Cloud Computing Security, Privacy, and Data Sensitivity Analysis
VerifiedAdded on 2020/02/24
|15
|1619
|198
Report
AI Summary
This report provides a comprehensive analysis of cloud computing security, focusing on the risks to employee data and privacy concerns. It examines various threats, including phishing, unauthorized access, and malicious software attacks. The report delves into digital identity issues such as password vulnerabilities, identity sprawl, and weak security policies. It also explores provider solution issues like backup and redundancy, multiplicity of providers, and PaaS vulnerabilities. Furthermore, it addresses data sensitivity concerns related to jurisdiction and data processing locations. The conclusion summarizes the risks before and after cloud migration, highlighting specific threats and vulnerabilities. The report also includes references to relevant research and publications, providing a solid foundation for understanding cloud security challenges and potential mitigation strategies. The report addresses how the security and privacy of employee data are impacted by the migration to cloud computing, including the importance of backup and redundancy, and the use of third-party software. It also explores the jurisdictional challenges that arise with cloud computing, and the need for data protection in light of complex regulations.

Running head: CLOUD COMPUTING 1
Cloud Computing
Names
Course
Unit
Date
Cloud Computing
Names
Course
Unit
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head: CLOUD COMPUTING 2
1. Security of Employee Data
S.No Security
Threat/ Risk
Description
Likeliho
od
Impact
Priority Preventive Actions Contingency Plans
Student 1 Student ID
1 Unauthorized
Access
H VH VH 1. Ensure users are given
strong APIs that cannot be
breached easily and have them
encrypted
2. Sensitize users to be careful
when accessing cloud services
3. Employ two step
authentication to restrict
unauthorized access
1. Disable suspected
APIs and stop all
remote access
2. Contact provider
and alert them of
security breaches
immediately
3. use traffic access
lists to monitor activity
2 Phishing H VH H 1. Implement two phase
authentication
2. Sensitize employees never
to give personal information
online; ever
3. Constant review of user
activity logs
4. restrict access using
personal devices
1. Disable the remote
access
2. Contact cloud
service provider and
report suspected
attacks
3 Data access risk M H VH 1. Ensure access is well
defined in SLAs
2. Strong access management
3. Encrypt data or ensure the
service provider offers full
encryption
4. Ensure the SLA specifies
data formats to ensure
smooth portability in future
(Behl, 2011)
1. remote backup to
ensure continuity
1. Security of Employee Data
S.No Security
Threat/ Risk
Description
Likeliho
od
Impact
Priority Preventive Actions Contingency Plans
Student 1 Student ID
1 Unauthorized
Access
H VH VH 1. Ensure users are given
strong APIs that cannot be
breached easily and have them
encrypted
2. Sensitize users to be careful
when accessing cloud services
3. Employ two step
authentication to restrict
unauthorized access
1. Disable suspected
APIs and stop all
remote access
2. Contact provider
and alert them of
security breaches
immediately
3. use traffic access
lists to monitor activity
2 Phishing H VH H 1. Implement two phase
authentication
2. Sensitize employees never
to give personal information
online; ever
