Analysis of Network Types and Standards: Benefits and Constraints
VerifiedAdded on 2021/08/16
|22
|5141
|7484
Report
AI Summary
This report provides a detailed analysis of various network types, including Local Area Networks (LAN), Wide Area Networks (WAN), Metropolitan Area Networks (MAN), and Global Area Networks (GAN), discussing their respective benefits and constraints. It further explores different network standards such as ITU, IEEE, ISO, IETF, and ISOC, outlining their roles and key features. The report also examines the impact of network topology, covering bus, star, ring, mesh, tree, and hybrid topologies, along with their advantages and disadvantages. Additionally, it delves into communication methods, specifically unicast, and their implications on network performance and efficiency. The document also discusses the effect of network topology, communication, and bandwidth requirements. This comprehensive overview aims to provide a thorough understanding of network technologies and their practical applications.
Benefits and constraints of different network types and standards.
I. Discuss the benefits and constraints of different network types:
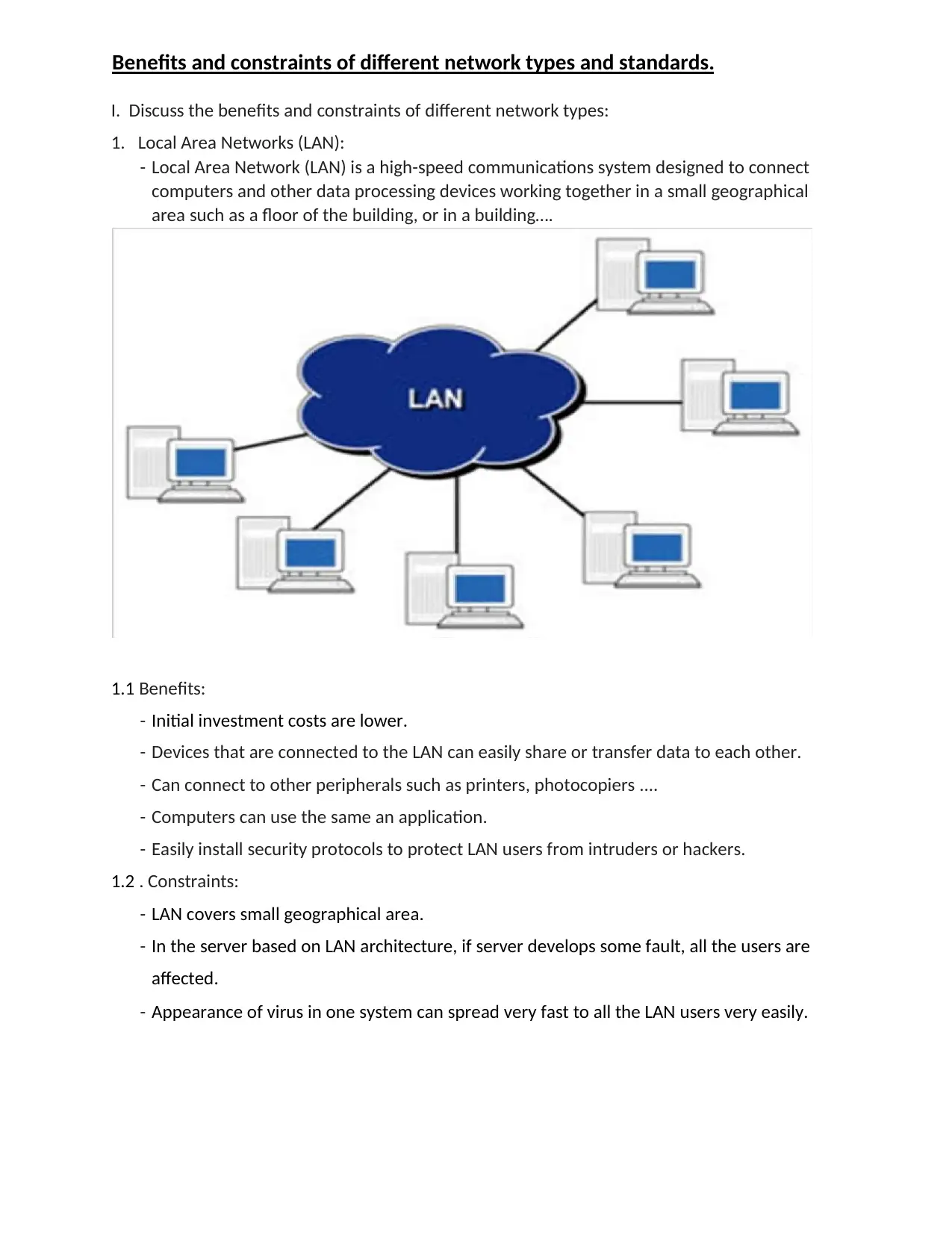
1. Local Area Networks (LAN):
- Local Area Network (LAN) is a high-speed communications system designed to connect
computers and other data processing devices working together in a small geographical
area such as a floor of the building, or in a building….
1.1 Benefits:
- Initial investment costs are lower.
- Devices that are connected to the LAN can easily share or transfer data to each other.
- Can connect to other peripherals such as printers, photocopiers ....
- Computers can use the same an application.
- Easily install security protocols to protect LAN users from intruders or hackers.
1.2 . Constraints:
- LAN covers small geographical area.
- In the server based on LAN architecture, if server develops some fault, all the users are
affected.
- Appearance of virus in one system can spread very fast to all the LAN users very easily.
I. Discuss the benefits and constraints of different network types:
1. Local Area Networks (LAN):
- Local Area Network (LAN) is a high-speed communications system designed to connect
computers and other data processing devices working together in a small geographical
area such as a floor of the building, or in a building….
1.1 Benefits:
- Initial investment costs are lower.
- Devices that are connected to the LAN can easily share or transfer data to each other.
- Can connect to other peripherals such as printers, photocopiers ....
- Computers can use the same an application.
- Easily install security protocols to protect LAN users from intruders or hackers.
1.2 . Constraints:
- LAN covers small geographical area.
- In the server based on LAN architecture, if server develops some fault, all the users are
affected.
- Appearance of virus in one system can spread very fast to all the LAN users very easily.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2. Wide Area Network (WAN):
- The WAN is a network which is a collection of LANs and other network types connected using
router. It covers large geographical distance compare to LAN and MAN types.
2.1. Benefits:
- WAN covers larger geographical area. Hence business offices situated at longer distances can
easily communicate.
- Like LAN, it alloows sharing of resources and application software among distributed
workstations or users.
