Software Development Life Cycle and Security
VerifiedAdded on 2020/04/21
|16
|3652
|74
AI Summary
This assignment delves into the Software Development Life Cycle (SDLC) and its crucial role in building secure software. It examines various SDLC models, including Waterfall and Agile, highlighting the importance of incorporating security considerations at each stage. The discussion emphasizes techniques for preventing vulnerabilities like command injection attacks and the significance of continuous testing and monitoring throughout the development process.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

1SOFTWARE ENGINEERING
SOFTWARE ENGINEERING
Name of the Student
Name of the University
Author Note
SOFTWARE ENGINEERING
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2SOFTWARE ENGINEERING
Table of Contents
Introduction................................................................................................................................3
Importance of system safety.......................................................................................................3
Safety critical activity................................................................................................................4
Activity 1: Develop a primary hazard list..................................................................................4
Implications followed by software development team..............................................................5
Use Case - software development as an application..................................................................8
Software model..........................................................................................................................8
Attack.......................................................................................................................................11
Services to comprehend the LDAP injection...........................................................................12
Prevent LDAP Injection with Veracode..................................................................................13
Types of attack.........................................................................................................................13
Conclusion................................................................................................................................14
Bibliography.............................................................................................................................15
Table of Contents
Introduction................................................................................................................................3
Importance of system safety.......................................................................................................3
Safety critical activity................................................................................................................4
Activity 1: Develop a primary hazard list..................................................................................4
Implications followed by software development team..............................................................5
Use Case - software development as an application..................................................................8
Software model..........................................................................................................................8
Attack.......................................................................................................................................11
Services to comprehend the LDAP injection...........................................................................12
Prevent LDAP Injection with Veracode..................................................................................13
Types of attack.........................................................................................................................13
Conclusion................................................................................................................................14
Bibliography.............................................................................................................................15

3SOFTWARE ENGINEERING
Introduction
Since the implementation of the digital computers, system safety practitioners have
been very much concerned with the implementation of the computers performing safety. In
the early age, engineers and programmers restricted themselves from performing in high risk
and hazardous operation where the intervention of human was nearly deemed1. The branch of
engineering which deals with the development of the software is known as software
engineering. This is done using specific science principles, procedures and methods. The
basic outcome of the process is an efficient and reliable software product.
The main aim of the report is to take into consideration there different life cycles
models of which two describes the security issue, which is involved in it. The risk factors,
which are associated with the process, is taken in to consideration. The threat assessment is
done for a particular task with it a taxonomy of attacks are taken into consideration.
Importance of system safety
Failure of a system to perform function which is intended to be performed by the system
The software performs the function that is not required at that time.
The software possesses sequential problem and timing
The software possesses timing or problem, which is sequential i.e. failing to ensure that
mainly two things can happen at the same time at different places or in a particular order.
2.
The common factors, which are associated with the software falling, are as follows:
1 SearchSecurity, 'Security In The Software Development Life Cycle' (SearchSecurity, 2017)
<http://searchsecurity.techtarget.com/tip/Security-in-the-software-development-life-cycle> accessed 8
November 2017.
2 Insights.sei.cmu.edu, 'The SPRUCE Series: Recommended Practices In The Software Development
Of Safety-Critical Systems' (Insights.sei.cmu.edu, 2017) <https://insights.sei.cmu.edu/sei_blog/2015/06/the-
spruce-series-recommended-practices-in-the-software-development-of-safety-critical-systems.html> accessed 8
November 2017.
Introduction
Since the implementation of the digital computers, system safety practitioners have
been very much concerned with the implementation of the computers performing safety. In
the early age, engineers and programmers restricted themselves from performing in high risk
and hazardous operation where the intervention of human was nearly deemed1. The branch of
engineering which deals with the development of the software is known as software
engineering. This is done using specific science principles, procedures and methods. The
basic outcome of the process is an efficient and reliable software product.
The main aim of the report is to take into consideration there different life cycles
models of which two describes the security issue, which is involved in it. The risk factors,
which are associated with the process, is taken in to consideration. The threat assessment is
done for a particular task with it a taxonomy of attacks are taken into consideration.
Importance of system safety
Failure of a system to perform function which is intended to be performed by the system
The software performs the function that is not required at that time.
The software possesses sequential problem and timing
The software possesses timing or problem, which is sequential i.e. failing to ensure that
mainly two things can happen at the same time at different places or in a particular order.
2.
The common factors, which are associated with the software falling, are as follows:
1 SearchSecurity, 'Security In The Software Development Life Cycle' (SearchSecurity, 2017)
<http://searchsecurity.techtarget.com/tip/Security-in-the-software-development-life-cycle> accessed 8
November 2017.
2 Insights.sei.cmu.edu, 'The SPRUCE Series: Recommended Practices In The Software Development
Of Safety-Critical Systems' (Insights.sei.cmu.edu, 2017) <https://insights.sei.cmu.edu/sei_blog/2015/06/the-
spruce-series-recommended-practices-in-the-software-development-of-safety-critical-systems.html> accessed 8
November 2017.

4SOFTWARE ENGINEERING
Specification error: specification error mainly includes improper statement, omitted code,
incorrect specification and their requirement.
Design and coding error: these errors are mainly understood by the programmers and can
directly result from the error in the specification. This is mainly caused due to poor
structure in the technique with aspect to the code.