3. Constant review of user
activity logs
4. restrict access using
personal devices
1. Disable the remote
access
2. Contact cloud
service provider and
report suspected
attacks
3 Data access risk M H VH 1. Ensure access is well
defined in SLAs
2. Strong access management
3. Encrypt data or ensure the
service provider offers full
encryption
4. Ensure the SLA specifies
data formats to ensure
smooth portability in future
(Behl, 2011)
1. remote backup to
ensure continuity
Running head: CLOUD COMPUTING 3
4 Data loss H VH VH 1. Sensitize employees
2. Have data distributed across
multiple locations
3. Have virtual backups and
implement a hybrid cloud
1. Sensitize employees
on safety
2. Instant file recovery
in case of accidental
deletion/ overwriting
Explain Issues
1. Internal threats by staff: Entails employees stealing data/ information, or creating backdoors that
malicious entities like hackers can use to exploit the DAS resources, either for financial gain or purely
out of malice
2. Malicious software exploitation due to unintended employee actions: This entails employee
actions that are unintended, such as downloading infected files and opening links that cause malware
within them to infect systems and wreak havoc
3. External attacks over the network: Entails hackers accessing the DAS ICT resources through the
use of malware over the network, especially by exploiting vulnerabilities in network devices such as
routers (wired and wireless), or through remote access by hacking user passwords
4. Disasters: Are events such as fires, physical failure of hard drives, or natural disasters such
as earthquakes and flooding
4 Data loss H VH VH 1. Sensitize employees
2. Have data distributed across
multiple locations
3. Have virtual backups and
implement a hybrid cloud
1. Sensitize employees
on safety
2. Instant file recovery
in case of accidental
deletion/ overwriting
Explain Issues
1. Internal threats by staff: Entails employees stealing data/ information, or creating backdoors that
malicious entities like hackers can use to exploit the DAS resources, either for financial gain or purely
out of malice
2. Malicious software exploitation due to unintended employee actions: This entails employee
actions that are unintended, such as downloading infected files and opening links that cause malware
within them to infect systems and wreak havoc
3. External attacks over the network: Entails hackers accessing the DAS ICT resources through the
use of malware over the network, especially by exploiting vulnerabilities in network devices such as
routers (wired and wireless), or through remote access by hacking user passwords
4. Disasters: Are events such as fires, physical failure of hard drives, or natural disasters such
as earthquakes and flooding
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running head: CLOUD COMPUTING 4
Severity of risk and threat to security employee data
S.No Security
Threat/ Risk
Description
Likeliho
od
Impact
Priority Preventive Actions Contingency Plans
Student 1 Student ID
1 Unauthorized
Access
H VH VH 1. Ensure users are given strong
APIs that cannot be breached
easily and have them encrypted
2. Sensitize users to be careful
when accessing cloud services
3. Employ two step
authentication to restrict
unauthorized access (Kuyoro,
Ibikunle, Awodele, 2011)
1. Disable suspected
APIs and stop all
remote access
2. Contact provider
and alert them of
security breaches
immediately
