Vulnerability of Autonomous Cars - Risks and Solutions
VerifiedAdded on 2023/06/10
|8
|1116
|343
AI Summary
This article critically analyzes media articles to explore the vulnerabilities and risks of autonomous cars. It covers topics such as cybersecurity, Lidar sensors, data storage, and more. The article also highlights potential solutions to address these vulnerabilities.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: VULNERABILITY OF AUTONOMOUS CARS
VULNERABILITY OF AUTONOMOUS CARS
Name of the University
Name of the student
Author Note
VULNERABILITY OF AUTONOMOUS CARS
Name of the University
Name of the student
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
1VULNERABILITY OF AUTONOMOUS CARS
With the growth in self-driving cars all around the world in the present decade, there
is an increasing need of evaluating the vulnerabilities and risks that this new technology
poses. The particular topic has been chosen for this assignment to address these
vulnerabilities and risks.
In the following sections, five media sites have been chosen to assess the
vulnerabilities that autonomous car poses in the present. The assignment performs a critical
analysis on the mentioned topic from the selected media articles.
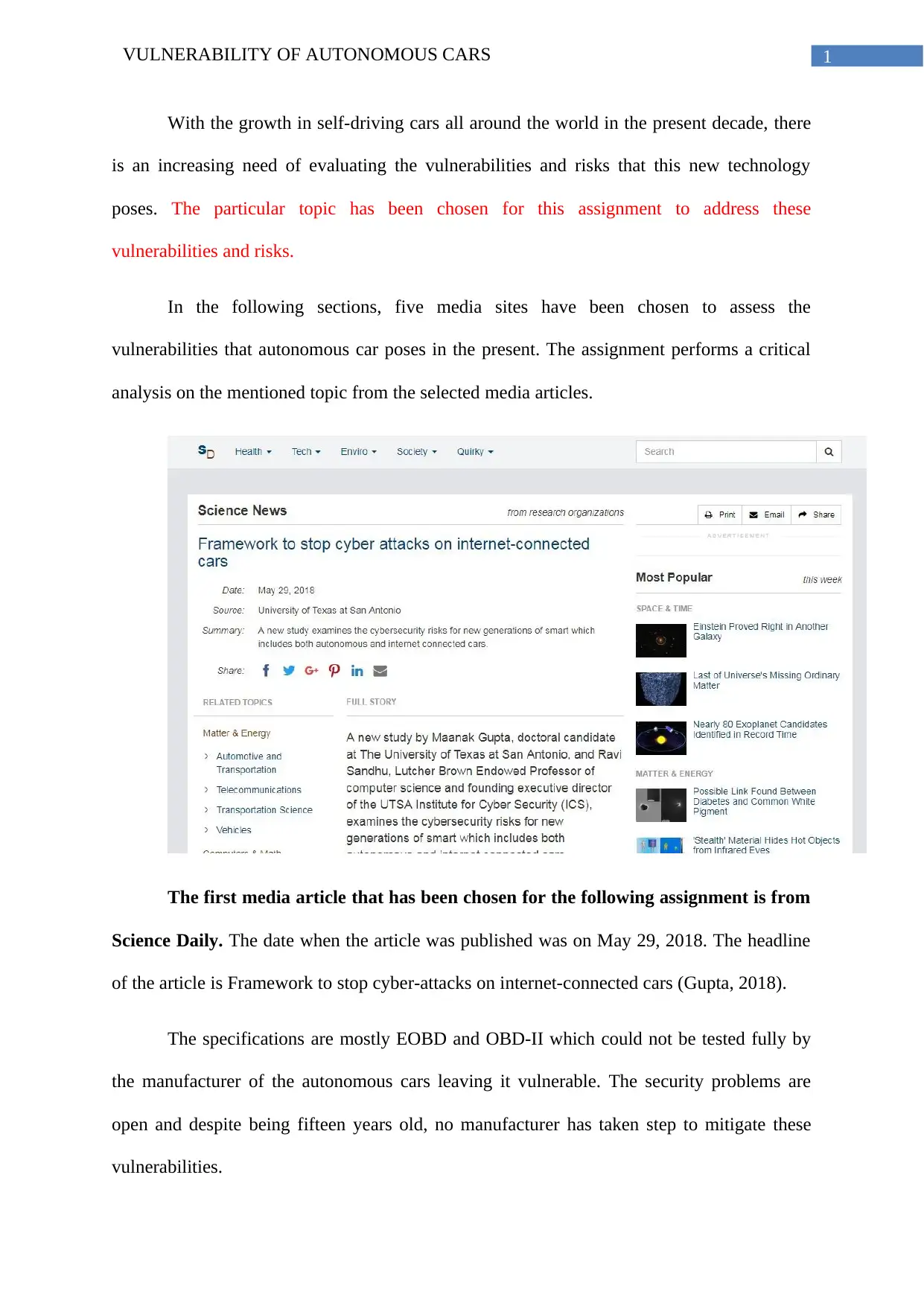
The first media article that has been chosen for the following assignment is from
Science Daily. The date when the article was published was on May 29, 2018. The headline
of the article is Framework to stop cyber-attacks on internet-connected cars (Gupta, 2018).
The specifications are mostly EOBD and OBD-II which could not be tested fully by
the manufacturer of the autonomous cars leaving it vulnerable. The security problems are
