Business Process Modelling: IIL IT Solution Design Report - Semester 1
VerifiedAdded on 2023/06/03
|16
|2713
|137
Report
AI Summary
This report presents a comprehensive business process modelling solution for Inshore Insurance Ltd (IIL), addressing the need for an improved IT infrastructure to handle increasing data volumes and enhance incident reporting capabilities. The report begins with an introduction, outlining the project scope, objectives, and constraints, including data sensitivity and financial limitations. It then details the use cases, actors, and use case diagrams to illustrate the system's functionalities. The design overview covers the solution architecture, project governance, IT infrastructure, security measures (such as encryption, firewalls, and two-factor authentication), and application and data solutions. The report also addresses capacity requirements, system interfaces, and non-functional requirements, including performance considerations and test criteria. The object model and collaboration diagrams are presented to showcase the integration of various subsystems like finance, claims, and system administration. The report concludes by summarizing the key findings and recommendations for IIL, providing a solid foundation for the development of a robust IT solution.

Running head: BUSINESS PROCESS MODELLING 1
Business Process Modelling
Student Name
Institutional Affiliation
Business Process Modelling
Student Name
Institutional Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BUSINESS PROCESS MODELLING 2
Table of Contents
1.0 Introduction.....................................................................................................................................3
1.1 Introduction.................................................................................................................................3
1.2 Solution Scope.............................................................................................................................3
1.3 Solution Overview.......................................................................................................................3
1.4 Constraints...................................................................................................................................4
1.5 Exclusions....................................................................................................................................5
2.0 Use Cases........................................................................................................................................5
2.1 Actors..........................................................................................................................................5
2.2 Use Case Diagrams......................................................................................................................6
3.0 Design Overview.............................................................................................................................6
3.1 Solution Architecture...................................................................................................................6
3.1.1 Project Governance Process.................................................................................................7
3.1.2 IT Infrastructure Solution.....................................................................................................8
3.1.3 Infrastructure Security.........................................................................................................8
3.1.4 Application Solution............................................................................................................9
3.1.5 Data Solution.....................................................................................................................10
3.2 Capacity Requirements..............................................................................................................10
3.3 System Interfaces.......................................................................................................................10
3.4 Constraints and Assumptions.....................................................................................................11
4.0 System Object Model....................................................................................................................11
4.1 Sub Systems...............................................................................................................................11
4.2 Subsystem Interfaces.................................................................................................................11
5.0 Object Collaboration......................................................................................................................12
5.1 Collaboration Diagrams.............................................................................................................12
5.2 Access Model............................................................................................................................12
6.0 Non-Functional Requirements.......................................................................................................12
6.1 Performance Considerations......................................................................................................12
6.2 Design Constraints.....................................................................................................................13
6.3 Test Criteria...............................................................................................................................13
6.4 Proof of Compliance..................................................................................................................14
7.0 Conclusion.....................................................................................................................................14
8.0 References.....................................................................................................................................15
Table of Contents
1.0 Introduction.....................................................................................................................................3
1.1 Introduction.................................................................................................................................3
1.2 Solution Scope.............................................................................................................................3
1.3 Solution Overview.......................................................................................................................3
1.4 Constraints...................................................................................................................................4
1.5 Exclusions....................................................................................................................................5
2.0 Use Cases........................................................................................................................................5
2.1 Actors..........................................................................................................................................5
2.2 Use Case Diagrams......................................................................................................................6
3.0 Design Overview.............................................................................................................................6
3.1 Solution Architecture...................................................................................................................6
3.1.1 Project Governance Process.................................................................................................7
3.1.2 IT Infrastructure Solution.....................................................................................................8
3.1.3 Infrastructure Security.........................................................................................................8
3.1.4 Application Solution............................................................................................................9
3.1.5 Data Solution.....................................................................................................................10
3.2 Capacity Requirements..............................................................................................................10
3.3 System Interfaces.......................................................................................................................10
3.4 Constraints and Assumptions.....................................................................................................11
4.0 System Object Model....................................................................................................................11
4.1 Sub Systems...............................................................................................................................11
4.2 Subsystem Interfaces.................................................................................................................11
5.0 Object Collaboration......................................................................................................................12
5.1 Collaboration Diagrams.............................................................................................................12
5.2 Access Model............................................................................................................................12
6.0 Non-Functional Requirements.......................................................................................................12
6.1 Performance Considerations......................................................................................................12
6.2 Design Constraints.....................................................................................................................13
6.3 Test Criteria...............................................................................................................................13
6.4 Proof of Compliance..................................................................................................................14
7.0 Conclusion.....................................................................................................................................14
8.0 References.....................................................................................................................................15

BUSINESS PROCESS MODELLING 3
1.0 Introduction
1.1 Introduction
Conducting system analysis and developing requirements specification is the first step in meeting
the business requirements. After a critical analysis, Inshore Insurance Ltd (IIL) realize that their
current Risk Analysis Product (RAP) application has some setbacks and cannot address some of
the business requirements like timing and locating crime incidences and accidents. Therefore, IIL
needs an IT solution that will solve the identified problems. Data storage is one of the essential
requirements that the solution should address because of the increasing amount of data that the
business is handling. The institution expects that the volume of data will increase drastically and
the solution should be able to operate on them using a single platform.
