IT Risk Management: ENISA Big Data Threat Landscape Analysis Report
VerifiedAdded on 2020/02/24
|16
|3718
|133
Report
AI Summary
This report provides an analysis of IT Risk Management, focusing on the ENISA Big Data Threat Landscape. It begins with an overview of the case study and presents a diagram of the ENISA Big Data security infrastructure. The report then identifies and discusses the most significant threats, categorizing them into groups such as eavesdropping, interception, and hijacking. It also examines key threat agents, including corporations, cybercriminals, cyber terrorists, and employees, and suggests methods to minimize their impact. The report further discusses the trends in threat probability and concludes with an examination of the ETL process, offering suggestions for improvement, such as tackling bottlenecks, loading data incrementally, partitioning large tables, cutting out extraneous data, and caching data. The report emphasizes the importance of security measures and staying updated in the face of evolving threats.

Running Head: IT RISK MANAGEMENT
IT RISK MANAGEMENT
Name of the Student
Name of the University
IT RISK MANAGEMENT
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
Table of Contents
ENISA Big Data Threat Landscape 2016......................................................................2
Question 1......................................................................................................................2
Question 2......................................................................................................................4
Question 3......................................................................................................................6
Question 4......................................................................................................................8
Question 5......................................................................................................................8
References....................................................................................................................11
Table of Contents
ENISA Big Data Threat Landscape 2016......................................................................2
Question 1......................................................................................................................2
Question 2......................................................................................................................4
Question 3......................................................................................................................6
Question 4......................................................................................................................8
Question 5......................................................................................................................8
References....................................................................................................................11

2IT RISK MANAGEMENT
ENISA Big Data Threat Landscape 2016
Question 1
Provide a brief overview of the case study and prepare a diagram for the ENISA Big Data
security infrastructure.
There is an elaboration of threats which is related to the Big Data in the case study.
There have been much gained traction within last few years and thus the data storage and
information technology has been anticipated to play a serious role on several new aspects in
the society (Marinos, 2013). The potential impact of the Big Data has been acknowledged by
the European Commission by identifying the strategic approach in the Big Data. The aspects
that can be developed and affected by the development of information technology and big
data are food security, health security, climate and resources that are efficient to energy,
intelligent transport system and smart cities. The data is thus conceivable to the economic
drive in the organizational system. In the field of science and research there is also a large
impact of the Big Data that continues to escalate. Thus, many agencies and institution all over
the globe are planning to launch the Big Data projects for better exploitation of data analysis
and cloud computing. Technologies of Big Data can also be used in the application of
military field, such as combat accommodating or fighting virtual or real terrorism. Thus
identifying and collecting the information from heterogeneous sources from any real filed or
open sources has a great impact (Marinos, Belmonte &Rekleitis, 2014). High tech and highly
novel ICT systems are used in the approach of Big Data. But increase in the use of this Big
Data technology has also frequently increased the chances of cyber attacks, data breaches and
hacking. The increases of this kind of challenges are both trending the number in
sophisticated and impact. By increase in the number of usability of business in Big Data and
ENISA Big Data Threat Landscape 2016
Question 1
Provide a brief overview of the case study and prepare a diagram for the ENISA Big Data
security infrastructure.
There is an elaboration of threats which is related to the Big Data in the case study.
There have been much gained traction within last few years and thus the data storage and
information technology has been anticipated to play a serious role on several new aspects in
the society (Marinos, 2013). The potential impact of the Big Data has been acknowledged by
the European Commission by identifying the strategic approach in the Big Data. The aspects
that can be developed and affected by the development of information technology and big
data are food security, health security, climate and resources that are efficient to energy,
intelligent transport system and smart cities. The data is thus conceivable to the economic
drive in the organizational system. In the field of science and research there is also a large
impact of the Big Data that continues to escalate. Thus, many agencies and institution all over
the globe are planning to launch the Big Data projects for better exploitation of data analysis
and cloud computing. Technologies of Big Data can also be used in the application of
military field, such as combat accommodating or fighting virtual or real terrorism. Thus
identifying and collecting the information from heterogeneous sources from any real filed or
open sources has a great impact (Marinos, Belmonte &Rekleitis, 2014). High tech and highly
novel ICT systems are used in the approach of Big Data. But increase in the use of this Big
Data technology has also frequently increased the chances of cyber attacks, data breaches and
hacking. The increases of this kind of challenges are both trending the number in
sophisticated and impact. By increase in the number of usability of business in Big Data and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
organizations, the attackers get incentives for developing and specializes attacks against Big
Data analysis. This technology are used by tools that has also the capability that combats the
cyber threats that offers privacy and security professionals that has valuable insights in
incident management and threats. In the area of Big Data analysis ENISA delivers the area of
this Threats Landscapes by the inputs from the ENISA Threat Landscape activities. The case
study discusses about the architecture, ENISA threat taxonomy the targeted audience of Big
Data approach, the asset taxonomy of Big Data, the methodology by which the case study has
been carried out, gaps of the study and finally recommending the approach.
