Strategic Information Systems: HI5019 Bell Studio Case Study Analysis
VerifiedAdded on 2023/03/23
|20
|3788
|84
Case Study
AI Summary
This case study analyzes Bell Studio's information systems, examining transaction cycles, financial and management reporting, and e-commerce aspects. It delves into the weaknesses in the purchase, cash disbursement, and payroll systems, highlighting issues like manual processes, human error, and non-compliance. The study identifies inherent risks in computer-based systems, including physical and non-physical threats, and explores the influence of various functional areas on disbursement practices. Furthermore, it discusses security measures for electronic commerce and the opportunities for computer fraud, offering data flow and system flow diagrams for clarity. The assignment aims to understand internal control weaknesses and the importance of risk mitigation strategies within the context of a business enterprise.

Running head: BELL STUDIO
BELL STUDIO
Name of Student
Name of University
Author’s Note
BELL STUDIO
Name of Student
Name of University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BELL STUDIO
Executive summary
Utilization of computer systems would allow the organization to automate most of their services
like ordering, processing the orders and many more. This reduces a huge amount of human error
that are involved in the entire system. Besides this, the usage of computer systems in the
operations can also prove to be the source of new risks, this takes place in most of the times and
the risks faced in the systems can be mitigated using various processes. The organization
selected for this particular organization is Bell Studio. Bell Studio also faces numerous issues in
its operations, the issues faced by the organization includes in the aspect of its payroll systems,
purchasing system, ordering system and many more. The systems of this organization has
numerous loopholes, these loopholes are mentioned in the report below, and they are presented
in details.
Executive summary
Utilization of computer systems would allow the organization to automate most of their services
like ordering, processing the orders and many more. This reduces a huge amount of human error
that are involved in the entire system. Besides this, the usage of computer systems in the
operations can also prove to be the source of new risks, this takes place in most of the times and
the risks faced in the systems can be mitigated using various processes. The organization
selected for this particular organization is Bell Studio. Bell Studio also faces numerous issues in
its operations, the issues faced by the organization includes in the aspect of its payroll systems,
purchasing system, ordering system and many more. The systems of this organization has
numerous loopholes, these loopholes are mentioned in the report below, and they are presented
in details.

2BELL STUDIO
Table of Contents
Introduction......................................................................................................................................3
Discussion........................................................................................................................................4
Internal control weaknesses.........................................................................................................4
Issues in purchase system........................................................................................................4
Issues in cash disbursement system.........................................................................................5
Various functional areas that influence disbursement.............................................................6
Issues in payroll system...........................................................................................................7
Risks inherent in computer based system 400.............................................................................8
Security measures in electronic commerce..................................................................................9
Data flow diagram of purchase and cash distribution systems..................................................11
Data flow diagram of payroll system.........................................................................................12
System flowchart of purchase system........................................................................................13
System flow chart of cash disbursements system......................................................................14
System flowchart of payroll system..........................................................................................15
Conclusion.....................................................................................................................................15
References......................................................................................................................................17
Table of Contents
Introduction......................................................................................................................................3
Discussion........................................................................................................................................4
Internal control weaknesses.........................................................................................................4
Issues in purchase system........................................................................................................4
Issues in cash disbursement system.........................................................................................5
Various functional areas that influence disbursement.............................................................6
Issues in payroll system...........................................................................................................7
Risks inherent in computer based system 400.............................................................................8
Security measures in electronic commerce..................................................................................9
Data flow diagram of purchase and cash distribution systems..................................................11
Data flow diagram of payroll system.........................................................................................12
System flowchart of purchase system........................................................................................13
System flow chart of cash disbursements system......................................................................14
System flowchart of payroll system..........................................................................................15
Conclusion.....................................................................................................................................15
References......................................................................................................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3BELL STUDIO
Introduction
Various operations that are undertaken within an organization might face numerous
issues, these issues can be solved with the usage of computer systems for carrying out most of
their operations. Usage of computer systems would allow the organization to automate most of
their services like ordering, processing the orders and many more. This reduces a huge amount
of human error which are involved in the entire system (Pearlson, Saunders and Galletta 2016).
