BYOD Policy Risk Assessment, Certificate Authentication & Spam Report
VerifiedAdded on 2023/06/05
|14
|2624
|89
Report
AI Summary
This report assesses the risks associated with a Bring Your Own Device (BYOD) policy to a university's information system. It identifies the most critical components of the system and prioritizes information assets based on their value and potential vulnerabilities. The report includes a technical analysis of certificate-based authentication as a security mechanism, highlighting its advantages, disadvantages, working principles, and differences from password-based authentication. Furthermore, it offers practical guidelines for university students and staff on combating spam, including identifying characteristics of spam messages, examples of different types of spam, and instructions for handling spam effectively. The report also provides recommendations for IT administrators on minimizing spam threats through software updates, sender authentication, recipient validation, and connection classification. This document is available on Desklib, where students can find a wealth of study resources including past papers and solved assignments.

1
STUDENT’S NAME
COURSE
INSTITUTION
DATE
STUDENT’S NAME
COURSE
INSTITUTION
DATE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Executive Summary.
The purpose of this report is to assess the risk from the BYOD policy to the university’s
information system, to identify the most critical component of the university information system,
to write a technical report on the certificate based authentication mechanism and to develop a
guideline of how university students and staff combat the threat of spam.
Executive Summary.
The purpose of this report is to assess the risk from the BYOD policy to the university’s
information system, to identify the most critical component of the university information system,
to write a technical report on the certificate based authentication mechanism and to develop a
guideline of how university students and staff combat the threat of spam.

3
Contents
2.0 Introduction..............................................................................................................................5
3.0Information Asset Classification.............................................................................................6
3.1 Information Asset Valuation..............................................................................................6
3.2 Information Asset Prioritization........................................................................................6
4.0 Certificate based authentication.............................................................................................9
4.1 Advantages of certificate based authentication................................................................9
4.4 Differences between certificate based authentication and password based
authentication...........................................................................................................................10
4.5 Useful features of certificate-based authentication for BYOD policy...........................10
5.0 Spam........................................................................................................................................11
Characteristics of spam..............................................................................................................11
5.1 Types of electronic messages to be treated as spam:......................................................11
5.2 Examples of spam messages..................................................................................................11
Instruction to users on how to handle spam..........................................................................12
Instruction to the IT administrator of how to minimize spam threat................................12
References.....................................................................................................................................13
Contents
2.0 Introduction..............................................................................................................................5
3.0Information Asset Classification.............................................................................................6
3.1 Information Asset Valuation..............................................................................................6
3.2 Information Asset Prioritization........................................................................................6
4.0 Certificate based authentication.............................................................................................9
4.1 Advantages of certificate based authentication................................................................9
4.4 Differences between certificate based authentication and password based
authentication...........................................................................................................................10
4.5 Useful features of certificate-based authentication for BYOD policy...........................10
5.0 Spam........................................................................................................................................11
Characteristics of spam..............................................................................................................11
5.1 Types of electronic messages to be treated as spam:......................................................11
5.2 Examples of spam messages..................................................................................................11
Instruction to users on how to handle spam..........................................................................12
Instruction to the IT administrator of how to minimize spam threat................................12
References.....................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
1.0 List of figures.
Fig 1: Weighted Factor Analysis Worksheet.
Fig 2: TVA worksheet.
1.0 List of figures.
Fig 1: Weighted Factor Analysis Worksheet.
Fig 2: TVA worksheet.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
2.0 Introduction.
Information system is a combination of software, hardware and telecommunications that people
build and use to collect, create and distribute useful data, mostly in organizational settings
(Elliott 2018)
2.0 Introduction.
Information system is a combination of software, hardware and telecommunications that people
build and use to collect, create and distribute useful data, mostly in organizational settings
(Elliott 2018)

6
Task 1.
3.0Information Asset Classification.
Many organizations use data classification schemes such as internal, public data. Classification
of components must be specific to allow determination of private levels. Categories must be
mutually exclusive that is to say an asset must belong to only one category (Bello, Murray &
Armarego 2017).
