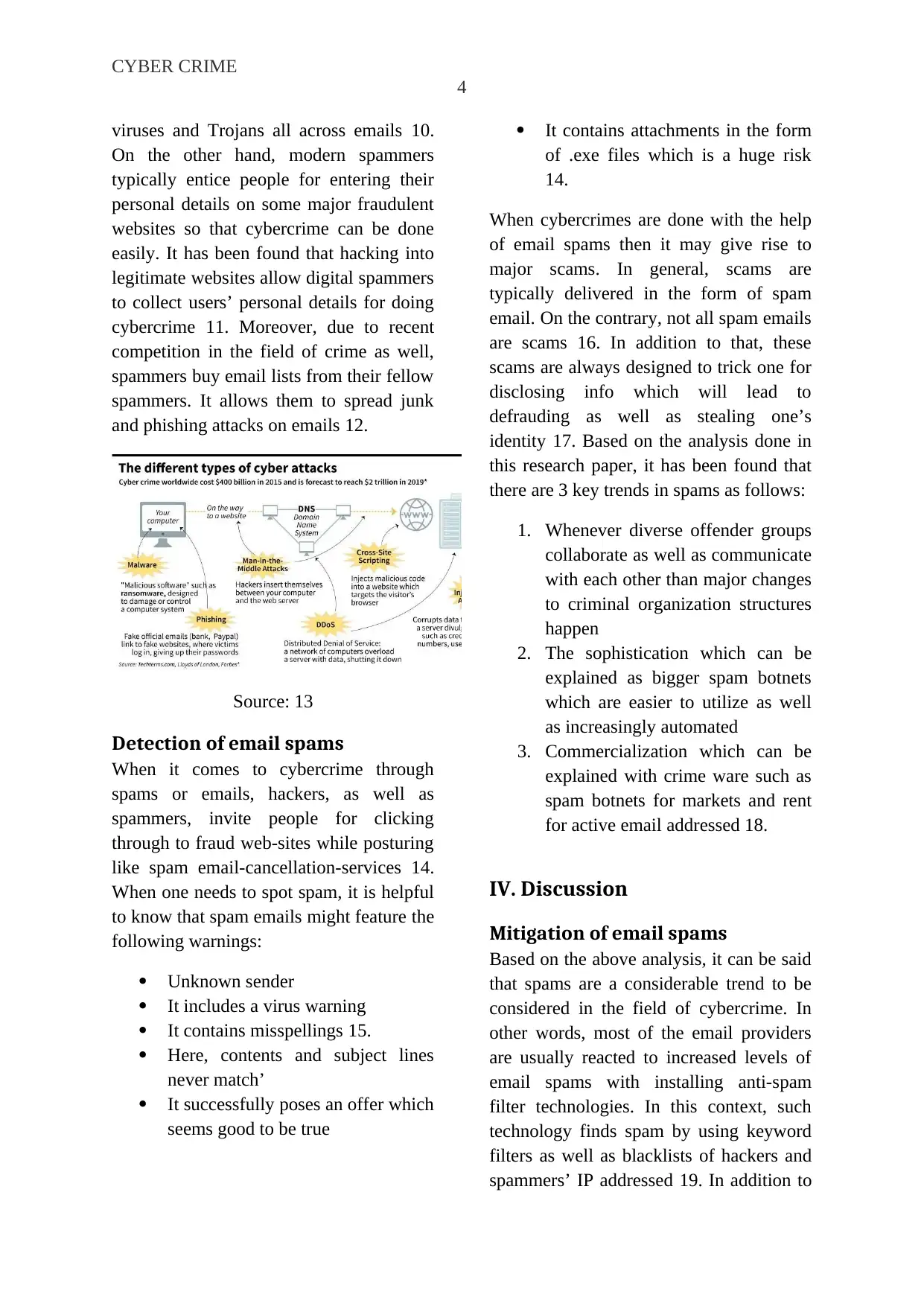
CYBER CRIME
4
viruses and Trojans all across emails 10.
