iT Risk Management: Biometric Systems, PETs, and WSN Analysis
VerifiedAdded on 2023/06/09
|11
|2471
|380
Report
AI Summary
This report provides an in-depth analysis of iT risk management, focusing on biometric systems, privacy-enhancing technologies (PETs), and wireless sensor networks (WSNs). The report begins by exploring various biometric systems like fingerprint recognition, hand geometry, and iris recognition, detailing their underlying technologies, advantages, disadvantages, and practical applications. The analysis extends to privacy-enhancing technologies used on the internet, discussing encryption, identity management, and remailer technologies, alongside illustrative examples of their application. Finally, the report addresses the security challenges faced by WSNs, examining various attack types such as those targeting secrecy, authentication, availability, and integrity, and suggests mitigation strategies including encryption, data partitioning, secure data aggregation, and cryptography. The report aims to offer a comprehensive understanding of these critical areas within iT risk management.

iT RISK MANAGEMENT
AUGUST 15, 2018
student NAme
Student code
AUGUST 15, 2018
student NAme
Student code
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Subject Code Subject Name Semester Number
Table of Contents
1.0 Biometric systems……………………………………………………………………………………...3
1.1 Fingerprint Recognition……………………………………………………………………………4
1.2 Hand Geometry……………………………………………………………………………………………………………………………5
1.3 Iris Recognition…………………………………………………………………………………………………………………….6
2.0 Privacy Enhancing Technologies Used on the Internet……………………………………………..7
3.0 Wireless Sensor Networks……………………………………………………………………………………………………………….8
Contents of Figures
Figure 1 types of biometrics........................................................................................................................1
Figure 2 Fingerprint Recognition................................................................................................................2
Figure 3 Working of the Iris Recognition System.........................................................................................4
Figure 4 Iris Recognition..............................................................................................................................4
2
Table of Contents
1.0 Biometric systems……………………………………………………………………………………...3
1.1 Fingerprint Recognition……………………………………………………………………………4
1.2 Hand Geometry……………………………………………………………………………………………………………………………5
1.3 Iris Recognition…………………………………………………………………………………………………………………….6
2.0 Privacy Enhancing Technologies Used on the Internet……………………………………………..7
3.0 Wireless Sensor Networks……………………………………………………………………………………………………………….8
Contents of Figures
Figure 1 types of biometrics........................................................................................................................1