open and despite being fifteen years old, no manufacturer has taken step to mitigate these
vulnerabilities.
With the growth in self-driving cars all around the world in the present decade, there
is an increasing need of evaluating the vulnerabilities and risks that this new technology
poses. The particular topic has been chosen for this assignment to address these
vulnerabilities and risks.
In the following sections, five media sites have been chosen to assess the
vulnerabilities that autonomous car poses in the present. The assignment performs a critical
analysis on the mentioned topic from the selected media articles.
The first media article that has been chosen for the following assignment is from
Science Daily. The date when the article was published was on May 29, 2018. The headline
of the article is Framework to stop cyber-attacks on internet-connected cars (Gupta, 2018).
The specifications are mostly EOBD and OBD-II which could not be tested fully by
the manufacturer of the autonomous cars leaving it vulnerable. The security problems are
open and despite being fifteen years old, no manufacturer has taken step to mitigate these
vulnerabilities.
2VULNERABILITY OF AUTONOMOUS CARS
The benefit of the article with regards to the mentioned topic is that it explores the
risks and vulnerabilities related to cybersecurity for both inter connected as well as
autonomous cars.
The author however failed to properly evaluate the authorization framework for the
autonomous cars in detail.
The article conclusively defines the framework that is required for determining
policies related to security authorization in various control decision points in autonomous
cars.
