Networking Report: Evaluation and Design of Network for LUCMAT Ltd
VerifiedAdded on 2020/10/05
|27
|5649
|353
Report
AI Summary
This report provides a comprehensive analysis of networking concepts, focusing on the design and implementation of a Local Area Network (LAN) for LUCMAT Ltd. It begins with an introduction to networking, defining key terms and outlining the report's structure. The report explores various network types (LAN, MAN, WAN) and their constraints and benefits, along with network standards. It then delves into network topologies (bus, ring, star, mesh), examining their impact on communication and bandwidth requirements. The operating principles of networking devices such as hubs and switches are discussed in detail. The report addresses the interdependence of hardware and software in a networked system and designs a networked system specifically for LUCMAT Ltd, utilizing star topology. The report also includes feedback from employees to evaluate the design, along with documentation and analysis of test results, concluding with a summary of findings and recommendations. The report emphasizes the importance of protocols in enabling effective networked systems and provides a detailed discussion on the identification of topology protocol in networking systems.

Networking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
P1 Discussion on constraints and benefits of network types and standards................................1
P2 Justify impact of network topology, communication and bandwidth requirements...............2
P3 Discuss operating principles of networking devices and server types...................................3
P4 Discuss interdependence of hardware workstation with networking software......................6
P5 Design of networked system to meet specifications of LUCMAT Ltd..................................7
P6 Test evaluate design so that requirements can be met and analyse feedback from user........8
P8 Documentation and analysis of test results against expected results......................................9
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................11
INTRODUCTION...........................................................................................................................1
P1 Discussion on constraints and benefits of network types and standards................................1
P2 Justify impact of network topology, communication and bandwidth requirements...............2
P3 Discuss operating principles of networking devices and server types...................................3
P4 Discuss interdependence of hardware workstation with networking software......................6
P5 Design of networked system to meet specifications of LUCMAT Ltd..................................7
P6 Test evaluate design so that requirements can be met and analyse feedback from user........8
P8 Documentation and analysis of test results against expected results......................................9
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................11

INTRODUCTION
In the present world, word networking define the accurate and easy exchange of ideas
and useful information between large number of people those share common profession and have
special interest basically in an informal social setting (Bernardos and et. al, 2014). In technical
word, computer networking is referred to the connection of number of devices in appropriate
manner that support to share the effective information and resources of software. This report is
based on LUCMAT Ltd which is an organisation which is opting to use LAN in their working
with IP address 192.168.10.0/24. This report consists of network types and standards, network
topology, their impact and operating principles. Furthermore, there interdependence is is
discussed and network design is provided with feedback from employees related to its working.
P1 Elaborate constraints and benefits of network types as well as standards.
Network refers to accumulation of two or more devices through which communication
can be carried out. These devices and systems are connected with each other by usage of wireless
or physical connections. Communication can occur by usage of emails, shared devices like
printers and shared storage devices. There are different network types but mostly LAN, MAN
and WAN are used for carrying out communication among organisations.
Local Area Network (LAN): It is restricted to specific areas like office, campus or
home. They are generally used as they are easy to implement and troubleshoot. It can be as
simple as connecting two computers for sharing files and storage space among them. They are
connected via Ethernet or Wi-Fi. There coverage area is small nearby 2500 metres or 2 miles
with speed which ranges from 10-1000 Mbps. The major constraint of LAN is its high setup cost,
data security threat, maintenance cost and limited area coverage.
Metropolitan Area Network (MAN): It is a large number which is used to organisations
which are present in same city. They are installed by usage of common carrier; they can be fiber
optic cable or twisted pair. They furnish fast communication by usage of high-speed carriers.
They cover up to 200 km or 100 miles and they have high speed of 100 Mbps. Its constraints are
that in case of wired network, lots of wire or cable is required and it is complex to secure system
from intruders due to graphical regions (De-Marcos and et. al, 2014).
Wide Area Network (WAN): It spans over large locality and connects with other
countries. They can be either private or public. Maintenance and designing of such systems is
1
In the present world, word networking define the accurate and easy exchange of ideas
and useful information between large number of people those share common profession and have
special interest basically in an informal social setting (Bernardos and et. al, 2014). In technical
word, computer networking is referred to the connection of number of devices in appropriate
manner that support to share the effective information and resources of software. This report is
based on LUCMAT Ltd which is an organisation which is opting to use LAN in their working
with IP address 192.168.10.0/24. This report consists of network types and standards, network
topology, their impact and operating principles. Furthermore, there interdependence is is
discussed and network design is provided with feedback from employees related to its working.
P1 Elaborate constraints and benefits of network types as well as standards.
Network refers to accumulation of two or more devices through which communication
can be carried out. These devices and systems are connected with each other by usage of wireless
or physical connections. Communication can occur by usage of emails, shared devices like
printers and shared storage devices. There are different network types but mostly LAN, MAN
and WAN are used for carrying out communication among organisations.
Local Area Network (LAN): It is restricted to specific areas like office, campus or
home. They are generally used as they are easy to implement and troubleshoot. It can be as
simple as connecting two computers for sharing files and storage space among them. They are
connected via Ethernet or Wi-Fi. There coverage area is small nearby 2500 metres or 2 miles
with speed which ranges from 10-1000 Mbps. The major constraint of LAN is its high setup cost,
data security threat, maintenance cost and limited area coverage.
Metropolitan Area Network (MAN): It is a large number which is used to organisations
which are present in same city. They are installed by usage of common carrier; they can be fiber
optic cable or twisted pair. They furnish fast communication by usage of high-speed carriers.
