Challenges and Mitigation Strategies in Bell Studio Operations
VerifiedAdded on 2022/11/26
|17
|3029
|144
AI Summary
This assignment describes the challenges faced by Bell Studio in its operations and provides mitigation strategies. It focuses on issues in the purchase system, cash disbursement system, and payroll system. The assignment also includes data flow diagrams and system flowcharts.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: BELL STUDIO
BELL STUDIO
Name of Student
Name of University
Author’s Note
BELL STUDIO
Name of Student
Name of University
Author’s Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1BELL STUDIO
Executive summary
Using the computer systems allow various enterprises in automating various services provided
by the organization. These services include dealing with orders, payment processes, delivery and
some more similar services. The organization that has been selected by this particular
organization is Bell Studio, this particular organization involves various manufactures who
belong to different countries such as China, Japan, Australia and some more. This assignment
describes regarding the organization named Bell Studio, it faces various challenges in the
operations that are carried out by the organization. The issues include some areas like payroll
systems, ordering systems, purchasing system and many more. The issue might be physical and
nonphysical as well. The description of the issues and their mitigation strategies have been
provided in this assignment.
Executive summary
Using the computer systems allow various enterprises in automating various services provided
by the organization. These services include dealing with orders, payment processes, delivery and
some more similar services. The organization that has been selected by this particular
organization is Bell Studio, this particular organization involves various manufactures who
belong to different countries such as China, Japan, Australia and some more. This assignment
describes regarding the organization named Bell Studio, it faces various challenges in the
operations that are carried out by the organization. The issues include some areas like payroll
systems, ordering systems, purchasing system and many more. The issue might be physical and
nonphysical as well. The description of the issues and their mitigation strategies have been
provided in this assignment.

2BELL STUDIO
Table of Contents
Introduction......................................................................................................................................3
Body.................................................................................................................................................3
Internal control weaknesses.........................................................................................................3
Challenges in purchase system................................................................................................3
Challenges in cash disbursement system.................................................................................5
Problems in payroll system......................................................................................................6
Risks in the systems.....................................................................................................................6
Security measures........................................................................................................................7
Data flow diagram of purchase and cash distribution systems....................................................9
Data flow diagram of payroll system.........................................................................................10
System flowchart of purchase system........................................................................................11
System flow chart of cash disbursements system......................................................................12
System flowchart of payroll system..........................................................................................13
Conclusion.....................................................................................................................................14
References......................................................................................................................................15
Table of Contents
Introduction......................................................................................................................................3
Body.................................................................................................................................................3
Internal control weaknesses.........................................................................................................3
Challenges in purchase system................................................................................................3
Challenges in cash disbursement system.................................................................................5
Problems in payroll system......................................................................................................6
Risks in the systems.....................................................................................................................6
Security measures........................................................................................................................7
Data flow diagram of purchase and cash distribution systems....................................................9
Data flow diagram of payroll system.........................................................................................10
System flowchart of purchase system........................................................................................11
System flow chart of cash disbursements system......................................................................12
System flowchart of payroll system..........................................................................................13
Conclusion.....................................................................................................................................14
References......................................................................................................................................15

3BELL STUDIO
Introduction
Numerous activities or tasks that are carried out in a particular organization have high
chances of facing various challenges. The challenges could be resolved with the utilization of
various computer systems, these systems are used for the purpose of various parts of their
operations (Chiang, Grover and Liang 2018). Using the computer systems allow various
enterprises in automating various services provided by the organization. These services include
dealing with orders, payment processes, delivery and some more similar services. Usage of the
computer systems contributes in reducing various errors that tend to slower down the success of
the operations carried out by the organization, besides this it acts as a catalyst in the fulfillment
of their projects and hence meeting the objectives of the organization as well (Pearlson, K.E.,
Saunders and Galletta 2016). The organization that has been selected by this particular
organization is Bell Studio, this particular organization involves various manufactures who
belong to different countries such as China, Japan, Australia and some more. Some of the
systems that already exists within the organization includes system for cash distribution,
purchase system, payroll system and some more that help in carrying out the operations of the
organization in an effective manner (Cassidy 2016). The system within Bell Studio has
numerous systems that have various defects, these issues have been mentioned in the report
below. The report also provides data flow diagrams and system flowcharts.
Body
Internal control weaknesses
Challenges in purchase system
Introduction
Numerous activities or tasks that are carried out in a particular organization have high
chances of facing various challenges. The challenges could be resolved with the utilization of
various computer systems, these systems are used for the purpose of various parts of their
operations (Chiang, Grover and Liang 2018). Using the computer systems allow various
enterprises in automating various services provided by the organization. These services include
dealing with orders, payment processes, delivery and some more similar services. Usage of the
computer systems contributes in reducing various errors that tend to slower down the success of
the operations carried out by the organization, besides this it acts as a catalyst in the fulfillment
of their projects and hence meeting the objectives of the organization as well (Pearlson, K.E.,
Saunders and Galletta 2016). The organization that has been selected by this particular
organization is Bell Studio, this particular organization involves various manufactures who
belong to different countries such as China, Japan, Australia and some more. Some of the
systems that already exists within the organization includes system for cash distribution,
purchase system, payroll system and some more that help in carrying out the operations of the
organization in an effective manner (Cassidy 2016). The system within Bell Studio has
numerous systems that have various defects, these issues have been mentioned in the report
below. The report also provides data flow diagrams and system flowcharts.
Body
Internal control weaknesses
Challenges in purchase system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4BELL STUDIO
Purchase system that exists within the Bell Studio does not have any technology
incorporated in it. The company carries out its operations using manual processes. Usage of
manual processes results in numerous complexities within the operations of which as a result
affects the services provided by the organization to its customers (Morecroft 2015). They face
various issues while taking orders as well as processing them. Utilization of paper based process
for procurement results in numerous issues for staffs, the files get piled up and there are high
chances that they might get misplaced or lost due to some reason. Every purchasing process
consists of around 7 documents, the process that consists more than 7 documents has high
chance to hamper the working procedure of the organization (Grover, Chiang and Liang 2018).