Hardware /computer included error: this error is not so common error as taking into
account other errors. This error mainly includes random power supply transients,
computer function that mainly transform one or more bit in the computer word that
intentionally change the meaning of the software instruction.
Safety critical activity
Activity 1: Develop a primary hazard list
The primary hazard list (PHL) is mainly generated at the start of each of the analysis,
which is related to the hazardous activity. It can be considered as a list of anything that can
be directly analysed that can be thought of anything which can go wrong. It provides a list of
hazards that are associated with the concept, which is under consideration. The contract can
be taken to be under consideration to involve investigation of future selected hazardous c
characteristics, which are identified by the PHL to determine their main significance. This
can be used in making series decision, which can range from “should the program continue”
to the concept of shaping the post contractual requirement related to safety. Either the host
employee or a contactor may generate the PHL. 3
3 Doss, Osama, and Tim P. Kelly. "Challenges and Opportunities in Agile Development in Safety
Critical Systems: A Survey." ACM SIGSOFT Software Engineering Notes 41.2 (2016): 30-31.
Specification error: specification error mainly includes improper statement, omitted code,
incorrect specification and their requirement.
Design and coding error: these errors are mainly understood by the programmers and can
directly result from the error in the specification. This is mainly caused due to poor
structure in the technique with aspect to the code.
Hardware /computer included error: this error is not so common error as taking into
account other errors. This error mainly includes random power supply transients,
computer function that mainly transform one or more bit in the computer word that
intentionally change the meaning of the software instruction.
Safety critical activity
Activity 1: Develop a primary hazard list
The primary hazard list (PHL) is mainly generated at the start of each of the analysis,
which is related to the hazardous activity. It can be considered as a list of anything that can
be directly analysed that can be thought of anything which can go wrong. It provides a list of
hazards that are associated with the concept, which is under consideration. The contract can
be taken to be under consideration to involve investigation of future selected hazardous c
characteristics, which are identified by the PHL to determine their main significance. This
can be used in making series decision, which can range from “should the program continue”
to the concept of shaping the post contractual requirement related to safety. Either the host
employee or a contactor may generate the PHL. 3
3 Doss, Osama, and Tim P. Kelly. "Challenges and Opportunities in Agile Development in Safety
Critical Systems: A Survey." ACM SIGSOFT Software Engineering Notes 41.2 (2016): 30-31.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

5SOFTWARE ENGINEERING
The PHL list, which is related to the hazard mainly, require special emphasis on the
design or the hazardous areas where in depth analysis need to done. Example of the use of
PHL include basically
Implications followed by software development team
Software Development’s working environment: flexibility, distributed and dynamic
The fluctuation, acceleration of the cooperating partner’s distribution of the
production sites and the complexity relating to the supply chain call for finding ways to build
the aspect of the continuity into the software development processes. In order to guarantee
the developers, have a shared vision, companies must invest in a proper way and significantly
in order to achieve proper communication which enables the team member to build strong
relationship to be clear about the concept of the security relevant information. Companies are
mainly advised to establish relationship, which are for the long run and on the other hand
establish relation, which are trustable.
Widespread adaptation of agile software development
Agile software development is sometimes referred to as a way to adapt to a rapidly
environment changing. As team and the team roles become flexible, the agile software
development raises the level of the information technology security. The latter must not be
overburdened with the aspect of the security. While the agile software development is about
the concept of adapting to rapidly changing circumstances which is forced into the scene of
the market. This makes it mandatory on the part of preserving the knowledge and to trace the
decision that majorly go into the system construction. Last but not the least, the concept of
the usability should be taken very much seriously as the factors, which are related to the
security aspect.
Code generation and assembly of (prefabricated) code
The PHL list, which is related to the hazard mainly, require special emphasis on the
design or the hazardous areas where in depth analysis need to done. Example of the use of
PHL include basically
Implications followed by software development team
Software Development’s working environment: flexibility, distributed and dynamic
The fluctuation, acceleration of the cooperating partner’s distribution of the
production sites and the complexity relating to the supply chain call for finding ways to build
the aspect of the continuity into the software development processes. In order to guarantee
the developers, have a shared vision, companies must invest in a proper way and significantly
in order to achieve proper communication which enables the team member to build strong
relationship to be clear about the concept of the security relevant information. Companies are
mainly advised to establish relationship, which are for the long run and on the other hand
establish relation, which are trustable.
Widespread adaptation of agile software development
Agile software development is sometimes referred to as a way to adapt to a rapidly
environment changing. As team and the team roles become flexible, the agile software
development raises the level of the information technology security. The latter must not be
overburdened with the aspect of the security. While the agile software development is about
the concept of adapting to rapidly changing circumstances which is forced into the scene of
the market. This makes it mandatory on the part of preserving the knowledge and to trace the
decision that majorly go into the system construction. Last but not the least, the concept of
the usability should be taken very much seriously as the factors, which are related to the
security aspect.