1.2 Solution Scope
The IIL board expects relevant recommendations and high-level assessment of the IT solution.
The scope of the project is that the Risk Analysis Product that is already in place will be used to
process all the required functionalities and user requests. The institution has utilized a virtualized
in-house platform to host the RAP application which will remain as an independent project. The
solution should also propose a single platform that will be able to process and handle huge
volume of primary and generated data.
1.3 Solution Overview
The IT solution should be able to address the storage and incident reporting challenges currently
faced by the institution. The volume of data is increasing and a high rate and the proposed IT
solution should have the ability to generate, store, examine, manage, and archive the data.
additionally, one of the key requirements that the solution should meet is the ability to record the
1.0 Introduction
1.1 Introduction
Conducting system analysis and developing requirements specification is the first step in meeting
the business requirements. After a critical analysis, Inshore Insurance Ltd (IIL) realize that their
current Risk Analysis Product (RAP) application has some setbacks and cannot address some of
the business requirements like timing and locating crime incidences and accidents. Therefore, IIL
needs an IT solution that will solve the identified problems. Data storage is one of the essential
requirements that the solution should address because of the increasing amount of data that the
business is handling. The institution expects that the volume of data will increase drastically and
the solution should be able to operate on them using a single platform.
1.2 Solution Scope
The IIL board expects relevant recommendations and high-level assessment of the IT solution.
The scope of the project is that the Risk Analysis Product that is already in place will be used to
process all the required functionalities and user requests. The institution has utilized a virtualized
in-house platform to host the RAP application which will remain as an independent project. The
solution should also propose a single platform that will be able to process and handle huge
volume of primary and generated data.
1.3 Solution Overview
The IT solution should be able to address the storage and incident reporting challenges currently
faced by the institution. The volume of data is increasing and a high rate and the proposed IT
solution should have the ability to generate, store, examine, manage, and archive the data.
additionally, one of the key requirements that the solution should meet is the ability to record the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BUSINESS PROCESS MODELLING 4
location and time when a crime or accident occurs. It should also have access control mechanism
so as to restrict the number of users accessing the system to the specified number.
1.4 Constraints
There are several constraints that is associated with the project including human resources,
financial constraints, data sensitivity, and risks. Data sensitivity is an important factor that should
be addressed in software development. It is the responsibility of the institution that the data
collected is kept safe from any unauthorized access or external attacks to maintain privacy and
confidentiality. Benefits realization plan aids in identifying, executing, and sustaining the
benefits associated with the IT solution. it is essential to have such a plan so as to give guidelines
on how to achieve the project objectives and benefits. The realization plan reflects on the
strategic goals that the business anticipates for instance, productivity, process improvements,
quality, customer satisfaction, efficiency, revenue generation, and rate of customer growth. In
project management, a threat model is a crucial tool for managing risks. Having a threat model
will help the project team to identify security threats that may face the system, prioritizing them,
and providing mitigation strategies.
Figure 1: Threat Risk Modelling
location and time when a crime or accident occurs. It should also have access control mechanism
so as to restrict the number of users accessing the system to the specified number.
