Security Risk Analysis of BYOD for Performance Education
VerifiedAdded on 2022/11/28
|20
|4618
|386
Report
AI Summary
This report conducts a comprehensive security risk analysis of a BYOD (Bring Your Own Device) policy implemented by Performance Education. The report begins by outlining the necessary network infrastructure, including routers, switches, and wireless access points, to support BYOD services. It then identifies and categorizes potential threats and vulnerabilities associated with these network assets, summarizing them in tables. The analysis further discusses the devices allowed on the network and explores the authentication mechanisms, particularly certificate-based authentication using digital signatures, detailing its working principles, advantages, and disadvantages compared to traditional methods. Finally, the report addresses cybersecurity awareness, emphasizes effective internet usage policies to prevent phishing attacks, provides an example of a recent phishing attack, and concludes with recommendations for enhancing overall network security. The report is designed to address the security concerns raised by the BYOD policy.

Running head: BYOD SECURITY RISK ANALYSIS
BYOD Security Risk Analysis
Name of the Student
Name of the University
Author Note
BYOD Security Risk Analysis
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
BYOD SECURITY RISK ANALYSIS
Summary
According to several researches that have been conducted in recent years, wireless network
connectivity and functionalities like BYOD (Bring Your Own Device) is playing an
important role in providing more convenient means of imparting education on part of the
universities and that too in a cost efficient and secure manner. First the report is to talk about
the network infrastructure that was required by Performance Education to make the BYOD
services available to the students and teachers. The report is to proceed by identifying and list
the network components necessary to set up the network. Then the report is to discuss the
threats and vulnerabilities associated with these networking assets and is to summarise them
in tabular formats after the discussion for threats and vulnerabilities respectively. Next the
report must briefly mention the devices that the students and teachers are allowed to bring
and how they are to be connected. After that the report should make a detailed discussion of
the authentication mechanisms to be applied along with a working principle explaining the
authentication technique workflow. Following this the advantages and disadvantages of this
authentication compared to traditional authentication techniques should also be given. After
that the report is to talk about the growing importance of cyber security awareness
programmes for organizational members and must lay down effective internet usage policies
to prevent phishing attacks. After providing an example of a recent phishing attack the report
ends with concluding notes.
BYOD SECURITY RISK ANALYSIS
Summary
According to several researches that have been conducted in recent years, wireless network
connectivity and functionalities like BYOD (Bring Your Own Device) is playing an
important role in providing more convenient means of imparting education on part of the
universities and that too in a cost efficient and secure manner. First the report is to talk about
the network infrastructure that was required by Performance Education to make the BYOD
services available to the students and teachers. The report is to proceed by identifying and list
the network components necessary to set up the network. Then the report is to discuss the
threats and vulnerabilities associated with these networking assets and is to summarise them
in tabular formats after the discussion for threats and vulnerabilities respectively. Next the
report must briefly mention the devices that the students and teachers are allowed to bring
and how they are to be connected. After that the report should make a detailed discussion of
the authentication mechanisms to be applied along with a working principle explaining the
authentication technique workflow. Following this the advantages and disadvantages of this
authentication compared to traditional authentication techniques should also be given. After
that the report is to talk about the growing importance of cyber security awareness
programmes for organizational members and must lay down effective internet usage policies
to prevent phishing attacks. After providing an example of a recent phishing attack the report
ends with concluding notes.

2
BYOD SECURITY RISK ANALYSIS
Table of Contents
Introduction................................................................................................................................3
Task 1: BYOD Threats and Vulnerabilities...............................................................................3
Threats....................................................................................................................................4
Vulnerabilities........................................................................................................................5
BYOD Devices Availing the Wireless Network....................................................................7
Task 2: Working principle and mechanism of Certificate-Based Authentication.....................8
Advantages.............................................................................................................................9
Disadvantages........................................................................................................................9
Task 3: Instructions and Guidelines for Anti-phishing............................................................10
Effective Usage Policies......................................................................................................10
Conclusion................................................................................................................................13
References................................................................................................................................14
BYOD SECURITY RISK ANALYSIS
Table of Contents
Introduction................................................................................................................................3
Task 1: BYOD Threats and Vulnerabilities...............................................................................3
Threats....................................................................................................................................4
Vulnerabilities........................................................................................................................5
BYOD Devices Availing the Wireless Network....................................................................7
Task 2: Working principle and mechanism of Certificate-Based Authentication.....................8
Advantages.............................................................................................................................9
Disadvantages........................................................................................................................9
Task 3: Instructions and Guidelines for Anti-phishing............................................................10
Effective Usage Policies......................................................................................................10
Conclusion................................................................................................................................13
References................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
BYOD SECURITY RISK ANALYSIS
Introduction
The report below attempts to highlight the role of wireless network connectivity and
BYOD (Bring Your Own Device) functionalities in providing more convenient means of
imparting education on universities in a secure yet cost effective manner (Song, and Kong
2017). The report begins by talking about the network infrastructure that was required by
Performance Education to make the BYOD services available to the students and teachers
(Hong et al. 2016). The report proceeds to identify and list the network components necessary
to set up the network. Then the report discusses the threats and vulnerabilities associated with
these networking assets and summarises them in tabular formats after the discussion for
threats and vulnerabilities respectively. Next the report briefly mentions the devices that the
students and teachers are allowed to bring and how they are to be connected. After that the
report makes a detailed discussion of the authentication mechanisms in place along with a
working principle explaining the authentication technique workflow. Following this the
advantages and disadvantages of this authentication compared to traditional authentication
techniques are given. After that the report talks about the growing importance of cyber
security awareness programmes for organizational members and lays out effective internet
usage policies to prevent phishing attacks. After providing an example of a recent phishing
attack the report ends with concluding notes.