Figure 2 Fingerprint Recognition................................................................................................................2
Figure 3 Working of the Iris Recognition System.........................................................................................4
Figure 4 Iris Recognition..............................................................................................................................4
2
Subject Code Subject Name Semester Number
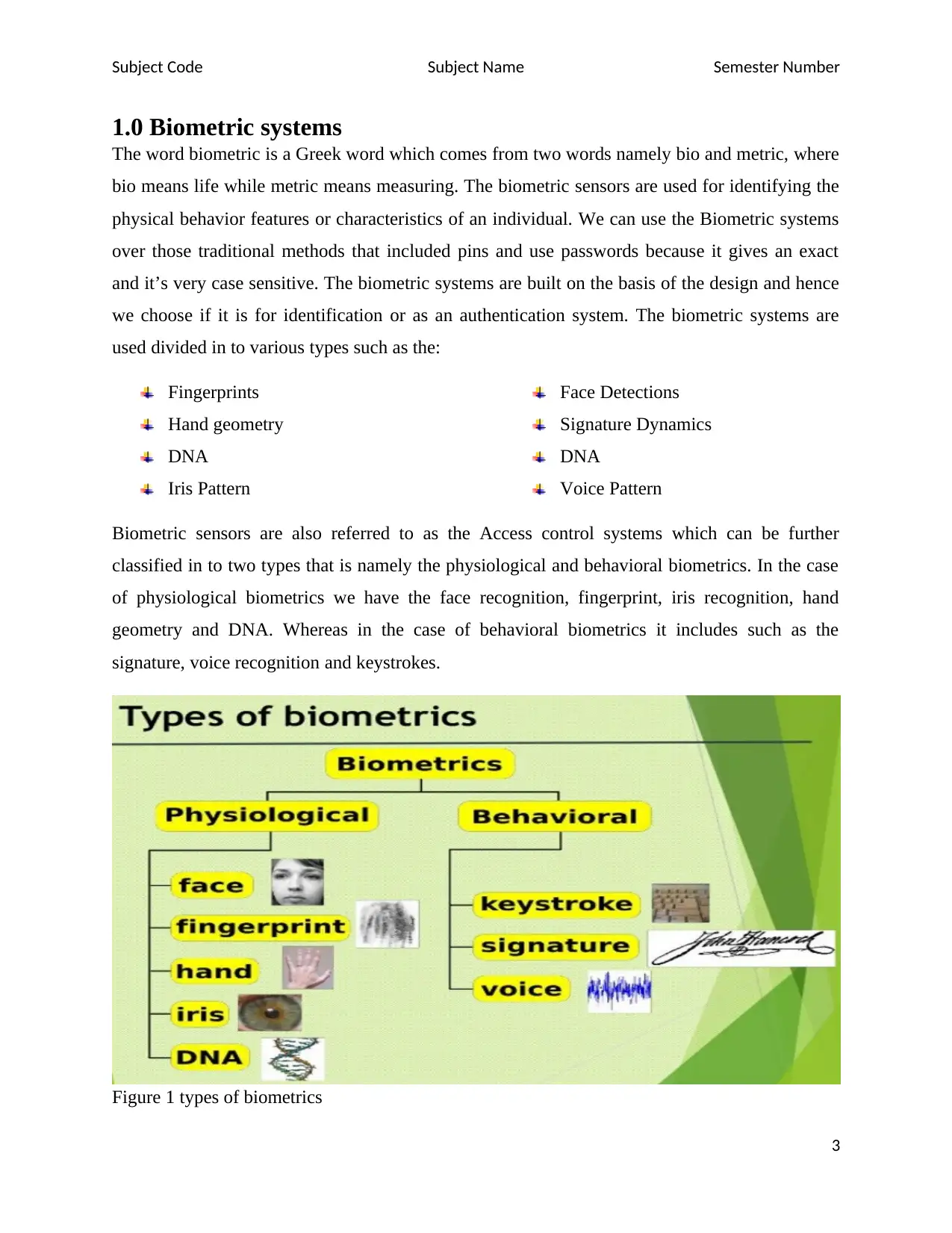
1.0 Biometric systems
The word biometric is a Greek word which comes from two words namely bio and metric, where
bio means life while metric means measuring. The biometric sensors are used for identifying the
physical behavior features or characteristics of an individual. We can use the Biometric systems
over those traditional methods that included pins and use passwords because it gives an exact
and it’s very case sensitive. The biometric systems are built on the basis of the design and hence
we choose if it is for identification or as an authentication system. The biometric systems are
used divided in to various types such as the:
Fingerprints
Hand geometry
DNA
Iris Pattern
Face Detections
Signature Dynamics
DNA
Voice Pattern
Biometric sensors are also referred to as the Access control systems which can be further
classified in to two types that is namely the physiological and behavioral biometrics. In the case
of physiological biometrics we have the face recognition, fingerprint, iris recognition, hand
geometry and DNA. Whereas in the case of behavioral biometrics it includes such as the
signature, voice recognition and keystrokes.
Figure 1 types of biometrics
3
1.0 Biometric systems
The word biometric is a Greek word which comes from two words namely bio and metric, where
bio means life while metric means measuring. The biometric sensors are used for identifying the
physical behavior features or characteristics of an individual. We can use the Biometric systems
over those traditional methods that included pins and use passwords because it gives an exact
and it’s very case sensitive. The biometric systems are built on the basis of the design and hence
we choose if it is for identification or as an authentication system. The biometric systems are
used divided in to various types such as the:
Fingerprints
Hand geometry
DNA
Iris Pattern
Face Detections
Signature Dynamics
DNA
Voice Pattern
Biometric sensors are also referred to as the Access control systems which can be further
classified in to two types that is namely the physiological and behavioral biometrics. In the case
of physiological biometrics we have the face recognition, fingerprint, iris recognition, hand
geometry and DNA. Whereas in the case of behavioral biometrics it includes such as the
signature, voice recognition and keystrokes.