Code generation and assembly of (prefabricated) code

6SOFTWARE ENGINEERING
There is certain democratization issue about the concept of the software development,
which allows the developers with the formal education about the concept of the coding. In
order to ensure coding quality by the nonprofessional, the aspect of the security must be
factored into the self-learning platform and the generation of the code. Taking into
consideration the concept of the software development relating to the industry, automated
security features into the integrated development environment, libraries and the framework
must generate the security aspect. The latter devices must be equipped with the tools that
mainly allow for the testing and means of generating secured building blocks. Developers
should always be equipped with tools that mainly allow testing and the generation of secured
building blocks. The developers must keep a very much consistent relationship between the
source code level and the modelling and to make in front decision about which framework is
to be selected. The developers should have the knowledge to check these types of code for
the purpose of the security, whereas companies may consider formulating sharing policies.
As the phenomenon which is related to the crowdsourcing software development which gains
a foothold, a research is called upon to investigate implications related to the security4.
Compositional modularization and system
Modularization and compositional entails a paradigm which is profound as aspect to
the security. Study participants mainly mentioned a range of measures that most of the
company may involve in order to increase the probability of producing secure compositional
system. The range of measures may include activity such as no integration related to the
external components as a black box. Rigorous testing of the security aspect and raising
security relevant parameters, safeguarding and checking the aspect of the compatibility of the
in house code with the external code, reducing the surface of the attack by deactivating the
4 McGregor, John D., and Roselane S. Silva. "Building Safety-Critical Systems Through Architecture-
Based Systematic Reuse." Mastering Scale and Complexity in Software Reuse: 16th International Conference
on Software Reuse, ICSR 2017, Salvador, Brazil, May 29-31, 2017, Proceedings. Vol. 10221. Springer, 2017.
There is certain democratization issue about the concept of the software development,
which allows the developers with the formal education about the concept of the coding. In
order to ensure coding quality by the nonprofessional, the aspect of the security must be
factored into the self-learning platform and the generation of the code. Taking into
consideration the concept of the software development relating to the industry, automated
security features into the integrated development environment, libraries and the framework
must generate the security aspect. The latter devices must be equipped with the tools that
mainly allow for the testing and means of generating secured building blocks. Developers
should always be equipped with tools that mainly allow testing and the generation of secured
building blocks. The developers must keep a very much consistent relationship between the
source code level and the modelling and to make in front decision about which framework is
to be selected. The developers should have the knowledge to check these types of code for
the purpose of the security, whereas companies may consider formulating sharing policies.
As the phenomenon which is related to the crowdsourcing software development which gains
a foothold, a research is called upon to investigate implications related to the security4.
Compositional modularization and system
Modularization and compositional entails a paradigm which is profound as aspect to
the security. Study participants mainly mentioned a range of measures that most of the
company may involve in order to increase the probability of producing secure compositional
system. The range of measures may include activity such as no integration related to the
external components as a black box. Rigorous testing of the security aspect and raising
security relevant parameters, safeguarding and checking the aspect of the compatibility of the
in house code with the external code, reducing the surface of the attack by deactivating the
4 McGregor, John D., and Roselane S. Silva. "Building Safety-Critical Systems Through Architecture-
Based Systematic Reuse." Mastering Scale and Complexity in Software Reuse: 16th International Conference
on Software Reuse, ICSR 2017, Salvador, Brazil, May 29-31, 2017, Proceedings. Vol. 10221. Springer, 2017.

7SOFTWARE ENGINEERING
components which are external and whose functionality is not in use. Taking into account the
future, it will be very much desirable to dispose of the formal specification of the
characteristics of the components and automatable procedures related to the testing and
specifications of the valid indicators concerning the dynamic and the static attribute of the
compositional system.
Distributed system and intensified (cross domain) networking5
There are many similar issues when it comes to distributed system: there is always a
demand to develop the techniques, which mainly allow one to directly determine the level of
the security at the run time of a distributed system. Taking into consideration the concept of
the cloud computing – one specific form related to the distributed system – technique to
separate sensitive information for the non-sensitive ones as well as solving liability and legal
issue. Furthermost as the distributed system from the different domain may network sub
systems, an amalgamation of the technique and the prospective from the different domains is
important. The aforementioned domains may involve security and safety realms, due to this
factor the aspect of the security and the safety mechanism must be explored. The
convergence of the world of information and the physical world renders it very much
necessary to invest in the research and the development on the security and the safety at ones.
5 Sit.fraunhofer.de, 'Cite A Website - Cite This For Me' (Sit.fraunhofer.de, 2017)
<https://www.sit.fraunhofer.de/fileadmin/dokumente/studien_und_technical_reports/SoftwareDevelopment-
Fraunhofer_SIT.pdf> accessed 8 November 2017.
components which are external and whose functionality is not in use. Taking into account the
future, it will be very much desirable to dispose of the formal specification of the
characteristics of the components and automatable procedures related to the testing and
specifications of the valid indicators concerning the dynamic and the static attribute of the
compositional system.
Distributed system and intensified (cross domain) networking5
There are many similar issues when it comes to distributed system: there is always a
demand to develop the techniques, which mainly allow one to directly determine the level of
the security at the run time of a distributed system. Taking into consideration the concept of
the cloud computing – one specific form related to the distributed system – technique to
separate sensitive information for the non-sensitive ones as well as solving liability and legal
issue. Furthermost as the distributed system from the different domain may network sub
systems, an amalgamation of the technique and the prospective from the different domains is
important. The aforementioned domains may involve security and safety realms, due to this
factor the aspect of the security and the safety mechanism must be explored. The
convergence of the world of information and the physical world renders it very much
necessary to invest in the research and the development on the security and the safety at ones.
