Information Security Assessment: ATM Security Fundamentals
VerifiedAdded on 2023/06/14
|10
|2235
|261
Homework Assignment
AI Summary
This assignment provides a comprehensive assessment of ATM information security fundamentals, addressing key concepts such as confidentiality, integrity, and availability. It explores scenarios like ATM break-ins and the potential for PIN compromise, along with the advantages and disadvantages of biometric authentication systems. The assignment also discusses the differences between false positive and false negative rates in security systems. Furthermore, it includes a practical decryption exercise using substitution and Caesar Cipher methods to reveal an encrypted message related to processor frequency. References to relevant academic papers and industry practices support the analysis throughout the assignment. The study material is available on Desklib, a platform offering AI-based study tools and a wide range of solved assignments.

Running head: ATM INFORMATION SECURITY
ATM Information Security
Assessment No-
Assessment Title-
Student Name and ID-
Student name and Code-
Student Email Address-
ATM Information Security
Assessment No-
Assessment Title-
Student Name and ID-
Student name and Code-
Student Email Address-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ATM INFORMATION SECURITY
Question Number 1:
The example of confidentiality, integrity, and availability are defined below:
Confidentiality: The confidentiality that is to be provided for the ATM card generally is to keep
the data or information that are stored in the ATM card secured and kept private from any other
intruders. The information in the card should not reach in the hand of unauthorized person.
Confidentiality gives the surety that the information that is transferred reaches only to the
authorized user (Kim et al., 2015). The data in the ATM card is to be kept private. Example
including in the confidentiality gives surety that the pin of the ATM card, CVV number and the
card number is made secret and needed to be kept secret throughout the lifetime of the card.
Integrity: There is a necessity in the ATM card that information is to be kept same as
transmitted by the sender. The information involved in the ATM card should be altered while
transmission (He & Wang, 2015). The process of integrity maintains the consistency,
trustworthiness, and the accuracy of the information. All certain measure are to be involved
providing the integrity security of the information in a transaction process. Many data integrity
controls are taken to keep the information safe throughout the transaction process (Siponen,
Mahmood & Pahnila, 2014). Examples of integrity measures that can be taken are the process of
encryption. Encryption is done to keep the data integrity in case there is some accidental reason
for data breach.
Availability:
Availability includes all data and information involved in the system are to be present with the
user so that the user do not face any kind of problem while the transaction process is going on. It
Question Number 1:
The example of confidentiality, integrity, and availability are defined below:
Confidentiality: The confidentiality that is to be provided for the ATM card generally is to keep
the data or information that are stored in the ATM card secured and kept private from any other
intruders. The information in the card should not reach in the hand of unauthorized person.
Confidentiality gives the surety that the information that is transferred reaches only to the
authorized user (Kim et al., 2015). The data in the ATM card is to be kept private. Example
including in the confidentiality gives surety that the pin of the ATM card, CVV number and the
card number is made secret and needed to be kept secret throughout the lifetime of the card.
Integrity: There is a necessity in the ATM card that information is to be kept same as
transmitted by the sender. The information involved in the ATM card should be altered while
transmission (He & Wang, 2015). The process of integrity maintains the consistency,
trustworthiness, and the accuracy of the information. All certain measure are to be involved
providing the integrity security of the information in a transaction process. Many data integrity
controls are taken to keep the information safe throughout the transaction process (Siponen,
Mahmood & Pahnila, 2014). Examples of integrity measures that can be taken are the process of
encryption. Encryption is done to keep the data integrity in case there is some accidental reason
for data breach.
Availability:
Availability includes all data and information involved in the system are to be present with the
user so that the user do not face any kind of problem while the transaction process is going on. It

2ATM INFORMATION SECURITY
is also to be kept in mind that the information is available only with the authenticated user
(Ciuffo & Weiss, 2017). Any unauthorized users do not use the information of other users. This
will lead to insecurity of the data available with the user (Thomas, Vinod & Robinson, 2017).
