ATM System Modelling: Sequence Diagram for Transaction Subsystem
VerifiedAdded on 2023/06/11
|18
|3089
|466
AI Summary
This article discusses the ATM system modelling and its sequence diagram for transaction subsystem. It covers the system documentation, transactions, components, operations, and feedback mechanism. It also provides insights into the database and backend processing system.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: OBJECT MODELING 1
ATM System Modelling
Author Name(s), First M. Last, Omit Titles and Degrees
Institutional Affiliation(s)
Author Note
Include any grant/funding information and a complete correspondence address.
ATM System Modelling
Author Name(s), First M. Last, Omit Titles and Degrees
Institutional Affiliation(s)
Author Note
Include any grant/funding information and a complete correspondence address.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

OBJECT MODELLING 2
Contents
System Modelling................................................................................................................5
Sequence diagram for the transaction subsystem of the ATM........................................5
System Documentation........................................................................................................9
System Transactions............................................................................................................9
Cash Withdrawal.............................................................................................................9
Cash Deposit....................................................................................................................9
Amount Transfer..............................................................................................................9
System Components............................................................................................................9
The card Reader...............................................................................................................9
The Keypad....................................................................................................................10
The Printer.....................................................................................................................10
The screen......................................................................................................................11
System Operations.............................................................................................................11
Authentication................................................................................................................11
ATM Withdrawal...........................................................................................................12
Depositing Funds...........................................................................................................12
Transfer Money.............................................................................................................13
Data communication..........................................................................................................13
Session handling................................................................................................................14
Contents
System Modelling................................................................................................................5
Sequence diagram for the transaction subsystem of the ATM........................................5
System Documentation........................................................................................................9
System Transactions............................................................................................................9
Cash Withdrawal.............................................................................................................9
Cash Deposit....................................................................................................................9
Amount Transfer..............................................................................................................9
System Components............................................................................................................9
The card Reader...............................................................................................................9
The Keypad....................................................................................................................10
The Printer.....................................................................................................................10
The screen......................................................................................................................11
System Operations.............................................................................................................11
Authentication................................................................................................................11
ATM Withdrawal...........................................................................................................12
Depositing Funds...........................................................................................................12
Transfer Money.............................................................................................................13
Data communication..........................................................................................................13
Session handling................................................................................................................14

OBJECT MODELLING 3
Feedback mechanism.........................................................................................................14
The database......................................................................................................................14
The backend processing system.........................................................................................15
Summary............................................................................................................................15
Conclusion.........................................................................................................................15
Recommendations..............................................................................................................15
Feedback mechanism.........................................................................................................14
The database......................................................................................................................14
The backend processing system.........................................................................................15
Summary............................................................................................................................15
Conclusion.........................................................................................................................15
Recommendations..............................................................................................................15

OBJECT MODELLING 4
Table of figures
Figure 1............................................................................................................................................5
Figure 2. Withdrawal Transaction...................................................................................................6
Figure 3. Deposit Transaction..........................................................................................................7
Figure 4. Money Transfer................................................................................................................8
Table of figures
Figure 1............................................................................................................................................5
Figure 2. Withdrawal Transaction...................................................................................................6
Figure 3. Deposit Transaction..........................................................................................................7
Figure 4. Money Transfer................................................................................................................8
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
OBJECT MODELLING 5
System Modelling
Sequence diagram for the transaction subsystem of the ATM
Sequnce diagrams allow engineers to model complex systems that interate functionality
that may be difficult to understand without proper visual representation (Campean & Yildirim,
2017). Thus by use of sequnce diagrams we can be able to show how a certain processing task is
carried out through sending messages between the interacting entities(Refsdal, Husa, & Stølen,
2005). From the use cases defined in the system design, we can be able to decompose the ATM
system into various subsystems. One major sub-system we can derive is the transaction module.
This part is composed of activities that involve the moving cash from one’s account to another or
from the account to physical cash and vice versa. The use case diagram is shown below.
Figure 1. Collins ATM Transaction Subsystem Use Cases
Withraw Cash
Withraw Cash
Withraw Cash
System Modelling
Sequence diagram for the transaction subsystem of the ATM
Sequnce diagrams allow engineers to model complex systems that interate functionality
that may be difficult to understand without proper visual representation (Campean & Yildirim,
2017). Thus by use of sequnce diagrams we can be able to show how a certain processing task is
carried out through sending messages between the interacting entities(Refsdal, Husa, & Stølen,
2005). From the use cases defined in the system design, we can be able to decompose the ATM
system into various subsystems. One major sub-system we can derive is the transaction module.
This part is composed of activities that involve the moving cash from one’s account to another or
from the account to physical cash and vice versa. The use case diagram is shown below.
