Detailed Analysis of ATM Security, PIN and Biometric Authentication
VerifiedAdded on 2023/06/13
|10
|2628
|282
Homework Assignment
AI Summary
This assignment solution covers various aspects of ATM security, including the importance of confidentiality, integrity, and availability in protecting PINs and bank account details. It addresses a scenario involving a compromised ATM and calculates the possible PIN permutations a thief could attempt. The solution further explores biometric authentication systems, discussing their benefits in preventing fake data and enhancing security, while also acknowledging the reasons why some individuals are hesitant to adopt them, such as password reset complexities, data accuracy concerns, and hardware requirements. It highlights the advantages and disadvantages of biometric systems, including scenarios where false negative rates can be more problematic than false positive rates. Finally, the assignment delves into transposition ciphers, specifically rail fence ciphers, and provides a decryption of a cipher text using Caesar cipher and substitution algorithms. Desklib offers this and other solved assignments to aid students in their studies.

Question 1.
ATM is an electronic device that helps to withdraw money without going to the bank. It is
extremely effective and is present in every city, village or country in the world. The customer,
who is withdrawing money, should have a valid bank account with balance in it (De Gramatica et
al., 2015). The major advantage of this electronic device is that there is no time restriction and
the client can withdraw his or her money anytime. Moreover, a huge amount of money could be
extracted from the account and thus it is extremely advantageous for the customer.
The ATM or the Automated Teller Machine users are solely provided with personal
identification number or PIN and an ATM card. The presence of both of these is required for any
transaction. This PIN is a unique number of four digit and it is kept hidden or private. There are
three basic requirements for maintenance of privacy and security in the PIN and other bank
account details (Peltier, 2016). These are known as CIA or simply confidentiality, integrity and
availability. The descriptions of these three requirements with proper examples are given below:
i) Confidentiality: The most important requirement for any ATM card is confidentiality. This can
be referred to as privacy. This confidentiality is maintained by the customers by not sharing the
credentials with the other users so that the data is not hacked at any cost.
The degree of importance of the confidentiality factor is extremely high as the PIN could
easily be utilized for any type of illegal activities by the hackers.
The two examples of confidentiality are as follows:
i) ATM card and PIN should be present to make the transaction.
ii) If the credentials would be lost, hackers would utilize them.
ATM is an electronic device that helps to withdraw money without going to the bank. It is
extremely effective and is present in every city, village or country in the world. The customer,
who is withdrawing money, should have a valid bank account with balance in it (De Gramatica et
al., 2015). The major advantage of this electronic device is that there is no time restriction and
the client can withdraw his or her money anytime. Moreover, a huge amount of money could be
extracted from the account and thus it is extremely advantageous for the customer.
The ATM or the Automated Teller Machine users are solely provided with personal
identification number or PIN and an ATM card. The presence of both of these is required for any
transaction. This PIN is a unique number of four digit and it is kept hidden or private. There are
three basic requirements for maintenance of privacy and security in the PIN and other bank
account details (Peltier, 2016). These are known as CIA or simply confidentiality, integrity and
availability. The descriptions of these three requirements with proper examples are given below:
i) Confidentiality: The most important requirement for any ATM card is confidentiality. This can
be referred to as privacy. This confidentiality is maintained by the customers by not sharing the
credentials with the other users so that the data is not hacked at any cost.
The degree of importance of the confidentiality factor is extremely high as the PIN could
easily be utilized for any type of illegal activities by the hackers.
The two examples of confidentiality are as follows:
i) ATM card and PIN should be present to make the transaction.
ii) If the credentials would be lost, hackers would utilize them.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ii) Integrity: It helps to maintain the data integrity and so that no data is altered at any cost
(Siponen, Mahmood & Pahnila, 2014).
The degree of importance of the integrity factor is extremely high as if the data would be
changed, it could be used by the hackers.
The two examples of integrity are as follows:
i) Altering data of ATM card and PIN.
ii) Unintentional change of data.
iii) Availability: The availability of relevant information and the hardware is required for making
the transaction (Von Solms & Van Niekerk, 2013).
The degree of importance of the availability factor is high as without the information and
hardware, transaction will not be made.
The examples of availability are as follows:
i) Absence of hardware will not allow transaction.
ii) Absence of information will not allow transaction.
Question 2.
According to the given scenario, a thief has broken the Automated Teller Machine or an
ATM after using a screwdriver and finally has jammed the card reader of that particular ATM
machine. Next, this thief has broken the five keys from the keypad of the ATM.