5 Sit.fraunhofer.de, 'Cite A Website - Cite This For Me' (Sit.fraunhofer.de, 2017)
<https://www.sit.fraunhofer.de/fileadmin/dokumente/studien_und_technical_reports/SoftwareDevelopment-
Fraunhofer_SIT.pdf> accessed 8 November 2017.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
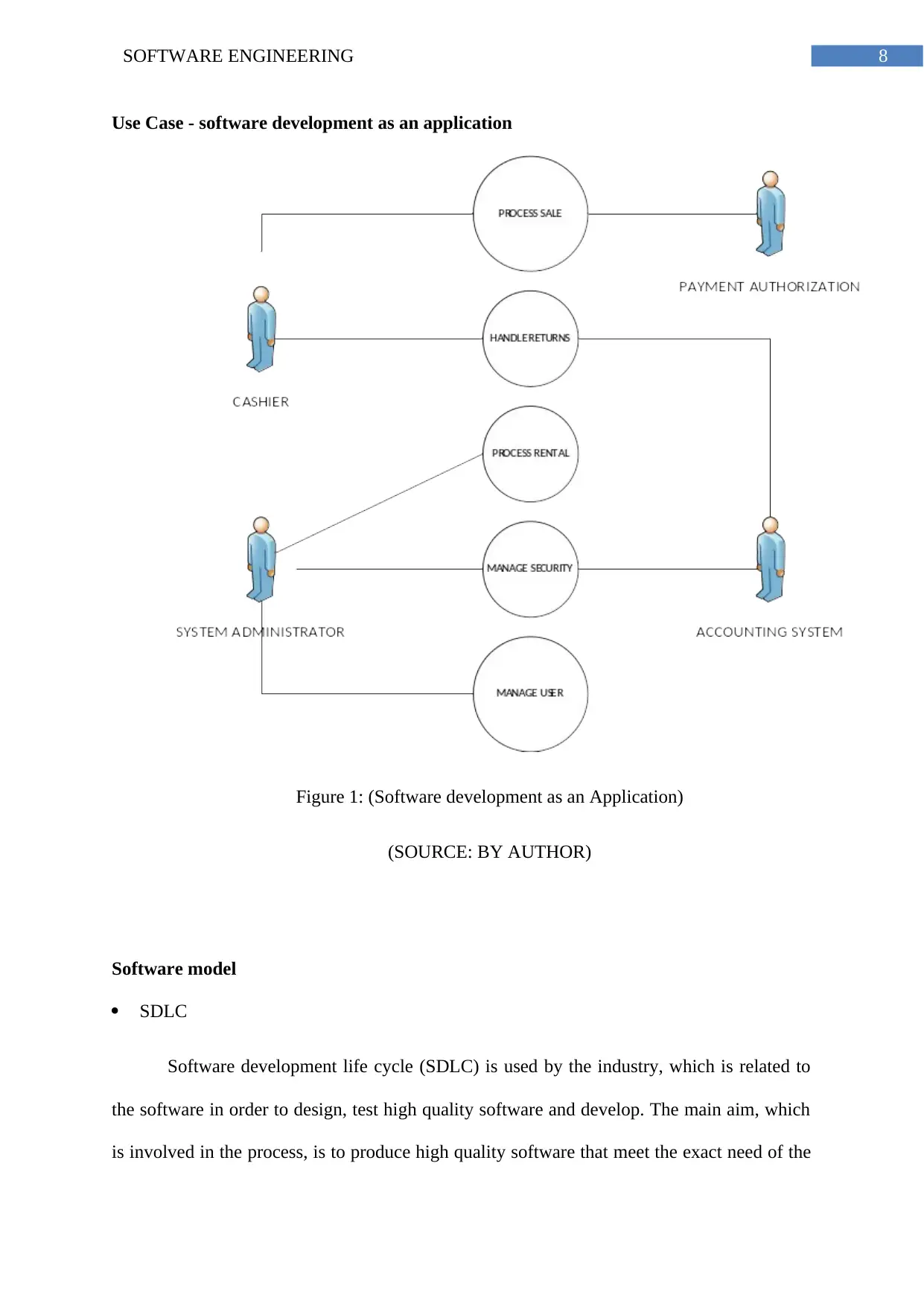
8SOFTWARE ENGINEERING
Use Case - software development as an application
Figure 1: (Software development as an Application)
(SOURCE: BY AUTHOR)
Software model
SDLC
Software development life cycle (SDLC) is used by the industry, which is related to
the software in order to design, test high quality software and develop. The main aim, which
is involved in the process, is to produce high quality software that meet the exact need of the
Use Case - software development as an application
Figure 1: (Software development as an Application)
(SOURCE: BY AUTHOR)
Software model
SDLC
Software development life cycle (SDLC) is used by the industry, which is related to
the software in order to design, test high quality software and develop. The main aim, which
is involved in the process, is to produce high quality software that meet the exact need of the

9SOFTWARE ENGINEERING
customer, reach the completion of any project within the framework of time expected and
within the budget estimation.
o SDLC is an acronym of the software development life cycle.
o It is also known as software development process
o The SDLC is a defining framework defining the task performed at each of the steps in the
process of the software development.
o ISO/IEC 12207 is considered as an international standard related to the software life cycle
processes. It defines a set of standard that defines all the task which is required for the
process of the development and the maintenance.