-Organizations can form their global integrated network through WAN. Moreover, it supports
global markets and global businesses.
2.2 Constraints:
- Initial investment costs are higher.
- It has lower security compare to LAN and MAN due to wider coverage and use of more
technologies.
- Security is big concern and requires use of firewall and security software/protocols at multiple
points across the entire system.
- There are more errors and issues due to wide coverage and use of different technologies.
- It is difficult to maintain the network.
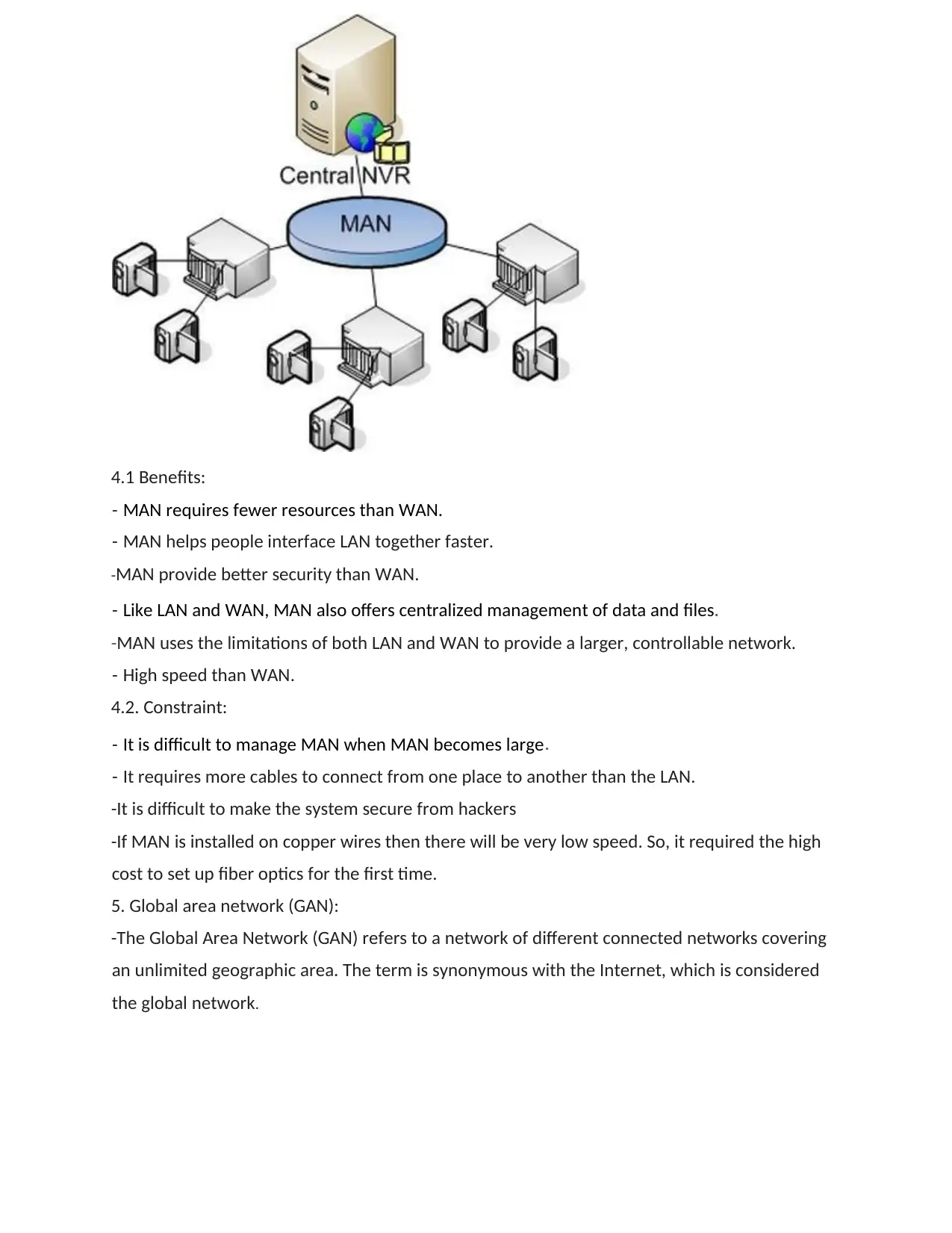
4. Metropolitan area network (MAN):
-A metropolitan area network (MAN) is a computer network that interconnects users with
computer resources in a geographic area or region larger than that covered by even a large
local area network (LAN) but smaller than the area covered by a wide area network (WAN).
- The WAN is a network which is a collection of LANs and other network types connected using
router. It covers large geographical distance compare to LAN and MAN types.
2.1. Benefits:
- WAN covers larger geographical area. Hence business offices situated at longer distances can
easily communicate.
- Like LAN, it alloows sharing of resources and application software among distributed
workstations or users.
-Organizations can form their global integrated network through WAN. Moreover, it supports
global markets and global businesses.
2.2 Constraints:
- Initial investment costs are higher.
- It has lower security compare to LAN and MAN due to wider coverage and use of more
technologies.
- Security is big concern and requires use of firewall and security software/protocols at multiple
points across the entire system.
- There are more errors and issues due to wide coverage and use of different technologies.
- It is difficult to maintain the network.
4. Metropolitan area network (MAN):
-A metropolitan area network (MAN) is a computer network that interconnects users with
computer resources in a geographic area or region larger than that covered by even a large
local area network (LAN) but smaller than the area covered by a wide area network (WAN).
4.1 Benefits:
- MAN requires fewer resources than WAN.
- MAN helps people interface LAN together faster.
-MAN provide better security than WAN.
- Like LAN and WAN, MAN also offers centralized management of data and files.
-MAN uses the limitations of both LAN and WAN to provide a larger, controllable network.
- High speed than WAN.
4.2. Constraint:
- It is difficult to manage MAN when MAN becomes large.
- It requires more cables to connect from one place to another than the LAN.
-It is difficult to make the system secure from hackers
-If MAN is installed on copper wires then there will be very low speed. So, it required the high
cost to set up fiber optics for the first time.
5. Global area network (GAN):
-The Global Area Network (GAN) refers to a network of different connected networks covering
an unlimited geographic area. The term is synonymous with the Internet, which is considered
the global network.
- MAN requires fewer resources than WAN.
- MAN helps people interface LAN together faster.
-MAN provide better security than WAN.
- Like LAN and WAN, MAN also offers centralized management of data and files.
-MAN uses the limitations of both LAN and WAN to provide a larger, controllable network.
- High speed than WAN.
4.2. Constraint:
- It is difficult to manage MAN when MAN becomes large.