The availability of the information can be made secured by keeping backup for the data to be
kept secret. Ina system, there can be a denial-of-attack by some unauthenticated user that can be
mitigated by backup process or the encryption process.
Question Number 2:
The given case study states that a thief broke in the ATM and the thief was successful in
jamming the card reader of the machine (De Luca et al, 2015). As a result, of jamming the ATM
card reader, the user who wants a transaction will not be able to take out the card from the ATM
machine. The thief also destroyed the machine by destroying the keypad of the machine, in
which the user enters the pin. But, while he was working on the keypad, a customer arrives the
center to withdraw cash. The thief was successful in destroying five keys, and five keys were left
undestroyed. The customer who came to the machine was successful in his transaction (Layton,
2016). But, after collecting the cash, the customer was unable to take out the card as the card
reader was jammed. While the customer was out for help, the thief tried to discover the pin and
take out some cash from the account. The total number of possibility that the thief can input with
the five keys available can be done by combining all the possibilities. The digits in a ATM pin is
4 and with the five keys good, the maximum number of possibilities that the thief can attempt is
5P4 = 5! / (5-4)! = 5 * 4 * 3 * 2 = 120 possible outcomes.
But, the security of the ATM does not allow the user for so many attempt. As per the
security of ATM machine, the maximum times a user can enter wrong pin is three times. If a
is also to be kept in mind that the information is available only with the authenticated user
(Ciuffo & Weiss, 2017). Any unauthorized users do not use the information of other users. This
will lead to insecurity of the data available with the user (Thomas, Vinod & Robinson, 2017).
The availability of the information can be made secured by keeping backup for the data to be
kept secret. Ina system, there can be a denial-of-attack by some unauthenticated user that can be
mitigated by backup process or the encryption process.
Question Number 2:
The given case study states that a thief broke in the ATM and the thief was successful in
jamming the card reader of the machine (De Luca et al, 2015). As a result, of jamming the ATM
card reader, the user who wants a transaction will not be able to take out the card from the ATM
machine. The thief also destroyed the machine by destroying the keypad of the machine, in
which the user enters the pin. But, while he was working on the keypad, a customer arrives the
center to withdraw cash. The thief was successful in destroying five keys, and five keys were left
undestroyed. The customer who came to the machine was successful in his transaction (Layton,
2016). But, after collecting the cash, the customer was unable to take out the card as the card
reader was jammed. While the customer was out for help, the thief tried to discover the pin and
take out some cash from the account. The total number of possibility that the thief can input with
the five keys available can be done by combining all the possibilities. The digits in a ATM pin is
4 and with the five keys good, the maximum number of possibilities that the thief can attempt is
5P4 = 5! / (5-4)! = 5 * 4 * 3 * 2 = 120 possible outcomes.
But, the security of the ATM does not allow the user for so many attempt. As per the
security of ATM machine, the maximum times a user can enter wrong pin is three times. If a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ATM INFORMATION SECURITY
customer enters three consecutive wrong pins, then the card will be blocked and the customer has
to call the Customer Care of the bank to unblock, or will have to wait for 24 hours for the card to
block (Alaskar, Vodanovich & Shen, 2015). Therefore, coincidently if the thief becomes
successful in giving the correct pin, he will be successful to collect some cash. But, he will not
be able to enter 120 attempts for determining the correct pin of the ATM card.
Question Number 3:
There can be many reasons due to which users finds the biometric system a secured one.
Out of all the advantages that biometric provides, three of the most important advantages are
listed below:
1) The administrative cost of a user or an organization is cut less. The installation process of
biometric is very less and does not much maintenance as there is no use of paper and much of the
work is done automatically by the system itself (Chen, Pande & Mohapatra, 2014). Also, to
maintain the system of biometric, no such training is required as it does not need any
professionals to handle the system.
2) Improves the return investment as this authentication system gives security for accuracy, the
misuse of resources is basically reduced, and the accountability is also increased for the
information stored in the system (Ogbanufe & Kim, 2017).
