Southern Cross University: Cybersecurity Report on BYOD Policy Threats
VerifiedAdded on 2023/06/03
|11
|2820
|426
Report
AI Summary
This report assesses the cybersecurity risks associated with Southern Cross University's Bring Your Own Device (BYOD) policy. It identifies critical information assets and vulnerabilities, including malware, phishing, and denial-of-service attacks. The report evaluates quantitative and qualitative risk assessment approaches and proposes a risk assessment process. It also explores certificate-based authentication as a security strategy, comparing it with password-based methods. Furthermore, the report provides anti-spam guidelines, detailing key characteristics of spam and best practices for minimizing spam within the university's information system. The report concludes by recommending the implementation of certificate-based authentication and adherence to anti-spam measures to mitigate BYOD-related cybersecurity threats, ensuring user-friendly, manageable, and secure access to university resources.

CYBERSECURITY 1
CYBERSECURITY: BYOD POLICY THREATS AND SECURITY STRATEGIES
By (Name)
(Unit)
(Professor’s Name)
(University)
(City where the university is located)
(Date)
CYBERSECURITY: BYOD POLICY THREATS AND SECURITY STRATEGIES
By (Name)
(Unit)
(Professor’s Name)
(University)
(City where the university is located)
(Date)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBERSECURITY 2
Table of Contents
Introduction.................................................................................................................................................3
BYOD Risk Assessment................................................................................................................................3
BYOD Policy: Threats and Vulnerabilities.................................................................................................4
Risk Assessment......................................................................................................................................4
Certificate-Based Authentication.................................................................................................................5
Anti-spam Guideline....................................................................................................................................8
Three Examples of Spams........................................................................................................................8
Conclusion.................................................................................................................................................10
References.................................................................................................................................................11
Table of Contents
Introduction.................................................................................................................................................3
BYOD Risk Assessment................................................................................................................................3
BYOD Policy: Threats and Vulnerabilities.................................................................................................4
Risk Assessment......................................................................................................................................4
Certificate-Based Authentication.................................................................................................................5
Anti-spam Guideline....................................................................................................................................8
Three Examples of Spams........................................................................................................................8
Conclusion.................................................................................................................................................10
References.................................................................................................................................................11

CYBERSECURITY 3
Introduction
In the current world of technological evolution, people and institutions rely on the
information systems to communicate and share information as well as store vital institution’s
data. Information system involves a network of assets which co-ordinate together to store,
transform, retrieve and disseminate information of a learning institution, a corporation or a
business. Information systems have essential contributions to the educational sector. To
harness the benefits of individuals using their own electronic devices the Southern Cross
University have adopted the policy of Bring Your Device (BYOD) to classes at Performance
Education.
The use of these electronic devices to access, process and create the information and
data of the university generates issues concerning information security breaches. The
institution needs to implement strategies to prevent security breaches to the information and
data. The university should undertake the information security strategies to guarantee that it
still controls and manages the data accessed using BYOD device and also ensure that few
reasonably possible restrictions are imposed on the university information resources accessed
utilizing the BYOD policy.
This report analyzes the critical information assets of the university and discusses the
threats caused by BYOD policy. It will also explore certificate-based authentication and compare
with another authentication technique and also provide spam handling instructions for the
university.
TASK 1
BYOD Risk Assessment
In developing, information security strategy, the first essential procedure is to identify
and comprehend the critical assets that require protection. The critical information assets in an
organization are the assets that impact integrity, confidentiality, availability and support the
institution’s mission and vision and it strategic objectives (Boranbayev, Mazhitov & Kakhanov
2015).
The critical information assets of Southern Cross University are namely
Educational and research: examinations, intellectual development, research projects
and information about students
Human resources: personal data of staff and reports.
Legal: contracts and internal documentation, employees confidential information of
staff
Introduction
In the current world of technological evolution, people and institutions rely on the
information systems to communicate and share information as well as store vital institution’s
data. Information system involves a network of assets which co-ordinate together to store,
transform, retrieve and disseminate information of a learning institution, a corporation or a
business. Information systems have essential contributions to the educational sector. To
harness the benefits of individuals using their own electronic devices the Southern Cross
University have adopted the policy of Bring Your Device (BYOD) to classes at Performance
Education.