3. use traffic access
lists to monitor activity
2 Phishing H VH H 1. Implement two phase
authentication (Carl &
Alexandros, 2008)
2. Sensitize employees never to
give personal information
online; ever
3. Constant review of user
activity logs
4. restrict access using personal
devices
1. Disable the remote
access
2. Contact cloud
service provider and
report suspected
attacks
Severity of risk and threat to security employee data
S.No Security
Threat/ Risk
Description
Likeliho
od
Impact
Priority Preventive Actions Contingency Plans
Student 1 Student ID
1 Unauthorized
Access
H VH VH 1. Ensure users are given strong
APIs that cannot be breached
easily and have them encrypted
2. Sensitize users to be careful
when accessing cloud services
3. Employ two step
authentication to restrict
unauthorized access (Kuyoro,
Ibikunle, Awodele, 2011)
1. Disable suspected
APIs and stop all
remote access
2. Contact provider
and alert them of
security breaches
immediately
3. use traffic access
lists to monitor activity
2 Phishing H VH H 1. Implement two phase
authentication (Carl &
Alexandros, 2008)
2. Sensitize employees never to
give personal information
online; ever
3. Constant review of user
activity logs
4. restrict access using personal
devices
1. Disable the remote
access
2. Contact cloud
service provider and
report suspected
attacks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head: CLOUD COMPUTING 5
3 Data access risk M H VH 1. Ensure access is well defined
in SLAs
2. Strong access management
3. Encrypt data or ensure the
service provider offers full
encryption
4. Ensure the SLA specifies
data formats to ensure
smooth portability in future
(Behl, 2011)
1. remote backup to
ensure continuity
4 Data loss H VH VH 1. Sensitize employees
2. Have data distributed across
multiple locations
3. Have virtual backups and
implement a hybrid cloud
(Stancu, 2016)
1. Sensitize employees
on safety
2. Instant file recovery
in case of accidental
deletion/ overwriting
Explain Issues
1. Unauthorized Access: Where persons without permission or the right credentials due to lack of
clear access polices or polices that have not been modified
2. Phishing: A type of fraud where an attackers attempts to obtain account information or log-in
credentials by pretending to be a reputable organization and then getting sensitive information through
e-mail and other channels, including social media
3. Data access risk: Where data is given to third parties and one is not sure who is accessing and/ or
using this data. There is potential for deletion, unauthorized dissemination, or data corruption
4. Data loss: Entails accidental deletion, modification of data by users; it also pertains to users losing
encryption keys for encrypted data that can then not be accessed until the encryption key is found
(Stancu, 2016).
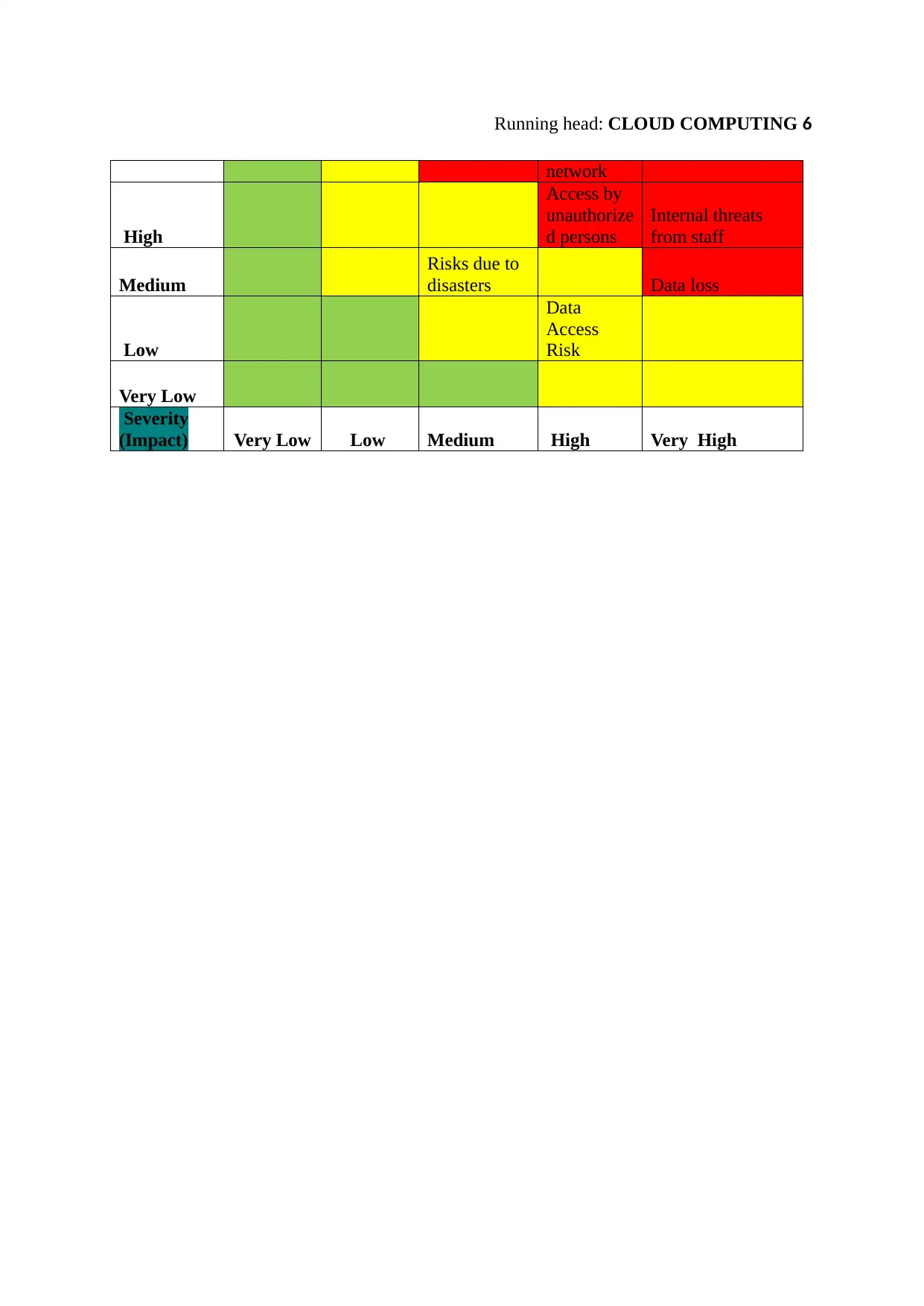
Severity risk and threat to security employee data
Probability
Very High Phishing External
exploitatio
n over
Malicious software
attacks over the
network
3 Data access risk M H VH 1. Ensure access is well defined
in SLAs
2. Strong access management
3. Encrypt data or ensure the
service provider offers full
encryption
4. Ensure the SLA specifies
data formats to ensure
smooth portability in future
(Behl, 2011)
1. remote backup to
ensure continuity
4 Data loss H VH VH 1. Sensitize employees
2. Have data distributed across
multiple locations
3. Have virtual backups and
implement a hybrid cloud