Task 1: BYOD Threats and Vulnerabilities
The institute Performance Education (PE) is making available BYOD or Bring Your
Own Device functionality in the campus premises (Keyes 2016). As a result, members of PE
will be able to bring with them their personal laptops, smartphones, tablets and other devices
and operate them for official purposes. For this PE requires to set up specialized network
infrastructure that is suitable to serve these devices (Newton et al. 2018). This can be setting
BYOD SECURITY RISK ANALYSIS
Introduction
The report below attempts to highlight the role of wireless network connectivity and
BYOD (Bring Your Own Device) functionalities in providing more convenient means of
imparting education on universities in a secure yet cost effective manner (Song, and Kong
2017). The report begins by talking about the network infrastructure that was required by
Performance Education to make the BYOD services available to the students and teachers
(Hong et al. 2016). The report proceeds to identify and list the network components necessary
to set up the network. Then the report discusses the threats and vulnerabilities associated with
these networking assets and summarises them in tabular formats after the discussion for
threats and vulnerabilities respectively. Next the report briefly mentions the devices that the
students and teachers are allowed to bring and how they are to be connected. After that the
report makes a detailed discussion of the authentication mechanisms in place along with a
working principle explaining the authentication technique workflow. Following this the
advantages and disadvantages of this authentication compared to traditional authentication
techniques are given. After that the report talks about the growing importance of cyber
security awareness programmes for organizational members and lays out effective internet
usage policies to prevent phishing attacks. After providing an example of a recent phishing
attack the report ends with concluding notes.
Task 1: BYOD Threats and Vulnerabilities
The institute Performance Education (PE) is making available BYOD or Bring Your
Own Device functionality in the campus premises (Keyes 2016). As a result, members of PE
will be able to bring with them their personal laptops, smartphones, tablets and other devices
and operate them for official purposes. For this PE requires to set up specialized network
infrastructure that is suitable to serve these devices (Newton et al. 2018). This can be setting
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
BYOD SECURITY RISK ANALYSIS
up a WLAN network for providing wireless network connectivity to the supported devices.
Therefore the required assets for BYOD services are the following:
1) Router
2) Multilayer Switch (Layer 3)
3) Access Layer Switch (Layer 2)
4) Wireless Routers
5) Wireless Access Points
For securing the operations of the network, password based authentication has been
used. This can be the WPA2 or Wi-Fi Protected Access authentication technique on the
hardware side by means of which the members are provided with pass keys that they need to
enter from their devices to connect to the network (Lorente, Meijer and Verdult, 2015). On
the software side the network is using digital signatures in SSL connections as digital
certificates in order to authenticate the clients through the server.
Threats
Router: Among the common threats to routers of a network are Denial of Service attacks or
Syn Flood attacks which end up suspending the operations of the router. Another threat to the
routers is brute force attack in which the hacker tries to crack the password based on
guesswork with the help of automated tools and various dictionary methods.
Multilayer Switch: Among the threats to layer 3 switches, major attacks are IP spoofing for
using forged IP addresses, Routing Information Protocol or RIP attacks for impersonating
hosts, ICMP attacks and ICMP flood or ping flood that ultimately leads to DoS attacks.
BYOD SECURITY RISK ANALYSIS
up a WLAN network for providing wireless network connectivity to the supported devices.