The process of purchasing include various subcategories such as requisitions, purchasing
numerous orders, quotations, advice notes, packing slips, invoices, good received notes and
some more. These include a huge amount of paper work that are produced as well as kept track
of on regular basis (DeLone and McLean 2016). For the purpose of carrying out effective as
well as efficient manner, proper maintenance of record keeping is necessary, there are a huge
number of issues that are faced by these records that are paper based. The manual processing of
the purchasing process, required a huge amount of paper work as well as more amount of time
consumed than expected (Peppard and Ward 2016). The major challenge that can be faced by
the company includes damage and loss of data, they might be destroyed accidentally. It might be
tough to spot various requests that are fake in nature, invoices and missing transactions, they
have a very high chance to result a huge amount of time along with money (Wu, Straub and
Liang 2015). Using a particular manual process, for the activity of purchasing has high chance
to require an updated and well maintained filing system, the files would have information
related to purchases that have been carried out by the company and with the details of the
Purchase system that exists within the Bell Studio does not have any technology
incorporated in it. The company carries out its operations using manual processes. Usage of
manual processes results in numerous complexities within the operations of which as a result
affects the services provided by the organization to its customers (Morecroft 2015). They face
various issues while taking orders as well as processing them. Utilization of paper based process
for procurement results in numerous issues for staffs, the files get piled up and there are high
chances that they might get misplaced or lost due to some reason. Every purchasing process
consists of around 7 documents, the process that consists more than 7 documents has high
chance to hamper the working procedure of the organization (Grover, Chiang and Liang 2018).
The process of purchasing include various subcategories such as requisitions, purchasing
numerous orders, quotations, advice notes, packing slips, invoices, good received notes and
some more. These include a huge amount of paper work that are produced as well as kept track
of on regular basis (DeLone and McLean 2016). For the purpose of carrying out effective as
well as efficient manner, proper maintenance of record keeping is necessary, there are a huge
number of issues that are faced by these records that are paper based. The manual processing of
the purchasing process, required a huge amount of paper work as well as more amount of time
consumed than expected (Peppard and Ward 2016). The major challenge that can be faced by
the company includes damage and loss of data, they might be destroyed accidentally. It might be
tough to spot various requests that are fake in nature, invoices and missing transactions, they
have a very high chance to result a huge amount of time along with money (Wu, Straub and
Liang 2015). Using a particular manual process, for the activity of purchasing has high chance
to require an updated and well maintained filing system, the files would have information
related to purchases that have been carried out by the company and with the details of the

5BELL STUDIO
organization (Kitsios and Kamariotou 2016). Manual purchasing would need a good amount of
updates that are regular in nature as well as efficient system for the purpose of filing, this would
use a huge amount of time as well as space for working effectively.
Challenges in cash disbursement system
The cash disbursement system of Bell Studio had been issued under various
circumstances, besides this it has also been facing various challenges. For example if a vendor is
supposed to deliver a particular product and collect the amount from the customer but there is no
other option for getting payment. In this particular case, the customer needs to provide a cheque
to the individual and accounting system is updated accordingly (Kamariotou and Kitsios 2019).
This sort of issue might be faced numerous times by the organization, these sort of occurrences
of the manual disbursements has the ability to produce even more issues for the organization.
There has been an easy process for a specific employee for steaming funds in case he us allowed
to access of various signature stamps and similar data that belongs to the organization (Vijayan
2018). Theft in this particular case could be covered by entering data in the accounting system
which indicates delivery only by cash from a specific supplier. The manual work would not be
necessary at all because the payment process might not process through the payable system of
the accounts. After that the individual realizes that the documents are not accessible (Coltman,
Tallon and Sharma 2015). This is due to the fact that it would be easy for criminals to carry out
frauds, hence the organization needs to examine numerous cash disbursement system for
checking the number of times disbursements in manual way have been carried out along with
the results along with the circumstances which might result after these payments.
organization (Kitsios and Kamariotou 2016). Manual purchasing would need a good amount of
updates that are regular in nature as well as efficient system for the purpose of filing, this would
use a huge amount of time as well as space for working effectively.
Challenges in cash disbursement system
The cash disbursement system of Bell Studio had been issued under various
circumstances, besides this it has also been facing various challenges. For example if a vendor is
supposed to deliver a particular product and collect the amount from the customer but there is no
other option for getting payment. In this particular case, the customer needs to provide a cheque
to the individual and accounting system is updated accordingly (Kamariotou and Kitsios 2019).
This sort of issue might be faced numerous times by the organization, these sort of occurrences
of the manual disbursements has the ability to produce even more issues for the organization.
There has been an easy process for a specific employee for steaming funds in case he us allowed
to access of various signature stamps and similar data that belongs to the organization (Vijayan
2018). Theft in this particular case could be covered by entering data in the accounting system
which indicates delivery only by cash from a specific supplier. The manual work would not be
necessary at all because the payment process might not process through the payable system of
the accounts. After that the individual realizes that the documents are not accessible (Coltman,
Tallon and Sharma 2015). This is due to the fact that it would be easy for criminals to carry out
frauds, hence the organization needs to examine numerous cash disbursement system for
checking the number of times disbursements in manual way have been carried out along with
the results along with the circumstances which might result after these payments.