3.1 Information Asset Valuation.
Coming up with questions will help develop the criteria for valuation of asset. Like which
information asset is:
1. Generates the most revenue?
2. Would be more expensive to replace or protect?
3. Is most critical to the organizations success?
3.2 Information Asset Prioritization.
Information asset will be prioritized by creating weighting for each category based on the
answers to questions. Calculate relative importance of each asset based on weighted factor
analysis. List the assets in order of importance using a weighted factor analysis worksheet.
Task 1.
3.0Information Asset Classification.
Many organizations use data classification schemes such as internal, public data. Classification
of components must be specific to allow determination of private levels. Categories must be
mutually exclusive that is to say an asset must belong to only one category (Bello, Murray &
Armarego 2017).
3.1 Information Asset Valuation.
Coming up with questions will help develop the criteria for valuation of asset. Like which
information asset is:
1. Generates the most revenue?
2. Would be more expensive to replace or protect?
3. Is most critical to the organizations success?
3.2 Information Asset Prioritization.
Information asset will be prioritized by creating weighting for each category based on the
answers to questions. Calculate relative importance of each asset based on weighted factor
analysis. List the assets in order of importance using a weighted factor analysis worksheet.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
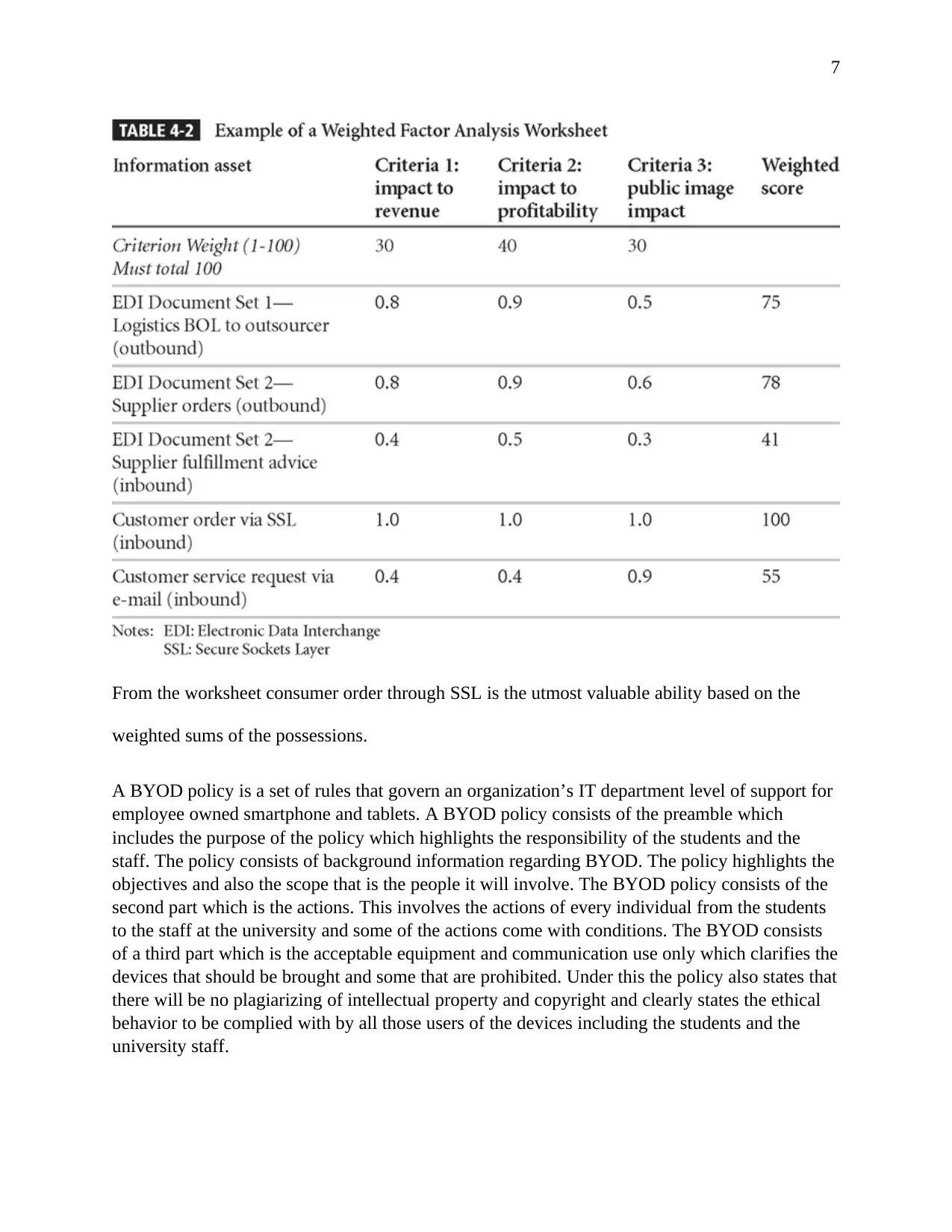
7
From the worksheet consumer order through SSL is the utmost valuable ability based on the
weighted sums of the possessions.