The use of these electronic devices to access, process and create the information and
data of the university generates issues concerning information security breaches. The
institution needs to implement strategies to prevent security breaches to the information and
data. The university should undertake the information security strategies to guarantee that it
still controls and manages the data accessed using BYOD device and also ensure that few
reasonably possible restrictions are imposed on the university information resources accessed
utilizing the BYOD policy.
This report analyzes the critical information assets of the university and discusses the
threats caused by BYOD policy. It will also explore certificate-based authentication and compare
with another authentication technique and also provide spam handling instructions for the
university.
TASK 1
BYOD Risk Assessment
In developing, information security strategy, the first essential procedure is to identify
and comprehend the critical assets that require protection. The critical information assets in an
organization are the assets that impact integrity, confidentiality, availability and support the
institution’s mission and vision and it strategic objectives (Boranbayev, Mazhitov & Kakhanov
2015).
The critical information assets of Southern Cross University are namely
Educational and research: examinations, intellectual development, research projects
and information about students
Human resources: personal data of staff and reports.
Legal: contracts and internal documentation, employees confidential information of
staff
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBERSECURITY 4
Finance and Economics: financial information and procurement documentation
Information Technology: Databases, logins, and passwords, IT management information
and IT developments copyright
BYOD Policy: Threats and Vulnerabilities
The adopted BYOD policy in classes at Performance education will arise various threats
to the identified critical information assets of the university. Organizations have no complete or
little control of the electronic devices in which their employees are utilizing and also have no
control of the security conditions when employees are assessing its information systems (Dang-
Pham & Pittayachawan 2015). The threats which may be brought by the BYOD policy are
malware, phishing, social engineering, malicious mobile applications and Denial of service.
Phishing is a well-constructed email that evades the network security strategies and obtains
information systems data (Chang et al. 2014).
Malware is a rapidly growing information systems problem due to a high number of
downloads and applications (Patten & Harris 2013). Malware may be utilized to steal the
confidential information of employees and students and deviate financial transactions by using
the security vulnerabilities such as insecure wireless networks and weak firewalls brought
about by the mobile devices which cannot be controlled by the information technology
department (Cuevas et al. 2015). Phishing utilizes vulnerabilities such as personal cloud services
and social networks in an unacknowledged staff or student collaboration environment to obtain
financial gain and steal personal information. In social engineering, spam emails and spam on
social networks utilize the vulnerabilities of human emotions to spread malware and
inappropriately obtain confidential staff and students’ data. Denial of service threats results
from vulnerabilities due to improper network planning resulting from the adoption of mobile
electronic devices results in attacks on databases and log repositories. Vulnerabilities such as
mobile device misconfiguration occur when employees install unauthorized and non-corporate
applications which then provide opportunities for stealing institution information such as legal
documents.
Risk Assessment
Information system risk assessment is implemented to give an a prioritized assessment
and evaluation of the probability and impact of information security occurrences and
presenting the potential threat to the information from each scenario as well as the existing
protective measures (Shedden et al. 2016). In deciding whether to implement a quantitative
and qualitative risk assessment, the advantages and disadvantages of the two frameworks are
analyzed. Quantitative style advantage is that it takes into consideration the risks and locates
section that requires urgent action (Tixteco et al. 2017). Its disadvantage is that it makes cost-
benefit analysis difficult because it does not provide specific, quantifiable magnitude of impacts
Finance and Economics: financial information and procurement documentation
Information Technology: Databases, logins, and passwords, IT management information
and IT developments copyright
BYOD Policy: Threats and Vulnerabilities
The adopted BYOD policy in classes at Performance education will arise various threats
to the identified critical information assets of the university. Organizations have no complete or
little control of the electronic devices in which their employees are utilizing and also have no
control of the security conditions when employees are assessing its information systems (Dang-
Pham & Pittayachawan 2015). The threats which may be brought by the BYOD policy are
malware, phishing, social engineering, malicious mobile applications and Denial of service.