Figure 1. Collins ATM Transaction Subsystem Use Cases
Withraw Cash
Withraw Cash
Withraw Cash
OBJECT MODELLING 6
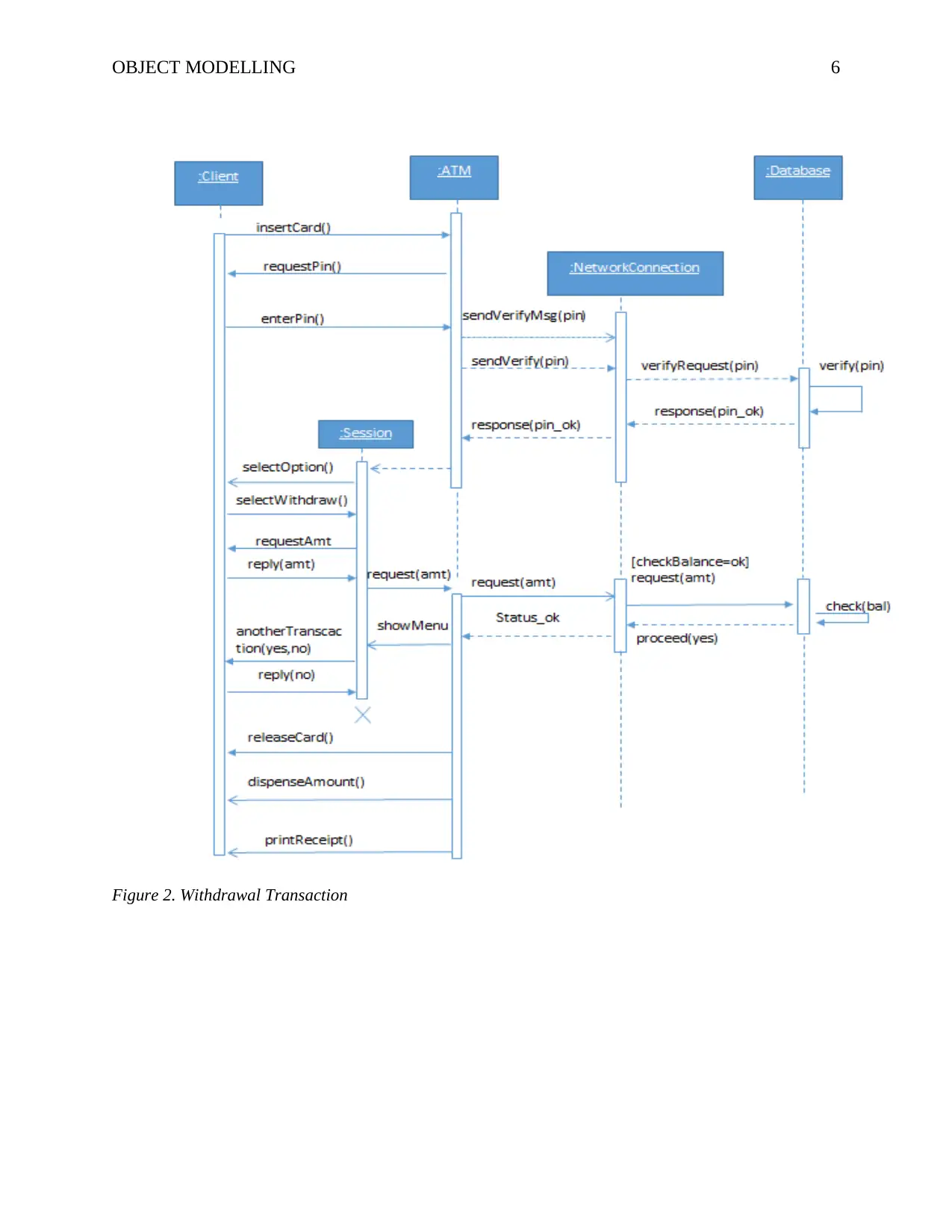
Figure 2. Withdrawal Transaction
Figure 2. Withdrawal Transaction
OBJECT MODELLING 7
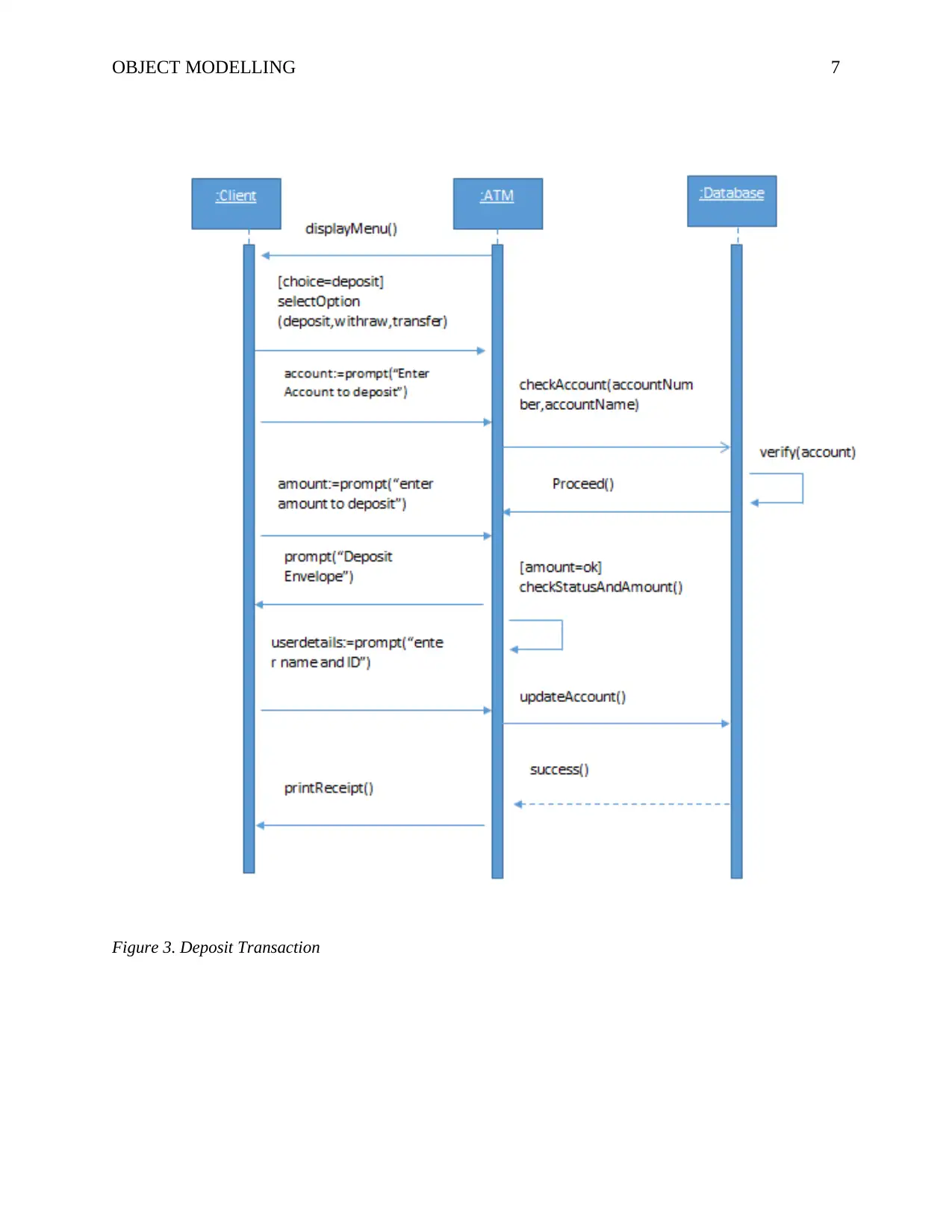
Figure 3. Deposit Transaction
Figure 3. Deposit Transaction
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
OBJECT MODELLING 8
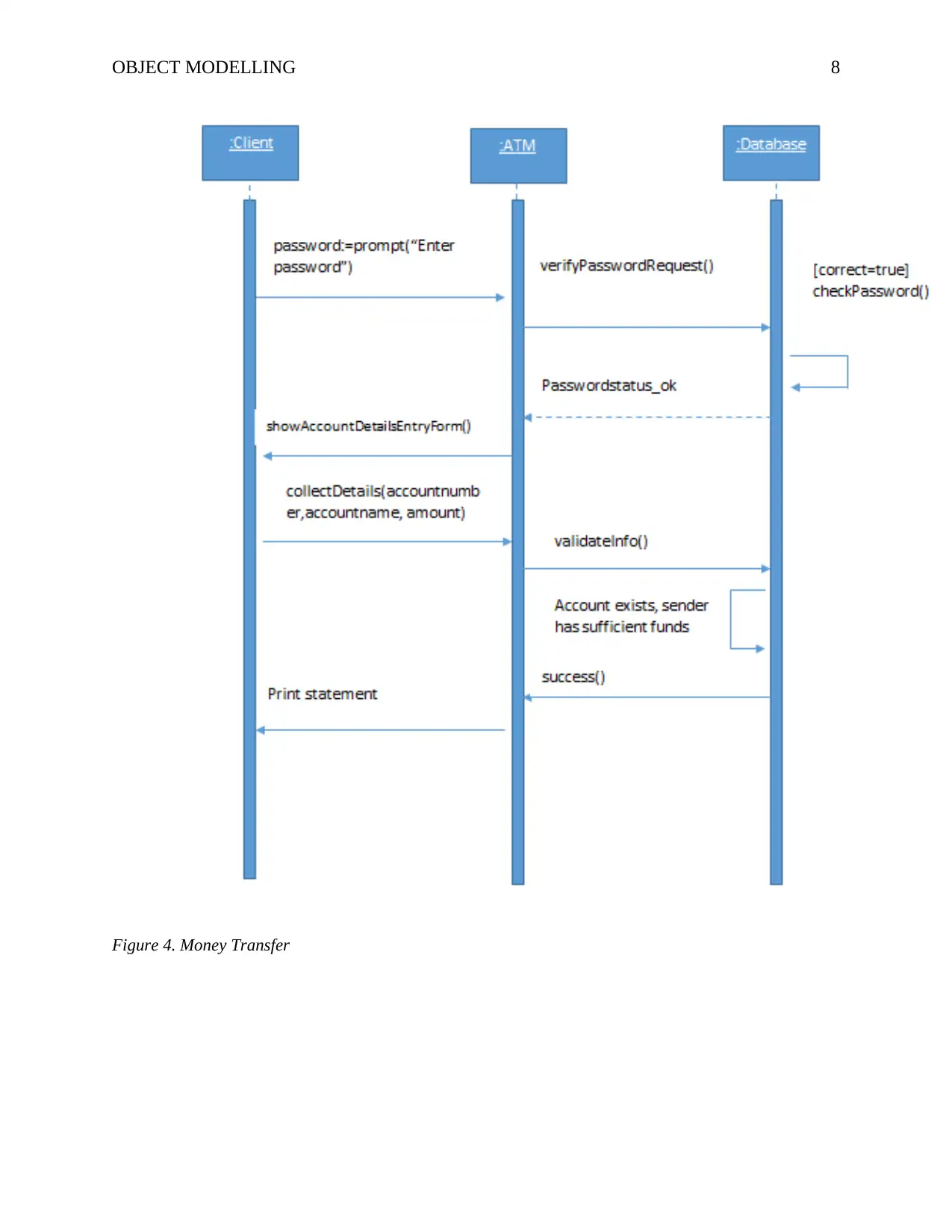
Figure 4. Money Transfer
Figure 4. Money Transfer

OBJECT MODELLING 9
System Documentation
The ATM system acts as the interface between the customers and the bank. It totally
eliminates the need for customers to visit the bank for basic transactions that can be self-served
(Saleh, 2016).
System Transactions
Our case study is modeled after the ATM to perform the following truncations:
Cash Withdrawal
Cash withdrawal transactions involve the transfer of money from the user’s account to
hard cash. During this process, the account is debited and the user is handed the money through
the cash dispenser.
Cash Deposit
Under this transaction, the user is able to add money to his/her account or even to
someone else’s account.
Amount Transfer
These services are offered by the ATM system and therefore, they are very important to
discuss. This is because they are at the heart of operation of any bank. They function by giving
direct service to the client thus adding a lot of value to the service model of any bank.
System Components
