A Research Report: BYOD Security Threats, Policies, and Implementation
VerifiedAdded on 2021/02/20
|12
|4334
|405
Report
AI Summary
This research report explores the Bring Your Own Device (BYOD) concept, examining its advantages and disadvantages in the workplace. The report focuses on the security threats associated with BYOD, including data breaches, malware, and unauthorized access, while also highlighting the benefits such as increased employee satisfaction and cost savings. It delves into the importance of BYOD, its uses, and the steps required for effective implementation. The report emphasizes the significance of security measures and countermeasures to mitigate risks and ensure data protection. The research includes a literature review and provides insights into the research problem of BYOD security threats. Furthermore, the report provides the steps for the successful implementation of the BYOD.

RESEARCH PROJECT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
ABSTRACT........................................................................................................................................................................1
INTRODUCTION...............................................................................................................................................................1
MAIN BODY.....................................................................................................................................................................2
CONCLUSION ..................................................................................................................................................................9
REFERENCES..................................................................................................................................................................10
ABSTRACT........................................................................................................................................................................1
INTRODUCTION...............................................................................................................................................................1
MAIN BODY.....................................................................................................................................................................2
CONCLUSION ..................................................................................................................................................................9
REFERENCES..................................................................................................................................................................10

ABSTRACT
BYOD devices means that the bring your own devices at the work place. In this concept the organisation
allows to the employees to bring their own devices at the workplace for the work. This is a beneficial for the
organisation because it save the cost of the installation of the working devices and employees are familiar to use
there own devices which increase there work efficiency and the working of the employees (Cheng, Guan and
Chau, 2016).
This term is used in the year of the 2009 firstly and credit goes to the Intel which started the concept of
bring Presenown smartphone and devices at the work place. And currently many organisations are using this
concept.
In essay the emphasizes is laid on identification of the issues associated with the use of BYOD device. In
addition to this, other problem highlighted in the essay is related to policy misuse. In essay the focus is on
advantages and disadvantages f BYOD devices. It has been found that BYOD in a useful technique for the
organisation because it helps to increase the productivity of the employees.
INTRODUCTION
Research is the process of collection of the data where it helps in the get the informations about the research
project research is the key to get success of any business or any of the research to the end of the work (Gray and
Malins, 2016). Organisation took help of the research to get there profits increase and to get the knowledge about
the given research problem. This report is based on the Security threats related to BYOD devices and
countermeasures. BYOD devices means the bring your own devices to the workplace is called the BYOD devices or
the BYOD concept. This is the widely used concept which is currently used in the process of the working in the
organisations. Also it can be says that the the employees use their own devices on the work place for the working.
This report will include the study based on the security threats of the BYOD devices or it can be says that the
measure security problems faced by the organisation. Further this report will includes the countermeasure should
be adopted for the security from the BYOD policy misuse or it can be prevention of the use of the techniques.
Further the repost will include the advantages and the disadvantage of the bring your own device and Steps to
implementation of the BYOD. It also includes the prevention should be done for the successful implementation of
the concept.
Research Problem
BYOD in a useful technique for the organisation because it helps to increase the productivity of the employees
Increase in the security threat in BYOD in a useful technique for the organisation because it helps to increase the
BYOD devices means that the bring your own devices at the work place. In this concept the organisation
allows to the employees to bring their own devices at the workplace for the work. This is a beneficial for the
organisation because it save the cost of the installation of the working devices and employees are familiar to use
there own devices which increase there work efficiency and the working of the employees (Cheng, Guan and
Chau, 2016).
This term is used in the year of the 2009 firstly and credit goes to the Intel which started the concept of
bring Presenown smartphone and devices at the work place. And currently many organisations are using this
concept.
In essay the emphasizes is laid on identification of the issues associated with the use of BYOD device. In
addition to this, other problem highlighted in the essay is related to policy misuse. In essay the focus is on
advantages and disadvantages f BYOD devices. It has been found that BYOD in a useful technique for the
organisation because it helps to increase the productivity of the employees.
INTRODUCTION
Research is the process of collection of the data where it helps in the get the informations about the research
project research is the key to get success of any business or any of the research to the end of the work (Gray and
Malins, 2016). Organisation took help of the research to get there profits increase and to get the knowledge about
the given research problem. This report is based on the Security threats related to BYOD devices and
countermeasures. BYOD devices means the bring your own devices to the workplace is called the BYOD devices or
the BYOD concept. This is the widely used concept which is currently used in the process of the working in the
organisations. Also it can be says that the the employees use their own devices on the work place for the working.
This report will include the study based on the security threats of the BYOD devices or it can be says that the
measure security problems faced by the organisation. Further this report will includes the countermeasure should
be adopted for the security from the BYOD policy misuse or it can be prevention of the use of the techniques.
Further the repost will include the advantages and the disadvantage of the bring your own device and Steps to
implementation of the BYOD. It also includes the prevention should be done for the successful implementation of
the concept.
Research Problem
BYOD in a useful technique for the organisation because it helps to increase the productivity of the employees
Increase in the security threat in BYOD in a useful technique for the organisation because it helps to increase the
You're viewing a preview
Unlock full access by subscribing today!

productivity of the employees relation to BYOD devices is the main issue which is highlighted in the report.
Research has been conducted in order to identify the reason for increase in such type of risk.
Literature Review
BYOD- Bring Your Own Devices
According to the view of author Bratthall Tideman and Lindström, 2018, the employees should bring their won
devices to do work. This concept is used by the many organisation in the world. Also it means that the policy where
employees brings the personally own devices in the organisation to work and they have authority to access the
data base of the company and the email of the company . However , it has been critique by other authors who
perceives that if workers will bring the BYOD devices at workplace they will get an access to email and the
database of the company which might lead to increase in threat to security and there are high chances of
unauthorised access of information by employees. According to the opinion of Keyes, 2016, management in an
organisation by allowing people to bring BYOD devices at workplace can support employees in improving their
performance and productivity at workplace. The author (Song and Kong, 2017). has stated that allow2ing the
BYOD devices at workplace will help in ensuring the development of working efficiency of the employees because
if the employees are using their own device than they are familiar with those devices which increase the efficiency
Importance of BYOD
According to the view of (Weeger, Wang and Gewald, 2016, BYOD is useful for every organisation
because it helps t o get the work done on time through the own devices because the person is familiar about using
of the devices and this help to use them without any hesitation. However, it has been argued by the other author
that allowing the BYOD devices will help in increasing the morale and convenience of the using own devices.