Figure 1 types of biometrics
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Subject Code Subject Name Semester Number
1.1 Fingerprint Recognition.
This is known to include fingerprint image of the persons and recording the features such as the
aches, whorls and loops along the edges outlined and furrows. To match the fingerprint we can
attain it using the following three technologies.
i. Munitiae based fingerprint matches store a plane that may include set of points
and setting the point that may corresponds in to template
ii. Correlation based fingerprint that matches the overlays of the two images of
fingerprints and the association between the pixels that bare equivalent when
calculated.
iii. Ridge Feature based fingerprints that matches the innovative method capturing
the ridges.
Figure 2 Fingerprint Recognition
In capturing the fingerprints we have to present the methods that will employ optical sensors
where they use a CMOS image sensors or a CCD. The following are some of the advantages and
disadvantages of Fingerprint recognition
ADVANTAGES DISADVANTAGES
4
1.1 Fingerprint Recognition.
This is known to include fingerprint image of the persons and recording the features such as the
aches, whorls and loops along the edges outlined and furrows. To match the fingerprint we can
attain it using the following three technologies.
i. Munitiae based fingerprint matches store a plane that may include set of points
and setting the point that may corresponds in to template
ii. Correlation based fingerprint that matches the overlays of the two images of
fingerprints and the association between the pixels that bare equivalent when
calculated.
iii. Ridge Feature based fingerprints that matches the innovative method capturing
the ridges.
Figure 2 Fingerprint Recognition
In capturing the fingerprints we have to present the methods that will employ optical sensors
where they use a CMOS image sensors or a CCD. The following are some of the advantages and
disadvantages of Fingerprint recognition
ADVANTAGES DISADVANTAGES
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Subject Code Subject Name Semester Number
The accuracy is very high Sometimes it may be intrusive as it has
relation with criminal identification
It is very economical in terms of cost
especially for PC user authentications
When the finger is dirty then it can make
mistakes, also the age of the individual may
vary and this may affect the fingerprint
growth and hence changing.
It is the most and widely developed
biometrics globally
It requires large memory of space for images
as the resolution required are high pixels
It is very easy when using
It is known for being standardized
It requires very small storage that will require
biometric template which will help in
reducing the database size required.
The areas of applications of fingerprint recognitions are such as the:
When doing population census using the biometrics
During voter registration and identification
Driver’s license and professional ID card verification with biometric identifiers
Border control via passport verification by using biological parameters.
1.2 Hand Geometry
Hand geometry is the grandfather of all the biometric devices in the technology as it has existed
for more than twenty years. Hand geometry is based on the facts where each and every
individual hand must be shaped differently than any other individual hand (Lancho, 2017). The
technology behind the hand geometry is behind the use of hand geometry as it measure the
records of physical geometric features of the hands of the individual (University, 2018). The
hand geometry has fallen in two categories that is the mechanical and image-edge detections.
The two methods uses to measure some specific characteristics of the person hand that includes
the finger length and thumbs, depths and widths (Sanchez-Reillo, Sanchez-Avila, & Gonzalez-
Marcos, 2000).
Hand geometry has been applied and used in the following areas.
- Applications of international banks
- Used of tracking prisoners
- It is applied for all the branches of the united states of America military
- It is applied by the Colombian legislature
5
The accuracy is very high Sometimes it may be intrusive as it has
relation with criminal identification
It is very economical in terms of cost
especially for PC user authentications
When the finger is dirty then it can make
mistakes, also the age of the individual may
vary and this may affect the fingerprint
growth and hence changing.
It is the most and widely developed
biometrics globally
It requires large memory of space for images
as the resolution required are high pixels
It is very easy when using
It is known for being standardized
It requires very small storage that will require
biometric template which will help in
reducing the database size required.
The areas of applications of fingerprint recognitions are such as the:
When doing population census using the biometrics
During voter registration and identification
Driver’s license and professional ID card verification with biometric identifiers
Border control via passport verification by using biological parameters.