Meanwhile, a customer gets in the ATM for withdrawing cash. He is successful in
withdrawing cash, however unsuccessful in taking out the card; since the card reader is jammed.
(Siponen, Mahmood & Pahnila, 2014).
The degree of importance of the integrity factor is extremely high as if the data would be
changed, it could be used by the hackers.
The two examples of integrity are as follows:
i) Altering data of ATM card and PIN.
ii) Unintentional change of data.
iii) Availability: The availability of relevant information and the hardware is required for making
the transaction (Von Solms & Van Niekerk, 2013).
The degree of importance of the availability factor is high as without the information and
hardware, transaction will not be made.
The examples of availability are as follows:
i) Absence of hardware will not allow transaction.
ii) Absence of information will not allow transaction.
Question 2.
According to the given scenario, a thief has broken the Automated Teller Machine or an
ATM after using a screwdriver and finally has jammed the card reader of that particular ATM
machine. Next, this thief has broken the five keys from the keypad of the ATM.
Meanwhile, a customer gets in the ATM for withdrawing cash. He is successful in
withdrawing cash, however unsuccessful in taking out the card; since the card reader is jammed.

He thus, goes out for calling of help for getting out his ATM card from the machine.
The thief now wants to discover the PIN of the customer.
Total number of keys in PIN= 4
Total number of keys broken by the thief = 5.
Therefore, the total number of possibilities of permutation of the four keys is give below:
5P4 = 5!/(5 - 4)! = 5!/4! = 120.
Hence, the thief can detect up to 120 ways of permutation.
However, there is a restriction of 3 times in every ATM. After the third wrong attempt, the
card would be blocked.
Question 3.
Biometric authentication systems are utilized for the proper and systematic identification
of any specific individual with the help of his or her biological features. The identity of the user
is verified with this type of system and thus is extremely effective and popular in respect to
others (Bhagavatula et al., 2015). The methods of the biometric authentication are utilized for the
protection of several types of systems. The logical systems that are facilitated through the access
points of hardware to all the physical systems that are protected by the physical barriers, like
secured research sites and secured facilities, are secured with biometric.
There are various types of biometric authentication systems that are utilized for
successfully identifying the individuals. The most popular types are the fingerprint recognition,
face recognition, scanning of iris, cornea, and hand palm, and voice recognition. These biometric
authentication systems help the individual to protect their valuables or get entry to any secured or
protected building (Frank et al., 2013). The most significant benefit of this type of system is that
The thief now wants to discover the PIN of the customer.
Total number of keys in PIN= 4
Total number of keys broken by the thief = 5.
Therefore, the total number of possibilities of permutation of the four keys is give below:
5P4 = 5!/(5 - 4)! = 5!/4! = 120.
Hence, the thief can detect up to 120 ways of permutation.
However, there is a restriction of 3 times in every ATM. After the third wrong attempt, the
card would be blocked.
Question 3.
Biometric authentication systems are utilized for the proper and systematic identification
of any specific individual with the help of his or her biological features. The identity of the user
is verified with this type of system and thus is extremely effective and popular in respect to
others (Bhagavatula et al., 2015). The methods of the biometric authentication are utilized for the
protection of several types of systems. The logical systems that are facilitated through the access
points of hardware to all the physical systems that are protected by the physical barriers, like
secured research sites and secured facilities, are secured with biometric.
There are various types of biometric authentication systems that are utilized for
successfully identifying the individuals. The most popular types are the fingerprint recognition,
face recognition, scanning of iris, cornea, and hand palm, and voice recognition. These biometric
authentication systems help the individual to protect their valuables or get entry to any secured or
protected building (Frank et al., 2013). The most significant benefit of this type of system is that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

fake data or information is restricted. A database or an information system is present within the
biometric system and the biological trait or data is matched with the previously existing data.
In spite of providing these benefits, few people do not want to use biometric
authentication systems. There are eventually three major reasons for this type of phenomenon.
The most significant reasons for not using biometric system are as follows:
i) Resetting Password: The process of password resetting is complex and thus is not used by all
individuals.
There are various regulations like HIPAA and PCI-DDS that are used for resolving this
problem.
ii) Lack of Data Accuracy: The next important problem is the lack of data accuracy as biometric
systems does not provide 100% accuracy in data.
Various metrics like FAR or FRR help in this type of situation. They are the False
Acceptance Rate and the False Rejection Rate.
iii) Requirement of Hardware: Biometric authentication systems require extra hardware for their
systems and thus this is an extra expense for the organization or individual using biometric.