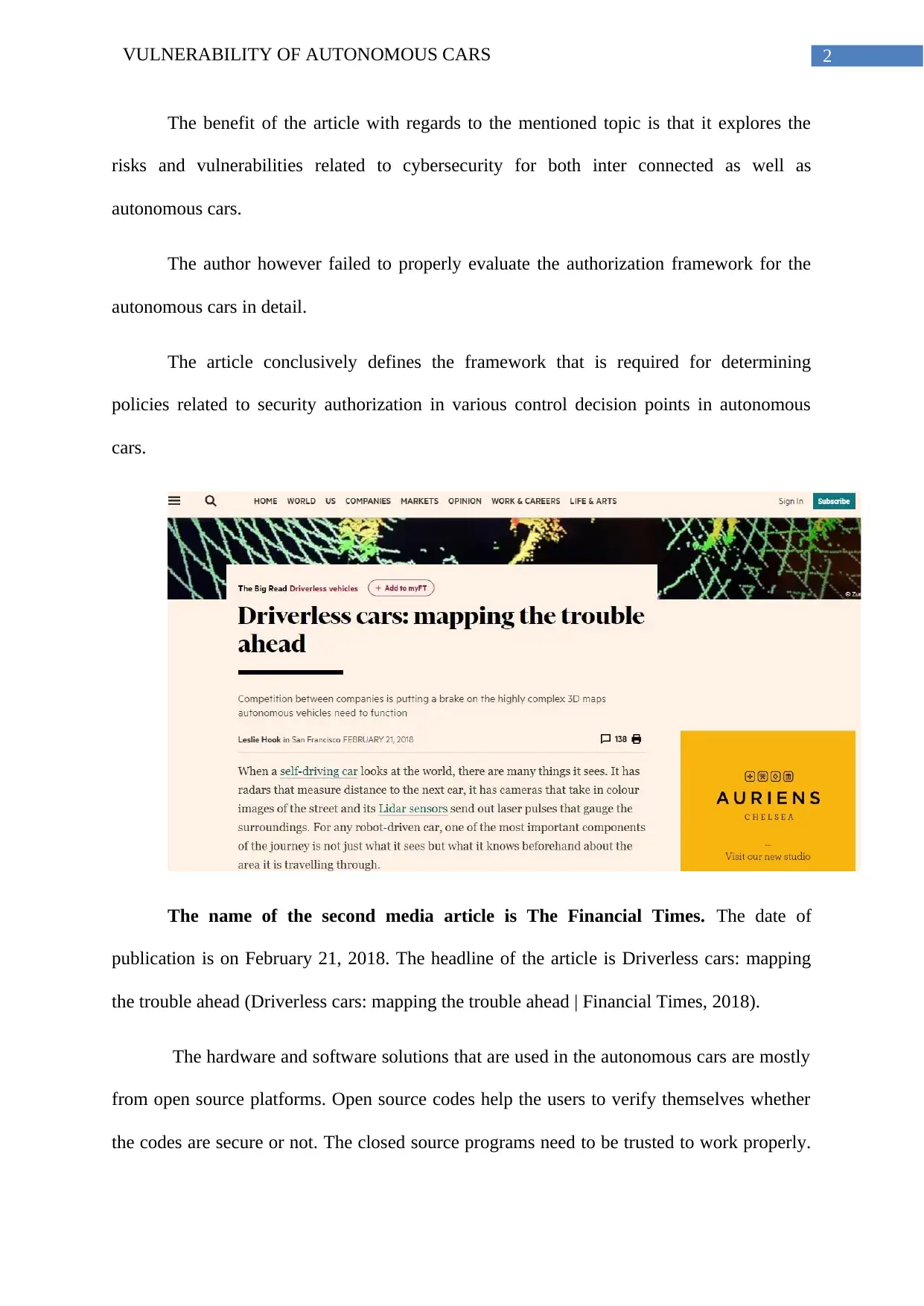
The name of the second media article is The Financial Times. The date of
publication is on February 21, 2018. The headline of the article is Driverless cars: mapping
the trouble ahead (Driverless cars: mapping the trouble ahead | Financial Times, 2018).
The hardware and software solutions that are used in the autonomous cars are mostly
from open source platforms. Open source codes help the users to verify themselves whether
the codes are secure or not. The closed source programs need to be trusted to work properly.
The benefit of the article with regards to the mentioned topic is that it explores the
risks and vulnerabilities related to cybersecurity for both inter connected as well as
autonomous cars.
The author however failed to properly evaluate the authorization framework for the
autonomous cars in detail.
The article conclusively defines the framework that is required for determining
policies related to security authorization in various control decision points in autonomous
cars.
The name of the second media article is The Financial Times. The date of
publication is on February 21, 2018. The headline of the article is Driverless cars: mapping
the trouble ahead (Driverless cars: mapping the trouble ahead | Financial Times, 2018).
The hardware and software solutions that are used in the autonomous cars are mostly
from open source platforms. Open source codes help the users to verify themselves whether
the codes are secure or not. The closed source programs need to be trusted to work properly.
