Biometric Systems, Privacy Enhancing Technologies, and Wireless Sensor Networks
VerifiedAdded on 2024/07/01
|12
|1948
|470
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

ITC – 596
Assignment - 2
1
Assignment - 2
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
(a) Biometric Systems................................................................................................................ 4
Fingerprint Recognition System............................................................................................4
Hand Geometry recognition system.......................................................................................6
Iris Recognition...................................................................................................................... 6
(b) Privacy enhancing technologies...........................................................................................8
(a) Wireless Sensor Networks.................................................................................................... 9
References................................................................................................................................ 12
2
(a) Biometric Systems................................................................................................................ 4
Fingerprint Recognition System............................................................................................4
Hand Geometry recognition system.......................................................................................6
Iris Recognition...................................................................................................................... 6
(b) Privacy enhancing technologies...........................................................................................8
(a) Wireless Sensor Networks.................................................................................................... 9
References................................................................................................................................ 12
2

List of Figures
Figure 1 Fingerprint biometric system....................................................................................... 5
Figure 2 Iris recognition system.................................................................................................7
Figure 3 WSN architecture.......................................................................................................10
3
Figure 1 Fingerprint biometric system....................................................................................... 5
Figure 2 Iris recognition system.................................................................................................7
Figure 3 WSN architecture.......................................................................................................10
3

(a) Biometric Systems
These are the technological systems which make use of the knowledge about any person in
order to identify the person. They highly depend on the particular data related to the
biological traits which are unique so as to work more effectively. The biometric systems use
algorithms to identify the user or an individual. The algorithms use biological data in the
processing. The technology has changed the identification process of the people and at the
same time reducing the time used in the verification and identification process. Following are
the types of the biometric systems:
Facial recognition
Iris recognition
Hand geometry recognition
DNA recognition
Fingerprint recognition
Speaker recognition
Signature recognition, etc.
Fingerprint Recognition System
The individuals are identified using their fingerprints. The block diagram of the working of a
fingerprint recognition system is given with this.
1. Fingerprint sensor: This sensor captures the digital image of the patterns of the
fingerprint. This is usually an electronic device. The image is called as live scan
which gets captured by the sensor. Then this live scan gets processed digitally and
biometric template of that fingerprint scan is created. Then this is stored in a database
and then at the time of verification and identification, these are used.
2. Image processing: This is the second stage of the fingerprint biometric system. This
step extracts the minutiae from the fingerprint scanned. This highly depends on the
quality of the image.
3. Minutia processing: The crossing number method is used for the extraction of the
minutia. A 3*3 window is used for extracting the minutia.
4. Minutia match: Minutia algorithm determines if the set of two minutia are similar or
not.
4
These are the technological systems which make use of the knowledge about any person in
order to identify the person. They highly depend on the particular data related to the
biological traits which are unique so as to work more effectively. The biometric systems use
algorithms to identify the user or an individual. The algorithms use biological data in the
processing. The technology has changed the identification process of the people and at the
same time reducing the time used in the verification and identification process. Following are
the types of the biometric systems:
Facial recognition
Iris recognition
Hand geometry recognition
DNA recognition
Fingerprint recognition
Speaker recognition
Signature recognition, etc.
Fingerprint Recognition System
The individuals are identified using their fingerprints. The block diagram of the working of a
fingerprint recognition system is given with this.
1. Fingerprint sensor: This sensor captures the digital image of the patterns of the
fingerprint. This is usually an electronic device. The image is called as live scan
which gets captured by the sensor. Then this live scan gets processed digitally and
biometric template of that fingerprint scan is created. Then this is stored in a database
and then at the time of verification and identification, these are used.
2. Image processing: This is the second stage of the fingerprint biometric system. This
step extracts the minutiae from the fingerprint scanned. This highly depends on the
quality of the image.
3. Minutia processing: The crossing number method is used for the extraction of the
minutia. A 3*3 window is used for extracting the minutia.
4. Minutia match: Minutia algorithm determines if the set of two minutia are similar or
not.
