BN205 Project Management Plan: Risk Identification and Mitigation
VerifiedAdded on 2020/02/19
|6
|1178
|33
Project
AI Summary
This project management assignment presents a risk management plan, focusing on the identification, analysis, and mitigation of potential risks within a project context. The plan begins with an executive summary highlighting the importance of managing project constraints, such as cost, time, and quality. It then delves into the background of a case study involving SFSU's OIT department and the transition of their ticketing system. The core of the assignment involves a detailed risk management plan, encompassing risk identification (including cost overruns, communication gaps, and time overruns), risk analysis (using a risk matrix), and a risk response plan. The assignment also covers the monitoring and controlling of risks throughout the project lifecycle, and concludes with an evaluation and justification of the risk management processes. References to relevant sources support the analysis and recommendations.

BN205 Project Management
University name
Risk Management
Plan
University name
Risk Management
Plan
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BN205 Project Management
Executive summary
The project is the activity or set of activities with defined period of time. So it becomes a real test for the
project manager to manage each one of the constraints (cost, time, quality, resource) related to the
activities in the schedule. In this report, the issues or threats which may develop in the middle of the
project life cycle are identified and analyzed. And afterwards the risks are positioned and their
mitigation plan is developed accordingly.
Table of Contents
Introduction.................................................................................................................................................2
Background of case study............................................................................................................................2
Risk Management Plan................................................................................................................................2
Risk Identification........................................................................................................................................3
Risk Analysis................................................................................................................................................3
Risk response plan.......................................................................................................................................4
Monitoring and Controlling Risk..................................................................................................................4
Evaluation / Justification.............................................................................................................................4
Conclusion...................................................................................................................................................4
References...................................................................................................................................................5
1
Executive summary
The project is the activity or set of activities with defined period of time. So it becomes a real test for the
project manager to manage each one of the constraints (cost, time, quality, resource) related to the
activities in the schedule. In this report, the issues or threats which may develop in the middle of the
project life cycle are identified and analyzed. And afterwards the risks are positioned and their
mitigation plan is developed accordingly.
Table of Contents
Introduction.................................................................................................................................................2
Background of case study............................................................................................................................2
Risk Management Plan................................................................................................................................2
Risk Identification........................................................................................................................................3
Risk Analysis................................................................................................................................................3
Risk response plan.......................................................................................................................................4
Monitoring and Controlling Risk..................................................................................................................4
Evaluation / Justification.............................................................................................................................4
Conclusion...................................................................................................................................................4
References...................................................................................................................................................5
1

BN205 Project Management
Introduction
Risk administration is a technique to identify the probable opportunity and risk1. Thereafter the list is
segregated as per the positions obtained during analysis. Subsequently the mitigation or response plan
is developed on the basis of positions obtained. The data obtained are required to be dealt with the
opportunity and threat and plan in like way with the objective that it doesn't let influence any of the
three limitations of the project.
Background of case study
SFSU (Silicon Forest State University) has numerous data framework related exercises which are being
regulated by the OIT (Office of Information Technology) division. The clients at back end of OIT used
'Request Tracker' for passing on and following the ticketing system in light of UNIX, while the clients at
front end were using ‘Remedy’ structure for making and following ticketing system which is being
utilized for observing and following the bugs. For any kind of interest to clients of back end, the clients
of front end need to physically type the issue to 'Request Tracker'. However, now the workplace
changed the product being utilized by the clients of front end to 'Request Tracker' and gave the task to
Ron to lead the venture with the help of Harry, however both of them need to report to two different
bosses.
Risk Management Plan
Opportunity and dangers in any assignment are coordinated on the preface of the techniques defined in
the risk management. The exercises which link into the masterminding of threat association design are
recognized, analyzed and positioned accordingly2. The opportunity and dangers can be of many sorts,
and fit for affecting cost, plan and quality, particular, really definitive and so forth. An entire reason for
the risk design is to set the activity and make ourselves ready for all the perceived dangers especially at
a range by saying rank ‘low’, ‘medium’ or 'high'. There are particular sorts of dangers facilitating
procedures or steps which should be taken in the wake of situating all the perceived opportunities and
threats. There can be many activity intends to moderate the hazard like exchanging it, imparting it to
any external party, staying away from it absolutely or tolerating.
