Case Investigation Report for Advanced Digital Forensics - Desklib
VerifiedAdded on 2023/06/07
|20
|2784
|380
AI Summary
Read this Case Investigation Report for Advanced Digital Forensics on Desklib. Get insights on necessary resources for forensic investigation, analysis of detailed findings, and review and reflection on the findings.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CASE INVESTIGATION REPORT
Case Investigation Report
SIT703: Advanced Digital Forensics
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Case Investigation Report
SIT703: Advanced Digital Forensics
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1CASE INVESTIGATION REPORT
Table of Contents
Introduction......................................................................................................................................2
1. Overview of the computer crime case.........................................................................................2
2. List of necessary resources for forensic investigation.................................................................4
3. Analysis of detailed findings.......................................................................................................5
4. Review and reflection on the findings.........................................................................................6
4.1 Review of findings.................................................................................................................6
4.2 Reflection on findings............................................................................................................7
Conclusion.......................................................................................................................................7
References........................................................................................................................................9
Appendix-Screenshots...................................................................................................................11
Table of Contents
Introduction......................................................................................................................................2
1. Overview of the computer crime case.........................................................................................2
2. List of necessary resources for forensic investigation.................................................................4
3. Analysis of detailed findings.......................................................................................................5
4. Review and reflection on the findings.........................................................................................6
4.1 Review of findings.................................................................................................................6
4.2 Reflection on findings............................................................................................................7
Conclusion.......................................................................................................................................7
References........................................................................................................................................9
Appendix-Screenshots...................................................................................................................11

2CASE INVESTIGATION REPORT
Introduction
According to Karie and Venter (2015), computer security functions have been largely
challenged with the innovation in the criminal activities and operations. The development of
successful security functions would be helpful for easing the implication of the operations for
organizations and individuals. The possible security flaws in the computer system would result in
forming major setback for execution of the operations without any fear of cyber crimes. The
attacks of cyber theft, misuses of information, manipulation of the data, and unauthorized access
in the computer system had resulted in forming the impact on economy, social, and operational.
The integrity of the data and information is largely compromised due to the lax of security
(Shalaginov and Franke 2015). The following report would be developed considering the
computer cyber criminal activities and the alignment of the successful and integrated
modification of the cyber criminal activities. The alignment would also be responsible for the
formation of the successful alignment model.
1. Overview of the computer crime case
The possible attacks on the computer devices like cyber theft, misuses of information,
manipulation of the data, and unauthorized access have been growing and the number of attacks
have rosed considerably in the last 5 years (Shalaginov and Franke 2015). The inclusion of the
successful alignment would be deployed for dealing with the possible attacks of the computer
devices. The intrusion of the successful functional development would be aligned for easing the
formation of the successful formation of the activities. The possible security flaws in the
computer system would result in forming major setback for execution of the operations without
Introduction
According to Karie and Venter (2015), computer security functions have been largely
challenged with the innovation in the criminal activities and operations. The development of
successful security functions would be helpful for easing the implication of the operations for
organizations and individuals. The possible security flaws in the computer system would result in
forming major setback for execution of the operations without any fear of cyber crimes. The
attacks of cyber theft, misuses of information, manipulation of the data, and unauthorized access
in the computer system had resulted in forming the impact on economy, social, and operational.
The integrity of the data and information is largely compromised due to the lax of security
(Shalaginov and Franke 2015). The following report would be developed considering the
computer cyber criminal activities and the alignment of the successful and integrated
modification of the cyber criminal activities. The alignment would also be responsible for the
formation of the successful alignment model.