The infrastructure layer in ENISA by Big Data is depicted by the Cloud Computing.
IT helps in meeting the infrastructure requirement like the elasticity, cost-effectiveness and
the ability to scale up and down. The security infrastructure of Big Data system in ENISA
follows:
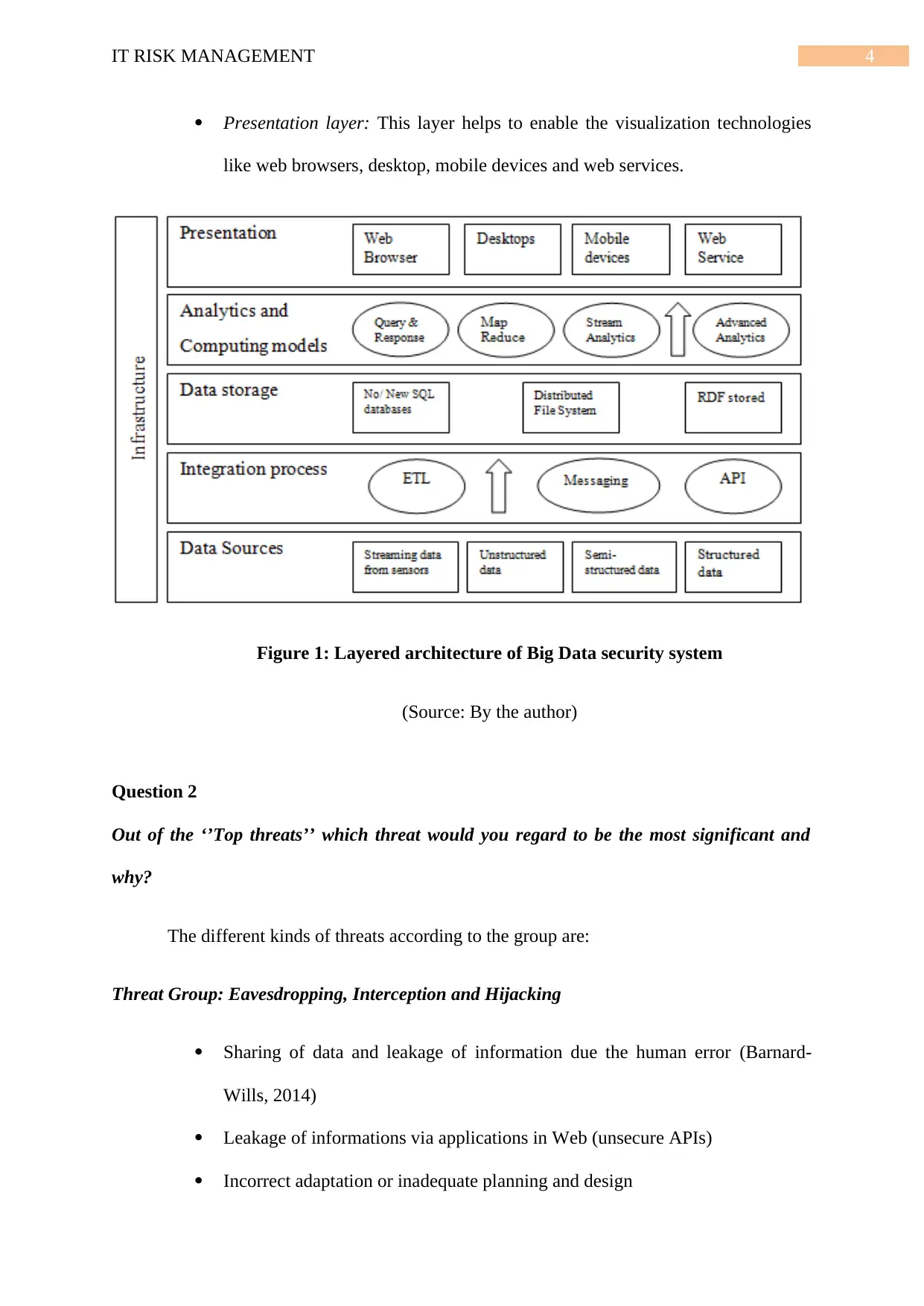
Data sources layer: The layer consist of streaming data from the data source
disparate, sensor and structured information like relational database, semi-
structured and unstructured data.