On the other hand, modern spammers
typically entice people for entering their
personal details on some major fraudulent
websites so that cybercrime can be done
easily. It has been found that hacking into
legitimate websites allow digital spammers
to collect users’ personal details for doing
cybercrime 11. Moreover, due to recent
competition in the field of crime as well,
spammers buy email lists from their fellow
spammers. It allows them to spread junk
and phishing attacks on emails 12.
Source: 13
Detection of email spams
When it comes to cybercrime through
spams or emails, hackers, as well as
spammers, invite people for clicking
through to fraud web-sites while posturing
like spam email-cancellation-services 14.
When one needs to spot spam, it is helpful
to know that spam emails might feature the
following warnings:
Unknown sender
It includes a virus warning
It contains misspellings 15.
Here, contents and subject lines
never match’
It successfully poses an offer which
seems good to be true
It contains attachments in the form
of .exe files which is a huge risk
14.
When cybercrimes are done with the help
of email spams then it may give rise to
major scams. In general, scams are
typically delivered in the form of spam
email. On the contrary, not all spam emails
are scams 16. In addition to that, these
scams are always designed to trick one for
disclosing info which will lead to
defrauding as well as stealing one’s
identity 17. Based on the analysis done in
this research paper, it has been found that
there are 3 key trends in spams as follows:
1. Whenever diverse offender groups
collaborate as well as communicate
with each other than major changes
to criminal organization structures
happen
2. The sophistication which can be
explained as bigger spam botnets
which are easier to utilize as well
as increasingly automated
3. Commercialization which can be
explained with crime ware such as
spam botnets for markets and rent
for active email addressed 18.
IV. Discussion
Mitigation of email spams
Based on the above analysis, it can be said
that spams are a considerable trend to be
considered in the field of cybercrime. In
other words, most of the email providers
are usually reacted to increased levels of
email spams with installing anti-spam
filter technologies. In this context, such
technology finds spam by using keyword
filters as well as blacklists of hackers and
spammers’ IP addressed 19. In addition to
4
viruses and Trojans all across emails 10.
On the other hand, modern spammers
typically entice people for entering their
personal details on some major fraudulent
websites so that cybercrime can be done
easily. It has been found that hacking into
legitimate websites allow digital spammers
to collect users’ personal details for doing
cybercrime 11. Moreover, due to recent
competition in the field of crime as well,
spammers buy email lists from their fellow
spammers. It allows them to spread junk
and phishing attacks on emails 12.
Source: 13
Detection of email spams
When it comes to cybercrime through
spams or emails, hackers, as well as
spammers, invite people for clicking
through to fraud web-sites while posturing
like spam email-cancellation-services 14.
When one needs to spot spam, it is helpful
to know that spam emails might feature the
following warnings:
Unknown sender
It includes a virus warning
It contains misspellings 15.
Here, contents and subject lines
never match’
It successfully poses an offer which
seems good to be true
It contains attachments in the form
of .exe files which is a huge risk
14.
When cybercrimes are done with the help
of email spams then it may give rise to
major scams. In general, scams are
typically delivered in the form of spam
email. On the contrary, not all spam emails
are scams 16. In addition to that, these
scams are always designed to trick one for
disclosing info which will lead to
defrauding as well as stealing one’s
identity 17. Based on the analysis done in
this research paper, it has been found that
there are 3 key trends in spams as follows:
1. Whenever diverse offender groups
collaborate as well as communicate
with each other than major changes
to criminal organization structures
happen
2. The sophistication which can be
explained as bigger spam botnets
which are easier to utilize as well
as increasingly automated
3. Commercialization which can be
explained with crime ware such as
spam botnets for markets and rent
for active email addressed 18.
IV. Discussion
Mitigation of email spams
Based on the above analysis, it can be said
that spams are a considerable trend to be
considered in the field of cybercrime. In
other words, most of the email providers
are usually reacted to increased levels of
email spams with installing anti-spam
filter technologies. In this context, such
technology finds spam by using keyword
filters as well as blacklists of hackers and
spammers’ IP addressed 19. In addition to

CYBER CRIME
5
that, when spam filter technology
continues to develop, hackers always find
ways through such systems. It can be done
by avoiding the most common keywords.