Therefore the required assets for BYOD services are the following:
1) Router
2) Multilayer Switch (Layer 3)
3) Access Layer Switch (Layer 2)
4) Wireless Routers
5) Wireless Access Points
For securing the operations of the network, password based authentication has been
used. This can be the WPA2 or Wi-Fi Protected Access authentication technique on the
hardware side by means of which the members are provided with pass keys that they need to
enter from their devices to connect to the network (Lorente, Meijer and Verdult, 2015). On
the software side the network is using digital signatures in SSL connections as digital
certificates in order to authenticate the clients through the server.
Threats
Router: Among the common threats to routers of a network are Denial of Service attacks or
Syn Flood attacks which end up suspending the operations of the router. Another threat to the
routers is brute force attack in which the hacker tries to crack the password based on
guesswork with the help of automated tools and various dictionary methods.
Multilayer Switch: Among the threats to layer 3 switches, major attacks are IP spoofing for
using forged IP addresses, Routing Information Protocol or RIP attacks for impersonating
hosts, ICMP attacks and ICMP flood or ping flood that ultimately leads to DoS attacks.
5
BYOD SECURITY RISK ANALYSIS
Access Layer Switch: The common attacks relating to the layer 2 switch are Spanning Tree
Protocol or STP attacks by attempting to alter STP, Address Resolution Protocol or ARP
attacks like MITM attacks and VLAN hopping like switch spoofing and double tagging.
Wireless Router: The threats revolving around wireless routers are rogue access points that
is improperly configured wireless routers added to the network as well as soft access points
which involve wireless hotspots which the users often forget to switch off after use.
Wireless Access Points: Among the possible threats to wireless access points are Evil Twins
which are made to act as legitimate access points but essentially serves hackers by creating
clones.
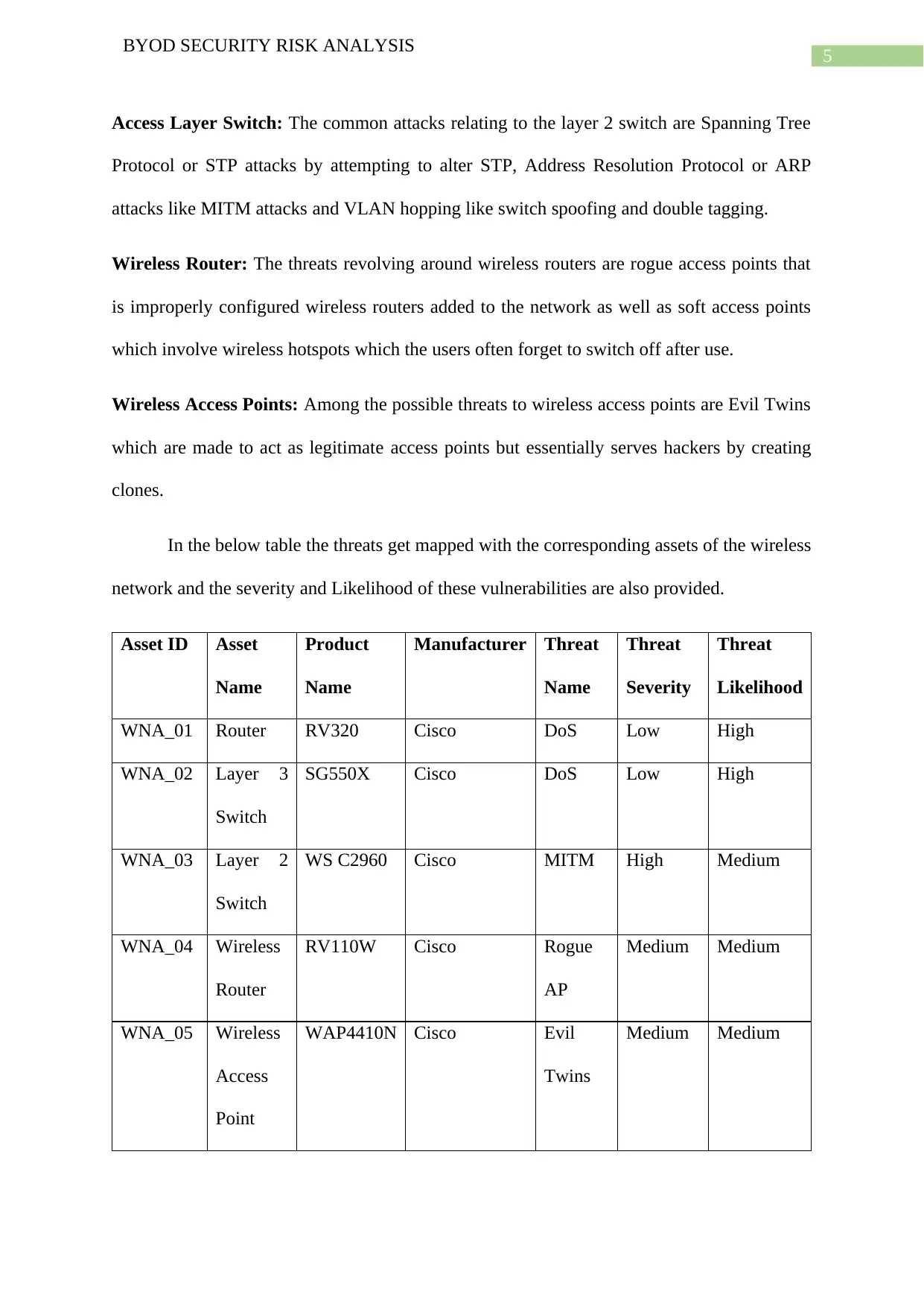
In the below table the threats get mapped with the corresponding assets of the wireless
network and the severity and Likelihood of these vulnerabilities are also provided.