Cheap hardware is the best answer for this problem.
Question 4.
Biometric authentication system is absolutely simple and easy in installing. Hence this
particular system is solely utilized many users. The offices or the educational institutes use this
system for the attendance purpose as this attendance is often forged by the employees or
students. The users of the system do not need to know anything regarding technology as it is very
biometric system and the biological trait or data is matched with the previously existing data.
In spite of providing these benefits, few people do not want to use biometric
authentication systems. There are eventually three major reasons for this type of phenomenon.
The most significant reasons for not using biometric system are as follows:
i) Resetting Password: The process of password resetting is complex and thus is not used by all
individuals.
There are various regulations like HIPAA and PCI-DDS that are used for resolving this
problem.
ii) Lack of Data Accuracy: The next important problem is the lack of data accuracy as biometric
systems does not provide 100% accuracy in data.
Various metrics like FAR or FRR help in this type of situation. They are the False
Acceptance Rate and the False Rejection Rate.
iii) Requirement of Hardware: Biometric authentication systems require extra hardware for their
systems and thus this is an extra expense for the organization or individual using biometric.
Cheap hardware is the best answer for this problem.
Question 4.
Biometric authentication system is absolutely simple and easy in installing. Hence this
particular system is solely utilized many users. The offices or the educational institutes use this
system for the attendance purpose as this attendance is often forged by the employees or
students. The users of the system do not need to know anything regarding technology as it is very
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

simple to use (Lu et al., 2015). Biometric authentication system even helps in securing the
phones, laptops, tablets or any computing devices. Since, the biological traits are unique, it is
nearly impossible to forge the data. Moreover, these types of traits or attributes could not be
given or transferred to anyone.
Two distinct types of biometric identification systems are present. One of them is based
on the behaviour and the other is based on physiological features. The physiological features
include fingerprint and face recognition, iris scan, cornea scan and many more. The behavioural
features include voice, gait and behaviour of the individual.
There are various advantages of this biometric authentication system. The most
significant advantage of this system is that it helps in the identification of the person uniquely
and eventually. However, various disadvantages are also present within the biometric
authentication system. Several situations occur, where the false negative rates of biometric are
more serious than the false positive rates.
Two examples of this type of situations are given below:
i) Limited Access to Own Possessions: Often biometric authentication systems fail to recognize
the authorized and authenticated users for their problem in the information systems or databases
(Andress, 2014). These users thus could not access their own possessions and their access is
restricted. This specific type of restriction is completely baseless; however the user faces this
type of situation. Thus, the false negative rates are more dangerous and serious than the false
positive rates.
ii) Fail to Identify Patients: The patients often fail to give biometric when they suffer from any
type of disease like eye infections, heart attacks, burnt fingers and many more. They do not have
the capability to give the biometric passwords in this situation and thus the system fails to
identify them. Thus, in spite of being the authenticated user, they cannot access their own
phones, laptops, tablets or any computing devices. Since, the biological traits are unique, it is
nearly impossible to forge the data. Moreover, these types of traits or attributes could not be
given or transferred to anyone.
Two distinct types of biometric identification systems are present. One of them is based
on the behaviour and the other is based on physiological features. The physiological features
include fingerprint and face recognition, iris scan, cornea scan and many more. The behavioural
features include voice, gait and behaviour of the individual.
There are various advantages of this biometric authentication system. The most
significant advantage of this system is that it helps in the identification of the person uniquely
and eventually. However, various disadvantages are also present within the biometric
authentication system. Several situations occur, where the false negative rates of biometric are
more serious than the false positive rates.
Two examples of this type of situations are given below:
i) Limited Access to Own Possessions: Often biometric authentication systems fail to recognize
the authorized and authenticated users for their problem in the information systems or databases
(Andress, 2014). These users thus could not access their own possessions and their access is
restricted. This specific type of restriction is completely baseless; however the user faces this
type of situation. Thus, the false negative rates are more dangerous and serious than the false
positive rates.
ii) Fail to Identify Patients: The patients often fail to give biometric when they suffer from any
type of disease like eye infections, heart attacks, burnt fingers and many more. They do not have
the capability to give the biometric passwords in this situation and thus the system fails to
identify them. Thus, in spite of being the authenticated user, they cannot access their own

possessions (Xu, Zhou & Lyu, 2014). This is another important example of false negative rates
being more dangerous than the false positive rates.
Question 5.