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
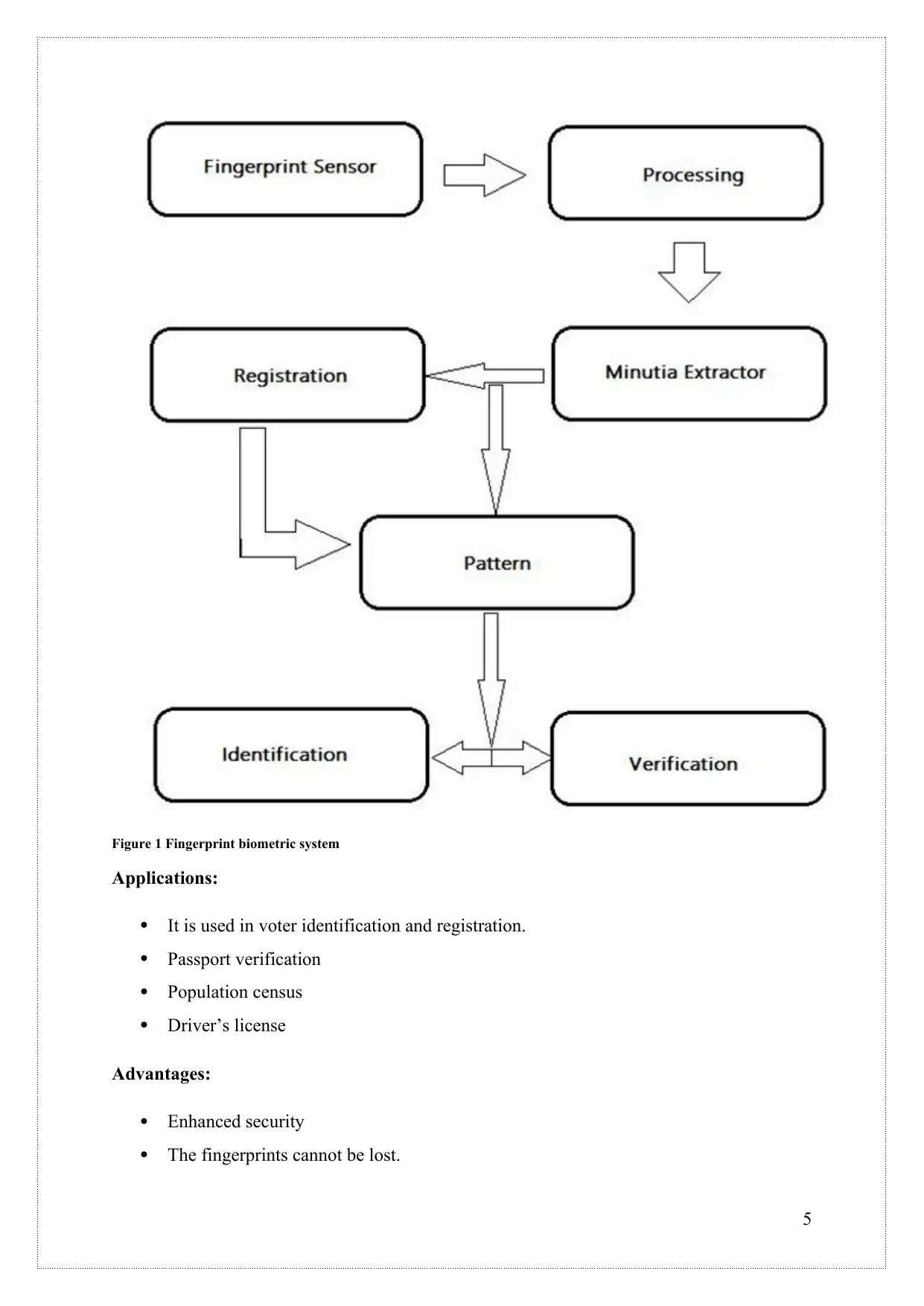
Figure 1 Fingerprint biometric system
Applications:
It is used in voter identification and registration.
Passport verification
Population census
Driver’s license
Advantages:
Enhanced security
The fingerprints cannot be lost.
5
Applications:
It is used in voter identification and registration.
Passport verification
Population census
Driver’s license
Advantages:
Enhanced security
The fingerprints cannot be lost.
5

Less cost for operation.
Better user experience.
Disadvantages:
They do not ensure 100% accuracy.
The measurements can get affected by the usage or environments.
They require additional hardware (Erden, 2016).