According to the investigation conducted by the IBM results of which reveals that the 82% of employees believes
that the using own devices in the working makes the easier the task and it plays critical role in the business.
Uses of BYOD devices
BYOD devices means the bring your own device at the work place such as the laptops, smartphones and tablet
PCs for the work in addition to the company supplied devices or instead of the company. Using own devices
increase the efficiency of the workers and it also increase the working speed and the performance of the
employees . Prevalence for the PresenBYOD in increasing with the increase in the technology. Major reason
behind the increase in the BYOD is to people use the high end devices and the computing technologies and familiar
with the own devices and operating systems. It will leads to the increase in the process of the working quite easy
than using the systems of organisation. Using the this concept also reduce the cost of the organisation because for
the installation of the high end techniques and devices may be charge a huge cost over the company but allowing
to bring own devices help to reduce that cost and reduce the investment of the company. As per the view of (Kant
and Lim Brocade Communications Systems LLC, 2017, BYOD helps companies to stay abreast to change in
technology because the employees use their own devices that is updated technologies and they use the same for
the organisation which lead to increase the productivity and the efficiency of the company . At present the
Research has been conducted in order to identify the reason for increase in such type of risk.
Literature Review
BYOD- Bring Your Own Devices
According to the view of author Bratthall Tideman and Lindström, 2018, the employees should bring their won
devices to do work. This concept is used by the many organisation in the world. Also it means that the policy where
employees brings the personally own devices in the organisation to work and they have authority to access the
data base of the company and the email of the company . However , it has been critique by other authors who
perceives that if workers will bring the BYOD devices at workplace they will get an access to email and the
database of the company which might lead to increase in threat to security and there are high chances of
unauthorised access of information by employees. According to the opinion of Keyes, 2016, management in an
organisation by allowing people to bring BYOD devices at workplace can support employees in improving their
performance and productivity at workplace. The author (Song and Kong, 2017). has stated that allow2ing the
BYOD devices at workplace will help in ensuring the development of working efficiency of the employees because
if the employees are using their own device than they are familiar with those devices which increase the efficiency
Importance of BYOD
According to the view of (Weeger, Wang and Gewald, 2016, BYOD is useful for every organisation
because it helps t o get the work done on time through the own devices because the person is familiar about using
of the devices and this help to use them without any hesitation. However, it has been argued by the other author
that allowing the BYOD devices will help in increasing the morale and convenience of the using own devices.
According to the investigation conducted by the IBM results of which reveals that the 82% of employees believes
that the using own devices in the working makes the easier the task and it plays critical role in the business.
Uses of BYOD devices
BYOD devices means the bring your own device at the work place such as the laptops, smartphones and tablet
PCs for the work in addition to the company supplied devices or instead of the company. Using own devices
increase the efficiency of the workers and it also increase the working speed and the performance of the
employees . Prevalence for the PresenBYOD in increasing with the increase in the technology. Major reason
behind the increase in the BYOD is to people use the high end devices and the computing technologies and familiar
with the own devices and operating systems. It will leads to the increase in the process of the working quite easy
than using the systems of organisation. Using the this concept also reduce the cost of the organisation because for
the installation of the high end techniques and devices may be charge a huge cost over the company but allowing
to bring own devices help to reduce that cost and reduce the investment of the company. As per the view of (Kant
and Lim Brocade Communications Systems LLC, 2017, BYOD helps companies to stay abreast to change in
technology because the employees use their own devices that is updated technologies and they use the same for
the organisation which lead to increase the productivity and the efficiency of the company . At present the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

revolution is take place and organisations are rely a lot on the BYOD concept. According to survey 40%
organisation are using this concept and at the end of the decade the 85% will be use this process. Most user of the
BYOD are small and medium size enterprises and organisation.
Advantages of the BYOD
Employ ee satisfaction:- it increase the employees satisfaction because if the employees are free to bring there
own devices it gives them motivation and increase there moral of working so that they will work hard for the
organisation. Also it increase the flexibility of the working in the of the of the employees so that they can work
according to their comfort. It make the employees loyal towards the organisation.
Decrease hardware investment: it decrease the hardware investment for the organisation because if the
employees work with the own devices than it need not install the technology for the organisation (Hong and et.al.,
2016).
Cost saving:- it is cost saving method for the organisation because if the employees cam work with their own
devices so that it saves the cost of the technological upgradation and maintenance of the devices and also reduce
the cost of the update the devices. So it can be says that the this are the cost efficient methods for the
organisation.
Increase the productivity and innovation:- it increase the productivity of the employees because if the employees
are motivated and free to work on their own devices so that they are familiar with their devices which increase
their speed and accuracy of the work. It save the time of working and gives the better result of the working so that
it can be completed on time. If a employee is completing the work on time in extraordinary performance so that it
increase the productivity of the firm (Dang-Pham and Pittayachawan, 2015).
Take the advantages of the newer technologies:- all the devices available with the employees are technologically
updated which can be use for the working. so it is beneficialPresen for the organisation to use the newer
technology. Which make work more accurate and efficient.
Issues related to security with BYOD devices or disadvantages of the BYOD
there are several problem will be faced by the organisation due to use the policy of the BYOD because it create
mPresenany security issues and many more as follows-
security issue:- using the own device may not insure the organisation that employees will remain loyal for the
organisation and the will not harm data of the company. It has the issue of the threats due the the numbers of
people access the company data and some may misuse the data of the company provided to them. It could also be
malware get through the BYOD devices.