1. Overview of the computer crime case
The possible attacks on the computer devices like cyber theft, misuses of information,
manipulation of the data, and unauthorized access have been growing and the number of attacks
have rosed considerably in the last 5 years (Shalaginov and Franke 2015). The inclusion of the
successful alignment would be deployed for dealing with the possible attacks of the computer
devices. The intrusion of the successful functional development would be aligned for easing the
formation of the successful formation of the activities. The possible security flaws in the
computer system would result in forming major setback for execution of the operations without

3CASE INVESTIGATION REPORT
any fear of cyber crimes. The integrity of the data and information is largely compromised due to
the lax of security. Some of the biggest computer crime cases are given below,
Notpetya: According to Kharraz et al. (2016), the Notpetya was a pseudo ransomware
that was prone in disrupting the information processing. The Notpetya attacked and disrupted
information from many organizations resulting in loss to a number of companies. However,
Maersk took the biggest toll of loss of $300million due to Notpetya attack. The shipping
company has faced the loss due to the damage to the operations at 76 ports resulting in
congestion and operations. The data access was stopped and hence most of the work was limited
resulting in delayed operations. The Damco freight and APM terminals took heavy toll and it
resulted in forming the major setback for the probable occurrence of information. The
ransomware was able to extract information or limit the transfer rate so that the operations can be
delayed. It resulted in both economic and functional loss to the people and organizations. The
ransomware attack proved fatal and it can be said that the attack showed the weakness in security
and integrity. The security system lacked the possible methods of detecting and preventing the
attacks (Scaife et al. 2016). It is evident that the study had resulted in forming many possible
issues for the development of the effective operations and development.
Locky: Mercaldo et al. (2016), have stated that the Locky was another ransomware that
attacked and took a toll of huge amount of economic loss to global organizations and individuals.
The attack was primitive and targeted for dealing damages with probable issues and integration
of the activities. The Locky attacked and disrupted information from many organizations
resulting in loss to a number of companies. The data access was stopped and hence most of the
work was limited resulting in delayed operations. The ransomware was able to extract
information or limit the transfer rate so that the operations can be delayed. It resulted in both
any fear of cyber crimes. The integrity of the data and information is largely compromised due to
the lax of security. Some of the biggest computer crime cases are given below,
Notpetya: According to Kharraz et al. (2016), the Notpetya was a pseudo ransomware
that was prone in disrupting the information processing. The Notpetya attacked and disrupted
information from many organizations resulting in loss to a number of companies. However,
Maersk took the biggest toll of loss of $300million due to Notpetya attack. The shipping
company has faced the loss due to the damage to the operations at 76 ports resulting in
congestion and operations. The data access was stopped and hence most of the work was limited
resulting in delayed operations. The Damco freight and APM terminals took heavy toll and it
resulted in forming the major setback for the probable occurrence of information. The
ransomware was able to extract information or limit the transfer rate so that the operations can be
delayed. It resulted in both economic and functional loss to the people and organizations. The
ransomware attack proved fatal and it can be said that the attack showed the weakness in security
and integrity. The security system lacked the possible methods of detecting and preventing the
attacks (Scaife et al. 2016). It is evident that the study had resulted in forming many possible
issues for the development of the effective operations and development.
Locky: Mercaldo et al. (2016), have stated that the Locky was another ransomware that
attacked and took a toll of huge amount of economic loss to global organizations and individuals.
The attack was primitive and targeted for dealing damages with probable issues and integration
of the activities. The Locky attacked and disrupted information from many organizations
resulting in loss to a number of companies. The data access was stopped and hence most of the
work was limited resulting in delayed operations. The ransomware was able to extract
information or limit the transfer rate so that the operations can be delayed. It resulted in both
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4CASE INVESTIGATION REPORT
economic and functional loss to the people and organizations. The ransomware attack proved
fatal and it can be said that the attack showed the weakness in security and integrity. The security
system lacked the possible methods of detecting and preventing the attacks (Kharraz et al. 2016).
It is evident that the study had resulted in forming many possible issues for the development of
the effective operations and development.
2. List of necessary resources for forensic investigation
Forensic investigation was done based on the alignment of the successive management of
the operations. The investigation would be successfully executed by the utilization of the
probable functional development. The analysis would be done for easing the functional
alignment of the articles and journals for listing the security of the information processing. The
following is the list of resources required for necessary forensic investigation,
Article/Journal Name of the Authors Published by (Source)
"Feature Based Cryptanalytic
Technique for Digital Forensics
Analysis of Visual Cryptographic
Digital Image Data Based on
Formal Concept Analysis."
Kester, Quist-Aphetsi,
Laurent Nana, Anca
Christine Pascu, Sophie
Gire, Jojo M. Eghan, and
Nii Narku Quaynor..
In Proceedings of the
International Conference on
Foundations of Computer
Science (FCS), p. 40
Cryptolock (and drop it): stopping
ransomware attacks on user data
Scaife, N., Carter, H.,
Traynor, P. and Butler,
K.R., 2016
In Distributed Computing
Systems (ICDCS), 2016
IEEE 36th International
Conference on (pp. 303-
economic and functional loss to the people and organizations. The ransomware attack proved
fatal and it can be said that the attack showed the weakness in security and integrity. The security
system lacked the possible methods of detecting and preventing the attacks (Kharraz et al. 2016).