- It requires more cables to connect from one place to another than the LAN.
-It is difficult to make the system secure from hackers
-If MAN is installed on copper wires then there will be very low speed. So, it required the high
cost to set up fiber optics for the first time.
5. Global area network (GAN):
-The Global Area Network (GAN) refers to a network of different connected networks covering
an unlimited geographic area. The term is synonymous with the Internet, which is considered
the global network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5.1 Benefits:
-Connect branches for data transmission purposes.
-Low cost, stable speed.
-Meet the requirements of information security.
-Simple to manage and easy to switch.
5.2 Constraint:
- It is easy for hackers to steal information and reveal
information. When centralized control is shared, the user can access
the data
- Network maintenance is difficult and costly - Lost information
or stolen.
II. Discuss the benefits and constraints of different network standard:
1. Definition:
- Network standards are a set of rules that ensure the interoperability of network technologies
by defining the rules of communication between networked devices. Network standards exist
to help ensure that the products of different vendors can work together in a network without
the risk of incompatibility.
2.Some common Network Standards:
2.1. ITU (International Telecommunication Union):
- The ITU is a specialized United Nations agency that regulates international
telecommunications, including radio and TV frequencies, satellite and telephony
specifications, networking infrastructure, and tariffs applied to global communications. It also
provides developing countries with technical expertise and equipment to advance those
nations’ technological bases.
-Connect branches for data transmission purposes.
-Low cost, stable speed.
-Meet the requirements of information security.
-Simple to manage and easy to switch.
5.2 Constraint:
- It is easy for hackers to steal information and reveal
information. When centralized control is shared, the user can access
the data
- Network maintenance is difficult and costly - Lost information
or stolen.
II. Discuss the benefits and constraints of different network standard:
1. Definition:
- Network standards are a set of rules that ensure the interoperability of network technologies
by defining the rules of communication between networked devices. Network standards exist
to help ensure that the products of different vendors can work together in a network without
the risk of incompatibility.
2.Some common Network Standards:
2.1. ITU (International Telecommunication Union):
- The ITU is a specialized United Nations agency that regulates international
telecommunications, including radio and TV frequencies, satellite and telephony
specifications, networking infrastructure, and tariffs applied to global communications. It also
provides developing countries with technical expertise and equipment to advance those
nations’ technological bases.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

- The main activities of the ITU cover all aspects of the field telecommunications sector. ITU
hasthree main areas of activity:
+ITU-R (Radiocommunication Sector): play an important role in the global management of
radio frequency resources and satellite orbits, construction Establish international standards for
radio communication systems.
+ ITU-T (Telecommunication Standardization Sector): a collection of experts from all over the
world to build international standards known by name. The ITU-T Recommendation, which
determines the global infrastructure of the public information and communication technology.
+ ITU-D (Development Sector): efforts to replicate telecom access Fair and reasonable as a way
to stimulate socio-economic development Wider.
- The purpose of ITU-T is to build, publish, disseminate and monitor the application.
Recommendation for standardization of telecommunications activities on a global level,
through research technical issues, manipulation and tariffs on international media. Currently
active ITU-T standardization is conducted by:
- Media Advisory Group (TSAG);
- Research Groups (SG);
- Co-ordinating Coordination Groups (with Radio Communications Unit).
2.2 IEEE (Institute of Electrical and Electronics Engineers):
-The IEEE (Institute of Electrical and Electronics Engineers), or “I-triple-E,” is an international
society composed of engineering professionals. Its goals are to promote development and
education in the electrical engineering and computer science fields. To this end, IEEE hosts
numerous symposia, conferences, and local chapter meetings and publishes papers designed to
educate members on technological advances. It also maintains a standards board that
establishes its own standards for the electronics and computer industries and contributes to
the work of other standards-setting bodies.
* Some of the best-known IEEE standards are as follows:
- IEEE 802.1 (LAN/MAN):
The IEEE 802.1 group defined internetworking standards, with IEEE 802.1d and IEEE 802.1q
used in the local-area networking environment.
- IEEE 802.3 (Ethernet):
+ Several Ethernet standards are used in today's network environment. Some of these
standards dictate the bandwidth and operation of the Ethernet LAN, such as Ethernet and Fast
Ethernet, whereas other standards dictate how these Ethernet networks function, such as the
STP.
+ The IEEE 802.3 standards define how the Ethernet standard is used in the networking
environment. Some IEEE 802.3:
hasthree main areas of activity:
+ITU-R (Radiocommunication Sector): play an important role in the global management of
radio frequency resources and satellite orbits, construction Establish international standards for
radio communication systems.
+ ITU-T (Telecommunication Standardization Sector): a collection of experts from all over the
world to build international standards known by name. The ITU-T Recommendation, which
determines the global infrastructure of the public information and communication technology.
+ ITU-D (Development Sector): efforts to replicate telecom access Fair and reasonable as a way
to stimulate socio-economic development Wider.
- The purpose of ITU-T is to build, publish, disseminate and monitor the application.
Recommendation for standardization of telecommunications activities on a global level,
through research technical issues, manipulation and tariffs on international media. Currently
active ITU-T standardization is conducted by:
- Media Advisory Group (TSAG);
- Research Groups (SG);
- Co-ordinating Coordination Groups (with Radio Communications Unit).
2.2 IEEE (Institute of Electrical and Electronics Engineers):
-The IEEE (Institute of Electrical and Electronics Engineers), or “I-triple-E,” is an international
society composed of engineering professionals. Its goals are to promote development and
education in the electrical engineering and computer science fields. To this end, IEEE hosts
numerous symposia, conferences, and local chapter meetings and publishes papers designed to
educate members on technological advances. It also maintains a standards board that
establishes its own standards for the electronics and computer industries and contributes to
the work of other standards-setting bodies.
* Some of the best-known IEEE standards are as follows:
- IEEE 802.1 (LAN/MAN):
The IEEE 802.1 group defined internetworking standards, with IEEE 802.1d and IEEE 802.1q
used in the local-area networking environment.
- IEEE 802.3 (Ethernet):
+ Several Ethernet standards are used in today's network environment. Some of these
standards dictate the bandwidth and operation of the Ethernet LAN, such as Ethernet and Fast
Ethernet, whereas other standards dictate how these Ethernet networks function, such as the
STP.
+ The IEEE 802.3 standards define how the Ethernet standard is used in the networking
environment. Some IEEE 802.3:

- IEEE 802.3 (Ethernet): 10-Mbps Ethernet specification developed by Xerox, often used in
LANs.