(Stancu, 2016)
1. Sensitize employees
on safety
2. Instant file recovery
in case of accidental
deletion/ overwriting
Explain Issues
1. Unauthorized Access: Where persons without permission or the right credentials due to lack of
clear access polices or polices that have not been modified
2. Phishing: A type of fraud where an attackers attempts to obtain account information or log-in
credentials by pretending to be a reputable organization and then getting sensitive information through
e-mail and other channels, including social media
3. Data access risk: Where data is given to third parties and one is not sure who is accessing and/ or
using this data. There is potential for deletion, unauthorized dissemination, or data corruption
4. Data loss: Entails accidental deletion, modification of data by users; it also pertains to users losing
encryption keys for encrypted data that can then not be accessed until the encryption key is found
(Stancu, 2016).
Severity risk and threat to security employee data
Probability
Very High Phishing External
exploitatio
n over
Malicious software
attacks over the
network
Running head: CLOUD COMPUTING 6
network
High
Access by
unauthorize
d persons
Internal threats
from staff
Medium
Risks due to
disasters Data loss
Low
Data
Access
Risk
Very Low
Severity
(Impact) Very Low Low Medium High Very High
network
High
Access by
unauthorize
d persons
Internal threats
from staff
Medium
Risks due to
disasters Data loss
Low
Data
Access
Risk
Very Low
Severity
(Impact) Very Low Low Medium High Very High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running head: CLOUD COMPUTING 7
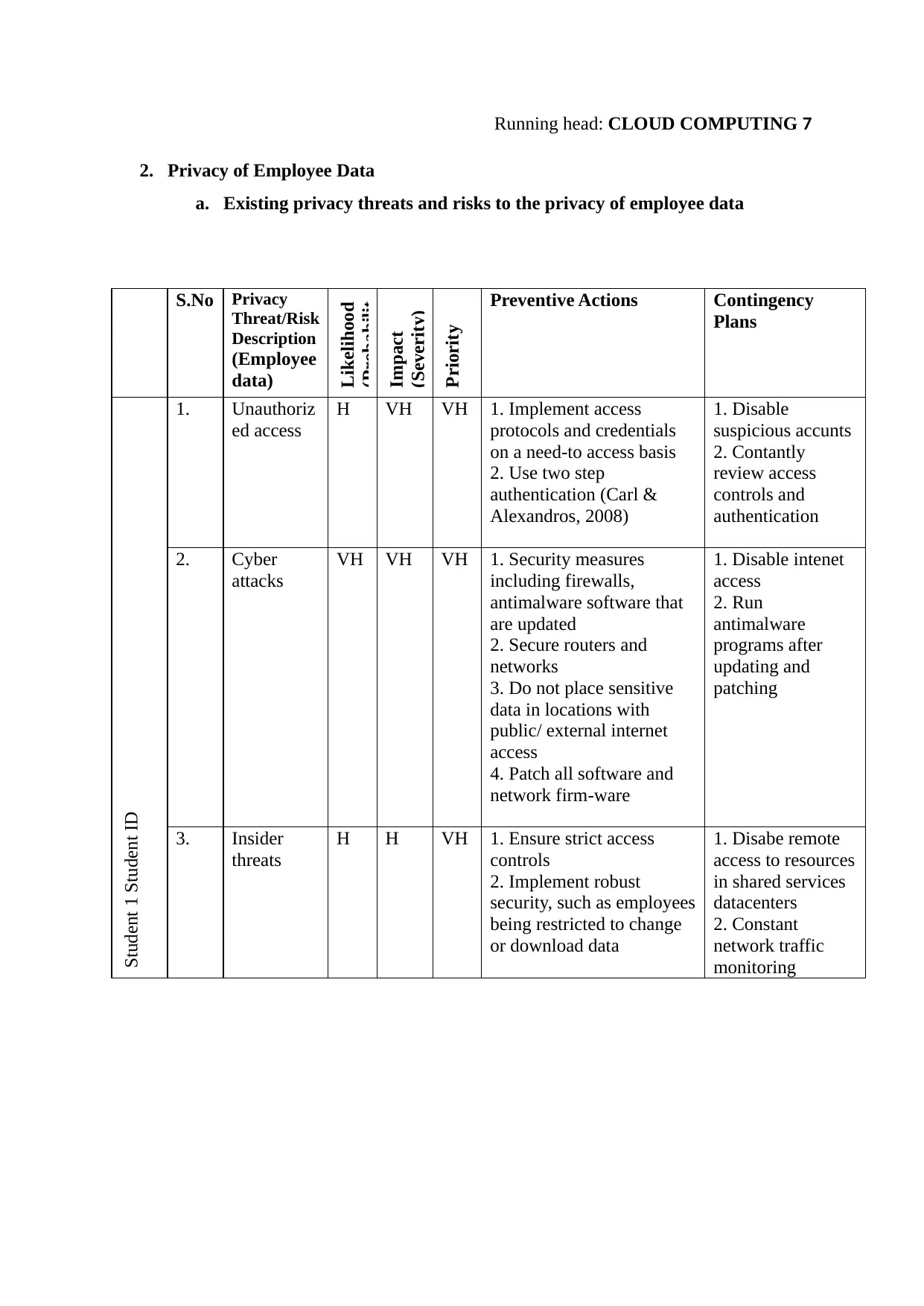
2. Privacy of Employee Data
a. Existing privacy threats and risks to the privacy of employee data
S.No Privacy
Threat/Risk
Description
(Employee
data)
Likelihood
(Probabilit
Impact
(Severity)
Priority Preventive Actions Contingency
Plans
Student 1 Student ID
1. Unauthoriz
ed access
H VH VH 1. Implement access
protocols and credentials
on a need-to access basis
2. Use two step
authentication (Carl &
Alexandros, 2008)
1. Disable
suspicious accunts
2. Contantly
review access
controls and
authentication
2. Cyber
attacks
VH VH VH 1. Security measures
including firewalls,
antimalware software that
are updated
2. Secure routers and
networks
3. Do not place sensitive
data in locations with
public/ external internet
access
4. Patch all software and
network firm-ware
1. Disable intenet
access
2. Run
antimalware
programs after
updating and
patching
3. Insider
threats
H H VH 1. Ensure strict access
controls
2. Implement robust
security, such as employees
being restricted to change
or download data
1. Disabe remote
access to resources
in shared services
datacenters
2. Constant
network traffic
monitoring
2. Privacy of Employee Data
a. Existing privacy threats and risks to the privacy of employee data
S.No Privacy
Threat/Risk
Description
(Employee
data)
Likelihood
(Probabilit
Impact
(Severity)
Priority Preventive Actions Contingency
Plans
Student 1 Student ID
1. Unauthoriz
ed access
H VH VH 1. Implement access
protocols and credentials
on a need-to access basis
2. Use two step
authentication (Carl &
Alexandros, 2008)
1. Disable
suspicious accunts
2. Contantly
review access
controls and
authentication
2. Cyber
attacks
VH VH VH 1. Security measures
including firewalls,
antimalware software that
are updated
2. Secure routers and
networks
3. Do not place sensitive