The paper has analysed that successful
detection of spam emails always depends
on the changes in the way these spam
emails are distributed. However, it is
difficult to identify spam for the email
providers through analysing the key
information about senders and thereby
difficult for the agencies to track
offenders. It has been found by the
technology experts that real resolution in
this fight against spam is to increase
transmission costs for the modern senders.
In this way, due to the low cost for the
offenders, spam email sending is quite
profitable when offenders are capable to
send millions of emails 14.
Effects of cybercrime through spams
There are some major critical impacts of
cybercrime resulted from spam emails.
Moreover, cybercrime in the form of
spams majorly threatens the critical
infrastructure of government and
businesses all across the world as it can
harm civilians in many ways. In this
context, a study suggests that more than
hundreds of billions of dollars have been
lost due to cybercrime in the context of the
world economy while there is no sign
found of slowing it down 20. Some key
effects of the same can be explained as
below:
Email scams
Identity theft
Direct financial loss
Customer compensation
Identity fraud
Regulatory penalties
Mitigation as well as recovery cost
Damage to brand and company
reputation
SLA breaches
Loss of intellectual property and
sensitive data
Job loss 20.
Prevention of cybercrime
Source: 2
In order to fight cybercrimes, modern
firms need to take adequate preventive
measures so that cybercrimes through
spams and any other way can be avoided
effectively. In this context, private and
public sectors require to form secure as
well as permanent information sharing
channels largely 10. To prevent
cybercrimes, information regarding new
modus operandi, hacking cases,
prosecution details, investigation
experiences, technological development
advancements and trends, technical
protection and prevention measures and
thereby IT practices should always flow
freely among various sectors of the
organizations. Moreover, preventive
measures for cybercrime include investing
in creative and technological innovations,
creating cybercrime taxonomy so that
future security challenges in the context of
spams can be meet successfully. Apart
from this, researchers suggest that people
and organizations can create regional as
5
that, when spam filter technology
continues to develop, hackers always find
ways through such systems. It can be done
by avoiding the most common keywords.
The paper has analysed that successful
detection of spam emails always depends
on the changes in the way these spam
emails are distributed. However, it is
difficult to identify spam for the email
providers through analysing the key
information about senders and thereby
difficult for the agencies to track
offenders. It has been found by the
technology experts that real resolution in
this fight against spam is to increase
transmission costs for the modern senders.
In this way, due to the low cost for the
offenders, spam email sending is quite
profitable when offenders are capable to
send millions of emails 14.
Effects of cybercrime through spams
There are some major critical impacts of
cybercrime resulted from spam emails.
Moreover, cybercrime in the form of
spams majorly threatens the critical
infrastructure of government and
businesses all across the world as it can
harm civilians in many ways. In this
context, a study suggests that more than
hundreds of billions of dollars have been
lost due to cybercrime in the context of the
world economy while there is no sign
found of slowing it down 20. Some key
effects of the same can be explained as
below:
Email scams
Identity theft
Direct financial loss
Customer compensation
Identity fraud
Regulatory penalties
Mitigation as well as recovery cost
Damage to brand and company
reputation
SLA breaches
Loss of intellectual property and
sensitive data
Job loss 20.
Prevention of cybercrime
Source: 2
In order to fight cybercrimes, modern
firms need to take adequate preventive
measures so that cybercrimes through
spams and any other way can be avoided
effectively. In this context, private and
public sectors require to form secure as
well as permanent information sharing
channels largely 10. To prevent
cybercrimes, information regarding new
modus operandi, hacking cases,
prosecution details, investigation
experiences, technological development
advancements and trends, technical
protection and prevention measures and
thereby IT practices should always flow
freely among various sectors of the
organizations. Moreover, preventive
measures for cybercrime include investing
in creative and technological innovations,
creating cybercrime taxonomy so that
future security challenges in the context of
spams can be meet successfully. Apart
from this, researchers suggest that people
and organizations can create regional as

CYBER CRIME
6
well as global public-private platforms for
further promoting enhanced cooperation
amid private sectors and enforcement
authorities which is highly beneficial 18.