1.4 Constraints
There are several constraints that is associated with the project including human resources,
financial constraints, data sensitivity, and risks. Data sensitivity is an important factor that should
be addressed in software development. It is the responsibility of the institution that the data
collected is kept safe from any unauthorized access or external attacks to maintain privacy and
confidentiality. Benefits realization plan aids in identifying, executing, and sustaining the
benefits associated with the IT solution. it is essential to have such a plan so as to give guidelines
on how to achieve the project objectives and benefits. The realization plan reflects on the
strategic goals that the business anticipates for instance, productivity, process improvements,
quality, customer satisfaction, efficiency, revenue generation, and rate of customer growth. In
project management, a threat model is a crucial tool for managing risks. Having a threat model
will help the project team to identify security threats that may face the system, prioritizing them,
and providing mitigation strategies.
Figure 1: Threat Risk Modelling
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BUSINESS PROCESS MODELLING 5
(Source: Owasp.org, 2018)
1.5 Exclusions
The technical details and requirements are not needed at this stage and only involves logical and
conceptual design.
2.0 Use Cases
2.1 Actors
The actors include:
Risk manager
Claims manager
Finance manager
Customer relationship manager
(Source: Owasp.org, 2018)
1.5 Exclusions
The technical details and requirements are not needed at this stage and only involves logical and
conceptual design.
2.0 Use Cases
2.1 Actors
The actors include:
Risk manager
Claims manager
Finance manager
Customer relationship manager
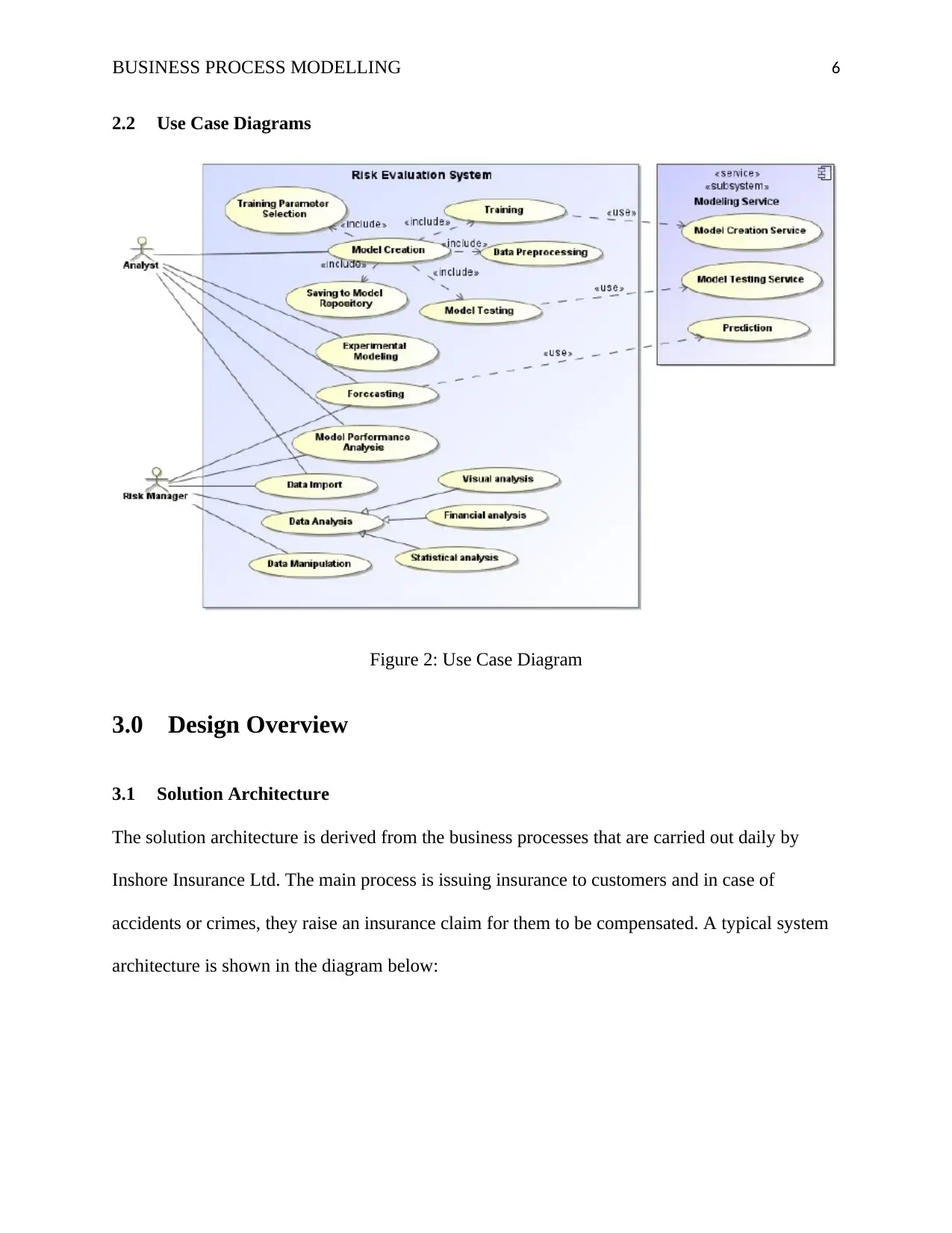
BUSINESS PROCESS MODELLING 6
2.2 Use Case Diagrams
Figure 2: Use Case Diagram
3.0 Design Overview
3.1 Solution Architecture
The solution architecture is derived from the business processes that are carried out daily by
Inshore Insurance Ltd. The main process is issuing insurance to customers and in case of
accidents or crimes, they raise an insurance claim for them to be compensated. A typical system
architecture is shown in the diagram below:
2.2 Use Case Diagrams
Figure 2: Use Case Diagram
3.0 Design Overview
3.1 Solution Architecture
The solution architecture is derived from the business processes that are carried out daily by
Inshore Insurance Ltd. The main process is issuing insurance to customers and in case of
accidents or crimes, they raise an insurance claim for them to be compensated. A typical system
architecture is shown in the diagram below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
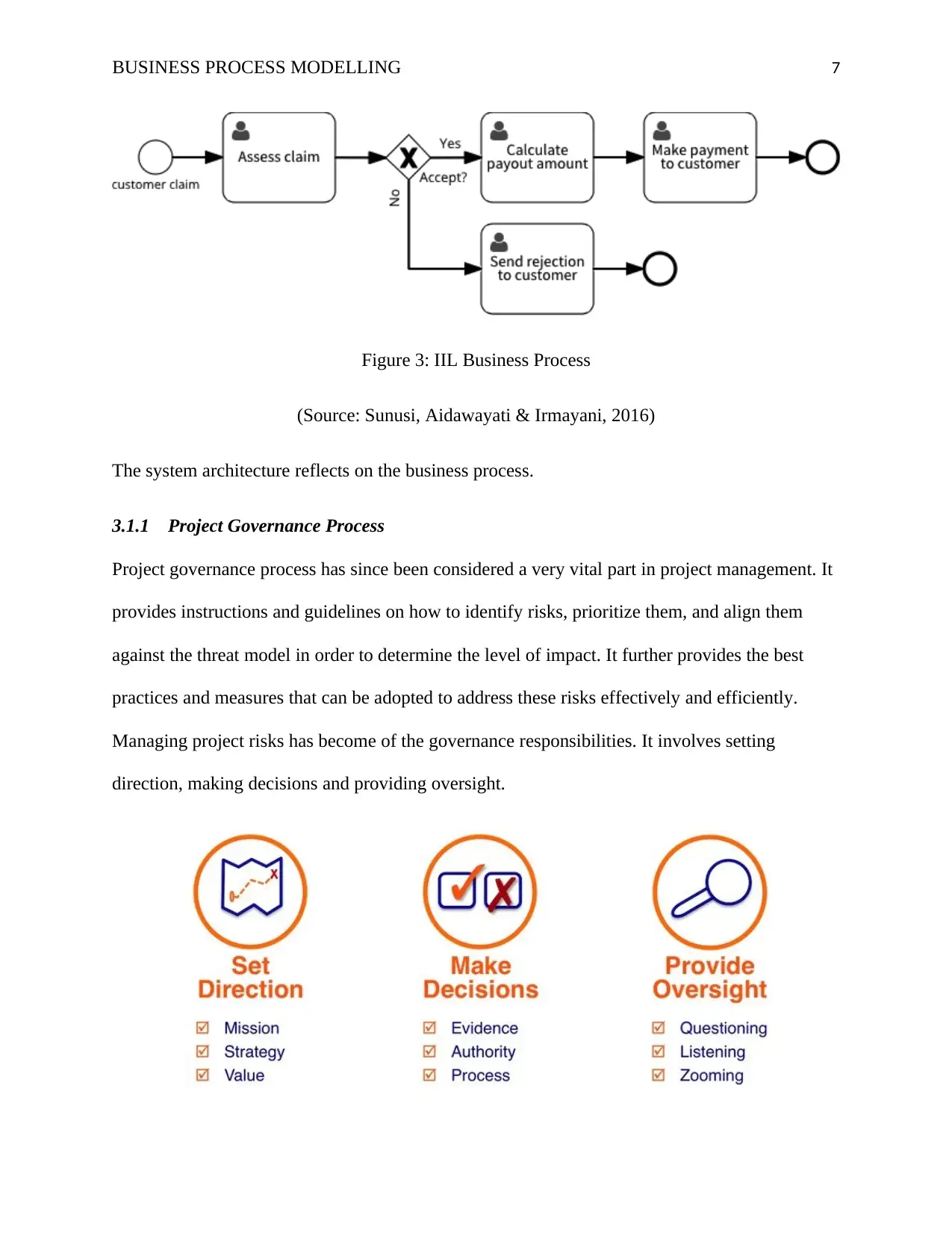
BUSINESS PROCESS MODELLING 7
Figure 3: IIL Business Process
(Source: Sunusi, Aidawayati & Irmayani, 2016)
The system architecture reflects on the business process.