Hand Geometry recognition system
This recognition method is the largest implementation method since the 1980s. For the ease
of use, acceptance and easy implementation methods, this method is more implemented. The
concept of biometric was developed by David Sidlaukas. This was first used in the Olympic
games of 1996 so as to control the access to Olympic village. In many companies, it is used
for marking attendance as well. This method uses the concept of recording and measuring the
surface area, thickness, width, and length of a person’s hand. Then the method uses a camera
so as to capture the hand image. Then on the image, about 31000 points get analyzed &
around 90 measurements are then taken. This data is. stored in the nine-byte data.
Advantages:
This is a simple and easy method.
It is an inexpensive method.
The geometry of hand can be easily collected.
Environmental factors do not create any issue.
Disadvantages
The geometries of the hand are not unique.
This system is not effective for the case of children (Das, 2018).
Iris Recognition
This method uses the techniques of recognizing patterns which are based on the distortion
free and high-resolution images of iris present in the eyes of the human. Iris is the part of the
human eye which remains constant throughout the life. That’s why this is used for
identification of the person. And is, therefore, a trusted method.
6
Better user experience.
Disadvantages:
They do not ensure 100% accuracy.
The measurements can get affected by the usage or environments.
They require additional hardware (Erden, 2016).
Hand Geometry recognition system
This recognition method is the largest implementation method since the 1980s. For the ease
of use, acceptance and easy implementation methods, this method is more implemented. The
concept of biometric was developed by David Sidlaukas. This was first used in the Olympic
games of 1996 so as to control the access to Olympic village. In many companies, it is used
for marking attendance as well. This method uses the concept of recording and measuring the
surface area, thickness, width, and length of a person’s hand. Then the method uses a camera
so as to capture the hand image. Then on the image, about 31000 points get analyzed &
around 90 measurements are then taken. This data is. stored in the nine-byte data.
Advantages:
This is a simple and easy method.
It is an inexpensive method.
The geometry of hand can be easily collected.
Environmental factors do not create any issue.
Disadvantages
The geometries of the hand are not unique.
This system is not effective for the case of children (Das, 2018).
Iris Recognition
This method uses the techniques of recognizing patterns which are based on the distortion
free and high-resolution images of iris present in the eyes of the human. Iris is the part of the
human eye which remains constant throughout the life. That’s why this is used for
identification of the person. And is, therefore, a trusted method.
6
