Information Security: ATM Systems, Biometrics and Cryptography
VerifiedAdded on 2023/06/13
|9
|1901
|332
Homework Assignment
AI Summary
This assignment delves into the critical aspects of information security within ATM systems, emphasizing the importance of confidentiality, availability, and integrity. It addresses how these security principles protect user data and prevent unauthorized access, denial-of-service attacks, and data modification. The assignment also explores the challenges and potential solutions associated with biometric authentication in ATMs, including user reluctance and accuracy issues. Furthermore, it discusses scenarios where false negatives can be more detrimental than false positives in biometric systems. Finally, the assignment provides a practical example of decrypting a transposition cipher using the Caesar Cipher method, demonstrating cryptographic techniques used to secure ATM communications. This document is available on Desklib, a platform offering a wealth of study resources and solved assignments for students.

Running head: INFORMATION SECURITY SYSTEMS IN ATM
INFORMATION SECURITY SYSTEMS IN ATM
Name of the Student
Name of the University
Author’s note:
INFORMATION SECURITY SYSTEMS IN ATM
Name of the Student
Name of the University
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY SYSTEMS IN ATM
Question 1: Importance of Confidentiality, Availability and Integrity within ATM Systems
The security in the network of ATMs is extremely important. The security specification,
which is included in the security services are in much need and they are highly needed for the
users who are trying to protect their ATM cards from misuse by unauthorized users. The
confidentiality, availability and integrity of data should be the major area of concern.
Confidentiality – The network of ATM should be capable of supporting the
confidentiality of the data of the user. The confidentiality of the data means that the vital
information should not be disclosed from unauthorized parties. The statements of the bank
accounts, personal information of an individual, secrets of trade, government documents and
credit/debit card numbers should remain confidential. Encryption is highly necessary to
implement this strategy. SSL/TLS is one example of encryption, which is used to ensure the
confidentiality of data (De Gramatica et al., 2015).
Availability – The data availability refers to ensure that the accredited parties are able to
gain information of the ATM systems when they would require. Access denial has become a
common attack in the ATM network. The main aim of DDoS attacks is meant to deny users of
accessing the private information that is contained in the ATM cards (Narman et al., 2014).
Integrity of Data – The integrity of data refers to the ways in which users of the ATM
systems can protect their information from any kind of modification by unofficial parties. The
most common methods of protecting the integrity of data is to hash the received data and thus
compare it to the hash of the original message that was sent (Ramasamy & Sabatini, 2015).
Question 1: Importance of Confidentiality, Availability and Integrity within ATM Systems
The security in the network of ATMs is extremely important. The security specification,
which is included in the security services are in much need and they are highly needed for the
users who are trying to protect their ATM cards from misuse by unauthorized users. The
confidentiality, availability and integrity of data should be the major area of concern.
Confidentiality – The network of ATM should be capable of supporting the
confidentiality of the data of the user. The confidentiality of the data means that the vital
information should not be disclosed from unauthorized parties. The statements of the bank
accounts, personal information of an individual, secrets of trade, government documents and
credit/debit card numbers should remain confidential. Encryption is highly necessary to
implement this strategy. SSL/TLS is one example of encryption, which is used to ensure the
confidentiality of data (De Gramatica et al., 2015).
Availability – The data availability refers to ensure that the accredited parties are able to
gain information of the ATM systems when they would require. Access denial has become a
common attack in the ATM network. The main aim of DDoS attacks is meant to deny users of
accessing the private information that is contained in the ATM cards (Narman et al., 2014).
Integrity of Data – The integrity of data refers to the ways in which users of the ATM
systems can protect their information from any kind of modification by unofficial parties. The
most common methods of protecting the integrity of data is to hash the received data and thus
compare it to the hash of the original message that was sent (Ramasamy & Sabatini, 2015).

2INFORMATION SECURITY SYSTEMS IN ATM
Question 2:
The thief would be able to find out different possibilities of entering the keys with the
help of four functional keys. The total number of possibilities, which could be entered by the
thief are:
5P4 = 5!/(5 - 4)! = 5!/4! = 120 ways by which the thief can detect the pin of the card.