It is evident that the study had resulted in forming many possible issues for the development of
the effective operations and development.
2. List of necessary resources for forensic investigation
Forensic investigation was done based on the alignment of the successive management of
the operations. The investigation would be successfully executed by the utilization of the
probable functional development. The analysis would be done for easing the functional
alignment of the articles and journals for listing the security of the information processing. The
following is the list of resources required for necessary forensic investigation,
Article/Journal Name of the Authors Published by (Source)
"Feature Based Cryptanalytic
Technique for Digital Forensics
Analysis of Visual Cryptographic
Digital Image Data Based on
Formal Concept Analysis."
Kester, Quist-Aphetsi,
Laurent Nana, Anca
Christine Pascu, Sophie
Gire, Jojo M. Eghan, and
Nii Narku Quaynor..
In Proceedings of the
International Conference on
Foundations of Computer
Science (FCS), p. 40
Cryptolock (and drop it): stopping
ransomware attacks on user data
Scaife, N., Carter, H.,
Traynor, P. and Butler,
K.R., 2016
In Distributed Computing
Systems (ICDCS), 2016
IEEE 36th International
Conference on (pp. 303-
5CASE INVESTIGATION REPORT
312). IEEE
Android forensics analysis: Private
chat on social messenger
Satrya, G.B., Daely, P.T.
and Shin, S.Y., 2016
In IEEE Conference Paper,
Research Gate
Individual information security,
user behaviour and cyber
victimisation: An empirical study of
social networking users
Saridakis, G., Benson, V.,
Ezingeard, J.N. and
Tennakoon, H., 2016
Technological Forecasting
and Social Change, 102,
pp.320-330
3. Analysis of detailed findings
According to Hui, Kim and Wang (2017), the possible attacks on the computer devices
like cyber theft, misuses of information, manipulation of the data, and unauthorized access have
been growing and the number of attacks have rosed considerably in the last 5 years. The
inclusion of the successful alignment would be deployed for dealing with the possible attacks of
the computer devices. The intrusion of the successful functional development would be aligned
for easing the formation of the successful formation of the activities. Saridakis et al. (2016), have
stated that the possible security flaws in the computer system would result in forming major
setback for execution of the operations without any fear of cyber crimes. The integrity of the data
and information is largely compromised due to the lax of security. The data access was stopped
and hence most of the work was limited resulting in delayed operations and it resulted in both
economic and functional loss to the people and organizations. The ransomware attack proved
fatal and it can be said that the attack showed the weakness in security and integrity. The security
312). IEEE
Android forensics analysis: Private
chat on social messenger
Satrya, G.B., Daely, P.T.
and Shin, S.Y., 2016
In IEEE Conference Paper,
Research Gate
Individual information security,
user behaviour and cyber
victimisation: An empirical study of
social networking users
Saridakis, G., Benson, V.,
Ezingeard, J.N. and
Tennakoon, H., 2016
Technological Forecasting
and Social Change, 102,
pp.320-330
3. Analysis of detailed findings
According to Hui, Kim and Wang (2017), the possible attacks on the computer devices
like cyber theft, misuses of information, manipulation of the data, and unauthorized access have
been growing and the number of attacks have rosed considerably in the last 5 years. The
inclusion of the successful alignment would be deployed for dealing with the possible attacks of
the computer devices. The intrusion of the successful functional development would be aligned
for easing the formation of the successful formation of the activities. Saridakis et al. (2016), have
stated that the possible security flaws in the computer system would result in forming major
setback for execution of the operations without any fear of cyber crimes. The integrity of the data
and information is largely compromised due to the lax of security. The data access was stopped
and hence most of the work was limited resulting in delayed operations and it resulted in both
economic and functional loss to the people and organizations. The ransomware attack proved
fatal and it can be said that the attack showed the weakness in security and integrity. The security

6CASE INVESTIGATION REPORT
system lacked the possible methods of detecting and preventing the attacks (Scaife et al. 2016).
It is evident that the study had resulted in forming many possible issues for the development of
the effective operations and development. Ghernaouti-Helie (2016) have pointed that the main
information storage system was attacked and took a toll of huge amount of economic loss to
global organizations and individuals. The attack was primitive and targeted for dealing damages
with probable issues and integration of the activities.