3.1.1 Project Governance Process
Project governance process has since been considered a very vital part in project management. It
provides instructions and guidelines on how to identify risks, prioritize them, and align them
against the threat model in order to determine the level of impact. It further provides the best
practices and measures that can be adopted to address these risks effectively and efficiently.
Managing project risks has become of the governance responsibilities. It involves setting
direction, making decisions and providing oversight.
Figure 3: IIL Business Process
(Source: Sunusi, Aidawayati & Irmayani, 2016)
The system architecture reflects on the business process.
3.1.1 Project Governance Process
Project governance process has since been considered a very vital part in project management. It
provides instructions and guidelines on how to identify risks, prioritize them, and align them
against the threat model in order to determine the level of impact. It further provides the best
practices and measures that can be adopted to address these risks effectively and efficiently.
Managing project risks has become of the governance responsibilities. It involves setting
direction, making decisions and providing oversight.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BUSINESS PROCESS MODELLING 8
Figure 4: Project Governance Process
(Source: Clayton, 2017)
3.1.2 IT Infrastructure Solution
The solution will be defined both at conceptual and logical level. The conceptual level will
provide a general picture of how the solution will work or look like while the logical level will
provide a logical design that gives detailed information of how every unit or module of the
system works. Both the conceptual and logical designs are necessary because they act as a
guideline for the project development team and give the business a picture or design of how the
expected product should operate. Logical design acts as a reference material for the software
development team to ensure that all the specified requirements in the logical design have been
met.
3.1.3 Infrastructure Security
IT infrastructure security is very essential in ensuring data privacy and confidentiality. The
following are some of the security measures that can be adopted by IIL to ensure the security of
the infrastructure. They include:
Encrypting data during transmission: this involves encoding data and information being
transferred over the network to prevent cyber criminals from accessing and reading por
modifying the contents. Encryption is a very effective tool for transmitting sensitive
information such as usernames, passwords, credit card information, and other private
information.
Installing firewall on the network: the firewall is the first line of defense to any enterprise
network. A firewall is needed to ensure that no malicious traffic is allowed to get into the
Figure 4: Project Governance Process
(Source: Clayton, 2017)
3.1.2 IT Infrastructure Solution
The solution will be defined both at conceptual and logical level. The conceptual level will
provide a general picture of how the solution will work or look like while the logical level will
provide a logical design that gives detailed information of how every unit or module of the
system works. Both the conceptual and logical designs are necessary because they act as a
guideline for the project development team and give the business a picture or design of how the
expected product should operate. Logical design acts as a reference material for the software
development team to ensure that all the specified requirements in the logical design have been
met.
3.1.3 Infrastructure Security
IT infrastructure security is very essential in ensuring data privacy and confidentiality. The
following are some of the security measures that can be adopted by IIL to ensure the security of
the infrastructure. They include:
Encrypting data during transmission: this involves encoding data and information being
transferred over the network to prevent cyber criminals from accessing and reading por
modifying the contents. Encryption is a very effective tool for transmitting sensitive
information such as usernames, passwords, credit card information, and other private
information.