3) The system of biometric security is the most secured system that is available for
authentication. As, the biometric system deals with the physical parts of the human body, there is
no chance of being theft and biometric of all humans are different from each other.
customer enters three consecutive wrong pins, then the card will be blocked and the customer has
to call the Customer Care of the bank to unblock, or will have to wait for 24 hours for the card to
block (Alaskar, Vodanovich & Shen, 2015). Therefore, coincidently if the thief becomes
successful in giving the correct pin, he will be successful to collect some cash. But, he will not
be able to enter 120 attempts for determining the correct pin of the ATM card.
Question Number 3:
There can be many reasons due to which users finds the biometric system a secured one.
Out of all the advantages that biometric provides, three of the most important advantages are
listed below:
1) The administrative cost of a user or an organization is cut less. The installation process of
biometric is very less and does not much maintenance as there is no use of paper and much of the
work is done automatically by the system itself (Chen, Pande & Mohapatra, 2014). Also, to
maintain the system of biometric, no such training is required as it does not need any
professionals to handle the system.
2) Improves the return investment as this authentication system gives security for accuracy, the
misuse of resources is basically reduced, and the accountability is also increased for the
information stored in the system (Ogbanufe & Kim, 2017).
3) The system of biometric security is the most secured system that is available for
authentication. As, the biometric system deals with the physical parts of the human body, there is
no chance of being theft and biometric of all humans are different from each other.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ATM INFORMATION SECURITY
Question Number 4:
There are many circumstances where false negative rates are more than the false positive
rates. False negative rate increases when the system cannot detect the data of an authenticated
user and rejects their authentication (Barbosa & Silva, 2015). One of the instances, which can
describe that false negative rate is more than that of false negative is the result of a test. In a
diagnosis test result, the system can wrongly deny the test report as a wrong one due to some
technical error in the database. False positive is a situation where the system of biometric detects
an unauthorized user as an authorized one wrongly. The rate of false positive is comparatively
less than the false positive rate.
Question Number 5:
Many algorithm processes are there in security system, by which a cipher text can be
encrypted or decrypted similar to that of the transposition method (Ab Rahman & Choo, 2015).
The other methods that work same like transposition method are Caesar Shift Method, Columnar
Transposition Method, Substitution Method, Baconian Method and many more.
The encrypted key given in the question is:
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
To decrypt the text, two methods are used in this solution. Firstly, by substitution method
followed by Caesar Cipher shifting by 3. The numeric values of the total encrypted key are
determined to proceed with the solution. Then, with the key 234 given, in a continuous way
substitution method is applied. After substitution method, Caesar Cipher method is applied of
back shifting by three. The desired result of the given encrypted text is given below:
Question Number 4:
There are many circumstances where false negative rates are more than the false positive
rates. False negative rate increases when the system cannot detect the data of an authenticated
user and rejects their authentication (Barbosa & Silva, 2015). One of the instances, which can
describe that false negative rate is more than that of false negative is the result of a test. In a
diagnosis test result, the system can wrongly deny the test report as a wrong one due to some
technical error in the database. False positive is a situation where the system of biometric detects
an unauthorized user as an authorized one wrongly. The rate of false positive is comparatively
less than the false positive rate.
Question Number 5:
Many algorithm processes are there in security system, by which a cipher text can be
encrypted or decrypted similar to that of the transposition method (Ab Rahman & Choo, 2015).
The other methods that work same like transposition method are Caesar Shift Method, Columnar
Transposition Method, Substitution Method, Baconian Method and many more.