data in locations with
public/ external internet
access
4. Patch all software and
network firm-ware
1. Disable intenet
access
2. Run
antimalware
programs after
updating and
patching
3. Insider
threats
H H VH 1. Ensure strict access
controls
2. Implement robust
security, such as employees
being restricted to change
or download data
1. Disabe remote
access to resources
in shared services
datacenters
2. Constant
network traffic
monitoring
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head: CLOUD COMPUTING 8
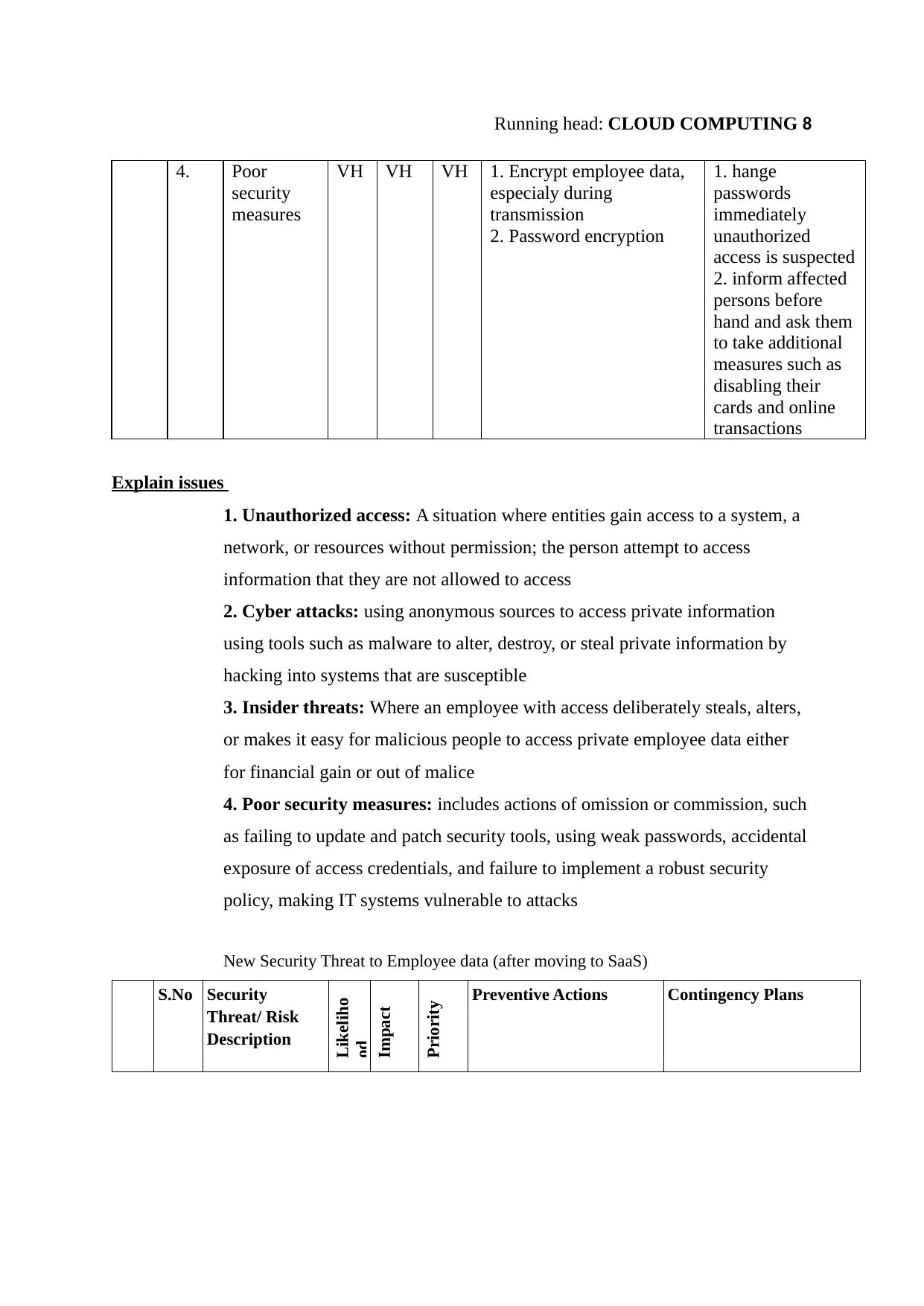
4. Poor
security
measures
VH VH VH 1. Encrypt employee data,
especialy during
transmission
2. Password encryption
1. hange
passwords
immediately
unauthorized
access is suspected
2. inform affected
persons before
hand and ask them
to take additional
measures such as
disabling their
cards and online
transactions
Explain issues
1. Unauthorized access: A situation where entities gain access to a system, a
network, or resources without permission; the person attempt to access
information that they are not allowed to access
2. Cyber attacks: using anonymous sources to access private information
using tools such as malware to alter, destroy, or steal private information by
hacking into systems that are susceptible
3. Insider threats: Where an employee with access deliberately steals, alters,
or makes it easy for malicious people to access private employee data either
for financial gain or out of malice
4. Poor security measures: includes actions of omission or commission, such
as failing to update and patch security tools, using weak passwords, accidental
exposure of access credentials, and failure to implement a robust security
policy, making IT systems vulnerable to attacks
New Security Threat to Employee data (after moving to SaaS)
S.No Security
Threat/ Risk
Description
Likeliho
od
Impact
Priority Preventive Actions Contingency Plans
4. Poor
security
measures
VH VH VH 1. Encrypt employee data,
especialy during
transmission
2. Password encryption
1. hange
passwords
immediately
unauthorized
access is suspected
2. inform affected
persons before
hand and ask them
to take additional
measures such as
disabling their
cards and online
transactions
Explain issues
1. Unauthorized access: A situation where entities gain access to a system, a
network, or resources without permission; the person attempt to access
information that they are not allowed to access
2. Cyber attacks: using anonymous sources to access private information
using tools such as malware to alter, destroy, or steal private information by
hacking into systems that are susceptible
3. Insider threats: Where an employee with access deliberately steals, alters,
or makes it easy for malicious people to access private employee data either
for financial gain or out of malice
4. Poor security measures: includes actions of omission or commission, such
as failing to update and patch security tools, using weak passwords, accidental
exposure of access credentials, and failure to implement a robust security
policy, making IT systems vulnerable to attacks
New Security Threat to Employee data (after moving to SaaS)
S.No Security
Threat/ Risk
Description
Likeliho
od
Impact
Priority Preventive Actions Contingency Plans
Running head: CLOUD COMPUTING 9
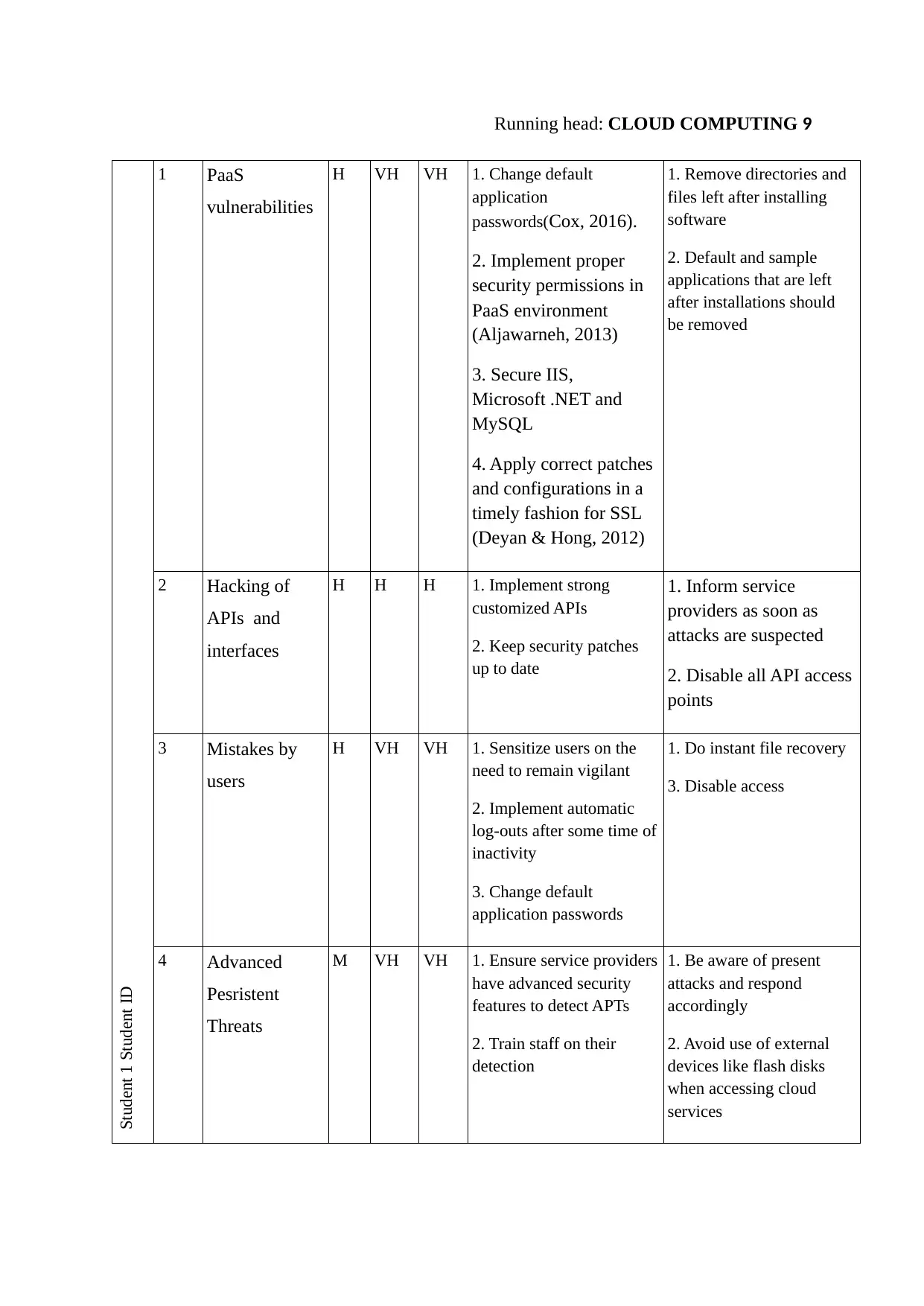
Student 1 Student ID
1 PaaS
vulnerabilities
H VH VH 1. Change default
application
passwords(Cox, 2016).