Asset ID Asset
Name
Product
Name
Manufacturer Threat
Name
Threat
Severity
Threat
Likelihood
WNA_01 Router RV320 Cisco DoS Low High
WNA_02 Layer 3
Switch
SG550X Cisco DoS Low High
WNA_03 Layer 2
Switch
WS C2960 Cisco MITM High Medium
WNA_04 Wireless
Router
RV110W Cisco Rogue
AP
Medium Medium
WNA_05 Wireless
Access
Point
WAP4410N Cisco Evil
Twins
Medium Medium
BYOD SECURITY RISK ANALYSIS
Access Layer Switch: The common attacks relating to the layer 2 switch are Spanning Tree
Protocol or STP attacks by attempting to alter STP, Address Resolution Protocol or ARP
attacks like MITM attacks and VLAN hopping like switch spoofing and double tagging.
Wireless Router: The threats revolving around wireless routers are rogue access points that
is improperly configured wireless routers added to the network as well as soft access points
which involve wireless hotspots which the users often forget to switch off after use.
Wireless Access Points: Among the possible threats to wireless access points are Evil Twins
which are made to act as legitimate access points but essentially serves hackers by creating
clones.
In the below table the threats get mapped with the corresponding assets of the wireless
network and the severity and Likelihood of these vulnerabilities are also provided.
Asset ID Asset
Name
Product
Name
Manufacturer Threat
Name
Threat
Severity
Threat
Likelihood
WNA_01 Router RV320 Cisco DoS Low High
WNA_02 Layer 3
Switch
SG550X Cisco DoS Low High
WNA_03 Layer 2
Switch
WS C2960 Cisco MITM High Medium
WNA_04 Wireless
Router
RV110W Cisco Rogue
AP
Medium Medium
WNA_05 Wireless
Access
Point
WAP4410N Cisco Evil
Twins
Medium Medium
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
BYOD SECURITY RISK ANALYSIS
Vulnerabilities
Router: The vulnerability CVE-2019-1653 for cisco small business routers RV320 and
RV325 WAN routers allow remote attackers in retrieving sensitive information. This results
from improper access controls for the respective URLs.
Multilayer Switch: The vulnerability CVE-2018-15372 in MACsec Key Agreement or
MKA through EAP-TLS (Extensible Authentication Protocol-Transport Layer Security)
functionality of the software Cisco IOS XE can allow unauthenticated and adjacent attackers
in bypassing authentication as well as pass traffic via Layer 3 interfaces of affected devices.
This vulnerability results from logic errors in affected software applications. Attackers can
exploit the vulnerability by connecting and passing traffic with Layer 3 interfaces of affected
devices.
Access Layer Switch: The vulnerability CVE-2019-1687 in TCP proxy functionalities for
Cisco ASA (Adaptive Security Appliance) and Cisco FTD (Firepower Threat Defense)
software applications allowed unauthenticated remote attackers in causing devices to undergo
unexpected restarts which lead to denial of service or DoS attacks (Asri and Pranggono
2015). This vulnerability is caused by errors in TCP based inspection of packets that causes
TCP packets in having invalid Layer 2 header information.
Wireless Router: The vulnerability CVE-2019-1663 in web based management interfaces of
the routers RV-110W Wireless-N VPN, RV130W Wireless-N Multifunction VPN Router and
RV215W Wireless-N VPN from Cisco have been allowing unauthenticated remote attackers
in arbitrary execution of codes on affected devices. The vulnerability results from incorrect
validation of data supplied by users in web based interfaces enabling attackers in sending
harmful HTTPS request messages to the intended targets.