Phishing is a well-constructed email that evades the network security strategies and obtains
information systems data (Chang et al. 2014).
Malware is a rapidly growing information systems problem due to a high number of
downloads and applications (Patten & Harris 2013). Malware may be utilized to steal the
confidential information of employees and students and deviate financial transactions by using
the security vulnerabilities such as insecure wireless networks and weak firewalls brought
about by the mobile devices which cannot be controlled by the information technology
department (Cuevas et al. 2015). Phishing utilizes vulnerabilities such as personal cloud services
and social networks in an unacknowledged staff or student collaboration environment to obtain
financial gain and steal personal information. In social engineering, spam emails and spam on
social networks utilize the vulnerabilities of human emotions to spread malware and
inappropriately obtain confidential staff and students’ data. Denial of service threats results
from vulnerabilities due to improper network planning resulting from the adoption of mobile
electronic devices results in attacks on databases and log repositories. Vulnerabilities such as
mobile device misconfiguration occur when employees install unauthorized and non-corporate
applications which then provide opportunities for stealing institution information such as legal
documents.
Risk Assessment
Information system risk assessment is implemented to give an a prioritized assessment
and evaluation of the probability and impact of information security occurrences and
presenting the potential threat to the information from each scenario as well as the existing
protective measures (Shedden et al. 2016). In deciding whether to implement a quantitative
and qualitative risk assessment, the advantages and disadvantages of the two frameworks are
analyzed. Quantitative style advantage is that it takes into consideration the risks and locates
section that requires urgent action (Tixteco et al. 2017). Its disadvantage is that it makes cost-
benefit analysis difficult because it does not provide specific, quantifiable magnitude of impacts
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBERSECURITY 5
measurements. Qualitative style advantage is that it provides cost-benefit analysis since it
provides specific, quantifiable magnitude of impacts measurements. Its disadvantage is that its
outcomes may be unclear depending on the measurements' numerical range.
The risk assessment process to be used by the university is outlined below;
I. Determine the critical processes of the university that guide and support them in
attaining the institution’s objectives and mission. The senior administrators and the
information systems senior officers should develop a framework for determining the
critical processes of the university.
II. Identification of the information assets from the determined critical processes
undertaken by the university in achieving their duties and mission objectives.
III. Establishment of the risk analysis scope and the objectives by considering the critical
processes and the information assets of the university and taking into account the
resources available to execute the activities.
IV. Review of the Institution’s environment and develop a list of the possible threats
scenarios and potential threat agents.
V. Evaluation of the risk scenarios by determining the probability of threat occurrence and
their potential impact on the institution’s information systems
VI. Determination of the framework for solving the identified risk; prevention, mitigation,
avoidance,
VII. Determine the cost-benefit analysis of the defined risk scenarios by taking into account
the risk level of the classified information assets.
VIII. Selecting the security strategies to be adopted to lessen the risk levels on the critical
information system assets of the institution
Task 2
Certificate-Based Authentication
Introduction
Threats of Bring Your Device and threats of rogue machines has resulted in institutions
adopting information security strategies that ensure approved users and devices to access the
network resources. One such security strategy which should be adopted by the Southern Cross
University is Certificate-Based Authentication. This technique employs the use of a digital
certificate to identify a user and device before giving access to an organization’s information
system resources. Certificate-Based Authentication comes with various benefits namely user-
friendly, easy deployment and management, mutual authentication, easy to extend to eternal
users and leverages on existing policies.
measurements. Qualitative style advantage is that it provides cost-benefit analysis since it
provides specific, quantifiable magnitude of impacts measurements. Its disadvantage is that its
outcomes may be unclear depending on the measurements' numerical range.
The risk assessment process to be used by the university is outlined below;
I. Determine the critical processes of the university that guide and support them in
attaining the institution’s objectives and mission. The senior administrators and the
information systems senior officers should develop a framework for determining the
critical processes of the university.