The transaction subsystem is made up of both hardware and software. The hardware
components involved in the operation of the ATM Transaction subsystem are:
The card Reader
This is the first component that the user interacts with on reaching the ATM. The card
reader is mostly located on the right of the system. It has an indicator light to be guide the user
System Documentation
The ATM system acts as the interface between the customers and the bank. It totally
eliminates the need for customers to visit the bank for basic transactions that can be self-served
(Saleh, 2016).
System Transactions
Our case study is modeled after the ATM to perform the following truncations:
Cash Withdrawal
Cash withdrawal transactions involve the transfer of money from the user’s account to
hard cash. During this process, the account is debited and the user is handed the money through
the cash dispenser.
Cash Deposit
Under this transaction, the user is able to add money to his/her account or even to
someone else’s account.
Amount Transfer
These services are offered by the ATM system and therefore, they are very important to
discuss. This is because they are at the heart of operation of any bank. They function by giving
direct service to the client thus adding a lot of value to the service model of any bank.
System Components
The transaction subsystem is made up of both hardware and software. The hardware
components involved in the operation of the ATM Transaction subsystem are:
The card Reader
This is the first component that the user interacts with on reaching the ATM. The card
reader is mostly located on the right of the system. It has an indicator light to be guide the user

OBJECT MODELLING 10
on how to insert the card. The Card reader reads the details and sends them to the transaction
processing system within the bank. In this design, the card reader acts in a similar fashion. From
the withdrawal sequence diagram (figure 2) above, the card initiates the transaction process.
Once the user enters the card, it triggers the ATM to request for password. This is the beginning
of the transaction. The card must be well inserted or the card reader will not be able read the
account information.
The Keypad
This part of the ATM is used for entering user input into the system. It may be a physical
keypad or a virtual keypad that appears on the screen. This keypad is very basic with only
numeric values and some special keys such as delete and send. This is because the ATM does not
handle very complex information from the user. In most cases, user input includes only selection
or entering numeric data such as amount or account number.
The Printer
The printer is used to produce hardcopy document containing information about the
transaction that has been carried out. The output from this device depends on whether the user
has instructed the ATM to produce the receipt or the document. The printer used is the thermal
printer. The output from the printer is very basic.