4. Review and reflection on the findings
4.1 Review of findings
As per the study of the articles by Kester et al. (2015), the attacks of cyber theft, misuses
of information, manipulation of the data, and unauthorized access in the computer system had
resulted in forming the impact on economy, social, and operational. It is evident from the study
that the integrity of the data and information is largely compromised due to the lax of security.
The intrusion of the successful functional development would be aligned for easing the
formation of the successful formation of the activities. Moreover, it can be stated that the
possible security flaws in the computer system would result in forming major setback for
execution of the operations without any fear of cyber crimes. The integrity of the data and
information is largely compromised due to the lax of security along with the stoppage of
information data access and hence most of the work was limited resulting in delayed operations.
Kharraz et al. (2016), provided an explanation that the ransomware was able to extract
information or limit the transfer rate so that the operations can be delayed. It resulted in both
economic and functional loss to the people and organizations. The ransomware attack proved
fatal and it can be said that the attack showed the weakness in security and integrity. The security
system lacked the possible methods of detecting and preventing the attacks (Scaife et al. 2016).
It is evident that the study had resulted in forming many possible issues for the development of
the effective operations and development. Ghernaouti-Helie (2016) have pointed that the main
information storage system was attacked and took a toll of huge amount of economic loss to
global organizations and individuals. The attack was primitive and targeted for dealing damages
with probable issues and integration of the activities.
4. Review and reflection on the findings
4.1 Review of findings
As per the study of the articles by Kester et al. (2015), the attacks of cyber theft, misuses
of information, manipulation of the data, and unauthorized access in the computer system had
resulted in forming the impact on economy, social, and operational. It is evident from the study
that the integrity of the data and information is largely compromised due to the lax of security.
The intrusion of the successful functional development would be aligned for easing the
formation of the successful formation of the activities. Moreover, it can be stated that the
possible security flaws in the computer system would result in forming major setback for
execution of the operations without any fear of cyber crimes. The integrity of the data and
information is largely compromised due to the lax of security along with the stoppage of
information data access and hence most of the work was limited resulting in delayed operations.
Kharraz et al. (2016), provided an explanation that the ransomware was able to extract
information or limit the transfer rate so that the operations can be delayed. It resulted in both
economic and functional loss to the people and organizations. The ransomware attack proved
fatal and it can be said that the attack showed the weakness in security and integrity. The security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CASE INVESTIGATION REPORT
system lacked the possible methods of detecting and preventing the attacks (Scaife et al. 2016).
It is evident that the study had resulted in forming many possible issues for the development of
the effective operations and development.
4.2 Reflection on findings
I had been studying on a number of articles and journals for developing the final solution
to the inclusion of the operations. The attacks of cyber theft, misuses of information,
manipulation of the data, and unauthorized access in the computer system had resulted in
forming the impact on economy, social, and operational. Moreover, we can state that the possible
security flaws in the computer system would result in forming major setback for execution of the
operations without any fear of cyber crimes. Our study helped in forming the inference that the
ransomware attack proved fatal and it can be said that the attack showed the weakness in security
and integrity. The security system lacked the possible methods of detecting and preventing the
attacks. The data access was stopped and hence most of the work was limited resulting in
delayed operations. It resulted in both economic and functional loss to the people and
organizations.
Conclusion
It can be concluded that computer security functions had been largely challenged with the
innovation in the criminal activities and operations. The possible attacks on the computer devices
like cyber theft, misuses of information, manipulation of the data, and unauthorized access have
been growing and the number of attacks have rosed considerably in the last 5 years. The
development of successful security functions had be helpful for easing the implication of the
operations for organizations and individuals. The possible security flaws in the computer system
system lacked the possible methods of detecting and preventing the attacks (Scaife et al. 2016).
It is evident that the study had resulted in forming many possible issues for the development of
the effective operations and development.
4.2 Reflection on findings
I had been studying on a number of articles and journals for developing the final solution
to the inclusion of the operations. The attacks of cyber theft, misuses of information,
manipulation of the data, and unauthorized access in the computer system had resulted in
forming the impact on economy, social, and operational. Moreover, we can state that the possible
security flaws in the computer system would result in forming major setback for execution of the
operations without any fear of cyber crimes. Our study helped in forming the inference that the
ransomware attack proved fatal and it can be said that the attack showed the weakness in security
and integrity. The security system lacked the possible methods of detecting and preventing the
attacks. The data access was stopped and hence most of the work was limited resulting in
delayed operations. It resulted in both economic and functional loss to the people and
organizations.