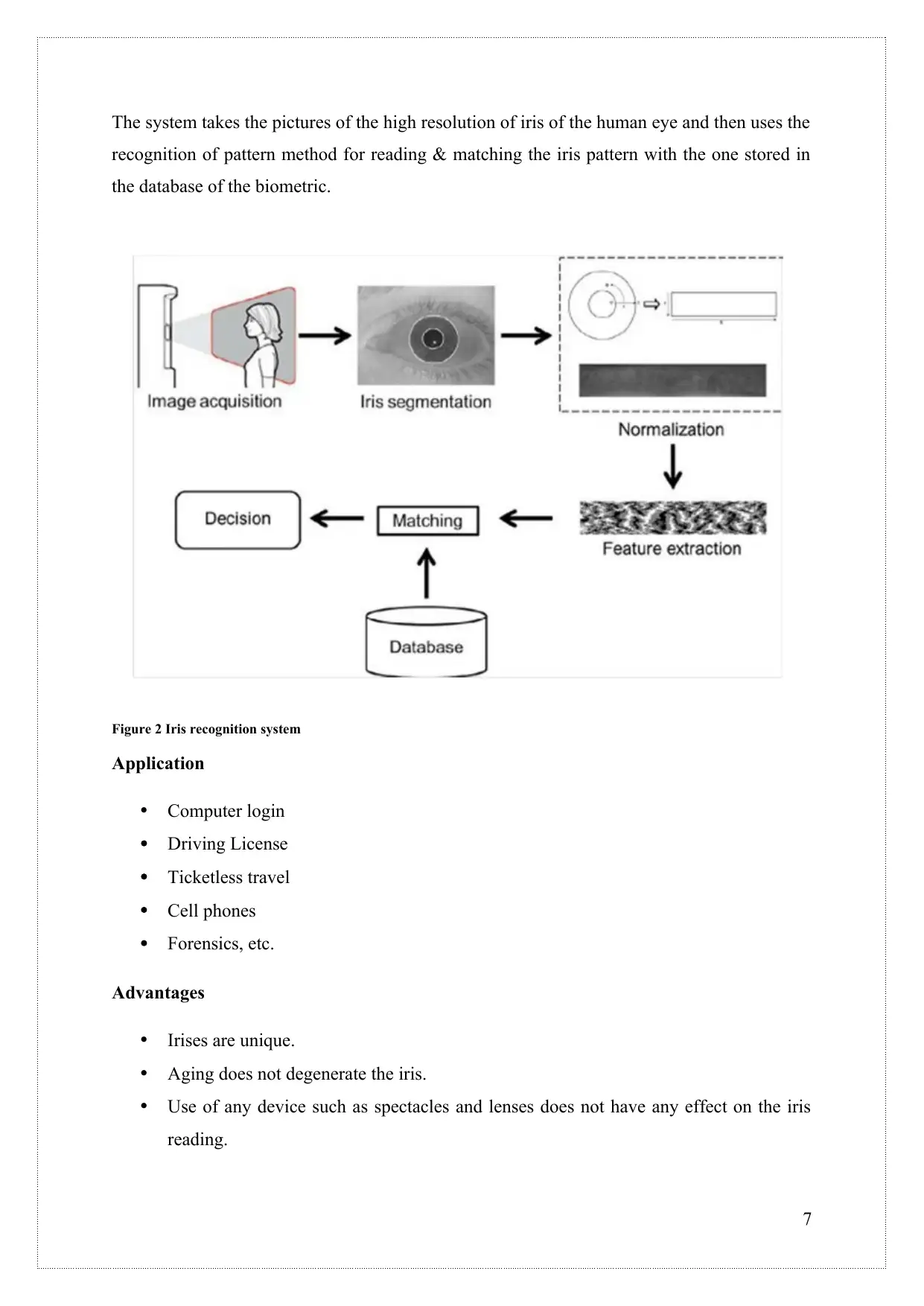
The system takes the pictures of the high resolution of iris of the human eye and then uses the
recognition of pattern method for reading & matching the iris pattern with the one stored in
the database of the biometric.
Figure 2 Iris recognition system
Application
Computer login
Driving License
Ticketless travel
Cell phones
Forensics, etc.
Advantages
Irises are unique.
Aging does not degenerate the iris.
Use of any device such as spectacles and lenses does not have any effect on the iris
reading.
7
recognition of pattern method for reading & matching the iris pattern with the one stored in
the database of the biometric.
Figure 2 Iris recognition system
Application
Computer login
Driving License
Ticketless travel
Cell phones
Forensics, etc.
Advantages
Irises are unique.
Aging does not degenerate the iris.
Use of any device such as spectacles and lenses does not have any effect on the iris
reading.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Disadvantages
There can be some connotations which are negative.
It is behind a curved and wet surface (Dascalescu, 2018).
(b) Privacy enhancing technologies
It is a standardized term used to specify the methods that work according to laws of
protection of data. The PET allows the users on the internet to have their private data
protected. It ensures the confidentiality of the data. Its main aim is to have an increased
control over the private data that is being sent and used online by various service providers
and users. It minimizes the use of private data that gets collected. The three PETs are as
under:
Private Payments
Anti-Phishing tools
Private credentials
Private Payments: Currently we do not have any serious online cash services. It is very
necessary for us to have that gap filled by applying the PET. So it is necessary to have a
centralized record of almost everything. But today these records are being stolen from the
databases of merchants or from firms that do processing of credit cards. The loss occurred
due to this, is causing identity theft and frauds in credit cards. At the same time, the
transactions done online vis PayPal etc are getting more popular. The Paypal provides the
interface in between financial system and electronic cash.
Anti-phishing tools: Phishing occurs when a user gets redirected to a website that is
malicious. This site is similar to any common website, by appearance. But in reality, it is
being run by some attacker. The instruction on the website makes users enter their private
details which get captured by the hacker and this data may be used for theft. The anti-
phishing tools provide the user an authentic website. This helps the user in identifying a
malicious website.
Private credentials: This separates authentication and authorization from each other. These
allow users the ability to prove themselves that they have authorized access to something and
at the same time not reviling any of their private information (Bodó, 2014).
