Cybersecurity and User-Centered Design
VerifiedAdded on 2020/10/05
|10
|2318
|346
AI Summary
This assignment delves into the realm of cybersecurity research methods, highlighting the significance of user-centered design in improving end-user security sensitivity. It examines various design techniques and applications of cyberphysical systems, as well as research methodologies used in qualitative, quantitative, or mixed-methods studies. The assignment also touches on the importance of cybersecurity and how to improve it through user accountability and socio-technical systems.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Graphic Design
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
TITLE: ............................................................................................................................................1
AIM .................................................................................................................................................1
LITERATURE AND CONTEXT ...................................................................................................1
METHODOLOGY .........................................................................................................................2
TIMESCALE ..................................................................................................................................3
EXPECTED OUTCOMES .............................................................................................................4
REFERENCES ...............................................................................................................................6
TITLE: ............................................................................................................................................1
AIM .................................................................................................................................................1
LITERATURE AND CONTEXT ...................................................................................................1
METHODOLOGY .........................................................................................................................2
TIMESCALE ..................................................................................................................................3
EXPECTED OUTCOMES .............................................................................................................4
REFERENCES ...............................................................................................................................6

TITLE:
To investigate how cyber security systems can be improved through implementation of
graphic design
AIM
To investigate how cyber security systems can be improved through implementation of
graphic design.
LITERATURE AND CONTEXT
Cyber security mechanisms are defined as the security measures which can protect the
data and information systems. In this digital era the dependencies on information technology
systems has been increasing rapidly. For successful and safe use of digital technology it is
essential that cyber security must be considered as an important part of the processes (Why Is
Cyber Security Important?, 2017). The graphic designing plays a significant role in enhancing
the security of systems. Graphic designing is defined as the approach to encourage
communication by using illustrations, photography and typography. It is mainly used in web
designing, editorial or corporate designing and in other web based applications.
The socio-technical systems consist of both technical and social elements like human
resources and organisations. The use of effective graphic designing techniques will enable users
to capture a more efficient and precise interaction with the computer systems so that security of
systems is not compromised. The utility and flexibility provided by the graphic designers must
be in alignment with the security needs of system (Improving Cybersecurity: User Accountability
and Socio technical Systems, 2017). The business organisations can combat the cyber attacks
with several strategies. For instance T systems has employed a graphical designing system which
is able to detect the vulnerabilities with the help of specialised protecting graphical designing. It
helps organisation to resolve its security concerns effectively (More proactive, less reactive,
2019).
Thus there is strong link between cyber security and graphic designing because this
designing aspect is associated with the system structure which can bring major differences in
security. According to Endsley, 2016, the use of strong and safe coding and design by graphic
designers provides strong protection against security vulnerabilities. When websites are designed
1
To investigate how cyber security systems can be improved through implementation of
graphic design
AIM
To investigate how cyber security systems can be improved through implementation of
graphic design.
LITERATURE AND CONTEXT
Cyber security mechanisms are defined as the security measures which can protect the
data and information systems. In this digital era the dependencies on information technology
systems has been increasing rapidly. For successful and safe use of digital technology it is
essential that cyber security must be considered as an important part of the processes (Why Is
Cyber Security Important?, 2017). The graphic designing plays a significant role in enhancing
the security of systems. Graphic designing is defined as the approach to encourage
communication by using illustrations, photography and typography. It is mainly used in web
designing, editorial or corporate designing and in other web based applications.
The socio-technical systems consist of both technical and social elements like human
resources and organisations. The use of effective graphic designing techniques will enable users
to capture a more efficient and precise interaction with the computer systems so that security of
systems is not compromised. The utility and flexibility provided by the graphic designers must
be in alignment with the security needs of system (Improving Cybersecurity: User Accountability
and Socio technical Systems, 2017). The business organisations can combat the cyber attacks
with several strategies. For instance T systems has employed a graphical designing system which
is able to detect the vulnerabilities with the help of specialised protecting graphical designing. It
helps organisation to resolve its security concerns effectively (More proactive, less reactive,
2019).
Thus there is strong link between cyber security and graphic designing because this
designing aspect is associated with the system structure which can bring major differences in
security. According to Endsley, 2016, the use of strong and safe coding and design by graphic
designers provides strong protection against security vulnerabilities. When websites are designed
1

with secure graphics then they provide strong foundation for management of cyber systems. The
formal verification and accuracy of the design algorithms used by the graphic designers assure
that designed websites and cyber security elements are provided with cryptographic protocols.
