Internet of Things: Survey and Applications
VerifiedAdded on 2020/05/28
|14
|1583
|77
AI Summary
This assignment delves into the Internet of Things (IoT), providing a detailed survey of enabling technologies, communication protocols, and diverse applications. It examines the transformative impact of IoT across various sectors, highlighting key trends, challenges, and future directions. The assignment encourages critical analysis and synthesis of information from scholarly sources to demonstrate a thorough understanding of IoT concepts and their implications.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: WIRELESS NETWORKING
WIRELESS NETWORKING
Name of the Student
Name of the University
Author Note
WIRELESS NETWORKING
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2WIRELESS NETWORKING
Table of Contents
Part 1..........................................................................................................................................3
Part 3..........................................................................................................................................4
Part 4 (Power Point Presentation)..............................................................................................5
References................................................................................................................................11
Table of Contents
Part 1..........................................................................................................................................3
Part 3..........................................................................................................................................4
Part 4 (Power Point Presentation)..............................................................................................5
References................................................................................................................................11
3WIRELESS NETWORKING
Part 1
Channel reuse feature can be configures to operate in the following three modes
Dynamic: In this type the clear Channel Assessment threshold are based on the load of
the channel and directly takes into account the location of the associated client.
Static: In this type, the mode of the coverage is based upon the Channel assessment
(CCA) threshold. In the static mode of operation, the CCA (Channel assessment
threshold) is adjusted according to configured power level of transmission.
Disable: this mode of operation does not support the tuning of the CCA threshold detect
(Jun et al., 2016)
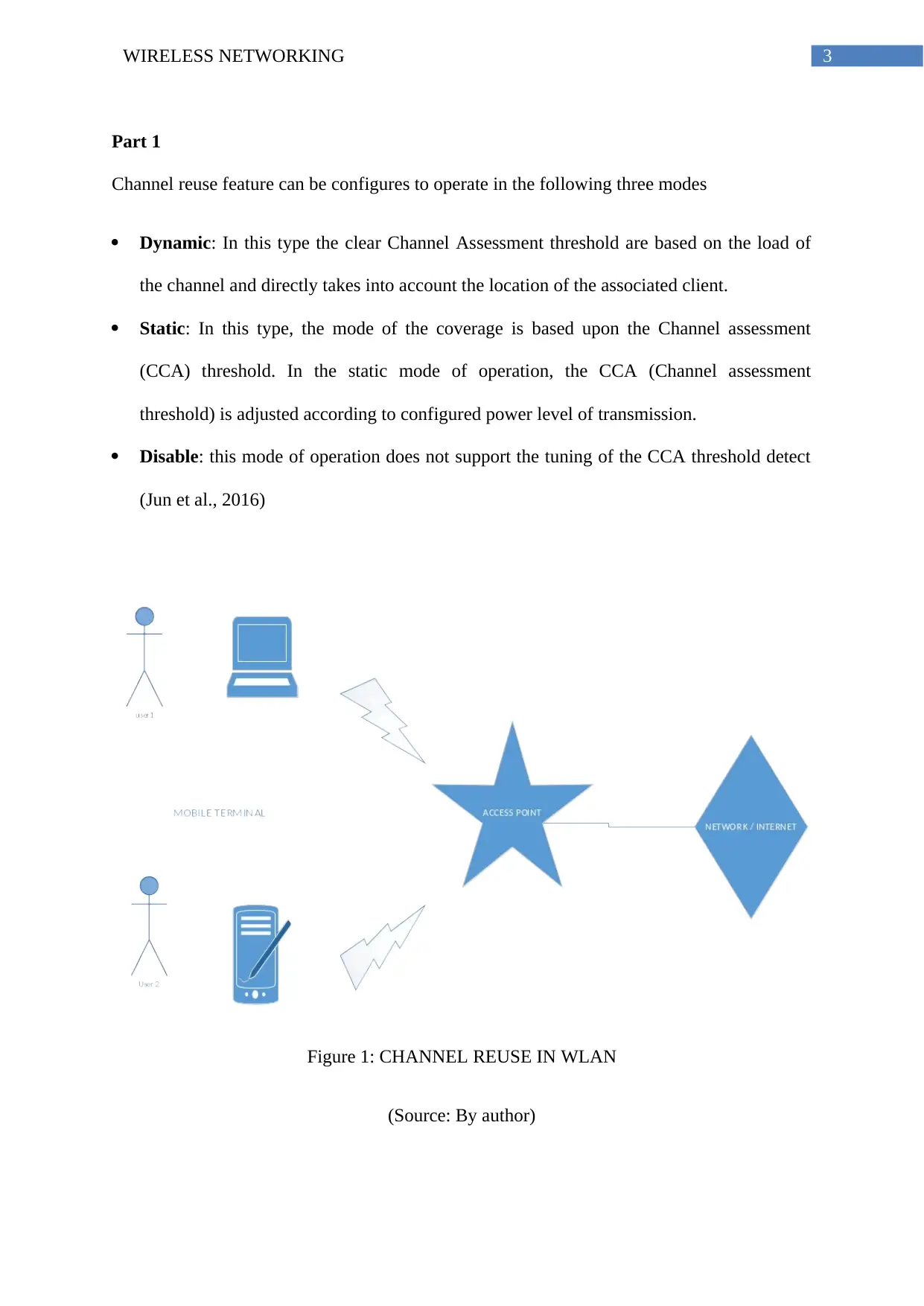
Figure 1: CHANNEL REUSE IN WLAN
(Source: By author)
Part 1
Channel reuse feature can be configures to operate in the following three modes
Dynamic: In this type the clear Channel Assessment threshold are based on the load of
the channel and directly takes into account the location of the associated client.
Static: In this type, the mode of the coverage is based upon the Channel assessment
(CCA) threshold. In the static mode of operation, the CCA (Channel assessment
threshold) is adjusted according to configured power level of transmission.
Disable: this mode of operation does not support the tuning of the CCA threshold detect
(Jun et al., 2016)
Figure 1: CHANNEL REUSE IN WLAN
(Source: By author)