In addition to that, there is one more
technique of preventing cybercrime by
simply inserting a gap between the two
major extensions include users and
hackers. In this way, the above practice
can easily prevent a few spam filters from
defining whether the attachment is an
executable file or not. As the modern IT
security is focusing on perimeter
protection which is increasingly
ineffective, therefore crime avoidance
activities should always refocus over the
modus-operandi of offenders as well as the
susceptibilities of the recent sufferers 12.
Mitigation techniques
In order to effectively mitigate email
spam, the following points can help protect
users from becoming a victim to spam
emails:
Most commonly, users must not
click links as well as download
files even when they come through
trustworthy sources.
Users must always be mindful of
organizations or individuals who
demand personal information.
However, most of the companies
never ask for sensitive data from
their users. Thus, whenever in
doubt, customers must verify with
the belonging company so that any
potential issue can be avoided.
One should always check for the
mismatched URLs as well as they
must avoid clicking on links
provided in emails until they are
certain which can be understood by
a legitimate link 19.
Modern IT users and internet users
must always take a closer look at
the sender’s info like display name
while checking the legitimacy of
the email. In this context, most of
the modern IT firms utilize a single
domain for the emails and URLs
thus any message coming from a
different domain other than the
original one, has a red flag. Such
information is very useful while
mitigating spam emails.
One should not utilise their
personal as well as business email
addresses while registering in
online contests or services like
applications, deal updates, and
many more. In addition to that, so
many spammers see these groups
or emailing lists for harvesting
novel email addresses.
In this way, there can be many
ways with which one can avoid
being a victim of spam emails as
well as messages. Most
importantly, one should always be
cautious while opening emails.
Thus, an individual should always
make sure that emails are from
trustworthy sources and hence they
should not look dubious. In this
way, whenever one receives any of
the suspicious emails, they should
report spam and exit rather than
clicking various links and
attachments in it 1.
Future recommendations
Based on research, analysis, and
discussion, there are some useful future
recommendations which can be used to
effectively mitigate spam emails, as
follows:
6
well as global public-private platforms for
further promoting enhanced cooperation
amid private sectors and enforcement
authorities which is highly beneficial 18.
In addition to that, there is one more
technique of preventing cybercrime by
simply inserting a gap between the two
major extensions include users and
hackers. In this way, the above practice
can easily prevent a few spam filters from
defining whether the attachment is an
executable file or not. As the modern IT
security is focusing on perimeter
protection which is increasingly
ineffective, therefore crime avoidance
activities should always refocus over the
modus-operandi of offenders as well as the
susceptibilities of the recent sufferers 12.
Mitigation techniques
In order to effectively mitigate email
spam, the following points can help protect
users from becoming a victim to spam
emails:
Most commonly, users must not
click links as well as download
files even when they come through
trustworthy sources.
Users must always be mindful of
organizations or individuals who
demand personal information.
However, most of the companies
never ask for sensitive data from
their users. Thus, whenever in
doubt, customers must verify with
the belonging company so that any
potential issue can be avoided.
One should always check for the
mismatched URLs as well as they
must avoid clicking on links
provided in emails until they are
certain which can be understood by
a legitimate link 19.
Modern IT users and internet users
must always take a closer look at
the sender’s info like display name
while checking the legitimacy of
the email. In this context, most of
the modern IT firms utilize a single
domain for the emails and URLs
thus any message coming from a
different domain other than the
original one, has a red flag. Such
information is very useful while
mitigating spam emails.
One should not utilise their
personal as well as business email
addresses while registering in
online contests or services like
applications, deal updates, and
many more. In addition to that, so
many spammers see these groups
or emailing lists for harvesting
novel email addresses.