These protocols are considered as one of the most essential and powerful requirement for system
security (Zhang-Kennedy, Chiasson and Biddle, 2016).
There have been regular advancements in the graphical designing. The systems are able
to integrating with real time data as well. Thus it is also required that with improved system
efficiencies the cyber threat must also be eliminated (Staheli, McKenna and Meyer, 2015).
However it is not possible to design a system and then directly at installation phase the threats
can be removed. Contrary it requires the efforts at graphical designing level that the system is
designed in a way such that it can cope up with the emerging challenges of cyber threats.
In the same context Khaitan and McCalley, 2015, believes that when designing protocols
are not in alignment with the security protocols then there are higher risks of cyber threats. Thus
it is very important that graphical designing protocols must be effective enough so that they can
introduce integrity, confidentiality and availability within designed systems which are key
principles in cyber security.
METHODOLOGY
Research methodology is systematic framework which explain the various stages for
achieving the research objectives. For conducting the research it is essential that research topic
must be analysed through effective methods. Research methodologies provides a systematic
guidelines to gather data so that suitable conclusions can be drawn through the analysis of the
collected data. For the proposed research following methods will be used:
Design: Research design can be defined as the methodology which describes the way to
accomplish the entire research. The design can be classified into three types: Descriptive design,
causal and exploratory design (Simonsohn, Nelson and Simmons, 2017). To study the impact
and methods of graphic designing in improving cyber security exploratory research design will
be employed in this research (Lupton and Phillips, 2015). Exploratory approach will provide a
better understanding of the issues so that new ideas will be generated to achieve the research
objectives.
2
formal verification and accuracy of the design algorithms used by the graphic designers assure
that designed websites and cyber security elements are provided with cryptographic protocols.
These protocols are considered as one of the most essential and powerful requirement for system
security (Zhang-Kennedy, Chiasson and Biddle, 2016).
There have been regular advancements in the graphical designing. The systems are able
to integrating with real time data as well. Thus it is also required that with improved system
efficiencies the cyber threat must also be eliminated (Staheli, McKenna and Meyer, 2015).
However it is not possible to design a system and then directly at installation phase the threats
can be removed. Contrary it requires the efforts at graphical designing level that the system is
designed in a way such that it can cope up with the emerging challenges of cyber threats.
In the same context Khaitan and McCalley, 2015, believes that when designing protocols
are not in alignment with the security protocols then there are higher risks of cyber threats. Thus
it is very important that graphical designing protocols must be effective enough so that they can
introduce integrity, confidentiality and availability within designed systems which are key
principles in cyber security.
METHODOLOGY
Research methodology is systematic framework which explain the various stages for
achieving the research objectives. For conducting the research it is essential that research topic
must be analysed through effective methods. Research methodologies provides a systematic
guidelines to gather data so that suitable conclusions can be drawn through the analysis of the
collected data. For the proposed research following methods will be used:
Design: Research design can be defined as the methodology which describes the way to
accomplish the entire research. The design can be classified into three types: Descriptive design,
causal and exploratory design (Simonsohn, Nelson and Simmons, 2017). To study the impact
and methods of graphic designing in improving cyber security exploratory research design will
be employed in this research (Lupton and Phillips, 2015). Exploratory approach will provide a
better understanding of the issues so that new ideas will be generated to achieve the research
objectives.
2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Research approach: The efficient research approach enables the researchers to follow the
simplified pathway for analysing the research questions. It will provide details of methods which
helps to interpret the data. Research approaches are divided into three types: Inductive research
approach, deductive approach and abductive. For the study purpose inductive approach will be
used and no hypothesis will be formed. Instead corresponding to the current implications and
trends of graphic designing in security various themes will be analysed.
Research philosophy: Without implementing the knowledge in an accurate direction it is
impossible to achieve research aims. The suitable philosophy helps to apply analysis skills into
accomplishment of research. The research philosophies can be classified as interpretivism
philosophy, realism and positivism philosophy. In the study interpretivism philosophy will be
used for analysing the real time concepts. It helps to develop conclusions through observations.
In context with the given research topic it will be easy to evaluate the different aspects of the
subject through interpretivism approach.
