Network Technologies and Design
VerifiedAdded on 2020/06/04
|40
|9127
|81
AI Summary
This assignment delves into various network technologies and design principles. It covers fundamental concepts like network topologies (bus, star, ring), the OSI model, the TCP/IP model, and Virtual Private Networks (VPNs). The assignment also explores Network Operating Systems (NOS) and their significance in managing network resources. Illustrative diagrams enhance understanding of these complex concepts.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Unit 24: Networking
Technologies
Technologies
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
TASK 1............................................................................................................................................1
1.1 Benefits of networking technologies and networking systems .......................................1
1.2 Impact of current network technologies .........................................................................5
1.3 Effective utilization of different networking system using protocols..............................8
M 1.................................................................................................................................................11
TASK 2..........................................................................................................................................11
2.1 Role of software and hardware components..................................................................11
2.2 Types of servers .............................................................................................................14
2.3 Interdependence of workstation hardware......................................................................15
M 2.................................................................................................................................................16
TASK 3.........................................................................................................................................18
TASK 4.........................................................................................................................................25
4.1 – Implement a network systems based on the proposed design. You are required to use me
ans of simulation software, establish a network according to the design in task 3..............25
4.2. Test network systems to meet user requirements. Your testing includes functionality of th
e network to ensure that your developed network will operate seamlessly in a physical environ
ment so that it can satisfy user requirements........................................................................30
4.3. Document and analyse test result against expected results. While carrying out task 4.2, th
e testing of the network has produced a number of results. List the results you have found in ta
sk 4.2 by contrasting them with your expected results.........................................................33
4.4. Recommend potential enhancement for the networked systems. Your discussions should i
nclude how your developed network will cope with future changing needs and should address
possible enhancements of your network to satisfy needs of changing future environment. 34
4.5. Design a maintenance schedule to support the network system. Your maintenance schedul
e should address various factors likepersonnel allocation, backup and recovery policy, maintai
ning security & integrity; and general administration to support the users..........................35
CONCLUSION..............................................................................................................................36
REFERENCES..............................................................................................................................37
INTRODUCTION...........................................................................................................................1
TASK 1............................................................................................................................................1
1.1 Benefits of networking technologies and networking systems .......................................1
1.2 Impact of current network technologies .........................................................................5
1.3 Effective utilization of different networking system using protocols..............................8
M 1.................................................................................................................................................11
TASK 2..........................................................................................................................................11
2.1 Role of software and hardware components..................................................................11
2.2 Types of servers .............................................................................................................14
2.3 Interdependence of workstation hardware......................................................................15
M 2.................................................................................................................................................16
TASK 3.........................................................................................................................................18
TASK 4.........................................................................................................................................25
4.1 – Implement a network systems based on the proposed design. You are required to use me
ans of simulation software, establish a network according to the design in task 3..............25
4.2. Test network systems to meet user requirements. Your testing includes functionality of th
e network to ensure that your developed network will operate seamlessly in a physical environ
ment so that it can satisfy user requirements........................................................................30
4.3. Document and analyse test result against expected results. While carrying out task 4.2, th
e testing of the network has produced a number of results. List the results you have found in ta
sk 4.2 by contrasting them with your expected results.........................................................33
4.4. Recommend potential enhancement for the networked systems. Your discussions should i
nclude how your developed network will cope with future changing needs and should address
possible enhancements of your network to satisfy needs of changing future environment. 34
4.5. Design a maintenance schedule to support the network system. Your maintenance schedul
e should address various factors likepersonnel allocation, backup and recovery policy, maintai
ning security & integrity; and general administration to support the users..........................35
CONCLUSION..............................................................................................................................36
REFERENCES..............................................................................................................................37