In this way, there can be many
ways with which one can avoid
being a victim of spam emails as
well as messages. Most
importantly, one should always be
cautious while opening emails.
Thus, an individual should always
make sure that emails are from
trustworthy sources and hence they
should not look dubious. In this
way, whenever one receives any of
the suspicious emails, they should
report spam and exit rather than
clicking various links and
attachments in it 1.
Future recommendations
Based on research, analysis, and
discussion, there are some useful future
recommendations which can be used to
effectively mitigate spam emails, as
follows:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBER CRIME
7
Never provide and post email
addresses publicly
Always be cautious and think
before clicking suspicious links in
the spam emails
Always own spam-filtering-tools as
well as antivirus software by
downloading them
Avoid utilizing business and
personal email address while
registering in online contests or
services
Never reply to spam emails and
messages
V. Conclusion
In whole, this research paper has
successfully talked about spams and
cybercrime from the perspective of the
security of the users on the internet. While
doing so, almost every possible aspect of
the spams and cybercrime has been
explored well. In this context, the paper
has discussed existing defense and
detection mechanisms in order to deal with
malicious spam emails. In this way, novel
malware embedded spam attacks should be
identified as quickly as possible while
waiting for the updates from blacklists or
spam scanners. Moreover, spam scanners
always attempt to filter suspicious emails
however cannot be upgraded quickly. The
research has found that cybercriminals
typically use sophisticated methodologies
as well as tools for distributing a broad
range of malicious content in the form of
spam emails. Three key trends in
cybercrime through spams have been
identified as commercialization,
sophistication and changes to criminal firm
structures. In addition to that, it has been
found that spam emails cannot be fought
by technical measures only hence law-
enforcement agencies must have the
capability to efficiently investigate as well
as prosecute cybercriminals like spam
emails. Thus, it is found that eelectronic
mail which is known as email; is one of
the most convenient channels which can be
used for transferring information and
thereby share data with others. Yet, email
is the most common way to receive
information which contains dubious
messages or malicious attachments.
References
x
[1] R.H. and Studer, E Weber, "Cybersecurity in the Internet of Things: Legal aspects.," Computer Law & Security Review, vol. 32, no.
5, pp. 715-728, 2016.
[2] R. Broadhurst and L. Chang , Cybercrime in Asia: trends and challenges. New York: Springer, 2013.
[3] Uri Rivner. (2019) 2019 Predictions - 10 Cybercrime Trends to Expect in the New Year. [Online].
https://www.biocatch.com/blog/2019-predictions-10-cybercrime-trends
[4] The SSL Store. (2019) The Top Cyber Security Trends in 2019 (and What to Expect in 2020). [Online].
https://www.thesslstore.com/blog/the-top-cyber-security-trends-in-2019-and-what-to-expect-in-2020/
[5] H. and Skinner, G. Aldawood, "Reviewing Cyber Security Social Engineering Training and Awareness Programs—Pitfalls and
Ongoing Issues.," Future Internet, vol. 11, no. 3, p. 73, 2019.
[6] Financier Worldwide Magazine. (2019) Emerging trends in cyber security. [Online].
https://www.financierworldwide.com/emerging-trends-in-cyber-security#.Xg3TKkczbIV
7
Never provide and post email
addresses publicly
Always be cautious and think
before clicking suspicious links in
the spam emails
Always own spam-filtering-tools as
well as antivirus software by
downloading them
Avoid utilizing business and
personal email address while
registering in online contests or
services
Never reply to spam emails and
messages
V. Conclusion
In whole, this research paper has
successfully talked about spams and
cybercrime from the perspective of the
security of the users on the internet. While
doing so, almost every possible aspect of
the spams and cybercrime has been
explored well. In this context, the paper
has discussed existing defense and
detection mechanisms in order to deal with
malicious spam emails. In this way, novel
malware embedded spam attacks should be
identified as quickly as possible while
waiting for the updates from blacklists or
spam scanners. Moreover, spam scanners
always attempt to filter suspicious emails
however cannot be upgraded quickly. The
research has found that cybercriminals
typically use sophisticated methodologies
as well as tools for distributing a broad
range of malicious content in the form of
spam emails. Three key trends in
cybercrime through spams have been
identified as commercialization,
sophistication and changes to criminal firm
structures. In addition to that, it has been
found that spam emails cannot be fought
by technical measures only hence law-
enforcement agencies must have the
capability to efficiently investigate as well
as prosecute cybercriminals like spam
emails. Thus, it is found that eelectronic
mail which is known as email; is one of
the most convenient channels which can be
used for transferring information and
thereby share data with others. Yet, email
is the most common way to receive
information which contains dubious
messages or malicious attachments.