Besides this, the usage of computer systems in the operations can also prove to be the source of
new risks, this takes place in most of the times and the risks faced in the systems can be
mitigated using various processes (Laudon and Laudon 2016). The risks faced by the
organization are dependent on the firms that it deals with along with the size of the firm.
The organization selected for this particular organization is Bell Studio, this organization
deals with a wholesaler art of supplies. It involves manufacturers from various countries
worldwide, some of the countries include Australia, Japan, China, New Zealand and many more.
This organization has various systems like purchase systems, cash distributed systems, payroll
systems and some more similar factors (Cassidy 2016). The systems of this organization has
numerous loopholes, these loopholes are mentioned in the report below, and they are presented
in details. This report further provides various diagrams like data flow diagrams of purchase and
cash distribution systems, System flowchart of purchases system, System flowchart of cash
disbursements system, Data flow diagram of payroll system, System flowchart of payroll
system, Description of internal control weakness in each system and risks associated with the
identified weakness (Chiang, Grover and Liang 2018). It also discusses regarding the threats that
might inherent in various computer based systems.
Introduction
Various operations that are undertaken within an organization might face numerous
issues, these issues can be solved with the usage of computer systems for carrying out most of
their operations. Usage of computer systems would allow the organization to automate most of
their services like ordering, processing the orders and many more. This reduces a huge amount
of human error which are involved in the entire system (Pearlson, Saunders and Galletta 2016).
Besides this, the usage of computer systems in the operations can also prove to be the source of
new risks, this takes place in most of the times and the risks faced in the systems can be
mitigated using various processes (Laudon and Laudon 2016). The risks faced by the
organization are dependent on the firms that it deals with along with the size of the firm.
The organization selected for this particular organization is Bell Studio, this organization
deals with a wholesaler art of supplies. It involves manufacturers from various countries
worldwide, some of the countries include Australia, Japan, China, New Zealand and many more.
This organization has various systems like purchase systems, cash distributed systems, payroll
systems and some more similar factors (Cassidy 2016). The systems of this organization has
numerous loopholes, these loopholes are mentioned in the report below, and they are presented
in details. This report further provides various diagrams like data flow diagrams of purchase and
cash distribution systems, System flowchart of purchases system, System flowchart of cash
disbursements system, Data flow diagram of payroll system, System flowchart of payroll
system, Description of internal control weakness in each system and risks associated with the
identified weakness (Chiang, Grover and Liang 2018). It also discusses regarding the threats that
might inherent in various computer based systems.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4BELL STUDIO
Discussion
Internal control weaknesses
Issues in purchase system
The purchase system of Bell Studio does not actually make use of any technology, it
processes its operations manually, and there exists a high level of complexity while taking as
well as fulfilling their orders. The might have various clauses like usage of multiple orders
capture as well as fulfillment legacy systems (DeLone and McLean 2016). A manual or a paper
based system for the purpose of procurement creates issues for the employees as well as the
entire organization. The organization is aiming at creating excess amount of documents. The
purchase cycle usually can consist up to 7 documents but more documents can hamper the entire
system (Ansoff, Kipley and Lewis 2018). The purchasing process includes requisitions,
purchasing various orders, order acknowledgements, quotations, good received notes, advice
notes, packing slips along with invoices. These are usually a huge amount of paper work to be
produced and keeping track of a particular process.
As much as proper record keeping is important for effective as well as efficient
procurement and purchasing, there are numerous problems that are included in the process of
paper based records (Wu, Straub and Liang 2015). The main issues that would be faced by the
organization include lost as well as damage of the records, they might get accidentally
destroyed. It would be usually hard to spot the fake requests, missing transactions and invoices;
these have high chances to cost a huge amount of money as well as time (Mignerat and Rivard
2015). Usage of manual process for the purpose of purchasing might require a regularly updated
as well as efficient filing system; these files would contain data regarding the purchases carried
out by the organization along with the organizational detail. Manual purchasing would require a
Discussion
Internal control weaknesses
Issues in purchase system
The purchase system of Bell Studio does not actually make use of any technology, it
processes its operations manually, and there exists a high level of complexity while taking as
well as fulfilling their orders. The might have various clauses like usage of multiple orders
capture as well as fulfillment legacy systems (DeLone and McLean 2016). A manual or a paper
based system for the purpose of procurement creates issues for the employees as well as the
entire organization. The organization is aiming at creating excess amount of documents. The
purchase cycle usually can consist up to 7 documents but more documents can hamper the entire
system (Ansoff, Kipley and Lewis 2018). The purchasing process includes requisitions,
purchasing various orders, order acknowledgements, quotations, good received notes, advice
notes, packing slips along with invoices. These are usually a huge amount of paper work to be
produced and keeping track of a particular process.