3VULNERABILITY OF AUTONOMOUS CARS
The developers need to address these issues for properly checking the vulnerabilities of the
autonomous cars.
The benefit of the article is that it explains the vulnerabilities of autonomous cars that
are related to properly mapping the environments with the help of Lidar sensors. The working
of the Lidar sensors and their functionalities have been evaluated in detail in the mentioned
media source.
However, the media article fails to properly provide a solution for the vulnerabilities
that are related to storage of data by these sensors.
The media source still manages to provide conclusive research on their vulnerabilities
and proposes the need for improvement of mapping systems with advanced 3D civil maps
and the privacy concerns that are related to it.
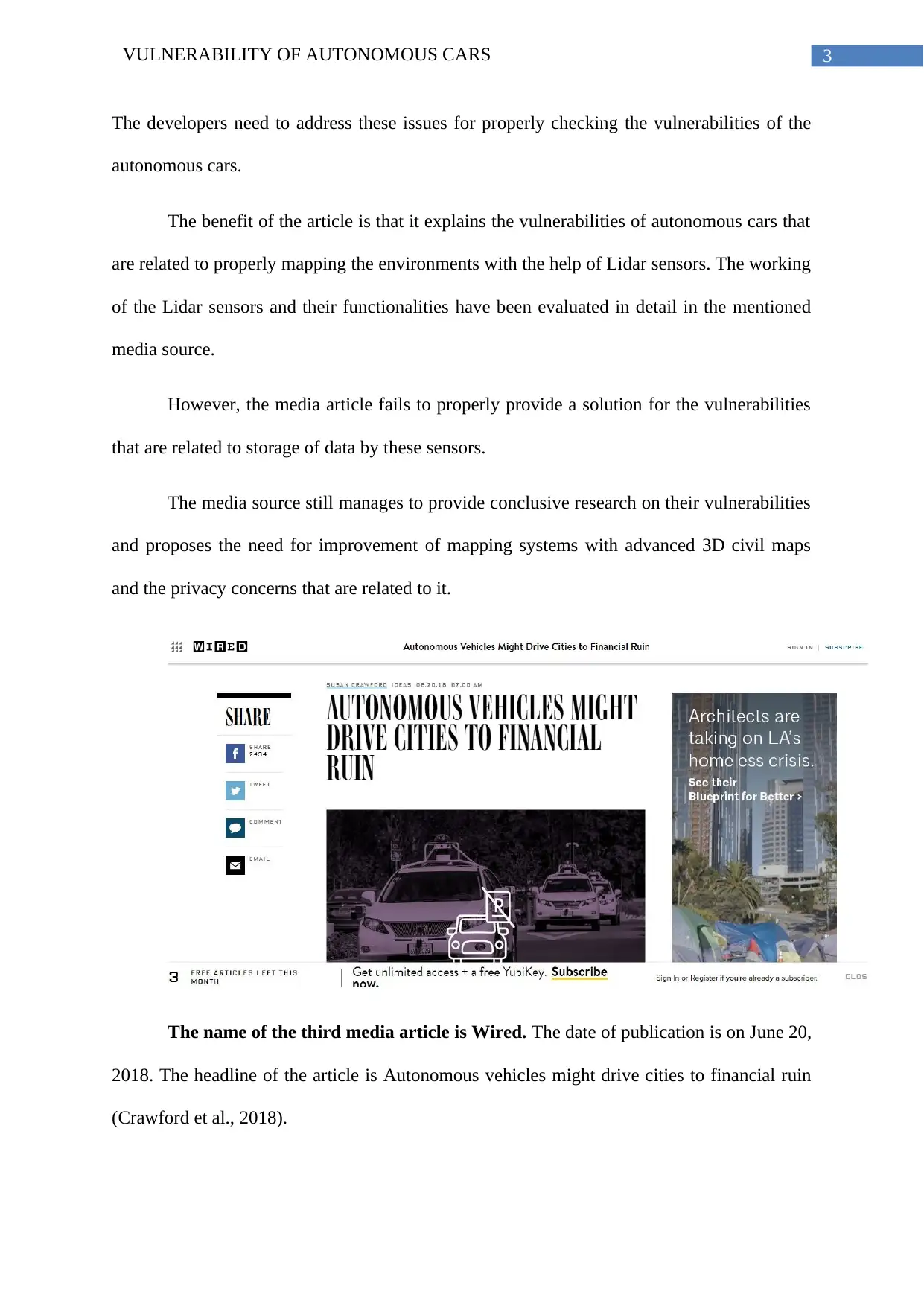
The name of the third media article is Wired. The date of publication is on June 20,
2018. The headline of the article is Autonomous vehicles might drive cities to financial ruin
(Crawford et al., 2018).