BYOD SECURITY RISK ANALYSIS
Vulnerabilities
Router: The vulnerability CVE-2019-1653 for cisco small business routers RV320 and
RV325 WAN routers allow remote attackers in retrieving sensitive information. This results
from improper access controls for the respective URLs.
Multilayer Switch: The vulnerability CVE-2018-15372 in MACsec Key Agreement or
MKA through EAP-TLS (Extensible Authentication Protocol-Transport Layer Security)
functionality of the software Cisco IOS XE can allow unauthenticated and adjacent attackers
in bypassing authentication as well as pass traffic via Layer 3 interfaces of affected devices.
This vulnerability results from logic errors in affected software applications. Attackers can
exploit the vulnerability by connecting and passing traffic with Layer 3 interfaces of affected
devices.
Access Layer Switch: The vulnerability CVE-2019-1687 in TCP proxy functionalities for
Cisco ASA (Adaptive Security Appliance) and Cisco FTD (Firepower Threat Defense)
software applications allowed unauthenticated remote attackers in causing devices to undergo
unexpected restarts which lead to denial of service or DoS attacks (Asri and Pranggono
2015). This vulnerability is caused by errors in TCP based inspection of packets that causes
TCP packets in having invalid Layer 2 header information.
Wireless Router: The vulnerability CVE-2019-1663 in web based management interfaces of
the routers RV-110W Wireless-N VPN, RV130W Wireless-N Multifunction VPN Router and
RV215W Wireless-N VPN from Cisco have been allowing unauthenticated remote attackers
in arbitrary execution of codes on affected devices. The vulnerability results from incorrect
validation of data supplied by users in web based interfaces enabling attackers in sending
harmful HTTPS request messages to the intended targets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
BYOD SECURITY RISK ANALYSIS
Wireless Access Points: The vulnerability CVE-2018-0443 in control and provisioning of
wireless access points or the CAPWAP protocol components of Cisco WLC (Wireless LAN
Controller) software application allowed unauthenticated attackers to operate remotely and
cause DoS or denial of service attacks (Fung and McCormick 2015). This vulnerability arises
from incorrect validation of inputs on fields of the packets of CAPWAP Discovery Request
by affected devices. Attackers exploited this vulnerability through transfer of malicious
CAPWAP Discovery Request packets to the Cisco WLC Software thereby disconnecting the
access points leading to DoS attacks.
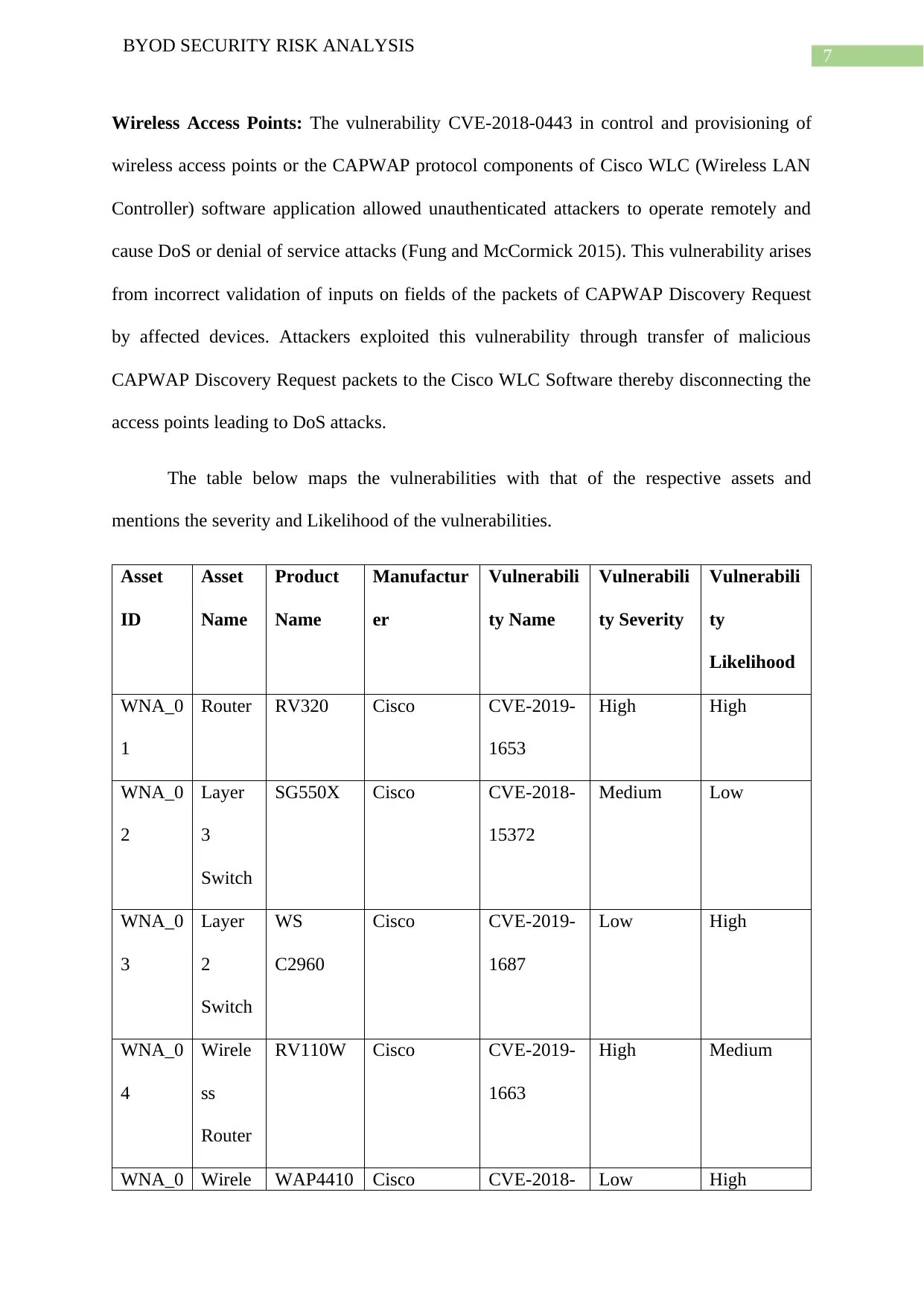