5 A)
The method of encrypting any plain text into the cipher text by shifting the characters or
the group of characters to any regular system for constituting a permutation of that plaintext is
known as transposition cipher in cryptography. The complete ordering of the units of that
plaintext is changes or reordered (Singh, 2013). A bijective function is eventually utilized for
encrypting the position of the characters of the plaintext and thus an inverse function is utilized
for decrypting those characters’ positions. A specific algorithm is utilized for the purpose of
encryption and decryption in transposition cipher.
One of the most simplified and an effective form of the transposition cipher is known as
the rail fence cipher. It has got its name from the process of its encryption. In this type of cipher,
the plain text to be converted is eventually written downwards, on the series of successive rails
within a fence that is imaginary. Then it moves up and again comes down. This goes in a series
and finally the plain text is converted to the cipher text and the cipher text is converted to a plain
text.
Columnar transposition helps to use to the algorithm as many times as required for
encryption. Thus, with the columnar transposition, the encryption could be done easily and
promptly.
5 B)
After using algorithms for Caesar cipher and substitution for George’s company, the
being more dangerous than the false positive rates.
Question 5.
5 A)
The method of encrypting any plain text into the cipher text by shifting the characters or
the group of characters to any regular system for constituting a permutation of that plaintext is
known as transposition cipher in cryptography. The complete ordering of the units of that
plaintext is changes or reordered (Singh, 2013). A bijective function is eventually utilized for
encrypting the position of the characters of the plaintext and thus an inverse function is utilized
for decrypting those characters’ positions. A specific algorithm is utilized for the purpose of
encryption and decryption in transposition cipher.
One of the most simplified and an effective form of the transposition cipher is known as
the rail fence cipher. It has got its name from the process of its encryption. In this type of cipher,
the plain text to be converted is eventually written downwards, on the series of successive rails
within a fence that is imaginary. Then it moves up and again comes down. This goes in a series
and finally the plain text is converted to the cipher text and the cipher text is converted to a plain
text.