They cover up to 200 km or 100 miles and they have high speed of 100 Mbps. Its constraints are
that in case of wired network, lots of wire or cable is required and it is complex to secure system
from intruders due to graphical regions (De-Marcos and et. al, 2014).
Wide Area Network (WAN): It spans over large locality and connects with other
countries. They can be either private or public. Maintenance and designing of such systems is
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

complex. Data transmission is low as number of devices connected in this type of network is
more. They have unlimited range normally 1000 km but it can be further extended by making
use of repeaters, hubs or any other switching devices. Its speed is slow nearly around 1.5 Mbps
but can vary depending upon wireless technologies. Its constraints comprises of its setup is
complex, expensive and speed is slow. Apart from this its maintenance cost is also high and
security is major concern (Farhady, Lee and Nakao, 2015).
P2 Justify impact of network topology, communication and bandwidth requirements.
A pattern in which nodes (they can be routers, hubs, printers, computers or other devices)
are connected with network like LAN, MAN or WAN through links such as optical fiber, copper
wire or twisted pair. There are different types of network topology, they are explained below
with their impacts on communication and bandwidth:
Bus Topology: In this type every system and network is connected via use of single
cable, it can be either optical fibre or coaxial cable. When there are exact two endpoints then it is
referred to as linear bus topology. Its impact on communication is worst as if cable fails then
interaction will not occur. In terms of bandwidth if there is high traffic then collisions will be
maximised. For this it is mandatory to use protocols such as Slotted Aloha, Pure Aloha, etc.
Ring topology: In this every computer is connected with one another in such a way that
ring is formed. There are exact two neighbours for every device. It is highly expensive. It do not
have negative impact on communication. Reason behind this is that, in this repeaters are used so
that if 50 node sends data to 1st node then it has to go through 49 nodes, so to prevent it and have
effective communications they are being sued. In terms of bandwidth it’s high and can range to
large distances (Franck, Alcatel-Lucent, 2016).
Star topology: In this computers are connected with each other through single hub via a
cable. All the systems are connected via central node i.e. hub. It can have negative impact on
communication as if hub fails then entire network will be stopped. Its bandwidth is dependent on
performance of hub and its capacity to connect to different devices. There is inefficient use of
bandwidth, consider an example like if there is an hub with 8 ports and five devices are
connected with it, then it is ensured that data is sent to right port but rest 3 ports are not used.
Mesh topology: It is a point-to-point connection with other devices or nodes. In this all
nodes are linked with each other. In this communication which occurs is effective as each system
2
more. They have unlimited range normally 1000 km but it can be further extended by making
use of repeaters, hubs or any other switching devices. Its speed is slow nearly around 1.5 Mbps
but can vary depending upon wireless technologies. Its constraints comprises of its setup is
complex, expensive and speed is slow. Apart from this its maintenance cost is also high and
security is major concern (Farhady, Lee and Nakao, 2015).
P2 Justify impact of network topology, communication and bandwidth requirements.
A pattern in which nodes (they can be routers, hubs, printers, computers or other devices)
are connected with network like LAN, MAN or WAN through links such as optical fiber, copper
wire or twisted pair. There are different types of network topology, they are explained below
with their impacts on communication and bandwidth:
Bus Topology: In this type every system and network is connected via use of single
cable, it can be either optical fibre or coaxial cable. When there are exact two endpoints then it is
referred to as linear bus topology. Its impact on communication is worst as if cable fails then
interaction will not occur. In terms of bandwidth if there is high traffic then collisions will be
maximised. For this it is mandatory to use protocols such as Slotted Aloha, Pure Aloha, etc.
Ring topology: In this every computer is connected with one another in such a way that
ring is formed. There are exact two neighbours for every device. It is highly expensive. It do not
have negative impact on communication. Reason behind this is that, in this repeaters are used so
that if 50 node sends data to 1st node then it has to go through 49 nodes, so to prevent it and have
effective communications they are being sued. In terms of bandwidth it’s high and can range to
large distances (Franck, Alcatel-Lucent, 2016).
Star topology: In this computers are connected with each other through single hub via a
cable. All the systems are connected via central node i.e. hub. It can have negative impact on
communication as if hub fails then entire network will be stopped. Its bandwidth is dependent on
performance of hub and its capacity to connect to different devices. There is inefficient use of
bandwidth, consider an example like if there is an hub with 8 ports and five devices are
connected with it, then it is ensured that data is sent to right port but rest 3 ports are not used.
Mesh topology: It is a point-to-point connection with other devices or nodes. In this all
nodes are linked with each other. In this communication which occurs is effective as each system
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

is connected directly with each other. In this case bandwidth is improvised with respect to ring
topology as devices have dedicated links with each other (Grassi and et. al, 2014).
M1 Compare networking principles and how protocols enable effectiveness of networked
system.
Networking refers to practice of transaction of data among nodes over shared medium
within information system. In this computer systems are connected with each other so that
information can be exchanged. Network possesses different principles, they are mentioned
below:
Principle 1: Usage of services for protection of data
In this aspect individual needs to find out who is managing network and with whom network is
shared. This principle aims at development of strategy for a security. It must be clearly informed
to individual’s threat associated with that as well as risk management approach. Information
must be in encrypted form so that performance is not compromised.
Principle 2: Design for interworking and flexibility
It comprises of wide range of network traffic, they have their own proprietary approaches and
standards within network. These principles make it easy to accomplish altering needs in terms of
what is required and when it is needed. Publish DNS records; it will enable wide range of people
to make use of service without any kind of restriction which is based on knowledge of their
name.