Cash dispenser
The cash dispenser is used to transfer the physical or hard cash from the bank to the
client. When this happens, the client’s account is debited and a similar amount of money is
released by the cash dispenser.
on how to insert the card. The Card reader reads the details and sends them to the transaction
processing system within the bank. In this design, the card reader acts in a similar fashion. From
the withdrawal sequence diagram (figure 2) above, the card initiates the transaction process.
Once the user enters the card, it triggers the ATM to request for password. This is the beginning
of the transaction. The card must be well inserted or the card reader will not be able read the
account information.
The Keypad
This part of the ATM is used for entering user input into the system. It may be a physical
keypad or a virtual keypad that appears on the screen. This keypad is very basic with only
numeric values and some special keys such as delete and send. This is because the ATM does not
handle very complex information from the user. In most cases, user input includes only selection
or entering numeric data such as amount or account number.
The Printer
The printer is used to produce hardcopy document containing information about the
transaction that has been carried out. The output from this device depends on whether the user
has instructed the ATM to produce the receipt or the document. The printer used is the thermal
printer. The output from the printer is very basic.
Cash dispenser
The cash dispenser is used to transfer the physical or hard cash from the bank to the
client. When this happens, the client’s account is debited and a similar amount of money is
released by the cash dispenser.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

OBJECT MODELLING 11
The screen
This is the main output device for the ATM. Any instructions will be displayed on this
device. It also acts as the input device for the system that implement the virtual keypad.
System Operations
Authentication
Authentication is very important to ensure that the person who is carrying out the
transaction is the owner of the card (Mondal, Deb, & Adnan, 2017)
When the user inserts the card into the card reader, he/she is prompted for a password. In
order to be able to enter this information, the user interacts with the second hardware component,
the keypad. Although there has been newer systems that have done away with the keypad, many
system still utilize this hardware component. When the user types the password, the information
is read by the ATM main processing unit. This information is then sent to the backend
processing for validation. This is achieved through the transmission of data over the network. In
the case of withdrawal shown in figure 2, this is achieved via the “sendVerifyMsg” function that
takes the pin as the input. Once this information is received by the backend processing system,
the pin is checked against the one stored on the database.
A proceed message is sent back to the ATM if the PIN is found to be correct. This allows
the transaction to proceed as required. The ATM then displays the use a list of options to select
the type of transaction. Here, in our model ATM system, this can either be withdrawing of cash,
change of PIN, depositing money, updating passbook or checking of balance. The user selects
the option in order to proceed. In case of invalid request, the session will be terminated and the
user required to enter the password again.
The screen
This is the main output device for the ATM. Any instructions will be displayed on this
device. It also acts as the input device for the system that implement the virtual keypad.
System Operations
Authentication
Authentication is very important to ensure that the person who is carrying out the
transaction is the owner of the card (Mondal, Deb, & Adnan, 2017)
When the user inserts the card into the card reader, he/she is prompted for a password. In
order to be able to enter this information, the user interacts with the second hardware component,
the keypad. Although there has been newer systems that have done away with the keypad, many
system still utilize this hardware component. When the user types the password, the information
is read by the ATM main processing unit. This information is then sent to the backend
processing for validation. This is achieved through the transmission of data over the network. In
the case of withdrawal shown in figure 2, this is achieved via the “sendVerifyMsg” function that
takes the pin as the input. Once this information is received by the backend processing system,
the pin is checked against the one stored on the database.
A proceed message is sent back to the ATM if the PIN is found to be correct. This allows
the transaction to proceed as required. The ATM then displays the use a list of options to select
the type of transaction. Here, in our model ATM system, this can either be withdrawing of cash,
change of PIN, depositing money, updating passbook or checking of balance. The user selects
the option in order to proceed. In case of invalid request, the session will be terminated and the
user required to enter the password again.

OBJECT MODELLING 12
ATM Withdrawal
When the user selects the correct option, say for example withdrawal of funds, the ATM
will prompt the user to enter the amount to withdraw. When the user responds with the amount,
the system will send a request to the backend database to check whether the user has sufficient
funds. If the funds are available, the system will send a message to the cash dispenser to dispense
the cash. Before this can happen, the ATM will prompt the user whether he/she would like to do
another transaction. If the answer is no, the ATM will release the card and dispense the cash
from the cash dispenser. In case of a response to the contrary, the ATM will dispense the cash
and still hold the card waiting for another instruction. If no transaction is given the ATM will
release the card and print the receipt and the session will be closed.
Depositing Funds
In this model system, the transaction would have taken a different route if the user had
selected deposit of funds instead of withdrawal. The ATM would have prompted the user to enter
the account to deposit to. After receiving the input of the account number, the ATM will then
send the number to the backend processing system to validate the existence of the account. This
process is carried out in order to reduce the chances of clients depositing money into inexistent
or flagged accounts to prevent fraud (Ibrahim, Mishra, & Barroon, 2010). When the account is
found, the system prompts the user to enter the amount that he/she wants to deposit. After the
user types the amount, the ATM will wait for the envelope containing the money to be deposited
in the ATM deposit box. Here the ATM will verify the amount that has been deposited to ensure
that it is the same as the user has typed into the system. When the amount match the user input,
the system will send a message to the backend processing system to credit the account. Once the
process is complete, the ATM will print the deposit slip to the user as a proof of payment.