Data can be stolen from the own devices and it can be goes in the wrong hand which may company could face the
losses from it. Many experts says that the using the own devices means to share the privacy of the company
(Garba and et.al., 2015).
organisation are using this concept and at the end of the decade the 85% will be use this process. Most user of the
BYOD are small and medium size enterprises and organisation.
Advantages of the BYOD
Employ ee satisfaction:- it increase the employees satisfaction because if the employees are free to bring there
own devices it gives them motivation and increase there moral of working so that they will work hard for the
organisation. Also it increase the flexibility of the working in the of the of the employees so that they can work
according to their comfort. It make the employees loyal towards the organisation.
Decrease hardware investment: it decrease the hardware investment for the organisation because if the
employees work with the own devices than it need not install the technology for the organisation (Hong and et.al.,
2016).
Cost saving:- it is cost saving method for the organisation because if the employees cam work with their own
devices so that it saves the cost of the technological upgradation and maintenance of the devices and also reduce
the cost of the update the devices. So it can be says that the this are the cost efficient methods for the
organisation.
Increase the productivity and innovation:- it increase the productivity of the employees because if the employees
are motivated and free to work on their own devices so that they are familiar with their devices which increase
their speed and accuracy of the work. It save the time of working and gives the better result of the working so that
it can be completed on time. If a employee is completing the work on time in extraordinary performance so that it
increase the productivity of the firm (Dang-Pham and Pittayachawan, 2015).
Take the advantages of the newer technologies:- all the devices available with the employees are technologically
updated which can be use for the working. so it is beneficialPresen for the organisation to use the newer
technology. Which make work more accurate and efficient.
Issues related to security with BYOD devices or disadvantages of the BYOD
there are several problem will be faced by the organisation due to use the policy of the BYOD because it create
mPresenany security issues and many more as follows-
security issue:- using the own device may not insure the organisation that employees will remain loyal for the
organisation and the will not harm data of the company. It has the issue of the threats due the the numbers of
people access the company data and some may misuse the data of the company provided to them. It could also be
malware get through the BYOD devices.
Data can be stolen from the own devices and it can be goes in the wrong hand which may company could face the
losses from it. Many experts says that the using the own devices means to share the privacy of the company
(Garba and et.al., 2015).
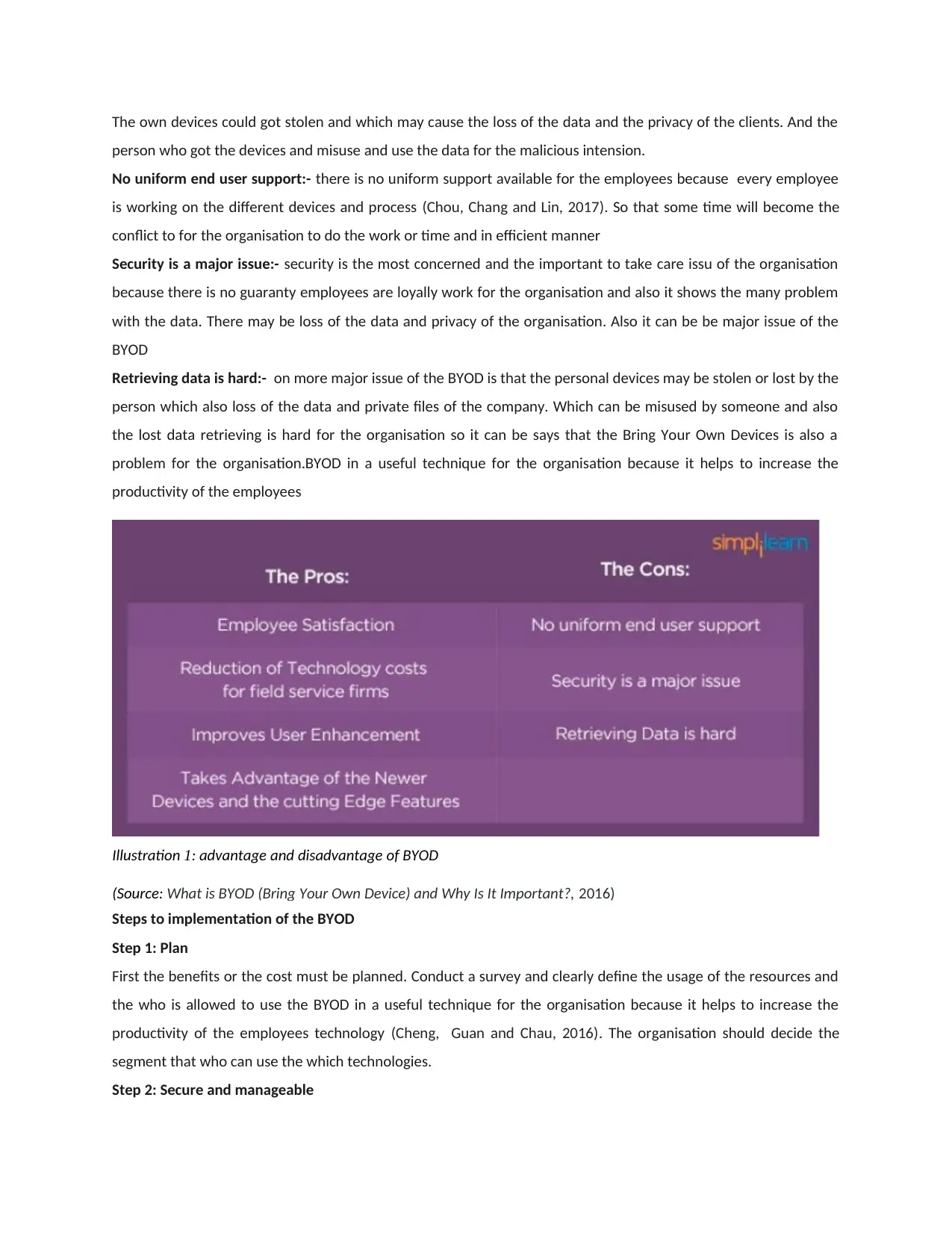
The own devices could got stolen and which may cause the loss of the data and the privacy of the clients. And the
person who got the devices and misuse and use the data for the malicious intension.