1.2 Hand Geometry
Hand geometry is the grandfather of all the biometric devices in the technology as it has existed
for more than twenty years. Hand geometry is based on the facts where each and every
individual hand must be shaped differently than any other individual hand (Lancho, 2017). The
technology behind the hand geometry is behind the use of hand geometry as it measure the
records of physical geometric features of the hands of the individual (University, 2018). The
hand geometry has fallen in two categories that is the mechanical and image-edge detections.
The two methods uses to measure some specific characteristics of the person hand that includes
the finger length and thumbs, depths and widths (Sanchez-Reillo, Sanchez-Avila, & Gonzalez-
Marcos, 2000).
Hand geometry has been applied and used in the following areas.
- Applications of international banks
- Used of tracking prisoners
- It is applied for all the branches of the united states of America military
- It is applied by the Colombian legislature
5
Subject Code Subject Name Semester Number
The following are some of the advantage and disadvantages of using Hand geometry as an access
control system.
ADVANTAGES DISADVANTAGES
It may require very special hardware’s that be
easily integrated in to other devices or
systems
It is very expensive
No public attitude problems have ever been
reported which are associated with the
authorization access
It has a considerable size
The amount of data will uniquely identify the
user of a system
It is not in any way valid for any arthritic
person as they cannot put hand their hand
properly on the scanner.
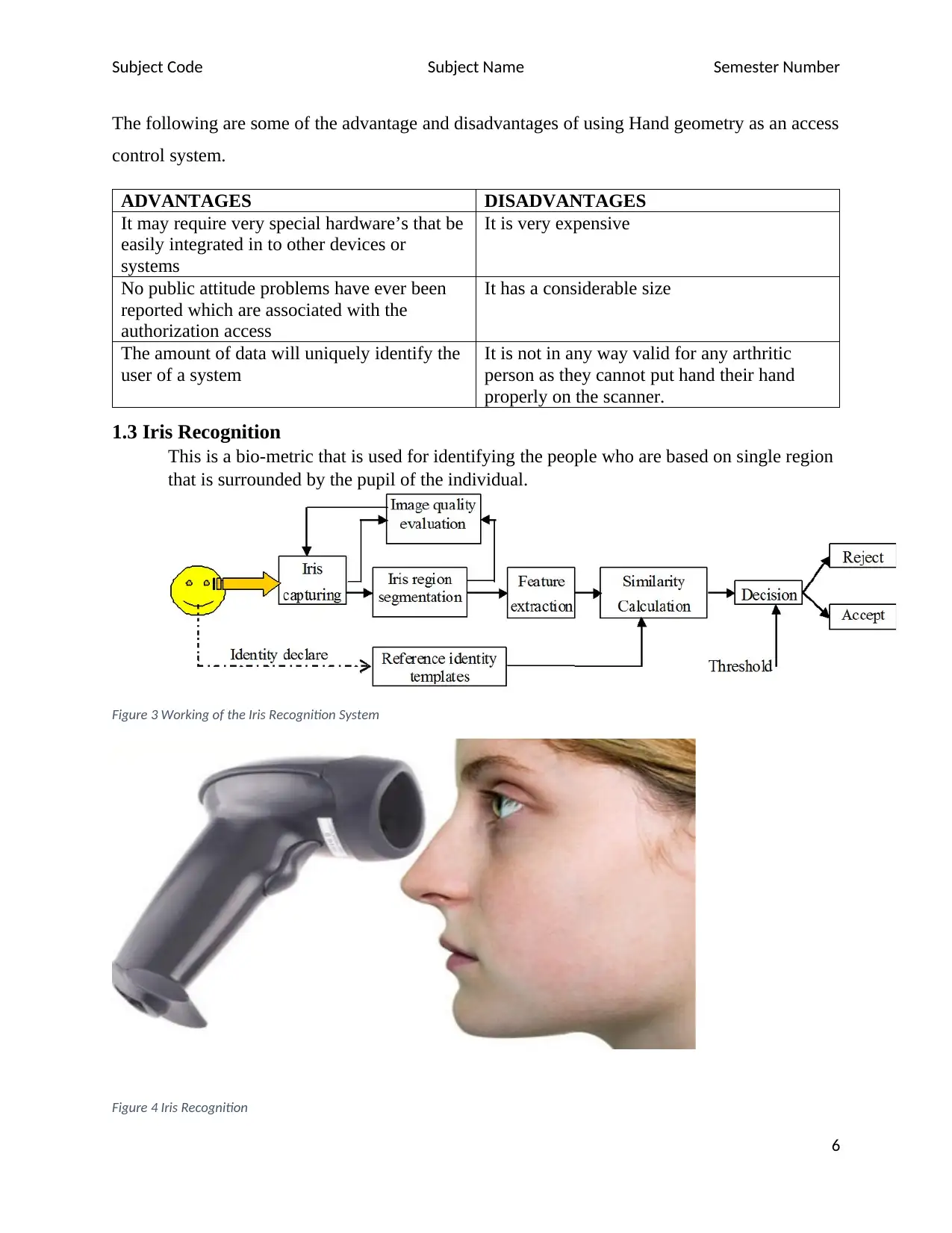
1.3 Iris Recognition
This is a bio-metric that is used for identifying the people who are based on single region
that is surrounded by the pupil of the individual.
Figure 3 Working of the Iris Recognition System
Figure 4 Iris Recognition
6
The following are some of the advantage and disadvantages of using Hand geometry as an access
control system.
ADVANTAGES DISADVANTAGES
It may require very special hardware’s that be
easily integrated in to other devices or
systems
It is very expensive
No public attitude problems have ever been
reported which are associated with the
authorization access
It has a considerable size
The amount of data will uniquely identify the
user of a system
It is not in any way valid for any arthritic
person as they cannot put hand their hand
properly on the scanner.
1.3 Iris Recognition
This is a bio-metric that is used for identifying the people who are based on single region
that is surrounded by the pupil of the individual.
Figure 3 Working of the Iris Recognition System
Figure 4 Iris Recognition