- IEEE 802.3u (Fast Ethernet) 100-Mbps Ethernet specification working at 10 times the speed
of 10-Mbps Ethernet, often used in LANs.
- IEEE 802.3z (Gigabit Ethernet) 1000-Mbps/1-Gbps Ethernet specification that transfers data
at 1 gigabit per second (1000 Mbps). Often used in large LANs (at the core layer).
- IEEE 802.3ae (10Gigabit Ethernet) 10,000-Mbps/10-Gbps Ethernet specification that
transfers data at 10 gigabits per second (10,000 Mbps). Often used in MANs.
- IEEE 802.5 (Token Ring): IEEE 802.5 is a specification that is relevant and compatible with
the Token Ring standard developed by IBM. Token Ring refers to both the IBM Token Ring
and IEEE 802.5 network deployments.
IEEE 802.11 (Wireless LAN): The IEEE 802.11 standard refers to a family of specifications
developed for wireless LAN technology. IEEE 802.11 specifies a wireless interface between a
wireless client and a base station, such as a wireless laptop and a wireless base unit or between
two wireless clients, such as between two wireless laptops.
2.3. ISO (International Organization for Standardization): -
ISO is the global alliance of national standards bodies.
- The goal of ISO is to promote the development of standardization and related activities
around the world in order to facilitate the international exchange of goods and services and
to develop cooperation in the field of mental activity. intellectual, scientific, technological
and economic.
2.4. IETF (Internet Engineering Task Force):
- IETF is the organization that sets standards for how systems communicate over the
Internet—inparticular, how protocols operate and interact.
- The purpose of the IETF is to develop and promote Internet standards, working closely with
standard organizations of the World Wide Web Consortium (W3C) and ISO / IEC
(International Electrotechnical Commission); and specifically address the TCP / IP standards
and Internet protocol suite. This is a voluntary open standards organization that does not
require formal or informal membership. 2.5. ISOC (Internet Society):
- ISOC is a professional membership society that helps set the technical standards for the
Internet.
-The purpose of ISOC is to guarantee, promote the development, expansion and use of the
Internet is most convenient for people around the world.
P2. Explain the impact of network topology, communication and bandwidth
requirements.
I. Explain the impact of network topology:
1. BUS TOPOLOGY:
LANs.
- IEEE 802.3u (Fast Ethernet) 100-Mbps Ethernet specification working at 10 times the speed
of 10-Mbps Ethernet, often used in LANs.
- IEEE 802.3z (Gigabit Ethernet) 1000-Mbps/1-Gbps Ethernet specification that transfers data
at 1 gigabit per second (1000 Mbps). Often used in large LANs (at the core layer).
- IEEE 802.3ae (10Gigabit Ethernet) 10,000-Mbps/10-Gbps Ethernet specification that
transfers data at 10 gigabits per second (10,000 Mbps). Often used in MANs.
- IEEE 802.5 (Token Ring): IEEE 802.5 is a specification that is relevant and compatible with
the Token Ring standard developed by IBM. Token Ring refers to both the IBM Token Ring
and IEEE 802.5 network deployments.
IEEE 802.11 (Wireless LAN): The IEEE 802.11 standard refers to a family of specifications
developed for wireless LAN technology. IEEE 802.11 specifies a wireless interface between a
wireless client and a base station, such as a wireless laptop and a wireless base unit or between
two wireless clients, such as between two wireless laptops.
2.3. ISO (International Organization for Standardization): -
ISO is the global alliance of national standards bodies.
- The goal of ISO is to promote the development of standardization and related activities
around the world in order to facilitate the international exchange of goods and services and
to develop cooperation in the field of mental activity. intellectual, scientific, technological
and economic.
2.4. IETF (Internet Engineering Task Force):
- IETF is the organization that sets standards for how systems communicate over the
Internet—inparticular, how protocols operate and interact.
- The purpose of the IETF is to develop and promote Internet standards, working closely with
standard organizations of the World Wide Web Consortium (W3C) and ISO / IEC
(International Electrotechnical Commission); and specifically address the TCP / IP standards
and Internet protocol suite. This is a voluntary open standards organization that does not
require formal or informal membership. 2.5. ISOC (Internet Society):
- ISOC is a professional membership society that helps set the technical standards for the
Internet.
-The purpose of ISOC is to guarantee, promote the development, expansion and use of the
Internet is most convenient for people around the world.
P2. Explain the impact of network topology, communication and bandwidth
requirements.
I. Explain the impact of network topology:
1. BUS TOPOLOGY:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
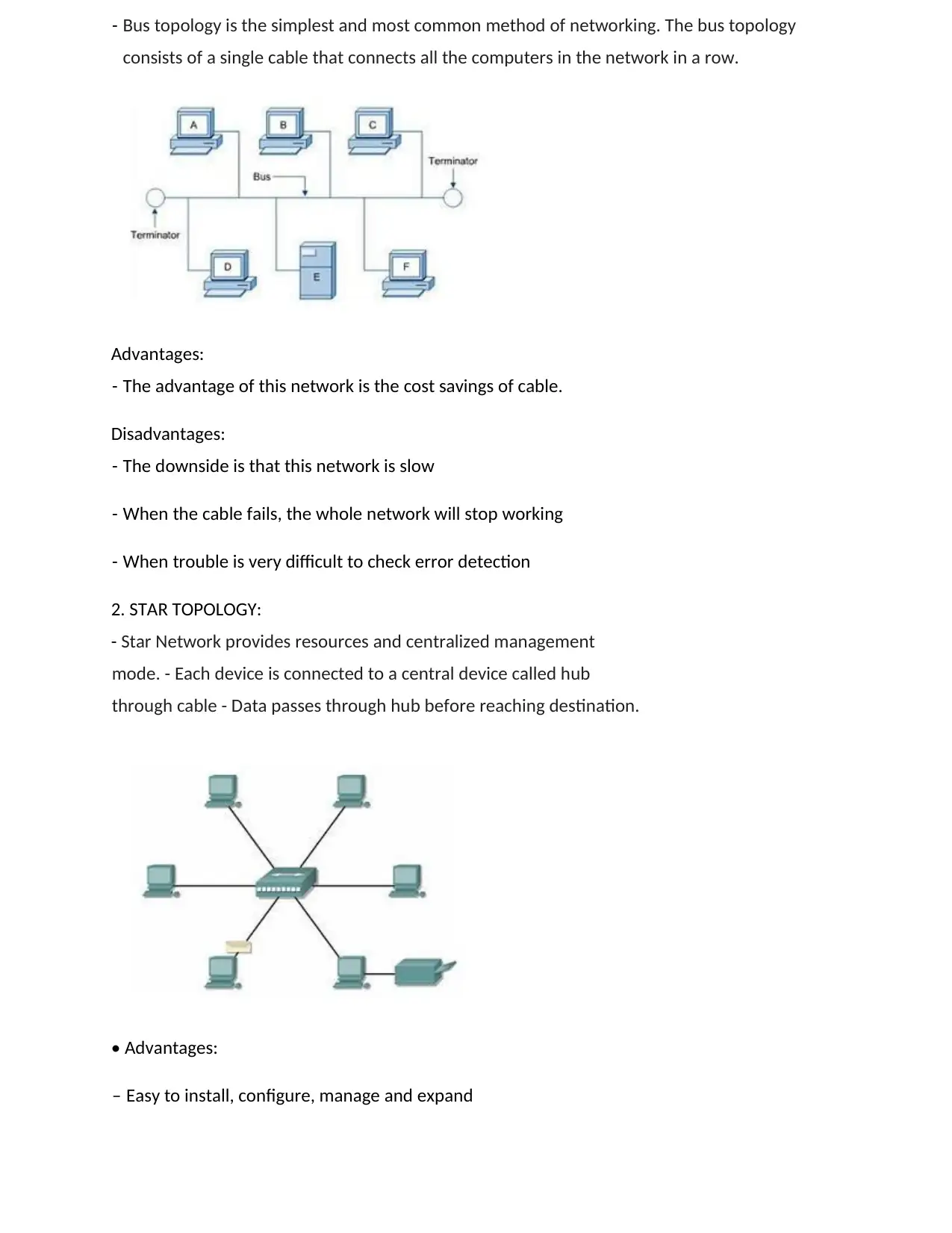
- Bus topology is the simplest and most common method of networking. The bus topology
consists of a single cable that connects all the computers in the network in a row.