Protocols refer to set of rules which enable communication among different systems.
Computer network is dependent on wide range of protocols so that they can work appropriately.
They make sure that different network are utilised appropriately. Like Layer 2 protocol of OSI
model assists in logical and physical connections to source packet to destination by making use
of NIC. Layer 3 IP (internetwork protocol) provides direct packets or datagrams from one
network to other and also routing.
3
topology as devices have dedicated links with each other (Grassi and et. al, 2014).
M1 Compare networking principles and how protocols enable effectiveness of networked
system.
Networking refers to practice of transaction of data among nodes over shared medium
within information system. In this computer systems are connected with each other so that
information can be exchanged. Network possesses different principles, they are mentioned
below:
Principle 1: Usage of services for protection of data
In this aspect individual needs to find out who is managing network and with whom network is
shared. This principle aims at development of strategy for a security. It must be clearly informed
to individual’s threat associated with that as well as risk management approach. Information
must be in encrypted form so that performance is not compromised.
Principle 2: Design for interworking and flexibility
It comprises of wide range of network traffic, they have their own proprietary approaches and
standards within network. These principles make it easy to accomplish altering needs in terms of
what is required and when it is needed. Publish DNS records; it will enable wide range of people
to make use of service without any kind of restriction which is based on knowledge of their
name.
Protocols refer to set of rules which enable communication among different systems.
Computer network is dependent on wide range of protocols so that they can work appropriately.
They make sure that different network are utilised appropriately. Like Layer 2 protocol of OSI
model assists in logical and physical connections to source packet to destination by making use
of NIC. Layer 3 IP (internetwork protocol) provides direct packets or datagrams from one
network to other and also routing.
3

D1 Identification of topology protocol in networking system.
LUCMAT Ltd. can make use of star topology to connect departmental LAN's for
establishing connection between switches while terminating routers and firewalls. Star topology
provides easy expansion which provides fast communication and is simple to implement.
Furthermore, by this they can establish effective connection with other departments. But the
major drawback is that a single point failure for central devices that means that if central device
either switch or hub will fail than entire network will fail.
(Source: What Is Star Topology? Advantages And Disadvantages Of A Star Topology, 2019)
P3 Discuss operating principles of networking devices and server types.
Network devices refer to components which are used for connecting electronic devices or
computers. They are also used for setting up LAN by making use of routers, hub and switches.
There are various network devices like modem, hubs, switches, repeaters and many more.
Operating principles of some network devices is provided below:
Hub: It refers to central connection point for devices within network. Basically they are
used for connecting segments of LAN. It works on half duplex communication mode. Its
operating principle with example is shown below:
4
Illustration 1: Star Topology
LUCMAT Ltd. can make use of star topology to connect departmental LAN's for
establishing connection between switches while terminating routers and firewalls. Star topology