Integration process layer: The layer only concern with important data having
pre-processing operation acquiring data hence integrated the datasets into a
structured form.
Data storage layer: This data layer is consist of large variety of resources like
RDF stores, NoSQL, distributed file system and NewSQL database, that are
suitable for large number of datasets that persistent storage.
Analytics and computing model layer: The layer encapsulates different data
tools like the MapReduce that runs over the resources that are stored, having
the model programming and data management.
organizations, the attackers get incentives for developing and specializes attacks against Big
Data analysis. This technology are used by tools that has also the capability that combats the
cyber threats that offers privacy and security professionals that has valuable insights in
incident management and threats. In the area of Big Data analysis ENISA delivers the area of
this Threats Landscapes by the inputs from the ENISA Threat Landscape activities. The case
study discusses about the architecture, ENISA threat taxonomy the targeted audience of Big
Data approach, the asset taxonomy of Big Data, the methodology by which the case study has
been carried out, gaps of the study and finally recommending the approach.
The infrastructure layer in ENISA by Big Data is depicted by the Cloud Computing.
IT helps in meeting the infrastructure requirement like the elasticity, cost-effectiveness and
the ability to scale up and down. The security infrastructure of Big Data system in ENISA
follows:
Data sources layer: The layer consist of streaming data from the data source
disparate, sensor and structured information like relational database, semi-
structured and unstructured data.
Integration process layer: The layer only concern with important data having
pre-processing operation acquiring data hence integrated the datasets into a
structured form.
Data storage layer: This data layer is consist of large variety of resources like
RDF stores, NoSQL, distributed file system and NewSQL database, that are
suitable for large number of datasets that persistent storage.
Analytics and computing model layer: The layer encapsulates different data
tools like the MapReduce that runs over the resources that are stored, having
the model programming and data management.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4IT RISK MANAGEMENT
Presentation layer: This layer helps to enable the visualization technologies
like web browsers, desktop, mobile devices and web services.
Figure 1: Layered architecture of Big Data security system
(Source: By the author)
Question 2
Out of the ‘’Top threats’’ which threat would you regard to be the most significant and
why?
The different kinds of threats according to the group are:
Threat Group: Eavesdropping, Interception and Hijacking
Sharing of data and leakage of information due the human error (Barnard-
Wills, 2014)
Leakage of informations via applications in Web (unsecure APIs)
Incorrect adaptation or inadequate planning and design
Presentation layer: This layer helps to enable the visualization technologies
like web browsers, desktop, mobile devices and web services.
Figure 1: Layered architecture of Big Data security system
(Source: By the author)
Question 2
Out of the ‘’Top threats’’ which threat would you regard to be the most significant and
why?