2. Implement proper
security permissions in
PaaS environment
(Aljawarneh, 2013)
3. Secure IIS,
Microsoft .NET and
MySQL
4. Apply correct patches
and configurations in a
timely fashion for SSL
(Deyan & Hong, 2012)
1. Remove directories and
files left after installing
software
2. Default and sample
applications that are left
after installations should
be removed
2 Hacking of
APIs and
interfaces
H H H 1. Implement strong
customized APIs
2. Keep security patches
up to date
1. Inform service
providers as soon as
attacks are suspected
2. Disable all API access
points
3 Mistakes by
users
H VH VH 1. Sensitize users on the
need to remain vigilant
2. Implement automatic
log-outs after some time of
inactivity
3. Change default
application passwords
1. Do instant file recovery
3. Disable access
4 Advanced
Pesristent
Threats
M VH VH 1. Ensure service providers
have advanced security
features to detect APTs
2. Train staff on their
detection
1. Be aware of present
attacks and respond
accordingly
2. Avoid use of external
devices like flash disks
when accessing cloud
services
Student 1 Student ID
1 PaaS
vulnerabilities
H VH VH 1. Change default
application
passwords(Cox, 2016).
2. Implement proper
security permissions in
PaaS environment
(Aljawarneh, 2013)
3. Secure IIS,
Microsoft .NET and
MySQL
4. Apply correct patches
and configurations in a
timely fashion for SSL
(Deyan & Hong, 2012)
1. Remove directories and
files left after installing
software
2. Default and sample
applications that are left
after installations should
be removed
2 Hacking of
APIs and
interfaces
H H H 1. Implement strong
customized APIs
2. Keep security patches
up to date
1. Inform service
providers as soon as
attacks are suspected
2. Disable all API access
points
3 Mistakes by
users
H VH VH 1. Sensitize users on the
need to remain vigilant
2. Implement automatic
log-outs after some time of
inactivity
3. Change default
application passwords
1. Do instant file recovery
3. Disable access
4 Advanced
Pesristent
Threats
M VH VH 1. Ensure service providers
have advanced security
features to detect APTs
2. Train staff on their
detection
1. Be aware of present
attacks and respond
accordingly
2. Avoid use of external
devices like flash disks
when accessing cloud
services
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running head: CLOUD COMPUTING 10
Explanation of Issues
1. PaaS Vulnerabilities: In this model, the security and control of application (Microsoft Share Point)
is the responsibility of the user, and so DAS must deal with SSL flaws, default application
configurations, and insecure permissions (Cox, 2016).
2. Hacking of APIs and Interfaces: APIs are utilized to interact and manage with cloud services;
with third parties such as the Microsoft Share Point the risks to APIs increase. He Interfaces and APIs
are accessed from open internet, making them the most vulnerable part in the cloud system.
3. Mistakes by users: Refers to situations where users make mistakes, such as losing encryption keys
pose threats to cloud data
4. Advanced Persistent Threats: These are parasitic forms of attack that infiltrate the system
laterally and blend with normal traffic, especially where a private cloud with a data center is being
used; they then stealthily steal intellectual property and employee data over a period of time. This
makes their detection very difficult
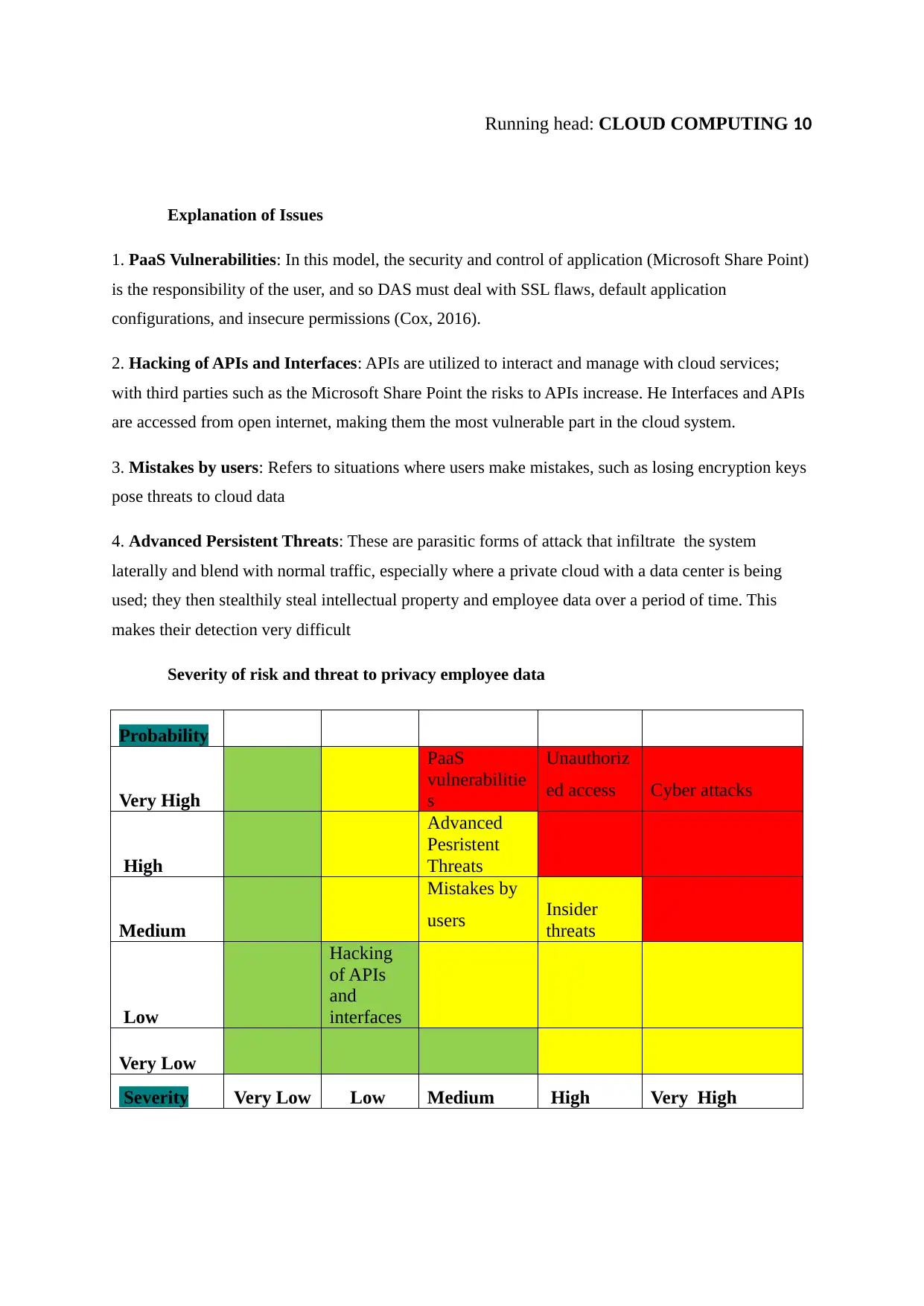
Severity of risk and threat to privacy employee data
Probability
Very High
PaaS
vulnerabilitie
s
Unauthoriz
ed access Cyber attacks
High
Advanced
Pesristent
Threats
Medium
Mistakes by
users Insider
threats
Low
Hacking
of APIs
and
interfaces
Very Low
Severity Very Low Low Medium High Very High
Explanation of Issues
1. PaaS Vulnerabilities: In this model, the security and control of application (Microsoft Share Point)
is the responsibility of the user, and so DAS must deal with SSL flaws, default application
configurations, and insecure permissions (Cox, 2016).
2. Hacking of APIs and Interfaces: APIs are utilized to interact and manage with cloud services;