No uniform end user support:- there is no uniform support available for the employees because every employee
is working on the different devices and process (Chou, Chang and Lin, 2017). So that some time will become the
conflict to for the organisation to do the work or time and in efficient manner
Security is a major issue:- security is the most concerned and the important to take care issu of the organisation
because there is no guaranty employees are loyally work for the organisation and also it shows the many problem
with the data. There may be loss of the data and privacy of the organisation. Also it can be be major issue of the
BYOD
Retrieving data is hard:- on more major issue of the BYOD is that the personal devices may be stolen or lost by the
person which also loss of the data and private files of the company. Which can be misused by someone and also
the lost data retrieving is hard for the organisation so it can be says that the Bring Your Own Devices is also a
problem for the organisation.BYOD in a useful technique for the organisation because it helps to increase the
productivity of the employees
Illustration 1: advantage and disadvantage of BYOD
(Source: What is BYOD (Bring Your Own Device) and Why Is It Important?, 2016)
Steps to implementation of the BYOD
Step 1: Plan
First the benefits or the cost must be planned. Conduct a survey and clearly define the usage of the resources and
the who is allowed to use the BYOD in a useful technique for the organisation because it helps to increase the
productivity of the employees technology (Cheng, Guan and Chau, 2016). The organisation should decide the
segment that who can use the which technologies.
Step 2: Secure and manageable
person who got the devices and misuse and use the data for the malicious intension.
No uniform end user support:- there is no uniform support available for the employees because every employee
is working on the different devices and process (Chou, Chang and Lin, 2017). So that some time will become the
conflict to for the organisation to do the work or time and in efficient manner
Security is a major issue:- security is the most concerned and the important to take care issu of the organisation
because there is no guaranty employees are loyally work for the organisation and also it shows the many problem
with the data. There may be loss of the data and privacy of the organisation. Also it can be be major issue of the
BYOD
Retrieving data is hard:- on more major issue of the BYOD is that the personal devices may be stolen or lost by the
person which also loss of the data and private files of the company. Which can be misused by someone and also
the lost data retrieving is hard for the organisation so it can be says that the Bring Your Own Devices is also a
problem for the organisation.BYOD in a useful technique for the organisation because it helps to increase the
productivity of the employees
Illustration 1: advantage and disadvantage of BYOD
(Source: What is BYOD (Bring Your Own Device) and Why Is It Important?, 2016)
Steps to implementation of the BYOD
Step 1: Plan
First the benefits or the cost must be planned. Conduct a survey and clearly define the usage of the resources and
the who is allowed to use the BYOD in a useful technique for the organisation because it helps to increase the
productivity of the employees technology (Cheng, Guan and Chau, 2016). The organisation should decide the
segment that who can use the which technologies.
Step 2: Secure and manageable
You're viewing a preview
Unlock full access by subscribing today!
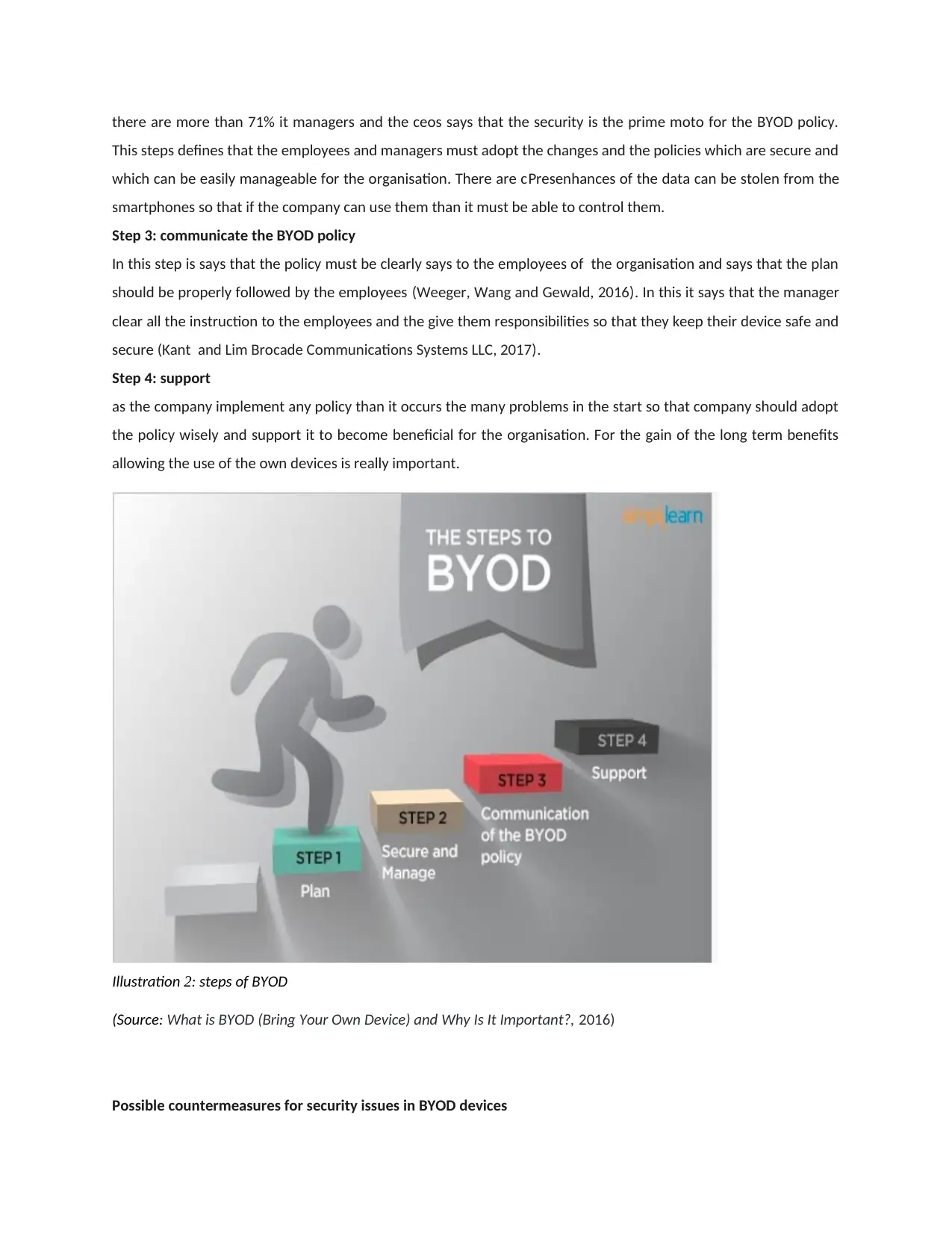
there are more than 71% it managers and the ceos says that the security is the prime moto for the BYOD policy.