The different kinds of threats according to the group are:
Threat Group: Eavesdropping, Interception and Hijacking
Sharing of data and leakage of information due the human error (Barnard-
Wills, 2014)
Leakage of informations via applications in Web (unsecure APIs)
Incorrect adaptation or inadequate planning and design

5IT RISK MANAGEMENT
Interception of information
Threat Group: Nefarious Activity/Abuse
Identity fraud
Denial of service (DoI)
Malicious codes / activities/ software
Use and generation or unauthorized certificates
Unauthorized activities / Misuse of audit tools / Abuse of authorizations
Business process failure (Lévy-Bencheton et al., 2015)
Threat Group: Legal
Breach of legislation / Abuse of personal data / Violation of laws or
regulations
Skill shortage
According the comparison of the three threats groups the most significant threat is the
“Eavesdropping, Interception and Hijacking”, since the most data and privacy risks are
related to this threat faces maximum difficulties, like the data braches, hacking, cyber attack
and many more. Affecting the most private and confidential resources of the company (Cho
et al., 2016). This threat agent is hostile in nature. Their goal is basically financial gain
having higher skill level. Cybercriminals can be organized on a local, national or even
international level. These agents are socially and politically motivated individuals using the
network or the computer system for protesting and promoting causes of the damage (Wang,
Anokhin & Anderl, 2017). The main attacks by this threat groups are Leakage of
Information /sharing because of human fault, Leaks of information via applications of web
(unsecure APIs), designing inadequately and planning, or wrong adaptation and Interception
Interception of information
Threat Group: Nefarious Activity/Abuse
Identity fraud
Denial of service (DoI)
Malicious codes / activities/ software
Use and generation or unauthorized certificates
Unauthorized activities / Misuse of audit tools / Abuse of authorizations
Business process failure (Lévy-Bencheton et al., 2015)
Threat Group: Legal
Breach of legislation / Abuse of personal data / Violation of laws or
regulations
Skill shortage
According the comparison of the three threats groups the most significant threat is the
“Eavesdropping, Interception and Hijacking”, since the most data and privacy risks are
related to this threat faces maximum difficulties, like the data braches, hacking, cyber attack
and many more. Affecting the most private and confidential resources of the company (Cho
et al., 2016). This threat agent is hostile in nature. Their goal is basically financial gain
having higher skill level. Cybercriminals can be organized on a local, national or even
international level. These agents are socially and politically motivated individuals using the
network or the computer system for protesting and promoting causes of the damage (Wang,
Anokhin & Anderl, 2017). The main attacks by this threat groups are Leakage of
Information /sharing because of human fault, Leaks of information via applications of web
(unsecure APIs), designing inadequately and planning, or wrong adaptation and Interception
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK MANAGEMENT
of information. The contribution of smart devices and computer platform from the
unprecedented networking to the Big Data may pose privacy concern where an individual’s
location, transaction and other behavior are digitally recorded (Scott et al., 2016). High
profile websites are generally being targeted along with intelligence agencies and military
institutions.
Question 3
Identify and discuss the key Threat Agents. What could be done to minimize their impact
on the system? Based on the data provided, discuss the trends in threat probability.
According the ENISA threat Landscape, the threat agent is described as “someone or
something with decent capabilities, a clear intention to manifest a threat and a record of past
activities in this regard” (Barnard-Wills, Marinos&Portesi, 2014). The organization using
Big Data application has to be aware of the threats that are emerging and from which threat
groups that they belong. There are categories by which the threat agents have been divided in:
Corporations: This category refers to the enterprises or organizations that may engage or
adapt any tactics that may be unethical and offensive to the enterprise. These are the hostile
threat agents having the motive to build competitive advantage over the competitors. The
organization generally sorts their main targets and focusing over the size and sectors the
enterprises possess capabilities to the area of significance, as well as from the area of
technological aspect to human engineering intelligence in the field of expertise (Brender&
Markov, 2013).
Cyber Criminals: This threat agent is hostile in nature. Their goal is basically financial gain
having higher skill level (Le Bray, Mayer &Aubert, 2016). Cybercriminals can be organized
on a local, national or even international level
of information. The contribution of smart devices and computer platform from the
unprecedented networking to the Big Data may pose privacy concern where an individual’s
location, transaction and other behavior are digitally recorded (Scott et al., 2016). High
profile websites are generally being targeted along with intelligence agencies and military
institutions.
Question 3
Identify and discuss the key Threat Agents. What could be done to minimize their impact
on the system? Based on the data provided, discuss the trends in threat probability.
According the ENISA threat Landscape, the threat agent is described as “someone or
something with decent capabilities, a clear intention to manifest a threat and a record of past
activities in this regard” (Barnard-Wills, Marinos&Portesi, 2014). The organization using
Big Data application has to be aware of the threats that are emerging and from which threat
groups that they belong. There are categories by which the threat agents have been divided in:
Corporations: This category refers to the enterprises or organizations that may engage or
adapt any tactics that may be unethical and offensive to the enterprise. These are the hostile
threat agents having the motive to build competitive advantage over the competitors. The
organization generally sorts their main targets and focusing over the size and sectors the
enterprises possess capabilities to the area of significance, as well as from the area of
technological aspect to human engineering intelligence in the field of expertise (Brender&
Markov, 2013).
Cyber Criminals: This threat agent is hostile in nature. Their goal is basically financial gain
having higher skill level (Le Bray, Mayer &Aubert, 2016). Cybercriminals can be organized
on a local, national or even international level
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
Cyber terrorists: The motivation of this threat agent can either be religious or political, that
expands the activity engaging in cyber-attacks. The targets that are preferred by the cyber
terrorists are mainly over critical infrastructure like in telecommunication, energy production
or public healthcare system (Olesen, 2016). This complex infrastructure is generally chosen
since failure of this organization creates as chaos and cause severe impact in the government
and society.