II. Identification of the information assets from the determined critical processes
undertaken by the university in achieving their duties and mission objectives.
III. Establishment of the risk analysis scope and the objectives by considering the critical
processes and the information assets of the university and taking into account the
resources available to execute the activities.
IV. Review of the Institution’s environment and develop a list of the possible threats
scenarios and potential threat agents.
V. Evaluation of the risk scenarios by determining the probability of threat occurrence and
their potential impact on the institution’s information systems
VI. Determination of the framework for solving the identified risk; prevention, mitigation,
avoidance,
VII. Determine the cost-benefit analysis of the defined risk scenarios by taking into account
the risk level of the classified information assets.
VIII. Selecting the security strategies to be adopted to lessen the risk levels on the critical
information system assets of the institution
Task 2
Certificate-Based Authentication
Introduction
Threats of Bring Your Device and threats of rogue machines has resulted in institutions
adopting information security strategies that ensure approved users and devices to access the
network resources. One such security strategy which should be adopted by the Southern Cross
University is Certificate-Based Authentication. This technique employs the use of a digital
certificate to identify a user and device before giving access to an organization’s information
system resources. Certificate-Based Authentication comes with various benefits namely user-
friendly, easy deployment and management, mutual authentication, easy to extend to eternal
users and leverages on existing policies.

CYBERSECURITY 6
Working Principle of certificate based authentication
The working principle of certificate-based authentication can be elaborated in the
following steps (O'Neil et al. 2017);
1) A certificate with published public keys is issued for a client, and private keys database
corresponding to the public keys is maintained by the client software. The password to
the database is given to the client upon request for the first time in any given session.
2) The private key for the user’s certificate is retrieved by the client by unlocking the
private database and then utilizes the private key to digitally sign randomly generated
data. The digitally signed data and the signature act as evidence for the validity of the
private key
3) The randomly generated signed data evidence and the user’s certificate is then sent by
the client through the network
4) The server then utilizes the submitted evidence and the user's certificate to authenticate
the identity of the user.
5) Finally, the server further performs other authentication tasks such as the presence of a
certificate in an LDAP entry evaluation of the client permission to access a particular
resource. If the user is allowed, its then enable the user to access the requested the
information system resource.
A typical certificate based authentication is where a server requests a client to provide a
valid certificate in order to allow access (O'Neil et al. 2017). The user then authenticates with
his username and password. User’s identity is not performed in this type of authentication since
the certificate is not cross-checked (Figure 1).
Figure 1: Typical certificate based authentication framework
Working Principle of certificate based authentication
The working principle of certificate-based authentication can be elaborated in the
following steps (O'Neil et al. 2017);
1) A certificate with published public keys is issued for a client, and private keys database
corresponding to the public keys is maintained by the client software. The password to
the database is given to the client upon request for the first time in any given session.
2) The private key for the user’s certificate is retrieved by the client by unlocking the
private database and then utilizes the private key to digitally sign randomly generated
data. The digitally signed data and the signature act as evidence for the validity of the
private key
3) The randomly generated signed data evidence and the user’s certificate is then sent by
the client through the network
4) The server then utilizes the submitted evidence and the user's certificate to authenticate
the identity of the user.
5) Finally, the server further performs other authentication tasks such as the presence of a
certificate in an LDAP entry evaluation of the client permission to access a particular
resource. If the user is allowed, its then enable the user to access the requested the
information system resource.
A typical certificate based authentication is where a server requests a client to provide a
valid certificate in order to allow access (O'Neil et al. 2017). The user then authenticates with
his username and password. User’s identity is not performed in this type of authentication since
the certificate is not cross-checked (Figure 1).