provides easy expansion which provides fast communication and is simple to implement.
Furthermore, by this they can establish effective connection with other departments. But the
major drawback is that a single point failure for central devices that means that if central device
either switch or hub will fail than entire network will fail.
(Source: What Is Star Topology? Advantages And Disadvantages Of A Star Topology, 2019)
P3 Discuss operating principles of networking devices and server types.
Network devices refer to components which are used for connecting electronic devices or
computers. They are also used for setting up LAN by making use of routers, hub and switches.
There are various network devices like modem, hubs, switches, repeaters and many more.
Operating principles of some network devices is provided below:
Hub: It refers to central connection point for devices within network. Basically they are
used for connecting segments of LAN. It works on half duplex communication mode. Its
operating principle with example is shown below:
4
Illustration 1: Star Topology
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
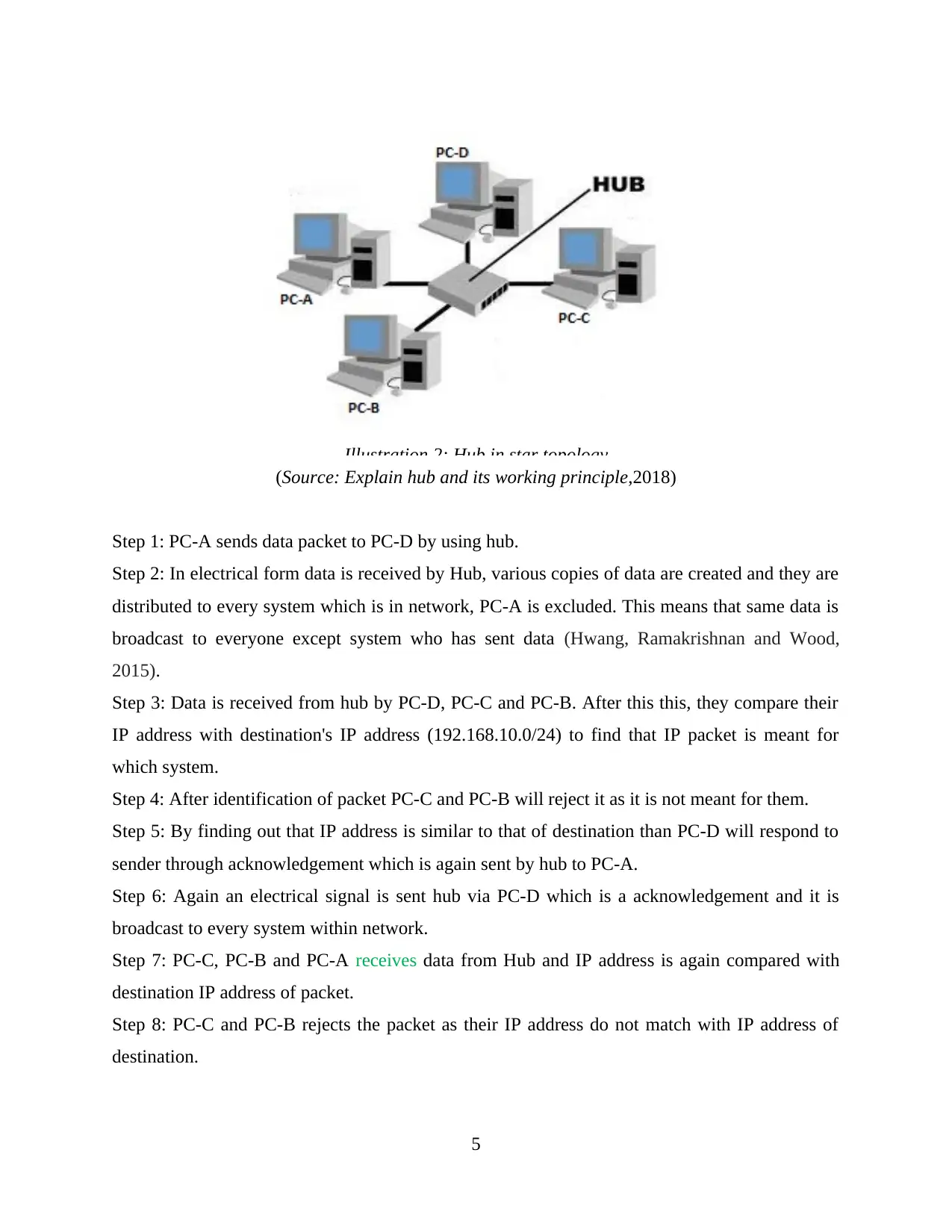
(Source: Explain hub and its working principle,2018)
Step 1: PC-A sends data packet to PC-D by using hub.
Step 2: In electrical form data is received by Hub, various copies of data are created and they are
distributed to every system which is in network, PC-A is excluded. This means that same data is
broadcast to everyone except system who has sent data (Hwang, Ramakrishnan and Wood,
2015).
Step 3: Data is received from hub by PC-D, PC-C and PC-B. After this this, they compare their
IP address with destination's IP address (192.168.10.0/24) to find that IP packet is meant for
which system.
Step 4: After identification of packet PC-C and PC-B will reject it as it is not meant for them.
Step 5: By finding out that IP address is similar to that of destination than PC-D will respond to
sender through acknowledgement which is again sent by hub to PC-A.
Step 6: Again an electrical signal is sent hub via PC-D which is a acknowledgement and it is
broadcast to every system within network.
Step 7: PC-C, PC-B and PC-A receives data from Hub and IP address is again compared with
destination IP address of packet.
Step 8: PC-C and PC-B rejects the packet as their IP address do not match with IP address of
destination.
5
Illustration 2: Hub in star topology
Step 1: PC-A sends data packet to PC-D by using hub.
Step 2: In electrical form data is received by Hub, various copies of data are created and they are
distributed to every system which is in network, PC-A is excluded. This means that same data is
broadcast to everyone except system who has sent data (Hwang, Ramakrishnan and Wood,
2015).
Step 3: Data is received from hub by PC-D, PC-C and PC-B. After this this, they compare their
IP address with destination's IP address (192.168.10.0/24) to find that IP packet is meant for
which system.
Step 4: After identification of packet PC-C and PC-B will reject it as it is not meant for them.
Step 5: By finding out that IP address is similar to that of destination than PC-D will respond to
sender through acknowledgement which is again sent by hub to PC-A.
Step 6: Again an electrical signal is sent hub via PC-D which is a acknowledgement and it is
broadcast to every system within network.
Step 7: PC-C, PC-B and PC-A receives data from Hub and IP address is again compared with
destination IP address of packet.
Step 8: PC-C and PC-B rejects the packet as their IP address do not match with IP address of
destination.
5
Illustration 2: Hub in star topology
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Step 9: PC-A will find that their address is similar, then they will receive acknowledgement
packet.