Conclusion
It can be concluded that computer security functions had been largely challenged with the
innovation in the criminal activities and operations. The possible attacks on the computer devices
like cyber theft, misuses of information, manipulation of the data, and unauthorized access have
been growing and the number of attacks have rosed considerably in the last 5 years. The
development of successful security functions had be helpful for easing the implication of the
operations for organizations and individuals. The possible security flaws in the computer system

8CASE INVESTIGATION REPORT
had resulted in forming major setback for execution of the operations without any fear of cyber
crimes. The attacks of cyber theft, misuses of information, manipulation of the data, and
unauthorized access in the computer system had resulted in forming the impact on economy,
social, and operational. The integrity of the data and information was largely compromised due
to the lax of security.
had resulted in forming major setback for execution of the operations without any fear of cyber
crimes. The attacks of cyber theft, misuses of information, manipulation of the data, and
unauthorized access in the computer system had resulted in forming the impact on economy,
social, and operational. The integrity of the data and information was largely compromised due
to the lax of security.

9CASE INVESTIGATION REPORT
References
Al Mutawa, N., Bryce, J., Franqueira, V.N. and Marrington, A., 2015, August. Behavioural
evidence analysis applied to digital forensics: an empirical analysis of child pornography cases
using P2P networks. In Availability, Reliability and Security (ARES), 2015 10th International
Conference on (pp. 293-302). IEEE.
Cummins Flory, T.A., 2016. Digital forensics in law enforcement: A needs based analysis of
Indiana agencies. Journal of Digital Forensics, Security and Law, 11(1), p.4.
Dilek, S., Çakır, H. and Aydın, M., 2015. Applications of artificial intelligence techniques to
combating cyber crimes: A review. arXiv preprint arXiv:1502.03552.
Ghernaouti-Helie, S., 2016. Cyber power: crime, conflict and security in cyberspace. EPFL
Press.
Hui, K.L., Kim, S.H. and Wang, Q.H., 2017. Cybercrime deterrence and international legislation:
evidence from distributed denial of service attacks. Mis Quarterly, 41(2), p.497.
Karie, N.M. and Venter, H.S., 2015. Taxonomy of challenges for digital forensics. Journal of
forensic sciences, 60(4), pp.885-893.
Kester, Quist-Aphetsi, Laurent Nana, Anca Christine Pascu, Sophie Gire, Jojo M. Eghan, and Nii
Narku Quaynor. 2015. "Feature Based Cryptanalytic Technique for Digital Forensics Analysis of
Visual Cryptographic Digital Image Data Based on Formal Concept Analysis." In Proceedings of
the International Conference on Foundations of Computer Science (FCS), p. 40. The Steering
Committee of The World Congress in Computer Science, Computer Engineering and Applied
Computing (WorldComp).
References
Al Mutawa, N., Bryce, J., Franqueira, V.N. and Marrington, A., 2015, August. Behavioural
evidence analysis applied to digital forensics: an empirical analysis of child pornography cases
using P2P networks. In Availability, Reliability and Security (ARES), 2015 10th International
Conference on (pp. 293-302). IEEE.
Cummins Flory, T.A., 2016. Digital forensics in law enforcement: A needs based analysis of
Indiana agencies. Journal of Digital Forensics, Security and Law, 11(1), p.4.
Dilek, S., Çakır, H. and Aydın, M., 2015. Applications of artificial intelligence techniques to
combating cyber crimes: A review. arXiv preprint arXiv:1502.03552.
Ghernaouti-Helie, S., 2016. Cyber power: crime, conflict and security in cyberspace. EPFL
Press.
Hui, K.L., Kim, S.H. and Wang, Q.H., 2017. Cybercrime deterrence and international legislation:
evidence from distributed denial of service attacks. Mis Quarterly, 41(2), p.497.
Karie, N.M. and Venter, H.S., 2015. Taxonomy of challenges for digital forensics. Journal of
forensic sciences, 60(4), pp.885-893.