Figure 1: Typical certificate based authentication framework
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
CYBERSECURITY 7
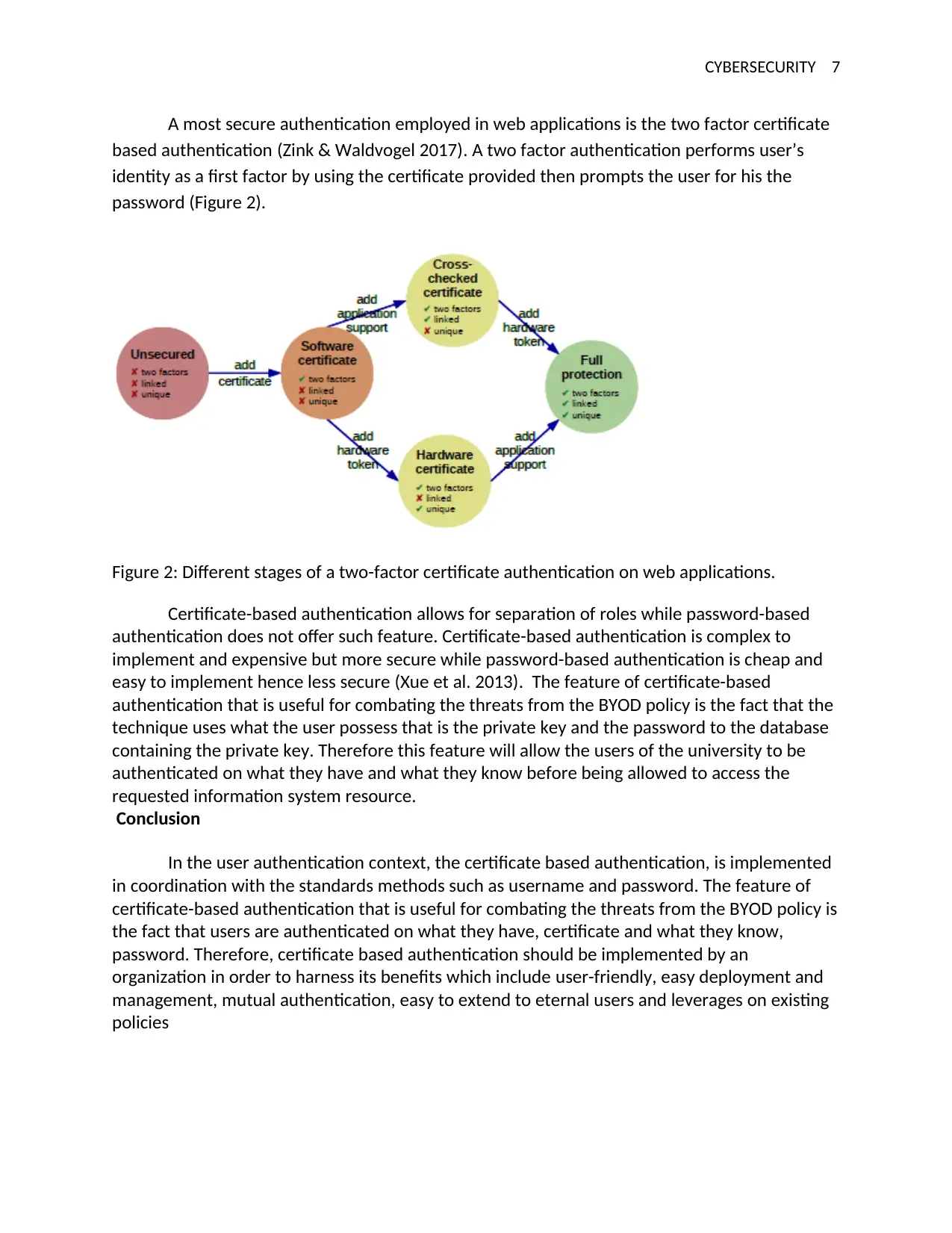
A most secure authentication employed in web applications is the two factor certificate
based authentication (Zink & Waldvogel 2017). A two factor authentication performs user’s
identity as a first factor by using the certificate provided then prompts the user for his the
password (Figure 2).
Figure 2: Different stages of a two-factor certificate authentication on web applications.