References
x
[1] R.H. and Studer, E Weber, "Cybersecurity in the Internet of Things: Legal aspects.," Computer Law & Security Review, vol. 32, no.
5, pp. 715-728, 2016.
[2] R. Broadhurst and L. Chang , Cybercrime in Asia: trends and challenges. New York: Springer, 2013.
[3] Uri Rivner. (2019) 2019 Predictions - 10 Cybercrime Trends to Expect in the New Year. [Online].
https://www.biocatch.com/blog/2019-predictions-10-cybercrime-trends
[4] The SSL Store. (2019) The Top Cyber Security Trends in 2019 (and What to Expect in 2020). [Online].
https://www.thesslstore.com/blog/the-top-cyber-security-trends-in-2019-and-what-to-expect-in-2020/
[5] H. and Skinner, G. Aldawood, "Reviewing Cyber Security Social Engineering Training and Awareness Programs—Pitfalls and
Ongoing Issues.," Future Internet, vol. 11, no. 3, p. 73, 2019.
[6] Financier Worldwide Magazine. (2019) Emerging trends in cyber security. [Online].
https://www.financierworldwide.com/emerging-trends-in-cyber-security#.Xg3TKkczbIV

CYBER CRIME
8
[7] Avery Blank. (2018) Forbes. [Online]. https://www.forbes.com/sites/averyblank/2018/01/02/how-successful-people-write-emails-to-
get-what-they-want-thatll-help-you-achieve-your-goals/#752d0c997672
[8] A. Bendovschi, "Cyber-attacks–trends, patterns and security countermeasures," Procedia Economics and Finance, vol. 28, pp. 24-
31, 2015.
[9] S. Chon, M. Alazab, P. Grabosky, and R. Broadhurst, "Organizations and Cyber crime: An Analysis of the Nature of," International
Journal of Cyber Criminology, vol. 8, no. 1, pp. 1-2, 2014.
[10] Continuum. (2019) Cybercrime & Security Overview: Terms, Trends, Statistics, and Takeaways. [Online].
https://www.continuum.net/resources/mspedia/cybercrime-and-security-overview
[11] B. Roderic, G. Peter, A. Mamoun, and C. Steve, "Organizations and cyber crime: an analysis of the nature of groups engaged in
cyber crime," International Journal of Cyber Criminiology, vol. 8, no. 1, pp. 1-20, 2014.
[12] Mathew Schwartz. (2018) Cybercrime: 15 Top Threats and Trends. [Online]. https://www.bankinfosecurity.com/cybercrime-trends-
hackers-still-prefer-bitcoin-a-11522
[13] M. Alazab and S. Venkatraman , "Detecting malicious behaviour using supervised learning algorithms of the," International Journal
of Electronic Security and Digital Forensics, vol. 5, no. 2, pp. 90-109, 2013.
[14] Nick Ismail. (2019) 10 cyber security trends to look out for in 2020. [Online]. https://www.information-age.com/10-cyber-security-
trends-look-2020-123463680/
[15] J. Iqbal and B. Beigh, "Cybercrime in India: Trends and Challenges," International Conference on Advancements and Innovations in
Engineering, Technology& Management, vol. 6, no. 12, 2017.