4WIRELESS NETWORKING
The above diagram explains the WLAN technology and its reuse in the mobile phone
network. It states that the access point can be accessed from different point and by multiple
user at a common time framework.
Part 2
The concept of the WLAN provides many advantages in the sector of cost, productivity and
convenience but it can be stated that the radio waves, which is used in the technology, can
create a risk (Katar et al., 2014). The risk is associated with the concept of the network being
hacked. The security challenges of two WLAN technology are:
Denial of service: This type of attack mainly consist of the hackers flooding the website
or a network with invalid or valid messages with directly affect the network resource
availability. The concept of the WLAN can be stated to be very much vulnerable to the
attack related to Denial of service. This is due to the factor that the WLAN have relatively
less bit rates, which can be easily be overwhelmed and make them open to the attack
related to the denial of service. The use of transceiver, which are powerful enough to
generate the radio interference unable the WLAN to communicate using the concept of
radio path.
Session hacking and spoofing: The attack directly result in the attackers gaining the
access to the data and the resources, which are over the network by means of assuming a
valid user identification. This mainly happens due to the factor that 802.11 network does
not validate or authenticate the address which is related to the source which is the MAC
(Medium Access Control) address relating to the frame. The attacker by means of taking
advantage of the loophole can spoof the MAC address and hijack the sessions. The
remedy of the attack is spoofing elimination, access control mechanism and
authentication in a proper way.
The above diagram explains the WLAN technology and its reuse in the mobile phone
network. It states that the access point can be accessed from different point and by multiple
user at a common time framework.
Part 2
The concept of the WLAN provides many advantages in the sector of cost, productivity and
convenience but it can be stated that the radio waves, which is used in the technology, can
create a risk (Katar et al., 2014). The risk is associated with the concept of the network being
hacked. The security challenges of two WLAN technology are:
Denial of service: This type of attack mainly consist of the hackers flooding the website
or a network with invalid or valid messages with directly affect the network resource
availability. The concept of the WLAN can be stated to be very much vulnerable to the
attack related to Denial of service. This is due to the factor that the WLAN have relatively
less bit rates, which can be easily be overwhelmed and make them open to the attack
related to the denial of service. The use of transceiver, which are powerful enough to
generate the radio interference unable the WLAN to communicate using the concept of
radio path.
Session hacking and spoofing: The attack directly result in the attackers gaining the
access to the data and the resources, which are over the network by means of assuming a
valid user identification. This mainly happens due to the factor that 802.11 network does
not validate or authenticate the address which is related to the source which is the MAC
(Medium Access Control) address relating to the frame. The attacker by means of taking
advantage of the loophole can spoof the MAC address and hijack the sessions. The
remedy of the attack is spoofing elimination, access control mechanism and
authentication in a proper way.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