Certificate-based authentication allows for separation of roles while password-based
authentication does not offer such feature. Certificate-based authentication is complex to
implement and expensive but more secure while password-based authentication is cheap and
easy to implement hence less secure (Xue et al. 2013). The feature of certificate-based
authentication that is useful for combating the threats from the BYOD policy is the fact that the
technique uses what the user possess that is the private key and the password to the database
containing the private key. Therefore this feature will allow the users of the university to be
authenticated on what they have and what they know before being allowed to access the
requested information system resource.
Conclusion
In the user authentication context, the certificate based authentication, is implemented
in coordination with the standards methods such as username and password. The feature of
certificate-based authentication that is useful for combating the threats from the BYOD policy is
the fact that users are authenticated on what they have, certificate and what they know,
password. Therefore, certificate based authentication should be implemented by an
organization in order to harness its benefits which include user-friendly, easy deployment and
management, mutual authentication, easy to extend to eternal users and leverages on existing
policies
A most secure authentication employed in web applications is the two factor certificate
based authentication (Zink & Waldvogel 2017). A two factor authentication performs user’s
identity as a first factor by using the certificate provided then prompts the user for his the
password (Figure 2).
Figure 2: Different stages of a two-factor certificate authentication on web applications.
Certificate-based authentication allows for separation of roles while password-based
authentication does not offer such feature. Certificate-based authentication is complex to
implement and expensive but more secure while password-based authentication is cheap and
easy to implement hence less secure (Xue et al. 2013). The feature of certificate-based
authentication that is useful for combating the threats from the BYOD policy is the fact that the
technique uses what the user possess that is the private key and the password to the database
containing the private key. Therefore this feature will allow the users of the university to be
authenticated on what they have and what they know before being allowed to access the
requested information system resource.
Conclusion
In the user authentication context, the certificate based authentication, is implemented
in coordination with the standards methods such as username and password. The feature of
certificate-based authentication that is useful for combating the threats from the BYOD policy is
the fact that users are authenticated on what they have, certificate and what they know,
password. Therefore, certificate based authentication should be implemented by an
organization in order to harness its benefits which include user-friendly, easy deployment and
management, mutual authentication, easy to extend to eternal users and leverages on existing
policies
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CYBERSECURITY 8
Task 3
Anti-spam Guideline
Spam relay the following key characteristics mass mailing, sender anonymity and
unsolicited. The major elements of the Spam Act 2003 provided that information any who
authorized the sending of a commercial electronic messages must be included in the messages,
commercial electronic messages enclose functional facility for unsubscribing, no use of an
address harvesting software and civil penalties and injections are the main penalties of the
Spam Act 2003 (Australian Government 2003).
Three Examples of Spams
1.
2.
Task 3
Anti-spam Guideline
Spam relay the following key characteristics mass mailing, sender anonymity and
unsolicited. The major elements of the Spam Act 2003 provided that information any who
authorized the sending of a commercial electronic messages must be included in the messages,
commercial electronic messages enclose functional facility for unsubscribing, no use of an
address harvesting software and civil penalties and injections are the main penalties of the
Spam Act 2003 (Australian Government 2003).
Three Examples of Spams
1.
2.
CYBERSECURITY 9
3.
The above examples of spam are obtained from itgsnews website; http://www.itgsnews.com/spam-and-
phishing-examples-itgs-revision/
Below are Anti-spam Guidelines and Best Practices that should be adopted by the
university to minimize spam within their information system.
Staffs should not use office replies to external messages, when applying an automatic
response for emails when not in the office, and should make it be sent only to their
contacts and not everyone.
Spam incidents reports should be reported to the specific domain where the spam was
received from.
Avoid providing your official email addresses when signing up to other websites mainly if
the website does not ensure a guarantee of privacy for the provided personal details.
The staff and the students should avoid providing email addresses in public blogs or
forums because have developed scripts that can notice email addresses and links in blog
pages.
Both the staff and the students should unsubscribe from non-required newsletters or
notifications by unchecking the newsletters and notifications boxes in website
Every user should disable auto-download of external images and their display of
because many spammers embed their phishing emails in external images.