As much as proper record keeping is important for effective as well as efficient
procurement and purchasing, there are numerous problems that are included in the process of
paper based records (Wu, Straub and Liang 2015). The main issues that would be faced by the
organization include lost as well as damage of the records, they might get accidentally
destroyed. It would be usually hard to spot the fake requests, missing transactions and invoices;
these have high chances to cost a huge amount of money as well as time (Mignerat and Rivard
2015). Usage of manual process for the purpose of purchasing might require a regularly updated
as well as efficient filing system; these files would contain data regarding the purchases carried
out by the organization along with the organizational detail. Manual purchasing would require a

5BELL STUDIO
huge amount of regular updates and efficient filing system; this would consume a huge amount
of space as well as man hours for the purpose of working in an effective manner (Hung, Huang
and Yen 2016). The purchasing process include numerous steps which are very lengthy as well
as time consuming, hence the manual purchasing system requires more time than expected.
Issues in cash disbursement system
The cash disbursement system of the organization usually issued under numerous special
circumstances, inspite of this, it faces numerous issues. Suppose a particular vendor drops the
materials for a particular delivery and he is supposed to be paid for that delivery immediately,
and there is no option to get payment using the regular accounts payable process (Chuang and
Lin 2017). A cheque has to be provided to the vendor and then the accounting system is updated
later. This situation might be faced by the organization. These occurrences of various manual
disbursements have the ability to create an issue. It is a very easy way for a particular employee
to steam funds if he has access to signature stamps, cheques and many more organizational data
(Du Toit 2016). The theft can be covered with the help of entering data in the presented
accounting system that indicates cash only delivery from a particular supplier. The paperwork
might not be necessary because the process of payment does not always go through the accounts
payable system. Later on it is realized by an individual that the supporting documentation is not
present (Morecroft 2015). This is because it is one of the easiest way for committing fraud. It is
very important for the organization to examine various cash disbursements in order to check
how many times manual disbursements are carried out and the circumstances that surround these
payments. It can prove to be helpful for the organization to sample various disbursements and
hence look for some documentation on its support (Cui, Ye and Teo 2015). It is also very
important to check these, at the time when frequency is very high or unusual.
huge amount of regular updates and efficient filing system; this would consume a huge amount
of space as well as man hours for the purpose of working in an effective manner (Hung, Huang
and Yen 2016). The purchasing process include numerous steps which are very lengthy as well
as time consuming, hence the manual purchasing system requires more time than expected.
Issues in cash disbursement system
The cash disbursement system of the organization usually issued under numerous special
circumstances, inspite of this, it faces numerous issues. Suppose a particular vendor drops the
materials for a particular delivery and he is supposed to be paid for that delivery immediately,
and there is no option to get payment using the regular accounts payable process (Chuang and
Lin 2017). A cheque has to be provided to the vendor and then the accounting system is updated
later. This situation might be faced by the organization. These occurrences of various manual
disbursements have the ability to create an issue. It is a very easy way for a particular employee
to steam funds if he has access to signature stamps, cheques and many more organizational data
(Du Toit 2016). The theft can be covered with the help of entering data in the presented
accounting system that indicates cash only delivery from a particular supplier. The paperwork
might not be necessary because the process of payment does not always go through the accounts
payable system. Later on it is realized by an individual that the supporting documentation is not
present (Morecroft 2015). This is because it is one of the easiest way for committing fraud. It is
very important for the organization to examine various cash disbursements in order to check
how many times manual disbursements are carried out and the circumstances that surround these
payments. It can prove to be helpful for the organization to sample various disbursements and
hence look for some documentation on its support (Cui, Ye and Teo 2015). It is also very
important to check these, at the time when frequency is very high or unusual.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6BELL STUDIO
Suppose the accounting manager had written cheques to himself and various manual
disbursements to various suppliers in order to maintain a bank account along with covering the
theft. He had known that the control of the company on supplies as well as inventory was poor,
hence management will not be able to reconcile amount on the accounting record (Aversa,
Cabantous and Haefliger 2018). After the theft had been uncovered, a particular examination on
disbursements had revealed a high amount of manual disbursements. Management had known
that the cash deliveries had been rare hence there must not be any volume of payments that had
been issued manually (Lee, Thomas and Baskerville 2015). If someone had been examined these
type of transactions, the theft would not have occurred. This example described, why it is
important for examining various disbursements. The accounting system of the company would
have a particular way for identifying the unusual payments (Peltier 2016). It might be a labor
intensive process for examining the disbursements. The work might result to be helpful when
fraud had been identified.