Data analysis: The study may analyse qualitative as well as quantitative data. The qualitative
data analysis includes the non-statistical data while the quantitative data includes the numerical
facts and figures which are analysed to make suitable conclusions. Data analysis is one of the
most crucial part of the research. In this study qualitative data will be analysed. The collected
data will be interpreted by thematic analysis of various themes formulated on the basis of subject
area.
Data collection: For the study purpose the data collection holds great importance. The data can
be collected by primary as well as secondary methods. Primary data collection methods gathers
data by analysing the various observations and results (McCusker and Gunaydin, 2015). While
on the other hand secondary data can be obtained from secondary sources of data such as
journals, books or the works of other scholars and then by using that work for further
interpretation (Simonsohn, Nelson and Simmons, 2017). The reliability and validity of the
research findings depends upon the accuracy and efficiency of data collected (Flick, 2015).
Along with secondary data sources primary data collection methods will be used for the study. It
will include a questionnaire for collecting the data from selected samples.
Sampling: For making this study possible and manageable a small size of samples are involved
in the study as participants. Sampling approaches are of probabilistic and non-probabilistic. In
3
simplified pathway for analysing the research questions. It will provide details of methods which
helps to interpret the data. Research approaches are divided into three types: Inductive research
approach, deductive approach and abductive. For the study purpose inductive approach will be
used and no hypothesis will be formed. Instead corresponding to the current implications and
trends of graphic designing in security various themes will be analysed.
Research philosophy: Without implementing the knowledge in an accurate direction it is
impossible to achieve research aims. The suitable philosophy helps to apply analysis skills into
accomplishment of research. The research philosophies can be classified as interpretivism
philosophy, realism and positivism philosophy. In the study interpretivism philosophy will be
used for analysing the real time concepts. It helps to develop conclusions through observations.
In context with the given research topic it will be easy to evaluate the different aspects of the
subject through interpretivism approach.
Data analysis: The study may analyse qualitative as well as quantitative data. The qualitative
data analysis includes the non-statistical data while the quantitative data includes the numerical
facts and figures which are analysed to make suitable conclusions. Data analysis is one of the
most crucial part of the research. In this study qualitative data will be analysed. The collected
data will be interpreted by thematic analysis of various themes formulated on the basis of subject
area.