The developers need to address these issues for properly checking the vulnerabilities of the
autonomous cars.
The benefit of the article is that it explains the vulnerabilities of autonomous cars that
are related to properly mapping the environments with the help of Lidar sensors. The working
of the Lidar sensors and their functionalities have been evaluated in detail in the mentioned
media source.
However, the media article fails to properly provide a solution for the vulnerabilities
that are related to storage of data by these sensors.
The media source still manages to provide conclusive research on their vulnerabilities
and proposes the need for improvement of mapping systems with advanced 3D civil maps
and the privacy concerns that are related to it.
The name of the third media article is Wired. The date of publication is on June 20,
2018. The headline of the article is Autonomous vehicles might drive cities to financial ruin
(Crawford et al., 2018).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4VULNERABILITY OF AUTONOMOUS CARS
The vulnerabilities can range from simple exploits like access mechanisms, back door
attacks like conventional approaches and front door attacks like getting access to the OEM.
Simple tools can be used to decipher the security which raises an important question whether
or not these autonomous cars are truly secure.
The benefit of the article is that it comprehensively defines how the vulnerabilities of
the autonomous cars can lead to financial ruins due to mass unemployment.
The drawback is that it fails to highlight why the growth of public transport will be beneficial
than autonomous cars.
In short, the rise of autonomous cars will decrease the tax inflow that the government
gets from registration fees, gas taxes and more.
The name of the fourth media article is The Verge. The date of publication is
on Apr 19, 2018. The headline of the article is How Tesla and Waymo are tackling a major
problem for self-driving cars: data (Kane, 2018).
The security of these cars are truly questionable as present technologies like GPS
spoofing and jamming and MMW radar attacks can potentially compromise these systems.
The vulnerabilities can range from simple exploits like access mechanisms, back door
attacks like conventional approaches and front door attacks like getting access to the OEM.
Simple tools can be used to decipher the security which raises an important question whether
or not these autonomous cars are truly secure.
The benefit of the article is that it comprehensively defines how the vulnerabilities of
the autonomous cars can lead to financial ruins due to mass unemployment.
The drawback is that it fails to highlight why the growth of public transport will be beneficial
than autonomous cars.
In short, the rise of autonomous cars will decrease the tax inflow that the government
gets from registration fees, gas taxes and more.
The name of the fourth media article is The Verge. The date of publication is
on Apr 19, 2018. The headline of the article is How Tesla and Waymo are tackling a major
problem for self-driving cars: data (Kane, 2018).
The security of these cars are truly questionable as present technologies like GPS
spoofing and jamming and MMW radar attacks can potentially compromise these systems.
5VULNERABILITY OF AUTONOMOUS CARS
The benefit of the article is that it highlights the vulnerabilities that are related to large
collection of car data by prospective organizations like Tesla.
The drawback of the article is that it fails to provide conclusive solution for
addressing these issues.