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Subject Code Subject Name Semester Number
The following are some of the advantages and disadvantages of iris recognition (PBworks,
2009).
ADVANTAGES DISADVANTAGES
It is Recognized for its accuracy being very
high
It is very intrusive
The verification may even take less than five
seconds
It needs a lot of memory for storage of the
data
The eye of a person who is dead deteriorate
very fast to be used and hence no extra
precautions will need to be taken with retina
scans to be sure when the user is alive.
It is very expensive.
Areas of applications of iris recognition are such as the:
Finance and banking
Healthcare and welfare- been used in hospitals to track the patient registration and to Checkup
arrangement and scheduling.
Also they have been applied in immigration borders control
For public safety
Also used for point of sale and ATM
2.0 Privacy Enhancing Technologies Used on the Internet
There are no constant definitions of Privacy enhancing technologies (PET) but we can define
PET as the use of tech to help in achieving it comply with data protection legislature. The
business case to adopt PETs is very limited to the personal information confidentiality i.e. we
may see many technologies may refer to PETS protecting all the corporate confidential info and
protecting the revenues by securing the integrity of the data. The following are some of the PETs
used over the internet.
i. Encryption. The term encryption has been relatively applied in the technology that is
mature, however it is still in the state of advancing. Encryption in the internet as a
type of PET has supported the security and the proportionality the principles of data
protection law. A good example is the use of PCI DSS standard for the credit card
data which has been the latest and recent announcement by the United Kingdom data
protection regulators. It is good to know that encryption is always relatively simple
when implementing and it is always easy and a very effective tool (Brewer, 2011).
ii. Identity Management. This is a fundamental principle of the data protections in
minimization of data. It is applied when we are seeking for authorization. Some of the
7
The following are some of the advantages and disadvantages of iris recognition (PBworks,
2009).
ADVANTAGES DISADVANTAGES
It is Recognized for its accuracy being very
high
It is very intrusive
The verification may even take less than five
seconds
It needs a lot of memory for storage of the
data
The eye of a person who is dead deteriorate
very fast to be used and hence no extra
precautions will need to be taken with retina
scans to be sure when the user is alive.