INTRODUCTION
Network is defined as connection of computers with an objective to share resources,
Process of exchanging information and data between systems is called networking technology.
Networking is defined as the structuring and making of network system by using cables and
bridges. It is used to manage network and telecommunication process of organisations. It plays
an important role in providing platform for communication purposes. It helps in connecting
people in by removing geographical limits. An important platform for networking technology is
internet.
Present report describes about benefits and constraints of various system of networking
and its types. Effect of current technology of network has been discussed in the report.
Furthermore, effective utilization of network is also explained. Role of software and hardware
elements and their applications has been illustrated. Types of servers and their selection ned in
company has been discussed. More over, inter dependence of workstation hardware with
network is also illustrated in the report.
TASK 1
1.1 Benefits of networking technologies and networking systems
According to the case study Beta communication Ltd is a telecommunication company.
The organisation was using stand alone PCs and dial up approach for their networking purposes.
Now the company is planing to build their own local are network system. Purpose of network in
the company to share their resources and information effectively (PSN .2017). There is major
role and benefits of networks in information sharing of the organisation. Some benefits of
network technology is as follows:
Sharing of information becomes easy by making us of networking technology in
organisation.
Networking systems makes it easy for sharing files and data remotely to different
connected computers (Brandwine and Hill, 2014).
Use of internal connected devices like printers and copiers helps in resource sharing.
In networking single internet link is share among PC's that helps in protecting system of
the organisation from hacking.
Network is defined as connection of computers with an objective to share resources,
Process of exchanging information and data between systems is called networking technology.
Networking is defined as the structuring and making of network system by using cables and
bridges. It is used to manage network and telecommunication process of organisations. It plays
an important role in providing platform for communication purposes. It helps in connecting
people in by removing geographical limits. An important platform for networking technology is
internet.
Present report describes about benefits and constraints of various system of networking
and its types. Effect of current technology of network has been discussed in the report.
Furthermore, effective utilization of network is also explained. Role of software and hardware
elements and their applications has been illustrated. Types of servers and their selection ned in
company has been discussed. More over, inter dependence of workstation hardware with
network is also illustrated in the report.
TASK 1
1.1 Benefits of networking technologies and networking systems
According to the case study Beta communication Ltd is a telecommunication company.
The organisation was using stand alone PCs and dial up approach for their networking purposes.
Now the company is planing to build their own local are network system. Purpose of network in
the company to share their resources and information effectively (PSN .2017). There is major
role and benefits of networks in information sharing of the organisation. Some benefits of
network technology is as follows:
Sharing of information becomes easy by making us of networking technology in
organisation.
Networking systems makes it easy for sharing files and data remotely to different
connected computers (Brandwine and Hill, 2014).
Use of internal connected devices like printers and copiers helps in resource sharing.
In networking single internet link is share among PC's that helps in protecting system of
the organisation from hacking.
Storage capacity of network connected devices gets increased.
Communication with suppliers and consumers of the company will also improve by
using networking systems.
Business of the organisation will become more efficient by using common database
which helps in avoiding data repetition
Centralized network supports in less requirement of IT.
There are four types networking system which have various benefits :
Local area network : LAN comprises a single network which is suitable for particular
physical location (Christensen, 2013). Local area network is very beneficial for sharing
resources within a building. It is very useful for Beta communication Ltd. as the
company need to share information among themselves. This networking system will also
fit in their budget as this costs low in deploying this system.
(Source: Networking types .2017. )
Metropolitan area network : MAN is network which is used for small region. It is
generally used to give internet access in entire city. A MAN is generally used to
connected together to make a bigger network.
Advantage and disadvantages of metropolitan are network :
It cover wider area so it become easy to provide conceptions.
◦ It is very useful for libraries and airports.
◦ MAN can operate only when a PC can compete.
Illustration 1: LAN
Communication with suppliers and consumers of the company will also improve by
using networking systems.
Business of the organisation will become more efficient by using common database
which helps in avoiding data repetition
Centralized network supports in less requirement of IT.
There are four types networking system which have various benefits :
Local area network : LAN comprises a single network which is suitable for particular
physical location (Christensen, 2013). Local area network is very beneficial for sharing
resources within a building. It is very useful for Beta communication Ltd. as the
company need to share information among themselves. This networking system will also
fit in their budget as this costs low in deploying this system.
(Source: Networking types .2017. )
Metropolitan area network : MAN is network which is used for small region. It is
generally used to give internet access in entire city. A MAN is generally used to
connected together to make a bigger network.
Advantage and disadvantages of metropolitan are network :
It cover wider area so it become easy to provide conceptions.
◦ It is very useful for libraries and airports.
◦ MAN can operate only when a PC can compete.
Illustration 1: LAN
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Wide area network : WAN is used to connect large area like whole country of region. It
contains various small networks like ;local and metropolitan area networks.
Advantages and disadvantages of WAN
WAN contains centralized IT structure due to which it eliminates the requirement of
buying servers.
Privacy level of the business information get increases using WAN.
It cost very high to setup WAN's.
Issue of maintenance is also there with WAN's Security breach problem is also with wide are networks.
Peer based network systems : in peer based network system two or more personal
computers are linked to share resources and information. Single universal bus is used to
connect PC's to transfer files. It can be used by Beta communication Ltd.
Advantages: It is easy to install per based networking systems. P2P is reliable networks
systems. Full time administrator is not required in this.
Disadvantage: In this system its becomes difficult to determine who is accessing the network.
Data backup is also difficult in this systems.
Client server based systems : It is made for end user who are termed as clients. These
clients can access information like files, documents and videos form the central computer
device which is called server (Da, He and Li, S., 2014). Cloud and clusters : In cloud computing file and data is saved on cloud system rather
than hard drive of computer. In clustering method two computers are linked in away so
that they can represent a single computer. It help in parallel processing. It is also
beneficial for the organisation.
Networking topologies: Networking topologies is an appropriate arrangement of networks I
order to connect different nodes. These are ring topology, start topology , mesh topology and bus
topology. In star topology nodes are connected in structure like star.
Ring topologies
contains various small networks like ;local and metropolitan area networks.
Advantages and disadvantages of WAN
WAN contains centralized IT structure due to which it eliminates the requirement of
buying servers.
Privacy level of the business information get increases using WAN.
It cost very high to setup WAN's.
Issue of maintenance is also there with WAN's Security breach problem is also with wide are networks.
Peer based network systems : in peer based network system two or more personal
computers are linked to share resources and information. Single universal bus is used to
connect PC's to transfer files. It can be used by Beta communication Ltd.
Advantages: It is easy to install per based networking systems. P2P is reliable networks
systems. Full time administrator is not required in this.
Disadvantage: In this system its becomes difficult to determine who is accessing the network.
Data backup is also difficult in this systems.
Client server based systems : It is made for end user who are termed as clients. These
clients can access information like files, documents and videos form the central computer
device which is called server (Da, He and Li, S., 2014). Cloud and clusters : In cloud computing file and data is saved on cloud system rather
than hard drive of computer. In clustering method two computers are linked in away so
that they can represent a single computer. It help in parallel processing. It is also
beneficial for the organisation.
Networking topologies: Networking topologies is an appropriate arrangement of networks I
order to connect different nodes. These are ring topology, start topology , mesh topology and bus
topology. In star topology nodes are connected in structure like star.
Ring topologies
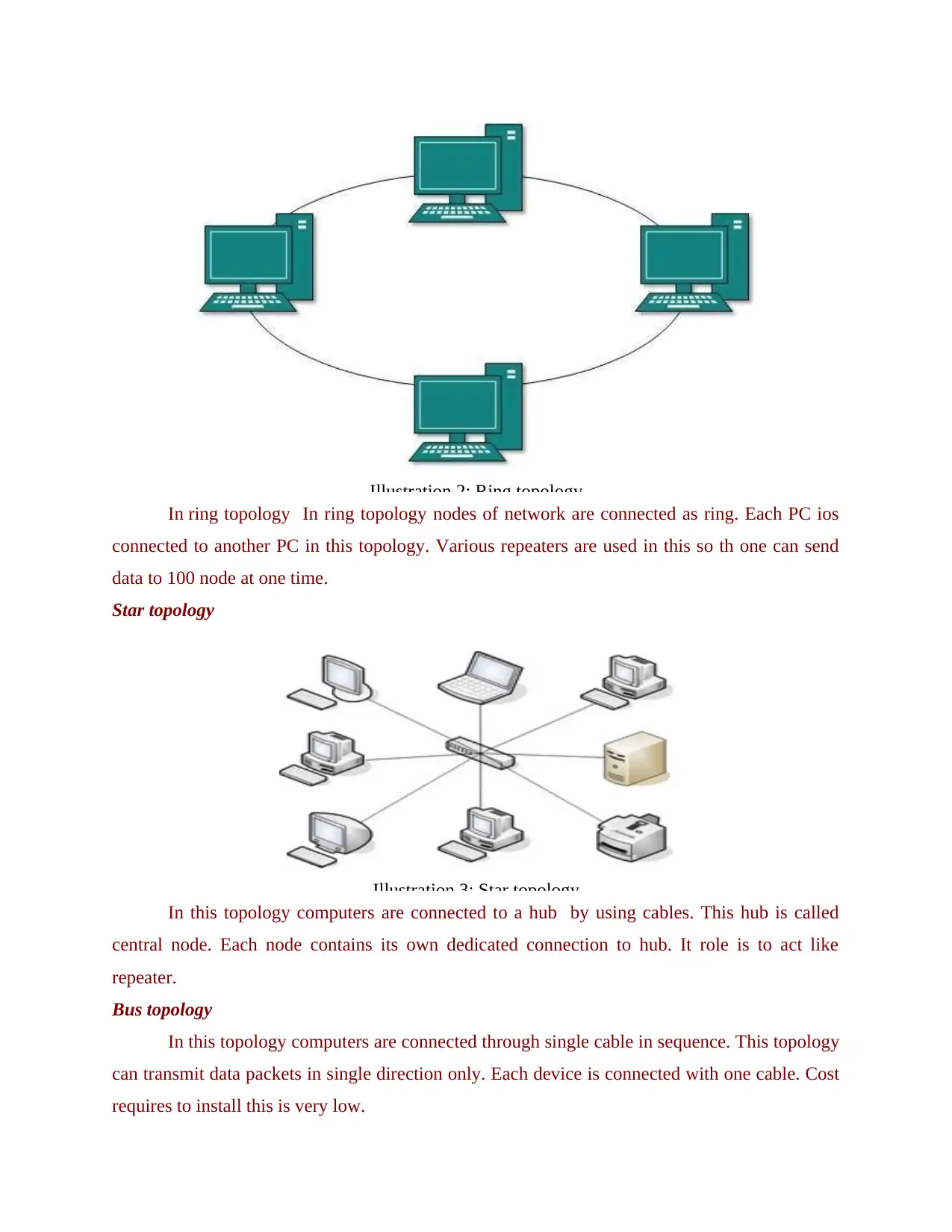
In ring topology In ring topology nodes of network are connected as ring. Each PC ios
connected to another PC in this topology. Various repeaters are used in this so th one can send
data to 100 node at one time.
Star topology
In this topology computers are connected to a hub by using cables. This hub is called
central node. Each node contains its own dedicated connection to hub. It role is to act like
repeater.
Bus topology
In this topology computers are connected through single cable in sequence. This topology
can transmit data packets in single direction only. Each device is connected with one cable. Cost
requires to install this is very low.
Illustration 3: Star topology
Illustration 2: Ring topology
connected to another PC in this topology. Various repeaters are used in this so th one can send
data to 100 node at one time.
Star topology
In this topology computers are connected to a hub by using cables. This hub is called
central node. Each node contains its own dedicated connection to hub. It role is to act like
repeater.
Bus topology
In this topology computers are connected through single cable in sequence. This topology
can transmit data packets in single direction only. Each device is connected with one cable. Cost
requires to install this is very low.
Illustration 3: Star topology
Illustration 2: Ring topology
Requirements for the organisation to install network
Beta communication Ltd. requires to analyse its communication methods, reporting hierarchy,
structure of the organisation. Local administrative rules and policies are need to be considered.
Further company will require Ethernet cables, modem, routers, switches, hubs repeaters etc to
install a network. Type of files and applications that need to be run on network should be
identified. Requirements for organisation to install a network are as follows:
Company should consider purpose of the network .Organisation requires networking variables
and maintenance of network. Company needs to understand physical networks and information
of active directory. Network structure of the area need to understand.
1.2 Impact of current network technologies
There is a huge impact of current network technologies on Beta communication Ltd.
Current network technologies an there effects are as follows:
File transfer protocol (FTP)
This protocol is a standard protocol which is used to transfer information and data form
one server to another one. It is a popular protocol which for upload and download process of
flies. This protocol uses TCP/ IP protocol for enabling transfer of data. In this client server
model is used to which is protected with SSL/ TLS. This enables file sharing through remote
computers. Data is transferred deficiently in this protocol. It provides authentication to user by
simple sign in protocol (Gubbi and et.al, 2013). Username and password are required by client
for authentication process. The FTP totally depends on client and server. It works in two mode
which are passive and active. In the active state client start initiating a session by sending a
command. This command is received by server and after that it make connection to client for
Illustration 4: Bus topology
Beta communication Ltd. requires to analyse its communication methods, reporting hierarchy,
structure of the organisation. Local administrative rules and policies are need to be considered.
Further company will require Ethernet cables, modem, routers, switches, hubs repeaters etc to
install a network. Type of files and applications that need to be run on network should be
identified. Requirements for organisation to install a network are as follows:
Company should consider purpose of the network .Organisation requires networking variables
and maintenance of network. Company needs to understand physical networks and information
of active directory. Network structure of the area need to understand.
1.2 Impact of current network technologies
There is a huge impact of current network technologies on Beta communication Ltd.
Current network technologies an there effects are as follows:
File transfer protocol (FTP)
This protocol is a standard protocol which is used to transfer information and data form
one server to another one. It is a popular protocol which for upload and download process of
flies. This protocol uses TCP/ IP protocol for enabling transfer of data. In this client server
model is used to which is protected with SSL/ TLS. This enables file sharing through remote
computers. Data is transferred deficiently in this protocol. It provides authentication to user by
simple sign in protocol (Gubbi and et.al, 2013). Username and password are required by client
for authentication process. The FTP totally depends on client and server. It works in two mode
which are passive and active. In the active state client start initiating a session by sending a
command. This command is received by server and after that it make connection to client for
Illustration 4: Bus topology
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

enabling data transfer. This protocol can be used by Beta communication Ltd. for efficient and
secure transfer of data.
Simple mail transfer protocol (SMTP)
It is an standard protocol which is used for email transferring services. This protocol also
uses TCP/IP protocol to enable file transferring. It is used to upload mail directly on networks.
Simple mail transfer protocol use POP 3 service. It is an application layer model which helps in
enabling transmission of emails over internet. It is popular model which is used for
communication via email. In SMTP there are four types of keys which is use between client and
server. These keys are Mail user agent, mail submission agent , mail transfer agent and agent for
mail delivery.
Hyper text transfer protocol (HTTP)
It is a protocol in which particular set of rules are defined for transferring files. This
protocol support in transferring files such as sound, text, video and various type of multimedia
files. File are transferred on the World Wide Web. Users use HTTP whenever they open web
browser on their computers. It is an application protocol whose functioning totally depends on
TCP/IP suite. Hypertext is used in this protocol which gives references to various files which are
result of user request on browser (Istepanian, Laxminarayan and Pattichis, 2014).
IPV4
IPV4 is a fourth version of internet protocol. It is used widely data communication on
various type of networks (Jain and Paul, 2013). It is connection less protocol which is sued in
Ethernet services. Logical connection is provided by IPV4 for device identification. This
protocol is configured using no automatic and automatic configurations. These configurations
depends on the type of network. This protocol do not provides guarantee of duplicate data.
IPV6
This protocol is 6th version of internet protocol. It is used to fulfil the requirements of
more addresses for internet (Kim, and et.al 2014). This protocol overcomes the bugs of previous
version i.e. IPV4. This protocol do not requires manual configuration because it is an auto
configured protocol. It provides better masticasting. It has inbuilt authentication support. Header
format is simpler that that of IPV4. Thus internet protocol should be used while designing
network system for beta communication Ltd.
Ethernet
secure transfer of data.
Simple mail transfer protocol (SMTP)
It is an standard protocol which is used for email transferring services. This protocol also
uses TCP/IP protocol to enable file transferring. It is used to upload mail directly on networks.
Simple mail transfer protocol use POP 3 service. It is an application layer model which helps in
enabling transmission of emails over internet. It is popular model which is used for
communication via email. In SMTP there are four types of keys which is use between client and
server. These keys are Mail user agent, mail submission agent , mail transfer agent and agent for
mail delivery.
Hyper text transfer protocol (HTTP)
It is a protocol in which particular set of rules are defined for transferring files. This
protocol support in transferring files such as sound, text, video and various type of multimedia
files. File are transferred on the World Wide Web. Users use HTTP whenever they open web
browser on their computers. It is an application protocol whose functioning totally depends on
TCP/IP suite. Hypertext is used in this protocol which gives references to various files which are
result of user request on browser (Istepanian, Laxminarayan and Pattichis, 2014).
IPV4
IPV4 is a fourth version of internet protocol. It is used widely data communication on
various type of networks (Jain and Paul, 2013). It is connection less protocol which is sued in
Ethernet services. Logical connection is provided by IPV4 for device identification. This
protocol is configured using no automatic and automatic configurations. These configurations
depends on the type of network. This protocol do not provides guarantee of duplicate data.
IPV6
This protocol is 6th version of internet protocol. It is used to fulfil the requirements of
more addresses for internet (Kim, and et.al 2014). This protocol overcomes the bugs of previous
version i.e. IPV4. This protocol do not requires manual configuration because it is an auto
configured protocol. It provides better masticasting. It has inbuilt authentication support. Header
format is simpler that that of IPV4. Thus internet protocol should be used while designing
network system for beta communication Ltd.
Ethernet
Ether net is used widely to install LAN. It is a physical layer technology which is used to
connect LAN to computers. It is attached with both layers physical and data link in OSI model. It
describes two aspect of transmission that are data packet and frame. Each frame is covered by
data packet. It allows data seeped of 10 Mbps and at base T Ethernet and 100 Mbps at fats
Ethernet an 1000 Mbps at Gigabit Ethernet. Ethernet contains two layers which are physical and
data link layer. The frame in Ethernet involves payload of data with addressing information by
determining the MAC address. The address is send to bot sender and receiver.
Illustration 5: TCP/IP model
connect LAN to computers. It is attached with both layers physical and data link in OSI model. It
describes two aspect of transmission that are data packet and frame. Each frame is covered by
data packet. It allows data seeped of 10 Mbps and at base T Ethernet and 100 Mbps at fats
Ethernet an 1000 Mbps at Gigabit Ethernet. Ethernet contains two layers which are physical and
data link layer. The frame in Ethernet involves payload of data with addressing information by
determining the MAC address. The address is send to bot sender and receiver.
Illustration 5: TCP/IP model