This steps defines that the employees and managers must adopt the changes and the policies which are secure and
which can be easily manageable for the organisation. There are cPresenhances of the data can be stolen from the
smartphones so that if the company can use them than it must be able to control them.
Step 3: communicate the BYOD policy
In this step is says that the policy must be clearly says to the employees of the organisation and says that the plan
should be properly followed by the employees (Weeger, Wang and Gewald, 2016). In this it says that the manager
clear all the instruction to the employees and the give them responsibilities so that they keep their device safe and
secure (Kant and Lim Brocade Communications Systems LLC, 2017).
Step 4: support
as the company implement any policy than it occurs the many problems in the start so that company should adopt
the policy wisely and support it to become beneficial for the organisation. For the gain of the long term benefits
allowing the use of the own devices is really important.
Illustration 2: steps of BYOD
(Source: What is BYOD (Bring Your Own Device) and Why Is It Important?, 2016)
Possible countermeasures for security issues in BYOD devices
This steps defines that the employees and managers must adopt the changes and the policies which are secure and
which can be easily manageable for the organisation. There are cPresenhances of the data can be stolen from the
smartphones so that if the company can use them than it must be able to control them.
Step 3: communicate the BYOD policy
In this step is says that the policy must be clearly says to the employees of the organisation and says that the plan
should be properly followed by the employees (Weeger, Wang and Gewald, 2016). In this it says that the manager
clear all the instruction to the employees and the give them responsibilities so that they keep their device safe and
secure (Kant and Lim Brocade Communications Systems LLC, 2017).
Step 4: support
as the company implement any policy than it occurs the many problems in the start so that company should adopt
the policy wisely and support it to become beneficial for the organisation. For the gain of the long term benefits
allowing the use of the own devices is really important.
Illustration 2: steps of BYOD
(Source: What is BYOD (Bring Your Own Device) and Why Is It Important?, 2016)
Possible countermeasures for security issues in BYOD devices
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

To prevent the issues and possible countermeasure are available for the organisation to use and prevent the
problems happen with the problems. If any organisation is use the concept of the BYOD have a clear policy of the
BYOD which must be followed to prevent the issues with the security from the using BYOD concept. Policies of the
BYOD.
BYOD policy should have to clear to every one and the it can be used the operating software which can be easily
controllable by the firm (Hong and et.al., 2016).
The policy should be clear while using the personal devices to the employees and it must have the clear instruction
regarding to the loss of data and misuse of the data.
The firm have the policy of the save the important document in the strong password protection so that it can not
be harmed (Dang-Pham and Pittayachawan, 2015).
There should clear about the cost of the devices and terms and conditions of the company.
For the countermeasure of the security issues of the BYOD it can be use the following tips- BYOD in a useful
technique for the organisation because it helps to increase the productivity of the employees
Specify the devices that will be permitted
the use of the which devices is clear in the organisation. Like the old days where the employees can use the
blackberry phones nothing other than that. This is the best policy to control the all the devicesPresen for the
organisation (Kant and Lim Brocade Communications Systems LLC, 2017). It is for the IT department to easily
evaluate the phones and it controls the misuse of the devices in the organisation. Also clears the who can use the
phones.
All devices should be strictly checked before permitted in the organisation
all the devices use in the premises must be strictly checked. Generally the user who owns the phone refuse the
open the locks of the but the management make the rule for the checking of the device when the employee enters
and when employees leave the premises. This will helps to secure the data and the policy to make efficient use
(Dang-Pham and Pittayachawan, 2015).
Clear service policy should be adopted
clearly defines that the for what purpose the device is allowed in the organisation or the its should be clears that
what are the services should be provided in by the devices in the organisation. It will help to determine the use of
the devices and the resolving the problems of the employee. This also defines the use by the employees and
restrict the extra usage.
Clearly communicate the apps and the data allowed to BYOD in a useful technique for the organisation because
it helps to increase the productivity of the employees use in the organisation
management should clearly communicate the uses of the device and the data which can be allow to keep in the
organisation while device is using for the organisation. This will help to the misuse of the data for the organisation
and help thBYOD in a useful technique for the organisation because it helps to increase the productivity of the
employees e prevent the mistake of the employees in the organisation.
problems happen with the problems. If any organisation is use the concept of the BYOD have a clear policy of the
BYOD which must be followed to prevent the issues with the security from the using BYOD concept. Policies of the
BYOD.
BYOD policy should have to clear to every one and the it can be used the operating software which can be easily
controllable by the firm (Hong and et.al., 2016).
The policy should be clear while using the personal devices to the employees and it must have the clear instruction
regarding to the loss of data and misuse of the data.
The firm have the policy of the save the important document in the strong password protection so that it can not
be harmed (Dang-Pham and Pittayachawan, 2015).
There should clear about the cost of the devices and terms and conditions of the company.