It is very expensive.
Areas of applications of iris recognition are such as the:
Finance and banking
Healthcare and welfare- been used in hospitals to track the patient registration and to Checkup
arrangement and scheduling.
Also they have been applied in immigration borders control
For public safety
Also used for point of sale and ATM
2.0 Privacy Enhancing Technologies Used on the Internet
There are no constant definitions of Privacy enhancing technologies (PET) but we can define
PET as the use of tech to help in achieving it comply with data protection legislature. The
business case to adopt PETs is very limited to the personal information confidentiality i.e. we
may see many technologies may refer to PETS protecting all the corporate confidential info and
protecting the revenues by securing the integrity of the data. The following are some of the PETs
used over the internet.
i. Encryption. The term encryption has been relatively applied in the technology that is
mature, however it is still in the state of advancing. Encryption in the internet as a
type of PET has supported the security and the proportionality the principles of data
protection law. A good example is the use of PCI DSS standard for the credit card
data which has been the latest and recent announcement by the United Kingdom data
protection regulators. It is good to know that encryption is always relatively simple
when implementing and it is always easy and a very effective tool (Brewer, 2011).
ii. Identity Management. This is a fundamental principle of the data protections in
minimization of data. It is applied when we are seeking for authorization. Some of the
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Subject Code Subject Name Semester Number
questions that we ask is that (do you have the right to perform such action?), (Who
are you?)Identity management may tend to empower people with the property of
cryptographic such as the conditional linkability where the users will have the consent
to any integration of their identities where the cryptography will make the mathematic
to be implausible and hence deducing the one identity from another in other contexts
(Goldberg, Wagner, & Brewer, 2017).
iii. The newest and one of the most recent and applied remailer technology which is a
type of PET is the use of Mixmaster and also known as Type II which has been used
as it provides the enhanced protection against the cases of eavesdropping attacks.
First we have to use chains and encrypts each links of the chain (james, 2018). Type
II remailers will use constant lengths by preventing the passive attacks that are
correlated where if the eavesdropper matches the up incoming an all outgoing
messages by size.
iv. The other latest Use Of PETS over the internet are such as the use of:
- Newnym-style Servers
- Use of message pools
- use of identifying headers and resend.
- Use of anonymous digital cash.
Example illustrating the use of PETs on the internet
For example, a consumer may be very willing to expose personal preferences about the purchase
of books on the Internet, but not about health-related goods.
For those wishing to avoid unwanted contact, the ideal business relationship is represented by a
single transaction that is neither tracked nor used as the basis for any further contact from the
merchant. Such buyers are most likely to reject merchants seeking a continuing relationship, or
merchants that require the creation and management of an account. These consumers would
prefer to have each transaction separate and isolated. Intrusive merchant practices, such as opt-
out email lists with difficult policies for subscription removal, are the bane of this consumer set.
8
questions that we ask is that (do you have the right to perform such action?), (Who
are you?)Identity management may tend to empower people with the property of
cryptographic such as the conditional linkability where the users will have the consent
to any integration of their identities where the cryptography will make the mathematic
to be implausible and hence deducing the one identity from another in other contexts
(Goldberg, Wagner, & Brewer, 2017).
iii. The newest and one of the most recent and applied remailer technology which is a
type of PET is the use of Mixmaster and also known as Type II which has been used
as it provides the enhanced protection against the cases of eavesdropping attacks.
First we have to use chains and encrypts each links of the chain (james, 2018). Type
II remailers will use constant lengths by preventing the passive attacks that are
correlated where if the eavesdropper matches the up incoming an all outgoing
messages by size.
iv. The other latest Use Of PETS over the internet are such as the use of:
- Newnym-style Servers
- Use of message pools
- use of identifying headers and resend.
- Use of anonymous digital cash.
Example illustrating the use of PETs on the internet
For example, a consumer may be very willing to expose personal preferences about the purchase
of books on the Internet, but not about health-related goods.