Token ring
It is also a type of LAN and in this structure PC's are connected in ring or star network
topology. All computers in the token ring are connected in shape of circle. For sending a
message computer gets a token and the message is attached to it. This message continuously
moves close to the network.
FDDI
It is fibre distributed data interface. It transmits data over the fibre optic cable. These
networks are also called token passing. Data rate up to 100 MBPS is provided by this network. It
incorporates two token rings form which one is for backup. It is used for interconnection of local
are networks. FDDI is based on token ring protocol. In addition to that this data interface
supports number of users at one time. FDDI is also called backbone of wide area network. This
interface consist of two token rings form which one is for use and one is for backup. It adds
capability to circuit switched network.
1.3 Effective utilization of different networking system using protocols
Networks protocols are used to ensure appropriate utilization of networks. There are
various model used to ensure proper use of networks. Some models are as follows:
OSI model
OSI model is an open system interconnection model which consist of 7 layers. This
model represents communication of application over network. It is used to ensure data
communication world wide (Leonardi, Huysman and Steinfield, 2013). It describes that systems
should be made which are able to communicate with one another. It also ensures compatibility of
systems. This model works on seven layers which are as follows: Physical layer : It is the lower most layer of the model. Role of this layer to establish
and deactivate physical connections. This layer is responsible for transmitting data over
the network. Analog signals are converted into digital signals in this layer. Encoding of
data is done in this layer.
Data link layer: This layer role is to synchronize the data which is to be transferred to
physical layer. Major role of this layer to transfer data without errors. Data frames are
It is also a type of LAN and in this structure PC's are connected in ring or star network
topology. All computers in the token ring are connected in shape of circle. For sending a
message computer gets a token and the message is attached to it. This message continuously
moves close to the network.
FDDI
It is fibre distributed data interface. It transmits data over the fibre optic cable. These
networks are also called token passing. Data rate up to 100 MBPS is provided by this network. It
incorporates two token rings form which one is for backup. It is used for interconnection of local
are networks. FDDI is based on token ring protocol. In addition to that this data interface
supports number of users at one time. FDDI is also called backbone of wide area network. This
interface consist of two token rings form which one is for use and one is for backup. It adds
capability to circuit switched network.
1.3 Effective utilization of different networking system using protocols
Networks protocols are used to ensure appropriate utilization of networks. There are
various model used to ensure proper use of networks. Some models are as follows:
OSI model
OSI model is an open system interconnection model which consist of 7 layers. This
model represents communication of application over network. It is used to ensure data
communication world wide (Leonardi, Huysman and Steinfield, 2013). It describes that systems
should be made which are able to communicate with one another. It also ensures compatibility of
systems. This model works on seven layers which are as follows: Physical layer : It is the lower most layer of the model. Role of this layer to establish
and deactivate physical connections. This layer is responsible for transmitting data over
the network. Analog signals are converted into digital signals in this layer. Encoding of
data is done in this layer.
Data link layer: This layer role is to synchronize the data which is to be transferred to
physical layer. Major role of this layer to transfer data without errors. Data frames are
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

transmitted and received over this layer. Logical layer is made by this layer for managing
frame traffic on the network.
(Source: OSI .2017 ) Network layer: This layer is used to route the signal via different channels form one link
to the other. The layer is responsible for controlling network and subnet traffic. It is used
to decide the route of data (Suthaharan, 2014.). Transport payer: This layer is used to decide path of transmission of data. This layer is
responsible for doing Multiplexing and segmenting of data. Messages are received by
this layer from the session layer. It convert message into packets. These packet are passed
to the network layer. Session layer: This layer is responsible for managing conversation which takes place
between two distinct applications. The mail responsibility of this layer is to avoid data
losses over the networks (Christensen, 2013). Presentation layer: Role of this layer is to make data understandable and usable. This
layer converts data for the layer below it which is application layer. Compression,
encryption and conversion of data is done by this layer.
Illustration 6: OSI model
frame traffic on the network.
(Source: OSI .2017 ) Network layer: This layer is used to route the signal via different channels form one link
to the other. The layer is responsible for controlling network and subnet traffic. It is used
to decide the route of data (Suthaharan, 2014.). Transport payer: This layer is used to decide path of transmission of data. This layer is
responsible for doing Multiplexing and segmenting of data. Messages are received by
this layer from the session layer. It convert message into packets. These packet are passed
to the network layer. Session layer: This layer is responsible for managing conversation which takes place
between two distinct applications. The mail responsibility of this layer is to avoid data
losses over the networks (Christensen, 2013). Presentation layer: Role of this layer is to make data understandable and usable. This
layer converts data for the layer below it which is application layer. Compression,
encryption and conversion of data is done by this layer.
Illustration 6: OSI model

Application layer: This layer is at the topmost of the 7 layer architecture. This layer role
is to contain and control application programs.
TCP/ IP model for communication standard is as follows:
The model is 4 layer architecture model and it means transmission control protocol and internet
protocol. Layers of the model is as follows:
Layer 1 : Host to network layer
It is the lowest layer of the model and it is used to connect host for transmission of data
packets over it. This layers varies form host to host and network to network.
Layer 2: Internet layer
This layer is responsible for holding the entire architecture. It supports data packets to
travel from one destination to another. This layer uses internet protocol.
Layer 3: Transport layer
This layer's role is to determine path of data transmission. Multiplexing, segmenting and
data splitting is done in this layer. This layer adds header to the data packet.
Layer 4: Application layer
This layer allows flexibility to data for accessing other applications such as HTTP, FTP,
SMTP etc.
DHCP: It is dynamic host control protocol. It is used to provide fast and automatic access for
distributing IP address within the network. It is used to assign unique IP address to each device
on TCP/IP model. IP addressed of computers moved form one subnet to another. With the help
of DHCP whole process for assigning IP addresses is done automatically. When device on TCP/
IP is turned on and linked to a network then DHCP server sends request to server which is called
DHCP DISCOVER.
DNS: It Is the by which internet domains names are allocated and translated into IP's. It is a
hierarchical framework fro computer and other resources. Names to system are provided by
using worldwide directory service.
Routing protocols
Routing protocols describes communication of routers with each other. . A routing
protocol shares this messages first among close neighbours, and then end-to-end the
communication system. In this way , routers increase cognition of the topology of the
is to contain and control application programs.
TCP/ IP model for communication standard is as follows:
The model is 4 layer architecture model and it means transmission control protocol and internet
protocol. Layers of the model is as follows:
Layer 1 : Host to network layer
It is the lowest layer of the model and it is used to connect host for transmission of data
packets over it. This layers varies form host to host and network to network.
Layer 2: Internet layer
This layer is responsible for holding the entire architecture. It supports data packets to
travel from one destination to another. This layer uses internet protocol.
Layer 3: Transport layer
This layer's role is to determine path of data transmission. Multiplexing, segmenting and
data splitting is done in this layer. This layer adds header to the data packet.
Layer 4: Application layer
This layer allows flexibility to data for accessing other applications such as HTTP, FTP,
SMTP etc.
DHCP: It is dynamic host control protocol. It is used to provide fast and automatic access for
distributing IP address within the network. It is used to assign unique IP address to each device
on TCP/IP model. IP addressed of computers moved form one subnet to another. With the help
of DHCP whole process for assigning IP addresses is done automatically. When device on TCP/
IP is turned on and linked to a network then DHCP server sends request to server which is called
DHCP DISCOVER.
DNS: It Is the by which internet domains names are allocated and translated into IP's. It is a
hierarchical framework fro computer and other resources. Names to system are provided by
using worldwide directory service.
Routing protocols
Routing protocols describes communication of routers with each other. . A routing
protocol shares this messages first among close neighbours, and then end-to-end the
communication system. In this way , routers increase cognition of the topology of the