Script kiddies: These agents use the scripts and the programs developed since these are
mainly unskilled, that attacks the network or the computer systems as well as websites.
Online social hackers (hacktivists): These agents are socially and politically motivated
individuals using the network or the computer system for protesting and promoting causes of
the damage (Bugeja, Jacobsson&Davidsson, 2017). High profile websites are generally being
targeted along with intelligence agencies and military institutions.
Employees: Sometime the employees for the deterioration of the company access the
company’s resources from inside and hence hostile and non-hostile agents both of these can
considered to the employee. This agent includes staffs, operational staffs, contractors or
security guards of the company (Belmonte Martin et al., 2015). A significant amount of
knowledge is required for this kind of threats, which helps them in placing the effective
attack against the assets of the company.
Nation states: these agents usually have offensive capabilities in cyber security and may use
it over an enterprise.
Protecting the Big Data assets by using applicable methods and techniques in the
organization. There has been a shared responsibility for the privacy, security and
infrastructure management of every organization. Since, the agents target the main
Cyber terrorists: The motivation of this threat agent can either be religious or political, that
expands the activity engaging in cyber-attacks. The targets that are preferred by the cyber
terrorists are mainly over critical infrastructure like in telecommunication, energy production
or public healthcare system (Olesen, 2016). This complex infrastructure is generally chosen
since failure of this organization creates as chaos and cause severe impact in the government
and society.
Script kiddies: These agents use the scripts and the programs developed since these are
mainly unskilled, that attacks the network or the computer systems as well as websites.
Online social hackers (hacktivists): These agents are socially and politically motivated
individuals using the network or the computer system for protesting and promoting causes of
the damage (Bugeja, Jacobsson&Davidsson, 2017). High profile websites are generally being
targeted along with intelligence agencies and military institutions.
Employees: Sometime the employees for the deterioration of the company access the
company’s resources from inside and hence hostile and non-hostile agents both of these can
considered to the employee. This agent includes staffs, operational staffs, contractors or
security guards of the company (Belmonte Martin et al., 2015). A significant amount of
knowledge is required for this kind of threats, which helps them in placing the effective
attack against the assets of the company.
Nation states: these agents usually have offensive capabilities in cyber security and may use
it over an enterprise.
Protecting the Big Data assets by using applicable methods and techniques in the
organization. There has been a shared responsibility for the privacy, security and
infrastructure management of every organization. Since, the agents target the main

8IT RISK MANAGEMENT
stakeholders of the Big Data focusing on the large amount of datasets (Belmonte Martin et
al., 2015). After a careful evolution of the life cycle of Big Data there should be aim of
verifying and proving the correct behavior. There can be success in vendors committed by the
third party, applying security measures and hence stay updated and focused.
On the basis of the data provided the trend in the threat probability it has been
explained that:
a. The most information leakage, planning or improperly adaptation, Inadequate
design and, Identity fraud, Malicious code, Misuse of audit tools, Failures of
business process, Breach of legislation or Abuse of personal data has been
threatened by the employees (Rhee et al., 2013).
b. Cyber criminals, corporations and cyber terrorists mainly affects the Leaks of
data via Web applications having unsecure APIs, Interception of information,
Identity fraud, DOI (Denial of service), Malicious code validation and use of
rogue certificates.
c. The least damaged has been done by the script kiddies as there are unskilled
agents.
Question 4
How could the ETL process be improved? Discuss.
The threats taxonomy as developed by the ENISA Threat Landscape (ETL) Group and this
includes threats that are applicable for the assets of the Big Data and these can be improves
by the following ways:
Tackling Bottlenecks: Making sure you log metrics such as time, number of records
processed and usage of hardware. Constructing facts and dimensions in the staging
stakeholders of the Big Data focusing on the large amount of datasets (Belmonte Martin et
al., 2015). After a careful evolution of the life cycle of Big Data there should be aim of
verifying and proving the correct behavior. There can be success in vendors committed by the
third party, applying security measures and hence stay updated and focused.