Various functional areas that influence disbursement
Organizational unit Practices or policies influenced
Accounts payable department Distributed policies
Disbursement scheduling or forecasts
Discount policies
Distributed records
Invoice information
Production department Status of inventory position
Initiation of orders and quantities
Initiation of charge-backs
Purchasing department Discount policies
Assist in determination of orders and
quantities
Usage of electronic purchase orders
and payment
Negotiation for vendors, terms and
prices
Vendor relations
Negotiation for vendors, terms and
Suppose the accounting manager had written cheques to himself and various manual
disbursements to various suppliers in order to maintain a bank account along with covering the
theft. He had known that the control of the company on supplies as well as inventory was poor,
hence management will not be able to reconcile amount on the accounting record (Aversa,
Cabantous and Haefliger 2018). After the theft had been uncovered, a particular examination on
disbursements had revealed a high amount of manual disbursements. Management had known
that the cash deliveries had been rare hence there must not be any volume of payments that had
been issued manually (Lee, Thomas and Baskerville 2015). If someone had been examined these
type of transactions, the theft would not have occurred. This example described, why it is
important for examining various disbursements. The accounting system of the company would
have a particular way for identifying the unusual payments (Peltier 2016). It might be a labor
intensive process for examining the disbursements. The work might result to be helpful when
fraud had been identified.
Various functional areas that influence disbursement
Organizational unit Practices or policies influenced
Accounts payable department Distributed policies
Disbursement scheduling or forecasts
Discount policies
Distributed records
Invoice information
Production department Status of inventory position
Initiation of orders and quantities
Initiation of charge-backs
Purchasing department Discount policies
Assist in determination of orders and
quantities
Usage of electronic purchase orders
and payment
Negotiation for vendors, terms and
prices
Vendor relations
Negotiation for vendors, terms and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7BELL STUDIO
prices
Personnel department Negotiation of wages and pay periods
Localized payroll policies
Direct deposit policies
Treasury department Bank relationships
Bank services
Disbursement policies
Funding policies
Disbursement mechanisms
Account balance overnight
Table: functional areas that influence disbursement
(Source: Kummer and Schmiedel 2016)
Issues in payroll system
Some issues that exist in the enterprise are presented below
Human error: The enterprise goes through a particular payroll process in a manual manner,
they usually undergo a great amount of frustration which is accompanied by various
interventions that are manual in nature. The payroll processing system had overburdened
numerous professionals including the finance teams, they left them with various mundane
activities such as repetitive cross checking and documentation (Goni, Chofreh and
Mukhtar2017). Suppose the enterprise had been through a particular transaction and this
transaction had been checked in an appropriate manner, after few months the professions require
the data regarding the transaction, for this purpose they need to inspect the transaction once
again, this causes a huge problem for them because the detailed data related to the activity is not
saved (Dwivedi, Wastell and Laumer 2015). This process is also very prone to various human
errors.