6BELL STUDIO
Problems in payroll system
The organization faces various issues that exists in the department that deals with the
payroll system. One of the major issue face by the organization includes non-compliance of the
system, the payroll processing system that is used by the organization has characteristics that are
non-compliance in nature (Yazid and Kofarnaisa 2019). The payroll system needs more
attention compared to any other department. This is due to the improvements that are to be
carried out like legislative updates. Abiding by various laws and flattering has the ability to
allow enterprises to serve various penalties and hence serve for non-compliance. One more
major issue in the payroll system of the organization includes the human error (Chuang and Lin
2017). The payroll process that has been used by the organization, is usually manual in nature,
they undertake a huge number of issues that are accompanied by numerous interventions which
are processed in manual. This particular system had overburdened a huge number of
professionals such as the ones belonging to finance teams, they had been left with numerous
activities that are mundane in nature (Dwivedi, Wastell and Laumer 2015). These tasks include
documentation and repetitive cross checking. Suppose the organization had been through a
particular transaction, this transaction is usually checked regarding every step that involves in
the process. After few days if the employees require data regarding this particular transaction,
for this, they would need to investigate the complete transaction once again, this makes the
process even more time taking because the data which has the information regarding the
transaction is not saved (Hung, Huang and Yen 2016). This process had been numerous errors
that are caused by human errors.
Problems in payroll system
The organization faces various issues that exists in the department that deals with the
payroll system. One of the major issue face by the organization includes non-compliance of the
system, the payroll processing system that is used by the organization has characteristics that are
non-compliance in nature (Yazid and Kofarnaisa 2019). The payroll system needs more
attention compared to any other department. This is due to the improvements that are to be
carried out like legislative updates. Abiding by various laws and flattering has the ability to
allow enterprises to serve various penalties and hence serve for non-compliance. One more
major issue in the payroll system of the organization includes the human error (Chuang and Lin
2017). The payroll process that has been used by the organization, is usually manual in nature,
they undertake a huge number of issues that are accompanied by numerous interventions which
are processed in manual. This particular system had overburdened a huge number of
professionals such as the ones belonging to finance teams, they had been left with numerous
activities that are mundane in nature (Dwivedi, Wastell and Laumer 2015). These tasks include
documentation and repetitive cross checking. Suppose the organization had been through a
particular transaction, this transaction is usually checked regarding every step that involves in
the process. After few days if the employees require data regarding this particular transaction,
for this, they would need to investigate the complete transaction once again, this makes the
process even more time taking because the data which has the information regarding the
transaction is not saved (Hung, Huang and Yen 2016). This process had been numerous errors
that are caused by human errors.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

7BELL STUDIO
Risks in the systems
Threats in computer system can be described as the one that results in loss of data,
corruption of data, and many more damages caused to hardware infrastructure. Knowing the
method by which numerous threats of security of computers would be identified and is
considered as the initial stage in the entire process of protection of computer system (Wu, Straub
and Liang 2015). The threats that are caused in the organization would result because of
numerous accidents, they would be caused intentionally or due to numerous natural disasters.
These security risks might be defined as a specific risk that has the ability to harm numerous
computer systems along with the organization. There are numerous risks which could be faced
by a specific system that is computer based might be physical as well (Kitsios and Kamariotou
2016). Physical threats are considered as various causes of a kind of accident which might cause
loss and any sort of damage to the systems. Physical damages could be categorized into various
parts, these parts include external, internal as well as human. Internal threat includes the harm
caused due to fire as well humidity that cause hardware of housing, unstable access to power
and some more (Kamariotou and Kitsios 2019). Human damages are result of floods, vandalism
of the infrastructure, vandalism of hardware and earthquake. External threats are result of
flooding, earthquake and lightening. There are some threats that are non-physical in nature
which could be faced by numerous computer systems, the issues include corruption of the
system information, disruption of business operations which has the capacity of relying on
various systems, illegal monitoring of numerous activities on system, loss of important data and
some more.
Risks in the systems
Threats in computer system can be described as the one that results in loss of data,
corruption of data, and many more damages caused to hardware infrastructure. Knowing the
method by which numerous threats of security of computers would be identified and is
considered as the initial stage in the entire process of protection of computer system (Wu, Straub
and Liang 2015). The threats that are caused in the organization would result because of
numerous accidents, they would be caused intentionally or due to numerous natural disasters.
These security risks might be defined as a specific risk that has the ability to harm numerous
computer systems along with the organization. There are numerous risks which could be faced
by a specific system that is computer based might be physical as well (Kitsios and Kamariotou
2016). Physical threats are considered as various causes of a kind of accident which might cause
loss and any sort of damage to the systems. Physical damages could be categorized into various
parts, these parts include external, internal as well as human. Internal threat includes the harm
caused due to fire as well humidity that cause hardware of housing, unstable access to power
and some more (Kamariotou and Kitsios 2019). Human damages are result of floods, vandalism
of the infrastructure, vandalism of hardware and earthquake. External threats are result of
flooding, earthquake and lightening. There are some threats that are non-physical in nature
which could be faced by numerous computer systems, the issues include corruption of the
system information, disruption of business operations which has the capacity of relying on
various systems, illegal monitoring of numerous activities on system, loss of important data and
some more.

8BELL STUDIO
Security measures
There are various risks that are physical as well as non-physical risks, the risks have
already been describes in the previous part of the assignment, these risks could be mitigated
with the use of numerous measures, the measures have been mentioned below (Coltman, Tallon
and Sharma2015). For protecting the computer systems, from numerous physical threats, the
company must have some control measures that provide physical. Security, the measures are
internal, external and human in nature. Internal threats could be prevented with the usage of fire
detectors besides extinguishers that do not make use of water for estinguishing fire. Stable
power supply can be achieved by using voltage controllers (Yazid and Kofarnaisa 2019). Air
conditioners can be used for the purpose of controlling humidity in the rooms present within the
organization where the systems have been stored. Various systems can be incorporated for the
purpose of protecting lightening, these systems might not provide complete security but they
would reduce the damage caused by them (Chuang and Lin 2017). Housing numerous systems
that are located at various high lands can be considered as various ways which can be used for
the purpose of protecting systems against various natural disasters like floods. Various threats
such as theft can be prevented by using locked doors along with restricted access of the
computer rooms (Dwivedi, Wastell and Laumer 2015). For protecting the computer systems
from threats, they should have numerous logical security measures along with proper place.