3.
The above examples of spam are obtained from itgsnews website; http://www.itgsnews.com/spam-and-
phishing-examples-itgs-revision/
Below are Anti-spam Guidelines and Best Practices that should be adopted by the
university to minimize spam within their information system.
Staffs should not use office replies to external messages, when applying an automatic
response for emails when not in the office, and should make it be sent only to their
contacts and not everyone.
Spam incidents reports should be reported to the specific domain where the spam was
received from.
Avoid providing your official email addresses when signing up to other websites mainly if
the website does not ensure a guarantee of privacy for the provided personal details.
The staff and the students should avoid providing email addresses in public blogs or
forums because have developed scripts that can notice email addresses and links in blog
pages.
Both the staff and the students should unsubscribe from non-required newsletters or
notifications by unchecking the newsletters and notifications boxes in website
Every user should disable auto-download of external images and their display of
because many spammers embed their phishing emails in external images.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBERSECURITY 10
IT administrator should Customize of SPF/DKM filtering from the control panel and
analyzed against adopted policies to avoid spam messages.
IT administrator should perform Spam filtering by checking the IP addresses and
domains against a developed blacklist exhaustive lists.
Conclusion
The adopted BYOD policy in classes at Performance education will result in various potential
threats to the critical information assets of the university. The critical information assets in an
organization are the assets that impact integrity, confidentiality, availability and support the
institution’s mission and vision and it strategic objectives. The University has adopted various
information security strategies including certificate-based authentication to guarantee that it
still controls and manages the data accessed using the BYOD device and also controls who
accesses the information system resources. The University should encourage their staff and
employees to adopt the developed Anti-spam guidelines to reduce, avoid and prevent
spamming of the university information system resources.
References
IT administrator should Customize of SPF/DKM filtering from the control panel and
analyzed against adopted policies to avoid spam messages.
IT administrator should perform Spam filtering by checking the IP addresses and
domains against a developed blacklist exhaustive lists.
Conclusion
The adopted BYOD policy in classes at Performance education will result in various potential
threats to the critical information assets of the university. The critical information assets in an
organization are the assets that impact integrity, confidentiality, availability and support the
institution’s mission and vision and it strategic objectives. The University has adopted various
information security strategies including certificate-based authentication to guarantee that it
still controls and manages the data accessed using the BYOD device and also controls who
accesses the information system resources. The University should encourage their staff and
employees to adopt the developed Anti-spam guidelines to reduce, avoid and prevent
spamming of the university information system resources.
References
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBERSECURITY 11
Australian Government 2003, 'Spam Act 2003', Government Act, Australian Governemnt.
Boranbayev, A, Mazhitov, M & Kakhanov, Z 2015, 'Implementation of Security Systems for Prevention of
Loss of Information at Organizations of Higher Education', 2015 12th International Conference on
Information Technology-New generations, Las Vegas, NV.
Chang, J, J, Ho, PC & Chang, TC 2014, ' Securing BYOD', IT Professional, vol 16, no. 5, pp. 9-11.
Cuevas, PD, Mora, A, Merelo, J, Castillo, P, Sanchez, PG & Fernandez-Ares, A 2015, 'Corporate security
solutions for BYOD: A novel user-centric and self-adaptive system', Computer Communications, vol 68,
pp. 83–95.
Dang-Pham, D & Pittayachawan, S 2015, 'Comparing intention to avoid malware across contexts in a
BYOD-enabled Australian university: A protection motivation theory approach', Computers & Security,
vol 48, pp. 281-297.
O'Neil, M, Heidbrink, S, Ruoti, S, Whitehead, J, Bunker, D, Dickinson, L, Hendershot, T, Reynolds, J,
Seamons, K & Zappala, D 2017, 'TrustBase: An Architecture to Repair and Strengthen Certificate-based
Authentication', Proceeedings of the 26th USENIX Security Symposium, Usenix, Vancouver, BC, Canada.