Non- compliance: The payroll processing system that exists within the organization is non-
compliance in nature. This particular process requires more attention for making improvement
legislative updates (Pearlson, Saunders and Galletta 2016). Faltering on and abiding by statutory
prices
Personnel department Negotiation of wages and pay periods
Localized payroll policies
Direct deposit policies
Treasury department Bank relationships
Bank services
Disbursement policies
Funding policies
Disbursement mechanisms
Account balance overnight
Table: functional areas that influence disbursement
(Source: Kummer and Schmiedel 2016)
Issues in payroll system
Some issues that exist in the enterprise are presented below
Human error: The enterprise goes through a particular payroll process in a manual manner,
they usually undergo a great amount of frustration which is accompanied by various
interventions that are manual in nature. The payroll processing system had overburdened
numerous professionals including the finance teams, they left them with various mundane
activities such as repetitive cross checking and documentation (Goni, Chofreh and
Mukhtar2017). Suppose the enterprise had been through a particular transaction and this
transaction had been checked in an appropriate manner, after few months the professions require
the data regarding the transaction, for this purpose they need to inspect the transaction once
again, this causes a huge problem for them because the detailed data related to the activity is not
saved (Dwivedi, Wastell and Laumer 2015). This process is also very prone to various human
errors.
Non- compliance: The payroll processing system that exists within the organization is non-
compliance in nature. This particular process requires more attention for making improvement
legislative updates (Pearlson, Saunders and Galletta 2016). Faltering on and abiding by statutory

8BELL STUDIO
laws has the ability to make the organization serve severe penalties and serves for the reason of
non-compliance.
Risks inherent in computer based system 400
Computer system threat can be described as the one that leads to corruption or loss of
information or any sort of physical damage to hardware and infrastructure. Knowing the ways
by which computer security threats are to be identified is considered as the very first step in the
process of protecting computer systems (Laudon and Laudon 2016). These threats might be
accidental, intentional and they might also be caused by various natural disasters. The security
threats could be defined as a particular risk that has the ability to potentially harm various
computer systems as well as organization (Cassidy 2016). There are various risk that can be
faced by a particular computer based system might be physical in nature, physical threat is a
particular potential cause of any sort of accident which might result in sort of loss or any
physical damage to the systems (DeLone and McLean 2016). Physical threat can be divided into
various categories include internal, external and human. The description of these categories as
follows
Internal threat: these threats include the damage caused by fire, humidity in office rooms
which causes housing or hardware, unstable supply of power and many more.
External threat: this kind of threats are caused due to floods, lightning, earthquakes and
many more.
Human: this sort of damage is cause due to theft, vandalism of hardware, vandalism of
infrastructure, disruption, accidental or any sort of intentional errors.
There are numerous non-physical threats that might be faced by computer systems, these
issues include loss and corruption of the system information, disruption of various business
laws has the ability to make the organization serve severe penalties and serves for the reason of
non-compliance.
Risks inherent in computer based system 400
Computer system threat can be described as the one that leads to corruption or loss of
information or any sort of physical damage to hardware and infrastructure. Knowing the ways
by which computer security threats are to be identified is considered as the very first step in the
process of protecting computer systems (Laudon and Laudon 2016). These threats might be
accidental, intentional and they might also be caused by various natural disasters. The security
threats could be defined as a particular risk that has the ability to potentially harm various
computer systems as well as organization (Cassidy 2016). There are various risk that can be
faced by a particular computer based system might be physical in nature, physical threat is a
particular potential cause of any sort of accident which might result in sort of loss or any
physical damage to the systems (DeLone and McLean 2016). Physical threat can be divided into
various categories include internal, external and human. The description of these categories as
follows
Internal threat: these threats include the damage caused by fire, humidity in office rooms
which causes housing or hardware, unstable supply of power and many more.
External threat: this kind of threats are caused due to floods, lightning, earthquakes and
many more.
Human: this sort of damage is cause due to theft, vandalism of hardware, vandalism of
infrastructure, disruption, accidental or any sort of intentional errors.
There are numerous non-physical threats that might be faced by computer systems, these
issues include loss and corruption of the system information, disruption of various business
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9BELL STUDIO
operations which has the tendency to rely on various computer systems, loss of confidential
information, illegal monitoring of various activities on the computer systems, cyber security
breaches and may more (Wu, Straub and Liang 2015). The nonphysical threats can also be called
as various logical threats. The common types of threats that are non-physical in nature include
viruses, Trojans, worms, spyware, key loggers, adware, denial of serve attacks, distributed denial
of service attacks, unauthorized access to the computer systems and resources like data, phishing
and many more computer security risks (Mignerat and Rivard 2015). The risks inherited in the
computer systems also includes some involvement of ethics. An organization must never allow
any employee to access data owned by other employees until and unless it is very urgent, this is
included within the ethical behavior of an employee (Morecroft 2015). Suppose an employee
accesses a particular data that belongs to another employee and that employee was supposed to
be confidential, the employee discloses the data within the organization, this would be violation
of the ethical roles within the policy (Chuang and Lin 2017). Hence ethics should be in place
during implementation of any strategy or process.