Some of the measures which can be used for protecting their cyber security are presented in this
assignment.
Security measures
There are various risks that are physical as well as non-physical risks, the risks have
already been describes in the previous part of the assignment, these risks could be mitigated
with the use of numerous measures, the measures have been mentioned below (Coltman, Tallon
and Sharma2015). For protecting the computer systems, from numerous physical threats, the
company must have some control measures that provide physical. Security, the measures are
internal, external and human in nature. Internal threats could be prevented with the usage of fire
detectors besides extinguishers that do not make use of water for estinguishing fire. Stable
power supply can be achieved by using voltage controllers (Yazid and Kofarnaisa 2019). Air
conditioners can be used for the purpose of controlling humidity in the rooms present within the
organization where the systems have been stored. Various systems can be incorporated for the
purpose of protecting lightening, these systems might not provide complete security but they
would reduce the damage caused by them (Chuang and Lin 2017). Housing numerous systems
that are located at various high lands can be considered as various ways which can be used for
the purpose of protecting systems against various natural disasters like floods. Various threats
such as theft can be prevented by using locked doors along with restricted access of the
computer rooms (Dwivedi, Wastell and Laumer 2015). For protecting the computer systems
from threats, they should have numerous logical security measures along with proper place.
Some of the measures which can be used for protecting their cyber security are presented in this
assignment.
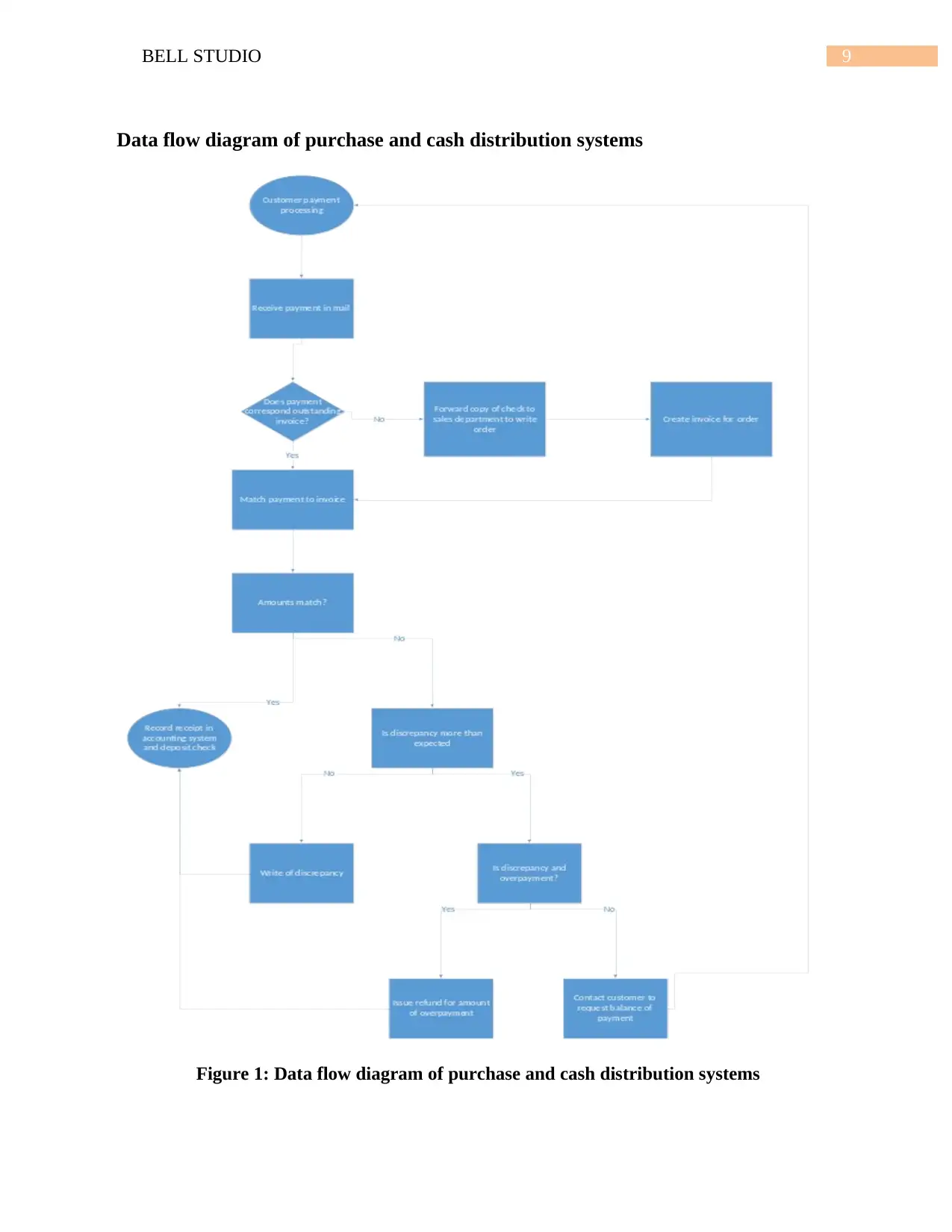
9BELL STUDIO
Data flow diagram of purchase and cash distribution systems
Figure 1: Data flow diagram of purchase and cash distribution systems
Data flow diagram of purchase and cash distribution systems
Figure 1: Data flow diagram of purchase and cash distribution systems
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
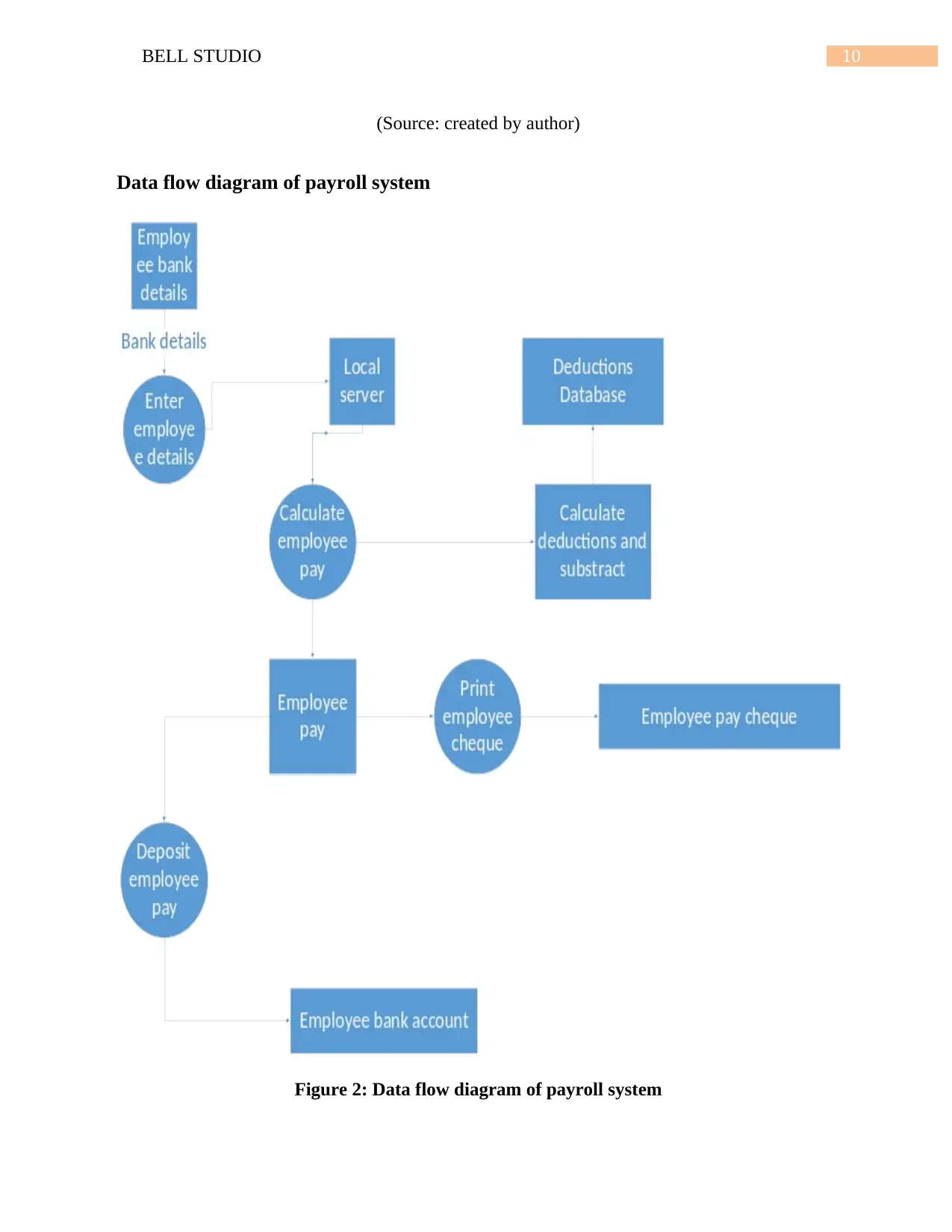
10BELL STUDIO
(Source: created by author)
Data flow diagram of payroll system
Figure 2: Data flow diagram of payroll system
(Source: created by author)
Data flow diagram of payroll system
Figure 2: Data flow diagram of payroll system
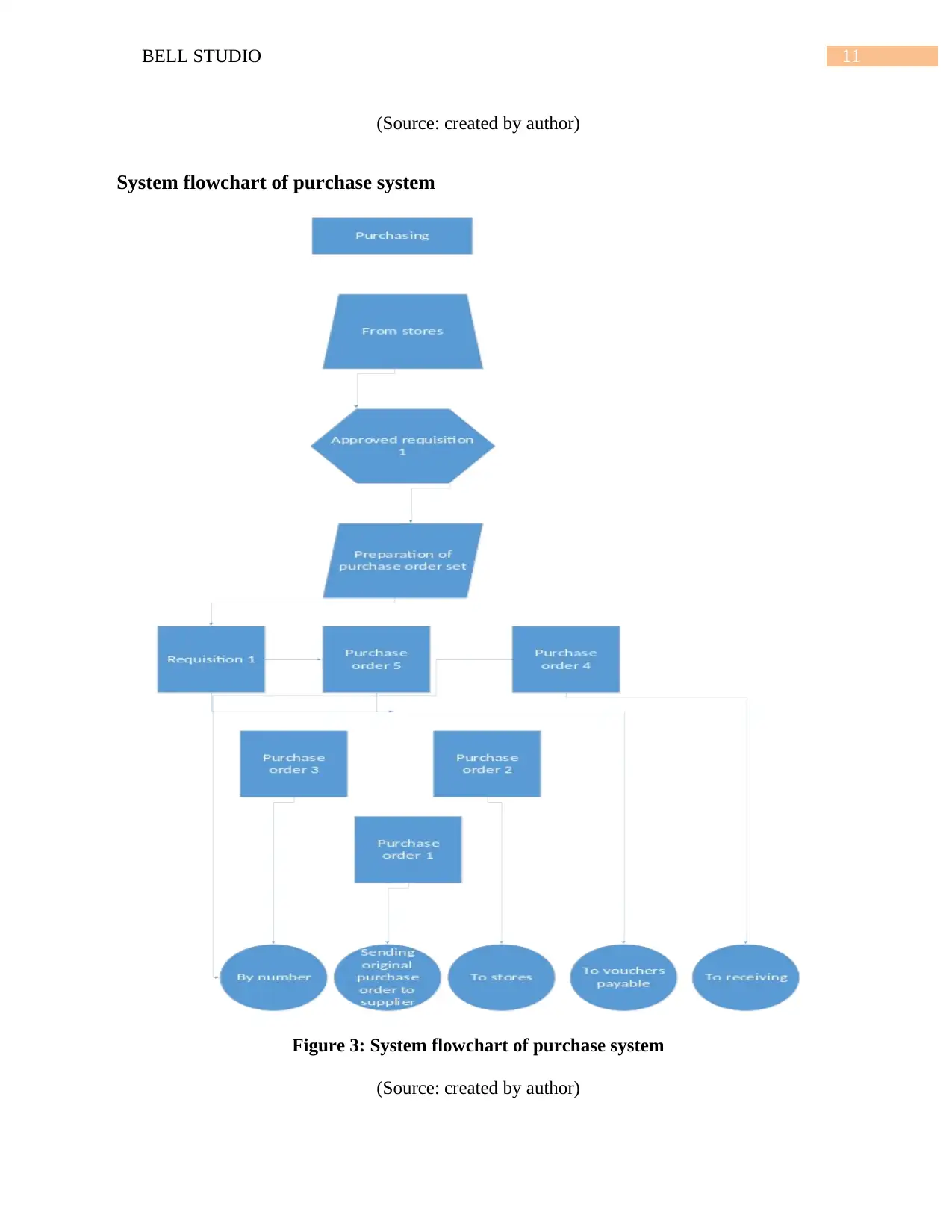
11BELL STUDIO
(Source: created by author)
System flowchart of purchase system
Figure 3: System flowchart of purchase system
(Source: created by author)
(Source: created by author)
System flowchart of purchase system
Figure 3: System flowchart of purchase system
(Source: created by author)
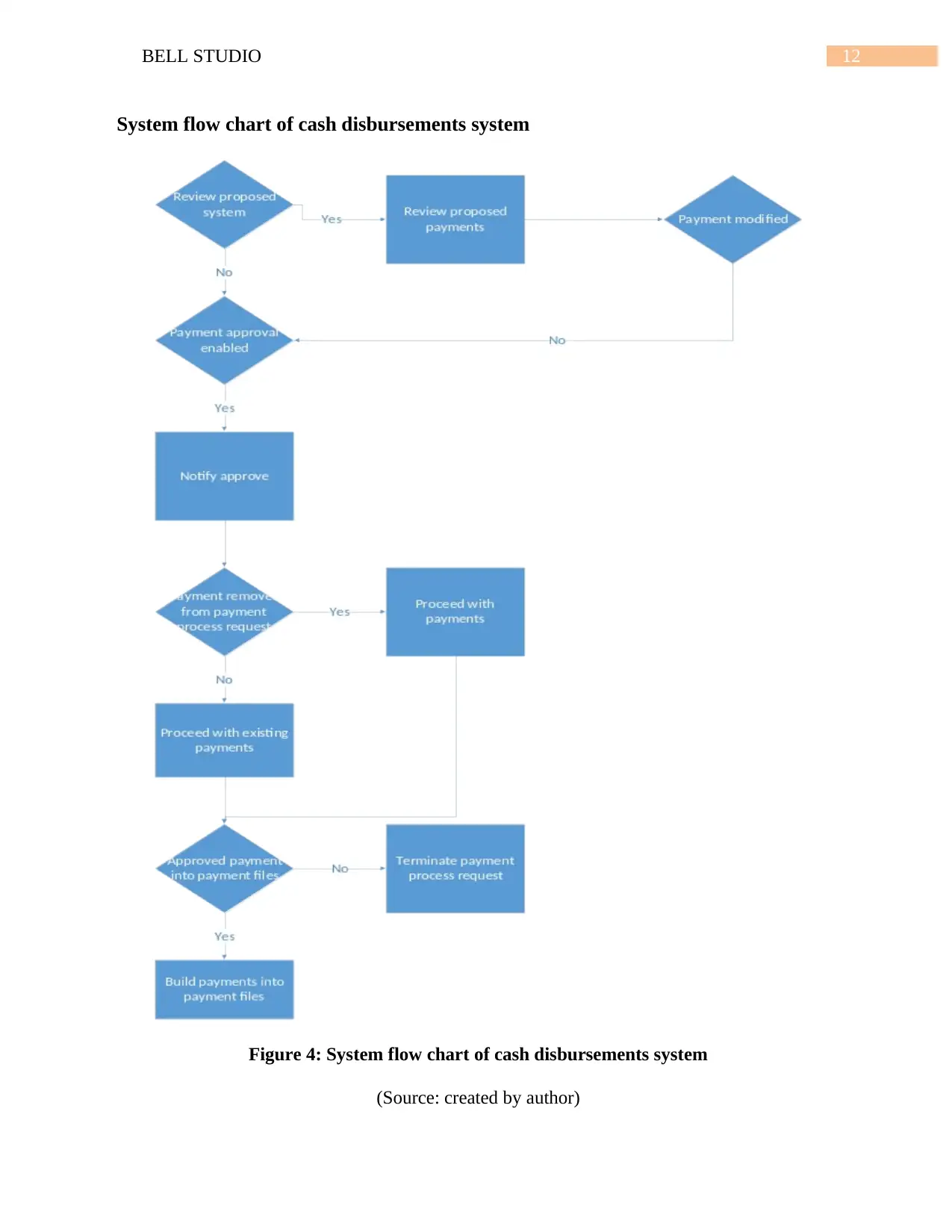
12BELL STUDIO
System flow chart of cash disbursements system
Figure 4: System flow chart of cash disbursements system