Switch: It is a high speed networking device which receive data packet and redirects
them LAN (Johannisson, 2017). They possess capability of unicast (interaction between single
sender and receiver). Its operating principles are provided below with example:
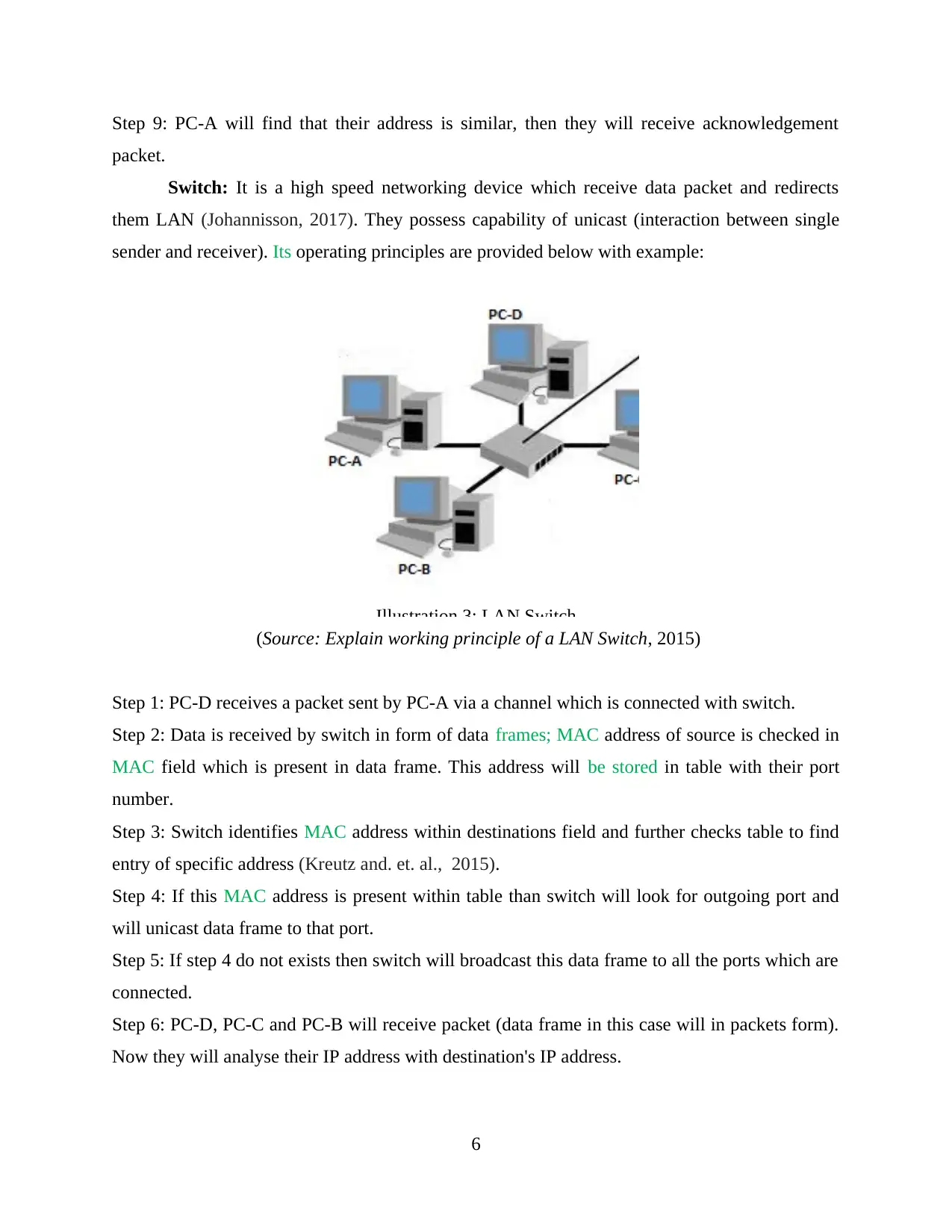
(Source: Explain working principle of a LAN Switch, 2015)
Step 1: PC-D receives a packet sent by PC-A via a channel which is connected with switch.
Step 2: Data is received by switch in form of data frames; MAC address of source is checked in
MAC field which is present in data frame. This address will be stored in table with their port
number.
Step 3: Switch identifies MAC address within destinations field and further checks table to find
entry of specific address (Kreutz and. et. al., 2015).
Step 4: If this MAC address is present within table than switch will look for outgoing port and
will unicast data frame to that port.
Step 5: If step 4 do not exists then switch will broadcast this data frame to all the ports which are
connected.
Step 6: PC-D, PC-C and PC-B will receive packet (data frame in this case will in packets form).
Now they will analyse their IP address with destination's IP address.
6
Illustration 3: LAN Switch
packet.
Switch: It is a high speed networking device which receive data packet and redirects
them LAN (Johannisson, 2017). They possess capability of unicast (interaction between single
sender and receiver). Its operating principles are provided below with example:
(Source: Explain working principle of a LAN Switch, 2015)
Step 1: PC-D receives a packet sent by PC-A via a channel which is connected with switch.
Step 2: Data is received by switch in form of data frames; MAC address of source is checked in
MAC field which is present in data frame. This address will be stored in table with their port
number.
Step 3: Switch identifies MAC address within destinations field and further checks table to find
entry of specific address (Kreutz and. et. al., 2015).
Step 4: If this MAC address is present within table than switch will look for outgoing port and
will unicast data frame to that port.
Step 5: If step 4 do not exists then switch will broadcast this data frame to all the ports which are
connected.
Step 6: PC-D, PC-C and PC-B will receive packet (data frame in this case will in packets form).
Now they will analyse their IP address with destination's IP address.
6
Illustration 3: LAN Switch

Step 7: PC-C and PC-B will reject packet as their IP address will not match as it is not meant for
them.
Step 8: PC-A will receive a acknowledgement packet through switch which is sent by PC-D.
Step 9: Acknowledgement data frame from PC-D is received by switch, MAC address is checked
within data frames field and this address is stored in address table along with its port number.
Step 10: Switch identify MAC address of destination from data frame and it will verify it in
address table to ensure its entry. Switch has already stored MAC address of PC-A, now
acknowledgement packet will be unicast.
Step 11: Once switch knows MAC address of all nodes, then data frames will be unicast to nodes
for whom it is meant.
Server is a device or computer program which furnish functionality to other devices and
programs. Basically they provide information to other systems which are present within network.
There are different servers which are meant to perform specific activities like DNS, DHCP, mail
server and many more (Parker, Verizon Patent and Licensing Inc, 2016). E-mail server with their
operating principles along with example is described:
E-mail server, makes use of client server approach. Here client indicates mail
application/mailer/mail program and server is device which manages emails. An example is
illustrated which includes sending, receiving and knowing of operating principles of email
system:
Step 1: Consider that person A sends message to B via email.
