Comprehensive Report on Kerberos Authentication and Network Security
VerifiedAdded on 2020/02/23
|7
|1660
|49
Report
AI Summary
This report provides a comprehensive analysis of the Kerberos authentication protocol and its role in network security. It begins by introducing the Kerberos protocol, explaining its function in sharing secret information using a trusted third party, the Key Distribution Center (KDC). The report then delves into potential security threats, including eavesdropping, brute force attacks, and cookie replay attacks, and explains how Kerberos addresses these vulnerabilities. A detailed network diagram illustrates the Kerberos environment, including routers, switches, and servers. The report outlines security objectives such as confidentiality, integrity, and availability within the network. It also compares Kerberos versions 4 and 5, highlighting key differences in encoding, ticket handling, and authentication support. Finally, the report identifies organizations like SAP and Microsoft that utilize Kerberos for their products, emphasizing its widespread use in cyber security. This report provides valuable insights into the implementation and benefits of Kerberos in securing network environments.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Table of Contents..................................................................................................................................1
1. Network Addressing Problem.......................................................................................................2
2. Threats..........................................................................................................................................2
3. Network Diagram..........................................................................................................................3
4. Security Objectives.......................................................................................................................4
5. Difference between Version 4 and Version 5...............................................................................4
6. Organizations................................................................................................................................5
References............................................................................................................................................5
1
Table of Contents..................................................................................................................................1
1. Network Addressing Problem.......................................................................................................2
2. Threats..........................................................................................................................................2
3. Network Diagram..........................................................................................................................3
4. Security Objectives.......................................................................................................................4
5. Difference between Version 4 and Version 5...............................................................................4
6. Organizations................................................................................................................................5
References............................................................................................................................................5
1

1. Network Addressing Problem
Kerberos is a protocol that is used for sharing the secret information and it makes use of the
trusted third party to evaluate the identity like usernamne and password of the client. The clients
may be either users, servers or may be a software. The trusted third party is known as the Key
Distribution Center called KDC which is used to run the Daemons of the Kerberos [1] . Kereberos has
the ability to make the enterprise in a secured manner. The Kerberos are used to send the
passwords of the plaintext in a secured way which is transmitted in a network. This system is used
for centralizing the information of the user like username and password which is used for data
manipulation. Ultimately it is used in the prevention of storing password information by reducing the
chance in which a single machine's compromise will make results in other compromises [2].
2. Threats
Authentication is known as the method for finding the entity by using the username and
password. Threats that are involved in the authentication are as follows
Eavesdropping of the network
A Hacker can find the user's identity or else the credentials of the user like username and
password by reading the traffic of the network.
Brute Force Attacks
Hacker makes guess on the username and password of the user by using the brute force.
Dictionary Attack
Dictionary attack can be used by the hacker by trying out all the possibilities that are
common terms in a dictionary.
Cookie Replay attack
A hacker can access the authenticated session of the data transmission by reusing the
cookie that is being stolen [4].
Use of kerberos in User Authentication
2
Kerberos is a protocol that is used for sharing the secret information and it makes use of the
trusted third party to evaluate the identity like usernamne and password of the client. The clients
may be either users, servers or may be a software. The trusted third party is known as the Key
Distribution Center called KDC which is used to run the Daemons of the Kerberos [1] . Kereberos has
the ability to make the enterprise in a secured manner. The Kerberos are used to send the
passwords of the plaintext in a secured way which is transmitted in a network. This system is used
for centralizing the information of the user like username and password which is used for data
manipulation. Ultimately it is used in the prevention of storing password information by reducing the
chance in which a single machine's compromise will make results in other compromises [2].
2. Threats
Authentication is known as the method for finding the entity by using the username and
password. Threats that are involved in the authentication are as follows
Eavesdropping of the network
A Hacker can find the user's identity or else the credentials of the user like username and
password by reading the traffic of the network.
Brute Force Attacks
Hacker makes guess on the username and password of the user by using the brute force.
Dictionary Attack
Dictionary attack can be used by the hacker by trying out all the possibilities that are
common terms in a dictionary.
