Block-Chain Enabled Applications | Security Investigation Paper
VerifiedAdded on 2022/09/06
|9
|1976
|14
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: SECURITY
0
Block-chain enabled applications
Security Investigation paper
(Student Details: )
4/10/2020
0
Block-chain enabled applications
Security Investigation paper
(Student Details: )
4/10/2020
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

SECURITY 1
Contents
Part 1: Abstract...........................................................................................................................2
Part 2: Security of blockchain-enabled applications (BCA) 1200.............................................3
Introduction................................................................................................................................3
Highlighting the challenges or problems in BCA......................................................................4
Scalability...............................................................................................................................4
Lack of interoperability..........................................................................................................4
Lack of blockchain talent.......................................................................................................4
Integration with legacy systems.............................................................................................5
Discussing issues addressed in the current literature.................................................................5
Highlighting issues not addressed..............................................................................................5
Discussing personal view on the issues.....................................................................................6
Conclusion..................................................................................................................................6
References..................................................................................................................................8
Contents
Part 1: Abstract...........................................................................................................................2
Part 2: Security of blockchain-enabled applications (BCA) 1200.............................................3
Introduction................................................................................................................................3
Highlighting the challenges or problems in BCA......................................................................4
Scalability...............................................................................................................................4
Lack of interoperability..........................................................................................................4
Lack of blockchain talent.......................................................................................................4
Integration with legacy systems.............................................................................................5
Discussing issues addressed in the current literature.................................................................5
Highlighting issues not addressed..............................................................................................5
Discussing personal view on the issues.....................................................................................6
Conclusion..................................................................................................................................6
References..................................................................................................................................8

SECURITY 2
Part 1: Abstract
The research paper is based on investigating the security of Blockchain-enabled
Applications (BCA). The topic has been selected as the key area for the research project
because Blockchain Technology (BT) has become essentially important as it allows people to
own digital assets, goods, and data efficiently. In this era, BT could be further revolutionized
through retail experiences for loyalty rewards. Modern businesses are using BCA at a large
level so as to make their business efficient, effective and adaptable as per the millennial
generation. While using BCA for business development and growth, and personal use by the
users, some key issues are being faced by both business developers and BCA users. The key
issues may include technical scalability, slow-moving adoption, limited interoperability,
insufficient standardization and most importantly the security of the data and information
shared with the BCAs. Thus, the paper has conducted in-depth research on security issues of
BCAs in a real-life context. It has been found that key possible solutions to these security
issues in blockchain-based applications can be found out only by assessing and integrating
diverse sectors such as business, supply chain, healthcare, privacy, IoT, and effective data
management within block-chain based applications.
Part 1: Abstract
The research paper is based on investigating the security of Blockchain-enabled
Applications (BCA). The topic has been selected as the key area for the research project
because Blockchain Technology (BT) has become essentially important as it allows people to
own digital assets, goods, and data efficiently. In this era, BT could be further revolutionized
through retail experiences for loyalty rewards. Modern businesses are using BCA at a large
level so as to make their business efficient, effective and adaptable as per the millennial
generation. While using BCA for business development and growth, and personal use by the
users, some key issues are being faced by both business developers and BCA users. The key
issues may include technical scalability, slow-moving adoption, limited interoperability,
insufficient standardization and most importantly the security of the data and information
shared with the BCAs. Thus, the paper has conducted in-depth research on security issues of
BCAs in a real-life context. It has been found that key possible solutions to these security
issues in blockchain-based applications can be found out only by assessing and integrating
diverse sectors such as business, supply chain, healthcare, privacy, IoT, and effective data
management within block-chain based applications.