The SDLC is followed for a software project, within the framework of software
organisation. The process consists of detail planning describing how to develop, replace,
maintain and alter or enhance the factor of software quality6.
Waterfall model
The waterfall model can be considered as the first process model. It is a linear sequential
life cycle model. This model is very much easy to understand and very easy to use and
each of the step has to completed before proceeding towards the next step and the
overlapping of the phase is not acquired. The waterfall development process is a
sequential model which is basically linear.
Requirement analysis and gathering: All the possible requirement of the system, which is
to be developed, are mainly captured and documented in a requirement document
specification.
6 SDLC Quick Guide, 'SDLC Quick Guide' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_quick_guide.htm> accessed 9 November 2017.
customer, reach the completion of any project within the framework of time expected and
within the budget estimation.
o SDLC is an acronym of the software development life cycle.
o It is also known as software development process
o The SDLC is a defining framework defining the task performed at each of the steps in the
process of the software development.
o ISO/IEC 12207 is considered as an international standard related to the software life cycle
processes. It defines a set of standard that defines all the task which is required for the
process of the development and the maintenance.
The SDLC is followed for a software project, within the framework of software
organisation. The process consists of detail planning describing how to develop, replace,
maintain and alter or enhance the factor of software quality6.
Waterfall model
The waterfall model can be considered as the first process model. It is a linear sequential
life cycle model. This model is very much easy to understand and very easy to use and
each of the step has to completed before proceeding towards the next step and the
overlapping of the phase is not acquired. The waterfall development process is a
sequential model which is basically linear.
Requirement analysis and gathering: All the possible requirement of the system, which is
to be developed, are mainly captured and documented in a requirement document
specification.
6 SDLC Quick Guide, 'SDLC Quick Guide' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_quick_guide.htm> accessed 9 November 2017.

10SOFTWARE ENGINEERING
System design: the basic requirement of the system is studied in this area. The main aim
of this phase is to specify the system requirement and the hardware requirement and helps
in overall defining of the system’s architecture.
Implementation: After achieving the system input, the development of the system is done
in small amount and can be referred to as units. This is mainly integrated in the next
phase. Each of the phases in this schedule are tested and developed in accordance to their
functionality, which can be referred to as unit testing.
Testing and integration: Ones the non-functional and the functional requirement testing is
completed. The product is deployed in the environment of the customer or released into
the market area.
Maintenance: There can be few issues that can come up with the environments of the
product. To fix those patches, issue is released. The enhancement sector is also taken into
account by implementing new up gradation in the software. Maintenance is mainly done
to deliver the changes in the customer environment7.
Agile software development
Agile SDLC model is a basic model of incremental process with the focus on the process
of customer satisfaction and adaptability of the software product. Agile method breaks the
main product into small incremental builds. This build is mainly provided in the phase of the
iteration. Each of the iteration mainly lasts for about one to three weeks. The iterations
involve cross-functional team who is basically involved in various aspects such as
Planning: In this phase the overall planning of the project is done. In this step the overall
planning involving the concept of project, the overall budget of the project and the estimated
time framework is taken into consideration.
7 SDLC Waterfall Model, 'SDLC Waterfall Model' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_waterfall_model.htm> accessed 9 November 2017.
System design: the basic requirement of the system is studied in this area. The main aim
of this phase is to specify the system requirement and the hardware requirement and helps
in overall defining of the system’s architecture.
Implementation: After achieving the system input, the development of the system is done
in small amount and can be referred to as units. This is mainly integrated in the next
phase. Each of the phases in this schedule are tested and developed in accordance to their
functionality, which can be referred to as unit testing.
Testing and integration: Ones the non-functional and the functional requirement testing is
completed. The product is deployed in the environment of the customer or released into
the market area.
Maintenance: There can be few issues that can come up with the environments of the
product. To fix those patches, issue is released. The enhancement sector is also taken into
account by implementing new up gradation in the software. Maintenance is mainly done
to deliver the changes in the customer environment7.
Agile software development
Agile SDLC model is a basic model of incremental process with the focus on the process
of customer satisfaction and adaptability of the software product. Agile method breaks the
main product into small incremental builds. This build is mainly provided in the phase of the
iteration. Each of the iteration mainly lasts for about one to three weeks. The iterations
involve cross-functional team who is basically involved in various aspects such as
Planning: In this phase the overall planning of the project is done. In this step the overall
planning involving the concept of project, the overall budget of the project and the estimated
time framework is taken into consideration.
7 SDLC Waterfall Model, 'SDLC Waterfall Model' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_waterfall_model.htm> accessed 9 November 2017.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

11SOFTWARE ENGINEERING
o Requirement analysis: the business requirement is taken into consideration in this part.
This phase is focus point of the project managers and the stakeholders.
o Design: In this phase the system and the design of the software is prepared from the
requirement specification, which is taken into consideration in the first phase. This phase
is very much helpful in defining the overall architecture of the system.
o Coding: In this phase the coding of the project is done. The main start of the project’s
implementation starts from this point onward.
o Unit testing: In this phase, the testing of the software is done in order to check for bugs
and error in the coding sector.
o Acceptance testing: In this phase the acceptance of the coding towards the system is done.
This phase mainly includes the bug’s detection, which is very much importance before
the product is launched into the market.