Question 3: Bio-Metric Authentication
The three possible reasons for which users are reluctant towards using bio-metrics are:
1. The biometric technology is complicated and costly to implement in various
organizations. The entire system of the deployment of biometrics would require the installation
of their personal application serves and hardware.
2. There are many situations in which there are some major problems of accuracy in
biometrics. There are many situations in which the biometric system cannot recognize the
identification of the user.
3. The users of the biometric system might have a notion that attackers might manipulate
the biometric system and thus they would gain access to their unique fingerprints. This would
lead to the loss of their personal identity as once the biometric of an individual is stolen, it cannot
be changed (Bolle et al., 2013).
The different ways of countering the issues related to biometrics are:
1. The biometric systems should be installed in such workplaces where there is a high
level of concern for the security and in disciplined workplaces. The cost benefit ratio should be
calculated before installation of the machine.
Question 2:
The thief would be able to find out different possibilities of entering the keys with the
help of four functional keys. The total number of possibilities, which could be entered by the
thief are:
5P4 = 5!/(5 - 4)! = 5!/4! = 120 ways by which the thief can detect the pin of the card.
Question 3: Bio-Metric Authentication
The three possible reasons for which users are reluctant towards using bio-metrics are:
1. The biometric technology is complicated and costly to implement in various
organizations. The entire system of the deployment of biometrics would require the installation
of their personal application serves and hardware.
2. There are many situations in which there are some major problems of accuracy in
biometrics. There are many situations in which the biometric system cannot recognize the
identification of the user.
3. The users of the biometric system might have a notion that attackers might manipulate
the biometric system and thus they would gain access to their unique fingerprints. This would
lead to the loss of their personal identity as once the biometric of an individual is stolen, it cannot
be changed (Bolle et al., 2013).
The different ways of countering the issues related to biometrics are:
1. The biometric systems should be installed in such workplaces where there is a high
level of concern for the security and in disciplined workplaces. The cost benefit ratio should be
calculated before installation of the machine.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY SYSTEMS IN ATM
2. The biometric systems have a high functionality level. The biometric system should be
efficient in order to validate the identity of a person properly by comparing it with the captured
characteristic of the biometric. Based on the validation process, the biometric would be able to
identify the authentic person.
3. The biometric system should be able to recognize a person based on a feature vector
that would be derived from a precise behavioral or physiological characteristic that is mainly
possessed by the person. Hence, the loss of personal identity should not be considered as
biometric systems are highly efficient in nature (Smith, 2013)
Question 4: Circumstances in which False Negatives are Serious than False Positives
False positive rate is the kind of solution when the identity of an unauthenticated user is
accepted that should had been rejected. The false negative is a kind of situation when there is a
rejection by an unauthenticated user instead of an acceptation. A false negative situation in a
biometric system occurs when the system would fail to recognize the authenticity of an
individual. This would lead to something, which might not happen. The false negative and the
false positive are such complimentary situations, which share an inverse relation. As the rate of
the authentication of the false positive increases, the rate of the authentication of the false
negative decreases and this process occurs vice-versa.
The two situations in which the false negatives are serious than false positives are:
1. Personal: The owner of a safe would be prevented from accessing the safe. This might
lead the person being unable to access a particular necessary resource.
2. Institutions: If a situation occurs when the entire infrastructure of the server would be
down and the user needs to access the data center for the service of restoration of the data. In
2. The biometric systems have a high functionality level. The biometric system should be
efficient in order to validate the identity of a person properly by comparing it with the captured
characteristic of the biometric. Based on the validation process, the biometric would be able to
identify the authentic person.