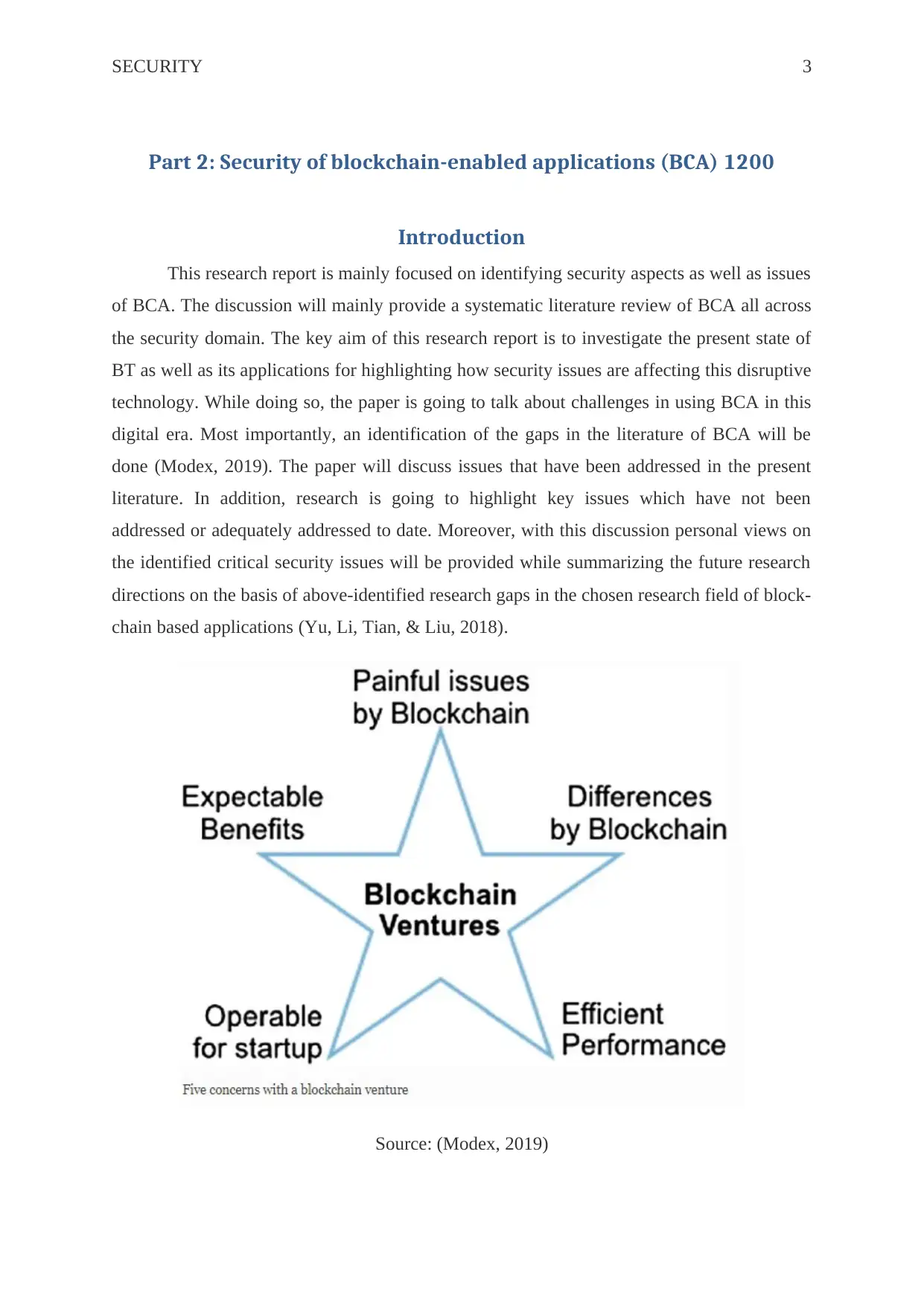
SECURITY 3
Part 2: Security of blockchain-enabled applications (BCA) 1200
Introduction
This research report is mainly focused on identifying security aspects as well as issues
of BCA. The discussion will mainly provide a systematic literature review of BCA all across
the security domain. The key aim of this research report is to investigate the present state of
BT as well as its applications for highlighting how security issues are affecting this disruptive
technology. While doing so, the paper is going to talk about challenges in using BCA in this
digital era. Most importantly, an identification of the gaps in the literature of BCA will be
done (Modex, 2019). The paper will discuss issues that have been addressed in the present
literature. In addition, research is going to highlight key issues which have not been
addressed or adequately addressed to date. Moreover, with this discussion personal views on
the identified critical security issues will be provided while summarizing the future research
directions on the basis of above-identified research gaps in the chosen research field of block-
chain based applications (Yu, Li, Tian, & Liu, 2018).
Source: (Modex, 2019)
Part 2: Security of blockchain-enabled applications (BCA) 1200
Introduction
This research report is mainly focused on identifying security aspects as well as issues
of BCA. The discussion will mainly provide a systematic literature review of BCA all across
the security domain. The key aim of this research report is to investigate the present state of
BT as well as its applications for highlighting how security issues are affecting this disruptive
technology. While doing so, the paper is going to talk about challenges in using BCA in this
digital era. Most importantly, an identification of the gaps in the literature of BCA will be
done (Modex, 2019). The paper will discuss issues that have been addressed in the present
literature. In addition, research is going to highlight key issues which have not been
addressed or adequately addressed to date. Moreover, with this discussion personal views on
the identified critical security issues will be provided while summarizing the future research
directions on the basis of above-identified research gaps in the chosen research field of block-
chain based applications (Yu, Li, Tian, & Liu, 2018).