Risk Identification
(27th August 2017) RISK 1. By Pike. There is threat of having cost overrun
2
Introduction
Risk administration is a technique to identify the probable opportunity and risk1. Thereafter the list is
segregated as per the positions obtained during analysis. Subsequently the mitigation or response plan
is developed on the basis of positions obtained. The data obtained are required to be dealt with the
opportunity and threat and plan in like way with the objective that it doesn't let influence any of the
three limitations of the project.
Background of case study
SFSU (Silicon Forest State University) has numerous data framework related exercises which are being
regulated by the OIT (Office of Information Technology) division. The clients at back end of OIT used
'Request Tracker' for passing on and following the ticketing system in light of UNIX, while the clients at
front end were using ‘Remedy’ structure for making and following ticketing system which is being
utilized for observing and following the bugs. For any kind of interest to clients of back end, the clients
of front end need to physically type the issue to 'Request Tracker'. However, now the workplace
changed the product being utilized by the clients of front end to 'Request Tracker' and gave the task to
Ron to lead the venture with the help of Harry, however both of them need to report to two different
bosses.
Risk Management Plan
Opportunity and dangers in any assignment are coordinated on the preface of the techniques defined in
the risk management. The exercises which link into the masterminding of threat association design are
recognized, analyzed and positioned accordingly2. The opportunity and dangers can be of many sorts,
and fit for affecting cost, plan and quality, particular, really definitive and so forth. An entire reason for
the risk design is to set the activity and make ourselves ready for all the perceived dangers especially at
a range by saying rank ‘low’, ‘medium’ or 'high'. There are particular sorts of dangers facilitating
procedures or steps which should be taken in the wake of situating all the perceived opportunities and
threats. There can be many activity intends to moderate the hazard like exchanging it, imparting it to
any external party, staying away from it absolutely or tolerating.
Risk Identification
(27th August 2017) RISK 1. By Pike. There is threat of having cost overrun
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
BN205 Project Management
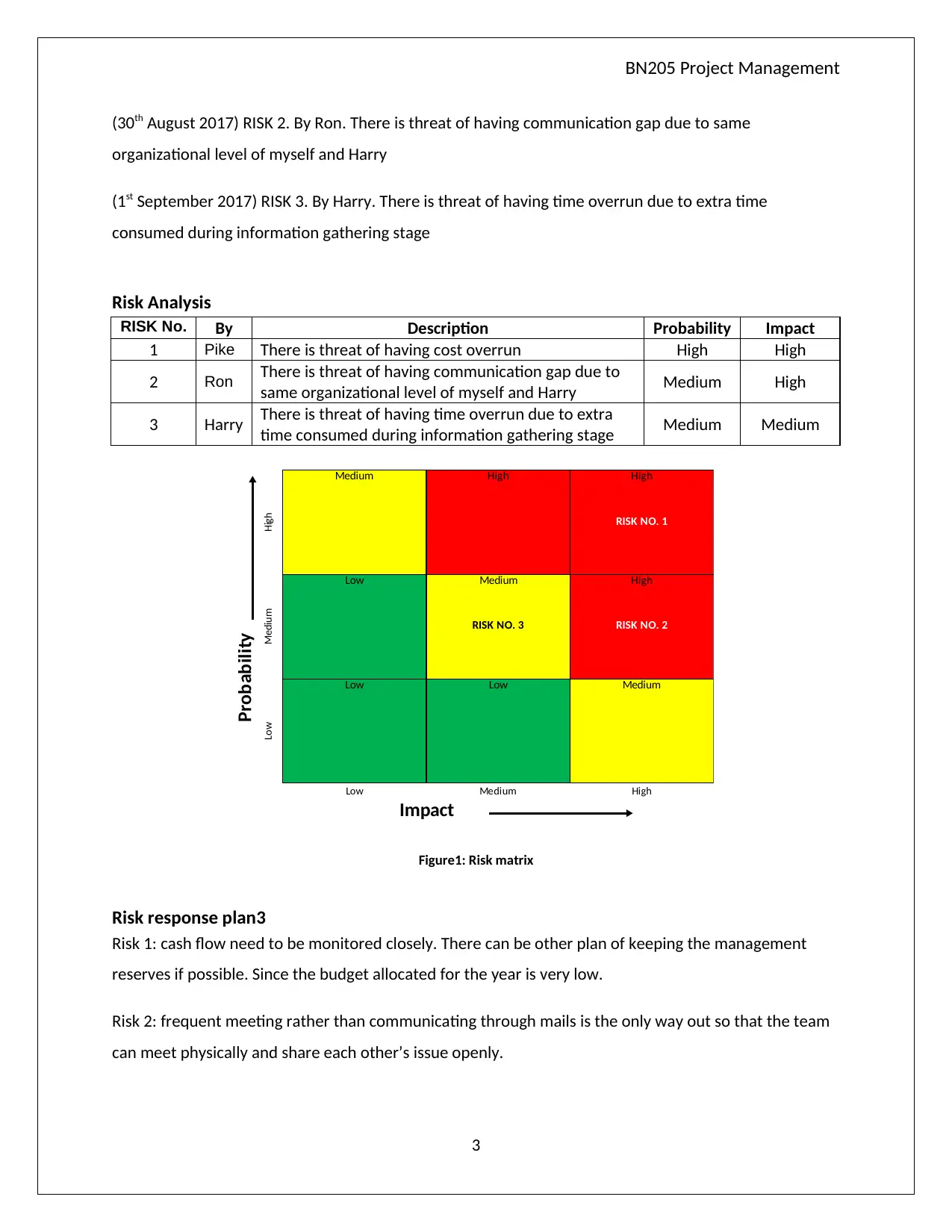