A BYOD policy is a set of rules that govern an organization’s IT department level of support for
employee owned smartphone and tablets. A BYOD policy consists of the preamble which
includes the purpose of the policy which highlights the responsibility of the students and the
staff. The policy consists of background information regarding BYOD. The policy highlights the
objectives and also the scope that is the people it will involve. The BYOD policy consists of the
second part which is the actions. This involves the actions of every individual from the students
to the staff at the university and some of the actions come with conditions. The BYOD consists
of a third part which is the acceptable equipment and communication use only which clarifies the
devices that should be brought and some that are prohibited. Under this the policy also states that
there will be no plagiarizing of intellectual property and copyright and clearly states the ethical
behavior to be complied with by all those users of the devices including the students and the
university staff.
From the worksheet consumer order through SSL is the utmost valuable ability based on the
weighted sums of the possessions.
A BYOD policy is a set of rules that govern an organization’s IT department level of support for
employee owned smartphone and tablets. A BYOD policy consists of the preamble which
includes the purpose of the policy which highlights the responsibility of the students and the
staff. The policy consists of background information regarding BYOD. The policy highlights the
objectives and also the scope that is the people it will involve. The BYOD policy consists of the
second part which is the actions. This involves the actions of every individual from the students
to the staff at the university and some of the actions come with conditions. The BYOD consists
of a third part which is the acceptable equipment and communication use only which clarifies the
devices that should be brought and some that are prohibited. Under this the policy also states that
there will be no plagiarizing of intellectual property and copyright and clearly states the ethical