Source: (Modex, 2019)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

SECURITY 4
Highlighting the challenges or problems in BCA
This section is going to highlight the key challenges in the field of BCA so that
possible solutions can be found in order to address them. In general, blockchain is a kind of
technology which allows us to keep a ledger including the whole transaction data as well as
to update the ledgers for further maintaining integrity in a new transaction (Casino, Dasaklis,
& Patsakis, 2019). It has been found that since the advancement of encryption technology and
the Internet, BT has made it possible for people to verify any transaction’s reliability. Thus,
with the help of BT, the single point of failure on an authorized third party arising from the
dependency has been solved successfully. The key challenges of BCA are as follows:
Scalability
The scalability is the huge challenge of using blockchain networks and it is directly
associated with the technical scalability of the blockchain network. It has been found that an
efficient solution for this issue of scalability is to add a second layer to the prime blockchain
network for further facilitating faster transactions (Yu, Li, Tian, & Liu, 2018).
Lack of interoperability
This challenge in BCA is usually occurred due to so many different networks. It is
because the blockchain space has an abundance of solutions and players too. Thus, due to a
lack of standards, BT allows diverse networks to communicate with each other which
ultimately escalate the issue of lack of interoperability. As a solution, there are some key
projects which offer interoperability like Ark that uses the SmartBridges architecture for
further addressing the challenge of interoperability (Modex, 2019).
Lack of blockchain talent
As BT is newly emerging technology hence developer community requires more
resources as well as time to accommodate the new demands hence lack of blockchain talent is
again a new challenge while using BCAs. In this way, such a gap in market demand and
current blockchain talent availability can be resolved with skilled developers. The company
can also pay the higher than average salaries to a blockchain professional to resolve the
challenge of blockchain skilled people (Evans, Barry, & Mason, 2018).
Integration with legacy systems
In addition, the integration of blockchain with the legacy system of any organization
requires to completely restructuring the previous system. Thus, to address this challenge
Highlighting the challenges or problems in BCA
This section is going to highlight the key challenges in the field of BCA so that
possible solutions can be found in order to address them. In general, blockchain is a kind of
technology which allows us to keep a ledger including the whole transaction data as well as
to update the ledgers for further maintaining integrity in a new transaction (Casino, Dasaklis,
& Patsakis, 2019). It has been found that since the advancement of encryption technology and
the Internet, BT has made it possible for people to verify any transaction’s reliability. Thus,
with the help of BT, the single point of failure on an authorized third party arising from the
dependency has been solved successfully. The key challenges of BCA are as follows:
Scalability
The scalability is the huge challenge of using blockchain networks and it is directly
associated with the technical scalability of the blockchain network. It has been found that an
efficient solution for this issue of scalability is to add a second layer to the prime blockchain
network for further facilitating faster transactions (Yu, Li, Tian, & Liu, 2018).
Lack of interoperability
This challenge in BCA is usually occurred due to so many different networks. It is
because the blockchain space has an abundance of solutions and players too. Thus, due to a
lack of standards, BT allows diverse networks to communicate with each other which
ultimately escalate the issue of lack of interoperability. As a solution, there are some key
projects which offer interoperability like Ark that uses the SmartBridges architecture for
further addressing the challenge of interoperability (Modex, 2019).
Lack of blockchain talent
As BT is newly emerging technology hence developer community requires more
resources as well as time to accommodate the new demands hence lack of blockchain talent is
again a new challenge while using BCAs. In this way, such a gap in market demand and
current blockchain talent availability can be resolved with skilled developers. The company
can also pay the higher than average salaries to a blockchain professional to resolve the
challenge of blockchain skilled people (Evans, Barry, & Mason, 2018).
Integration with legacy systems
In addition, the integration of blockchain with the legacy system of any organization
requires to completely restructuring the previous system. Thus, to address this challenge

SECURITY 5
organization can devise a way to successfully integrate the two technologies (Yu, Li, Tian, &
Liu, 2018).
Discussing issues addressed in the current literature
The key issues, as well as challenges related to security, have been addressed in the
current literature (Macaulay, 2018). As we know, several industrial, government and
commercial sectors adopt BT; hence there is a need to address such security issues until they
become paramount. There are some key security issues which have been successfully
addressed in the current literature as follows:
Endpoint vulnerabilities (Yu, Li, Tian, & Liu, 2018)
51% of attacks are addressed with the Proof-of-Work (PoW) consensus mechanism
Exchange security hacks with the use of paper or hardware wallet
Social engineering challenges with the enhanced training and studying about
engineering scams so as to avoid facing them
Software and Malware flaws through vigilance, contract audits, penetration testing,
and code reviews (Casino, Dasaklis, & Patsakis, 2019).