with third parties such as the Microsoft Share Point the risks to APIs increase. He Interfaces and APIs
are accessed from open internet, making them the most vulnerable part in the cloud system.
3. Mistakes by users: Refers to situations where users make mistakes, such as losing encryption keys
pose threats to cloud data
4. Advanced Persistent Threats: These are parasitic forms of attack that infiltrate the system
laterally and blend with normal traffic, especially where a private cloud with a data center is being
used; they then stealthily steal intellectual property and employee data over a period of time. This
makes their detection very difficult
Severity of risk and threat to privacy employee data
Probability
Very High
PaaS
vulnerabilitie
s
Unauthoriz
ed access Cyber attacks
High
Advanced
Pesristent
Threats
Medium
Mistakes by
users Insider
threats
Low
Hacking
of APIs
and
interfaces
Very Low
Severity Very Low Low Medium High Very High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: CLOUD COMPUTING 11
3. Digital Identity Issues (threats and risks to the digital identities of Government
employees from the move to SaaS applications) (some issues from Q3
Assignment1)
Student 1 Student ID
1. Security: use of single factor digital identities through passwords create huge
vulnerabilities because they are usually familiar or can be easily cracked; such as by brute
force. Default or breached passwords and knowledge based authentication which are highly
susceptible
2. Identity sprawl: A situation where the Government employees have several fragmented
identities so they use easy and weak passwords that they can easily remember; a single
breach can open the door to other systems; for instance if the payroll password is cracked,
hackers can access a users’ credentials to human resource, identity, and performance records
3. Weak policies: users can just write and post passwords on a stick-on; making it easily
vulnerability to be stolen or breached and used maliciously. Even with policies, there is the
challenge of a dearth of usability consciousness authentication systems, making them
meaningless.
4. Multiple access points: This is where the government employees can access the cloud
services from any location, including using their personal devices, which can be breached and
cause identity theft and be used to access the entire cloud and compromise it
4. Provider Solution Issues and why?
Issues because of provider solutions:
Student 1 Student ID
1. Backup and redundancy: having the two solution providers have alternate
location for their data centers provides an added layer of security in case of a disaster
in one location; the second location can provide backup, ensuring data safety and
security
2. Multiplicity of providers: DAS will use different cloud service providers; each
which have other third parties or sourced services, such as processing in Bangalore;
3. Digital Identity Issues (threats and risks to the digital identities of Government
employees from the move to SaaS applications) (some issues from Q3
Assignment1)
Student 1 Student ID
1. Security: use of single factor digital identities through passwords create huge
vulnerabilities because they are usually familiar or can be easily cracked; such as by brute
force. Default or breached passwords and knowledge based authentication which are highly
susceptible
2. Identity sprawl: A situation where the Government employees have several fragmented
identities so they use easy and weak passwords that they can easily remember; a single
breach can open the door to other systems; for instance if the payroll password is cracked,
hackers can access a users’ credentials to human resource, identity, and performance records
3. Weak policies: users can just write and post passwords on a stick-on; making it easily
vulnerability to be stolen or breached and used maliciously. Even with policies, there is the
challenge of a dearth of usability consciousness authentication systems, making them
meaningless.