Step 2: By making use of mail client or mailer program, A compose message and clicks on send.
Step 3: This message is dispatched to mail server of B by SMTP (simple mail transfer protocol).
Step 4: Mail server stores this message in disk space (mail spool) which has been assigned to B.
Step 5: Consider that person B is running on POP (post office protocol) client and knows ways in
which interaction with mail server of B will occur (Raleigh and et. al, 2016).
Step 6: POP server of poll will be periodically checked to identify that email has received by B.
As A has sent email to B, so it is forwarded over network of B. This will be stored on PC of B.
7
them.
Step 8: PC-A will receive a acknowledgement packet through switch which is sent by PC-D.
Step 9: Acknowledgement data frame from PC-D is received by switch, MAC address is checked
within data frames field and this address is stored in address table along with its port number.
Step 10: Switch identify MAC address of destination from data frame and it will verify it in
address table to ensure its entry. Switch has already stored MAC address of PC-A, now
acknowledgement packet will be unicast.
Step 11: Once switch knows MAC address of all nodes, then data frames will be unicast to nodes
for whom it is meant.
Server is a device or computer program which furnish functionality to other devices and
programs. Basically they provide information to other systems which are present within network.
There are different servers which are meant to perform specific activities like DNS, DHCP, mail
server and many more (Parker, Verizon Patent and Licensing Inc, 2016). E-mail server with their
operating principles along with example is described:
E-mail server, makes use of client server approach. Here client indicates mail
application/mailer/mail program and server is device which manages emails. An example is
illustrated which includes sending, receiving and knowing of operating principles of email
system:
Step 1: Consider that person A sends message to B via email.
Step 2: By making use of mail client or mailer program, A compose message and clicks on send.
Step 3: This message is dispatched to mail server of B by SMTP (simple mail transfer protocol).
Step 4: Mail server stores this message in disk space (mail spool) which has been assigned to B.
Step 5: Consider that person B is running on POP (post office protocol) client and knows ways in
which interaction with mail server of B will occur (Raleigh and et. al, 2016).
Step 6: POP server of poll will be periodically checked to identify that email has received by B.
As A has sent email to B, so it is forwarded over network of B. This will be stored on PC of B.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
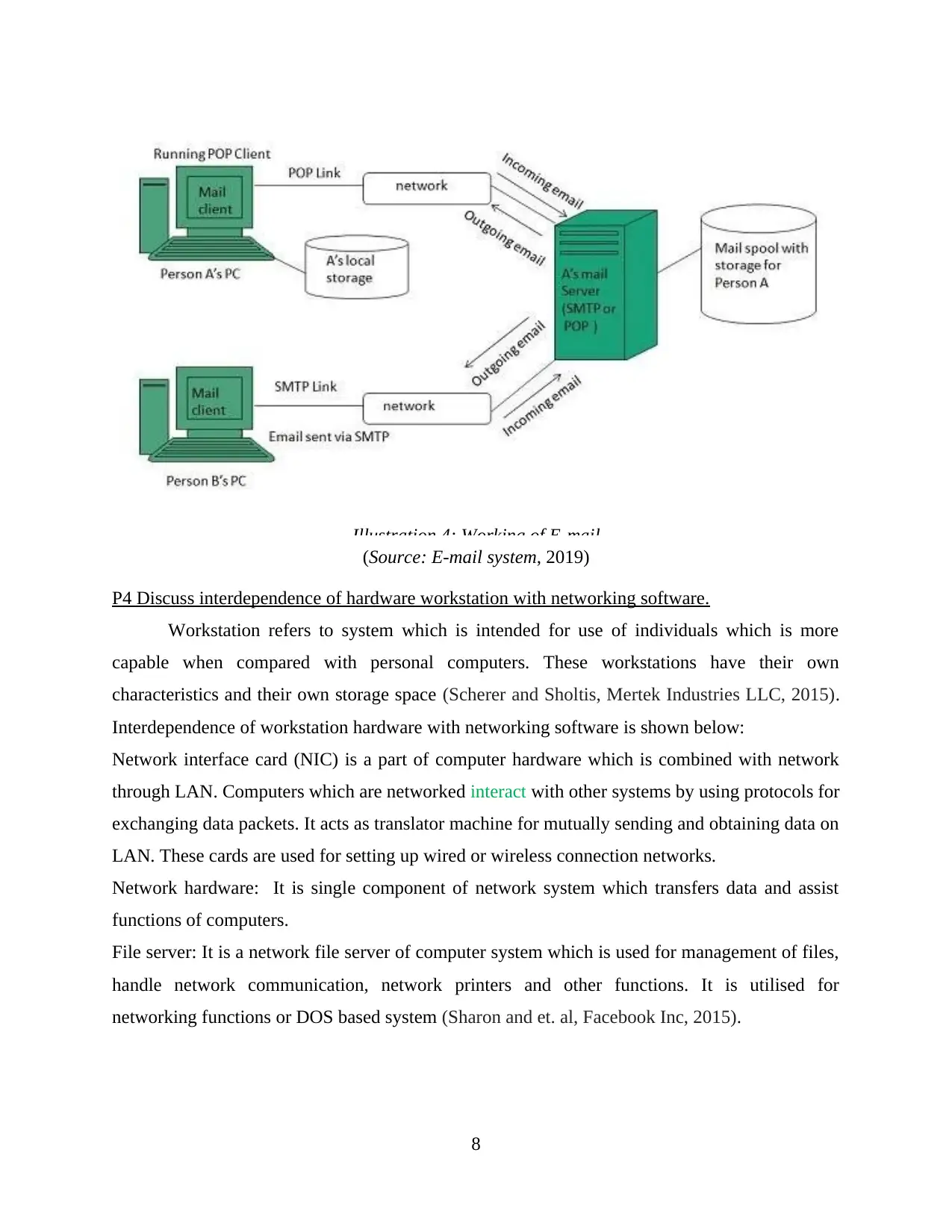
(Source: E-mail system, 2019)
P4 Discuss interdependence of hardware workstation with networking software.