3. The biometric system should be able to recognize a person based on a feature vector
that would be derived from a precise behavioral or physiological characteristic that is mainly
possessed by the person. Hence, the loss of personal identity should not be considered as
biometric systems are highly efficient in nature (Smith, 2013)
Question 4: Circumstances in which False Negatives are Serious than False Positives
False positive rate is the kind of solution when the identity of an unauthenticated user is
accepted that should had been rejected. The false negative is a kind of situation when there is a
rejection by an unauthenticated user instead of an acceptation. A false negative situation in a
biometric system occurs when the system would fail to recognize the authenticity of an
individual. This would lead to something, which might not happen. The false negative and the
false positive are such complimentary situations, which share an inverse relation. As the rate of
the authentication of the false positive increases, the rate of the authentication of the false
negative decreases and this process occurs vice-versa.
The two situations in which the false negatives are serious than false positives are:
1. Personal: The owner of a safe would be prevented from accessing the safe. This might
lead the person being unable to access a particular necessary resource.
2. Institutions: If a situation occurs when the entire infrastructure of the server would be
down and the user needs to access the data center for the service of restoration of the data. In
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY SYSTEMS IN ATM
such a situation, if the biometric system does not recognize the user then the organization could
lose a lot of money and reputation of the organization.
Question 5: Transposition
In cryptography techniques, a transposition cipher is one kind of method of encryption in
which the positions, which are held by plaintext units would be shifted based on a regular