8
There can be some connotations which are negative.
It is behind a curved and wet surface (Dascalescu, 2018).
(b) Privacy enhancing technologies
It is a standardized term used to specify the methods that work according to laws of
protection of data. The PET allows the users on the internet to have their private data
protected. It ensures the confidentiality of the data. Its main aim is to have an increased
control over the private data that is being sent and used online by various service providers
and users. It minimizes the use of private data that gets collected. The three PETs are as
under:
Private Payments
Anti-Phishing tools
Private credentials
Private Payments: Currently we do not have any serious online cash services. It is very
necessary for us to have that gap filled by applying the PET. So it is necessary to have a
centralized record of almost everything. But today these records are being stolen from the
databases of merchants or from firms that do processing of credit cards. The loss occurred
due to this, is causing identity theft and frauds in credit cards. At the same time, the
transactions done online vis PayPal etc are getting more popular. The Paypal provides the
interface in between financial system and electronic cash.
Anti-phishing tools: Phishing occurs when a user gets redirected to a website that is
malicious. This site is similar to any common website, by appearance. But in reality, it is
being run by some attacker. The instruction on the website makes users enter their private
details which get captured by the hacker and this data may be used for theft. The anti-
phishing tools provide the user an authentic website. This helps the user in identifying a
malicious website.
Private credentials: This separates authentication and authorization from each other. These
allow users the ability to prove themselves that they have authorized access to something and
at the same time not reviling any of their private information (Bodó, 2014).
8

(a) Wireless Sensor Networks
It is a standard service used in industrial applications and in commercial applications. This is
because of its development in the processor, embedded devices, and communications. It is
built using nodes which observes the environment such as temperature, pressure, humidity
etc. The nodes are also used in different applications of real time so that they can perform
activities such as smart detection, data collection, synchronization etc. It is basically a kind of
wireless network consisting of nodes.
Characteristics:
The failure of nodes can be handled.
Consist of cross-layer design.
Easy to use.
More Scalable
Applications:
Health Application
Home Application
Area monitoring
Landslide detection
Military Application
Environmental application
Industrial monitoring
Commercial applications, etc.
Advantages:
The arrangements of the network can be done without the use of immovable
infrastructures.
This is flexible.
It can accommodate any device, any time.
It is able to be opened with centralized monitoring.
9
It is a standard service used in industrial applications and in commercial applications. This is
because of its development in the processor, embedded devices, and communications. It is
built using nodes which observes the environment such as temperature, pressure, humidity
etc. The nodes are also used in different applications of real time so that they can perform
activities such as smart detection, data collection, synchronization etc. It is basically a kind of
wireless network consisting of nodes.
Characteristics:
The failure of nodes can be handled.
Consist of cross-layer design.
Easy to use.
More Scalable
Applications:
Health Application
Home Application
Area monitoring
Landslide detection
Military Application
Environmental application
Industrial monitoring
Commercial applications, etc.
Advantages:
The arrangements of the network can be done without the use of immovable
infrastructures.
This is flexible.
It can accommodate any device, any time.
It is able to be opened with centralized monitoring.