Security measures in electronic commerce
Threat can be defined as a particular activity which can lead to data corruption as well as
data loss that is through to the disruption of normal operations of the business (Kummer and
Schmiedel 2016). There are physical as well as nonphysical risks, these risks are mentioned
above and can be mitigated using various measures, these measures are mentioned below
In order to protect various computer systems from various mentioned physical threats, the
organization should have various physical security control measures, the measures are
Internal: fire threats can be prevented with the usage of automatic fire detectors as well as
extinguishers which do not make use of water for the purpose of putting out fire (Aversa,
operations which has the tendency to rely on various computer systems, loss of confidential
information, illegal monitoring of various activities on the computer systems, cyber security
breaches and may more (Wu, Straub and Liang 2015). The nonphysical threats can also be called
as various logical threats. The common types of threats that are non-physical in nature include
viruses, Trojans, worms, spyware, key loggers, adware, denial of serve attacks, distributed denial
of service attacks, unauthorized access to the computer systems and resources like data, phishing
and many more computer security risks (Mignerat and Rivard 2015). The risks inherited in the
computer systems also includes some involvement of ethics. An organization must never allow
any employee to access data owned by other employees until and unless it is very urgent, this is
included within the ethical behavior of an employee (Morecroft 2015). Suppose an employee
accesses a particular data that belongs to another employee and that employee was supposed to
be confidential, the employee discloses the data within the organization, this would be violation
of the ethical roles within the policy (Chuang and Lin 2017). Hence ethics should be in place
during implementation of any strategy or process.
Security measures in electronic commerce
Threat can be defined as a particular activity which can lead to data corruption as well as
data loss that is through to the disruption of normal operations of the business (Kummer and
Schmiedel 2016). There are physical as well as nonphysical risks, these risks are mentioned
above and can be mitigated using various measures, these measures are mentioned below
In order to protect various computer systems from various mentioned physical threats, the
organization should have various physical security control measures, the measures are
Internal: fire threats can be prevented with the usage of automatic fire detectors as well as
extinguishers which do not make use of water for the purpose of putting out fire (Aversa,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10BELL STUDIO
Cabantous and Haefliger 2018). Unstable power supply could be avoided by the usage of
various voltage controllers. A particular air conditioner could be used for the purpose of
controlling the humidity in the room where computers are stored.
External: systems for lightning protection could be used for protecting computer systems
against these attacks. Lightning protection systems might not be perfect but up to a particular
extent, they would reduce the chance of lightning that causes damage (Lee, Thomas and
Baskerville 2015). Housing the computer systems in various high lands can be considered as one
of the ways for the purpose of protecting systems against natural disasters like floods.
Humans: threats like theft could be prevented with the usage of locked doors as well as
restricted access to the computer rooms.
In order to protect various computer systems from various threats that, they must have
various logical security measures as well in proper place (Peltier 2016). Some possible measures
that could be used by the organizations in order to protect their cyber security threats are as
follows
Cabantous and Haefliger 2018). Unstable power supply could be avoided by the usage of
various voltage controllers. A particular air conditioner could be used for the purpose of
controlling the humidity in the room where computers are stored.
External: systems for lightning protection could be used for protecting computer systems
against these attacks. Lightning protection systems might not be perfect but up to a particular
extent, they would reduce the chance of lightning that causes damage (Lee, Thomas and
Baskerville 2015). Housing the computer systems in various high lands can be considered as one
of the ways for the purpose of protecting systems against natural disasters like floods.
Humans: threats like theft could be prevented with the usage of locked doors as well as
restricted access to the computer rooms.