behavior to be complied with by all those users of the devices including the students and the
university staff.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
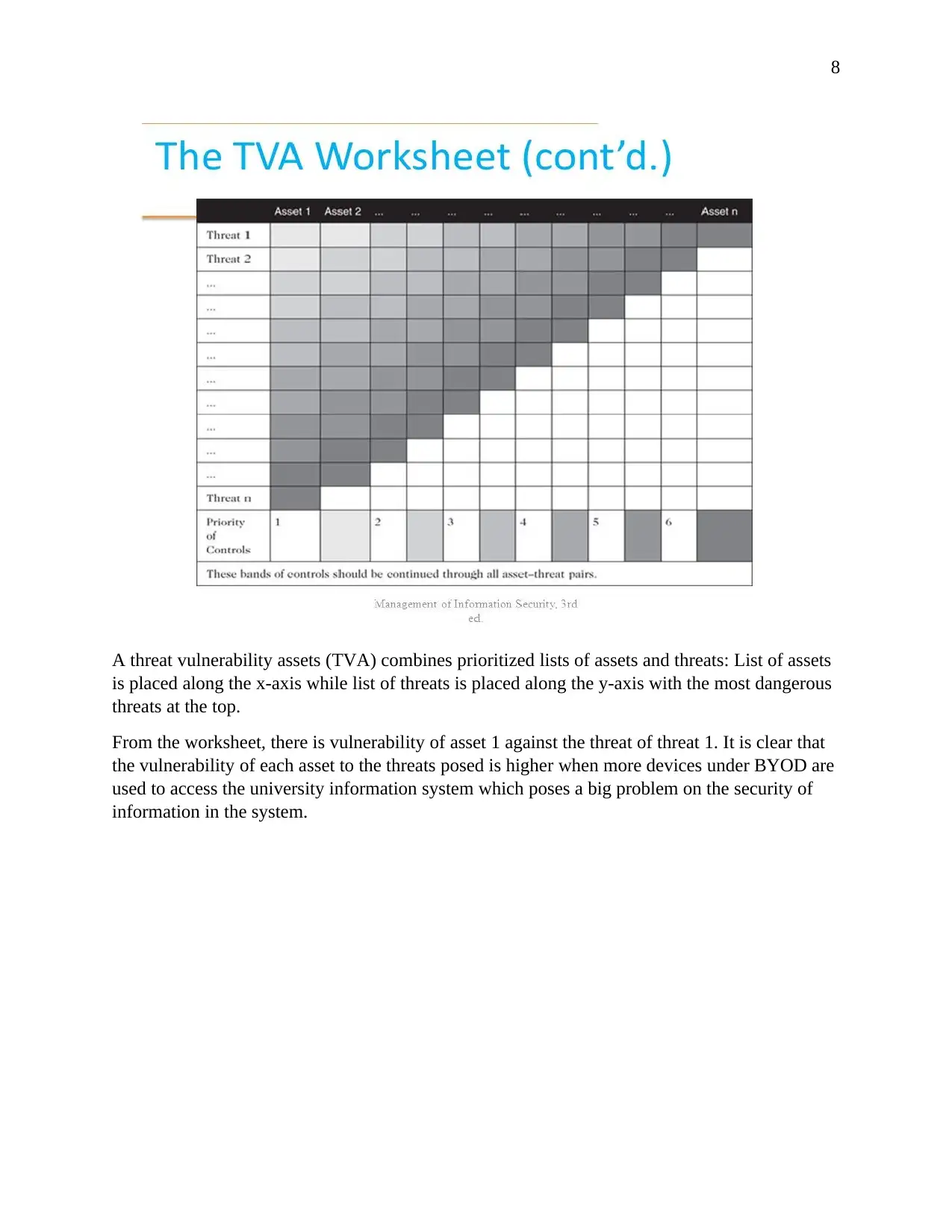
8
A threat vulnerability assets (TVA) combines prioritized lists of assets and threats: List of assets
is placed along the x-axis while list of threats is placed along the y-axis with the most dangerous
threats at the top.
From the worksheet, there is vulnerability of asset 1 against the threat of threat 1. It is clear that
the vulnerability of each asset to the threats posed is higher when more devices under BYOD are
used to access the university information system which poses a big problem on the security of
information in the system.
A threat vulnerability assets (TVA) combines prioritized lists of assets and threats: List of assets
is placed along the x-axis while list of threats is placed along the y-axis with the most dangerous
threats at the top.
From the worksheet, there is vulnerability of asset 1 against the threat of threat 1. It is clear that
the vulnerability of each asset to the threats posed is higher when more devices under BYOD are
used to access the university information system which poses a big problem on the security of
information in the system.

9
4.0 Certificate based authentication
Certificate-based endorsement is the practice of a digital credential to identify a user, appliance,
or gadget before allowing access to a resource or a linkage (Kawan et al .2017).In the case of
user verification, it is installed in coordination with old-fashioned method of authentication such
as keyword authentication (Bratthall & Lindstrom 2018).
4.1 Advantages of certificate based authentication.
1. It is user-friendly – Once the certificate is installed it’s easy to use and furthermost
enterprise solutions back certificate-based authentication.
2. It leverages existing admission control policies – This is done to regulate which users
can admit different applications plus networks to ensure only lucky users can access
crucial operations.