Data collection: For the study purpose the data collection holds great importance. The data can
be collected by primary as well as secondary methods. Primary data collection methods gathers
data by analysing the various observations and results (McCusker and Gunaydin, 2015). While
on the other hand secondary data can be obtained from secondary sources of data such as
journals, books or the works of other scholars and then by using that work for further
interpretation (Simonsohn, Nelson and Simmons, 2017). The reliability and validity of the
research findings depends upon the accuracy and efficiency of data collected (Flick, 2015).
Along with secondary data sources primary data collection methods will be used for the study. It
will include a questionnaire for collecting the data from selected samples.
Sampling: For making this study possible and manageable a small size of samples are involved
in the study as participants. Sampling approaches are of probabilistic and non-probabilistic. In
3
probability sampling each sample is selected with equal probability of selection while in case of
non-probabilistic sampling certain conditions or criteria is used to choose the sample population
(Short, 2016). The samples are collected by probability sampling approach so that validate
results are obtained for the study.
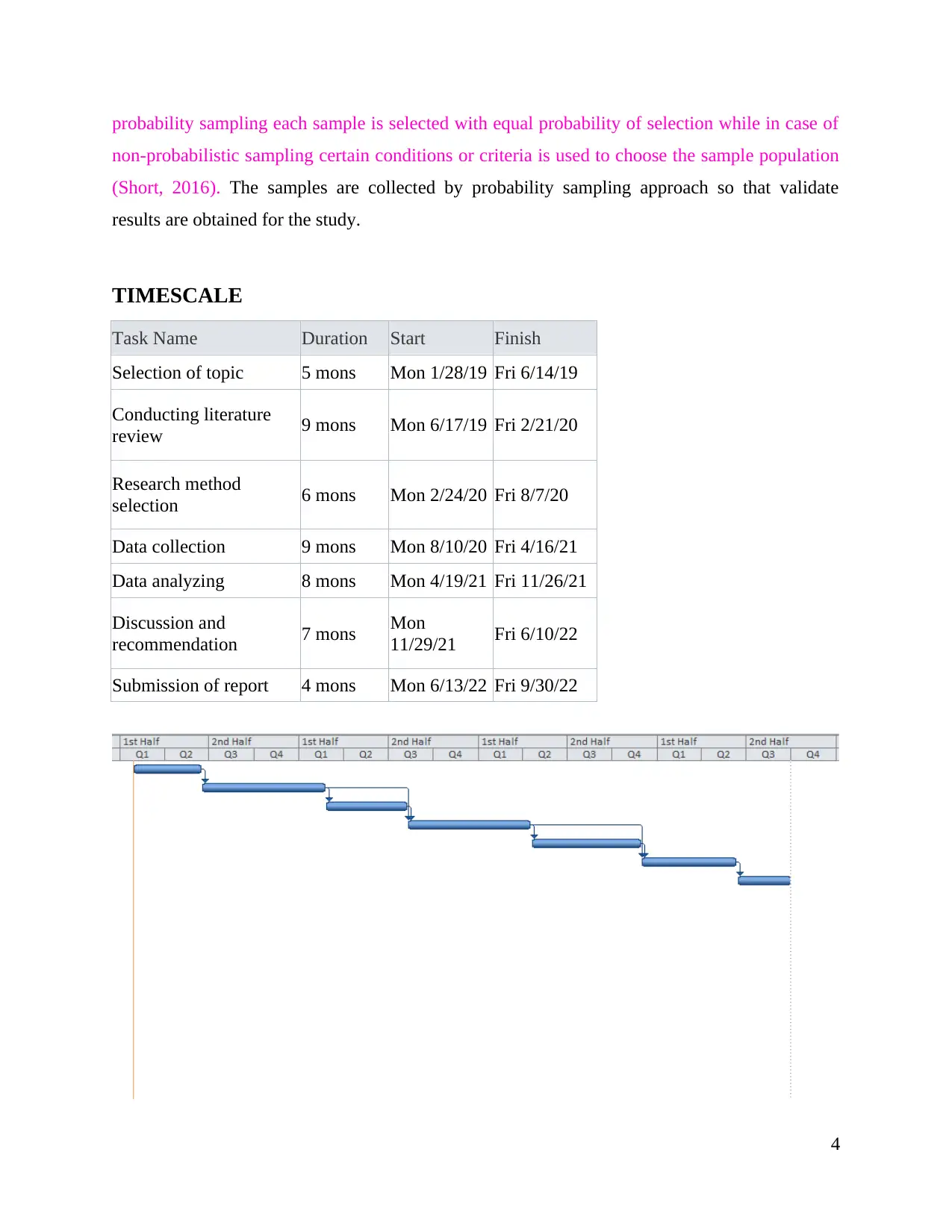
TIMESCALE
Task Name Duration Start Finish
Selection of topic 5 mons Mon 1/28/19 Fri 6/14/19
Conducting literature
review 9 mons Mon 6/17/19 Fri 2/21/20
Research method
selection 6 mons Mon 2/24/20 Fri 8/7/20
Data collection 9 mons Mon 8/10/20 Fri 4/16/21
Data analyzing 8 mons Mon 4/19/21 Fri 11/26/21
Discussion and
recommendation 7 mons Mon
11/29/21 Fri 6/10/22
Submission of report 4 mons Mon 6/13/22 Fri 9/30/22
4
non-probabilistic sampling certain conditions or criteria is used to choose the sample population
(Short, 2016). The samples are collected by probability sampling approach so that validate
results are obtained for the study.
TIMESCALE
Task Name Duration Start Finish
Selection of topic 5 mons Mon 1/28/19 Fri 6/14/19
Conducting literature
review 9 mons Mon 6/17/19 Fri 2/21/20
Research method
selection 6 mons Mon 2/24/20 Fri 8/7/20
Data collection 9 mons Mon 8/10/20 Fri 4/16/21
Data analyzing 8 mons Mon 4/19/21 Fri 11/26/21
Discussion and
recommendation 7 mons Mon
11/29/21 Fri 6/10/22
Submission of report 4 mons Mon 6/13/22 Fri 9/30/22
4

Challenges:
During the research it will be challenging to gather the accurate data. The graphical
designers can provide the more accurate information that how their current designing approaches
can meet the objectives of cyber security (McKenna, Staheli and Meyer, 2015). However it is
very challenging to obtain samples who are expertise in their designing skills as per the
complexity of security threats. The analysis of various methods and approaches of graphical
designing from perspective of cyber security can be challenging due to regular and rapid
advancements in security threats and design approaches (Zahabi, Kaber and Swangnetr, 2015).