The principle, which is associated with the agile manifesto, are:
o Individuals and interactions: In the agile development, self-motivation and organisation
are important. As the interaction like the pair programming and the co-location.
o Working software: demo working of any software is the best communication mean with
the customer to understand their main requirement instead of putting full dedication
towards the documentation8.
o Customer collaboration: At the beginning, the full requirement cannot be gathered. This
can be due to various factors, continuous customer interaction that is very much important
to get the requirement of the product.
o Response to change: Agile development is mainly focused on quick response to change
and development, which is continuous9.
8 Coleman, Gerry. "Agile Software Development." Software Quality Professional 19.1 (2016).
9 SDLC Agile Model, 'SDLC Agile Model' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_agile_model.htm> accessed 9 November 2017.
o Requirement analysis: the business requirement is taken into consideration in this part.
This phase is focus point of the project managers and the stakeholders.
o Design: In this phase the system and the design of the software is prepared from the
requirement specification, which is taken into consideration in the first phase. This phase
is very much helpful in defining the overall architecture of the system.
o Coding: In this phase the coding of the project is done. The main start of the project’s
implementation starts from this point onward.
o Unit testing: In this phase, the testing of the software is done in order to check for bugs
and error in the coding sector.
o Acceptance testing: In this phase the acceptance of the coding towards the system is done.
This phase mainly includes the bug’s detection, which is very much importance before
the product is launched into the market.
The principle, which is associated with the agile manifesto, are:
o Individuals and interactions: In the agile development, self-motivation and organisation
are important. As the interaction like the pair programming and the co-location.
o Working software: demo working of any software is the best communication mean with
the customer to understand their main requirement instead of putting full dedication
towards the documentation8.
o Customer collaboration: At the beginning, the full requirement cannot be gathered. This
can be due to various factors, continuous customer interaction that is very much important
to get the requirement of the product.
o Response to change: Agile development is mainly focused on quick response to change
and development, which is continuous9.
8 Coleman, Gerry. "Agile Software Development." Software Quality Professional 19.1 (2016).
9 SDLC Agile Model, 'SDLC Agile Model' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_agile_model.htm> accessed 9 November 2017.

12SOFTWARE ENGINEERING
Attack
The LDAP injection is an attack, which is initiated on web application where the
hackers place a malicious code in the field of user input. Just like the Java SQL injection or
the .NET SQL injection, an LAPD injection can directly lead to information theft, session
hacking, browser, decrement of the website or sometimes worst. In a LDAP injection, it uses
client-supplied data in the LDAP (lightweight directory access protocol) statements without
removing the potential code, which is harmful from the request10. When the concept of the
sanitize of the user supplied input is not considered properly hackers are able to change the
construction of the LDAP statement which will run with the permission which is as same as
the components that execute the command. For example, the attacker might use the LDAP
injection code with the main motive to see the password as well as the username, which is
assigned for that particular system, or to add names as their system administrator. A
successful LDAP injection can result in a security issue, which can cause a major threat in the
field of breach, causing headaches, reputation damage and losses relating to finance. If th e
permission is granted in the right way with aspect of modify, query and remove anything
inside the LDAP tree, there can be a huge loss in the security issue in this field.
Services to comprehend the LDAP injection
Veracode Greenlight: This is a service that scans in background as developers write the
code and provide the immediate feedback, which prevents error in the coding part.
Static analysis: A service, which mainly scans binaries and identifies security flaws in a
variety of major language and framework in order to prevent LDAP injection in web
application and websites.
Web application scanning: This is mainly a tool of identifying the LDAP Injection in
web applications and websites.
10 Nguyen-Tuong, Anh, et al. "Methods, systems and computer readable media for detecting command
injection attacks." U.S. Patent No. 9,635,033. 25 Apr. 2017.
Attack
The LDAP injection is an attack, which is initiated on web application where the
hackers place a malicious code in the field of user input. Just like the Java SQL injection or
the .NET SQL injection, an LAPD injection can directly lead to information theft, session
hacking, browser, decrement of the website or sometimes worst. In a LDAP injection, it uses
client-supplied data in the LDAP (lightweight directory access protocol) statements without
removing the potential code, which is harmful from the request10. When the concept of the
sanitize of the user supplied input is not considered properly hackers are able to change the
construction of the LDAP statement which will run with the permission which is as same as
the components that execute the command. For example, the attacker might use the LDAP
injection code with the main motive to see the password as well as the username, which is
assigned for that particular system, or to add names as their system administrator. A
successful LDAP injection can result in a security issue, which can cause a major threat in the
field of breach, causing headaches, reputation damage and losses relating to finance. If th e
permission is granted in the right way with aspect of modify, query and remove anything
inside the LDAP tree, there can be a huge loss in the security issue in this field.
Services to comprehend the LDAP injection
Veracode Greenlight: This is a service that scans in background as developers write the
code and provide the immediate feedback, which prevents error in the coding part.
Static analysis: A service, which mainly scans binaries and identifies security flaws in a
variety of major language and framework in order to prevent LDAP injection in web
application and websites.
Web application scanning: This is mainly a tool of identifying the LDAP Injection in
web applications and websites.
10 Nguyen-Tuong, Anh, et al. "Methods, systems and computer readable media for detecting command
injection attacks." U.S. Patent No. 9,635,033. 25 Apr. 2017.

13SOFTWARE ENGINEERING
Software composition analysis: for the scanning of the source code in order to search
vulnerability.