communication networks. Every routing protocol performs 3 type of functions which are as
follows:
Discovery : determining other available on the network.
Route management: recording all possible destinations with describing pathway of each
data packet.
Path determination: making decision on which path data will be send.
OSI model's layer number 2 manages physical connections and logical connections. These
connections are handled by using network interface card. Layer number 5 which is session layer
ensure error free data . So this model can be used in implementing network system for Beta
communication Ltd.
M 1
As per case scenario beta communication Ltd. can make its networking system by using
local are network system(LAN).It is most suitable networking system type for the company. Per
base network system should be used as it requires only single bus to transfer information form
one node to another. File transfer protocol can be used by organisation as it is making a
networking system in small premises. It also ned class C IP address which ned sub netting to
permit interaction with other departments. This sub netting will be implemented perfectly in
IPV6 internet protocol. This protocol do not requires manual configuration.
TASK 2
2.1 Role of software and hardware components
There are various software and hardware components that the Beta Communication Ltd
can adopt for their company and these are described as under :
Software components
These are considered as the section of composition with properly specified interfaces and
clear context dependencies. These components can be placed independently and are subjected for
the composition by the third parties. The Beta Communication Ltd can make use of various
software components which are discussed as under :
Network operating systems
It is a system that functions on computers and servers. Network operating systems allows
computer devices to interact and communicate on network. It is used to give support to
workstations, PC's and various other terminals that are linked to LAN (Leonardi, Huysman and
follows:
Discovery : determining other available on the network.
Route management: recording all possible destinations with describing pathway of each
data packet.
Path determination: making decision on which path data will be send.
OSI model's layer number 2 manages physical connections and logical connections. These
connections are handled by using network interface card. Layer number 5 which is session layer
ensure error free data . So this model can be used in implementing network system for Beta
communication Ltd.
M 1
As per case scenario beta communication Ltd. can make its networking system by using
local are network system(LAN).It is most suitable networking system type for the company. Per
base network system should be used as it requires only single bus to transfer information form
one node to another. File transfer protocol can be used by organisation as it is making a
networking system in small premises. It also ned class C IP address which ned sub netting to
permit interaction with other departments. This sub netting will be implemented perfectly in
IPV6 internet protocol. This protocol do not requires manual configuration.
TASK 2
2.1 Role of software and hardware components
There are various software and hardware components that the Beta Communication Ltd
can adopt for their company and these are described as under :
Software components
These are considered as the section of composition with properly specified interfaces and
clear context dependencies. These components can be placed independently and are subjected for
the composition by the third parties. The Beta Communication Ltd can make use of various
software components which are discussed as under :
Network operating systems
It is a system that functions on computers and servers. Network operating systems allows
computer devices to interact and communicate on network. It is used to give support to
workstations, PC's and various other terminals that are linked to LAN (Leonardi, Huysman and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Steinfield, 2013). It gives support to processors, internet protocol to run efficiently. NOS
provides security to data by featuring authentications. It can prove very beneficial for the Beta
Communication Ltd as they can be able to secure their data more efficiently.
(Source : Introduction to Network Operating System, 2017)
Client server operating system
This operating system facilitates networks to run servers over them. The client server
operating system is the major component of computer system as it provides security to shared
resources. Client can access information accessible on file servers. It permit several users to
share same information without concerning physical position. This can help the Beta
Communication Ltd in centralisation and proper management of all the files. Also, it can help in
up gradation and scalability in the whole set up of client and server.
Firewall
It is a software system which is used for security of data which is sent over the network.
It prevents unauthorised access to network. Network firewalls are used to restrict unauthorised
user to access interconnected networks (Brandwine and Hill, 2014). All the information which is
shared on the network passes though this software. It block the information which do not meet
the criteria defined for security. It can help the Beta Communication Ltd as it blocks the traffic
Illustration 7: Network Opearting System
provides security to data by featuring authentications. It can prove very beneficial for the Beta
Communication Ltd as they can be able to secure their data more efficiently.
(Source : Introduction to Network Operating System, 2017)
Client server operating system
This operating system facilitates networks to run servers over them. The client server
operating system is the major component of computer system as it provides security to shared
resources. Client can access information accessible on file servers. It permit several users to
share same information without concerning physical position. This can help the Beta
Communication Ltd in centralisation and proper management of all the files. Also, it can help in
up gradation and scalability in the whole set up of client and server.
Firewall
It is a software system which is used for security of data which is sent over the network.
It prevents unauthorised access to network. Network firewalls are used to restrict unauthorised
user to access interconnected networks (Brandwine and Hill, 2014). All the information which is
shared on the network passes though this software. It block the information which do not meet
the criteria defined for security. It can help the Beta Communication Ltd as it blocks the traffic
Illustration 7: Network Opearting System

and will help their data to be secured from any unauthorised bodies and safeguards it from any
hacking or attack.
There are various hardware components also which the company can use and these are described
as under :
Hardware Components
The hardware of a computer is a group of physical parts of a computer system. It is a
collection of a hardware package. Various examples are as following:
Switches
A switch is device used to connect two ports. Switch can handle more that two
communication at one time. It is device which can link data. It performs error examine error
before data transmission (Da, He and Li, 2014). It transmits the data packet which are error free.
When the data transmission is at first port it use medium access controller (MAC) to identify the
port on which the data and information is to be sent.
Bridges
This device works in data link layer. Bridge is generally an enhanced version of repeater.
It filters data by using MAC address of the source an d port at destination. Bridge is used for
interconnection of two local area networks. It only contains one input and one output. Thus it is
called two port instrument.
Hubs
It is also called multi port repeater. It connects many wires from distinct branches.
Connector in star schema is used to connect multiple stations together. This device do not filters
data due to which packets of data are forwarded to all connected computers. Hubs are not able to
determine the best path for data transmission.
Routers
It is device which is used to route data packets according to the IP address. It is a device
used for network layer in the OSI model (Jain and Paul, 2013). They are used to connect local
area network and wide area network. Routers makes routing tables to decide routing of packets.
It splits broadcasting areas of hosts which are linked to it.
Repeaters
hacking or attack.
There are various hardware components also which the company can use and these are described
as under :
Hardware Components
The hardware of a computer is a group of physical parts of a computer system. It is a
collection of a hardware package. Various examples are as following:
Switches
A switch is device used to connect two ports. Switch can handle more that two
communication at one time. It is device which can link data. It performs error examine error
before data transmission (Da, He and Li, 2014). It transmits the data packet which are error free.
When the data transmission is at first port it use medium access controller (MAC) to identify the
port on which the data and information is to be sent.
Bridges
This device works in data link layer. Bridge is generally an enhanced version of repeater.
It filters data by using MAC address of the source an d port at destination. Bridge is used for
interconnection of two local area networks. It only contains one input and one output. Thus it is
called two port instrument.
Hubs
It is also called multi port repeater. It connects many wires from distinct branches.
Connector in star schema is used to connect multiple stations together. This device do not filters
data due to which packets of data are forwarded to all connected computers. Hubs are not able to
determine the best path for data transmission.
Routers
It is device which is used to route data packets according to the IP address. It is a device
used for network layer in the OSI model (Jain and Paul, 2013). They are used to connect local
area network and wide area network. Routers makes routing tables to decide routing of packets.
It splits broadcasting areas of hosts which are linked to it.
Repeaters