Several secondary data sources have also been used in the study. It is essential to ensure the
validity of these secondary sources which is another challenge for successfully conducting this
research. There has been regular changes in the technology thus the results and duration of the
study can be affected by the variable nature and behaviour of IT systems and their security
concerns (Das, 2016).
Milestone of research:
This study will be a milestone in encouraging further developments in graphical
designing so that security can be enhanced from designing level instead of implementation level.
It will make cyber security process more efficient and cost effective as well.
Progression:
In the first year I wish to achieve the in-depth knowledge of graphic designing so that I
can understand that how this aspect can influence the cyber security. This knowledge will help
me to improve the existing approaches for overcoming the security concerns.
EXPECTED OUTCOMES
From this research study following outcomes are expected:
It will create more emphasis on the designing approaches so that security risks can be
minimized from ground or designing level itself (Ahram, Karwowski and Taiar, 2018).
5
During the research it will be challenging to gather the accurate data. The graphical
designers can provide the more accurate information that how their current designing approaches
can meet the objectives of cyber security (McKenna, Staheli and Meyer, 2015). However it is
very challenging to obtain samples who are expertise in their designing skills as per the
complexity of security threats. The analysis of various methods and approaches of graphical
designing from perspective of cyber security can be challenging due to regular and rapid
advancements in security threats and design approaches (Zahabi, Kaber and Swangnetr, 2015).
Several secondary data sources have also been used in the study. It is essential to ensure the
validity of these secondary sources which is another challenge for successfully conducting this
research. There has been regular changes in the technology thus the results and duration of the
study can be affected by the variable nature and behaviour of IT systems and their security
concerns (Das, 2016).
Milestone of research:
This study will be a milestone in encouraging further developments in graphical
designing so that security can be enhanced from designing level instead of implementation level.
It will make cyber security process more efficient and cost effective as well.
Progression:
In the first year I wish to achieve the in-depth knowledge of graphic designing so that I
can understand that how this aspect can influence the cyber security. This knowledge will help
me to improve the existing approaches for overcoming the security concerns.
EXPECTED OUTCOMES
From this research study following outcomes are expected:
It will create more emphasis on the designing approaches so that security risks can be
minimized from ground or designing level itself (Ahram, Karwowski and Taiar, 2018).
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The study will also help to determine the current gaps which are identified promoting
cyber security through graphic designing.
It will provide an analytical description of the wide range of methods which can improve
the security of information systems and can make processes more effective and secure for
the use (Endsley, 2016).
Further the study will also provide foundation for the new trends in graphical design
techniques which not only support the web designing but can also make eliminate the
security vulnerabilities.
The research will help to evaluate the existing challenges and scope of graphical
designing in meeting the security standards related to information technology.
6
cyber security through graphic designing.
It will provide an analytical description of the wide range of methods which can improve
the security of information systems and can make processes more effective and secure for
the use (Endsley, 2016).
Further the study will also provide foundation for the new trends in graphical design
techniques which not only support the web designing but can also make eliminate the
security vulnerabilities.
The research will help to evaluate the existing challenges and scope of graphical
designing in meeting the security standards related to information technology.
6

REFERENCES
Books and Journals
Ahram, T., Karwowski, W. and Taiar, R. eds., 2018. Human Systems Engineering and Design:
Proceedings of the 1st International Conference on Human Systems Engineering and
Design (IHSED2018): Future Trends and Applications, October 25-27, 2018, CHU-
Université de Reims Champagne-Ardenne, France (Vol. 876). Springer.
Das, S., 2016. Social Cybersecurity: Understanding and Leveraging Social Influence to Improve
End-User Security Sensitivity (Doctoral dissertation, University of California, Berkeley).
Endsley, M.R., 2016. Designing for situation awareness: An approach to user-centered design.
CRC press.
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage.
Khaitan, S.K. and McCalley, J.D., 2015. Design techniques and applications of cyberphysical
systems: A survey. IEEE Systems Journal. 9(2). pp.350-365.
Lupton, E. and Phillips, J.C., 2015. Graphic Design: The New Basics: Revised and Expanded.
Chronicle Books.
McCusker, K. and Gunaydin, S., 2015. Research using qualitative, quantitative or mixed
methods and choice based on the research. Perfusion. 30(7). pp.537-542.
McKenna, S., Staheli, D. and Meyer, M., 2015, October. Unlocking user-centered design
methods for building cyber security visualizations. In Visualization for Cyber Security
(VizSec), 2015 IEEE Symposium on (pp. 1-8). IEEE.