Installing firewall on the network: the firewall is the first line of defense to any enterprise
network. A firewall is needed to ensure that no malicious traffic is allowed to get into the

BUSINESS PROCESS MODELLING 9
network. It operates by analyzing the traffic that gets into the network and filters them
depending on the rules that have been set on the firewall.
Using two-factor authentication: this is a very effective approach of dealing with
unauthorized access because it ensures that other than having a password one has to use
biometric details or use a code that has been sent to email or via SMS. This prevents
unauthorized users who might have had access to the user’s password from accessing the
system because of the need to have a different authentication procedure.
Installing antiviruses and antimalware: the users’ computers should be installed with
antiviruses to detect any malicious program that might be affecting the performance of
the system, destroying files, or secretly sharing sensitive information without the users’
knowledge. Antiviruses should be updated regularly to ensure that the latest virus
signatures have been captured.
Creating access control mechanism: access control measure ensures that access privileges
and user access rights are controlled and managed to ensure that users are only accessing
what is relevant to them.
3.1.4 Application Solution
The solution is expected to be flexible enough to address the increasing needs of the business.
Additionally, it should automate the insurance claim process so as to enable customers make
their claims online and be able to receive notifications about the status of the claim. The software
should also enable users to generate and print various types of reports including financial reports,
claim reports, customer reports, pending issues among others.
network. It operates by analyzing the traffic that gets into the network and filters them
depending on the rules that have been set on the firewall.
Using two-factor authentication: this is a very effective approach of dealing with
unauthorized access because it ensures that other than having a password one has to use
biometric details or use a code that has been sent to email or via SMS. This prevents
unauthorized users who might have had access to the user’s password from accessing the
system because of the need to have a different authentication procedure.
Installing antiviruses and antimalware: the users’ computers should be installed with
antiviruses to detect any malicious program that might be affecting the performance of
the system, destroying files, or secretly sharing sensitive information without the users’
knowledge. Antiviruses should be updated regularly to ensure that the latest virus
signatures have been captured.
Creating access control mechanism: access control measure ensures that access privileges
and user access rights are controlled and managed to ensure that users are only accessing
what is relevant to them.
3.1.4 Application Solution
The solution is expected to be flexible enough to address the increasing needs of the business.
Additionally, it should automate the insurance claim process so as to enable customers make
their claims online and be able to receive notifications about the status of the claim. The software
should also enable users to generate and print various types of reports including financial reports,
claim reports, customer reports, pending issues among others.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BUSINESS PROCESS MODELLING 10
3.1.5 Data Solution
The application should facilitate structuring and classifying data for easy access and retrieval.
Classifying data make the analysis process easy because data of the same class/ category can be
analyzed at the same time. Additionally, there is need to have data archiving strategies. This is
because even if the data is no longer usable or active, it can still serve as reference material for
future cases. Therefore, the solution should provide data archiving procedures after a specific
period in order to create more space for active and usable data (Margaret, 2016).
3.2 Capacity Requirements
System performance is dependent on the capacity requirements. These requirements include
processor speed and type, size of the RAM, hard disk capacity, workload, operating system, and
number of users (TechNet, 2014). There should be minimum requirements that should be met
before using the system.
3.3 System Interfaces
The system interfaces are the first parts the users interact with. Therefore, it should be friendly
and easy to use. Expected user interfaces include registration pages for registering new
customers, employees, crimes and accidents, report generation, profile and claim analysis, search
space, data archiving panel, and payment interface. It is recommended to keep the interfaces
consistent, simple, proper use of texture and color, purposeful, and should communicate to the
user on the running processes (Garrett, 2014).
3.1.5 Data Solution
The application should facilitate structuring and classifying data for easy access and retrieval.
Classifying data make the analysis process easy because data of the same class/ category can be
analyzed at the same time. Additionally, there is need to have data archiving strategies. This is
because even if the data is no longer usable or active, it can still serve as reference material for
future cases. Therefore, the solution should provide data archiving procedures after a specific
period in order to create more space for active and usable data (Margaret, 2016).
3.2 Capacity Requirements
System performance is dependent on the capacity requirements. These requirements include
processor speed and type, size of the RAM, hard disk capacity, workload, operating system, and
number of users (TechNet, 2014). There should be minimum requirements that should be met
before using the system.