[16] Einaras von Gravrock. (2019) Here are the biggest cybercrime trends of 2019. [Online].
https://www.weforum.org/agenda/2019/03/here-are-the-biggest-cybercrime-trends-of-2019/
[17] John Hall. (2018) Forbes. [Online]. https://www.forbes.com/sites/johnhall/2018/06/03/8-simple-tips-that-will-improve-the-way-you-
use-email/#356d1d01115e
[18] North-Wales Police. (2019) What is Spam? [Online]. https://www.north-wales.police.uk/advice-and-support/cyber-crime/spam
[19] Derek Menky. (2018) 5 Emerging Trends in Cybercrime. [Online]. https://www.darkreading.com/endpoint/5-emerging-trends-in-
cybercrime/a/d-id/1333363
[20] ITU, UNDERSTANDING CYBERCRIME:P H E N O M E N A , C H A L L E N G E S. Switzerland: ITU, 2012.
[21] Wrap. (2018, November) Wrap. [Online]. http://www.wrap.org.uk/content/food-surplus-and-waste-uk-key-facts-nov18
[22] Nils van Dam. (2018) Home delivery is better for the environment! [Online]. https://www.duvalunionconsulting.com/home-delivery-
better-for-the-environment/
[23] Amazon. (2019) Amazon Pantry Delivery Fee. [Online]. https://www.amazon.co.uk/gp/help/customer/display.html?
nodeId=201963680
[24] Evgeniy A Nataliya Kh. (2019, Jan.) cleveroad. [Online]. https://www.cleveroad.com/blog/how-much-does-it-cost-to-create-an-
app#how-much-does-app-development-cost-worldwide
[25] Chris Leone. (2019) How Much Should You Budget For Marketing In 2019? [Online]. https://www.webstrategiesinc.com/blog/how-
much-budget-for-online-marketing-in-2014#:~:targetText=For%20B2C%20firms%2C%20marketing%20budgets,to%20as%20much
%20as%2016%25.
[26] PayScale. (2019, Nov.) PayScale. [Online]. https://www.payscale.com/research/UK/Job=Software_Developer/Salary
[27] AWS. (2019, Dec.) AWS TCO Calculator. [Online].
https://www.awstcocalculator.com/Output/Load/e8675272132206799572337979#
[28] Samuel Banks. (2016, Apr.) digital22. [Online]. https://www.digital22.com/insights/ppc-insight-how-much-does-adwords-cost
8
[7] Avery Blank. (2018) Forbes. [Online]. https://www.forbes.com/sites/averyblank/2018/01/02/how-successful-people-write-emails-to-
get-what-they-want-thatll-help-you-achieve-your-goals/#752d0c997672
[8] A. Bendovschi, "Cyber-attacks–trends, patterns and security countermeasures," Procedia Economics and Finance, vol. 28, pp. 24-
31, 2015.
[9] S. Chon, M. Alazab, P. Grabosky, and R. Broadhurst, "Organizations and Cyber crime: An Analysis of the Nature of," International
Journal of Cyber Criminology, vol. 8, no. 1, pp. 1-2, 2014.
[10] Continuum. (2019) Cybercrime & Security Overview: Terms, Trends, Statistics, and Takeaways. [Online].
https://www.continuum.net/resources/mspedia/cybercrime-and-security-overview
[11] B. Roderic, G. Peter, A. Mamoun, and C. Steve, "Organizations and cyber crime: an analysis of the nature of groups engaged in
cyber crime," International Journal of Cyber Criminiology, vol. 8, no. 1, pp. 1-20, 2014.
[12] Mathew Schwartz. (2018) Cybercrime: 15 Top Threats and Trends. [Online]. https://www.bankinfosecurity.com/cybercrime-trends-
hackers-still-prefer-bitcoin-a-11522
[13] M. Alazab and S. Venkatraman , "Detecting malicious behaviour using supervised learning algorithms of the," International Journal
of Electronic Security and Digital Forensics, vol. 5, no. 2, pp. 90-109, 2013.