On the basis of the data provided the trend in the threat probability it has been
explained that:
a. The most information leakage, planning or improperly adaptation, Inadequate
design and, Identity fraud, Malicious code, Misuse of audit tools, Failures of
business process, Breach of legislation or Abuse of personal data has been
threatened by the employees (Rhee et al., 2013).
b. Cyber criminals, corporations and cyber terrorists mainly affects the Leaks of
data via Web applications having unsecure APIs, Interception of information,
Identity fraud, DOI (Denial of service), Malicious code validation and use of
rogue certificates.
c. The least damaged has been done by the script kiddies as there are unskilled
agents.
Question 4
How could the ETL process be improved? Discuss.
The threats taxonomy as developed by the ENISA Threat Landscape (ETL) Group and this
includes threats that are applicable for the assets of the Big Data and these can be improves
by the following ways:
Tackling Bottlenecks: Making sure you log metrics such as time, number of records
processed and usage of hardware. Constructing facts and dimensions in the staging
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK MANAGEMENT
environment. Where ever the bottle neck dive into the code and takes deep breath.
Checking how many resources each part of the process intakes and hence addresses
the most heavy one (Rhee et al., 2013).
Load Data Incrementally: It’s more difficult to implement and maintain, but difficult
doesn’t mean impossible, so do consider it. Changes loaded between the new and the
previous data saves a lot of time as compared to a full load. Loading incrementally
can definitely improve the ETL performance.
Partition large tables: The usage of large relational database that may improve the
data processing windows can be partitioned in large tables. Means cut big tables down
to physically smaller ones, probably by dates. Each parcel has its own records and the
files tree is shallower in this way taking into consideration snappier access to the
information. It additionally permits exchanging information all through a table in a
brisk. Meta information operation rather than genuine inclusion or erasure of
information records.
Cut out extraneous data: The accumulation of information however much as could be
expected is essential, might be not every one of the information but rather it is
sufficiently commendable to enter the information stockroom. For example, pictures
of furniture models are pointless to BI investigators. On the off chance that you need
to enhance the ETL execution, take a seat and characterize precisely which
information ought to be prepared and leave superfluous lines/segments out. Better to
begin little and develop as you go instead of making a mammoth information creature
that takes ages to process.
Cache the data: It is possible for the cache data to speed up greatly since access
memory performs faster than do hard drives. Note that caching is limited by the
environment. Where ever the bottle neck dive into the code and takes deep breath.
Checking how many resources each part of the process intakes and hence addresses
the most heavy one (Rhee et al., 2013).
Load Data Incrementally: It’s more difficult to implement and maintain, but difficult
doesn’t mean impossible, so do consider it. Changes loaded between the new and the
previous data saves a lot of time as compared to a full load. Loading incrementally
can definitely improve the ETL performance.
Partition large tables: The usage of large relational database that may improve the
data processing windows can be partitioned in large tables. Means cut big tables down
to physically smaller ones, probably by dates. Each parcel has its own records and the
files tree is shallower in this way taking into consideration snappier access to the
information. It additionally permits exchanging information all through a table in a
brisk. Meta information operation rather than genuine inclusion or erasure of
information records.
Cut out extraneous data: The accumulation of information however much as could be
expected is essential, might be not every one of the information but rather it is
sufficiently commendable to enter the information stockroom. For example, pictures
of furniture models are pointless to BI investigators. On the off chance that you need
to enhance the ETL execution, take a seat and characterize precisely which
information ought to be prepared and leave superfluous lines/segments out. Better to
begin little and develop as you go instead of making a mammoth information creature
that takes ages to process.
Cache the data: It is possible for the cache data to speed up greatly since access
memory performs faster than do hard drives. Note that caching is limited by the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT RISK MANAGEMENT
maximum amount of memory your hardware supports. There is always a fitting
problem regarding the plastic furnitures.
Process in parallel: Other than serial processing, optimization of resources is vital by
parallel correction the entire time. These techniques can scale up by upgrading the
CPU, but only up to a limited part. There can be better solutions as well.
Use Hadoop: Apache Hadoop software is a open source library including software
service that allows the distribution process of large sets of data across the clusters of
computers by using simple program models. It has been designed to scale up from
one-to-multiple machines that is, from single server to multiple other servers or
machines, which offers local storage and computation.
Question 5
To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or Why
not?
As per the ENISA Big Data there are few points on the security infrastructure:
For the application level to the network protocol the trusted components shall always
be used in all levels of the information system, which are usually based on the key
management and the strongest technique to encrypt (Karchefsky& Rao, 2017). Some
of the examples of this trusted infrastructure are secure communication protocols,
authentication infrastructure public key infrastructure components and many more.