Cookie Replay attack
A hacker can access the authenticated session of the data transmission by reusing the
cookie that is being stolen [4].
Use of kerberos in User Authentication
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Kerberos varies from the authentication method which includes username and password.
Inspite of authenticating one user to one network service, Kerberos makes use of the encryption
method and also a trusted third party for user authentication. The trusted third party is called as KDC
and while the user authenticate the KDC, this party sends a ticket of the session to the machine of
the user. Kerberos aware services searches for the tickets on the machine of the user. The kerberos
aware network keeps the logs and send their principal to the trusted third party which is KDC. The
KDC verifies the principal in its database and it creates a TGT in an encrypted form, the TGT is being
sent to that user. The user can make use of the TGT whenever he wants to access the network [5].
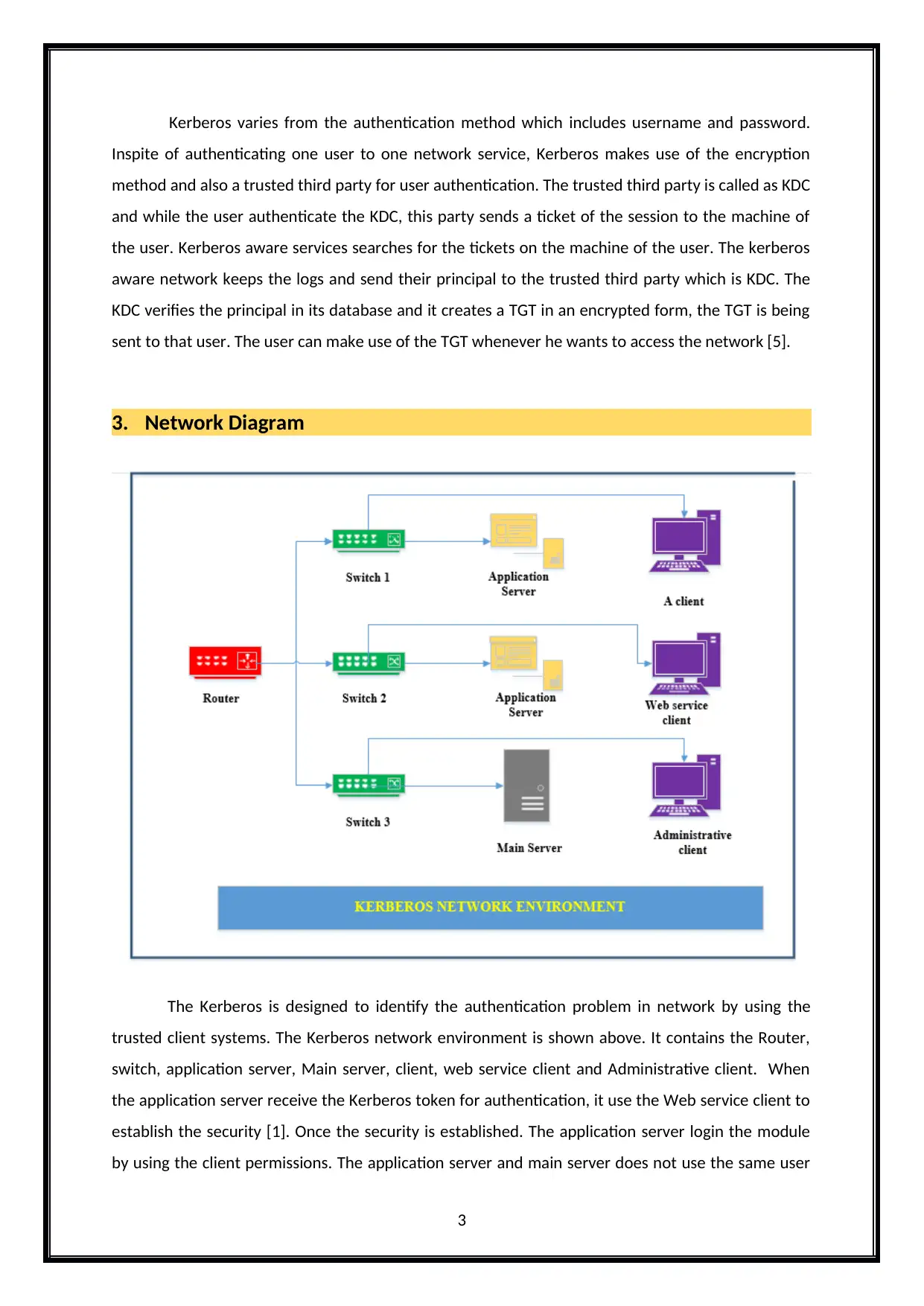
3. Network Diagram
The Kerberos is designed to identify the authentication problem in network by using the
trusted client systems. The Kerberos network environment is shown above. It contains the Router,
switch, application server, Main server, client, web service client and Administrative client. When
the application server receive the Kerberos token for authentication, it use the Web service client to
establish the security [1]. Once the security is established. The application server login the module
by using the client permissions. The application server and main server does not use the same user
3
Inspite of authenticating one user to one network service, Kerberos makes use of the encryption
method and also a trusted third party for user authentication. The trusted third party is called as KDC
and while the user authenticate the KDC, this party sends a ticket of the session to the machine of
the user. Kerberos aware services searches for the tickets on the machine of the user. The kerberos
aware network keeps the logs and send their principal to the trusted third party which is KDC. The
KDC verifies the principal in its database and it creates a TGT in an encrypted form, the TGT is being
sent to that user. The user can make use of the TGT whenever he wants to access the network [5].
3. Network Diagram
The Kerberos is designed to identify the authentication problem in network by using the
trusted client systems. The Kerberos network environment is shown above. It contains the Router,
switch, application server, Main server, client, web service client and Administrative client. When
the application server receive the Kerberos token for authentication, it use the Web service client to
establish the security [1]. Once the security is established. The application server login the module
by using the client permissions. The application server and main server does not use the same user
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

registry and it requires the custom login module to map the Kerberos principal name and application
server user name. The application server provides the new security and it contains he various