9
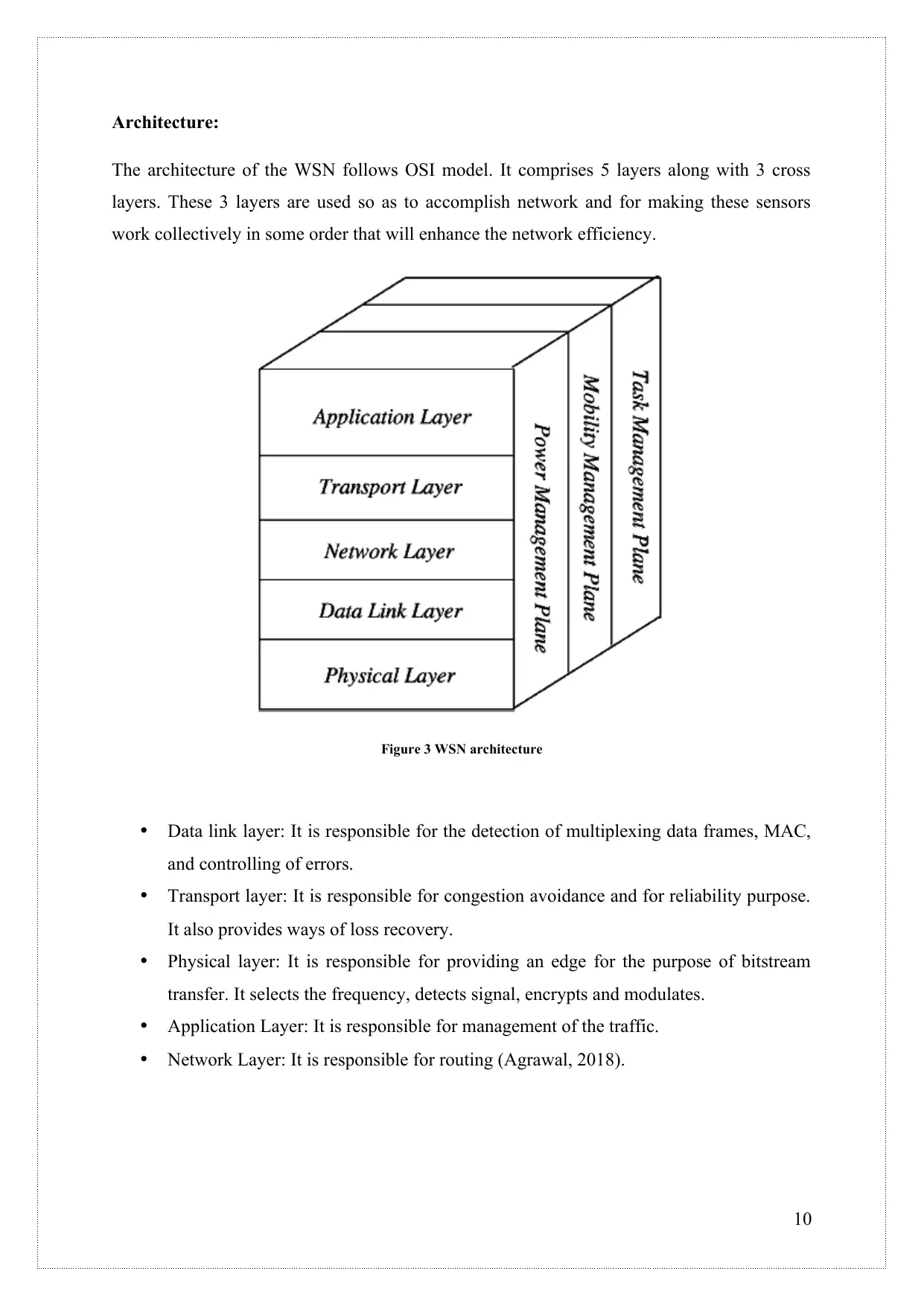
Architecture:
The architecture of the WSN follows OSI model. It comprises 5 layers along with 3 cross
layers. These 3 layers are used so as to accomplish network and for making these sensors
work collectively in some order that will enhance the network efficiency.
Figure 3 WSN architecture
Data link layer: It is responsible for the detection of multiplexing data frames, MAC,
and controlling of errors.
Transport layer: It is responsible for congestion avoidance and for reliability purpose.
It also provides ways of loss recovery.
Physical layer: It is responsible for providing an edge for the purpose of bitstream
transfer. It selects the frequency, detects signal, encrypts and modulates.
Application Layer: It is responsible for management of the traffic.
Network Layer: It is responsible for routing (Agrawal, 2018).
10
The architecture of the WSN follows OSI model. It comprises 5 layers along with 3 cross
layers. These 3 layers are used so as to accomplish network and for making these sensors
work collectively in some order that will enhance the network efficiency.
Figure 3 WSN architecture
Data link layer: It is responsible for the detection of multiplexing data frames, MAC,
and controlling of errors.
Transport layer: It is responsible for congestion avoidance and for reliability purpose.
It also provides ways of loss recovery.
Physical layer: It is responsible for providing an edge for the purpose of bitstream
transfer. It selects the frequency, detects signal, encrypts and modulates.
Application Layer: It is responsible for management of the traffic.
Network Layer: It is responsible for routing (Agrawal, 2018).