Vendor application testing security: this is done for the concept of evaluating the
security risk in the third party application11.
Prevent LDAP Injection with Veracode
Veracode is one of the leaders in the security application related to the cloud
technology. It provides comprehensive SaaS based testing service, which is on demand to
combat the LDAP injections, and other threats, which are related to, reflected XSS AND
SQL attacks. Veracode testing service can be integrated into each and every step of the
development of the software lifecycle (SDLC) and the agile process of testing. Helping
organisations and the developers to improve security in the application while reducing the
aspect of the cost and accelerating the development related to the time framework.
Preventing LDAP injection mainly require programming which is defensive,
sophisticated validation of the input, dynamic check and the source of the code analysis
which is static 12.
Types of attack
The attack types, which are related to the LDAP attack, are as follows:
ARP Spoofing: ARP spoofing is a type of attack in which an actor, which is malicious,
sends falsified ARP (Address Resolution Protocol) message over a network, which is
local.
Botnet: A botnet is a compromised computer network under the control of a malicious
actor. Each of the individual device in a botnet is referred to as a bot.
11 Thome, Julian, et al. "Security slicing for auditing common injection vulnerabilities." Journal of
Systems and Software(2017).
12 Perkins, Jeff, et al. "AutoRand: Automatic Keyword Randomization to Prevent Injection
Attacks." Detection of Intrusions and Malware, and Vulnerability Assessment. Springer International
Publishing, 2016. 37-57.
Software composition analysis: for the scanning of the source code in order to search
vulnerability.
Vendor application testing security: this is done for the concept of evaluating the
security risk in the third party application11.
Prevent LDAP Injection with Veracode
Veracode is one of the leaders in the security application related to the cloud
technology. It provides comprehensive SaaS based testing service, which is on demand to
combat the LDAP injections, and other threats, which are related to, reflected XSS AND
SQL attacks. Veracode testing service can be integrated into each and every step of the
development of the software lifecycle (SDLC) and the agile process of testing. Helping
organisations and the developers to improve security in the application while reducing the
aspect of the cost and accelerating the development related to the time framework.
Preventing LDAP injection mainly require programming which is defensive,
sophisticated validation of the input, dynamic check and the source of the code analysis
which is static 12.
Types of attack
The attack types, which are related to the LDAP attack, are as follows:
ARP Spoofing: ARP spoofing is a type of attack in which an actor, which is malicious,
sends falsified ARP (Address Resolution Protocol) message over a network, which is
local.
Botnet: A botnet is a compromised computer network under the control of a malicious
actor. Each of the individual device in a botnet is referred to as a bot.
11 Thome, Julian, et al. "Security slicing for auditing common injection vulnerabilities." Journal of
Systems and Software(2017).
12 Perkins, Jeff, et al. "AutoRand: Automatic Keyword Randomization to Prevent Injection
Attacks." Detection of Intrusions and Malware, and Vulnerability Assessment. Springer International
Publishing, 2016. 37-57.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

14SOFTWARE ENGINEERING
Cache poisoning: cache poisoning is a type if attack, which mainly involve corrupted
data, which is inserted into the system cache database of the domain name system (DNS)
name server. The domain system is a system that is associated with the domain name with
the internet protocol address.
Key loggers: key loggers or the key stroke is software program or the hardware device
that mainly track the activity of a keyboard. Key loggers is a form of spyware where a
computer user are basically unaware of their action are being tracked13.
Conclusion
It can be concluded from the report that the software development process has mainly
steps involved in it. For a successful implementation of a software product, the overall
requirement has to be gathered before the actual phase of the development starts. The
implications that are followed by a software development team is of high importance due to
the factor that is directly involve the overall working of the project which is undertaken and is
under process. Few models can be taken into consideration in order to implement a software
development like the waterfall model, which plots down the basic process, which are
involved in the software life cycle. There is other model also for example agile model and
SDLC.
13 Nguyen-Tuong, Anh, et al. "Methods, systems and computer readable media for detecting command
injection attacks." U.S. Patent No. 9,635,033. 25 Apr. 2017.
Cache poisoning: cache poisoning is a type if attack, which mainly involve corrupted
data, which is inserted into the system cache database of the domain name system (DNS)
name server. The domain system is a system that is associated with the domain name with
the internet protocol address.
Key loggers: key loggers or the key stroke is software program or the hardware device
that mainly track the activity of a keyboard. Key loggers is a form of spyware where a
computer user are basically unaware of their action are being tracked13.
Conclusion
It can be concluded from the report that the software development process has mainly
steps involved in it. For a successful implementation of a software product, the overall
requirement has to be gathered before the actual phase of the development starts. The
implications that are followed by a software development team is of high importance due to
the factor that is directly involve the overall working of the project which is undertaken and is
under process. Few models can be taken into consideration in order to implement a software
development like the waterfall model, which plots down the basic process, which are
involved in the software life cycle. There is other model also for example agile model and
SDLC.
13 Nguyen-Tuong, Anh, et al. "Methods, systems and computer readable media for detecting command
injection attacks." U.S. Patent No. 9,635,033. 25 Apr. 2017.

15SOFTWARE ENGINEERING
Bibliography
Coleman, Gerry. "Agile Software Development." Software Quality Professional 19.1 (2016).