Advantages:
- The advantage of this network is the cost savings of cable.
Disadvantages:
- The downside is that this network is slow
- When the cable fails, the whole network will stop working
- When trouble is very difficult to check error detection
2. STAR TOPOLOGY:
- Star Network provides resources and centralized management
mode. - Each device is connected to a central device called hub
through cable - Data passes through hub before reaching destination.
• Advantages:
– Easy to install, configure, manage and expand
consists of a single cable that connects all the computers in the network in a row.
Advantages:
- The advantage of this network is the cost savings of cable.
Disadvantages:
- The downside is that this network is slow
- When the cable fails, the whole network will stop working
- When trouble is very difficult to check error detection
2. STAR TOPOLOGY:
- Star Network provides resources and centralized management
mode. - Each device is connected to a central device called hub
through cable - Data passes through hub before reaching destination.
• Advantages:
– Easy to install, configure, manage and expand
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
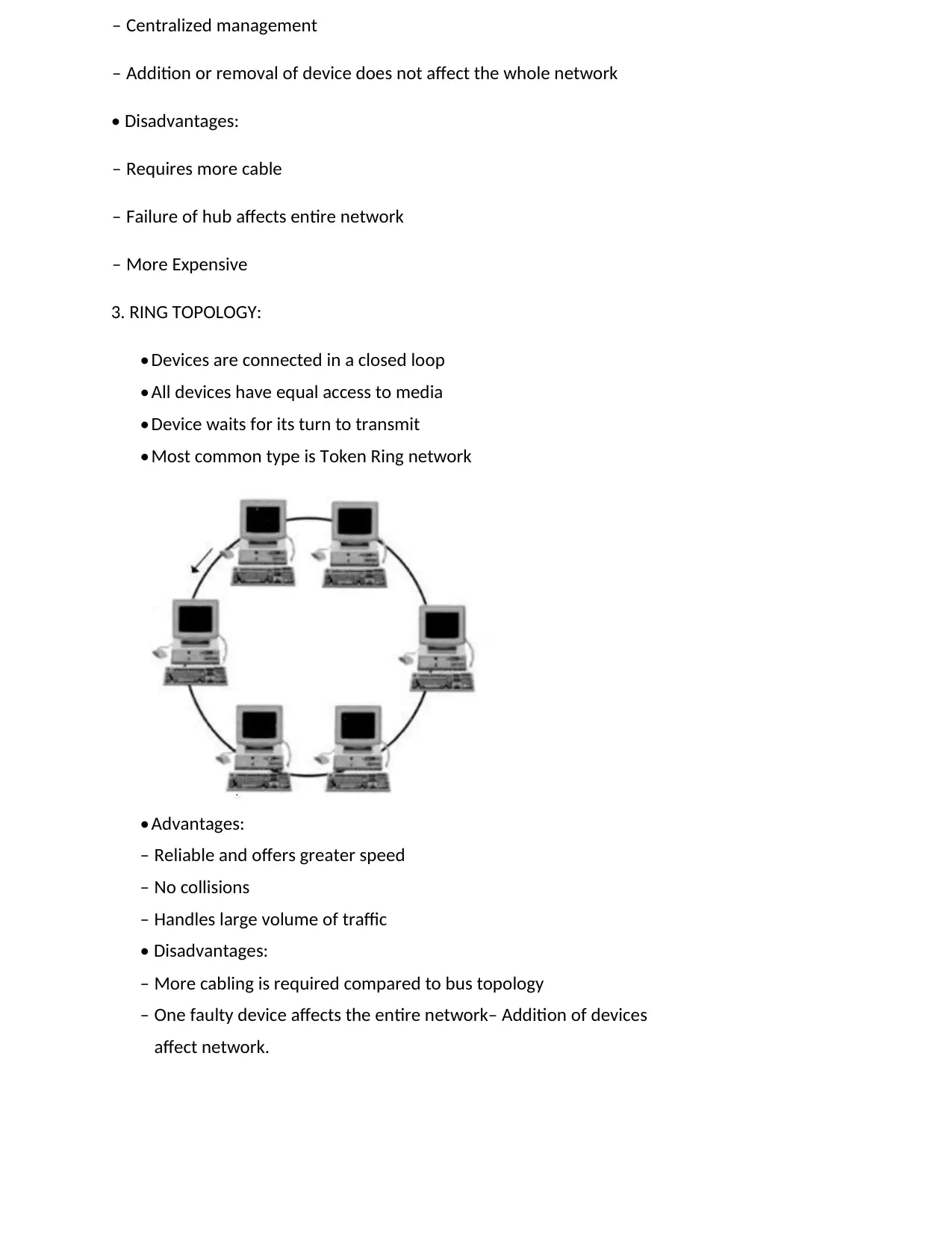
– Centralized management
– Addition or removal of device does not affect the whole network
• Disadvantages:
– Requires more cable
– Failure of hub affects entire network
– More Expensive
3. RING TOPOLOGY:
• Devices are connected in a closed loop
• All devices have equal access to media
• Device waits for its turn to transmit
• Most common type is Token Ring network
• Advantages:
– Reliable and offers greater speed
– No collisions
– Handles large volume of traffic
• Disadvantages:
– More cabling is required compared to bus topology
– One faulty device affects the entire network– Addition of devices
affect network.