domains. The domains are only support the Kerberos at the cell level. The application server must be
using the same Kerberos realm. The Kerberos authentication having the own Kerberos realm by
using the backend and client resources. The Kerberos using the application library to provides the
interface for application server and application clients. The Kerberos encrypting the data. It provides
the network security by using the various methods. The administrative server is used to provide the
network interface to the database.
4. Security Objectives
Confidentiality is similar to privacy which includes the access of the information only by the
authorized users. So in the above network diagram we had used separate switches for client and
web service client. As the switches are separate there is less chance for affecting the confidentiality
of the information that is being transmitted.
Integrity is nothing but the accuracy of the information in which the data should not be
changed and it should have the assurance that it cannot be modified by any unauthorized access.
Router passes the information to 3 different switches that can send the information to the
Application server. The server is used as a mediator between the client and the switch, so there is no
possibility of modifying the information by the unauthorised access.
Availability is associated with the hardware. The system should be ready to perform when
there is any hardware failure. The information should be available even after the failure. Here as
there is a server in the above network diagram in case of hardware repair in the client systems, the
information can be backed up from the application server.
5. Difference between Version 4 and Version 5
Version 4 and Version 5 of kerberos are the updations of the Kerberos software. Kerberos v5
is the successor of v4. Kerberos v4 was released at the end of 1980 and v5 was published in 1993.
Kerberos Version 4 utilizes the reciever makes right system for encoding purpose whereas Version 5
uses the ASN.1 system for encoding. Kerberos v4 provides the satisfactory support for ticket
whereas v5 facilitates forward and renewal of packets during transmission. V4 contains ony few IP
address but V5 contains multiple IP addresses. Version 4 has no present support for authentication
but v5 provides the reasonable support for authentication [6]. version 4 of kerberos uses Data
Encryption Standard to offer the service of authentication. To improve the security in the network,
4
server user name. The application server provides the new security and it contains he various
domains. The domains are only support the Kerberos at the cell level. The application server must be
using the same Kerberos realm. The Kerberos authentication having the own Kerberos realm by
using the backend and client resources. The Kerberos using the application library to provides the
interface for application server and application clients. The Kerberos encrypting the data. It provides
the network security by using the various methods. The administrative server is used to provide the
network interface to the database.