Workstation refers to system which is intended for use of individuals which is more
capable when compared with personal computers. These workstations have their own
characteristics and their own storage space (Scherer and Sholtis, Mertek Industries LLC, 2015).
Interdependence of workstation hardware with networking software is shown below:
Network interface card (NIC) is a part of computer hardware which is combined with network
through LAN. Computers which are networked interact with other systems by using protocols for
exchanging data packets. It acts as translator machine for mutually sending and obtaining data on
LAN. These cards are used for setting up wired or wireless connection networks.
Network hardware: It is single component of network system which transfers data and assist
functions of computers.
File server: It is a network file server of computer system which is used for management of files,
handle network communication, network printers and other functions. It is utilised for
networking functions or DOS based system (Sharon and et. al, Facebook Inc, 2015).
8
Illustration 4: Working of E-mail
P4 Discuss interdependence of hardware workstation with networking software.
Workstation refers to system which is intended for use of individuals which is more
capable when compared with personal computers. These workstations have their own
characteristics and their own storage space (Scherer and Sholtis, Mertek Industries LLC, 2015).
Interdependence of workstation hardware with networking software is shown below:
Network interface card (NIC) is a part of computer hardware which is combined with network
through LAN. Computers which are networked interact with other systems by using protocols for
exchanging data packets. It acts as translator machine for mutually sending and obtaining data on
LAN. These cards are used for setting up wired or wireless connection networks.
Network hardware: It is single component of network system which transfers data and assist
functions of computers.
File server: It is a network file server of computer system which is used for management of files,
handle network communication, network printers and other functions. It is utilised for
networking functions or DOS based system (Sharon and et. al, Facebook Inc, 2015).
8
Illustration 4: Working of E-mail
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking operating system: It is loaded into hard disk of servers along with user utilities and
system management tools. NOS boots and other servers come in control when systems are
started.
Network cabling: When workstations, NIC and servers are placed then network cabling will be
used to network all components. These cables are: coaxial cable, twisted pair, fiber optics cable.
They are interdependent on one another for carrying out network functions appropriately.
M2 Exploration of range of servers and which server is used by LUCMAT Ltd with respect to
cost and performance optimisation.
There are different computer servers which can be used by organisation depending upon
their requirements. They have opted to make use of Web, email and DNS server for working in
suitable manner and also carry out their operations in enhanced way. Mail server will assist them
to have interaction with different departments present within organisation which will have
enhanced impact on their performance. Domain name server (DNS) is backbone of networking
communication. If DNS fails than IP address cannot be found and internet services cannot be
used. It assists in moving, adding and changing internet services by making its use. Furthermore,
web server can be used by them to store their web site files as well as broadcast them to visitor's
file. They are not cost effective but still they will provide LUCMAT Ltd the enhanced value to
carry out their services.
P5 Design of networked system to meet specifications of LUCMAT Ltd.
There network is designed by making use of Wi-Fi and Ethernet network technologies.
Apart from this star and bus topologies are used by LUCMAT Ltd. These components are
connected with each other through inexpensive and Ethernet technology. Their departments are
facilitated by usage of Wi-Fi technology as more efficient workstations are used and are
controlled by management of each department (HR, design,sales and R&D). Then these all
departments are connected with each other so that they can share resources as well as
information via internet and this information can be accessed by employees from anywhere (Xia
and et. Al, 2015).
9
system management tools. NOS boots and other servers come in control when systems are
started.
Network cabling: When workstations, NIC and servers are placed then network cabling will be
used to network all components. These cables are: coaxial cable, twisted pair, fiber optics cable.
They are interdependent on one another for carrying out network functions appropriately.
M2 Exploration of range of servers and which server is used by LUCMAT Ltd with respect to
cost and performance optimisation.
There are different computer servers which can be used by organisation depending upon
their requirements. They have opted to make use of Web, email and DNS server for working in
suitable manner and also carry out their operations in enhanced way. Mail server will assist them
to have interaction with different departments present within organisation which will have
enhanced impact on their performance. Domain name server (DNS) is backbone of networking
communication. If DNS fails than IP address cannot be found and internet services cannot be
used. It assists in moving, adding and changing internet services by making its use. Furthermore,
web server can be used by them to store their web site files as well as broadcast them to visitor's
file. They are not cost effective but still they will provide LUCMAT Ltd the enhanced value to
carry out their services.
P5 Design of networked system to meet specifications of LUCMAT Ltd.
There network is designed by making use of Wi-Fi and Ethernet network technologies.
Apart from this star and bus topologies are used by LUCMAT Ltd. These components are
connected with each other through inexpensive and Ethernet technology. Their departments are
facilitated by usage of Wi-Fi technology as more efficient workstations are used and are
controlled by management of each department (HR, design,sales and R&D). Then these all
departments are connected with each other so that they can share resources as well as
information via internet and this information can be accessed by employees from anywhere (Xia
and et. Al, 2015).