For the countermeasure of the security issues of the BYOD it can be use the following tips- BYOD in a useful
technique for the organisation because it helps to increase the productivity of the employees
Specify the devices that will be permitted
the use of the which devices is clear in the organisation. Like the old days where the employees can use the
blackberry phones nothing other than that. This is the best policy to control the all the devicesPresen for the
organisation (Kant and Lim Brocade Communications Systems LLC, 2017). It is for the IT department to easily
evaluate the phones and it controls the misuse of the devices in the organisation. Also clears the who can use the
phones.
All devices should be strictly checked before permitted in the organisation
all the devices use in the premises must be strictly checked. Generally the user who owns the phone refuse the
open the locks of the but the management make the rule for the checking of the device when the employee enters
and when employees leave the premises. This will helps to secure the data and the policy to make efficient use
(Dang-Pham and Pittayachawan, 2015).
Clear service policy should be adopted
clearly defines that the for what purpose the device is allowed in the organisation or the its should be clears that
what are the services should be provided in by the devices in the organisation. It will help to determine the use of
the devices and the resolving the problems of the employee. This also defines the use by the employees and
restrict the extra usage.
Clearly communicate the apps and the data allowed to BYOD in a useful technique for the organisation because
it helps to increase the productivity of the employees use in the organisation
management should clearly communicate the uses of the device and the data which can be allow to keep in the
organisation while device is using for the organisation. This will help to the misuse of the data for the organisation
and help thBYOD in a useful technique for the organisation because it helps to increase the productivity of the
employees e prevent the mistake of the employees in the organisation.
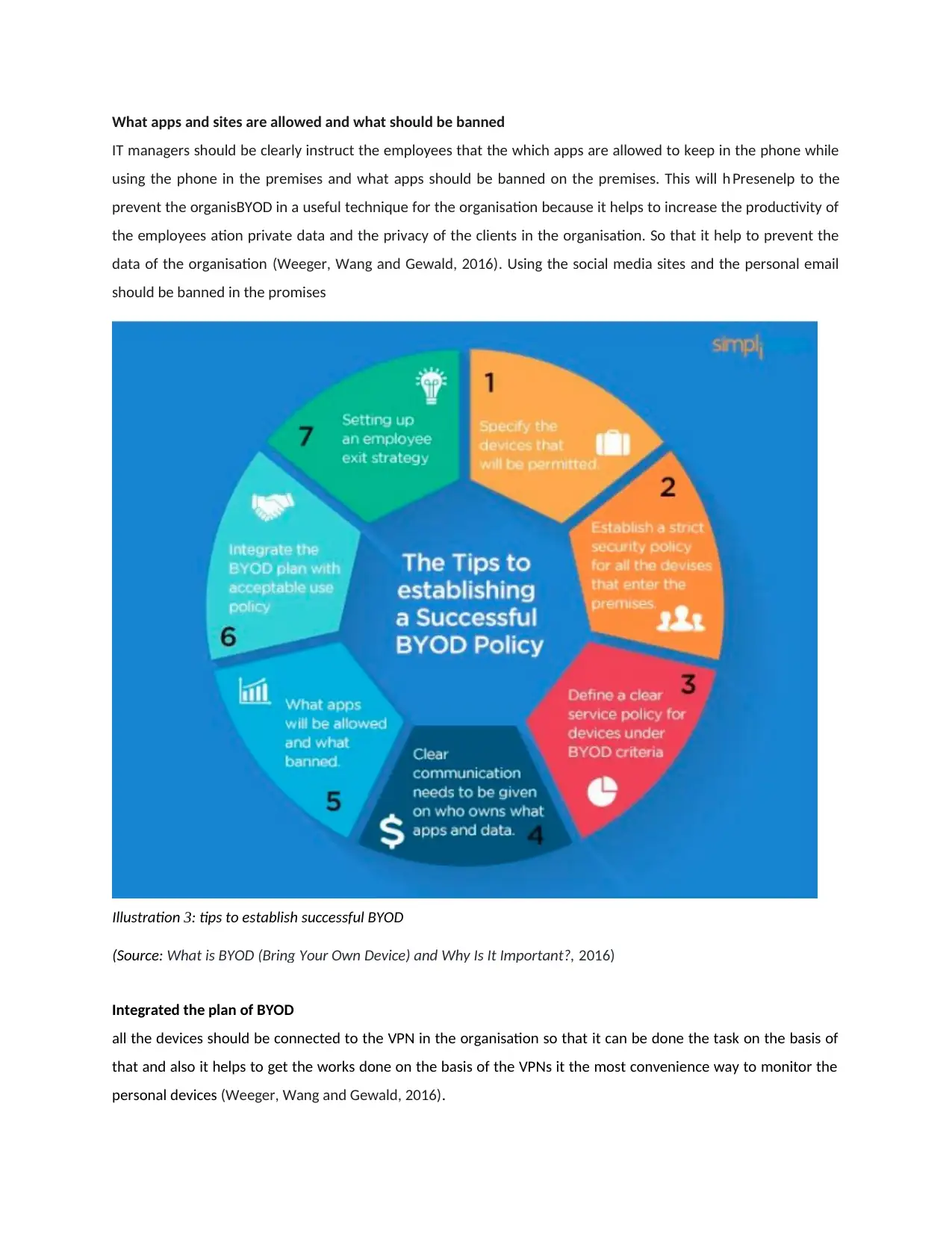
What apps and sites are allowed and what should be banned
IT managers should be clearly instruct the employees that the which apps are allowed to keep in the phone while
using the phone in the premises and what apps should be banned on the premises. This will h Presenelp to the
prevent the organisBYOD in a useful technique for the organisation because it helps to increase the productivity of
the employees ation private data and the privacy of the clients in the organisation. So that it help to prevent the
data of the organisation (Weeger, Wang and Gewald, 2016). Using the social media sites and the personal email
should be banned in the promises
Illustration 3: tips to establish successful BYOD
(Source: What is BYOD (Bring Your Own Device) and Why Is It Important?, 2016)
Integrated the plan of BYOD
all the devices should be connected to the VPN in the organisation so that it can be done the task on the basis of
that and also it helps to get the works done on the basis of the VPNs it the most convenience way to monitor the
personal devices (Weeger, Wang and Gewald, 2016).