3. Ease of placement and ongoing control – Certificate based solutions emanate through
cloud-based management stand to make it tranquil for administrators to subject
certificates to new staffs, reintroduce certificates when a worker leaves an
organization. Certificates being stored locally not only saves on costs but lifts
management pain in revoking or distributing tokens.
4. Mutual authentication – This means both entities involved in messaging are
recognizing themselves from a machine to machine or user to user.
5. Extending to outdoor users – Certificates are relaxed to roll out to operators outside of
the body plus the ease of use, you will not need to offer extra training.
4.2 Disadvantages of certificate based verification.
One of the disadvantages is that certificate based authentication requires public key infrastructure
which can increase the cost of initial deployment in some deployment (Hafeez 2018)
Another disadvantage is that the system of certificate based authentication is not an infallible
one. This is because hackers can target authorities issuing the digital certificate in order to
influence certificate data. Consequently, hackers create website or send emails that appear
genuine plus cleared certification tests nevertheless are falsified since the certificate authority is
compromised (Cho & Ip 2018).
4.3 Working Principle.
Certificate based verification can occur on double sides: proof of a host or confirmation of a
client. This means that if you need to validate a consumer, the consumer needs to have a
document dispensed by a certificate consultant which the host confidences or if you need to
authenticate a server the host needs to gain a certificate entitled its hostname and allotted by a
credential authority which the client beliefs (Dashti & Radomirovic 2017).
4.0 Certificate based authentication
Certificate-based endorsement is the practice of a digital credential to identify a user, appliance,
or gadget before allowing access to a resource or a linkage (Kawan et al .2017).In the case of
user verification, it is installed in coordination with old-fashioned method of authentication such
as keyword authentication (Bratthall & Lindstrom 2018).
4.1 Advantages of certificate based authentication.
1. It is user-friendly – Once the certificate is installed it’s easy to use and furthermost
enterprise solutions back certificate-based authentication.
2. It leverages existing admission control policies – This is done to regulate which users
can admit different applications plus networks to ensure only lucky users can access
crucial operations.
3. Ease of placement and ongoing control – Certificate based solutions emanate through
cloud-based management stand to make it tranquil for administrators to subject
certificates to new staffs, reintroduce certificates when a worker leaves an
organization. Certificates being stored locally not only saves on costs but lifts
management pain in revoking or distributing tokens.
4. Mutual authentication – This means both entities involved in messaging are
recognizing themselves from a machine to machine or user to user.
5. Extending to outdoor users – Certificates are relaxed to roll out to operators outside of
the body plus the ease of use, you will not need to offer extra training.
4.2 Disadvantages of certificate based verification.
One of the disadvantages is that certificate based authentication requires public key infrastructure
which can increase the cost of initial deployment in some deployment (Hafeez 2018)
Another disadvantage is that the system of certificate based authentication is not an infallible
one. This is because hackers can target authorities issuing the digital certificate in order to
influence certificate data. Consequently, hackers create website or send emails that appear
genuine plus cleared certification tests nevertheless are falsified since the certificate authority is
compromised (Cho & Ip 2018).
4.3 Working Principle.
Certificate based verification can occur on double sides: proof of a host or confirmation of a
client. This means that if you need to validate a consumer, the consumer needs to have a
document dispensed by a certificate consultant which the host confidences or if you need to
authenticate a server the host needs to gain a certificate entitled its hostname and allotted by a
credential authority which the client beliefs (Dashti & Radomirovic 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
4.4 Differences between certificate based authentication and password based
authentication.
Users are prone to forget their passwords since passwords depend on on a part of the
operator which tends to forget when handling security that is the human brain. Password strength
might be improved by mandatory rules but those instructions are seen as a drain by the users who
tend to forget the correct format of the password that is at least eight characters, at least one
uppercase and lowercase letter. Besides, user certificates suggest a storage system which is
secure plus is handled well compared with choosing a password (Hammad & Faith 2017)
Certificates use asymmetric cryptography which means that the certificate is supplied by
a certification authority who assures the link between a physical distinctiveness and a
cryptographic public key. The verifier might be a different object that can authenticate a link
then use it to confirm the user without receiving the ability to mimic the user in contrast to a
password in which whoever authenticates the password recognizes at some point the password.