system. In this method, the cipher text creates a permutation of the plain text. In this permutation
the order of the units are altered. With respect to the theory of mathematics, a bijective function
is used on the positioning of the characters that are meant to encrypt them and an inverse
function is used to decrypt the positioning of the characters (Mishra, 2013).
The one way in which a piece of cipher text could be determined quickly as a result of
transposition is Rail Fence Cipher. This is a kind of cipher transposition in which the plaintext is
written in a downwards format on the successive rails of an imaginary fence and then it shifts
upwards. The message of this plaintext is then read in rows.
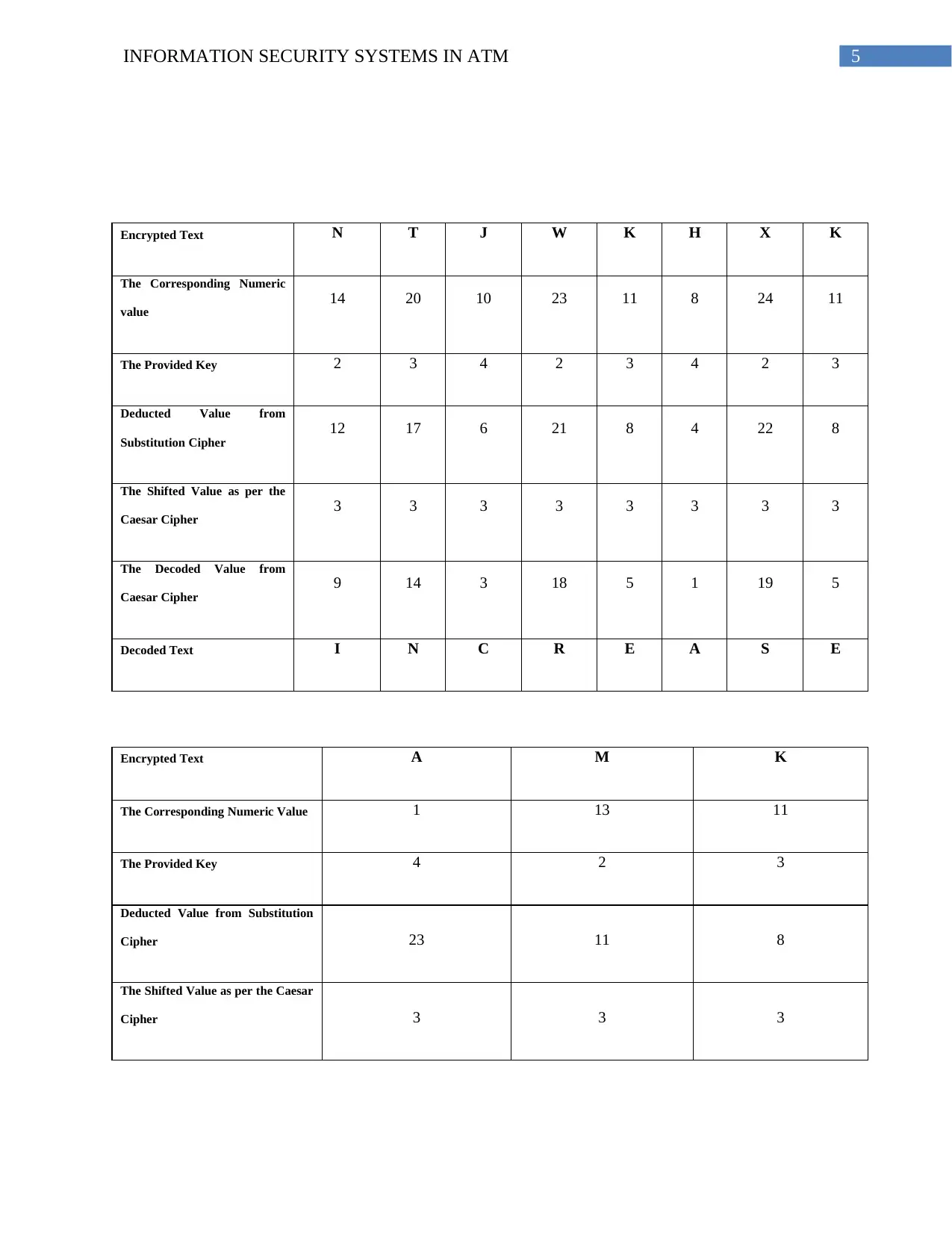
The provided encrypted text is: NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
The key, which is provided is: 234
With the help of the algorithm of Caesar Cipher and the method of substitution, the
encrypted text would be decrypted as follows:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
such a situation, if the biometric system does not recognize the user then the organization could
lose a lot of money and reputation of the organization.
Question 5: Transposition
In cryptography techniques, a transposition cipher is one kind of method of encryption in
which the positions, which are held by plaintext units would be shifted based on a regular
system. In this method, the cipher text creates a permutation of the plain text. In this permutation
the order of the units are altered. With respect to the theory of mathematics, a bijective function
is used on the positioning of the characters that are meant to encrypt them and an inverse
function is used to decrypt the positioning of the characters (Mishra, 2013).
The one way in which a piece of cipher text could be determined quickly as a result of
transposition is Rail Fence Cipher. This is a kind of cipher transposition in which the plaintext is