Short, K.G., 2016. Critical content analysis as a research methodology. In Critical Content
Analysis of Children's and Young Adult Literature: Reframing Perspective. Taylor and
Francis Inc..
Simonsohn, U., Nelson, L. and Simmons, J., 2017. Research Methodology, Design and
Analysis. Annual Review of Psychology. 1(69).
7
Books and Journals
Ahram, T., Karwowski, W. and Taiar, R. eds., 2018. Human Systems Engineering and Design:
Proceedings of the 1st International Conference on Human Systems Engineering and
Design (IHSED2018): Future Trends and Applications, October 25-27, 2018, CHU-
Université de Reims Champagne-Ardenne, France (Vol. 876). Springer.
Das, S., 2016. Social Cybersecurity: Understanding and Leveraging Social Influence to Improve
End-User Security Sensitivity (Doctoral dissertation, University of California, Berkeley).
Endsley, M.R., 2016. Designing for situation awareness: An approach to user-centered design.
CRC press.
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage.
Khaitan, S.K. and McCalley, J.D., 2015. Design techniques and applications of cyberphysical
systems: A survey. IEEE Systems Journal. 9(2). pp.350-365.
Lupton, E. and Phillips, J.C., 2015. Graphic Design: The New Basics: Revised and Expanded.
Chronicle Books.
McCusker, K. and Gunaydin, S., 2015. Research using qualitative, quantitative or mixed
methods and choice based on the research. Perfusion. 30(7). pp.537-542.
McKenna, S., Staheli, D. and Meyer, M., 2015, October. Unlocking user-centered design
methods for building cyber security visualizations. In Visualization for Cyber Security
(VizSec), 2015 IEEE Symposium on (pp. 1-8). IEEE.
Short, K.G., 2016. Critical content analysis as a research methodology. In Critical Content
Analysis of Children's and Young Adult Literature: Reframing Perspective. Taylor and
Francis Inc..
Simonsohn, U., Nelson, L. and Simmons, J., 2017. Research Methodology, Design and
Analysis. Annual Review of Psychology. 1(69).
7

Staheli, D.P., McKenna, S. and Meyer, M., 2015. Unlocking User-Centered Design Methods for
Building Cyber Security Visualizations. MIT Lincoln Laboratory Lexington United
States.
Zahabi, M., Kaber, D.B. and Swangnetr, M., 2015. Usability and safety in electronic medical
records interface design: a review of recent literature and guideline formulation. Human
factors. 57(5). pp.805-834.
Zhang-Kennedy, L., Chiasson, S. and Biddle, R., 2016. The role of instructional design in
persuasion: A comics approach for improving cybersecurity. International Journal of
Human-Computer Interaction, 32(3), pp.215-257.
Online
Why Is Cyber Security Important?, 2017. [Online]. Accessed through
<https://www.transunion.com/blog/identity-protection/why-is-cyber-security-important>
Improving Cybersecurity: User Accountability and Socio technical Systems, 2017. [Online].
Accessed through <https://www.computer.org/web/computingnow/archive/improving-
cybersecurity-april-2017-introduction>
More proactive, less reactive, 2019. [Online]. Accessed through
<https://www.t-systems.com/de/en/references/use-cases/use-case/cyber-attacks-defense-
239464>
8
Building Cyber Security Visualizations. MIT Lincoln Laboratory Lexington United
States.
Zahabi, M., Kaber, D.B. and Swangnetr, M., 2015. Usability and safety in electronic medical
records interface design: a review of recent literature and guideline formulation. Human
factors. 57(5). pp.805-834.
Zhang-Kennedy, L., Chiasson, S. and Biddle, R., 2016. The role of instructional design in
persuasion: A comics approach for improving cybersecurity. International Journal of
Human-Computer Interaction, 32(3), pp.215-257.
Online
Why Is Cyber Security Important?, 2017. [Online]. Accessed through
<https://www.transunion.com/blog/identity-protection/why-is-cyber-security-important>
Improving Cybersecurity: User Accountability and Socio technical Systems, 2017. [Online].
Accessed through <https://www.computer.org/web/computingnow/archive/improving-
cybersecurity-april-2017-introduction>
More proactive, less reactive, 2019. [Online]. Accessed through
<https://www.t-systems.com/de/en/references/use-cases/use-case/cyber-attacks-defense-
239464>
8
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