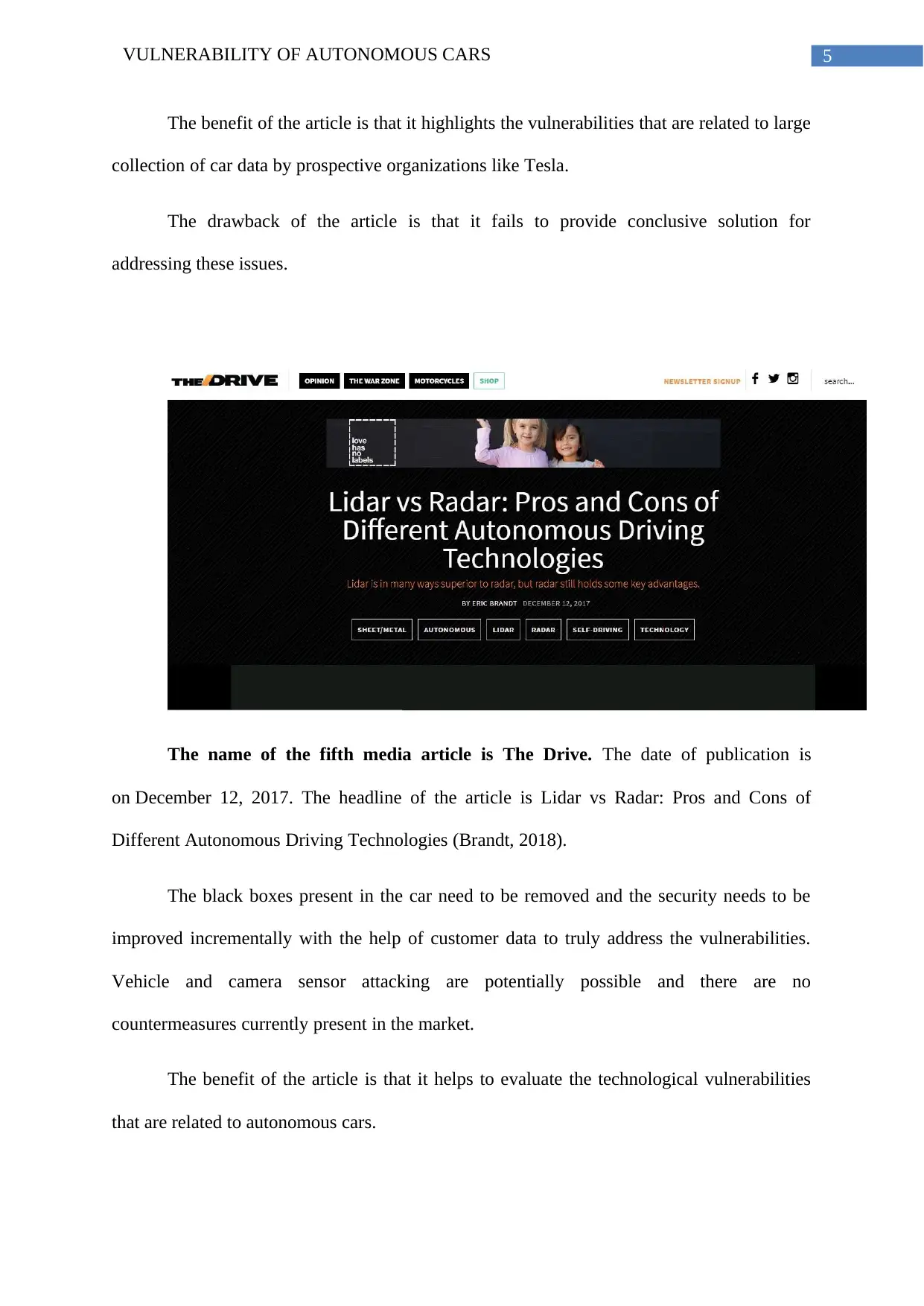
The name of the fifth media article is The Drive. The date of publication is
on December 12, 2017. The headline of the article is Lidar vs Radar: Pros and Cons of
Different Autonomous Driving Technologies (Brandt, 2018).