written in a downwards format on the successive rails of an imaginary fence and then it shifts
upwards. The message of this plaintext is then read in rows.
The provided encrypted text is: NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
The key, which is provided is: 234
With the help of the algorithm of Caesar Cipher and the method of substitution, the
encrypted text would be decrypted as follows:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
5INFORMATION SECURITY SYSTEMS IN ATM
Encrypted Text N T J W K H X K
The Corresponding Numeric
value
14 20 10 23 11 8 24 11
The Provided Key 2 3 4 2 3 4 2 3
Deducted Value from
Substitution Cipher
12 17 6 21 8 4 22 8
The Shifted Value as per the
Caesar Cipher
3 3 3 3 3 3 3 3
The Decoded Value from
Caesar Cipher
9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
The Corresponding Numeric Value 1 13 11
The Provided Key 4 2 3
Deducted Value from Substitution
Cipher 23 11 8
The Shifted Value as per the Caesar
Cipher 3 3 3
Encrypted Text N T J W K H X K
The Corresponding Numeric
value
14 20 10 23 11 8 24 11
The Provided Key 2 3 4 2 3 4 2 3
Deducted Value from
Substitution Cipher
12 17 6 21 8 4 22 8
The Shifted Value as per the
Caesar Cipher
3 3 3 3 3 3 3 3
The Decoded Value from
Caesar Cipher
9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
The Corresponding Numeric Value 1 13 11
The Provided Key 4 2 3
Deducted Value from Substitution
Cipher 23 11 8
The Shifted Value as per the Caesar
Cipher 3 3 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6INFORMATION SECURITY SYSTEMS IN ATM
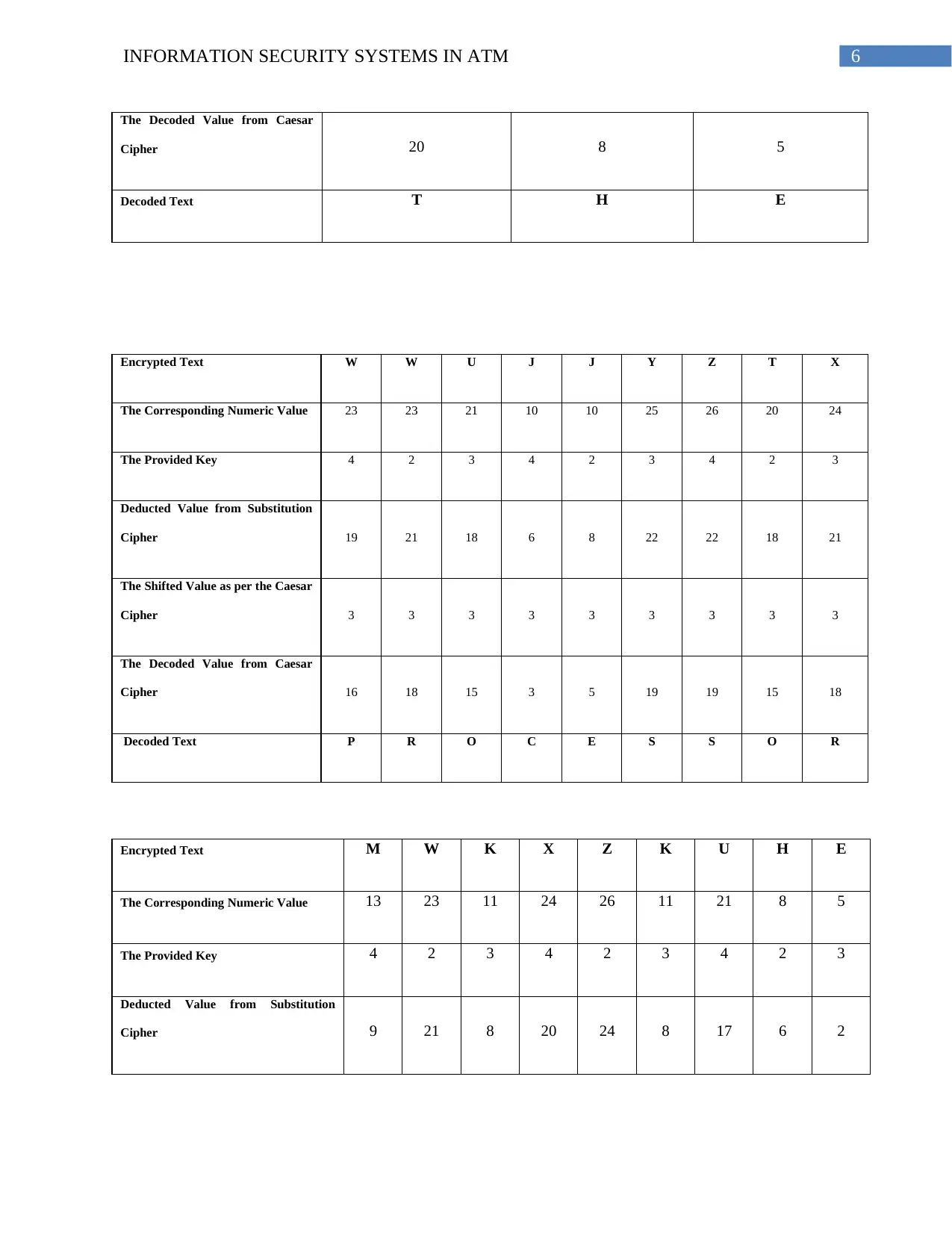
The Decoded Value from Caesar
Cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
The Corresponding Numeric Value 23 23 21 10 10 25 26 20 24
The Provided Key 4 2 3 4 2 3 4 2 3
Deducted Value from Substitution
Cipher 19 21 18 6 8 22 22 18 21
The Shifted Value as per the Caesar
Cipher 3 3 3 3 3 3 3 3 3
The Decoded Value from Caesar
Cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