4. Security Objectives
Confidentiality is similar to privacy which includes the access of the information only by the
authorized users. So in the above network diagram we had used separate switches for client and
web service client. As the switches are separate there is less chance for affecting the confidentiality
of the information that is being transmitted.
Integrity is nothing but the accuracy of the information in which the data should not be
changed and it should have the assurance that it cannot be modified by any unauthorized access.
Router passes the information to 3 different switches that can send the information to the
Application server. The server is used as a mediator between the client and the switch, so there is no
possibility of modifying the information by the unauthorised access.
Availability is associated with the hardware. The system should be ready to perform when
there is any hardware failure. The information should be available even after the failure. Here as
there is a server in the above network diagram in case of hardware repair in the client systems, the
information can be backed up from the application server.
5. Difference between Version 4 and Version 5
Version 4 and Version 5 of kerberos are the updations of the Kerberos software. Kerberos v5
is the successor of v4. Kerberos v4 was released at the end of 1980 and v5 was published in 1993.
Kerberos Version 4 utilizes the reciever makes right system for encoding purpose whereas Version 5
uses the ASN.1 system for encoding. Kerberos v4 provides the satisfactory support for ticket
whereas v5 facilitates forward and renewal of packets during transmission. V4 contains ony few IP
address but V5 contains multiple IP addresses. Version 4 has no present support for authentication
but v5 provides the reasonable support for authentication [6]. version 4 of kerberos uses Data
Encryption Standard to offer the service of authentication. To improve the security in the network,
4

kerberos 5 has been added with few enhanced features. Kerberos version 5 has limitations in
addresses. In kerberos version 4 kerberos to kerberos relationship is required whereas Version 5 can
support only fewer relationships [7].
6. Organizations
Kerberos are used in the Network based organizations. For example it can be used in cyber
security systems and the organizations which makes use of the cyber crime and security. It is quiet
difficult to list the companies which and all uses the kerberos. So some few companies which are
familiar are listed below and those are the companies which is related to the products based on
Cyber Security. It is used approximately by 100 million people around the world for the security
purpose. The organizations that make use of the kerberos for some of their products is listed as
follows
1. SAP
Few software that needs license from SAP involves Kerberos implementation. When it is
being used, there will not be interoperability issues or copy right changes.
2. Microsoft
The Microsoft is one of the leading companies which uses the kerberos protocol in some of
their products. Microsoft windows and Microsoft active directory uses the kerberos. In this microsoft
network users perform authentication process using the kerberos protocol. The credentials provided
can be used later by the user to various other applications which are enabled by kerberos [9].
References
[1]D. Kapse and V. Bagdi, "Efficient Security Services of Honeypot using Kerberos for Detecting
Intruders", International Journal of System and Software Engineering, vol. 3, no. 2, 2015.
[2]"An Overview of a Kerberos Infrastructure", Tldp.org, 2017. [Online]. Available:
http://tldp.org/HOWTO/Kerberos-Infrastructure-HOWTO/overview.html. [Accessed: 30- Aug-
2017].
5
addresses. In kerberos version 4 kerberos to kerberos relationship is required whereas Version 5 can
support only fewer relationships [7].
6. Organizations
Kerberos are used in the Network based organizations. For example it can be used in cyber
security systems and the organizations which makes use of the cyber crime and security. It is quiet
difficult to list the companies which and all uses the kerberos. So some few companies which are
familiar are listed below and those are the companies which is related to the products based on
Cyber Security. It is used approximately by 100 million people around the world for the security
purpose. The organizations that make use of the kerberos for some of their products is listed as
follows
1. SAP
Few software that needs license from SAP involves Kerberos implementation. When it is
being used, there will not be interoperability issues or copy right changes.