The table below maps the vulnerabilities with that of the respective assets and
mentions the severity and Likelihood of the vulnerabilities.
Asset
ID
Asset
Name
Product
Name
Manufactur
er
Vulnerabili
ty Name
Vulnerabili
ty Severity
Vulnerabili
ty
Likelihood
WNA_0
1
Router RV320 Cisco CVE-2019-
1653
High High
WNA_0
2
Layer
3
Switch
SG550X Cisco CVE-2018-
15372
Medium Low
WNA_0
3
Layer
2
Switch
WS
C2960
Cisco CVE-2019-
1687
Low High
WNA_0
4
Wirele
ss
Router
RV110W Cisco CVE-2019-
1663
High Medium
WNA_0 Wirele WAP4410 Cisco CVE-2018- Low High
BYOD SECURITY RISK ANALYSIS
Wireless Access Points: The vulnerability CVE-2018-0443 in control and provisioning of
wireless access points or the CAPWAP protocol components of Cisco WLC (Wireless LAN
Controller) software application allowed unauthenticated attackers to operate remotely and
cause DoS or denial of service attacks (Fung and McCormick 2015). This vulnerability arises
from incorrect validation of inputs on fields of the packets of CAPWAP Discovery Request
by affected devices. Attackers exploited this vulnerability through transfer of malicious
CAPWAP Discovery Request packets to the Cisco WLC Software thereby disconnecting the
access points leading to DoS attacks.
The table below maps the vulnerabilities with that of the respective assets and
mentions the severity and Likelihood of the vulnerabilities.
Asset
ID
Asset
Name
Product
Name
Manufactur
er
Vulnerabili
ty Name
Vulnerabili
ty Severity
Vulnerabili
ty
Likelihood
WNA_0
1
Router RV320 Cisco CVE-2019-
1653
High High
WNA_0
2
Layer
3
Switch
SG550X Cisco CVE-2018-
15372
Medium Low
WNA_0
3
Layer
2
Switch
WS
C2960
Cisco CVE-2019-
1687
Low High
WNA_0
4
Wirele
ss
Router
RV110W Cisco CVE-2019-
1663
High Medium
WNA_0 Wirele WAP4410 Cisco CVE-2018- Low High

8
BYOD SECURITY RISK ANALYSIS
5 ss
Access
Point
N 0443
BYOD Devices Availing the Wireless Network
The BYOD or bring your own devices that are being used by the teachers and
students that access the wireless network connectivity WLAN made available by the wireless
routers and access points are laptops, notebooks, mac book pro and similar devices (Byrom et
al. 2019). Students are not encouraged to bring any peripheral equipment associated with
these devices and will themselves be responsible for any loss of these components (Cheng,
Guan and Chau 2016). Peripheral equipment like these can include chargers, charging cables,
docking cradles, external devices for pointing such as mouse, adapters for video output/data
transfer. The devices are only to connect to the wireless network.