(30th August 2017) RISK 2. By Ron. There is threat of having communication gap due to same
organizational level of myself and Harry
(1st September 2017) RISK 3. By Harry. There is threat of having time overrun due to extra time
consumed during information gathering stage
Risk Analysis
RISK No. By Description Probability Impact
1 Pike There is threat of having cost overrun High High
2 Ron There is threat of having communication gap due to
same organizational level of myself and Harry Medium High
3 Harry There is threat of having time overrun due to extra
time consumed during information gathering stage Medium Medium
High
Medium High High
RISK NO. 1
Medium
Low Medium
RISK NO. 3
High
RISK NO. 2
Low
Low Low Medium
Low Medium High
Impact
Probability
Figure1: Risk matrix
Risk response plan3
Risk 1: cash flow need to be monitored closely. There can be other plan of keeping the management
reserves if possible. Since the budget allocated for the year is very low.
Risk 2: frequent meeting rather than communicating through mails is the only way out so that the team
can meet physically and share each other’s issue openly.
3
(30th August 2017) RISK 2. By Ron. There is threat of having communication gap due to same
organizational level of myself and Harry
(1st September 2017) RISK 3. By Harry. There is threat of having time overrun due to extra time
consumed during information gathering stage
Risk Analysis
RISK No. By Description Probability Impact
1 Pike There is threat of having cost overrun High High
2 Ron There is threat of having communication gap due to
same organizational level of myself and Harry Medium High
3 Harry There is threat of having time overrun due to extra
time consumed during information gathering stage Medium Medium
High
Medium High High
RISK NO. 1
Medium
Low Medium
RISK NO. 3
High
RISK NO. 2
Low
Low Low Medium
Low Medium High
Impact
Probability
Figure1: Risk matrix
Risk response plan3
Risk 1: cash flow need to be monitored closely. There can be other plan of keeping the management
reserves if possible. Since the budget allocated for the year is very low.
Risk 2: frequent meeting rather than communicating through mails is the only way out so that the team
can meet physically and share each other’s issue openly.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BN205 Project Management
Risk 3: time schedule need to be monitored closely to avoid any delay, else the extra time consumed for
gathering the information can cause the overall delay of the project and the communication gap can
increase.