In order to protect various computer systems from various threats that, they must have
various logical security measures as well in proper place (Peltier 2016). Some possible measures
that could be used by the organizations in order to protect their cyber security threats are as
follows
11BELL STUDIO
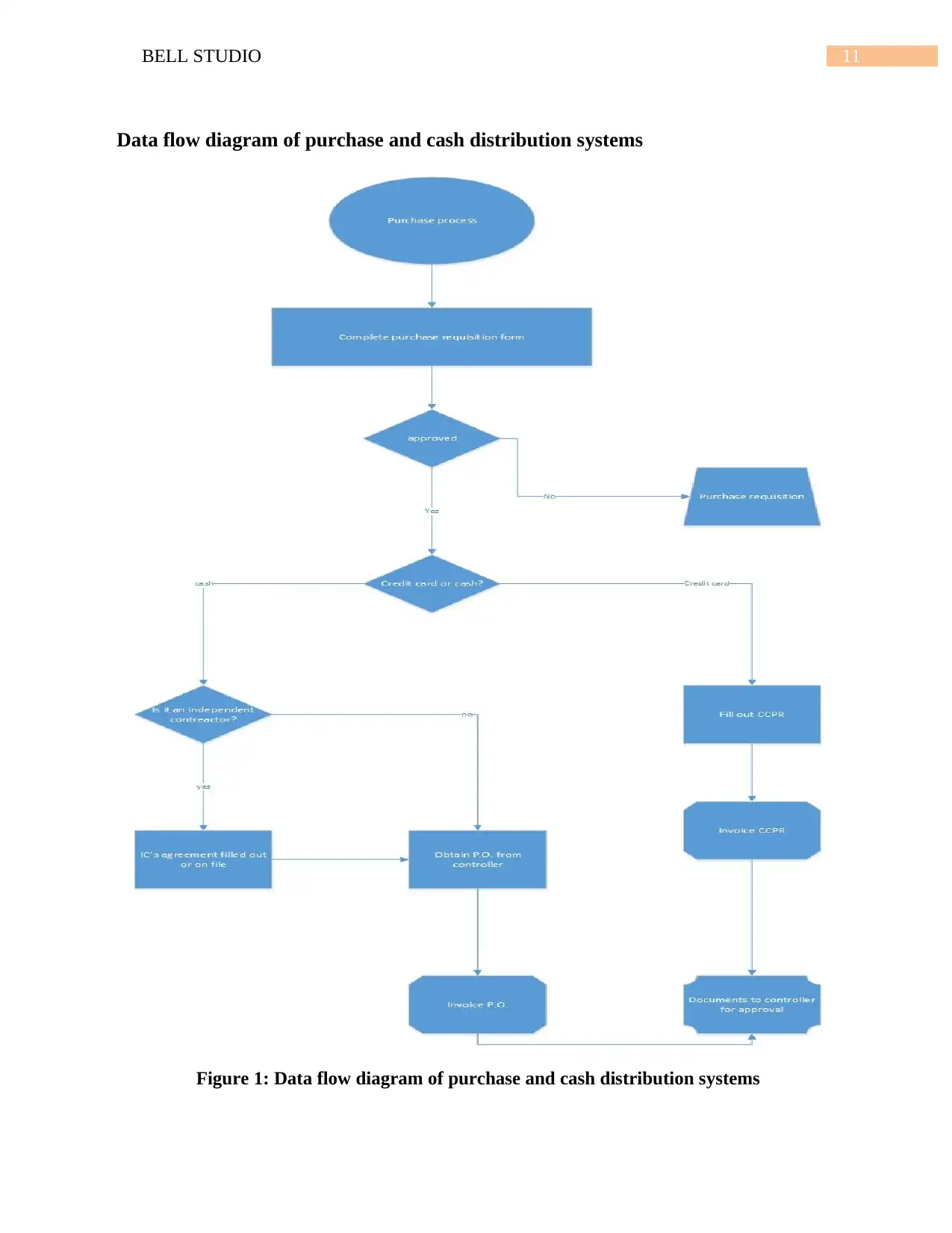
Data flow diagram of purchase and cash distribution systems
Figure 1: Data flow diagram of purchase and cash distribution systems
Data flow diagram of purchase and cash distribution systems
Figure 1: Data flow diagram of purchase and cash distribution systems
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