4. Multiple access points: This is where the government employees can access the cloud
services from any location, including using their personal devices, which can be breached and
cause identity theft and be used to access the entire cloud and compromise it
4. Provider Solution Issues and why?
Issues because of provider solutions:
Student 1 Student ID
1. Backup and redundancy: having the two solution providers have alternate
location for their data centers provides an added layer of security in case of a disaster
in one location; the second location can provide backup, ensuring data safety and
security
2. Multiplicity of providers: DAS will use different cloud service providers; each
which have other third parties or sourced services, such as processing in Bangalore;
Running head: CLOUD COMPUTING 12
the result is lack of total control over its data that can be breached or mishandled by
the service provider; adversely affecting data security and privacy
3. PaaS: PaaS behooves DAS to manage secure and control the application security;
any known vulnerabilities of Microsoft SharePoint must be effectively managed,
otherwise areas such as SSL, default configurations, and insecure permissions can be
exploited, posing a threat to employee data privacy and security
4. Third party software threat: using COTS for managing payroll in the cloud
creates a risk to data security and privacy as COTS is a third party software. Third
party software can have vulnerabilities that can be exploited in the cloud; leading to
breaches such as theft of employee data (Cox, 2016)
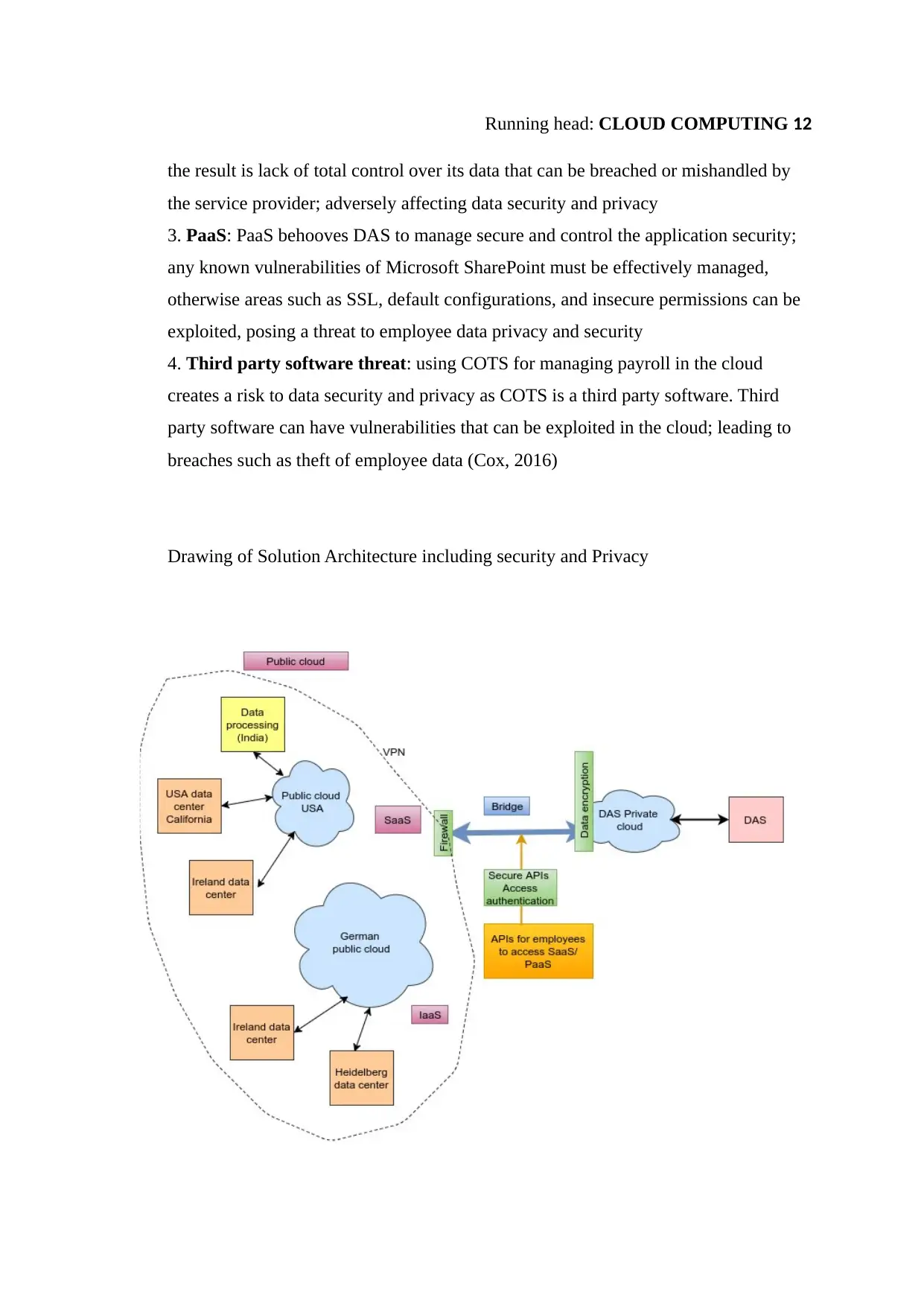
Drawing of Solution Architecture including security and Privacy
the result is lack of total control over its data that can be breached or mishandled by
the service provider; adversely affecting data security and privacy
3. PaaS: PaaS behooves DAS to manage secure and control the application security;
any known vulnerabilities of Microsoft SharePoint must be effectively managed,
otherwise areas such as SSL, default configurations, and insecure permissions can be
exploited, posing a threat to employee data privacy and security
4. Third party software threat: using COTS for managing payroll in the cloud
creates a risk to data security and privacy as COTS is a third party software. Third
party software can have vulnerabilities that can be exploited in the cloud; leading to
breaches such as theft of employee data (Cox, 2016)
Drawing of Solution Architecture including security and Privacy
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