5WIRELESS NETWORKING
Part 3
The internet of things is playing vital role in the sphere of life. It can be stated that the
internet of things is and would be playing a dominant role in the future. According to the
concept of implementation of internet of things in the aspect of business it can be widely be
used to gain business efficiency and improvement in the sector of customer satisfaction and
operations. I have come across more of the sectors other than the business orientation that can
benefit from the concept like the transportation, public safety as well as the health care. This
majorly incorporate better communication of the information which is been transferred into
the concept (Whitmore, Agarwal & Da Xu, 2015). There are mainly three Cs, which are
related to the internet of things:
Communication: The internet of things communicates to the people information relating to
the health and state of equipment. This can be related to weather the equipment, the system is
on or off, or it is fully charged or not (Wortmann & Flüchter, 2015). It can be also be used for
the detection of a person’s vital sign. Earlier we could not get the appropriate information at
the right time or the information was not perfect and appropriate. In the sector of the hospital,
the internet of things can be used to locate information about anything such as cardiac
defibrillators to wheel chairs. In transportation industry, it can be used for the tracking
purpose relating to the position of the pellets and parcels (Wortmann & Flüchter, 2015).
Automation and control: In the concept of connected world, we are connected to each and
everything with the technology. Many times a user or a person can make use of a technology
to access a device. This is achieved by the implementation of the internet of things concept.
In a business environment, the concept can be applied if a device has to be switched of or a
part of the device has to be switched off. A customer can remotely use the concept of the
Part 3
The internet of things is playing vital role in the sphere of life. It can be stated that the
internet of things is and would be playing a dominant role in the future. According to the
concept of implementation of internet of things in the aspect of business it can be widely be
used to gain business efficiency and improvement in the sector of customer satisfaction and
operations. I have come across more of the sectors other than the business orientation that can
benefit from the concept like the transportation, public safety as well as the health care. This
majorly incorporate better communication of the information which is been transferred into
the concept (Whitmore, Agarwal & Da Xu, 2015). There are mainly three Cs, which are
related to the internet of things:
Communication: The internet of things communicates to the people information relating to
the health and state of equipment. This can be related to weather the equipment, the system is
on or off, or it is fully charged or not (Wortmann & Flüchter, 2015). It can be also be used for
the detection of a person’s vital sign. Earlier we could not get the appropriate information at
the right time or the information was not perfect and appropriate. In the sector of the hospital,
the internet of things can be used to locate information about anything such as cardiac
defibrillators to wheel chairs. In transportation industry, it can be used for the tracking
purpose relating to the position of the pellets and parcels (Wortmann & Flüchter, 2015).
Automation and control: In the concept of connected world, we are connected to each and
everything with the technology. Many times a user or a person can make use of a technology
to access a device. This is achieved by the implementation of the internet of things concept.
In a business environment, the concept can be applied if a device has to be switched of or a
part of the device has to be switched off. A customer can remotely use the concept of the

6WIRELESS NETWORKING
internet of things to unlock their personal cars or start a washing machine. In this concept I
have seen that one’s a baseline of performance is created it can send alert and directly provide
a response in automated form. This concept can act also as a security concern for example if a
break paddle of a truck is about to fail it can send automated response and it can suggest the
company to put the truck out of service and suggest a maintenance schedule for it.
Saving of cost: Most of the companies adopt the concept of the internet of things to
implement cost saving. The measurement directly provides the equipment health as well as
the data of the performance instead of just framing up of the estimation. Most of the business
body face lots of monitory loss due to the factor of equipment failure. When the concept of
the internet of things is implemented in can directly help the company to minimize the aspect
of the equipment failure and allows the business body to perform maintenance planning. The
the new meters when incorporated into the business and homes can provide the data which
can help people to be more concern towards the factor of consumption of the energy which
can directly reduce the cost related to the implementation (Zhu et al., 2017).
Part 4 (Power Point Presentation)
internet of things to unlock their personal cars or start a washing machine. In this concept I
have seen that one’s a baseline of performance is created it can send alert and directly provide
a response in automated form. This concept can act also as a security concern for example if a
break paddle of a truck is about to fail it can send automated response and it can suggest the
company to put the truck out of service and suggest a maintenance schedule for it.
Saving of cost: Most of the companies adopt the concept of the internet of things to
implement cost saving. The measurement directly provides the equipment health as well as
the data of the performance instead of just framing up of the estimation. Most of the business
body face lots of monitory loss due to the factor of equipment failure. When the concept of
the internet of things is implemented in can directly help the company to minimize the aspect
of the equipment failure and allows the business body to perform maintenance planning. The
the new meters when incorporated into the business and homes can provide the data which
can help people to be more concern towards the factor of consumption of the energy which
can directly reduce the cost related to the implementation (Zhu et al., 2017).
Part 4 (Power Point Presentation)