(Source: created by author)
System flow chart of cash disbursements system
Figure 4: System flow chart of cash disbursements system
(Source: created by author)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
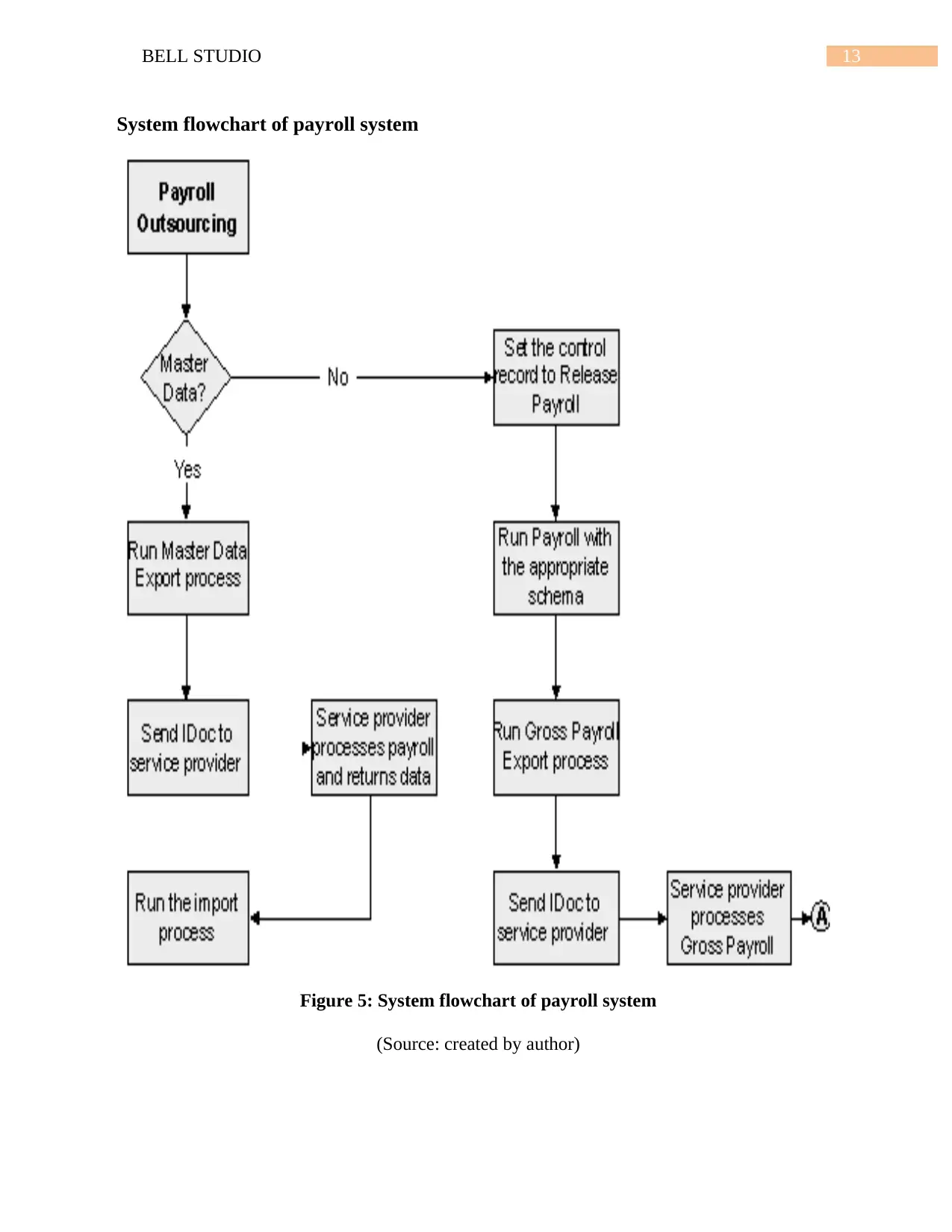
13BELL STUDIO
System flowchart of payroll system
Figure 5: System flowchart of payroll system
(Source: created by author)
System flowchart of payroll system
Figure 5: System flowchart of payroll system
(Source: created by author)

14BELL STUDIO
Conclusion
From the report presented above, it can be concluded that numerous operations which
have been carried by Bell Studio has numerous problems, the problems can be very vulnerable
in nature for the staffs of the company along with the entire organization by affecting the
processes that are being used by the organization. This assignment describes regarding the
organization named Bell Studio, it faces various challenges in the operations that are carried out
by the organization. The issues include some areas like payroll systems, ordering systems,
purchasing system and many more. The challenges that are faced by them can be resolved with
the use of computer systems, these systems would aim in providing further issues which can be
mitigated by the company. The issue might be physical and nonphysical as well. The description
of the issues and their mitigation strategies have been provided in this assignment.
Conclusion
From the report presented above, it can be concluded that numerous operations which
have been carried by Bell Studio has numerous problems, the problems can be very vulnerable
in nature for the staffs of the company along with the entire organization by affecting the
processes that are being used by the organization. This assignment describes regarding the
organization named Bell Studio, it faces various challenges in the operations that are carried out
by the organization. The issues include some areas like payroll systems, ordering systems,
purchasing system and many more. The challenges that are faced by them can be resolved with
the use of computer systems, these systems would aim in providing further issues which can be
mitigated by the company. The issue might be physical and nonphysical as well. The description
of the issues and their mitigation strategies have been provided in this assignment.

15BELL STUDIO
References
Cassidy, A., 2016. A practical guide to information systems strategic planning. Auerbach
Publications.
Chiang, R.H., Grover, V., Liang, T.P. and Zhang, D., 2018. Strategic Value of Big Data and
Business Analytics.
Chuang, S.H. and Lin, H.N., 2017. Performance implications of information-value offering in e-
service systems: Examining the resource-based perspective and innovation strategy. The Journal
of Strategic Information Systems, 26(1), pp.22-38.
Coltman, T., Tallon, P., Sharma, R. and Queiroz, M., 2015. Strategic IT alignment: twenty-five
years on.