Monitoring and Controlling Risk
This stage of risk administration is required for the proper management of the risks throughout the
project life cycle4. The risks are very dynamic in nature and can change its ranking frequently as or the
environmental conditions. So the risk register need to be reviewed in every stages of the project for
proper monitoring. Moreover the new risks identification should not be stopped and the identified risks
need to be again analyzed as above and ranking and its mitigation and response plan need to be
developed.
Evaluation / Justification
Finally it can be justified that the result obtained by the processes of identification and analysis of the
risks, the obtained result are the real cause of tension for Ron. There is always a chance of cost and time
overrun because of communication gap. Also the steps need to be continued throughout the project life
cycle to identify any more threats5.
Conclusion
So now it can be finished up at long last that the undertaking brought about by OIT should be followed
categorically like cost, time and communication and none of the issues can be overlooked. Else there
can be cost and time overrun. So it should be Ron’s responsibility to take care of the constraints and
discuss these issues in every meeting to infiltrate the issues to all stakeholders.
References
x
[1] Australian Government. (2017) http://www.austrac.gov.au. [Online].
http://www.austrac.gov.au/risk-management-tool-small-medium-sized-businesses
[2] Institute of Risk Management. (2016) About Risk Management. [Online].
https://www.theirm.org/the-risk-profession/risk-management.aspx
[3] et al. Wiley. (2017) 11.2 Risk Management Process. [Online]. https://pm4id.org/chapter/11-2-risk-
4
Risk 3: time schedule need to be monitored closely to avoid any delay, else the extra time consumed for
gathering the information can cause the overall delay of the project and the communication gap can
increase.
Monitoring and Controlling Risk
This stage of risk administration is required for the proper management of the risks throughout the
project life cycle4. The risks are very dynamic in nature and can change its ranking frequently as or the
environmental conditions. So the risk register need to be reviewed in every stages of the project for
proper monitoring. Moreover the new risks identification should not be stopped and the identified risks
need to be again analyzed as above and ranking and its mitigation and response plan need to be
developed.
Evaluation / Justification
Finally it can be justified that the result obtained by the processes of identification and analysis of the
risks, the obtained result are the real cause of tension for Ron. There is always a chance of cost and time
overrun because of communication gap. Also the steps need to be continued throughout the project life
cycle to identify any more threats5.
Conclusion
So now it can be finished up at long last that the undertaking brought about by OIT should be followed
categorically like cost, time and communication and none of the issues can be overlooked. Else there
can be cost and time overrun. So it should be Ron’s responsibility to take care of the constraints and
discuss these issues in every meeting to infiltrate the issues to all stakeholders.
References
x
[1] Australian Government. (2017) http://www.austrac.gov.au. [Online].
http://www.austrac.gov.au/risk-management-tool-small-medium-sized-businesses
[2] Institute of Risk Management. (2016) About Risk Management. [Online].
https://www.theirm.org/the-risk-profession/risk-management.aspx
[3] et al. Wiley. (2017) 11.2 Risk Management Process. [Online]. https://pm4id.org/chapter/11-2-risk-
4

BN205 Project Management
management-process/
[4] MyManagementGuide. (2010, May) 2. Risk management plan for a project: Definition, Purpose,
Software, Content and Approaches. [Online].
http://www.mymanagementguide.com/guidelines/project-management/risk-management/risk-
management-plan-for-a-project-definition-purpose-software-content-and-approaches/
[5] Educba. (2016, July) 6 Basic Steps to Develop a Project Risk Management Plan. [Online].
https://www.educba.com/project-risk-management-plan/
x
5
management-process/
[4] MyManagementGuide. (2010, May) 2. Risk management plan for a project: Definition, Purpose,
Software, Content and Approaches. [Online].
http://www.mymanagementguide.com/guidelines/project-management/risk-management/risk-
management-plan-for-a-project-definition-purpose-software-content-and-approaches/
[5] Educba. (2016, July) 6 Basic Steps to Develop a Project Risk Management Plan. [Online].
https://www.educba.com/project-risk-management-plan/
x
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