This device works at physical layer of OSI model. Repeater is two port component. Role
of repeaters is to generate signals before the signal gets corrupted. They widens length of the
weak signal. Repeater do not amplifies signal. When signal get corrupted the make the copy of it
and regenerate it.
These components can help the Beta Communication Ltd in producing a faster boot up time and
becoming no or less prone to any type of failure, data loss or any related issues. These will help
the company in achieving the targets at a faster rate.
2.2 Types of servers
Server is termed as a programs which helps in proper functioning of other programs
which are termed as clients. There are mail four types of servers which can be use in designing
of network of Beta communication Ltd. Types and requirement of them is as follows: Mail servers: These servers are present almost everywhere in all networking systems.
These servers sends, receives and stores mails over local and wide are networks. Web servers: This server is used for hosting websites. They serves web browser for
running websites efficiently. It loads webpage for the internet and displays it on browser.
The entire transferring of data is intermediate by browser and server by communicating
through HTTP. FTP servers: It is used to serve files over the network. This is done by making use of file
transfer protocol. This server shares files between two or more computers. This server
ensures data integrity and security. This server is use commonly used in web servers. It
allows users to transfer , change and delete files form web using file transfer protocol
clients. Application server: This server controls all application between client and server.
Application server is also referred as middle ware. They contain large clump of
computing region between database server and end client. Proxy servers: This server is used to make link between browser and external server to
provide result of user query. This server is responsible for making connection between
client and external server to respond to request for connection and making enhancement
in performance. Telnet servers: It help users to sign on onto host PC and perform task like they doing on
remote computers.
of repeaters is to generate signals before the signal gets corrupted. They widens length of the
weak signal. Repeater do not amplifies signal. When signal get corrupted the make the copy of it
and regenerate it.
These components can help the Beta Communication Ltd in producing a faster boot up time and
becoming no or less prone to any type of failure, data loss or any related issues. These will help
the company in achieving the targets at a faster rate.
2.2 Types of servers
Server is termed as a programs which helps in proper functioning of other programs
which are termed as clients. There are mail four types of servers which can be use in designing
of network of Beta communication Ltd. Types and requirement of them is as follows: Mail servers: These servers are present almost everywhere in all networking systems.
These servers sends, receives and stores mails over local and wide are networks. Web servers: This server is used for hosting websites. They serves web browser for
running websites efficiently. It loads webpage for the internet and displays it on browser.
The entire transferring of data is intermediate by browser and server by communicating
through HTTP. FTP servers: It is used to serve files over the network. This is done by making use of file
transfer protocol. This server shares files between two or more computers. This server
ensures data integrity and security. This server is use commonly used in web servers. It
allows users to transfer , change and delete files form web using file transfer protocol
clients. Application server: This server controls all application between client and server.
Application server is also referred as middle ware. They contain large clump of
computing region between database server and end client. Proxy servers: This server is used to make link between browser and external server to
provide result of user query. This server is responsible for making connection between
client and external server to respond to request for connection and making enhancement
in performance. Telnet servers: It help users to sign on onto host PC and perform task like they doing on
remote computers.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Real time communication servers: These servers are used for instant messaging. It
enable users to share information instantly.
Virtual server: These servers enable cloud computing and help in sharing data over the
cloud.
2.3 Interdependence of workstation hardware
Workstations that should be used in network designing of Beta communication Ltd. is as
follows:
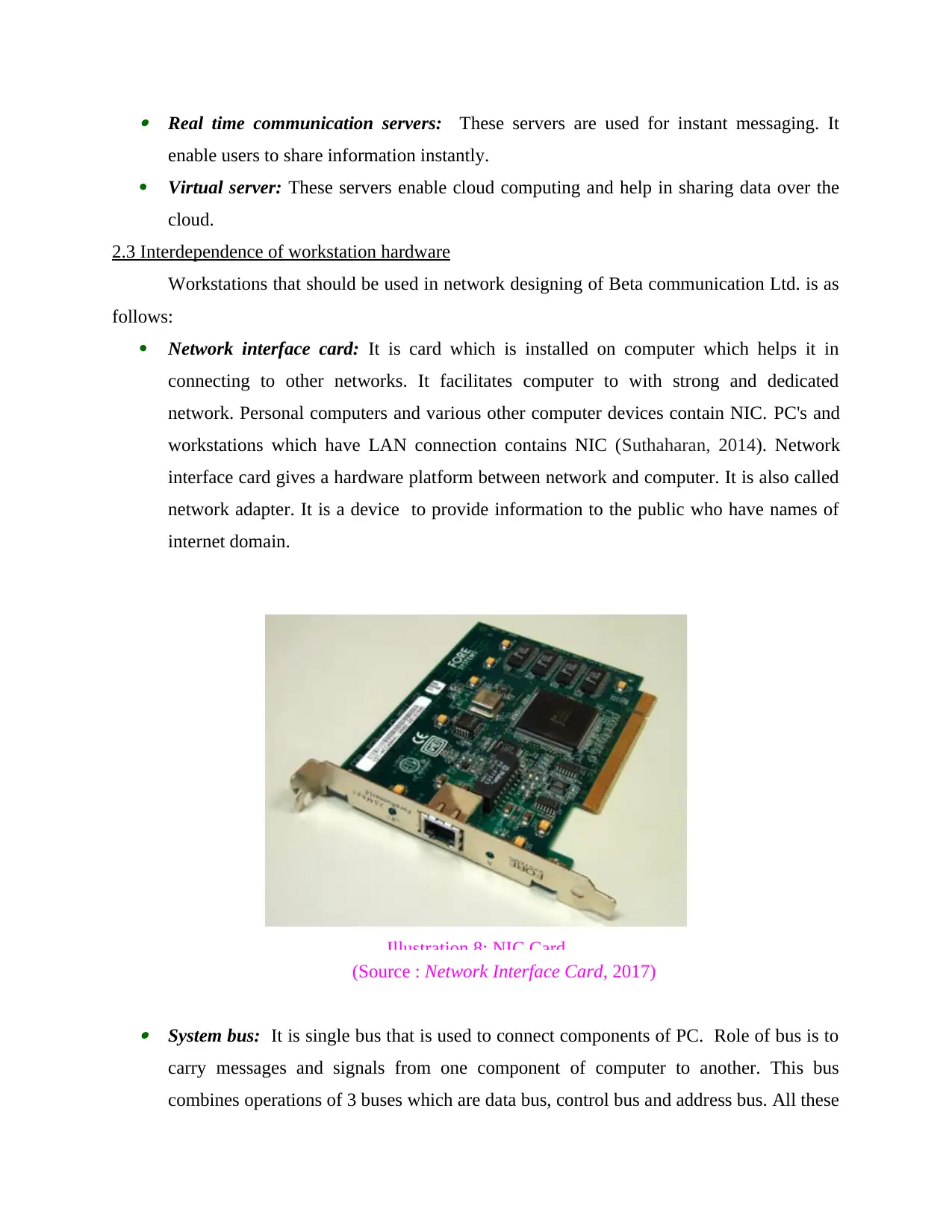
Network interface card: It is card which is installed on computer which helps it in
connecting to other networks. It facilitates computer to with strong and dedicated
network. Personal computers and various other computer devices contain NIC. PC's and
workstations which have LAN connection contains NIC (Suthaharan, 2014). Network
interface card gives a hardware platform between network and computer. It is also called
network adapter. It is a device to provide information to the public who have names of
internet domain.
(Source : Network Interface Card, 2017)
System bus: It is single bus that is used to connect components of PC. Role of bus is to
carry messages and signals from one component of computer to another. This bus
combines operations of 3 buses which are data bus, control bus and address bus. All these
Illustration 8: NIC Card
enable users to share information instantly.
Virtual server: These servers enable cloud computing and help in sharing data over the
cloud.
2.3 Interdependence of workstation hardware
Workstations that should be used in network designing of Beta communication Ltd. is as
follows:
Network interface card: It is card which is installed on computer which helps it in
connecting to other networks. It facilitates computer to with strong and dedicated
network. Personal computers and various other computer devices contain NIC. PC's and
workstations which have LAN connection contains NIC (Suthaharan, 2014). Network
interface card gives a hardware platform between network and computer. It is also called
network adapter. It is a device to provide information to the public who have names of
internet domain.
(Source : Network Interface Card, 2017)
System bus: It is single bus that is used to connect components of PC. Role of bus is to
carry messages and signals from one component of computer to another. This bus
combines operations of 3 buses which are data bus, control bus and address bus. All these
Illustration 8: NIC Card

buses contains distinct characteristics. Characteristics of system bus depends upon
requirement of processor (Christensen, 2013). Design of this bus is based on particular
processor's technology. Size of system bus is termed as width. This width also determines
amount of data that can be transmitted over wires. Mother boards speed is affected by this
bus. I/O devices: Input output devices in computer networking includes cables , wires, CD
ROM etc. that are used to transfer data to other computers. These are hardware
components which are required for communication between computers (Vinel and et.al ,
2016). Example of I/O devices are floppy disk, hard drive, USB's modem, SD card. Wireless NIC : It is a network interface controller which makes connection with wireless
radio that is based on computer network. Wireless NIC is same as NIC which works on
layer 1 and layer 2 of open system interconnection model. WNIC connects using PCI bus
in desktop computer. Fast Ethernet: It is also a local area network standard for transmitting data. It provides a
data rate of 100 mbps. Workstations of Ethernet are 10 mbps. Ethernet card can be linked
to fast Ethernet.
Gigabyte Ethernet : Gigabyte Ethernet is a technology for transmission which is based
on frame of Ethernet and local area network protocol. It provides data rate of 1 billion per
second.
M 2
Role of hardware and software component is significant in computer networking system.
These components provides effective communication between nodes. Switches , router, bridges
are some device that helps in transmission of data and information. Client server operating
system can be sued by Beta communication for transferring their information within the
organisation. Firewall software is necessary in each computer device to restrict unauthorised
access. FTP server and application server can be used while designing networking system of the
company. Network interface card provides information to the public who have names of internet
domain. Role of system bus is to carry information and signals from one component of computer
to another. Network interface card gives a hardware platform between network and computer. It
is also called network adapter. It is a device to provide information to the public who have
names of internet domain.
requirement of processor (Christensen, 2013). Design of this bus is based on particular
processor's technology. Size of system bus is termed as width. This width also determines
amount of data that can be transmitted over wires. Mother boards speed is affected by this
bus. I/O devices: Input output devices in computer networking includes cables , wires, CD
ROM etc. that are used to transfer data to other computers. These are hardware
components which are required for communication between computers (Vinel and et.al ,
2016). Example of I/O devices are floppy disk, hard drive, USB's modem, SD card. Wireless NIC : It is a network interface controller which makes connection with wireless
radio that is based on computer network. Wireless NIC is same as NIC which works on
layer 1 and layer 2 of open system interconnection model. WNIC connects using PCI bus
in desktop computer. Fast Ethernet: It is also a local area network standard for transmitting data. It provides a
data rate of 100 mbps. Workstations of Ethernet are 10 mbps. Ethernet card can be linked
to fast Ethernet.
Gigabyte Ethernet : Gigabyte Ethernet is a technology for transmission which is based
on frame of Ethernet and local area network protocol. It provides data rate of 1 billion per
second.
M 2
Role of hardware and software component is significant in computer networking system.
These components provides effective communication between nodes. Switches , router, bridges
are some device that helps in transmission of data and information. Client server operating
system can be sued by Beta communication for transferring their information within the
organisation. Firewall software is necessary in each computer device to restrict unauthorised
access. FTP server and application server can be used while designing networking system of the
company. Network interface card provides information to the public who have names of internet
domain. Role of system bus is to carry information and signals from one component of computer
to another. Network interface card gives a hardware platform between network and computer. It
is also called network adapter. It is a device to provide information to the public who have
names of internet domain.

Networking Technologies
Student's Name:
Instructor's Name:
Date:
19
Student's Name:
Instructor's Name:
Date:
19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TASK 3
A primitive LAN layout for Beta Communications network requirement would be as follows:
With the help of this network architecture, Beta Communication will not have any problems exp
anding to remote locations too. The Building backbone can be broken into smaller segments. Acc
ording to current business functionalities, Beta Communications has broken down tasks to three
different buildings. It would be ideal to carry all important resources in a single building and cha
nnel to the other buildings. Ideally, the building (C) with the network infrastructure manager and
technical teams should act as the central block. Servers, hardware resources and software solutio
ns must be deployed at this building (C). Employees located in the other buildings can accept dat
a from building (C). Such an architecture will make sure Beta Communication performs all its op
erations in a secure and resilient manner.
20
A primitive LAN layout for Beta Communications network requirement would be as follows:
With the help of this network architecture, Beta Communication will not have any problems exp
anding to remote locations too. The Building backbone can be broken into smaller segments. Acc
ording to current business functionalities, Beta Communications has broken down tasks to three
different buildings. It would be ideal to carry all important resources in a single building and cha
nnel to the other buildings. Ideally, the building (C) with the network infrastructure manager and
technical teams should act as the central block. Servers, hardware resources and software solutio
ns must be deployed at this building (C). Employees located in the other buildings can accept dat
a from building (C). Such an architecture will make sure Beta Communication performs all its op
erations in a secure and resilient manner.
20

Building (C) that acts as the core should be further broken into several segments. With proper br
anching, individual modules can be accessed and maintained without compromising on the overa
ll quality of the network. The network at building C should have multiple distribution switches.
Connection between building A, B and C can be established using access layer switches. These s
witches can be spread across different buildings, irrespective of their location. The switches are c
onnected using Ethernet cables. The Ethernet cables are responsible for transferring data from on
e location to another. Ethernet cabling will be useful when Beta Communication wants to expand
. The cables are known for its high performance and reliable nature. They can handle huge perfor
mance goals without any problems. That means, Beta Communication can attach many more nod
es and not worry about speed, response rate, turnaround time or safety. Ethernet cabling promise
s high bandwidth for Beta Communication. There are special, fine-tuned protocols at Ethernet ca
bling level to ensure data communication happens without any compromises. For instance, Beta
Communication can use 10-Gigabit uplink connectivity. This technique makes sure performance
and flexibility is achieved. Ethernet cabling and protocols form a part of Layer 2.
Benefits of using this multiple distribution layer architecture:
1) Nodes will be connected in a structured fashion.
2) It will be easier to find and remove faulty nodes.
21
anching, individual modules can be accessed and maintained without compromising on the overa
ll quality of the network. The network at building C should have multiple distribution switches.
Connection between building A, B and C can be established using access layer switches. These s
witches can be spread across different buildings, irrespective of their location. The switches are c
onnected using Ethernet cables. The Ethernet cables are responsible for transferring data from on
e location to another. Ethernet cabling will be useful when Beta Communication wants to expand
. The cables are known for its high performance and reliable nature. They can handle huge perfor
mance goals without any problems. That means, Beta Communication can attach many more nod
es and not worry about speed, response rate, turnaround time or safety. Ethernet cabling promise
s high bandwidth for Beta Communication. There are special, fine-tuned protocols at Ethernet ca
bling level to ensure data communication happens without any compromises. For instance, Beta
Communication can use 10-Gigabit uplink connectivity. This technique makes sure performance
and flexibility is achieved. Ethernet cabling and protocols form a part of Layer 2.
Benefits of using this multiple distribution layer architecture:
1) Nodes will be connected in a structured fashion.
2) It will be easier to find and remove faulty nodes.
21