Patten, KP & Harris, MA 2013, 'The Need to Address Mobile Device Security in the Higher Education IT
Curriculum', Journal of Information Systems Education, vol 24, no. 1, pp. 41-52.
Shedden, P, Ahmad, A, Smith, W, Tscherning, H & Scheepers, R 2016, 'Asset Identification in Information
Security Risk Assessment: A Business Practice Approach', Communications of the Association for
Information Systems, vol 39, no. 15, pp. 297-320.
Tixteco, LP, Tixteco, MC, Perez, GS, Medina, LK, Gomez, J & Tellez, AC 2017, 'Recommendations for Risk
Analysis in Higher Education Institutions', The Eleventh International Conference on Emerging Security
Information, Systems and Technologies, IARIA.
Xue, K, Ma, C, Hong, P & Ding, R 2013, 'A temporal-credential-based mutual authentication and key
agreement scheme for wireless sensor networks', Journal of Network and Computer Applications, vol 36,
no. 1, pp. 316-323, https://DOI.org/10.1016/j.jnca.2012.05.010.
Zink, T & Waldvogel, M 2017, 'X.509 User Certificate-based Two-Factor Authentication For Web
Applications', Technical report, Department of Computer and Information Science, University of
Konstanz, KN-2017-DISY-03, Distributed Systems Laboratory, Germany.
Australian Government 2003, 'Spam Act 2003', Government Act, Australian Governemnt.
Boranbayev, A, Mazhitov, M & Kakhanov, Z 2015, 'Implementation of Security Systems for Prevention of
Loss of Information at Organizations of Higher Education', 2015 12th International Conference on
Information Technology-New generations, Las Vegas, NV.
Chang, J, J, Ho, PC & Chang, TC 2014, ' Securing BYOD', IT Professional, vol 16, no. 5, pp. 9-11.
Cuevas, PD, Mora, A, Merelo, J, Castillo, P, Sanchez, PG & Fernandez-Ares, A 2015, 'Corporate security
solutions for BYOD: A novel user-centric and self-adaptive system', Computer Communications, vol 68,
pp. 83–95.
Dang-Pham, D & Pittayachawan, S 2015, 'Comparing intention to avoid malware across contexts in a
BYOD-enabled Australian university: A protection motivation theory approach', Computers & Security,
vol 48, pp. 281-297.
O'Neil, M, Heidbrink, S, Ruoti, S, Whitehead, J, Bunker, D, Dickinson, L, Hendershot, T, Reynolds, J,
Seamons, K & Zappala, D 2017, 'TrustBase: An Architecture to Repair and Strengthen Certificate-based
Authentication', Proceeedings of the 26th USENIX Security Symposium, Usenix, Vancouver, BC, Canada.
Patten, KP & Harris, MA 2013, 'The Need to Address Mobile Device Security in the Higher Education IT
Curriculum', Journal of Information Systems Education, vol 24, no. 1, pp. 41-52.
Shedden, P, Ahmad, A, Smith, W, Tscherning, H & Scheepers, R 2016, 'Asset Identification in Information
Security Risk Assessment: A Business Practice Approach', Communications of the Association for
Information Systems, vol 39, no. 15, pp. 297-320.
Tixteco, LP, Tixteco, MC, Perez, GS, Medina, LK, Gomez, J & Tellez, AC 2017, 'Recommendations for Risk
Analysis in Higher Education Institutions', The Eleventh International Conference on Emerging Security
Information, Systems and Technologies, IARIA.
Xue, K, Ma, C, Hong, P & Ding, R 2013, 'A temporal-credential-based mutual authentication and key
agreement scheme for wireless sensor networks', Journal of Network and Computer Applications, vol 36,
no. 1, pp. 316-323, https://DOI.org/10.1016/j.jnca.2012.05.010.
Zink, T & Waldvogel, M 2017, 'X.509 User Certificate-based Two-Factor Authentication For Web
Applications', Technical report, Department of Computer and Information Science, University of
Konstanz, KN-2017-DISY-03, Distributed Systems Laboratory, Germany.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