The encrypted key given in the question is:
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
To decrypt the text, two methods are used in this solution. Firstly, by substitution method
followed by Caesar Cipher shifting by 3. The numeric values of the total encrypted key are
determined to proceed with the solution. Then, with the key 234 given, in a continuous way
substitution method is applied. After substitution method, Caesar Cipher method is applied of
back shifting by three. The desired result of the given encrypted text is given below:
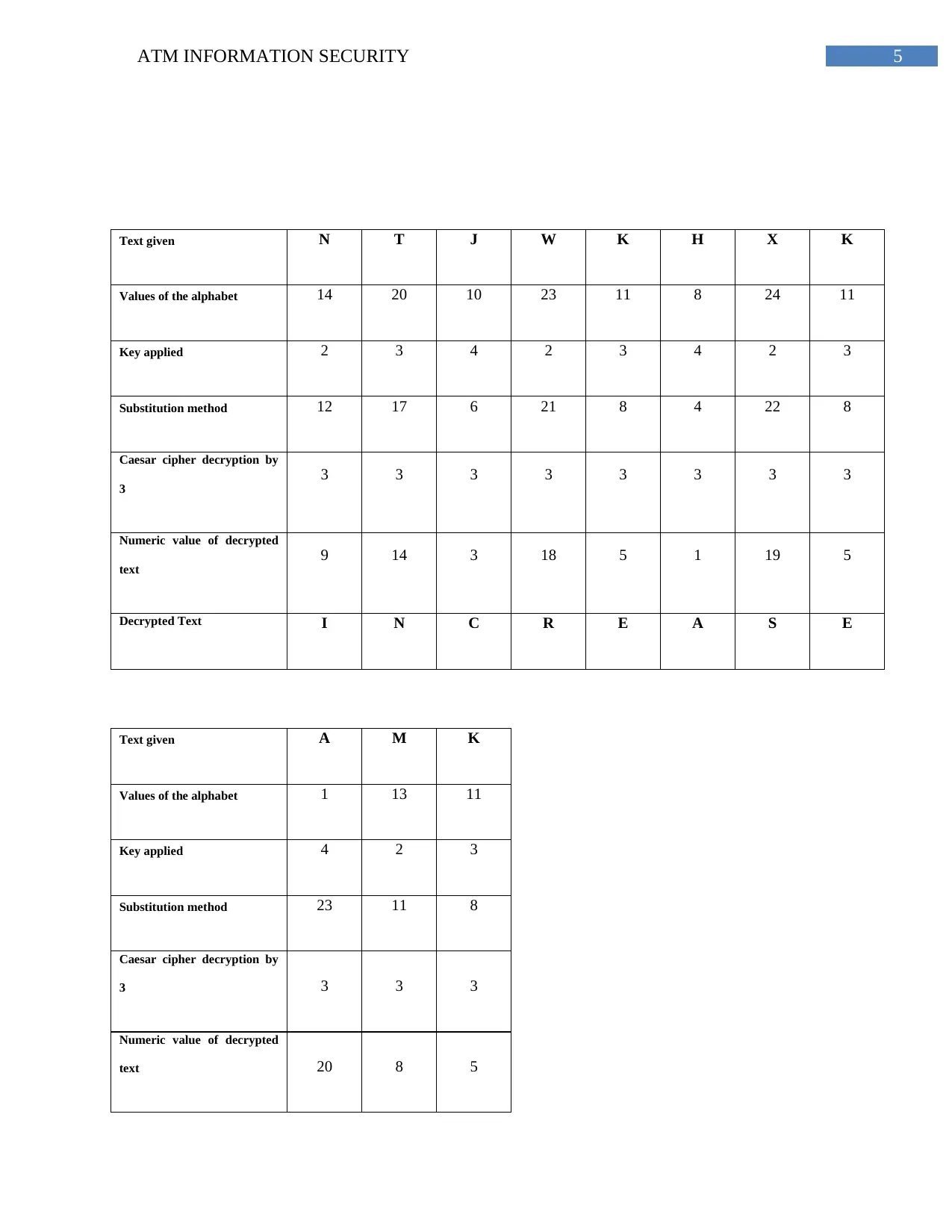
5ATM INFORMATION SECURITY
Text given N T J W K H X K
Values of the alphabet 14 20 10 23 11 8 24 11
Key applied 2 3 4 2 3 4 2 3
Substitution method 12 17 6 21 8 4 22 8
Caesar cipher decryption by
3
3 3 3 3 3 3 3 3
Numeric value of decrypted
text
9 14 3 18 5 1 19 5
Decrypted Text I N C R E A S E
Text given A M K
Values of the alphabet 1 13 11
Key applied 4 2 3
Substitution method 23 11 8
Caesar cipher decryption by
3 3 3 3
Numeric value of decrypted
text 20 8 5
Text given N T J W K H X K
Values of the alphabet 14 20 10 23 11 8 24 11
Key applied 2 3 4 2 3 4 2 3
Substitution method 12 17 6 21 8 4 22 8
Caesar cipher decryption by
3
3 3 3 3 3 3 3 3
Numeric value of decrypted
text
9 14 3 18 5 1 19 5
Decrypted Text I N C R E A S E
Text given A M K
Values of the alphabet 1 13 11