Doss, Osama, and Tim P. Kelly. "Challenges and Opportunities in Agile Development in
Safety Critical Systems: A Survey." ACM SIGSOFT Software Engineering Notes 41.2
(2016): 30-31.
Insights.sei.cmu.edu, 'The SPRUCE Series: Recommended Practices In The Software
Development Of Safety-Critical Systems' (Insights.sei.cmu.edu, 2017)
<https://insights.sei.cmu.edu/sei_blog/2015/06/the-spruce-series-recommended-practices-in-
the-software-development-of-safety-critical-systems.html> accessed 8 November 2017.
McGregor, John D., and Roselane S. Silva. "Building Safety-Critical Systems Through
Architecture-Based Systematic Reuse." Mastering Scale and Complexity in Software Reuse:
16th International Conference on Software Reuse, ICSR 2017, Salvador, Brazil, May 29-31,
2017, Proceedings. Vol. 10221. Springer, 2017.
Nguyen-Tuong, Anh, et al. "Methods, systems and computer readable media for detecting
command injection attacks." U.S. Patent No. 9,635,033. 25 Apr. 2017.
Nguyen-Tuong, Anh, et al. "Methods, systems and computer readable media for detecting
command injection attacks." U.S. Patent No. 9,635,033. 25 Apr. 2017.
Perkins, Jeff, et al. "AutoRand: Automatic Keyword Randomization to Prevent Injection
Attacks." Detection of Intrusions and Malware, and Vulnerability Assessment. Springer
International Publishing, 2016. 37-57.
SDLC Agile Model, 'SDLC Agile Model' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_agile_model.htm> accessed 9 November 2017
Bibliography
Coleman, Gerry. "Agile Software Development." Software Quality Professional 19.1 (2016).
Doss, Osama, and Tim P. Kelly. "Challenges and Opportunities in Agile Development in
Safety Critical Systems: A Survey." ACM SIGSOFT Software Engineering Notes 41.2
(2016): 30-31.
Insights.sei.cmu.edu, 'The SPRUCE Series: Recommended Practices In The Software
Development Of Safety-Critical Systems' (Insights.sei.cmu.edu, 2017)
<https://insights.sei.cmu.edu/sei_blog/2015/06/the-spruce-series-recommended-practices-in-
the-software-development-of-safety-critical-systems.html> accessed 8 November 2017.
McGregor, John D., and Roselane S. Silva. "Building Safety-Critical Systems Through
Architecture-Based Systematic Reuse." Mastering Scale and Complexity in Software Reuse:
16th International Conference on Software Reuse, ICSR 2017, Salvador, Brazil, May 29-31,
2017, Proceedings. Vol. 10221. Springer, 2017.
Nguyen-Tuong, Anh, et al. "Methods, systems and computer readable media for detecting
command injection attacks." U.S. Patent No. 9,635,033. 25 Apr. 2017.
Nguyen-Tuong, Anh, et al. "Methods, systems and computer readable media for detecting
command injection attacks." U.S. Patent No. 9,635,033. 25 Apr. 2017.
Perkins, Jeff, et al. "AutoRand: Automatic Keyword Randomization to Prevent Injection
Attacks." Detection of Intrusions and Malware, and Vulnerability Assessment. Springer
International Publishing, 2016. 37-57.
SDLC Agile Model, 'SDLC Agile Model' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_agile_model.htm> accessed 9 November 2017

16SOFTWARE ENGINEERING
SDLC Quick Guide, 'SDLC Quick Guide' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_quick_guide.htm> accessed 9 November 2017.
SDLC Waterfall Model, 'SDLC Waterfall Model' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_waterfall_model.htm> accessed 9 November
2017.
SearchSecurity, 'Security In The Software Development Life Cycle' (SearchSecurity, 2017)
<http://searchsecurity.techtarget.com/tip/Security-in-the-software-development-life-cycle>
accessed 8 November 2017.
Sit.fraunhofer.de, 'Cite A Website - Cite This For Me' (Sit.fraunhofer.de, 2017)
<https://www.sit.fraunhofer.de/fileadmin/dokumente/studien_und_technical_reports/
SoftwareDevelopment-Fraunhofer_SIT.pdf> accessed 8 November 2017.
Thome, Julian, et al. "Security slicing for auditing common injection vulnerabilities." Journal
of Systems and Software(2017).
SDLC Quick Guide, 'SDLC Quick Guide' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_quick_guide.htm> accessed 9 November 2017.
SDLC Waterfall Model, 'SDLC Waterfall Model' (www.tutorialspoint.com, 2017)
<https://www.tutorialspoint.com/sdlc/sdlc_waterfall_model.htm> accessed 9 November
2017.
SearchSecurity, 'Security In The Software Development Life Cycle' (SearchSecurity, 2017)
<http://searchsecurity.techtarget.com/tip/Security-in-the-software-development-life-cycle>
accessed 8 November 2017.
Sit.fraunhofer.de, 'Cite A Website - Cite This For Me' (Sit.fraunhofer.de, 2017)
<https://www.sit.fraunhofer.de/fileadmin/dokumente/studien_und_technical_reports/
SoftwareDevelopment-Fraunhofer_SIT.pdf> accessed 8 November 2017.
Thome, Julian, et al. "Security slicing for auditing common injection vulnerabilities." Journal
of Systems and Software(2017).
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