Highlighting issues not addressed
In addition to that, there are some critical security issues which have not been
addressed or adequately addressed; they are as follows:
Public and Private Key Security
Vendor Risks
Untested Code (Dhillon, Metcalf, & Hooper, 2017)
Protection against data tampering
Untested at Full Scale
Prevention of identity theft
Lack of Standards and Regulation
structural security of IoT devices
Security of internal communications
Making passwords obsolete
Privacy and security of digital chats
Protection of critical infrastructure
organization can devise a way to successfully integrate the two technologies (Yu, Li, Tian, &
Liu, 2018).
Discussing issues addressed in the current literature
The key issues, as well as challenges related to security, have been addressed in the
current literature (Macaulay, 2018). As we know, several industrial, government and
commercial sectors adopt BT; hence there is a need to address such security issues until they
become paramount. There are some key security issues which have been successfully
addressed in the current literature as follows:
Endpoint vulnerabilities (Yu, Li, Tian, & Liu, 2018)
51% of attacks are addressed with the Proof-of-Work (PoW) consensus mechanism
Exchange security hacks with the use of paper or hardware wallet
Social engineering challenges with the enhanced training and studying about
engineering scams so as to avoid facing them
Software and Malware flaws through vigilance, contract audits, penetration testing,
and code reviews (Casino, Dasaklis, & Patsakis, 2019).
Highlighting issues not addressed
In addition to that, there are some critical security issues which have not been
addressed or adequately addressed; they are as follows:
Public and Private Key Security
Vendor Risks
Untested Code (Dhillon, Metcalf, & Hooper, 2017)
Protection against data tampering
Untested at Full Scale
Prevention of identity theft
Lack of Standards and Regulation
structural security of IoT devices
Security of internal communications
Making passwords obsolete
Privacy and security of digital chats
Protection of critical infrastructure

SECURITY 6
Security of Transaction
In this context, the above-mentioned security issues and threats are those concerns
related to blockchain-based applications which are pending to be addressed fully and
effectively yet (Modex, 2019).
Discussing personal view on the issues
In my opinion, BT and BCA have proven to be secure and robust in the past yet there
are several security issues and challenges which are affecting the security of the whole
ecosystem. I consider that it is required to have a detailed understanding of the security issues
and concerns in order to navigate the highly complex area of blockchain development in the
form of blockchain-enabled applications (Yu, Li, Tian, & Liu, 2018). I believe that
mitigation, prevention and addressing of security issues of blockchain technology can only be
possible by manifesting the real interest in the efficient applicability of BT in an organization
use cases. Based on this research, I have found that there is an increase in trust and eagerness
to tap into the benefits of blockchain which is clear through increased use of BCA. On the
contrary, there are still numerous challenges including security and privacy challenges which
need to be addressed prior to the critical stage (Casino, Dasaklis, & Patsakis, 2019). Apart
from these security and vulnerability issues, the key benefits of blockchain are showing that
the technology is on the right track of digitalization. I can now say that emerging disruptors
like blockchain technology need to focus to create a perfect single form of the technology, as
well as focus on multiple iterations, with the unique use case (Arli, Dylke, Burgess, Campus,
& Soldo, 2013).
Conclusion
In whole, this research paper has successfully explored blockchain as an embarked on
an ascending trend of BCA. It has been found that in the form of Blockchain-enabled
Application, global countries are constantly manifesting key interest in the applicability of
the BT within enterprise use cases. The discussion on security issues of BCA suggests that
blockchain is steadily maturing with the benefits and challenges both. The paper has included
a shortlist of blockchain security issues that need to be addressed adequately and effectively.
Based on the identified gaps in the literature review conducted above, this research is
indicating that cybercriminals always update their tactics with the evolution of security
Security of Transaction
In this context, the above-mentioned security issues and threats are those concerns
related to blockchain-based applications which are pending to be addressed fully and
effectively yet (Modex, 2019).
Discussing personal view on the issues
In my opinion, BT and BCA have proven to be secure and robust in the past yet there
are several security issues and challenges which are affecting the security of the whole
ecosystem. I consider that it is required to have a detailed understanding of the security issues
and concerns in order to navigate the highly complex area of blockchain development in the
form of blockchain-enabled applications (Yu, Li, Tian, & Liu, 2018). I believe that
mitigation, prevention and addressing of security issues of blockchain technology can only be
possible by manifesting the real interest in the efficient applicability of BT in an organization
use cases. Based on this research, I have found that there is an increase in trust and eagerness
to tap into the benefits of blockchain which is clear through increased use of BCA. On the
contrary, there are still numerous challenges including security and privacy challenges which
need to be addressed prior to the critical stage (Casino, Dasaklis, & Patsakis, 2019). Apart
from these security and vulnerability issues, the key benefits of blockchain are showing that
the technology is on the right track of digitalization. I can now say that emerging disruptors
like blockchain technology need to focus to create a perfect single form of the technology, as
well as focus on multiple iterations, with the unique use case (Arli, Dylke, Burgess, Campus,
& Soldo, 2013).