3.3 System Interfaces
The system interfaces are the first parts the users interact with. Therefore, it should be friendly
and easy to use. Expected user interfaces include registration pages for registering new
customers, employees, crimes and accidents, report generation, profile and claim analysis, search
space, data archiving panel, and payment interface. It is recommended to keep the interfaces
consistent, simple, proper use of texture and color, purposeful, and should communicate to the
user on the running processes (Garrett, 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BUSINESS PROCESS MODELLING 11
3.4 Constraints and Assumptions
The constraints include limited budget, time, and human resource. The assumptions made is that
the institution has the required infrastructure to support the system and the users have the
knowledge about the use of computers.
4.0 System Object Model
4.1 Sub Systems
The IT solution will have several subsystems that will integrate and collaborate together to
achieve a common objective. The subsystem includes finance, claims, finance and marketing,
data archiving, and system administration.
4.2 Subsystem Interfaces
The interfaces that the IT solution is expected to have are:
Customer interface- the customer should be able to register and update profile, initiate
claims and view claim status.
System administration interface- the system administrator should have full control of the
system and should be able to monitor system functionalities and troubleshoot.
Finance interface- the finance manager should be able to receive approved claims from
the claim manager and initiate the payment process.
Claims interface- the claim manager should be able to view all the customer claims,
analyze them and approve them for payment or reject depending on the outcome of the
analysis process.
Sales and marketing interface- should be able to carry out advertisement, sakes, and
promotion to increase awareness and market share.
3.4 Constraints and Assumptions
The constraints include limited budget, time, and human resource. The assumptions made is that
the institution has the required infrastructure to support the system and the users have the
knowledge about the use of computers.
4.0 System Object Model
4.1 Sub Systems
The IT solution will have several subsystems that will integrate and collaborate together to
achieve a common objective. The subsystem includes finance, claims, finance and marketing,
data archiving, and system administration.
4.2 Subsystem Interfaces
The interfaces that the IT solution is expected to have are:
Customer interface- the customer should be able to register and update profile, initiate
claims and view claim status.
System administration interface- the system administrator should have full control of the
system and should be able to monitor system functionalities and troubleshoot.
Finance interface- the finance manager should be able to receive approved claims from
the claim manager and initiate the payment process.
Claims interface- the claim manager should be able to view all the customer claims,
analyze them and approve them for payment or reject depending on the outcome of the
analysis process.
Sales and marketing interface- should be able to carry out advertisement, sakes, and
promotion to increase awareness and market share.

BUSINESS PROCESS MODELLING 12
5.0 Object Collaboration
5.1 Collaboration Diagrams
The IT solution is expected to ensure that the business processes integrate and collaborate
together to attain the business goals. The various departments should work collaboratively to
achieve business objective (Valentijn et al., 2015). Collaboration system allows employees from
different departments to work together on processes and tasks that are normally inefficient and
tedious if handled by one person. The application should support sharing of documents and other
files like videos so as to improve decision making process. Having a collaboration system will
allow employees to work remotely and provide the necessary
5.2 Access Model
In order to restrict system access, IIL should adopt access control mechanism which entails
creating password policies and guidelines of creating strong password to prevent unauthorized
access, controlling user access rights and management, password management, operating system
access control, and privilege management.
6.0 Non-Functional Requirements
6.1 Performance Considerations
The following consideration should be made
The capacity of the hard disk
Size of the RAM
Processing speed
Operating system
5.0 Object Collaboration
5.1 Collaboration Diagrams
The IT solution is expected to ensure that the business processes integrate and collaborate
together to attain the business goals. The various departments should work collaboratively to
achieve business objective (Valentijn et al., 2015). Collaboration system allows employees from
different departments to work together on processes and tasks that are normally inefficient and
tedious if handled by one person. The application should support sharing of documents and other
files like videos so as to improve decision making process. Having a collaboration system will
allow employees to work remotely and provide the necessary
5.2 Access Model
In order to restrict system access, IIL should adopt access control mechanism which entails
creating password policies and guidelines of creating strong password to prevent unauthorized
access, controlling user access rights and management, password management, operating system
access control, and privilege management.
6.0 Non-Functional Requirements
6.1 Performance Considerations
The following consideration should be made
The capacity of the hard disk
Size of the RAM
Processing speed
Operating system
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