The Corresponding Numeric Value 13 23 11 24 26 11 21 8 5
The Provided Key 4 2 3 4 2 3 4 2 3
Deducted Value from Substitution
Cipher 9 21 8 20 24 8 17 6 2
The Decoded Value from Caesar
Cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
The Corresponding Numeric Value 23 23 21 10 10 25 26 20 24
The Provided Key 4 2 3 4 2 3 4 2 3
Deducted Value from Substitution
Cipher 19 21 18 6 8 22 22 18 21
The Shifted Value as per the Caesar
Cipher 3 3 3 3 3 3 3 3 3
The Decoded Value from Caesar
Cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
The Corresponding Numeric Value 13 23 11 24 26 11 21 8 5
The Provided Key 4 2 3 4 2 3 4 2 3
Deducted Value from Substitution
Cipher 9 21 8 20 24 8 17 6 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7INFORMATION SECURITY SYSTEMS IN ATM
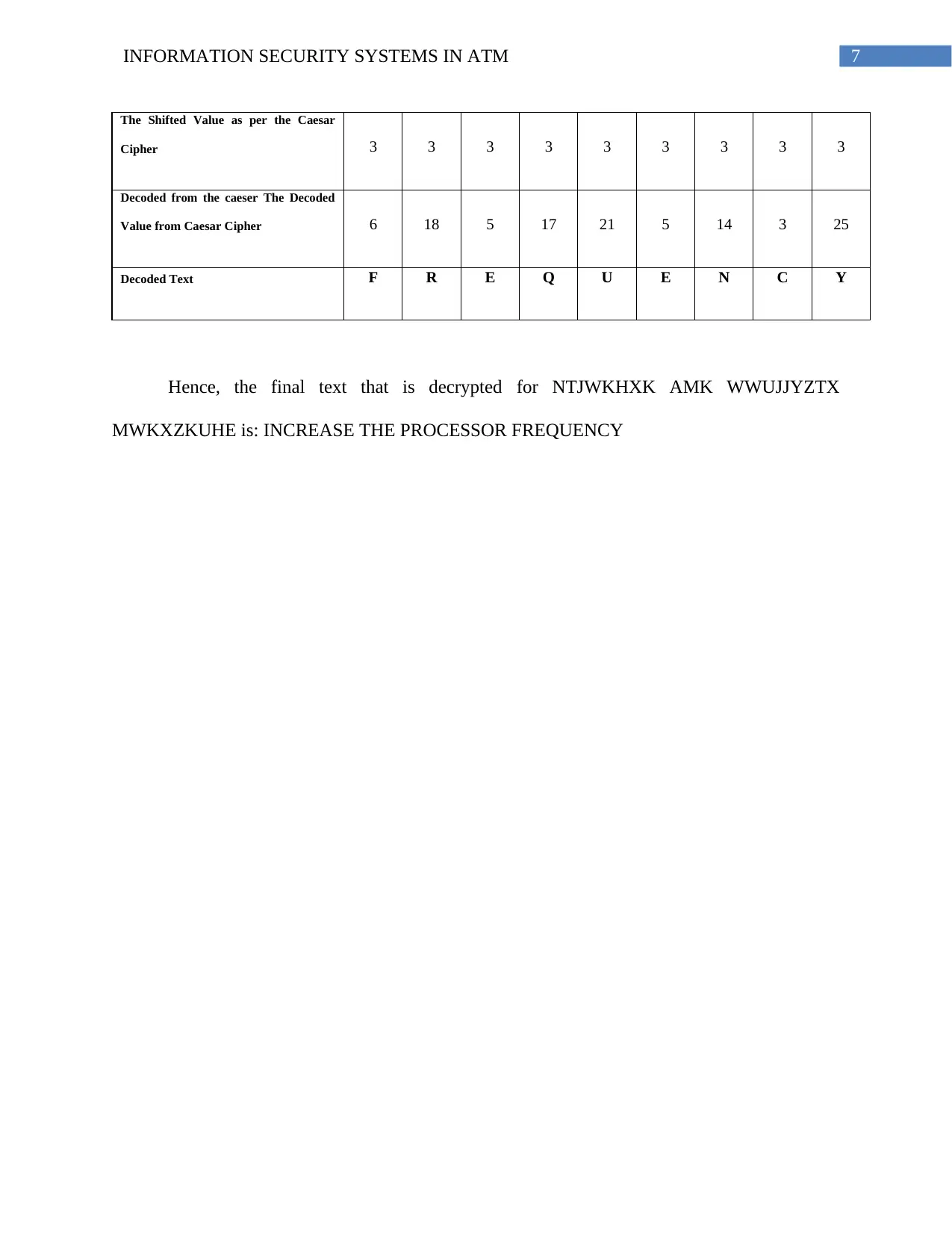
The Shifted Value as per the Caesar
Cipher 3 3 3 3 3 3 3 3 3
Decoded from the caeser The Decoded
Value from Caesar Cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Hence, the final text that is decrypted for NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is: INCREASE THE PROCESSOR FREQUENCY
The Shifted Value as per the Caesar
Cipher 3 3 3 3 3 3 3 3 3
Decoded from the caeser The Decoded
Value from Caesar Cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Hence, the final text that is decrypted for NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is: INCREASE THE PROCESSOR FREQUENCY

8INFORMATION SECURITY SYSTEMS IN ATM
References
Bolle, R. M., Connell, J. H., Pankanti, S., Ratha, N. K., & Senior, A. W. (2013). Guide to
biometrics. Springer Science & Business Media.
De Gramatica, M., Labunets, K., Massacci, F., Paci, F., & Tedeschi, A. (2015, March). The role
of catalogues of threats and security controls in security risk assessment: an empirical
study with ATM professionals. In International Working Conference on Requirements
Engineering: Foundation for Software Quality (pp. 98-114). Springer, Cham.