Conclusion
In whole, this research paper has successfully explored blockchain as an embarked on
an ascending trend of BCA. It has been found that in the form of Blockchain-enabled
Application, global countries are constantly manifesting key interest in the applicability of
the BT within enterprise use cases. The discussion on security issues of BCA suggests that
blockchain is steadily maturing with the benefits and challenges both. The paper has included
a shortlist of blockchain security issues that need to be addressed adequately and effectively.
Based on the identified gaps in the literature review conducted above, this research is
indicating that cybercriminals always update their tactics with the evolution of security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SECURITY 7
strategies. In this way, for avoiding becoming a victim, it is required to stay up-to-date with
the latest blockchain security issues as well as preventative security measures. In whole,
addressing identified security issues in blockchain technology has become essential as it only
takes a blockchain security vulnerability to cause permanent damage to a business or an
institution.
strategies. In this way, for avoiding becoming a victim, it is required to stay up-to-date with
the latest blockchain security issues as well as preventative security measures. In whole,
addressing identified security issues in blockchain technology has become essential as it only
takes a blockchain security vulnerability to cause permanent damage to a business or an
institution.

SECURITY 8
References
Arli, V., Dylke, S., Burgess, R., Campus, R., & Soldo, E. (2013). Woolworths Australia and
Walmart US: Best practices in supply chain collaboration. Journal of Economics,
Business & Accountancy Ventura (JEBAV), 16(1).
Casino, F., Dasaklis, T., & Patsakis, C. (2019). A systematic literature review of blockchain-
based applications: current status, classification and open issues. Telematics and
Informatics, 36, 55-81.
Dhillon, V., Metcalf, D., & Hooper, M. (2017). Blockchain Enabled Applications:
Understand the Blockchain Ecosystem and How to Make it Work for You. London:
Apress.
Evans, Barry, & Mason, R. (2018). The lean supply chain: managing the challenge at Tesco
(2nd ed.). London : Kogan Page .
Macaulay, T. (2018). Eddie Stobart CIO John Court on how IoT, blockchain and AI are
transforming transport and logistics. Retrieved from CIO:
https://www.cio.com/article/3525254/eddie-stobart-cio-john-court-on-how-iot-
blockchain-and-ai-are-transforming-transport-and-logistics.html
Modex. (2019). The Challenges Of Blockchain Adoption. Retrieved from Modex:
https://modex.tech/the-challenges-of-blockchain-adoption/
Yu, Y., Li, Y., Tian, J., & Liu, J. (2018). Blockchain-based solutions to security and privacy
issues in the Internet of Things. IEEE Wireless Communications, 25(6), 12-18.
References
Arli, V., Dylke, S., Burgess, R., Campus, R., & Soldo, E. (2013). Woolworths Australia and
Walmart US: Best practices in supply chain collaboration. Journal of Economics,
Business & Accountancy Ventura (JEBAV), 16(1).
Casino, F., Dasaklis, T., & Patsakis, C. (2019). A systematic literature review of blockchain-
based applications: current status, classification and open issues. Telematics and
Informatics, 36, 55-81.
Dhillon, V., Metcalf, D., & Hooper, M. (2017). Blockchain Enabled Applications:
Understand the Blockchain Ecosystem and How to Make it Work for You. London:
Apress.
Evans, Barry, & Mason, R. (2018). The lean supply chain: managing the challenge at Tesco
(2nd ed.). London : Kogan Page .
Macaulay, T. (2018). Eddie Stobart CIO John Court on how IoT, blockchain and AI are
transforming transport and logistics. Retrieved from CIO:
https://www.cio.com/article/3525254/eddie-stobart-cio-john-court-on-how-iot-
blockchain-and-ai-are-transforming-transport-and-logistics.html
Modex. (2019). The Challenges Of Blockchain Adoption. Retrieved from Modex:
https://modex.tech/the-challenges-of-blockchain-adoption/
Yu, Y., Li, Y., Tian, J., & Liu, J. (2018). Blockchain-based solutions to security and privacy
issues in the Internet of Things. IEEE Wireless Communications, 25(6), 12-18.
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