ATM Withdrawal
When the user selects the correct option, say for example withdrawal of funds, the ATM
will prompt the user to enter the amount to withdraw. When the user responds with the amount,
the system will send a request to the backend database to check whether the user has sufficient
funds. If the funds are available, the system will send a message to the cash dispenser to dispense
the cash. Before this can happen, the ATM will prompt the user whether he/she would like to do
another transaction. If the answer is no, the ATM will release the card and dispense the cash
from the cash dispenser. In case of a response to the contrary, the ATM will dispense the cash
and still hold the card waiting for another instruction. If no transaction is given the ATM will
release the card and print the receipt and the session will be closed.
Depositing Funds
In this model system, the transaction would have taken a different route if the user had
selected deposit of funds instead of withdrawal. The ATM would have prompted the user to enter
the account to deposit to. After receiving the input of the account number, the ATM will then
send the number to the backend processing system to validate the existence of the account. This
process is carried out in order to reduce the chances of clients depositing money into inexistent
or flagged accounts to prevent fraud (Ibrahim, Mishra, & Barroon, 2010). When the account is
found, the system prompts the user to enter the amount that he/she wants to deposit. After the
user types the amount, the ATM will wait for the envelope containing the money to be deposited
in the ATM deposit box. Here the ATM will verify the amount that has been deposited to ensure
that it is the same as the user has typed into the system. When the amount match the user input,
the system will send a message to the backend processing system to credit the account. Once the
process is complete, the ATM will print the deposit slip to the user as a proof of payment.

OBJECT MODELLING 13
Transfer Money
The ATM system allows the user to transfer money from the his/her account to another
users account or to a different account owned by the user. The process is initiated when the user
is presented with a choice to select by the ATM. This prompt will include all the possible
services that are offered by the ATM. In response, the user should select Money Transfer. Since
this is a risky operation, unlike the deposit transaction, the ATM will require the user to
authenticate him/herself. Therefore, the system will prompt the user to enter password to
continue. The user will therefore type the password and the ATM messaging system will send
the details to the backend processing system to verify them against the one persistent on the
database. If the details match, the use will be prompted to enter account to transfer the money to.
The same process of verification of the account will be executed. The system will also check
whether the user has sufficient funds to do the transfer. If this checks out, the transaction will be
persisted and the ATM will print the statement with the transfer status.
Data communication
The transfer of information between the ATM and the backend processing system takes
place over the network. This process is initiate by the ATM the moment the customer enters the
pin. This is because the PIN has to be verified by comparing with the one already stored in the
database. Other events that lead to the creation of a network session include verifying whether
the account has sufficient funds and verifying whether a bank account exists. However data
transfer between the ATM and the bank is limited and takes place only when necessary.
Otherwise much of the interaction occurs between the user and the ATM. This communication
can also occur with other third party networks either through regional or national EFT networks
(Hayashi, Sullivan, & Weiner, 2003), and mobile money transfers and withdrawals for
Transfer Money
The ATM system allows the user to transfer money from the his/her account to another
users account or to a different account owned by the user. The process is initiated when the user
is presented with a choice to select by the ATM. This prompt will include all the possible
services that are offered by the ATM. In response, the user should select Money Transfer. Since
this is a risky operation, unlike the deposit transaction, the ATM will require the user to
authenticate him/herself. Therefore, the system will prompt the user to enter password to
continue. The user will therefore type the password and the ATM messaging system will send
the details to the backend processing system to verify them against the one persistent on the
database. If the details match, the use will be prompted to enter account to transfer the money to.
The same process of verification of the account will be executed. The system will also check
whether the user has sufficient funds to do the transfer. If this checks out, the transaction will be
persisted and the ATM will print the statement with the transfer status.
Data communication
The transfer of information between the ATM and the backend processing system takes
place over the network. This process is initiate by the ATM the moment the customer enters the
pin. This is because the PIN has to be verified by comparing with the one already stored in the
database. Other events that lead to the creation of a network session include verifying whether
the account has sufficient funds and verifying whether a bank account exists. However data
transfer between the ATM and the bank is limited and takes place only when necessary.
Otherwise much of the interaction occurs between the user and the ATM. This communication
can also occur with other third party networks either through regional or national EFT networks
(Hayashi, Sullivan, & Weiner, 2003), and mobile money transfers and withdrawals for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OBJECT MODELLING 14
correspondent banking (Mettenheim et al., 2014). This is because the transaction may be
interbank cash transfer or withdrawal by a client who is not a member of the bank.