2. Microsoft
The Microsoft is one of the leading companies which uses the kerberos protocol in some of
their products. Microsoft windows and Microsoft active directory uses the kerberos. In this microsoft
network users perform authentication process using the kerberos protocol. The credentials provided
can be used later by the user to various other applications which are enabled by kerberos [9].
References
[1]D. Kapse and V. Bagdi, "Efficient Security Services of Honeypot using Kerberos for Detecting
Intruders", International Journal of System and Software Engineering, vol. 3, no. 2, 2015.
[2]"An Overview of a Kerberos Infrastructure", Tldp.org, 2017. [Online]. Available:
http://tldp.org/HOWTO/Kerberos-Infrastructure-HOWTO/overview.html. [Accessed: 30- Aug-
2017].
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[3]"threats and attacks on user authentication in a cloud environment", 2017. [Online]. Available:
https://www.quora.com/What-are-some-of-the-threats-and-attacks-on-user-authentication-in-
a-cloud-environment. [Accessed: 30- Aug- 2017].
[4]E. EMANDII, "AUTHENTICATION - THREATS AND COUNTERMEASURES", Scientific Bulletin of Naval
Academy, vol. 19, no. 1, pp. 378-381, 2016.
[5]X. Ma, J. Han, Z. Wei and H. Liu, "Hierarchical proxy authentication model in Kerberos inter-realm
based on RSA", JOURNAL OF ELECTRONIC MEASUREMENT AND INSTRUMENT, vol. 27, no. 2, pp.
105-109, 2013.
[6]"Difference between Kerberos v4 and Kerberos v5 | Kerberos v4 vs Kerberos
v5", Differencebetween.info, 2017. [Online]. Available:
http://www.differencebetween.info/difference-between-kerberos-v4-and-kerberos-v5.
[Accessed: 30- Aug- 2017].
[7]A. B.A., "Kerberos: A Review of the Modification in Versions 4-To-5 Transition", African journal of
computing & ICT reference format, vol. 6, no. 3, 2013.
[8]"Kerberos, Pluto's oddball moon", New Scientist, vol. 226, no. 3024, p. 16, 2015.
[9]"Organizations that use kerberos", cybersafe, 2017. .
[10]"Commercial Kerberos vendors", Web.ornl.gov, 2017. [Online]. Available:
http://web.ornl.gov/~romeja/commerce.htm. [Accessed: 30- Aug- 2017].
6
https://www.quora.com/What-are-some-of-the-threats-and-attacks-on-user-authentication-in-
a-cloud-environment. [Accessed: 30- Aug- 2017].
[4]E. EMANDII, "AUTHENTICATION - THREATS AND COUNTERMEASURES", Scientific Bulletin of Naval
Academy, vol. 19, no. 1, pp. 378-381, 2016.
[5]X. Ma, J. Han, Z. Wei and H. Liu, "Hierarchical proxy authentication model in Kerberos inter-realm
based on RSA", JOURNAL OF ELECTRONIC MEASUREMENT AND INSTRUMENT, vol. 27, no. 2, pp.
105-109, 2013.
[6]"Difference between Kerberos v4 and Kerberos v5 | Kerberos v4 vs Kerberos
v5", Differencebetween.info, 2017. [Online]. Available:
http://www.differencebetween.info/difference-between-kerberos-v4-and-kerberos-v5.
[Accessed: 30- Aug- 2017].
[7]A. B.A., "Kerberos: A Review of the Modification in Versions 4-To-5 Transition", African journal of
computing & ICT reference format, vol. 6, no. 3, 2013.
[8]"Kerberos, Pluto's oddball moon", New Scientist, vol. 226, no. 3024, p. 16, 2015.
[9]"Organizations that use kerberos", cybersafe, 2017. .
[10]"Commercial Kerberos vendors", Web.ornl.gov, 2017. [Online]. Available:
http://web.ornl.gov/~romeja/commerce.htm. [Accessed: 30- Aug- 2017].
6
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