For those wishing to avoid unwanted contact, the ideal business relationship is represented by a
single transaction that is neither tracked nor used as the basis for any further contact from the
merchant. Such buyers are most likely to reject merchants seeking a continuing relationship, or
merchants that require the creation and management of an account. These consumers would
prefer to have each transaction separate and isolated. Intrusive merchant practices, such as opt-
out email lists with difficult policies for subscription removal, are the bane of this consumer set.
8

Subject Code Subject Name Semester Number
3.0 Wireless Sensor Networks
There are many security attacking the Wireless sensor networks. There are three types of attacks:
- Attacks on the secrecy and authentication. These are the standard cryptography
techniques protecting the secrecy and authenticating the communication channels from
attacks outsides such as eavesdropping, and the packet replay attacks.
- Attacks on the Availability of the network this are referred to as the denial-of-service
(DoS) attacks.
- Stealthy attack that is against the integrity of the service.
DoS attacks are the attacks that diminishes or attempts in reducing the network’s capacity in
performing the expected function (Estrin, 2002). The following are some of the major attacks of
DOS in WSN.
i. Physical Layer Attacks- it is responsible for the selection of frequency, modulation an
encryption of data.
ii. Link layer attacks- it is responsible for multiplexing of streaming data, detection of
data frame, medium access control and controlling errors.
iii. Network Layer attacks- this is a layer that attacks the WSN and this has been made
vulnerable and is of different types such as the:
- Spoofed-routing-information
- Wormhole
- Sybil attack
- Selective forwarding
- Acknowledgement spoofing
iv. Transport layer attacks- which are launched on the layer of transport of the WSN
such as the following:
- Flooding
- De-synchronization
- Analysis of Traffic
- Camouflage
The following are some of the recommendations on how the threats and the vulnerabilities can
be mitigated for Wireless Sensor Networks.
9
3.0 Wireless Sensor Networks
There are many security attacking the Wireless sensor networks. There are three types of attacks:
- Attacks on the secrecy and authentication. These are the standard cryptography
techniques protecting the secrecy and authenticating the communication channels from
attacks outsides such as eavesdropping, and the packet replay attacks.
- Attacks on the Availability of the network this are referred to as the denial-of-service
(DoS) attacks.
- Stealthy attack that is against the integrity of the service.
DoS attacks are the attacks that diminishes or attempts in reducing the network’s capacity in
performing the expected function (Estrin, 2002). The following are some of the major attacks of
DOS in WSN.
i. Physical Layer Attacks- it is responsible for the selection of frequency, modulation an
encryption of data.
ii. Link layer attacks- it is responsible for multiplexing of streaming data, detection of
data frame, medium access control and controlling errors.
iii. Network Layer attacks- this is a layer that attacks the WSN and this has been made
vulnerable and is of different types such as the:
- Spoofed-routing-information
- Wormhole
- Sybil attack
- Selective forwarding
- Acknowledgement spoofing
iv. Transport layer attacks- which are launched on the layer of transport of the WSN
such as the following:
- Flooding
- De-synchronization
- Analysis of Traffic
- Camouflage
The following are some of the recommendations on how the threats and the vulnerabilities can
be mitigated for Wireless Sensor Networks.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Subject Code Subject Name Semester Number
i. Encryption: most WSN have held very open areas that are very dangerously and
susceptible to the attacks over the network. If we apply encryption then we can
protect WSN such as the key message code authenticated, symmetric encryption and
the public key cryptography.]
ii. Data Partitioning: the idea here is giving a separate data in networks in to some parts.
The recommendation given by Deng is that data partitioning will give a solution that
will ensure that all the attackers cannot have possession of the information.
iii. Secure Data Aggregation: transmission of data in WSN has increased than it was
there before. This has resulted to us having most issues in network data traffic and
this leading to rise in cost. For the reduction of high cost and network traffic, WSN
has aggregated the measurements before they are transferred to the station at the base
(Pathan, 2006). The recommendations is that the locations of the aggregation should
always be secure.
iv. Cryptography and shared Keys.
s
List of References
Brewer, I. G. (2011). . Privacy-enhancing technologies (PETs. Berkeley: University of California.