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Types of threats:
1. Denial of service:
This occurs when nodes get failed unintentionally or through some malicious
attack. In this attack, the attacker attempts to destroy the network. It eventually
decreases the capacity of the network. Any simple DOS attack will try to
absorb the resources by sending some extra and unnecessary packets in the
network.
This can be defended by reducing the false rate of the alarm
2. Tampering:
This is done in the physical layer of the model. When the attacker gets the
physical access to the data then he becomes able to extract the private data
such as private keys etc.
This attack can be defended by utilizing tamper proofing method at the
physical package of the node.
3. Jamming:
This attack is also done at the physical layer. The jamming interferes with the
radio frequencies of the network. The source jamming can be powerful enough
to destroy the whole network or can be less powerful that it can only destroy a
small portion of the network only.
To overcome this, code spreading and frequency hopping can be done (Bilal,
2015).
11
1. Denial of service:
This occurs when nodes get failed unintentionally or through some malicious
attack. In this attack, the attacker attempts to destroy the network. It eventually
decreases the capacity of the network. Any simple DOS attack will try to
absorb the resources by sending some extra and unnecessary packets in the
network.
This can be defended by reducing the false rate of the alarm
2. Tampering:
This is done in the physical layer of the model. When the attacker gets the
physical access to the data then he becomes able to extract the private data
such as private keys etc.
This attack can be defended by utilizing tamper proofing method at the
physical package of the node.
3. Jamming:
This attack is also done at the physical layer. The jamming interferes with the
radio frequencies of the network. The source jamming can be powerful enough
to destroy the whole network or can be less powerful that it can only destroy a
small portion of the network only.
To overcome this, code spreading and frequency hopping can be done (Bilal,
2015).
11

References
1. Erden, M. (2016). Advantages and Disadvantages of Biometric Authentication |
SESTEK Blog. Retrieved from http://www.sestek.com/2016/11/advantages-
disadvantages-biometric-authentication/
2. Das, R. (2018). The Oldest Biometric of All – Hand Geometry Recognition. Retrieved
from https://resources.infosecinstitute.com/oldest-biometric-hand-geometry-recognition/#gref
3. Dascalescu, A. (2018). Biometric Authentication Overview, Advantages &
Disadvantages. Retrieved from https://heimdalsecurity.com/blog/biometric-authentication/
4. Bodó, B. (2014). Hacktivism 1-2-3: how privacy enhancing technologies change the
face of anonymous hacktivism. Retrieved from
https://policyreview.info/articles/analysis/hacktivism-1-2-3-how-privacy-enhancing-
technologies-change-face-anonymous
5. Agrawal, T. (2018). Wireless Sensor Network (WSN) Architecture And Applications.
Retrieved from https://www.elprocus.com/architecture-of-wireless-sensor-network-and-
applications/
6. Bilal. (2015). WIRELESS SENSOR NETWORKS and APPLICATIONS. Retrieved
from http://microcontrollerslab.com/wireless-sensor-networks-wsn-applications/
12
1. Erden, M. (2016). Advantages and Disadvantages of Biometric Authentication |
SESTEK Blog. Retrieved from http://www.sestek.com/2016/11/advantages-
disadvantages-biometric-authentication/
2. Das, R. (2018). The Oldest Biometric of All – Hand Geometry Recognition. Retrieved
from https://resources.infosecinstitute.com/oldest-biometric-hand-geometry-recognition/#gref
3. Dascalescu, A. (2018). Biometric Authentication Overview, Advantages &
Disadvantages. Retrieved from https://heimdalsecurity.com/blog/biometric-authentication/
4. Bodó, B. (2014). Hacktivism 1-2-3: how privacy enhancing technologies change the
face of anonymous hacktivism. Retrieved from
https://policyreview.info/articles/analysis/hacktivism-1-2-3-how-privacy-enhancing-
technologies-change-face-anonymous
5. Agrawal, T. (2018). Wireless Sensor Network (WSN) Architecture And Applications.
Retrieved from https://www.elprocus.com/architecture-of-wireless-sensor-network-and-
applications/
6. Bilal. (2015). WIRELESS SENSOR NETWORKS and APPLICATIONS. Retrieved
from http://microcontrollerslab.com/wireless-sensor-networks-wsn-applications/
12
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