[14] Nick Ismail. (2019) 10 cyber security trends to look out for in 2020. [Online]. https://www.information-age.com/10-cyber-security-
trends-look-2020-123463680/
[15] J. Iqbal and B. Beigh, "Cybercrime in India: Trends and Challenges," International Conference on Advancements and Innovations in
Engineering, Technology& Management, vol. 6, no. 12, 2017.
[16] Einaras von Gravrock. (2019) Here are the biggest cybercrime trends of 2019. [Online].
https://www.weforum.org/agenda/2019/03/here-are-the-biggest-cybercrime-trends-of-2019/
[17] John Hall. (2018) Forbes. [Online]. https://www.forbes.com/sites/johnhall/2018/06/03/8-simple-tips-that-will-improve-the-way-you-
use-email/#356d1d01115e
[18] North-Wales Police. (2019) What is Spam? [Online]. https://www.north-wales.police.uk/advice-and-support/cyber-crime/spam
[19] Derek Menky. (2018) 5 Emerging Trends in Cybercrime. [Online]. https://www.darkreading.com/endpoint/5-emerging-trends-in-
cybercrime/a/d-id/1333363
[20] ITU, UNDERSTANDING CYBERCRIME:P H E N O M E N A , C H A L L E N G E S. Switzerland: ITU, 2012.
[21] Wrap. (2018, November) Wrap. [Online]. http://www.wrap.org.uk/content/food-surplus-and-waste-uk-key-facts-nov18
[22] Nils van Dam. (2018) Home delivery is better for the environment! [Online]. https://www.duvalunionconsulting.com/home-delivery-
better-for-the-environment/
[23] Amazon. (2019) Amazon Pantry Delivery Fee. [Online]. https://www.amazon.co.uk/gp/help/customer/display.html?
nodeId=201963680
[24] Evgeniy A Nataliya Kh. (2019, Jan.) cleveroad. [Online]. https://www.cleveroad.com/blog/how-much-does-it-cost-to-create-an-
app#how-much-does-app-development-cost-worldwide
[25] Chris Leone. (2019) How Much Should You Budget For Marketing In 2019? [Online]. https://www.webstrategiesinc.com/blog/how-
much-budget-for-online-marketing-in-2014#:~:targetText=For%20B2C%20firms%2C%20marketing%20budgets,to%20as%20much
%20as%2016%25.
[26] PayScale. (2019, Nov.) PayScale. [Online]. https://www.payscale.com/research/UK/Job=Software_Developer/Salary
[27] AWS. (2019, Dec.) AWS TCO Calculator. [Online].
https://www.awstcocalculator.com/Output/Load/e8675272132206799572337979#
[28] Samuel Banks. (2016, Apr.) digital22. [Online]. https://www.digital22.com/insights/ppc-insight-how-much-does-adwords-cost

CYBER CRIME
9
[29] influence rmarketing hub. (2019, Mar.) influencermarketinghub. [Online]. https://influencermarketinghub.com/how-much-does-it-
cost-to-advertise-on-instagram/
[30] Betsy Mcleod. (2017, Mar.) bluecorona. [Online]. https://www.bluecorona.com/blog/how-much-facebook-advertising-costs
[31] webfx. (2019, Sep.) webfx. [Online]. https://www.webfx.com/internet-marketing/how-much-does-youtube-advertising-cost.html
[32] Taylor Schaller. (2019, Dec.) strikesocial. [Online]. https://strikesocial.com/blog/snapchat-cost/
x
9
[29] influence rmarketing hub. (2019, Mar.) influencermarketinghub. [Online]. https://influencermarketinghub.com/how-much-does-it-
cost-to-advertise-on-instagram/
[30] Betsy Mcleod. (2017, Mar.) bluecorona. [Online]. https://www.bluecorona.com/blog/how-much-facebook-advertising-costs
[31] webfx. (2019, Sep.) webfx. [Online]. https://www.webfx.com/internet-marketing/how-much-does-youtube-advertising-cost.html
[32] Taylor Schaller. (2019, Dec.) strikesocial. [Online]. https://strikesocial.com/blog/snapchat-cost/
x
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