Estrin, D. B. (2002). "Rumor routing algorithm for sensor networks. In Proceedings of the 1st ACM
International Workshop on Wireless Sensor Networks and Applications (pp. 22-31). New York,
USA: ACM press.
Goldberg, I., Wagner, D., & Brewer, E. (2017). Privacy-enhancing technologies for the Internet. San
Jose: IEEE.
james, K. (2018, March 07). A tool on Privacy Enhancing Technologies (PETs) knowledge... Retrieved
from ENISA European Union Agency for :
https://www.enisa.europa.eu/topics/data-protection/privacy-enhancing-technologies
Lancho, A. G. (2017, June 21). Neural Networks Applied to Fingerprint Recognition. Retrieved from
Multi-layer perceptron neural network with learning algorithm retropropagation errors, for
application in fingerprint recognition.: https://link.springer.com/chapter/10.1007/978-3-642-
02481-8_91
10
i. Encryption: most WSN have held very open areas that are very dangerously and
susceptible to the attacks over the network. If we apply encryption then we can
protect WSN such as the key message code authenticated, symmetric encryption and
the public key cryptography.]
ii. Data Partitioning: the idea here is giving a separate data in networks in to some parts.
The recommendation given by Deng is that data partitioning will give a solution that
will ensure that all the attackers cannot have possession of the information.
iii. Secure Data Aggregation: transmission of data in WSN has increased than it was
there before. This has resulted to us having most issues in network data traffic and
this leading to rise in cost. For the reduction of high cost and network traffic, WSN
has aggregated the measurements before they are transferred to the station at the base
(Pathan, 2006). The recommendations is that the locations of the aggregation should
always be secure.
iv. Cryptography and shared Keys.
s
List of References
Brewer, I. G. (2011). . Privacy-enhancing technologies (PETs. Berkeley: University of California.
Estrin, D. B. (2002). "Rumor routing algorithm for sensor networks. In Proceedings of the 1st ACM
International Workshop on Wireless Sensor Networks and Applications (pp. 22-31). New York,
USA: ACM press.
Goldberg, I., Wagner, D., & Brewer, E. (2017). Privacy-enhancing technologies for the Internet. San
Jose: IEEE.
james, K. (2018, March 07). A tool on Privacy Enhancing Technologies (PETs) knowledge... Retrieved
from ENISA European Union Agency for :
https://www.enisa.europa.eu/topics/data-protection/privacy-enhancing-technologies
Lancho, A. G. (2017, June 21). Neural Networks Applied to Fingerprint Recognition. Retrieved from
Multi-layer perceptron neural network with learning algorithm retropropagation errors, for
application in fingerprint recognition.: https://link.springer.com/chapter/10.1007/978-3-642-
02481-8_91
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Subject Code Subject Name Semester Number
Pathan, A. S.-W. (2006). Security in Wireless Sensor Networks: Issues and Challenges” . Hongkong:
Advanced Communication Technology (ICACT).
PBworks. (2009). Advantages and disadvantages of technologies. iris recognition, 11-17.
Sanchez-Reillo, R., Sanchez-Avila, C., & Gonzalez-Marcos, A. (2000). Biometric identification through
hand geometry measurements. IEEE Transactions on Pattern Analysis and Machine Intelligence,
1168 - 1171.
University, P. (2018). MS in Biometrics(Online). Retrieved Aug 15, 2018, from international Center for
Biometric Research: https://polytechnic.purdue.edu/degrees/ms-biometrics-online
11
Pathan, A. S.-W. (2006). Security in Wireless Sensor Networks: Issues and Challenges” . Hongkong:
Advanced Communication Technology (ICACT).
PBworks. (2009). Advantages and disadvantages of technologies. iris recognition, 11-17.
Sanchez-Reillo, R., Sanchez-Avila, C., & Gonzalez-Marcos, A. (2000). Biometric identification through
hand geometry measurements. IEEE Transactions on Pattern Analysis and Machine Intelligence,
1168 - 1171.
University, P. (2018). MS in Biometrics(Online). Retrieved Aug 15, 2018, from international Center for
Biometric Research: https://polytechnic.purdue.edu/degrees/ms-biometrics-online
11
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