– Addition or removal of device does not affect the whole network
• Disadvantages:
– Requires more cable
– Failure of hub affects entire network
– More Expensive
3. RING TOPOLOGY:
• Devices are connected in a closed loop
• All devices have equal access to media
• Device waits for its turn to transmit
• Most common type is Token Ring network
• Advantages:
– Reliable and offers greater speed
– No collisions
– Handles large volume of traffic
• Disadvantages:
– More cabling is required compared to bus topology
– One faulty device affects the entire network– Addition of devices
affect network.
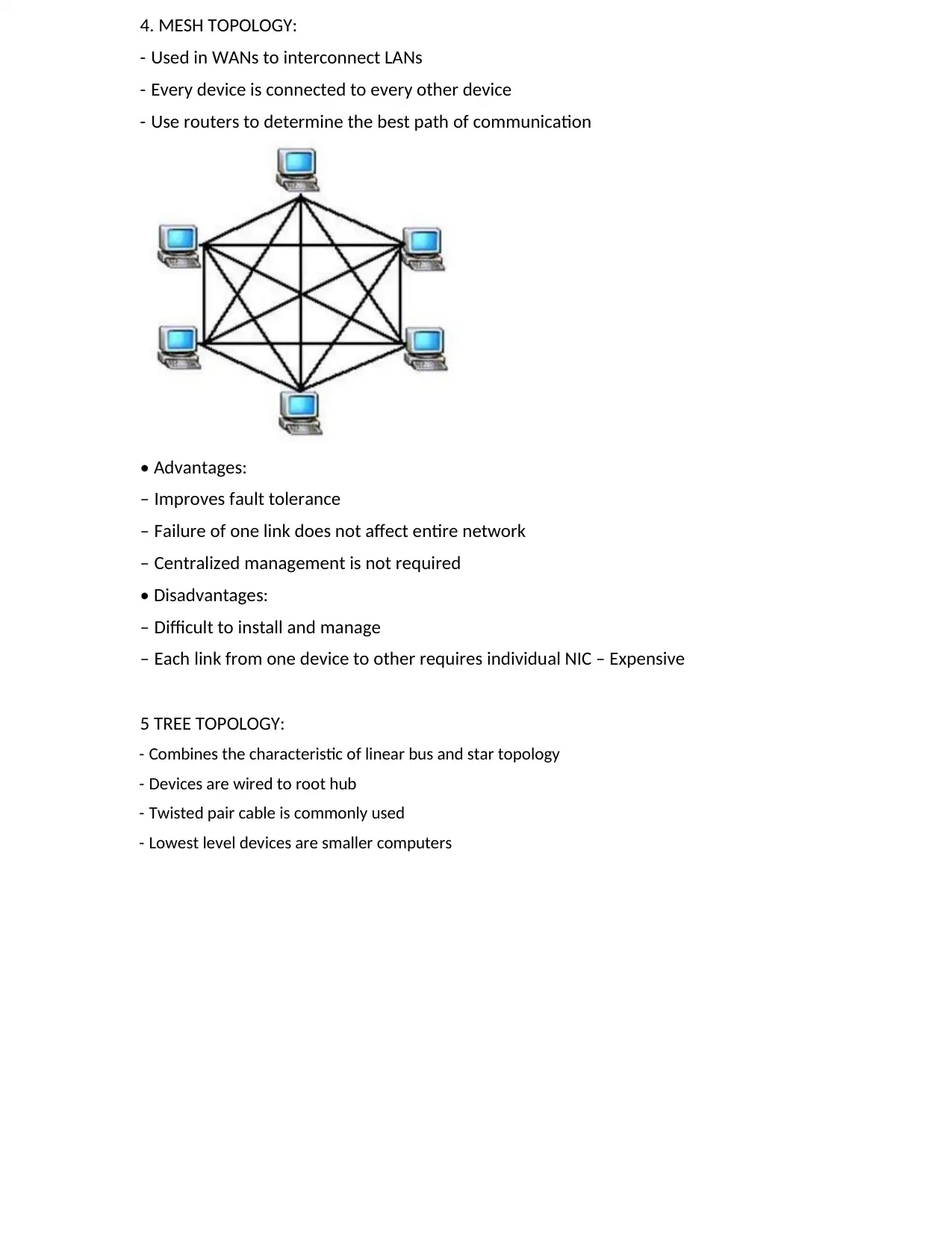
4. MESH TOPOLOGY:
- Used in WANs to interconnect LANs
- Every device is connected to every other device
- Use routers to determine the best path of communication
• Advantages:
– Improves fault tolerance
– Failure of one link does not affect entire network
– Centralized management is not required
• Disadvantages:
– Difficult to install and manage
– Each link from one device to other requires individual NIC – Expensive
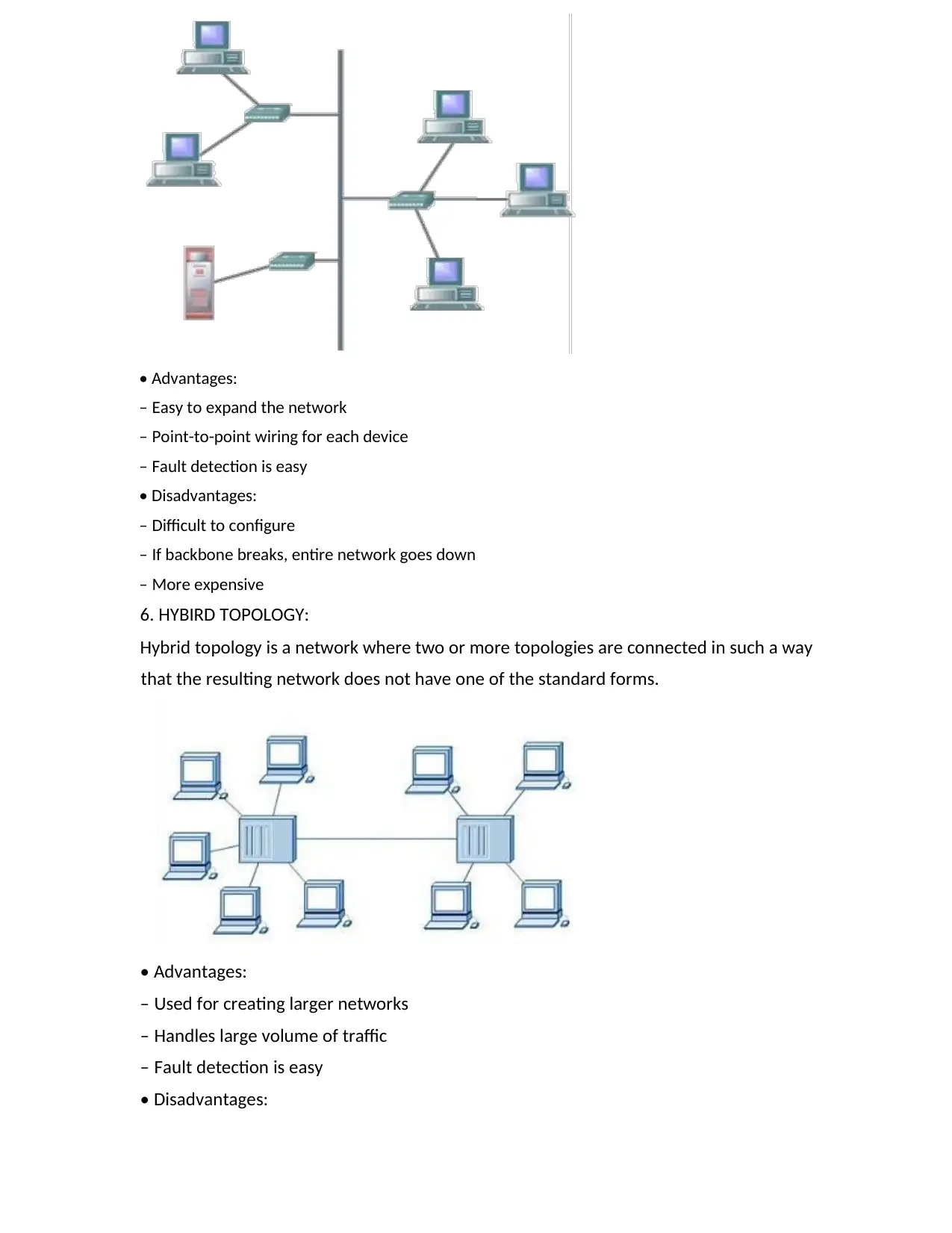
5 TREE TOPOLOGY:
- Combines the characteristic of linear bus and star topology