Task 2: Working principle and mechanism of Certificate-Based
Authentication
Figure 1: Working principle of Digital Signature
BYOD SECURITY RISK ANALYSIS
5 ss
Access
Point
N 0443
BYOD Devices Availing the Wireless Network
The BYOD or bring your own devices that are being used by the teachers and
students that access the wireless network connectivity WLAN made available by the wireless
routers and access points are laptops, notebooks, mac book pro and similar devices (Byrom et
al. 2019). Students are not encouraged to bring any peripheral equipment associated with
these devices and will themselves be responsible for any loss of these components (Cheng,
Guan and Chau 2016). Peripheral equipment like these can include chargers, charging cables,
docking cradles, external devices for pointing such as mouse, adapters for video output/data
transfer. The devices are only to connect to the wireless network.
Task 2: Working principle and mechanism of Certificate-Based
Authentication
Figure 1: Working principle of Digital Signature
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
BYOD SECURITY RISK ANALYSIS
The certificate-based authentication that is being used by the network infrastructure
configured and setup for providing services like BYOD functionality is Digital Signature
(Handley 2018). These serve as evidence of inputs or signed data acquired from the specific
user which includes the original data as well as the digital signature (the one way hash of the
original data that has been encrypted with the private key of the user). This signed data then
gets shared over the network to the intended recipient who decrypts the hash by using the
public key (Beullens and Blackburn 2018). This recipient then uses the same hashing
algorithm that has been used for generating the original hash file so a new hash of the same
file can be created. The recipient then compares this new hash with the original hash and
checks whether any changes have been made since the data was signed (Ardy et al. 2017). If
no changes are found, no data tampering is present, if hashes do not match, tampering is
involved. In the network of the institute the users send their messages with digital signatures
applied (Howe et al. 2015). The authentication server obtains the digital certificate, extracts
the digital signature and thereby identifying the user trying to communicate within the
network (Yoo et al. 2017). In this way, the network of PE ensures that communications over
the network is only granted to the intended recipients. To implement use of digital certificates
in network communications, the institute is required to acquire the service from a certificate
authority on a subscription basis.
Advantages
1. Compared to traditional authentication methods, certificate-based authentication helps
secure sensitive information like transactional data in online banking services.
2. The use of digital certificate helps banks know the correct amount in checks and the
digital signature helps identify the individual thus preventing fraudulent transactions
compared to physical signatures which can be forged.
BYOD SECURITY RISK ANALYSIS
The certificate-based authentication that is being used by the network infrastructure
configured and setup for providing services like BYOD functionality is Digital Signature
(Handley 2018). These serve as evidence of inputs or signed data acquired from the specific
user which includes the original data as well as the digital signature (the one way hash of the
original data that has been encrypted with the private key of the user). This signed data then
gets shared over the network to the intended recipient who decrypts the hash by using the
public key (Beullens and Blackburn 2018). This recipient then uses the same hashing
algorithm that has been used for generating the original hash file so a new hash of the same
file can be created. The recipient then compares this new hash with the original hash and
checks whether any changes have been made since the data was signed (Ardy et al. 2017). If
no changes are found, no data tampering is present, if hashes do not match, tampering is
involved. In the network of the institute the users send their messages with digital signatures
applied (Howe et al. 2015). The authentication server obtains the digital certificate, extracts
the digital signature and thereby identifying the user trying to communicate within the
network (Yoo et al. 2017). In this way, the network of PE ensures that communications over
the network is only granted to the intended recipients. To implement use of digital certificates
in network communications, the institute is required to acquire the service from a certificate
authority on a subscription basis.
Advantages
1. Compared to traditional authentication methods, certificate-based authentication helps
secure sensitive information like transactional data in online banking services.
2. The use of digital certificate helps banks know the correct amount in checks and the
digital signature helps identify the individual thus preventing fraudulent transactions
compared to physical signatures which can be forged.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
BYOD SECURITY RISK ANALYSIS
3. Contrary to traditional authentication, certificate-based authentication protects clients
in legally binding situations encountered online with the help of digital signatures
verifying the identities of the parties involved.
4. Digital signatures help businesses in finding cost effective solutions in securing
network communications.
5. Improves upon the existing digital operations of businesses thereby saving time.
Disadvantages
1. The digital certificates have to be purchased by businesses from a certificate
authority.
2. These certificate authorities serve as third party issuers who ensure acceptance of the
certificate.
3. In general, the certificate authorities provide subscription-based services forcing
businesses to renew their certificates periodically.