9
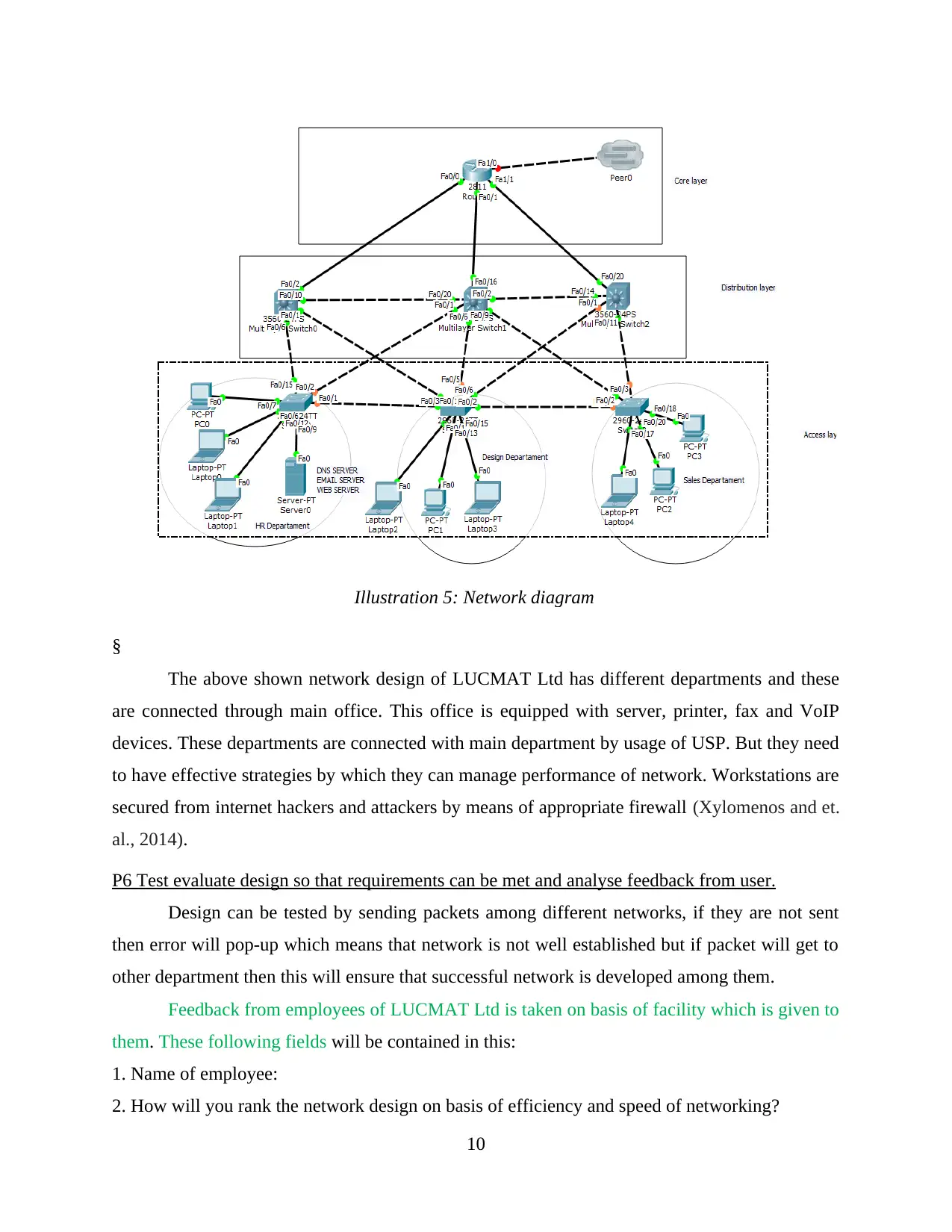
Illustration 5: Network diagram
§
The above shown network design of LUCMAT Ltd has different departments and these
are connected through main office. This office is equipped with server, printer, fax and VoIP
devices. These departments are connected with main department by usage of USP. But they need
to have effective strategies by which they can manage performance of network. Workstations are
secured from internet hackers and attackers by means of appropriate firewall (Xylomenos and et.
al., 2014).
P6 Test evaluate design so that requirements can be met and analyse feedback from user.
Design can be tested by sending packets among different networks, if they are not sent
then error will pop-up which means that network is not well established but if packet will get to
other department then this will ensure that successful network is developed among them.
Feedback from employees of LUCMAT Ltd is taken on basis of facility which is given to
them. These following fields will be contained in this:
1. Name of employee:
2. How will you rank the network design on basis of efficiency and speed of networking?
10
§
The above shown network design of LUCMAT Ltd has different departments and these
are connected through main office. This office is equipped with server, printer, fax and VoIP
devices. These departments are connected with main department by usage of USP. But they need
to have effective strategies by which they can manage performance of network. Workstations are
secured from internet hackers and attackers by means of appropriate firewall (Xylomenos and et.
al., 2014).
P6 Test evaluate design so that requirements can be met and analyse feedback from user.
Design can be tested by sending packets among different networks, if they are not sent
then error will pop-up which means that network is not well established but if packet will get to
other department then this will ensure that successful network is developed among them.
Feedback from employees of LUCMAT Ltd is taken on basis of facility which is given to
them. These following fields will be contained in this:
1. Name of employee:
2. How will you rank the network design on basis of efficiency and speed of networking?
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