IT managers should be clearly instruct the employees that the which apps are allowed to keep in the phone while
using the phone in the premises and what apps should be banned on the premises. This will h Presenelp to the
prevent the organisBYOD in a useful technique for the organisation because it helps to increase the productivity of
the employees ation private data and the privacy of the clients in the organisation. So that it help to prevent the
data of the organisation (Weeger, Wang and Gewald, 2016). Using the social media sites and the personal email
should be banned in the promises
Illustration 3: tips to establish successful BYOD
(Source: What is BYOD (Bring Your Own Device) and Why Is It Important?, 2016)
Integrated the plan of BYOD
all the devices should be connected to the VPN in the organisation so that it can be done the task on the basis of
that and also it helps to get the works done on the basis of the VPNs it the most convenience way to monitor the
personal devices (Weeger, Wang and Gewald, 2016).
You're viewing a preview
Unlock full access by subscribing today!

Setting up the employee exit policy
lastly check the what happened when the employee leave the organisation it must be check the devices properly
and the plan should be done on the basis of that. It must be ensure that the all the data of the organisation must
be removed from the devices and that should be clear. This will help to prevent the data base of the organisation
and secure the all the problem of the devices and the privacy of client data (Kant and Lim Brocade
Communications Systems LLC, 2017).
All the above policies should be prevent the the data from the stolen. And it also effective the use of the bring your
own device (BYOD) in the company also it will help to the get the utilisation of the all the problems. If any company
wants to successful implementation of the BYOD concept than it should strictly follow the above tips and
techniques so that it can be successfully implied and the problems can be minimise (Bratthall Tideman and
Lindström, 2018).
Other similar techniques of BYOD
Bring your own technology is very essential technology or can be defined as secured technique which is used by
research business now a days. In this employees use their own devices such as smartphones, computer to work in
the organization. Company does not provide any kind of device to workers to work (Weeger, Wang and Gewald,
2016). As people are more comfortable in working on their own devices hence if they use their own technologies
then it may help companies to raises productivity of users.
The main reason of using this technique is to raise moral of employees and enhance their production
ability. But if workers use their own devices then there is high chances of data leakage which may create security
issue for companies to great extent. Most of the companies take support of different software but it is very difficult
for staff members to understand such software hence it may create problem for companies to give them training
and make them understand towards this machine or device (Kant and Lim Brocade Communications Systems LLC,
2017).
Research justification
The implication and continuous increase in the BYOD devices by employees ta wo9rkplace has
encouraged researcher to conduct investigation on the particular topic. In addition to this, the other reason for
facilitating investigation on specific topic is that investigator want to identify the reason because of which
companies is allowing their employees to bring their own devices at workplace. Other rationale for performing the
research on particular topic is that researcher intend to develop the understanding about the potential threat
which are associated with permitting workers to bring BYOD devices.
Proposed design
lastly check the what happened when the employee leave the organisation it must be check the devices properly
and the plan should be done on the basis of that. It must be ensure that the all the data of the organisation must
be removed from the devices and that should be clear. This will help to prevent the data base of the organisation
and secure the all the problem of the devices and the privacy of client data (Kant and Lim Brocade
Communications Systems LLC, 2017).
All the above policies should be prevent the the data from the stolen. And it also effective the use of the bring your
own device (BYOD) in the company also it will help to the get the utilisation of the all the problems. If any company
wants to successful implementation of the BYOD concept than it should strictly follow the above tips and
techniques so that it can be successfully implied and the problems can be minimise (Bratthall Tideman and
Lindström, 2018).
Other similar techniques of BYOD
Bring your own technology is very essential technology or can be defined as secured technique which is used by
research business now a days. In this employees use their own devices such as smartphones, computer to work in
the organization. Company does not provide any kind of device to workers to work (Weeger, Wang and Gewald,
2016). As people are more comfortable in working on their own devices hence if they use their own technologies
then it may help companies to raises productivity of users.
The main reason of using this technique is to raise moral of employees and enhance their production
ability. But if workers use their own devices then there is high chances of data leakage which may create security
issue for companies to great extent. Most of the companies take support of different software but it is very difficult
for staff members to understand such software hence it may create problem for companies to give them training
and make them understand towards this machine or device (Kant and Lim Brocade Communications Systems LLC,
2017).
Research justification
The implication and continuous increase in the BYOD devices by employees ta wo9rkplace has
encouraged researcher to conduct investigation on the particular topic. In addition to this, the other reason for
facilitating investigation on specific topic is that investigator want to identify the reason because of which
companies is allowing their employees to bring their own devices at workplace. Other rationale for performing the
research on particular topic is that researcher intend to develop the understanding about the potential threat
which are associated with permitting workers to bring BYOD devices.
Proposed design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The research design is basically a structure of various techniques which are utilised by researcher for
performing the investigation. There are different types of research design these are descriptive, explanatory,
experimental, exploratory. The proposed research design for present investigation is explanatory. Such research
design has been suggested as it will provide investigator an ease in explaining the phenomenon. However , other
researcher has critique the selected research design by stating that in context of explanatory research design
there are high chances of biases in interpretation the data which might further have adverse effect on research
outcome. Other research design which has been proposed is descriptive, the main advantages of using the
descriptive research design is that by utilising the specific design investigator will able to observe the phenomenon
in a completely natural and unchanged natural environment.