Key applied 4 2 3
Substitution method 23 11 8
Caesar cipher decryption by
3 3 3 3
Numeric value of decrypted
text 20 8 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
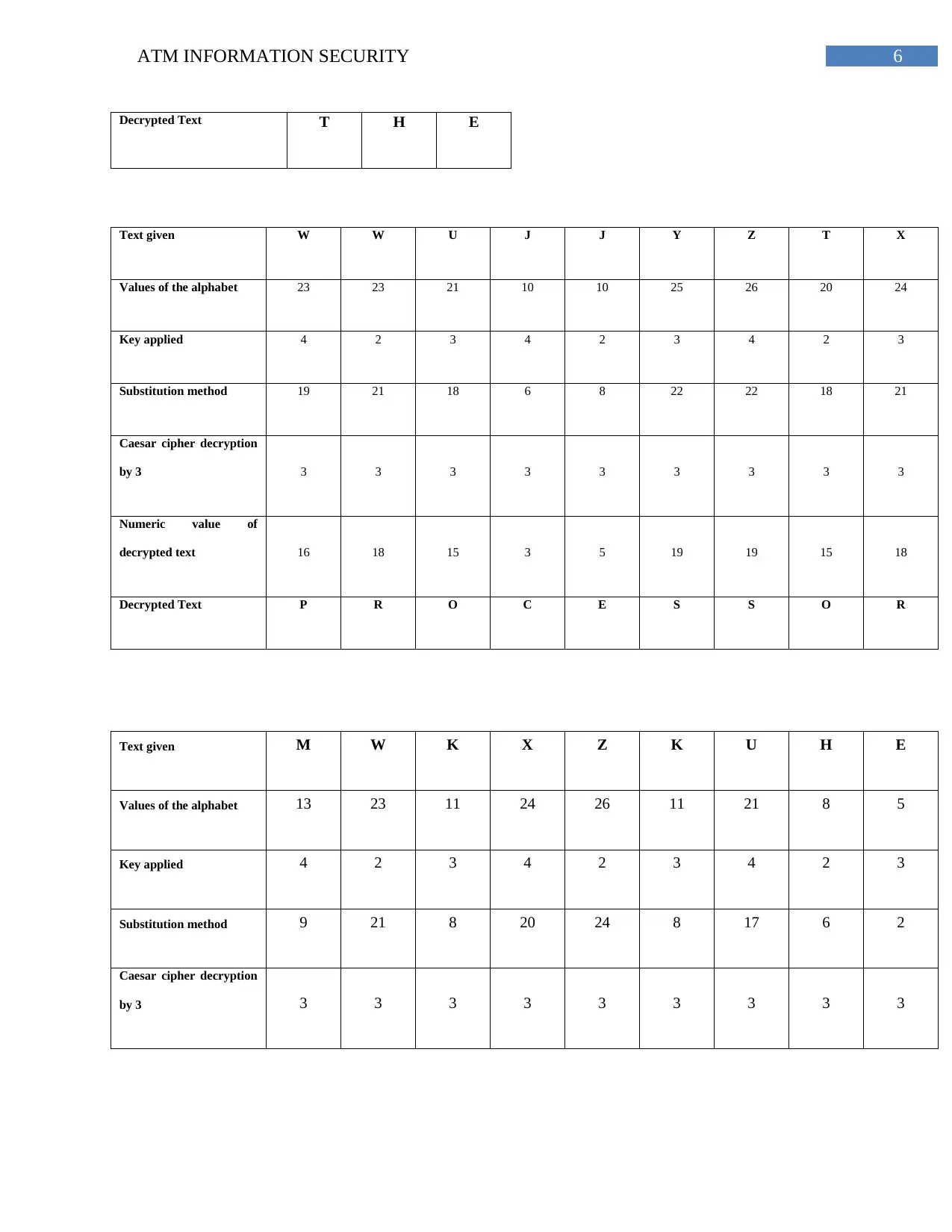
6ATM INFORMATION SECURITY
Decrypted Text T H E
Text given W W U J J Y Z T X
Values of the alphabet 23 23 21 10 10 25 26 20 24
Key applied 4 2 3 4 2 3 4 2 3
Substitution method 19 21 18 6 8 22 22 18 21
Caesar cipher decryption
by 3 3 3 3 3 3 3 3 3 3
Numeric value of
decrypted text 16 18 15 3 5 19 19 15 18
Decrypted Text P R O C E S S O R
Text given M W K X Z K U H E
Values of the alphabet 13 23 11 24 26 11 21 8 5
Key applied 4 2 3 4 2 3 4 2 3
Substitution method 9 21 8 20 24 8 17 6 2
Caesar cipher decryption
by 3 3 3 3 3 3 3 3 3 3
Decrypted Text T H E
Text given W W U J J Y Z T X
Values of the alphabet 23 23 21 10 10 25 26 20 24
Key applied 4 2 3 4 2 3 4 2 3
Substitution method 19 21 18 6 8 22 22 18 21
Caesar cipher decryption
by 3 3 3 3 3 3 3 3 3 3
Numeric value of
decrypted text 16 18 15 3 5 19 19 15 18
Decrypted Text P R O C E S S O R
Text given M W K X Z K U H E
Values of the alphabet 13 23 11 24 26 11 21 8 5
Key applied 4 2 3 4 2 3 4 2 3
Substitution method 9 21 8 20 24 8 17 6 2
Caesar cipher decryption
by 3 3 3 3 3 3 3 3 3 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ATM INFORMATION SECURITY
Numeric value of