Session handling
Each transaction that takes place occurs within a session. A session is used to structure
communication between the communicating entities over the period of communication (Dezani
& De’Liguoro, 2009). A session is created once the customer is requested for a pin and it is
verified. This session is alive as long as the customer has not terminated the current ongoing
transaction. Whenever the session is closed, the user will be required to enter the PIN again
before another session is established. Due to the nature of the ATM, there cannot be two sessions
going on at the same time. The user has to interact with only one session. The session represents
an actual processing. Thus a client cannot have two transactions going on at the same time. For
example, a user cannot be withdrawing money while at the same time he/she is sending money.
Each session will present the user with various options depending on the type of transaction
chosen.
Feedback mechanism
This functionality is implemented in order to be able to inform the user of the status of
the ongoing transaction. This mostly occurs through the screen and the speakers. When the ATM
requires any user action, it will display on the screen as well as play the prompts on the speakers.
The speakers complement the screen to ensure that the user does not fail to get the message.
The database
The ATM database sits at the bank’s headquarters on a secure network. All account
information is stored on this database. Any transaction process cannot proceed without
connecting to the database. However, the connection is closed as soon as information is read or
correspondent banking (Mettenheim et al., 2014). This is because the transaction may be
interbank cash transfer or withdrawal by a client who is not a member of the bank.
Session handling
Each transaction that takes place occurs within a session. A session is used to structure
communication between the communicating entities over the period of communication (Dezani
& De’Liguoro, 2009). A session is created once the customer is requested for a pin and it is
verified. This session is alive as long as the customer has not terminated the current ongoing
transaction. Whenever the session is closed, the user will be required to enter the PIN again
before another session is established. Due to the nature of the ATM, there cannot be two sessions
going on at the same time. The user has to interact with only one session. The session represents
an actual processing. Thus a client cannot have two transactions going on at the same time. For
example, a user cannot be withdrawing money while at the same time he/she is sending money.
Each session will present the user with various options depending on the type of transaction
chosen.
Feedback mechanism
This functionality is implemented in order to be able to inform the user of the status of
the ongoing transaction. This mostly occurs through the screen and the speakers. When the ATM
requires any user action, it will display on the screen as well as play the prompts on the speakers.
The speakers complement the screen to ensure that the user does not fail to get the message.
The database
The ATM database sits at the bank’s headquarters on a secure network. All account
information is stored on this database. Any transaction process cannot proceed without
connecting to the database. However, the connection is closed as soon as information is read or

OBJECT MODELLING 15
written. This is to avoid long running processes that would lead to the database becoming
unavailable due to too many connections.
The backend processing system
This system will accept requests from the ATM, process the information and give the
result. The ATM is limited in functionality and therefore relies heavily on this system. This
system sit on a very powerful computer in order to be able to perform very fast.
Summary
The ATM system is composed of the input system, the processing system and the output
system. The input system is composed of the keypad, the card reader and the envelop deposit
box. The output system is made up of the screen, the speakers, the printer and the cash dispenser.
The processing unit is made up of the minimal ATM processing functionality and the robust
backend processing system.
Conclusion
The ATM system is highly structured and well modeled to fit within the business model
of the bank. All the transaction paths are defined as well as the user input. This model allows the
ATM to operate at minimal processing needs as well as avoid common pitfalls that could prove
catastrophic in a banking environment.
Recommendations
Although the current system is able to meet the needs of the users, more features would
be added to enhance service delivery as well as security. A good example would be to use
biometric authentication instead of the PIN. Both could also be used for even more security. The
system could also use three factor authentication. This is because the ATM card on its own is
written. This is to avoid long running processes that would lead to the database becoming
unavailable due to too many connections.
The backend processing system
This system will accept requests from the ATM, process the information and give the
result. The ATM is limited in functionality and therefore relies heavily on this system. This
system sit on a very powerful computer in order to be able to perform very fast.
Summary
The ATM system is composed of the input system, the processing system and the output
system. The input system is composed of the keypad, the card reader and the envelop deposit
box. The output system is made up of the screen, the speakers, the printer and the cash dispenser.
The processing unit is made up of the minimal ATM processing functionality and the robust
backend processing system.
Conclusion
The ATM system is highly structured and well modeled to fit within the business model
of the bank. All the transaction paths are defined as well as the user input. This model allows the
ATM to operate at minimal processing needs as well as avoid common pitfalls that could prove
catastrophic in a banking environment.
Recommendations
Although the current system is able to meet the needs of the users, more features would
be added to enhance service delivery as well as security. A good example would be to use
biometric authentication instead of the PIN. Both could also be used for even more security. The
system could also use three factor authentication. This is because the ATM card on its own is

OBJECT MODELLING 16
subject to many security threats such as skimming and cloning (Iyabode, Nureni, F. Adebayo, &
A. Olamide, 2015), (Sharma & Rathore, 2012).
subject to many security threats such as skimming and cloning (Iyabode, Nureni, F. Adebayo, &
A. Olamide, 2015), (Sharma & Rathore, 2012).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

OBJECT MODELLING 17
REFERENCES
Campean, F., & Yildirim, U. (2017). Enhanced Sequence Diagram for Function Modelling of
Complex Systems. Procedia CIRP (Vol. 60). https://doi.org/10.1016/j.procir.2017.01.053
Dezani, M., & De’Liguoro, U. (2009). Sessions and Session Types: An Overview.