CONCLUSION
From the above study it can be concluded that the BYOD in a useful technique for the organisation because it helps
to increase the productivity of the employees by using their own devices and it also decrease the cost of the
company of installing the new devices and the technology. It has concluded the advantages of the bring your own
device which says that the it is helpful in the reducing the cost and the also helps for the betterment of the
companies efficiency . It has concluded the steps of the BYOD implementation in which the company should plan
the all the activities that should be conducted in the premises with the help of the devices. It has also concludes
the company will implement the policy with some guideline and the effectiveness.
performing the investigation. There are different types of research design these are descriptive, explanatory,
experimental, exploratory. The proposed research design for present investigation is explanatory. Such research
design has been suggested as it will provide investigator an ease in explaining the phenomenon. However , other
researcher has critique the selected research design by stating that in context of explanatory research design
there are high chances of biases in interpretation the data which might further have adverse effect on research
outcome. Other research design which has been proposed is descriptive, the main advantages of using the
descriptive research design is that by utilising the specific design investigator will able to observe the phenomenon
in a completely natural and unchanged natural environment.
CONCLUSION
From the above study it can be concluded that the BYOD in a useful technique for the organisation because it helps
to increase the productivity of the employees by using their own devices and it also decrease the cost of the
company of installing the new devices and the technology. It has concluded the advantages of the bring your own
device which says that the it is helpful in the reducing the cost and the also helps for the betterment of the
companies efficiency . It has concluded the steps of the BYOD implementation in which the company should plan
the all the activities that should be conducted in the premises with the help of the devices. It has also concludes
the company will implement the policy with some guideline and the effectiveness.

REFERENCES
Books and Journals
Bratthall Tideman, J. and Lindström, J., 2018. Key components when utilising BYOD within organisations-A framework for
developing the BYOD policy.
Cheng, G., Guan, Y. and Chau, J., 2016. An empirical study towards understanding user acceptance of bring your own device
(BYOD) in higher education. Australasian Journal of Educational Technology. 32(4).
Chou, P.N., Chang, C.C. and Lin, C.H., 2017. BYOD or not: A comparison of two assessment strategies for student learning.
Computers in Human Behavior, 74, pp.63-71.
Dang-Pham, D. and Pittayachawan, S., 2015. Comparing intention to avoid malware across contexts in a BYOD-enabled
Australian university: A Protection Motivation Theory approach. Computers & Security, 48, pp.281-297.
Garba, A.B., and et.al., 2015. Review of the information security and privacy challenges in Bring Your Own Device (BYOD)
environments. Journal of Information privacy and security, 11(1), pp.38-54.
Gray, C. and Malins, J., 2016. Visualizing research: A guide to the research process in art and design. Routledge.
Hong, S. and et.al., 2016, February. Towards SDN-Defined Programmable BYOD (Bring Your Own Device) Security. In NDSS.
Kant, N. and Lim, H., Brocade Communications Systems LLC, 2017. Method and system for selective and secure interaction of
BYOD (bring your own device) with enterprise network through mobile wireless networks. U.S. Patent 9,716,996.
Keyes, J., 2016. Bring your own devices (BYOD) survival guide. Auerbach Publications.
Kortz, K.M. and van der Hoeven Kraft, K.J., 2016. Geoscience education research project: Student benefits and effective design
of a course-based undergraduate research experience. Journal of Geoscience Education. 64(1), pp.24-36.
Song, Y. and Kong, S.C., 2017. Affordances and constraints of BYOD (Bring Your Own Device) for learning and teaching in higher
education: Teachers’ perspectives. The Internet and Higher Education. 32(1), pp.39-46.
Weeger, A., Wang, X. and Gewald, H., 2016. IT consumerization: BYOD-program acceptance and its impact on employer
attractiveness. Journal of Computer Information Systems, 56(1), pp.1-10.
Online
What is BYOD (Bring Your Own Device) and Why Is It Important?. 2016. [online]. Available through
<https://www.simplilearn.com/what-is-byod-and-why-it-is-important-article>
Books and Journals
Bratthall Tideman, J. and Lindström, J., 2018. Key components when utilising BYOD within organisations-A framework for
developing the BYOD policy.
Cheng, G., Guan, Y. and Chau, J., 2016. An empirical study towards understanding user acceptance of bring your own device
(BYOD) in higher education. Australasian Journal of Educational Technology. 32(4).
Chou, P.N., Chang, C.C. and Lin, C.H., 2017. BYOD or not: A comparison of two assessment strategies for student learning.
Computers in Human Behavior, 74, pp.63-71.
Dang-Pham, D. and Pittayachawan, S., 2015. Comparing intention to avoid malware across contexts in a BYOD-enabled
Australian university: A Protection Motivation Theory approach. Computers & Security, 48, pp.281-297.
Garba, A.B., and et.al., 2015. Review of the information security and privacy challenges in Bring Your Own Device (BYOD)
environments. Journal of Information privacy and security, 11(1), pp.38-54.
Gray, C. and Malins, J., 2016. Visualizing research: A guide to the research process in art and design. Routledge.
Hong, S. and et.al., 2016, February. Towards SDN-Defined Programmable BYOD (Bring Your Own Device) Security. In NDSS.
Kant, N. and Lim, H., Brocade Communications Systems LLC, 2017. Method and system for selective and secure interaction of
BYOD (bring your own device) with enterprise network through mobile wireless networks. U.S. Patent 9,716,996.
Keyes, J., 2016. Bring your own devices (BYOD) survival guide. Auerbach Publications.
Kortz, K.M. and van der Hoeven Kraft, K.J., 2016. Geoscience education research project: Student benefits and effective design
of a course-based undergraduate research experience. Journal of Geoscience Education. 64(1), pp.24-36.
Song, Y. and Kong, S.C., 2017. Affordances and constraints of BYOD (Bring Your Own Device) for learning and teaching in higher
education: Teachers’ perspectives. The Internet and Higher Education. 32(1), pp.39-46.
Weeger, A., Wang, X. and Gewald, H., 2016. IT consumerization: BYOD-program acceptance and its impact on employer
attractiveness. Journal of Computer Information Systems, 56(1), pp.1-10.
Online
What is BYOD (Bring Your Own Device) and Why Is It Important?. 2016. [online]. Available through
<https://www.simplilearn.com/what-is-byod-and-why-it-is-important-article>
You're viewing a preview
Unlock full access by subscribing today!
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