In addition passwords are prone to phishing assaults whereas certificates are not for the reason
that of unevenness (Herrera, Ron & Rabadao 2017)
Certificates are complex hence they are expensive in that issuing and managing
certificates is full of problems and is evidenced by any PKI vendor. PKI is about 5%
cryptography and 95% procedures which shows it can be done but not cheaply. Also for user
certificates, average users can learn to use client certificates for a HTTPS connection to a
website, but at the cost of finding a way to ignore occasional warning popup, which makes them
more vulnerable to some attacks. On the other hand, password based authentication is easy to
integrate everywhere and does not involve some incompressible extra costs (Kalisiki, Sheth &
Shyamsunder 2018).
4.5 Useful features of certificate-based authentication for BYOD policy.
1. Certificate based authentication policy via an administrator generates and assigns
certificate to devices in the organization via a certificate management portal to an
accomplished provision.
2. The bureaucrat aligns his user handbook and network safety systems to trust precise users
and devices for validation via bringing in digital credentials of the devices in query
3. By cataloging in, an access application is directed from the gadget to the link. This
warrants determined fulfillment that the memorandums sent have been correctly decrypted
and the authorizations sound.
4. There is mutual verification to enhance the gadget is attached to the server it anticipates
and the server can also confirm the exact gadget is connecting upon checking, it allows
the device access improving security of the data and the network.
4.4 Differences between certificate based authentication and password based
authentication.
Users are prone to forget their passwords since passwords depend on on a part of the
operator which tends to forget when handling security that is the human brain. Password strength
might be improved by mandatory rules but those instructions are seen as a drain by the users who
tend to forget the correct format of the password that is at least eight characters, at least one
uppercase and lowercase letter. Besides, user certificates suggest a storage system which is
secure plus is handled well compared with choosing a password (Hammad & Faith 2017)
Certificates use asymmetric cryptography which means that the certificate is supplied by
a certification authority who assures the link between a physical distinctiveness and a
cryptographic public key. The verifier might be a different object that can authenticate a link
then use it to confirm the user without receiving the ability to mimic the user in contrast to a
password in which whoever authenticates the password recognizes at some point the password.
In addition passwords are prone to phishing assaults whereas certificates are not for the reason
that of unevenness (Herrera, Ron & Rabadao 2017)
Certificates are complex hence they are expensive in that issuing and managing
certificates is full of problems and is evidenced by any PKI vendor. PKI is about 5%
cryptography and 95% procedures which shows it can be done but not cheaply. Also for user
certificates, average users can learn to use client certificates for a HTTPS connection to a
website, but at the cost of finding a way to ignore occasional warning popup, which makes them
more vulnerable to some attacks. On the other hand, password based authentication is easy to
integrate everywhere and does not involve some incompressible extra costs (Kalisiki, Sheth &
Shyamsunder 2018).
4.5 Useful features of certificate-based authentication for BYOD policy.
1. Certificate based authentication policy via an administrator generates and assigns
certificate to devices in the organization via a certificate management portal to an
accomplished provision.
2. The bureaucrat aligns his user handbook and network safety systems to trust precise users
and devices for validation via bringing in digital credentials of the devices in query
3. By cataloging in, an access application is directed from the gadget to the link. This
warrants determined fulfillment that the memorandums sent have been correctly decrypted
and the authorizations sound.
4. There is mutual verification to enhance the gadget is attached to the server it anticipates
and the server can also confirm the exact gadget is connecting upon checking, it allows
the device access improving security of the data and the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
5.0 Spam.
Spam is known as the sending of unsolicited commercial electronic messages by SMS, email,
MMS or instant messaging (Spam Act 2003).
Characteristics of spam.
1. Sender anonymity – The sender of the spam messages is always unknown and many
senders use IP addresses to further protect their identity.
2. Unsolicited – The recipients never request for spam messages and there is no way to
avoid future spam messages and most spam messages are sent with the intention of
asking sensitive information.