4. Digital certificates bring with them compatibility issues with software applications
being used and their versions.
5. This requires businesses to spend resources like internal auditors and senior IT
engineers in selection of the certificates and network environment.
Task 3: Instructions and Guidelines for Anti-phishing
In this digital age, cyber security risks are becoming immune to software security
solutions like antivirus and antimalware programs as they attempt lure the user of the
computer in opening the malicious files in order to infect the systems (Jalali et al. 2019). As
the result, more than installing and operating costly security solutions, it becomes more
important to spread awareness on security threats to the members of PE who are accessing
the workstations, PCs and other information technology assets involved. Thus, it is pivotal
BYOD SECURITY RISK ANALYSIS
3. Contrary to traditional authentication, certificate-based authentication protects clients
in legally binding situations encountered online with the help of digital signatures
verifying the identities of the parties involved.
4. Digital signatures help businesses in finding cost effective solutions in securing
network communications.
5. Improves upon the existing digital operations of businesses thereby saving time.
Disadvantages
1. The digital certificates have to be purchased by businesses from a certificate
authority.
2. These certificate authorities serve as third party issuers who ensure acceptance of the
certificate.
3. In general, the certificate authorities provide subscription-based services forcing
businesses to renew their certificates periodically.
4. Digital certificates bring with them compatibility issues with software applications
being used and their versions.
5. This requires businesses to spend resources like internal auditors and senior IT
engineers in selection of the certificates and network environment.
Task 3: Instructions and Guidelines for Anti-phishing
In this digital age, cyber security risks are becoming immune to software security
solutions like antivirus and antimalware programs as they attempt lure the user of the
computer in opening the malicious files in order to infect the systems (Jalali et al. 2019). As
the result, more than installing and operating costly security solutions, it becomes more
important to spread awareness on security threats to the members of PE who are accessing
the workstations, PCs and other information technology assets involved. Thus, it is pivotal

11
BYOD SECURITY RISK ANALYSIS
that an internet usage policy is drafted and put to use by every organization (Safa, Von Solms
and Furnell 2016). These policies tend to vary from one organization to another in that some
organizations may impose very strict policies while other organizations might provide more
liberty to their members. Effective usage policies ensure that valuable resources and
confidential data of the organization do not get exposed to external threats as well as placing
some restrictions on accessing select group of websites. Thus, best practises for secure
Internet access and safe mailing should be carefully operationalized while also keeping in
mind the considerations that need to be made.
The issues pertaining to one-off training classes for security awareness is that the
lessons taught can easily be forgot (Choi et al. 2018). To help retain this awareness of
potential threats and suspicious network activity, organizational members need to be
reminded periodically of the secure usage policies as part of the awareness sessions.
Effective Usage Policies
The instructions and guidelines to prevent employees from falling victim to phishing attacks
can be:
1. To allow some level of recreation and personal use
Businesses should take note that even the most workaholic employees and staff
should be allowed to take breaks from their stressful routines and be able to scroll through
the news feeds of their social media accounts. Therefore personal usage should be limited
but not totally eliminated.
2. Keeping Staff Updated on Phishing Techniques
Every day newer and newer phishing scams get developed. If the organizational
members do not stay on top of these phishing techniques, one of them can end up being
BYOD SECURITY RISK ANALYSIS
that an internet usage policy is drafted and put to use by every organization (Safa, Von Solms
and Furnell 2016). These policies tend to vary from one organization to another in that some
organizations may impose very strict policies while other organizations might provide more
liberty to their members. Effective usage policies ensure that valuable resources and
confidential data of the organization do not get exposed to external threats as well as placing
some restrictions on accessing select group of websites. Thus, best practises for secure
Internet access and safe mailing should be carefully operationalized while also keeping in
mind the considerations that need to be made.
The issues pertaining to one-off training classes for security awareness is that the
lessons taught can easily be forgot (Choi et al. 2018). To help retain this awareness of
potential threats and suspicious network activity, organizational members need to be
reminded periodically of the secure usage policies as part of the awareness sessions.
Effective Usage Policies
The instructions and guidelines to prevent employees from falling victim to phishing attacks
can be:
1. To allow some level of recreation and personal use
Businesses should take note that even the most workaholic employees and staff
should be allowed to take breaks from their stressful routines and be able to scroll through
the news feeds of their social media accounts. Therefore personal usage should be limited
but not totally eliminated.
2. Keeping Staff Updated on Phishing Techniques
Every day newer and newer phishing scams get developed. If the organizational
members do not stay on top of these phishing techniques, one of them can end up being
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