It is vital for the organization to own a trusted infrastructure, such that to build the
information security on the basis of the security measure at every level and thus
providing the authentication systems and partners with trust worth transactions,
connection and electronic signatures.
maximum amount of memory your hardware supports. There is always a fitting
problem regarding the plastic furnitures.
Process in parallel: Other than serial processing, optimization of resources is vital by
parallel correction the entire time. These techniques can scale up by upgrading the
CPU, but only up to a limited part. There can be better solutions as well.
Use Hadoop: Apache Hadoop software is a open source library including software
service that allows the distribution process of large sets of data across the clusters of
computers by using simple program models. It has been designed to scale up from
one-to-multiple machines that is, from single server to multiple other servers or
machines, which offers local storage and computation.
Question 5
To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or Why
not?
As per the ENISA Big Data there are few points on the security infrastructure:
For the application level to the network protocol the trusted components shall always
be used in all levels of the information system, which are usually based on the key
management and the strongest technique to encrypt (Karchefsky& Rao, 2017). Some
of the examples of this trusted infrastructure are secure communication protocols,
authentication infrastructure public key infrastructure components and many more.
It is vital for the organization to own a trusted infrastructure, such that to build the
information security on the basis of the security measure at every level and thus
providing the authentication systems and partners with trust worth transactions,
connection and electronic signatures.

11IT RISK MANAGEMENT
As the ENISA explained, there would be a great potential impact on increase in the
concentration of data in cloud computing for the hackers, since there is always a
chance for exploitation of confidential and personal information. The cyber criminals
often store malwares in the network system or may use the platform to launch an
attack for their own profit.
As an emerging security issue big data is on the top of the list as a widely spreading
consequence of cloud computing, social technologies and other internet subscriptions.
This has become a newly emerging security issue.
The data privacy is mainly affected by the exploitation of this big data by
unauthorized users. But in case of advertisement, big data exploitation may invite new
kinds of attack vectors.
There are several kinds of challenges identifies in the security system of Big Data. These
challenges must need data protection, control accessibility of data and data filtering (Lykou,
2016). As said by the ENISA there are several issues regarding huge amount of data control
that is beyond the processing power of products in Security information and Event
Management (SIEM).
Yes, ENISA be satisfied with its current state of IT Security. There are gaps in data
protection due to the threats and confidentiality of sensor data streams. In cases of identity
fraud the traffic captured and the Big Data analysis helps in facilitating the privacy intrusion
by strengthening the common techniques and on further research in the required fields. In
year 2009 the ENISA has decided to update and assess the risks and benefits for higher
reflection to the current situation of the organization. It has been detected that the main risk
that is by using cloud computing has not changed but there has been a decision of
reconstructing the risks having the aim of making the descriptions much uniform (Lévy-
Bencheton et al., 2015). There has been an introduction of legal and data protection aspects of
As the ENISA explained, there would be a great potential impact on increase in the
concentration of data in cloud computing for the hackers, since there is always a
chance for exploitation of confidential and personal information. The cyber criminals
often store malwares in the network system or may use the platform to launch an
attack for their own profit.
As an emerging security issue big data is on the top of the list as a widely spreading
consequence of cloud computing, social technologies and other internet subscriptions.
This has become a newly emerging security issue.
The data privacy is mainly affected by the exploitation of this big data by
unauthorized users. But in case of advertisement, big data exploitation may invite new
kinds of attack vectors.
There are several kinds of challenges identifies in the security system of Big Data. These
challenges must need data protection, control accessibility of data and data filtering (Lykou,
2016). As said by the ENISA there are several issues regarding huge amount of data control
that is beyond the processing power of products in Security information and Event
Management (SIEM).
Yes, ENISA be satisfied with its current state of IT Security. There are gaps in data
protection due to the threats and confidentiality of sensor data streams. In cases of identity
fraud the traffic captured and the Big Data analysis helps in facilitating the privacy intrusion
by strengthening the common techniques and on further research in the required fields. In
year 2009 the ENISA has decided to update and assess the risks and benefits for higher
reflection to the current situation of the organization. It has been detected that the main risk
that is by using cloud computing has not changed but there has been a decision of
reconstructing the risks having the aim of making the descriptions much uniform (Lévy-
Bencheton et al., 2015). There has been an introduction of legal and data protection aspects of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