Mishra, A. (2013). Enhancing security of caesar cipher using different methods. International
Journal of Research in Engineering and Technology, 2(09), 327-332.
Närman, P., Franke, U., König, J., Buschle, M., & Ekstedt, M. (2014). Enterprise architecture
availability analysis using fault trees and stakeholder interviews. Enterprise Information
Systems, 8(1), 1-25.
Ramasamy, S., & Sabatini, R. (2015). Communication, navigation and surveillance performance
criteria for safety-critical avionics and ATM systems. In AIAC 16: Multinatioinal
Aerospace Programs-Benefits and Challenges (pp. 1-12). Engineers Australia.
Smith, R. G. (2013). Biometric solutions to identity-related cybercrime. In Crime online (pp. 54-
69). Willan.
References
Bolle, R. M., Connell, J. H., Pankanti, S., Ratha, N. K., & Senior, A. W. (2013). Guide to
biometrics. Springer Science & Business Media.
De Gramatica, M., Labunets, K., Massacci, F., Paci, F., & Tedeschi, A. (2015, March). The role
of catalogues of threats and security controls in security risk assessment: an empirical
study with ATM professionals. In International Working Conference on Requirements
Engineering: Foundation for Software Quality (pp. 98-114). Springer, Cham.
Mishra, A. (2013). Enhancing security of caesar cipher using different methods. International
Journal of Research in Engineering and Technology, 2(09), 327-332.
Närman, P., Franke, U., König, J., Buschle, M., & Ekstedt, M. (2014). Enterprise architecture
availability analysis using fault trees and stakeholder interviews. Enterprise Information
Systems, 8(1), 1-25.
Ramasamy, S., & Sabatini, R. (2015). Communication, navigation and surveillance performance
criteria for safety-critical avionics and ATM systems. In AIAC 16: Multinatioinal
Aerospace Programs-Benefits and Challenges (pp. 1-12). Engineers Australia.
Smith, R. G. (2013). Biometric solutions to identity-related cybercrime. In Crime online (pp. 54-
69). Willan.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



