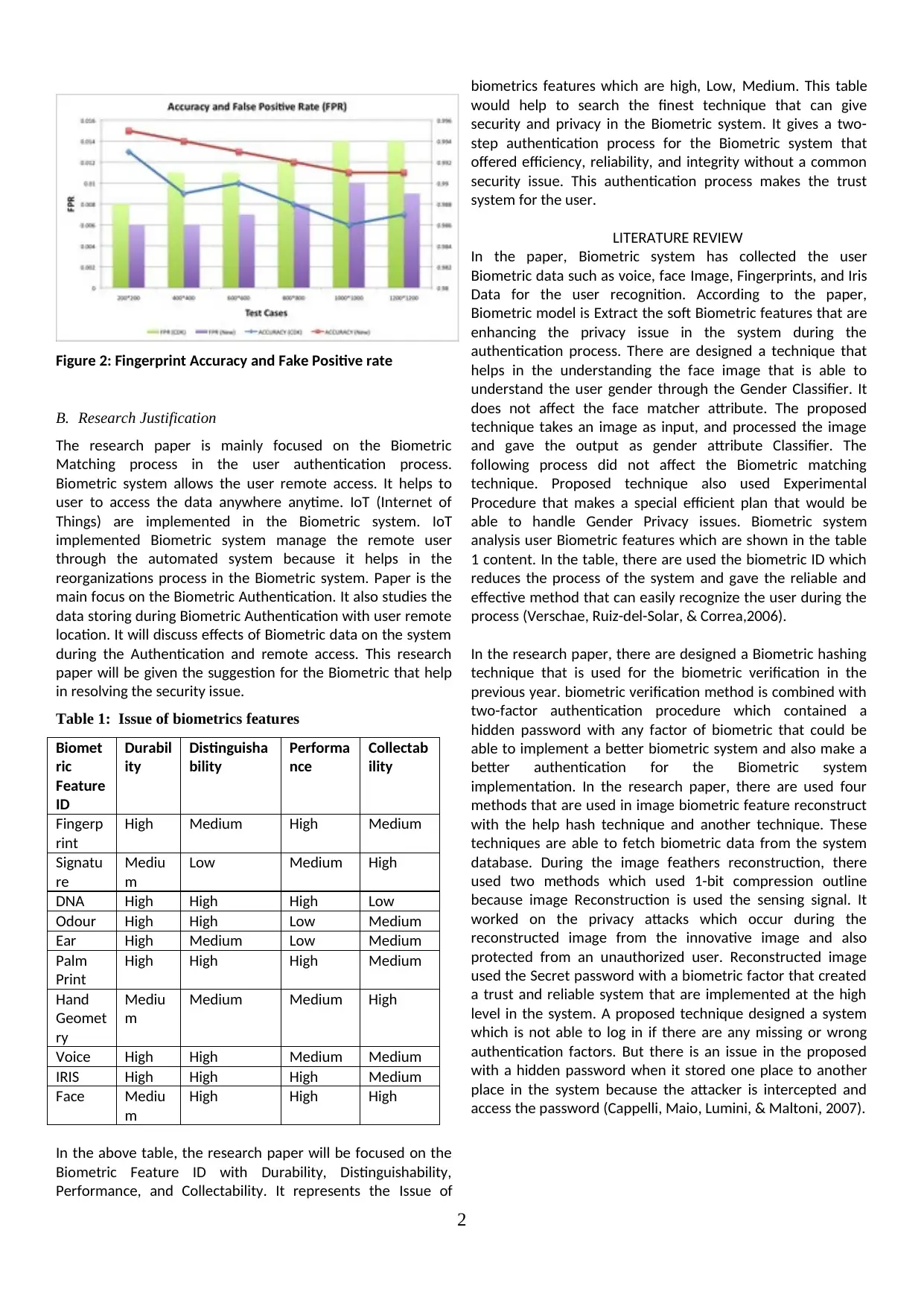
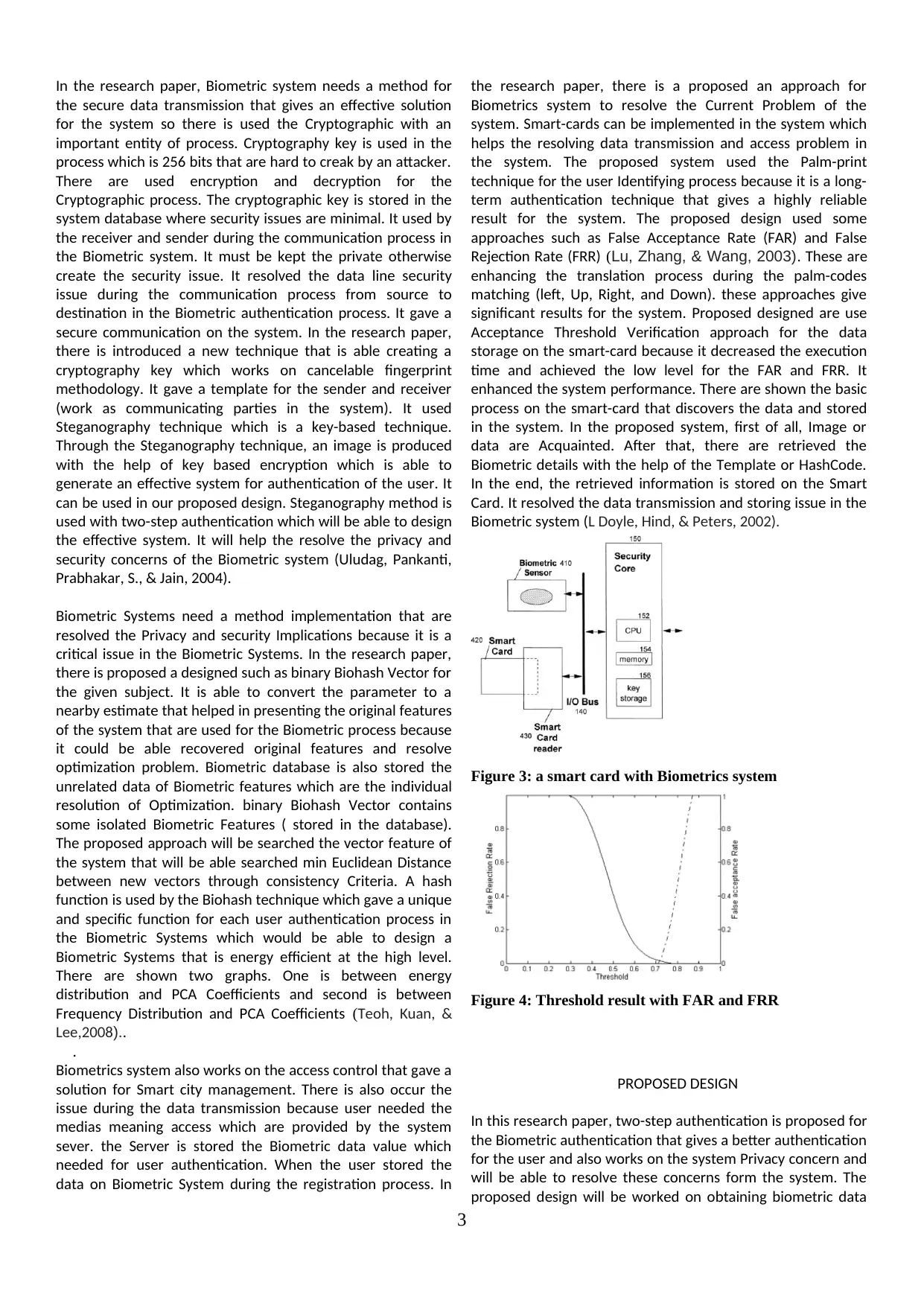
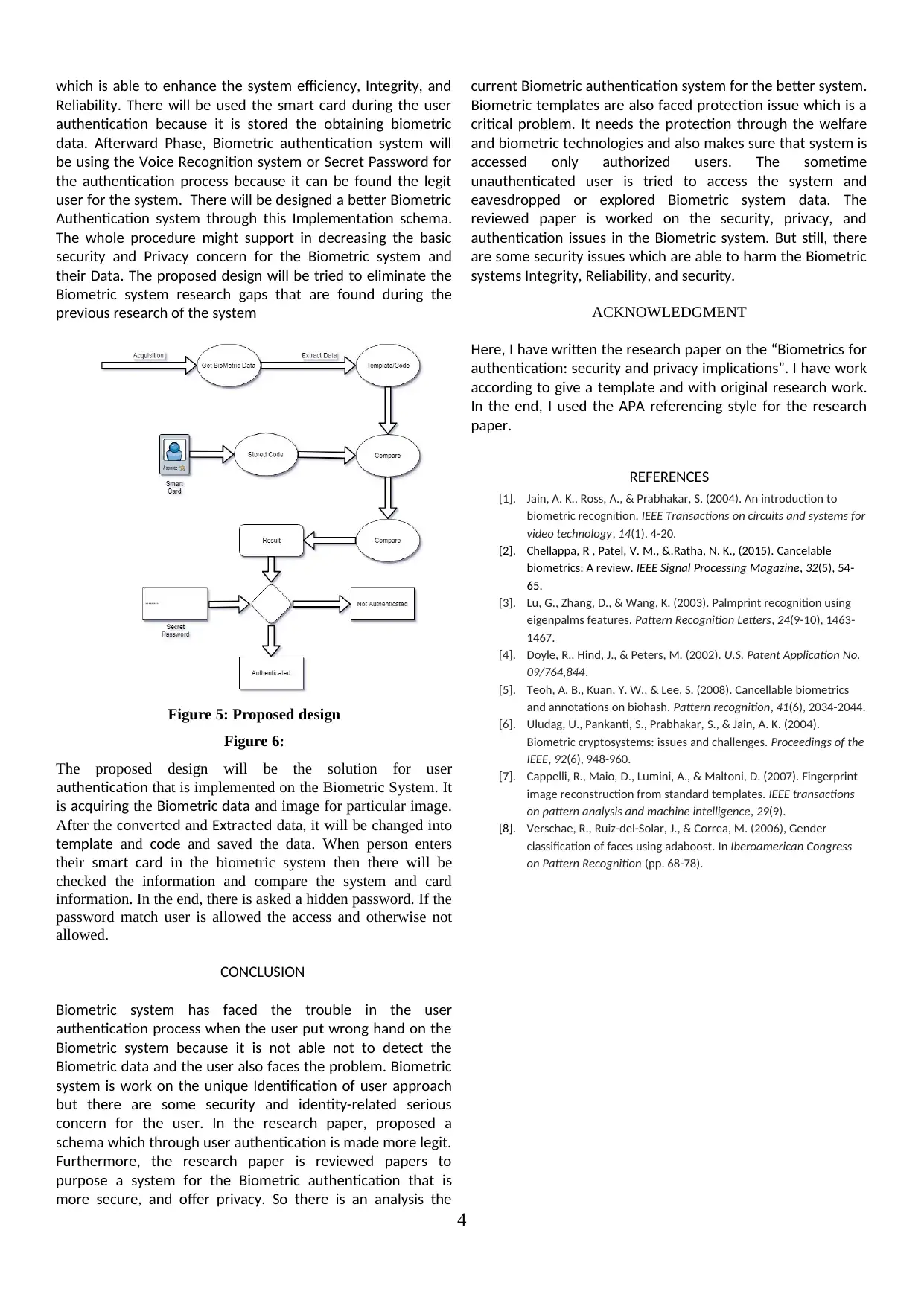
This research paper investigates the security and privacy implications of biometric authentication systems. It explores the challenges posed by advanced technology attacks and the need for robust security measures to protect sensitive user data. The paper proposes a two-step authentication process that combines biometric recognition with voice recognition or a secret password, aiming to enhance the security and reliability of biometric systems. It also examines various techniques for data protection, including cryptography, steganography, and smart card implementation. The research highlights the importance of addressing privacy concerns related to biometric data collection and storage, emphasizing the need for secure data transmission and access control mechanisms. The paper concludes by presenting a proposed design for a more secure and privacy-aware biometric authentication system.
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)