7WIRELESS NETWORKING
Slide 1
Slide 2
Slide 1
Slide 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8WIRELESS NETWORKING
Slide 3
Slide 4
Slide 3
Slide 4

9WIRELESS NETWORKING
Slide 5
Slide 6
Slide 5
Slide 6

10WIRELESS NETWORKING
Slide 7
Slide 8
Slide 7
Slide 8
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

11WIRELESS NETWORKING
Slide 9
Slide 10
Slide 9
Slide 10

12WIRELESS NETWORKING

13WIRELESS NETWORKING
References
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., & Ayyash, M. (2015). Internet
of things: A survey on enabling technologies, protocols, and applications. IEEE
Communications Surveys & Tutorials, 17(4), 2347-2376.
Chandrakanth, S., Venkatesh, K., Uma Mahesh, J., & Naganjaneyulu, K. V. (2014). Internet
of things. International Journal of Innovations & Advancement in Computer
Science, 3(8), 16-20.
Cui, X. (2016). The internet of things. In Ethical Ripples of Creativity and Innovation (pp.
61-68). Palgrave Macmillan, London.
Da Xu, L., He, W., & Li, S. (2014). Internet of things in industries: A survey. IEEE
Transactions on industrial informatics, 10(4), 2233-2243.
Jun, J., Yeon, S., Kundu, T., Agrawal, D. P., & Jeong, J. (2016, June). Caca: Link-based
channel allocation exploiting capture effect for channel reuse in wireless sensor
networks. In Distributed Computing Systems (ICDCS), 2016 IEEE 36th International
Conference on (pp. 600-608). IEEE.
Katar, S., Zhu, H., Yonge III, L. W., Krishnam, M. A., & Stanley, J. K. I. (2014). U.S. Patent
No. 8,886,203. Washington, DC: U.S. Patent and Trademark Office.
Osseiran, A., Elloumi, O., Song, J., & Monserrat, J. F. (2017). Internet of Things. IEEE
Communications Standards Magazine, 1(2), 84-84.
Whitmore, A., Agarwal, A., & Da Xu, L. (2015). The Internet of Things—A survey of topics
and trends. Information Systems Frontiers, 17(2), 261-274.
References
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., & Ayyash, M. (2015). Internet
of things: A survey on enabling technologies, protocols, and applications. IEEE
Communications Surveys & Tutorials, 17(4), 2347-2376.
Chandrakanth, S., Venkatesh, K., Uma Mahesh, J., & Naganjaneyulu, K. V. (2014). Internet
of things. International Journal of Innovations & Advancement in Computer
Science, 3(8), 16-20.
Cui, X. (2016). The internet of things. In Ethical Ripples of Creativity and Innovation (pp.
61-68). Palgrave Macmillan, London.
Da Xu, L., He, W., & Li, S. (2014). Internet of things in industries: A survey. IEEE
Transactions on industrial informatics, 10(4), 2233-2243.
Jun, J., Yeon, S., Kundu, T., Agrawal, D. P., & Jeong, J. (2016, June). Caca: Link-based
channel allocation exploiting capture effect for channel reuse in wireless sensor
networks. In Distributed Computing Systems (ICDCS), 2016 IEEE 36th International
Conference on (pp. 600-608). IEEE.
Katar, S., Zhu, H., Yonge III, L. W., Krishnam, M. A., & Stanley, J. K. I. (2014). U.S. Patent
No. 8,886,203. Washington, DC: U.S. Patent and Trademark Office.
Osseiran, A., Elloumi, O., Song, J., & Monserrat, J. F. (2017). Internet of Things. IEEE
Communications Standards Magazine, 1(2), 84-84.
Whitmore, A., Agarwal, A., & Da Xu, L. (2015). The Internet of Things—A survey of topics
and trends. Information Systems Frontiers, 17(2), 261-274.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

14WIRELESS NETWORKING
Wortmann, F., & Flüchter, K. (2015). Internet of things. Business & Information Systems
Engineering, 57(3), 221-224.
Zhu, H., Katar, S., Merlin, S., Zou, C., Barriac, G. D., Cherian, G., & Sampath, H.
(2017). U.S. Patent No. 9,622,262. Washington, DC: U.S. Patent and Trademark
Office.
Wortmann, F., & Flüchter, K. (2015). Internet of things. Business & Information Systems
Engineering, 57(3), 221-224.
Zhu, H., Katar, S., Merlin, S., Zou, C., Barriac, G. D., Cherian, G., & Sampath, H.
(2017). U.S. Patent No. 9,622,262. Washington, DC: U.S. Patent and Trademark
Office.
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