The black boxes present in the car need to be removed and the security needs to be
improved incrementally with the help of customer data to truly address the vulnerabilities.
Vehicle and camera sensor attacking are potentially possible and there are no
countermeasures currently present in the market.
The benefit of the article is that it helps to evaluate the technological vulnerabilities
that are related to autonomous cars.
The benefit of the article is that it highlights the vulnerabilities that are related to large
collection of car data by prospective organizations like Tesla.
The drawback of the article is that it fails to provide conclusive solution for
addressing these issues.
The name of the fifth media article is The Drive. The date of publication is
on December 12, 2017. The headline of the article is Lidar vs Radar: Pros and Cons of
Different Autonomous Driving Technologies (Brandt, 2018).
The black boxes present in the car need to be removed and the security needs to be
improved incrementally with the help of customer data to truly address the vulnerabilities.
Vehicle and camera sensor attacking are potentially possible and there are no
countermeasures currently present in the market.
The benefit of the article is that it helps to evaluate the technological vulnerabilities
that are related to autonomous cars.

6VULNERABILITY OF AUTONOMOUS CARS
The drawback is that it does not provide an alternative to address the drawbacks of the
mentioned technologies.
Till then, the autonomous car companies have to choose between cheap radar systems
and high tech Lidar systems.
The drawback is that it does not provide an alternative to address the drawbacks of the
mentioned technologies.
Till then, the autonomous car companies have to choose between cheap radar systems
and high tech Lidar systems.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7VULNERABILITY OF AUTONOMOUS CARS
References
Brandt, E. (2018). Lidar vs Radar: Pros and Cons of Different Autonomous Driving
Technologies. Retrieved from http://www.thedrive.com/sheetmetal/16916/lidar-vs-
radar-pros-and-cons-of-different-autonomous-driving-technologies
Crawford, S., Salmon, F., Heffernan, V., Pao, E., Pontin, J., & Mckenna, M. (2018).
Autonomous Vehicles Might Drive Cities to Financial Ruin. Retrieved from
https://www.wired.com/story/autonomous-vehicles-might-drive-cities-to-financial-
ruin/
Driverless cars: mapping the trouble ahead | Financial Times. (2018). Retrieved from
https://www.ft.com/content/2a8941a4-1625-11e8-9e9c-25c814761640
Gupta, M. (2018). Framework to stop cyber attacks on internet-connected cars. Retrieved
from https://www.sciencedaily.com/releases/2018/05/180529092157.htm
Kane, S. (2018). Tesla and Waymo are taking wildly different paths to creating self-driving
cars. Retrieved from
https://www.theverge.com/transportation/2018/4/19/17204044/tesla-waymo-self-
driving-car-data-simulation
References
Brandt, E. (2018). Lidar vs Radar: Pros and Cons of Different Autonomous Driving
Technologies. Retrieved from http://www.thedrive.com/sheetmetal/16916/lidar-vs-
radar-pros-and-cons-of-different-autonomous-driving-technologies
Crawford, S., Salmon, F., Heffernan, V., Pao, E., Pontin, J., & Mckenna, M. (2018).
Autonomous Vehicles Might Drive Cities to Financial Ruin. Retrieved from
https://www.wired.com/story/autonomous-vehicles-might-drive-cities-to-financial-
ruin/
Driverless cars: mapping the trouble ahead | Financial Times. (2018). Retrieved from
https://www.ft.com/content/2a8941a4-1625-11e8-9e9c-25c814761640
Gupta, M. (2018). Framework to stop cyber attacks on internet-connected cars. Retrieved
from https://www.sciencedaily.com/releases/2018/05/180529092157.htm
Kane, S. (2018). Tesla and Waymo are taking wildly different paths to creating self-driving
cars. Retrieved from
https://www.theverge.com/transportation/2018/4/19/17204044/tesla-waymo-self-
driving-car-data-simulation
1 out of 8
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.