Columnar transposition helps to use to the algorithm as many times as required for
encryption. Thus, with the columnar transposition, the encryption could be done easily and
promptly.
5 B)
After using algorithms for Caesar cipher and substitution for George’s company, the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
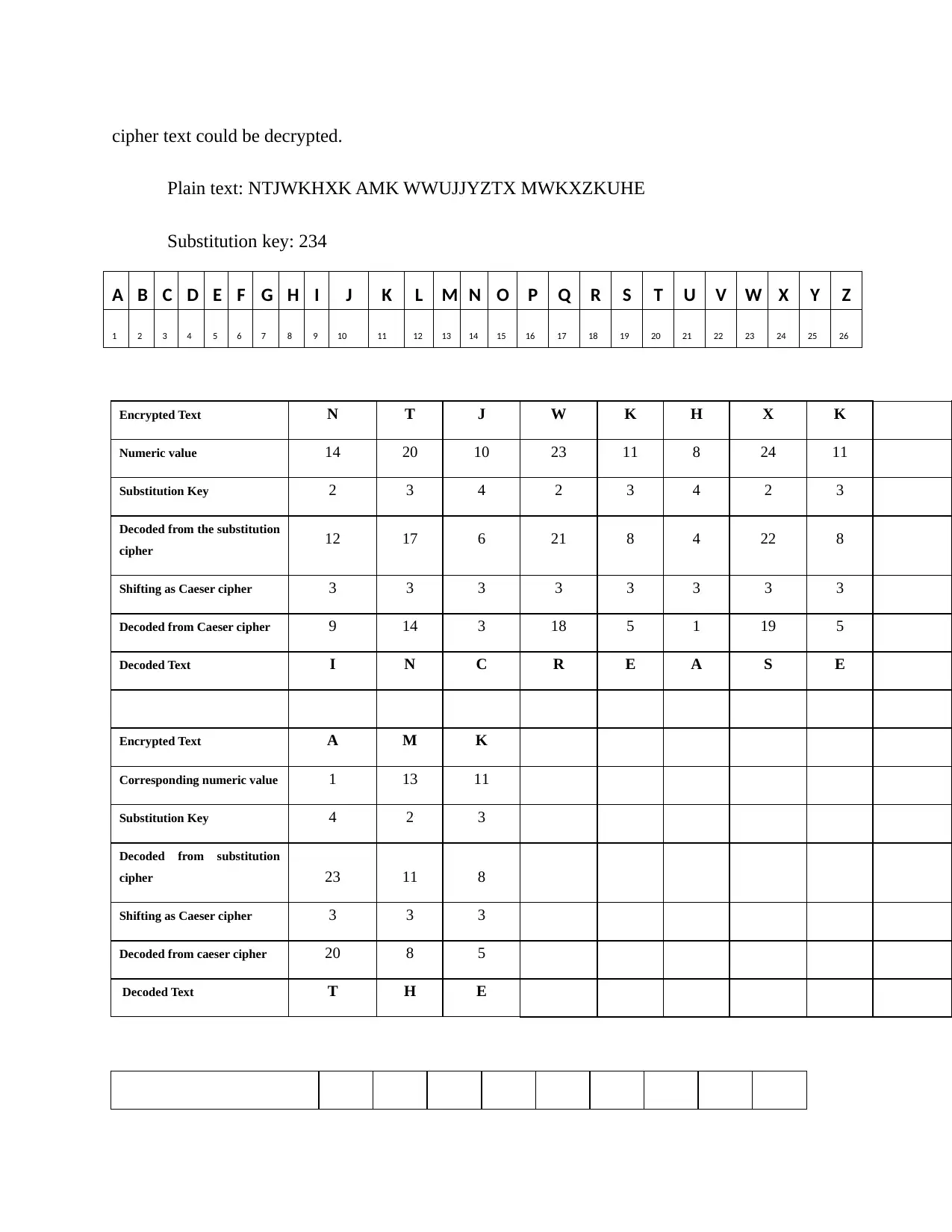
cipher text could be decrypted.
Plain text: NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Substitution key: 234
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 12 17 6 21 8 4 22 8
Shifting as Caeser cipher 3 3 3 3 3 3 3 3
Decoded from Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Substitution Key 4 2 3
Decoded from substitution
cipher 23 11 8
Shifting as Caeser cipher 3 3 3
Decoded from caeser cipher 20 8 5
Decoded Text T H E
Plain text: NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Substitution key: 234
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 12 17 6 21 8 4 22 8
Shifting as Caeser cipher 3 3 3 3 3 3 3 3
Decoded from Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Substitution Key 4 2 3
Decoded from substitution
cipher 23 11 8
Shifting as Caeser cipher 3 3 3
Decoded from caeser cipher 20 8 5
Decoded Text T H E
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
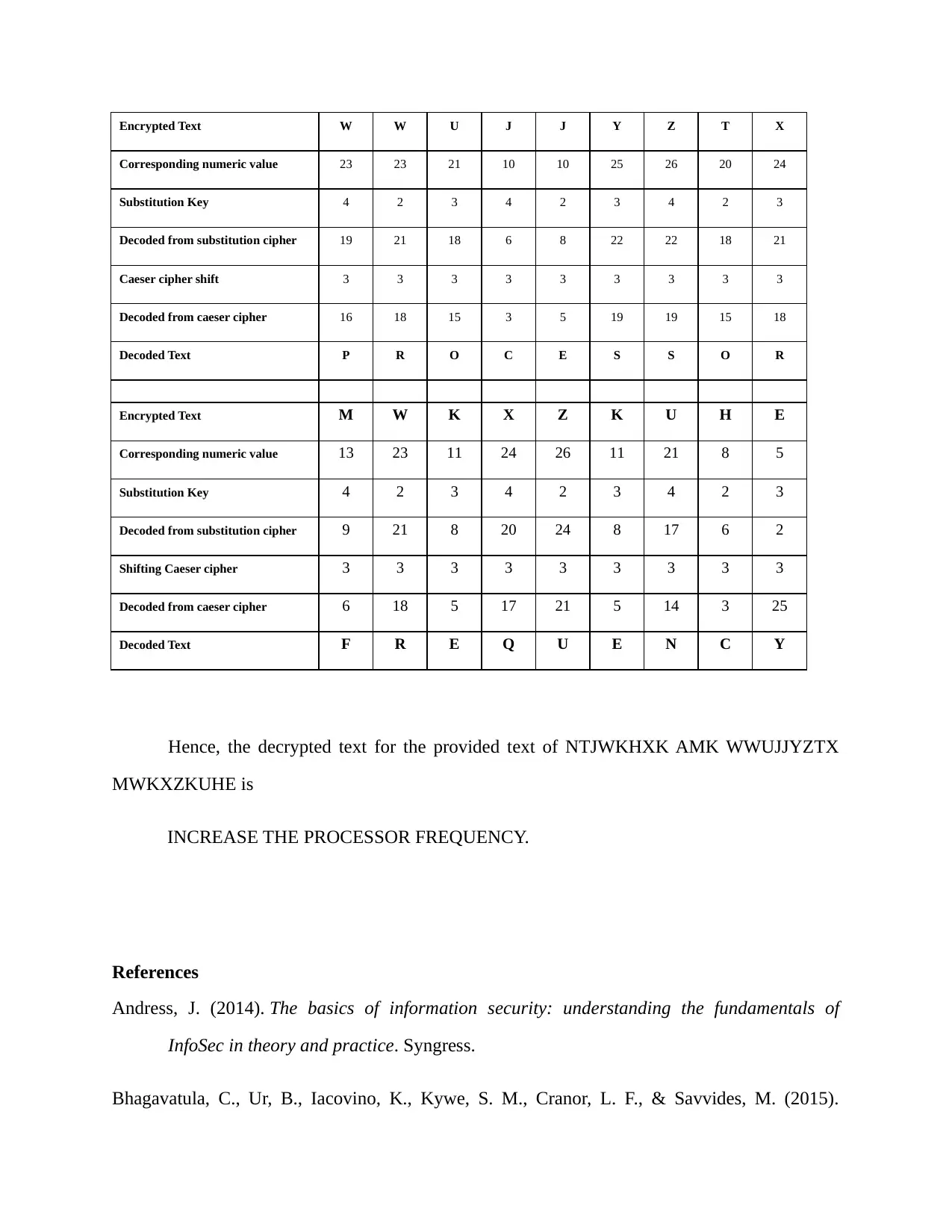
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 9 21 8 20 24 8 17 6 2
Shifting Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Hence, the decrypted text for the provided text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is
INCREASE THE PROCESSOR FREQUENCY.
References
Andress, J. (2014). The basics of information security: understanding the fundamentals of
InfoSec in theory and practice. Syngress.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 9 21 8 20 24 8 17 6 2
Shifting Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Hence, the decrypted text for the provided text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is
INCREASE THE PROCESSOR FREQUENCY.
References
Andress, J. (2014). The basics of information security: understanding the fundamentals of
InfoSec in theory and practice. Syngress.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).

Biometric authentication on iphone and android: Usability, perceptions, and influences on
adoption. Proc. USEC, 1-2.
De Gramatica, M., Labunets, K., Massacci, F., Paci, F., & Tedeschi, A. (2015, March). The role
of catalogues of threats and security controls in security risk assessment: an empirical
study with ATM professionals. In International Working Conference on Requirements