3. Mass mailing – Spam emails are sent to many at once.
5.1 Types of electronic messages to be treated as spam:
1. A message that offer, advertise or promote goods or services, land or industry or an
investment prospect.
2. Market a supplier of merchandises or services or land or a worker of a business or
investment prospect.
3. Help or enable a person to falsely obtain property belonging to an additional person.
4. Help or enable a person to falsely obtain a financial benefit or other gain from an extra
person.
5. If the information is retrieved via hyperlinks, cell phone numbers or contact data if the
communication has a commercial drive (Butcher 2018).
5.2 Examples of spam messages.
1. SMS or electronic message promotion of courting websites and services. This is spam
since you never solicited for it.
2. Advance fee, get-rich-fast schemes and betting services. Advance pay is whereby a
person asserts to have access to moneys currently held in a bank account besides offering
a large amount for assistance comprising providing bank account information or
disbursing for administration fee.
3. Offer of stock market alternatives, loan and mortgage arrangements. This is spam since
you never requested for it but showed up in your device.
4. Offer of computer goods including software and hardware. This is spam since you did not
solicit for it.
5.0 Spam.
Spam is known as the sending of unsolicited commercial electronic messages by SMS, email,
MMS or instant messaging (Spam Act 2003).
Characteristics of spam.
1. Sender anonymity – The sender of the spam messages is always unknown and many
senders use IP addresses to further protect their identity.
2. Unsolicited – The recipients never request for spam messages and there is no way to
avoid future spam messages and most spam messages are sent with the intention of
asking sensitive information.
3. Mass mailing – Spam emails are sent to many at once.
5.1 Types of electronic messages to be treated as spam:
1. A message that offer, advertise or promote goods or services, land or industry or an
investment prospect.
2. Market a supplier of merchandises or services or land or a worker of a business or
investment prospect.
3. Help or enable a person to falsely obtain property belonging to an additional person.
4. Help or enable a person to falsely obtain a financial benefit or other gain from an extra
person.
5. If the information is retrieved via hyperlinks, cell phone numbers or contact data if the
communication has a commercial drive (Butcher 2018).
5.2 Examples of spam messages.
1. SMS or electronic message promotion of courting websites and services. This is spam
since you never solicited for it.
2. Advance fee, get-rich-fast schemes and betting services. Advance pay is whereby a
person asserts to have access to moneys currently held in a bank account besides offering
a large amount for assistance comprising providing bank account information or
disbursing for administration fee.
3. Offer of stock market alternatives, loan and mortgage arrangements. This is spam since
you never requested for it but showed up in your device.
4. Offer of computer goods including software and hardware. This is spam since you did not
solicit for it.

12
Instruction to users on how to handle spam.
1. Do not reply to the spam message. This will cause all original addressees to receive the
reply causing another flood.
2. Do not respond to instructions to remove me from the mailing list. This will result in a
bounced mail message to you.
3. Report the spam.
4. Ensure the junk email filtering is turned on especially if you’re unlucky to receive
offensive spam.
Instruction to the IT administrator of how to minimize spam threat.
1. Keep the software up to date to make sure you are up to date with the latest antispam
software.
2. Enable sender authentication.
3. Implement recipient validation for all domains possible.
4. Learn about email and spam so as to learn the protocols, technology and techniques
involved.
5. Enable connection classification (Bacalao et al. 2017).
Instruction to users on how to handle spam.
1. Do not reply to the spam message. This will cause all original addressees to receive the
reply causing another flood.
2. Do not respond to instructions to remove me from the mailing list. This will result in a
bounced mail message to you.
3. Report the spam.
4. Ensure the junk email filtering is turned on especially if you’re unlucky to receive
offensive spam.
Instruction to the IT administrator of how to minimize spam threat.
1. Keep the software up to date to make sure you are up to date with the latest antispam
software.
2. Enable sender authentication.
3. Implement recipient validation for all domains possible.
4. Learn about email and spam so as to learn the protocols, technology and techniques
involved.
5. Enable connection classification (Bacalao et al. 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