DeLone, W.H. and McLean, E.R., 2016. Information systems success
measurement. Foundations and Trends® in Information Systems, 2(1), pp.1-116.
Dwivedi, Y.K., Wastell, D., Laumer, S., Henriksen, H.Z., Myers, M.D., Bunker, D., Elbanna,
A., Ravishankar, M.N. and Srivastava, S.C., 2015. Research on information systems failures and
successes: Status update and future directions. Information Systems Frontiers, 17(1), pp.143-
157.
Grover, V., Chiang, R.H., Liang, T.P. and Zhang, D., 2018. Creating strategic business value
from big data analytics: A research framework. Journal of Management Information
Systems, 35(2), pp.388-423.
Hung, S.Y., Huang, W.M., Yen, D.C., Chang, S.I. and Lu, C.C., 2016. Effect of information
service competence and contextual factors on the effectiveness of strategic information systems
planning in Hospitals. Journal of Global Information Management (JGIM), 24(1), pp.14-36.
References
Cassidy, A., 2016. A practical guide to information systems strategic planning. Auerbach
Publications.
Chiang, R.H., Grover, V., Liang, T.P. and Zhang, D., 2018. Strategic Value of Big Data and
Business Analytics.
Chuang, S.H. and Lin, H.N., 2017. Performance implications of information-value offering in e-
service systems: Examining the resource-based perspective and innovation strategy. The Journal
of Strategic Information Systems, 26(1), pp.22-38.
Coltman, T., Tallon, P., Sharma, R. and Queiroz, M., 2015. Strategic IT alignment: twenty-five
years on.
DeLone, W.H. and McLean, E.R., 2016. Information systems success
measurement. Foundations and Trends® in Information Systems, 2(1), pp.1-116.
Dwivedi, Y.K., Wastell, D., Laumer, S., Henriksen, H.Z., Myers, M.D., Bunker, D., Elbanna,
A., Ravishankar, M.N. and Srivastava, S.C., 2015. Research on information systems failures and
successes: Status update and future directions. Information Systems Frontiers, 17(1), pp.143-
157.
Grover, V., Chiang, R.H., Liang, T.P. and Zhang, D., 2018. Creating strategic business value
from big data analytics: A research framework. Journal of Management Information
Systems, 35(2), pp.388-423.
Hung, S.Y., Huang, W.M., Yen, D.C., Chang, S.I. and Lu, C.C., 2016. Effect of information
service competence and contextual factors on the effectiveness of strategic information systems
planning in Hospitals. Journal of Global Information Management (JGIM), 24(1), pp.14-36.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

16BELL STUDIO
Kamariotou, M. and Kitsios, F., 2019. Strategic information systems planning. In Advanced
Methodologies and Technologies in Business Operations and Management (pp. 535-546). IGI
Global.
Kitsios, F. and Kamariotou, M., 2016, September. Decision support systems and business
strategy: a conceptual framework for strategic information systems planning. In 2016 6th
International Conference on IT Convergence and Security (ICITCS) (pp. 1-5). IEEE.
Morecroft, J.D., 2015. Strategic modelling and business dynamics: A feedback systems
approach. John Wiley & Sons.
Pearlson, K.E., Saunders, C.S. and Galletta, D.F., 2016. Managing and using information
systems, binder ready version: a strategic approach. John Wiley & Sons.
Peppard, J. and Ward, J., 2016. The strategic management of information systems: Building a
digital strategy. John Wiley & Sons.
Vijayan, G.I., 2018, August. Strategic Environmental Assessment (SEA) Process for Green
Information Technology and Management Engineering Systems towards Sustainable Education
Process Business Excellence Achievements. In 2018 International Conference on Information
Technology and Management Engineering (ICITME 2018). Atlantis Press.
Wu, S.P.J., Straub, D.W. and Liang, T.P., 2015. How information technology governance
mechanisms and strategic alignment influence organizational performance: Insights from a
matched survey of business and IT managers. Mis Quarterly, 39(2), pp.497-518.
Yazid, A.S. and Kofarnaisa, F.U., 2019. Sophisticated strategic information systems and
strategic performance of Islamic banks: a review of literature. International Journal of Business
Information Systems, 30(1), pp.79-91.
Kamariotou, M. and Kitsios, F., 2019. Strategic information systems planning. In Advanced
Methodologies and Technologies in Business Operations and Management (pp. 535-546). IGI
Global.
Kitsios, F. and Kamariotou, M., 2016, September. Decision support systems and business
strategy: a conceptual framework for strategic information systems planning. In 2016 6th
International Conference on IT Convergence and Security (ICITCS) (pp. 1-5). IEEE.
Morecroft, J.D., 2015. Strategic modelling and business dynamics: A feedback systems
approach. John Wiley & Sons.
Pearlson, K.E., Saunders, C.S. and Galletta, D.F., 2016. Managing and using information
systems, binder ready version: a strategic approach. John Wiley & Sons.
Peppard, J. and Ward, J., 2016. The strategic management of information systems: Building a
digital strategy. John Wiley & Sons.
Vijayan, G.I., 2018, August. Strategic Environmental Assessment (SEA) Process for Green
Information Technology and Management Engineering Systems towards Sustainable Education
Process Business Excellence Achievements. In 2018 International Conference on Information
Technology and Management Engineering (ICITME 2018). Atlantis Press.
Wu, S.P.J., Straub, D.W. and Liang, T.P., 2015. How information technology governance
mechanisms and strategic alignment influence organizational performance: Insights from a
matched survey of business and IT managers. Mis Quarterly, 39(2), pp.497-518.
Yazid, A.S. and Kofarnaisa, F.U., 2019. Sophisticated strategic information systems and
strategic performance of Islamic banks: a review of literature. International Journal of Business
Information Systems, 30(1), pp.79-91.
1 out of 17
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)