- Devices are wired to root hub
- Twisted pair cable is commonly used
- Lowest level devices are smaller computers
- Used in WANs to interconnect LANs
- Every device is connected to every other device
- Use routers to determine the best path of communication
• Advantages:
– Improves fault tolerance
– Failure of one link does not affect entire network
– Centralized management is not required
• Disadvantages:
– Difficult to install and manage
– Each link from one device to other requires individual NIC – Expensive
5 TREE TOPOLOGY:
- Combines the characteristic of linear bus and star topology
- Devices are wired to root hub
- Twisted pair cable is commonly used
- Lowest level devices are smaller computers
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
• Advantages:
– Easy to expand the network
– Point-to-point wiring for each device
– Fault detection is easy
• Disadvantages:
– Difficult to configure
– If backbone breaks, entire network goes down
– More expensive
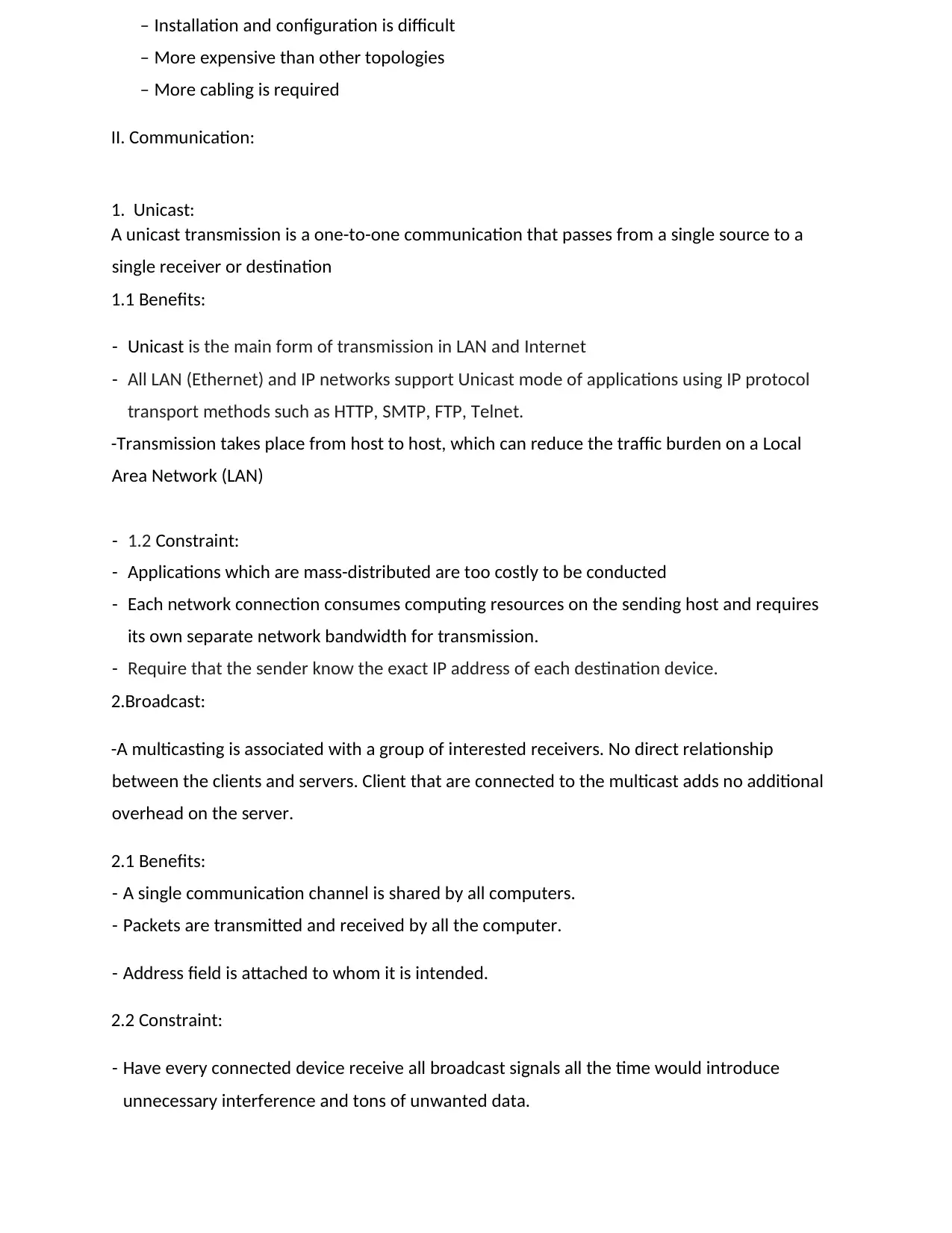
6. HYBIRD TOPOLOGY:
Hybrid topology is a network where two or more topologies are connected in such a way
that the resulting network does not have one of the standard forms.