Hayashi, F., Sullivan, R., & Weiner, S. E. (2003). A Guide to the ATM and Debit Card Industry.
Retrieved from http://www.kc.frb.org/publicat/PSR/BksJournArticles/ATMPaper.pdf
Ibrahim, A., Mishra, A., & Barroon, I. A. (2010). Fraud Detection and Control on Atm Machines
, an Algorithm for Combating Cash and Fund Transfer . Abstract :, (August 2014).
Iyabode, A. M., Nureni, Y. N., F. Adebayo, A., & A. Olamide, O. (2015). Card-Less Electronic
Automated Teller Machine (EATM) With Biometric Authentication. International Journal
of Engineering Trends and Technology, 30(2), 99–105.
https://doi.org/10.14445/22315381/IJETT-V30P219
Mettenheim, K., Diniz, E., Gonzalez, L., Committee, O., Ware, P., Stuart, G., & Rosengard, J.
(2014). New Perspectives on Banking and Agendas for Financial Inclusion . New
Perspectives on Banking and Agendas for Financial Inclusion Call for Papers , Financial
Inclusion Research Conference , 2013 Cambridge Massachusetts, (August 2015).
Mondal, P. C., Deb, R., & Adnan, M. N. (2017). On reinforcing automatic teller machine (ATM)
transaction authentication security process by imposing behavioral biometrics. In 2017 4th
International Conference on Advances in Electrical Engineering (ICAEE) (pp. 369–372).
https://doi.org/10.1109/ICAEE.2017.8255383
Refsdal, A., Husa, K., & Stølen, K. (2005). Specification and Refinement of Soft Real-Time
Requirements Using Sequence Diagrams. https://doi.org/10.1007/11603009_4
Saleh, O. S. (2016). Designing and Implementing of ATM System Using Object Oriented
REFERENCES
Campean, F., & Yildirim, U. (2017). Enhanced Sequence Diagram for Function Modelling of
Complex Systems. Procedia CIRP (Vol. 60). https://doi.org/10.1016/j.procir.2017.01.053
Dezani, M., & De’Liguoro, U. (2009). Sessions and Session Types: An Overview.
Hayashi, F., Sullivan, R., & Weiner, S. E. (2003). A Guide to the ATM and Debit Card Industry.
Retrieved from http://www.kc.frb.org/publicat/PSR/BksJournArticles/ATMPaper.pdf
Ibrahim, A., Mishra, A., & Barroon, I. A. (2010). Fraud Detection and Control on Atm Machines
, an Algorithm for Combating Cash and Fund Transfer . Abstract :, (August 2014).
Iyabode, A. M., Nureni, Y. N., F. Adebayo, A., & A. Olamide, O. (2015). Card-Less Electronic
Automated Teller Machine (EATM) With Biometric Authentication. International Journal
of Engineering Trends and Technology, 30(2), 99–105.
https://doi.org/10.14445/22315381/IJETT-V30P219
Mettenheim, K., Diniz, E., Gonzalez, L., Committee, O., Ware, P., Stuart, G., & Rosengard, J.
(2014). New Perspectives on Banking and Agendas for Financial Inclusion . New
Perspectives on Banking and Agendas for Financial Inclusion Call for Papers , Financial
Inclusion Research Conference , 2013 Cambridge Massachusetts, (August 2015).
Mondal, P. C., Deb, R., & Adnan, M. N. (2017). On reinforcing automatic teller machine (ATM)
transaction authentication security process by imposing behavioral biometrics. In 2017 4th
International Conference on Advances in Electrical Engineering (ICAEE) (pp. 369–372).
https://doi.org/10.1109/ICAEE.2017.8255383
Refsdal, A., Husa, K., & Stølen, K. (2005). Specification and Refinement of Soft Real-Time
Requirements Using Sequence Diagrams. https://doi.org/10.1007/11603009_4
Saleh, O. S. (2016). Designing and Implementing of ATM System Using Object Oriented

OBJECT MODELLING 18
Approach, (July 2015).
Sharma, N., & Rathore, D. V. S. (2012). Analysis of Different Vulnerabilities in Auto Teller
Machine. Journal of Global Research in Computer Science, 3(3), 2010–2012.
Approach, (July 2015).
Sharma, N., & Rathore, D. V. S. (2012). Analysis of Different Vulnerabilities in Auto Teller
Machine. Journal of Global Research in Computer Science, 3(3), 2010–2012.
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