Engineering: Foundation for Software Quality (pp. 98-114). Springer, Cham.
Frank, M., Biedert, R., Ma, E., Martinovic, I., & Song, D. (2013). Touchalytics: On the
applicability of touchscreen input as a behavioral biometric for continuous
authentication. IEEE transactions on information forensics and security, 8(1), 136-148.
Lu, Y., Li, L., Peng, H., & Yang, Y. (2015). An enhanced biometric-based authentication scheme
for telecare medicine information systems using elliptic curve cryptosystem. Journal of
medical systems, 39(3), 32.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Singh, G. (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for information
security. International Journal of Computer Applications, 67(19).
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-224.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber security. computers
& security, 38, 97-102.
Xu, H., Zhou, Y., & Lyu, M. R. (2014, July). Towards continuous and passive authentication via
touch biometrics: An experimental study on smartphones. In Symposium On Usable
Privacy and Security, SOUPS (Vol. 14, pp. 187-198).
adoption. Proc. USEC, 1-2.
De Gramatica, M., Labunets, K., Massacci, F., Paci, F., & Tedeschi, A. (2015, March). The role
of catalogues of threats and security controls in security risk assessment: an empirical
study with ATM professionals. In International Working Conference on Requirements
Engineering: Foundation for Software Quality (pp. 98-114). Springer, Cham.
Frank, M., Biedert, R., Ma, E., Martinovic, I., & Song, D. (2013). Touchalytics: On the
applicability of touchscreen input as a behavioral biometric for continuous
authentication. IEEE transactions on information forensics and security, 8(1), 136-148.
Lu, Y., Li, L., Peng, H., & Yang, Y. (2015). An enhanced biometric-based authentication scheme
for telecare medicine information systems using elliptic curve cryptosystem. Journal of
medical systems, 39(3), 32.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Singh, G. (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for information
security. International Journal of Computer Applications, 67(19).
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-224.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber security. computers
& security, 38, 97-102.
Xu, H., Zhou, Y., & Lyu, M. R. (2014, July). Towards continuous and passive authentication via
touch biometrics: An experimental study on smartphones. In Symposium On Usable
Privacy and Security, SOUPS (Vol. 14, pp. 187-198).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