• Advantages:
– Used for creating larger networks
– Handles large volume of traffic
– Fault detection is easy
• Disadvantages:
– Easy to expand the network
– Point-to-point wiring for each device
– Fault detection is easy
• Disadvantages:
– Difficult to configure
– If backbone breaks, entire network goes down
– More expensive
6. HYBIRD TOPOLOGY:
Hybrid topology is a network where two or more topologies are connected in such a way
that the resulting network does not have one of the standard forms.
• Advantages:
– Used for creating larger networks
– Handles large volume of traffic
– Fault detection is easy
• Disadvantages:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
– Installation and configuration is difficult
– More expensive than other topologies
– More cabling is required
II. Communication:
1. Unicast:
A unicast transmission is a one-to-one communication that passes from a single source to a
single receiver or destination
1.1 Benefits:
- Unicast is the main form of transmission in LAN and Internet
- All LAN (Ethernet) and IP networks support Unicast mode of applications using IP protocol
transport methods such as HTTP, SMTP, FTP, Telnet.
-Transmission takes place from host to host, which can reduce the traffic burden on a Local
Area Network (LAN)
- 1.2 Constraint:
- Applications which are mass-distributed are too costly to be conducted
- Each network connection consumes computing resources on the sending host and requires
its own separate network bandwidth for transmission.
- Require that the sender know the exact IP address of each destination device.
2.Broadcast:
-A multicasting is associated with a group of interested receivers. No direct relationship
between the clients and servers. Client that are connected to the multicast adds no additional
overhead on the server.
2.1 Benefits:
- A single communication channel is shared by all computers.
- Packets are transmitted and received by all the computer.
- Address field is attached to whom it is intended.
2.2 Constraint:
- Have every connected device receive all broadcast signals all the time would introduce
unnecessary interference and tons of unwanted data.
– More expensive than other topologies
– More cabling is required
II. Communication:
1. Unicast:
A unicast transmission is a one-to-one communication that passes from a single source to a
single receiver or destination
1.1 Benefits:
- Unicast is the main form of transmission in LAN and Internet
- All LAN (Ethernet) and IP networks support Unicast mode of applications using IP protocol
transport methods such as HTTP, SMTP, FTP, Telnet.
-Transmission takes place from host to host, which can reduce the traffic burden on a Local
Area Network (LAN)
- 1.2 Constraint:
- Applications which are mass-distributed are too costly to be conducted
- Each network connection consumes computing resources on the sending host and requires
its own separate network bandwidth for transmission.
- Require that the sender know the exact IP address of each destination device.
2.Broadcast:
-A multicasting is associated with a group of interested receivers. No direct relationship
between the clients and servers. Client that are connected to the multicast adds no additional
overhead on the server.
2.1 Benefits:
- A single communication channel is shared by all computers.
- Packets are transmitted and received by all the computer.
- Address field is attached to whom it is intended.
2.2 Constraint:
- Have every connected device receive all broadcast signals all the time would introduce
unnecessary interference and tons of unwanted data.

-Broadcasts are available on many levels of the OSI model, so they must be adjusted to fit from
one floor to the next.
- Network allows the server to provide data of limited bandwidth, maximum bandwidth client =
general service bandwidth.
3.Multicast:
- Multicast is the way the message is sent from one point to another, and thus a multi-point
connection. This technique is used under the OSI model in the network layer.
3.1 Benefits:
-Its advantage is that at the same time the message is sent to multiple participants or to a group
of private users. The transmitter only needs the data transfer rate as if there was only one
receiver while multicasting. Multicast is useful if a group of customers requires a common set of
data at the same time. Multicast transmission saves significant bandwidth.
- Capable of controlling network traffic and reducing server and CPU load, optimize
transmission performance
3.2 Constraint:
-Lack of TCP windowing and “slow start” mechanisms can result in network congestion.
- Some multicast protocol mechanisms result in the occasional generation of duplicate packets.
III. Bandwidth Requirement:
1. Bandwidth:
- Bandwidth is a term refers to the flow of electrical signals transmitted through the
transmission device per second. 2. Bandwidth Requirement:
- Expected average load
- Anticipated peak load
- Local internet availability
- Cost constraints, throughput.
P3. Discuss the operating principles of networking devices and server types.
Implement a network design topology infrastructure based on a prepared design
and list the different type of topologies.
I. Discuss the operating principles of networking devices.
1. Repeater:
1.1 What is Repeater:
one floor to the next.
- Network allows the server to provide data of limited bandwidth, maximum bandwidth client =
general service bandwidth.
3.Multicast:
- Multicast is the way the message is sent from one point to another, and thus a multi-point
connection. This technique is used under the OSI model in the network layer.
3.1 Benefits:
-Its advantage is that at the same time the message is sent to multiple participants or to a group
of private users. The transmitter only needs the data transfer rate as if there was only one
receiver while multicasting. Multicast is useful if a group of customers requires a common set of
data at the same time. Multicast transmission saves significant bandwidth.
- Capable of controlling network traffic and reducing server and CPU load, optimize
transmission performance
3.2 Constraint:
-Lack of TCP windowing and “slow start” mechanisms can result in network congestion.
- Some multicast protocol mechanisms result in the occasional generation of duplicate packets.
III. Bandwidth Requirement:
1. Bandwidth:
- Bandwidth is a term refers to the flow of electrical signals transmitted through the
transmission device per second. 2. Bandwidth Requirement:
- Expected average load
- Anticipated peak load
- Local internet availability
- Cost constraints, throughput.
P3. Discuss the operating principles of networking devices and server types.
Implement a network design topology infrastructure based on a prepared design
and list the different type of topologies.
I. Discuss the operating principles of networking devices.
1. Repeater:
1.1 What is Repeater:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