3) It will be easier to maintain the overall network, without compromising on performance.
4) It will be easier to add new nodes to the overall system.
Designing the Distribution Layer
The distribution layer is responsible for aggregating all the access layer switches. It is necessary t
o design the overall architecture of the distribution layer, before developing the access layer. The
distribution layer works across the three buildings. It is a medium to connect the access layer swi
tches. According to the proposed problem statement, Beta Communication functions across three
different buildings. The distribution layer is responsible for connecting all access layer switches t
hat are present in a particular building. Later, the distribution layers can be connected together. T
he distribution layer plays an integral role in this design. It acts as a boundary between layer 2 an
d 3 protocols.
Layer 2 is responsible for handling the spanning tree protocols. These protocols are necessary to
identify the route each packet in the network would take. The spanning tree protocols make sure
packets take the shortest and best possible route. There are several different types of spanning tre
e protocols. Beta Communication has a network that is restricted to three buildings that are closel
y located. A simple spanning tree protocol will be sufficient to ensure quick and reliable commu
nication. Moving on, the spanning tree protocolhandles all faults in layer 2.
22
4) It will be easier to add new nodes to the overall system.
Designing the Distribution Layer
The distribution layer is responsible for aggregating all the access layer switches. It is necessary t
o design the overall architecture of the distribution layer, before developing the access layer. The
distribution layer works across the three buildings. It is a medium to connect the access layer swi
tches. According to the proposed problem statement, Beta Communication functions across three
different buildings. The distribution layer is responsible for connecting all access layer switches t
hat are present in a particular building. Later, the distribution layers can be connected together. T
he distribution layer plays an integral role in this design. It acts as a boundary between layer 2 an
d 3 protocols.
Layer 2 is responsible for handling the spanning tree protocols. These protocols are necessary to
identify the route each packet in the network would take. The spanning tree protocols make sure
packets take the shortest and best possible route. There are several different types of spanning tre
e protocols. Beta Communication has a network that is restricted to three buildings that are closel
y located. A simple spanning tree protocol will be sufficient to ensure quick and reliable commu
nication. Moving on, the spanning tree protocolhandles all faults in layer 2.
22
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Layer 3 is responsible for holding information about the IP routing tables. The proposed network
design needs very few IP routing tables. These tables make sure packets are sent to the right netw
ork gateway. With fewer number of routing tables, the process of troubleshooting errors and reco
vering from faults becomes easier. The IP tables carry information about sources and potential de
stinations. Packets transferred from one building to another should go through the routing tables i
n Layer 3.
Designing the Access Layer
Once the multiple distribution layer is established, the individual access layers for each building
should be designed. The access layer can be deployed independently in each building. The access
layer can be independent from one another. Independent access layer switches help in maintainin
g consistency and a stable network. Anyone who has access to these switches will be able to tran
sfer and receive data. Conversely, the access layer switches can be protected using power firewal
ls. These firewalls can be configured from a single interface that is maintained in Building C – th
e core! Access layer switches are responsible for connecting network hardware devices. It acts as
an interface that allows various devices like standalone computers, IP phones and wireless access
points to be connected. However, access layer switches are destined to function in a specific buil
ding. Access layer switches in each building can be connected together. This forms a complete L
AN network for Beta Communications.
23
design needs very few IP routing tables. These tables make sure packets are sent to the right netw
ork gateway. With fewer number of routing tables, the process of troubleshooting errors and reco
vering from faults becomes easier. The IP tables carry information about sources and potential de
stinations. Packets transferred from one building to another should go through the routing tables i
n Layer 3.
Designing the Access Layer
Once the multiple distribution layer is established, the individual access layers for each building
should be designed. The access layer can be deployed independently in each building. The access
layer can be independent from one another. Independent access layer switches help in maintainin
g consistency and a stable network. Anyone who has access to these switches will be able to tran
sfer and receive data. Conversely, the access layer switches can be protected using power firewal
ls. These firewalls can be configured from a single interface that is maintained in Building C – th
e core! Access layer switches are responsible for connecting network hardware devices. It acts as
an interface that allows various devices like standalone computers, IP phones and wireless access
points to be connected. However, access layer switches are destined to function in a specific buil
ding. Access layer switches in each building can be connected together. This forms a complete L
AN network for Beta Communications.
23

Design Stages
To implement this LAN network, Beta communication should follow these stages:
1) The platform over which the network would be established has to be configured.
2) The LAN switches (both distribution layer and access layer switches) should be configure
d. These switches should be configured with universal settings.
3) Wires that flow between the buildings should be configured. These wires should be config
ured in line with the universal settings. The wires are important, since they transfer and re
ceive data! All firewall settings are dependent on the way these wires are configured.
4) The unicast routing protocols should be configured.
5) The multicast routing protocols should be configured.
6) The distribution layer should be configured.
7) The access layer switches in each building should be configured.
8) The access layer switches in each building should be connected together.
9) The connected access layer switches should be linked to the distribution layer.
10) The WAN router for this network should be configured and shared across the LAN core.
11) Firewall configuration has to be done to ensure safe and secure communication between
buildings.
24
To implement this LAN network, Beta communication should follow these stages:
1) The platform over which the network would be established has to be configured.
2) The LAN switches (both distribution layer and access layer switches) should be configure
d. These switches should be configured with universal settings.
3) Wires that flow between the buildings should be configured. These wires should be config
ured in line with the universal settings. The wires are important, since they transfer and re
ceive data! All firewall settings are dependent on the way these wires are configured.
4) The unicast routing protocols should be configured.
5) The multicast routing protocols should be configured.
6) The distribution layer should be configured.
7) The access layer switches in each building should be configured.
8) The access layer switches in each building should be connected together.
9) The connected access layer switches should be linked to the distribution layer.
10) The WAN router for this network should be configured and shared across the LAN core.
11) Firewall configuration has to be done to ensure safe and secure communication between
buildings.
24

12) Users should be registered and appropriate username & passwords should be generated.
Routing in the Beta Communication Network
In Beta Communication, a switch is used to connect two or more devices. It is necessary for exch
ange of information or data within the connected systems. The switches are then linked to the rou
ter. The router is responsible for positioning and direction of web traffic. The router configuratio
n of Beta Communication will be as follows:
1) Navigate to Network Configuration, and click on “LAN setup”
2) Enter the IP address of the router
3) Enter the Domain name of the router
4) The starting and ending IP addresses are mentioned. For example, subnet 1 has a host rang
e between 200.168.0.1 – 200.168.0.14. Routers that handle traffic in this subnet will be as
signed the previous range. Likewise, Routers in subnet 2 will manage a host range of 200.
168.0.17 to 200.168.0.30. According to current design, here is a table to show how the cla
ss range will be for each router.
Router – subnet id Host Range
25
Routing in the Beta Communication Network
In Beta Communication, a switch is used to connect two or more devices. It is necessary for exch
ange of information or data within the connected systems. The switches are then linked to the rou
ter. The router is responsible for positioning and direction of web traffic. The router configuratio
n of Beta Communication will be as follows:
1) Navigate to Network Configuration, and click on “LAN setup”
2) Enter the IP address of the router
3) Enter the Domain name of the router
4) The starting and ending IP addresses are mentioned. For example, subnet 1 has a host rang
e between 200.168.0.1 – 200.168.0.14. Routers that handle traffic in this subnet will be as
signed the previous range. Likewise, Routers in subnet 2 will manage a host range of 200.
168.0.17 to 200.168.0.30. According to current design, here is a table to show how the cla
ss range will be for each router.
Router – subnet id Host Range
25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Router in subnet 1 200.168.0.1 – 200.168.0.14
Router in subnet 2 200.168.0.17 – 200.168.0.30
Router in subnet 3 200.168.0.33 – 200.168.0.46
Router in subnet 4 200.168.0.49 – 200.168.0.50
Router in subnet 5 200.168.0.53 – 200.168.0.54
Router in subnet 6 200.168.0.57 – 200.168.0.58
5) A Lease time is generated for clients
6) A DNS Proxy is enabled for the clients
7) Once the above steps are completed, the LAN router settings are saved.
Data Center Core Router Devices
Currently, Beta Communication is focusing on three separate buildings. Network managers at Be
ta communication build data center networks with separate core router pairs. These routers are co
nnected to external networks and user access networks through firewalls. By choosing a separate
26
Router in subnet 2 200.168.0.17 – 200.168.0.30
Router in subnet 3 200.168.0.33 – 200.168.0.46
Router in subnet 4 200.168.0.49 – 200.168.0.50
Router in subnet 5 200.168.0.53 – 200.168.0.54
Router in subnet 6 200.168.0.57 – 200.168.0.58
5) A Lease time is generated for clients
6) A DNS Proxy is enabled for the clients
7) Once the above steps are completed, the LAN router settings are saved.
Data Center Core Router Devices
Currently, Beta Communication is focusing on three separate buildings. Network managers at Be
ta communication build data center networks with separate core router pairs. These routers are co
nnected to external networks and user access networks through firewalls. By choosing a separate
26

router, operational and capital expenses will be high, but the final network will be extremely effi
cient.
The routers are a part of Layer 3 component. Routing between subnets ensures high data security
.
TASK 4
4.1 – Implement a network systems based on the proposed design. You are required to use means
of simulation software, establish a network according to the design in task 3
# To be able to use nam, we should Create a nam trace datafile. set namfile [open results/
versuch1.nam w]
$ns namtrace-all $namfile
# After that, we should create the nodes
{ set node($i) [$ns node]}
27
cient.
The routers are a part of Layer 3 component. Routing between subnets ensures high data security
.
TASK 4
4.1 – Implement a network systems based on the proposed design. You are required to use means
of simulation software, establish a network according to the design in task 3
# To be able to use nam, we should Create a nam trace datafile. set namfile [open results/
versuch1.nam w]
$ns namtrace-all $namfile
# After that, we should create the nodes
{ set node($i) [$ns node]}
27