decrypted text 6 18 5 17 21 5 14 3 25
Decrypted Text F R E Q U E N C Y
So, after the decryption, the text that is determined is
INCREASE THE PROCESSOR FREQUENCY
References
Ab Rahman, N. H., & Choo, K. K. R. (2015). A survey of information security incident handling
in the cloud. Computers & Security, 49, 45-69.
Alaskar, M., Vodanovich, S., & Shen, K. N. (2015, January). Evolvement of Information
Security Research on Employees' Behavior: A Systematic Review and Future Direction.
In System Sciences (HICSS), 2015 48th Hawaii International Conference on (pp. 4241-
4250). IEEE.
Barbosa, F. G., & Silva, W. L. S. (2015, November). Support vector machines, Mel-Frequency
Cepstral Coefficients and the Discrete Cosine Transform applied on voice based
biometric authentication. In SAI Intelligent Systems Conference (IntelliSys), 2015 (pp.
1032-1039). IEEE.
Chen, S., Pande, A., & Mohapatra, P. (2014, June). Sensor-assisted facial recognition: an
enhanced biometric authentication system for smartphones. In Proceedings of the 12th
Numeric value of
decrypted text 6 18 5 17 21 5 14 3 25
Decrypted Text F R E Q U E N C Y
So, after the decryption, the text that is determined is
INCREASE THE PROCESSOR FREQUENCY
References
Ab Rahman, N. H., & Choo, K. K. R. (2015). A survey of information security incident handling
in the cloud. Computers & Security, 49, 45-69.