$ns run
# After that, we should connect the nodes with each other
$ns duplex-link $node(0) $node(1) 1.0Mb 20.0ms DropTail
$ns duplex-link $node(0) $node(2) 1.0Mb 20.0ms DropTail
$ns duplex-link $node(1) $node(2) 1.0Mb 20.0ms DropTail
$ns run
# After that, we have to create the
Connection for one of the Core nodes in the building
$agents set agent(0) [new Agent/UDP]
$ns attach-agent $node(1) $agent(0)
$agent(0) set fid_ 6
$ns color 6 "red„
set sink(0) [new Agent/Null]
$ns attach-agent $node(1) $sink(0)
28
# After that, we should connect the nodes with each other
$ns duplex-link $node(0) $node(1) 1.0Mb 20.0ms DropTail
$ns duplex-link $node(0) $node(2) 1.0Mb 20.0ms DropTail
$ns duplex-link $node(1) $node(2) 1.0Mb 20.0ms DropTail
$ns run
# After that, we have to create the
Connection for one of the Core nodes in the building
$agents set agent(0) [new Agent/UDP]
$ns attach-agent $node(1) $agent(0)
$agent(0) set fid_ 6
$ns color 6 "red„
set sink(0) [new Agent/Null]
$ns attach-agent $node(1) $sink(0)
28
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

$ns connect $agent(0) $sink(0)
# After that, we have to create traffic source and add it to the
agent set traffic_source(0) [new Application/Traffic/CBR]
$traffic_source(0) set interval_ 0.001950
$traffic_source(0) set paketSize_ 230
$traffic_source(0) attach-agent $agent(0)
# Now, we have to schedule starting and stopping the traffic source
$ns at 3.0 "$traffic_source(0) start„
$ns at 100.0 "$traffic_source(0) stop„
29
# After that, we have to create traffic source and add it to the
agent set traffic_source(0) [new Application/Traffic/CBR]
$traffic_source(0) set interval_ 0.001950
$traffic_source(0) set paketSize_ 230
$traffic_source(0) attach-agent $agent(0)
# Now, we have to schedule starting and stopping the traffic source
$ns at 3.0 "$traffic_source(0) start„
$ns at 100.0 "$traffic_source(0) stop„
29

# Now, we have to start the finish
procedure proc finish {} {
global ns namfile $ns flush-trace close $namfile
exec nam results/versuch1.nam & exit 0
}
# After that, we have to schedule the stop
procedure $ns at 110.000000 "finish"
To Handle Mobility Between Nodes
30
procedure proc finish {} {
global ns namfile $ns flush-trace close $namfile
exec nam results/versuch1.nam & exit 0
}
# After that, we have to schedule the stop
procedure $ns at 110.000000 "finish"
To Handle Mobility Between Nodes
30

# Create simulator instance
set ns_ [new Simulator]
# Create nam and trace files
set tracefd [open out.tr w]
set namtrace [open out.nam w]
$ns_ trace-all $tracefd
$ns_ namtrace-all-wireless $namtrace $opt(x) $opt(y)
# Create a file to record the lost packets for UDP
31
set ns_ [new Simulator]
# Create nam and trace files
set tracefd [open out.tr w]
set namtrace [open out.nam w]
$ns_ trace-all $tracefd
$ns_ namtrace-all-wireless $namtrace $opt(x) $opt(y)
# Create a file to record the lost packets for UDP
31
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

set LostPackets [open UDPlost.tr w]
Set up the hierarchical routing
$ns_ node-config -addressType hierarchical
AddrParams set domain_num_ 7 lappend
cluster_num 1 1 1 1 1 1 1 AddrParams
set cluster_num_ $cluster_numlappendeilastlevel 2 2 1 1 1 1 1 AddrParams
set nodes_num_ $eilastlevel
32
Set up the hierarchical routing
$ns_ node-config -addressType hierarchical
AddrParams set domain_num_ 7 lappend
cluster_num 1 1 1 1 1 1 1 AddrParams
set cluster_num_ $cluster_numlappendeilastlevel 2 2 1 1 1 1 1 AddrParams
set nodes_num_ $eilastlevel
32

4.2. Test network systems to meet user requirements. Your testing includes functionality of the n
etwork to ensure that your developed network will operate seamlessly in a physical environ
ment so that it can satisfy user requirements.
The LAN solution for Beta Communication has to be tested. Network testing revolves around pa
rameters like performance, security, reliability, scalability and flexibility. Here are few ways the
proposed solution can be tested:
1) The proposed LAN solution should ensure high performance. Regardless of the number of
employees connected or the number of devices accessing information, it should be up and
running. The network should not compromise on network speed or availability. By definit
ion, network availability is the power to access data from a network at all times!
2) Security plays an important role in any network. Here, data access should be governed by
user privileges. Only authorized users should be allowed to access or modify data. Also, f
irewalls should define the flow of information from one building to another.
3) The proposed Beta Communication network should be reliable at all levels. It should ensur
e authorized data access and availability.
4) Scalability is a long term test parameter. The company shouldn’t have any issues expandin
g the network at any time! It should be able to add new devices and workstations without
compromising on performance.
Test Scenarios:
33
etwork to ensure that your developed network will operate seamlessly in a physical environ
ment so that it can satisfy user requirements.
The LAN solution for Beta Communication has to be tested. Network testing revolves around pa
rameters like performance, security, reliability, scalability and flexibility. Here are few ways the
proposed solution can be tested:
1) The proposed LAN solution should ensure high performance. Regardless of the number of
employees connected or the number of devices accessing information, it should be up and
running. The network should not compromise on network speed or availability. By definit
ion, network availability is the power to access data from a network at all times!
2) Security plays an important role in any network. Here, data access should be governed by
user privileges. Only authorized users should be allowed to access or modify data. Also, f
irewalls should define the flow of information from one building to another.
3) The proposed Beta Communication network should be reliable at all levels. It should ensur
e authorized data access and availability.
4) Scalability is a long term test parameter. The company shouldn’t have any issues expandin
g the network at any time! It should be able to add new devices and workstations without
compromising on performance.
Test Scenarios:
33

1) Ping Building A from Building B and Building C. The ping should be successful. The time
to receive a response should remain consistent. The bandwidth should be high and reliabl
e at all times.
2) Transfer files from Building A to Building B. The file should be transferred at steady spee
d.
3) To ensure availability, an access layer switch should be unplugged. The network infrastruc
ture manager should ping a device attached to the unplugged access layer switch. Incomi
ng traffic should be noted.
4) Filters and rules should be applied at different access layer switches. When data packets fl
ow, traffic across these access layer switches should be noted.
5) Beta communication focuses on subnet wise access. Users at each subnet can have differe
nt rules and regulations. Devices in each subnet should be accessed individually. Normal
and abnormal rules should be applied during the access.
6) There are special software programs to control and generate traffic at each workstation. Th
e traffic generator helps in understanding the reliability and availability of each workstati
on at different traffic levels.
7) Firewalls can be tested using authorized and unauthorized device access.
34
to receive a response should remain consistent. The bandwidth should be high and reliabl
e at all times.
2) Transfer files from Building A to Building B. The file should be transferred at steady spee
d.
3) To ensure availability, an access layer switch should be unplugged. The network infrastruc
ture manager should ping a device attached to the unplugged access layer switch. Incomi
ng traffic should be noted.
4) Filters and rules should be applied at different access layer switches. When data packets fl
ow, traffic across these access layer switches should be noted.
5) Beta communication focuses on subnet wise access. Users at each subnet can have differe
nt rules and regulations. Devices in each subnet should be accessed individually. Normal
and abnormal rules should be applied during the access.
6) There are special software programs to control and generate traffic at each workstation. Th
e traffic generator helps in understanding the reliability and availability of each workstati
on at different traffic levels.
7) Firewalls can be tested using authorized and unauthorized device access.
34
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4.3. Document and analyse test result against expected results. While carrying out task 4.2, the te
sting of the network has produced a number of results. List the results you have found in ta
sk 4.2 by contrasting them with your expected results.
A potential test result for the tested LAN is as follows:
The three different colors represent building A, building B and building C. Data access at differe
nt bandwidths and extreme network conditions are analyzed. Throughout the test, the LAN netw
ork showed consisted results.
35
sting of the network has produced a number of results. List the results you have found in ta
sk 4.2 by contrasting them with your expected results.
A potential test result for the tested LAN is as follows:
The three different colors represent building A, building B and building C. Data access at differe
nt bandwidths and extreme network conditions are analyzed. Throughout the test, the LAN netw
ork showed consisted results.
35

4.4. Recommend potential enhancement for the networked systems. Your discussions should incl
ude how your developed network will cope with future changing needs and should address
possible enhancements of your network to satisfy needs of changing future environment.
Scalability is an important feature in this network design. Beta Communication has the fr
eedom to expand its network without much issues. That is because the proposed design follows a
modular structure. Any required changes can be introduced into the system easily. Here are few
scenarios where the network design has to be improved or scaled:
1) The current network design revolves around LAN infrastructure. The company can upgrad
e to wireless LAN. This will remove the need for expensive wiring. Also, users can acces
s the machines from remote locations using authorized credentials. The wireless LAN en
vironment represents a sophisticated network design.
2) The present servers are meant to handle the current population of Beta Communication. In
the long run, the company can upgrade its server configuration. It can install power server
s to ensure higher and better performance. Also, it doesn’t have to worry about the speed
at which functionalities are carried out.
3) Network infrastructure manager can propose the use of virtual servers. These servers are c
heaper than actual devices. Virtualization can improve the rate at which the company scal
es. It can test different environments and identify configurations that best suit its needs.
4) If Beta Communication has plans of creating new branches in different destinations, it sho
uld adopt to WAN. Luckily, the proposed network has already taken WAN into considera
tion. That means, it will not have any problem migrating to WAN.
36
ude how your developed network will cope with future changing needs and should address
possible enhancements of your network to satisfy needs of changing future environment.
Scalability is an important feature in this network design. Beta Communication has the fr
eedom to expand its network without much issues. That is because the proposed design follows a
modular structure. Any required changes can be introduced into the system easily. Here are few
scenarios where the network design has to be improved or scaled:
1) The current network design revolves around LAN infrastructure. The company can upgrad
e to wireless LAN. This will remove the need for expensive wiring. Also, users can acces
s the machines from remote locations using authorized credentials. The wireless LAN en
vironment represents a sophisticated network design.
2) The present servers are meant to handle the current population of Beta Communication. In
the long run, the company can upgrade its server configuration. It can install power server
s to ensure higher and better performance. Also, it doesn’t have to worry about the speed
at which functionalities are carried out.
3) Network infrastructure manager can propose the use of virtual servers. These servers are c
heaper than actual devices. Virtualization can improve the rate at which the company scal
es. It can test different environments and identify configurations that best suit its needs.
4) If Beta Communication has plans of creating new branches in different destinations, it sho
uld adopt to WAN. Luckily, the proposed network has already taken WAN into considera
tion. That means, it will not have any problem migrating to WAN.
36