Alaskar, M., Vodanovich, S., & Shen, K. N. (2015, January). Evolvement of Information
Security Research on Employees' Behavior: A Systematic Review and Future Direction.
In System Sciences (HICSS), 2015 48th Hawaii International Conference on (pp. 4241-
4250). IEEE.
Barbosa, F. G., & Silva, W. L. S. (2015, November). Support vector machines, Mel-Frequency
Cepstral Coefficients and the Discrete Cosine Transform applied on voice based
biometric authentication. In SAI Intelligent Systems Conference (IntelliSys), 2015 (pp.
1032-1039). IEEE.
Chen, S., Pande, A., & Mohapatra, P. (2014, June). Sensor-assisted facial recognition: an
enhanced biometric authentication system for smartphones. In Proceedings of the 12th

8ATM INFORMATION SECURITY
annual international conference on Mobile systems, applications, and services (pp. 109-
122). ACM.
Ciuffo, F., & Weiss, G. M. (2017, October). Smartwatch-based transcription biometrics.
In Ubiquitous Computing, Electronics and Mobile Communication Conference
(UEMCON), 2017 IEEE 8th Annual (pp. 145-149). IEEE.
De Luca, A., Hang, A., Von Zezschwitz, E., & Hussmann, H. (2015, April). I feel like I'm taking
selfies all day!: towards understanding biometric authentication on smartphones.
In Proceedings of the 33rd Annual ACM Conference on Human Factors in Computing
Systems (pp. 1411-1414). ACM.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), 816-823.
Kim, H., Park, J., Lee, J., & Ryou, J. (2015). Biometric authentication technology trends in smart
device environment. In Mobile and Wireless Technology 2015 (pp. 199-206). Springer,
Berlin, Heidelberg.
Layton, T. P. (2016). Information Security: Design, implementation, measurement, and
compliance. CRC Press.
Ogbanufe, O., & Kim, D. J. (2017). Comparing fingerprint-based biometrics authentication
versus traditional authentication methods for e-payment. Decision Support Systems.
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-
224.
annual international conference on Mobile systems, applications, and services (pp. 109-
122). ACM.
Ciuffo, F., & Weiss, G. M. (2017, October). Smartwatch-based transcription biometrics.
In Ubiquitous Computing, Electronics and Mobile Communication Conference
(UEMCON), 2017 IEEE 8th Annual (pp. 145-149). IEEE.
De Luca, A., Hang, A., Von Zezschwitz, E., & Hussmann, H. (2015, April). I feel like I'm taking
selfies all day!: towards understanding biometric authentication on smartphones.
In Proceedings of the 33rd Annual ACM Conference on Human Factors in Computing
Systems (pp. 1411-1414). ACM.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), 816-823.
Kim, H., Park, J., Lee, J., & Ryou, J. (2015). Biometric authentication technology trends in smart
device environment. In Mobile and Wireless Technology 2015 (pp. 199-206). Springer,
Berlin, Heidelberg.
Layton, T. P. (2016). Information Security: Design, implementation, measurement, and
compliance. CRC Press.
Ogbanufe, O., & Kim, D. J. (2017). Comparing fingerprint-based biometrics authentication
versus traditional authentication methods for e-payment. Decision Support Systems.
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-
224.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ATM INFORMATION SECURITY
Thomas, K. P., Vinod, A. P., & Robinson, N. (2017, March). Online Biometric Authentication
Using Subject-Specific Band Power features of EEG. In Proceedings of the 2017
International Conference on Cryptography, Security and Privacy (pp. 136-141). ACM.
Thomas, K. P., Vinod, A. P., & Robinson, N. (2017, March). Online Biometric Authentication
Using Subject-Specific Band Power features of EEG. In Proceedings of the 2017
International Conference on Cryptography, Security and Privacy (pp. 136-141). ACM.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