5) If required, the company can invest on cloud infrastructure too. Cloud will help the compa
ny reduce most of its hardware and software costs.
4.5. Design a maintenance schedule to support the network system. Your maintenance schedule s
hould address various factors likepersonnel allocation, backup and recovery policy, mainta
ining security & integrity; and general administration to support the users.
Big or small, any network requires prompt maintenance. Maintenance will make sure the networ
k lasts longer and doesn’t compromise on performance. Network maintenance will also reduce th
e risks of downtime. However, Beta Communication should plan its maintenance routines. It sho
uld not affect normal functionalities of the company.
Here are few important maintenance routines Beta Communication should follow:
1) Every employee should take time and maintain their individual workstations. They should
take periodic backups of data. Meanwhile, the network infrastructure manager should rev
iew disk usage. They should make sure disk usage is limited and not overloaded at any w
orkstation. If required, additional disk space should be provided. Service packs must be in
stalled in each workstation when required. Workstations should be protected using antivir
us programs too.
2) Network maintenance is one of the primitive tasks of the network infrastructure manager.
To begin with, the manager should maintain a document will all network devices (switch
es, routers and gateways). The NIM should update device configuration when required. A
dditionally, firewalls should be updated whenever required! Network maintenance should
happen periodically and it should be a planned activity.
37
ny reduce most of its hardware and software costs.
4.5. Design a maintenance schedule to support the network system. Your maintenance schedule s
hould address various factors likepersonnel allocation, backup and recovery policy, mainta
ining security & integrity; and general administration to support the users.
Big or small, any network requires prompt maintenance. Maintenance will make sure the networ
k lasts longer and doesn’t compromise on performance. Network maintenance will also reduce th
e risks of downtime. However, Beta Communication should plan its maintenance routines. It sho
uld not affect normal functionalities of the company.
Here are few important maintenance routines Beta Communication should follow:
1) Every employee should take time and maintain their individual workstations. They should
take periodic backups of data. Meanwhile, the network infrastructure manager should rev
iew disk usage. They should make sure disk usage is limited and not overloaded at any w
orkstation. If required, additional disk space should be provided. Service packs must be in
stalled in each workstation when required. Workstations should be protected using antivir
us programs too.
2) Network maintenance is one of the primitive tasks of the network infrastructure manager.
To begin with, the manager should maintain a document will all network devices (switch
es, routers and gateways). The NIM should update device configuration when required. A
dditionally, firewalls should be updated whenever required! Network maintenance should
happen periodically and it should be a planned activity.
37
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3) Server maintenance doesn’t have to happen periodically. However, it should not be neglec
ted. All logs should be stored for future reference. If required service pack updates should
be done with hotfix installations!
CONCLUSION
Summing up the above report it can be concluded that networking styles and networking
topology should be chosen according to the requirement of organisation. There are various
benefits of networking system which supports in effective communication. File transfer protocol
and simple mail transfer protocol support in effective transferring of mail and file over nodes.
Network interface card provides information to the public who have names of internet domain.
Right NIC should be chosen for smooth connection with other networks.
38
ted. All logs should be stored for future reference. If required service pack updates should
be done with hotfix installations!
CONCLUSION
Summing up the above report it can be concluded that networking styles and networking
topology should be chosen according to the requirement of organisation. There are various
benefits of networking system which supports in effective communication. File transfer protocol
and simple mail transfer protocol support in effective transferring of mail and file over nodes.
Network interface card provides information to the public who have names of internet domain.
Right NIC should be chosen for smooth connection with other networks.
38

REFERENCES
Books and journals
Brandwine, E.J. and Hill, P.J., 2014.Providing virtual networking functionality for managed
computer networks. U.S. Patent 8,644,188.
Christensen, C.M., 2013.The innovator's dilemma: when new technologies cause great firms to
fail. Harvard Business Review Press.
Da Xu, L., He, W. and Li, S., 2014. Internet of things in industries: A survey.IEEE Transactions
on industrial informatics. 10(4). pp.2233-2243.
Gubbi, J. and et.al ,2013. Internet of Things (IoT): A vision, architectural elements, and future
directions.Future generation computer systems. 29(7). pp.1645-1660.
Istepanian, R., Laxminarayan, S. and Pattichis, C.S., 2014.M-health. John Wiley & Sons.
Jain, R. and Paul, S., 2013. Network virtualization and software defined networking for cloud
computing: a survey.IEEE Communications Magazine. 51(11). pp.24-31.
Kim, J. and et.al, 2014. M2M Service Platforms: Survey, Issues, and Enabling
Technologies.IEEE Communications Surveys and Tutorials. 16(1). pp.61-76.
Leonardi, P.M., Huysman, M. and Steinfield, C., 2013. Enterprise social media: Definition,
history, and prospects for the study of social technologies in organizations.Journal of
Computer‐Mediated Communication. 19(1). pp.1-19.
Suthaharan, S., 2014. Big data classification: Problems and challenges in network intrusion
prediction with machine learning.ACM SIGMETRICS Performance Evaluation Review.
41(4). pp.70-73.
Vinel, A. and et.al , 2016. Enabling wireless communication and networking technologies for
the internet of things [Guest editorial].IEEE wireless communications. 23(5). pp.8-9.
Thomas, T. 2010. OSPF Network Design Solutions (2nd Edition). TX, U.S.A.: Cisco Press.
Luo, W., Pignataro, C., Chan, A. & Bokotey, D. 2004. Layer 2 VPN Architectures 1st Edition,
Kindle Edition. U.S.A.: Cisco Press.
39
Books and journals
Brandwine, E.J. and Hill, P.J., 2014.Providing virtual networking functionality for managed
computer networks. U.S. Patent 8,644,188.
Christensen, C.M., 2013.The innovator's dilemma: when new technologies cause great firms to
fail. Harvard Business Review Press.
Da Xu, L., He, W. and Li, S., 2014. Internet of things in industries: A survey.IEEE Transactions
on industrial informatics. 10(4). pp.2233-2243.
Gubbi, J. and et.al ,2013. Internet of Things (IoT): A vision, architectural elements, and future
directions.Future generation computer systems. 29(7). pp.1645-1660.
Istepanian, R., Laxminarayan, S. and Pattichis, C.S., 2014.M-health. John Wiley & Sons.
Jain, R. and Paul, S., 2013. Network virtualization and software defined networking for cloud
computing: a survey.IEEE Communications Magazine. 51(11). pp.24-31.
Kim, J. and et.al, 2014. M2M Service Platforms: Survey, Issues, and Enabling
Technologies.IEEE Communications Surveys and Tutorials. 16(1). pp.61-76.
Leonardi, P.M., Huysman, M. and Steinfield, C., 2013. Enterprise social media: Definition,
history, and prospects for the study of social technologies in organizations.Journal of
Computer‐Mediated Communication. 19(1). pp.1-19.
Suthaharan, S., 2014. Big data classification: Problems and challenges in network intrusion
prediction with machine learning.ACM SIGMETRICS Performance Evaluation Review.
41(4). pp.70-73.
Vinel, A. and et.al , 2016. Enabling wireless communication and networking technologies for
the internet of things [Guest editorial].IEEE wireless communications. 23(5). pp.8-9.
Thomas, T. 2010. OSPF Network Design Solutions (2nd Edition). TX, U.S.A.: Cisco Press.
Luo, W., Pignataro, C., Chan, A. & Bokotey, D. 2004. Layer 2 VPN Architectures 1st Edition,
Kindle Edition. U.S.A.: Cisco Press.
39

Szigeti, T., & Hattingh, C. 2004. End-to-End QoS Network Design: Quality of Service in LANs,
WANs, and VPNs (Networking Technology) 1st Edition, Kindle Edition. U.S.A.: Cisco Press.
White, R. & Donohue, D. 2014. The Art of Network Architecture: Business-Driven Design
(Networking Technology) 1st Edition, Kindle Edition. U.S.A.: Cisco Press
Online
PSN .2017. Accessed through<https://www.gov.uk/government/groups/public-services-
network>[Accessed on 26th June 2017]
OSI .2017. Accessed through<https://www.lifewire.com>[Accessed on 26th June 2017]
Networking types .2017. Accessed through<http://www.webopedia.com/>[Accessed on 26th June
2017]
Introduction to Network Operating System., 2017. [Online]. Available
through:<http://www.assignmenthelp.net/network-operating-systems>. Accessed on 16th August
2017].
Network Interface Card., 2017.
[Online].Availablethrough:<http://study.com/academy/lesson/network-interface-card-nic-types-
function-definition.html>. [Accessed on 16th August 2017].
40
WANs, and VPNs (Networking Technology) 1st Edition, Kindle Edition. U.S.A.: Cisco Press.
White, R. & Donohue, D. 2014. The Art of Network Architecture: Business-Driven Design
(Networking Technology) 1st Edition, Kindle Edition. U.S.A.: Cisco Press
Online
PSN .2017. Accessed through<https://www.gov.uk/government/groups/public-services-
network>[Accessed on 26th June 2017]
OSI .2017. Accessed through<https://www.lifewire.com>[Accessed on 26th June 2017]
Networking types .2017. Accessed through<http://www.webopedia.com/>[Accessed on 26th June
2017]
Introduction to Network Operating System., 2017. [Online]. Available
through:<http://www.assignmenthelp.net/network-operating-systems>. Accessed on 16th August
2017].
Network Interface Card., 2017.
[Online].Availablethrough:<http://study.com/academy/lesson/network-interface-card-nic-types-
function-definition.html>. [Accessed on 16th August 2017].
40
1 out of 40
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