Kester, Quist-Aphetsi, Laurent Nana, Anca Christine Pascu, Sophie Gire, Jojo M. Eghan, and Nii
Narku Quaynor. 2015. "Feature Based Cryptanalytic Technique for Digital Forensics Analysis of
Visual Cryptographic Digital Image Data Based on Formal Concept Analysis." In Proceedings of
the International Conference on Foundations of Computer Science (FCS), p. 40. The Steering
Committee of The World Congress in Computer Science, Computer Engineering and Applied
Computing (WorldComp).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10CASE INVESTIGATION REPORT
Kharraz, A., Arshad, S., Mulliner, C., Robertson, W.K. and Kirda, E., 2016, August. UNVEIL:
A Large-Scale, Automated Approach to Detecting Ransomware. In USENIX Security
Symposium (pp. 757-772).
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L. and Kirda, E., 2015, July. Cutting the
gordian knot: A look under the hood of ransomware attacks. In International Conference on
Detection of Intrusions and Malware, and Vulnerability Assessment (pp. 3-24). Springer, Cham.
Mercaldo, F., Nardone, V., Santone, A. and Visaggio, C.A., 2016, June. Ransomware steals your
phone. formal methods rescue it. In International Conference on Formal Techniques for
Distributed Objects, Components, and Systems (pp. 212-221). Springer, Cham.
Sammons, J. ed., 2015. Digital Forensics: Threatscape and Best Practices. Syngress.
Saridakis, G., Benson, V., Ezingeard, J.N. and Tennakoon, H., 2016. Individual information
security, user behaviour and cyber victimisation: An empirical study of social networking
users. Technological Forecasting and Social Change, 102, pp.320-330.
Satrya, G.B., Daely, P.T. and Shin, S.Y., 2016, July. Android forensics analysis: Private chat on
social messenger. In IEEE Conference Paper, Research Gate.
Scaife, N., Carter, H., Traynor, P. and Butler, K.R., 2016, June. Cryptolock (and drop it):
stopping ransomware attacks on user data. In Distributed Computing Systems (ICDCS), 2016
IEEE 36th International Conference on (pp. 303-312). IEEE.
Shalaginov, A. and Franke, K., 2015, November. Automated generation of fuzzy rules from
large-scale network traffic analysis in digital forensics investigations. In Soft Computing and
Pattern Recognition (SoCPaR), 2015 7th International Conference of (pp. 31-36). IEEE.
Kharraz, A., Arshad, S., Mulliner, C., Robertson, W.K. and Kirda, E., 2016, August. UNVEIL:
A Large-Scale, Automated Approach to Detecting Ransomware. In USENIX Security
Symposium (pp. 757-772).
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L. and Kirda, E., 2015, July. Cutting the
gordian knot: A look under the hood of ransomware attacks. In International Conference on
Detection of Intrusions and Malware, and Vulnerability Assessment (pp. 3-24). Springer, Cham.
Mercaldo, F., Nardone, V., Santone, A. and Visaggio, C.A., 2016, June. Ransomware steals your
phone. formal methods rescue it. In International Conference on Formal Techniques for
Distributed Objects, Components, and Systems (pp. 212-221). Springer, Cham.
Sammons, J. ed., 2015. Digital Forensics: Threatscape and Best Practices. Syngress.
Saridakis, G., Benson, V., Ezingeard, J.N. and Tennakoon, H., 2016. Individual information
security, user behaviour and cyber victimisation: An empirical study of social networking
users. Technological Forecasting and Social Change, 102, pp.320-330.
Satrya, G.B., Daely, P.T. and Shin, S.Y., 2016, July. Android forensics analysis: Private chat on
social messenger. In IEEE Conference Paper, Research Gate.
Scaife, N., Carter, H., Traynor, P. and Butler, K.R., 2016, June. Cryptolock (and drop it):
stopping ransomware attacks on user data. In Distributed Computing Systems (ICDCS), 2016
IEEE 36th International Conference on (pp. 303-312). IEEE.
Shalaginov, A. and Franke, K., 2015, November. Automated generation of fuzzy rules from
large-scale network traffic analysis in digital forensics investigations. In Soft Computing and
Pattern Recognition (SoCPaR), 2015 7th International Conference of (pp. 31-36). IEEE.
11CASE INVESTIGATION REPORT
Appendix-Screenshots
Appendix-Screenshots
12CASE INVESTIGATION REPORT
.
.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13CASE INVESTIGATION REPORT
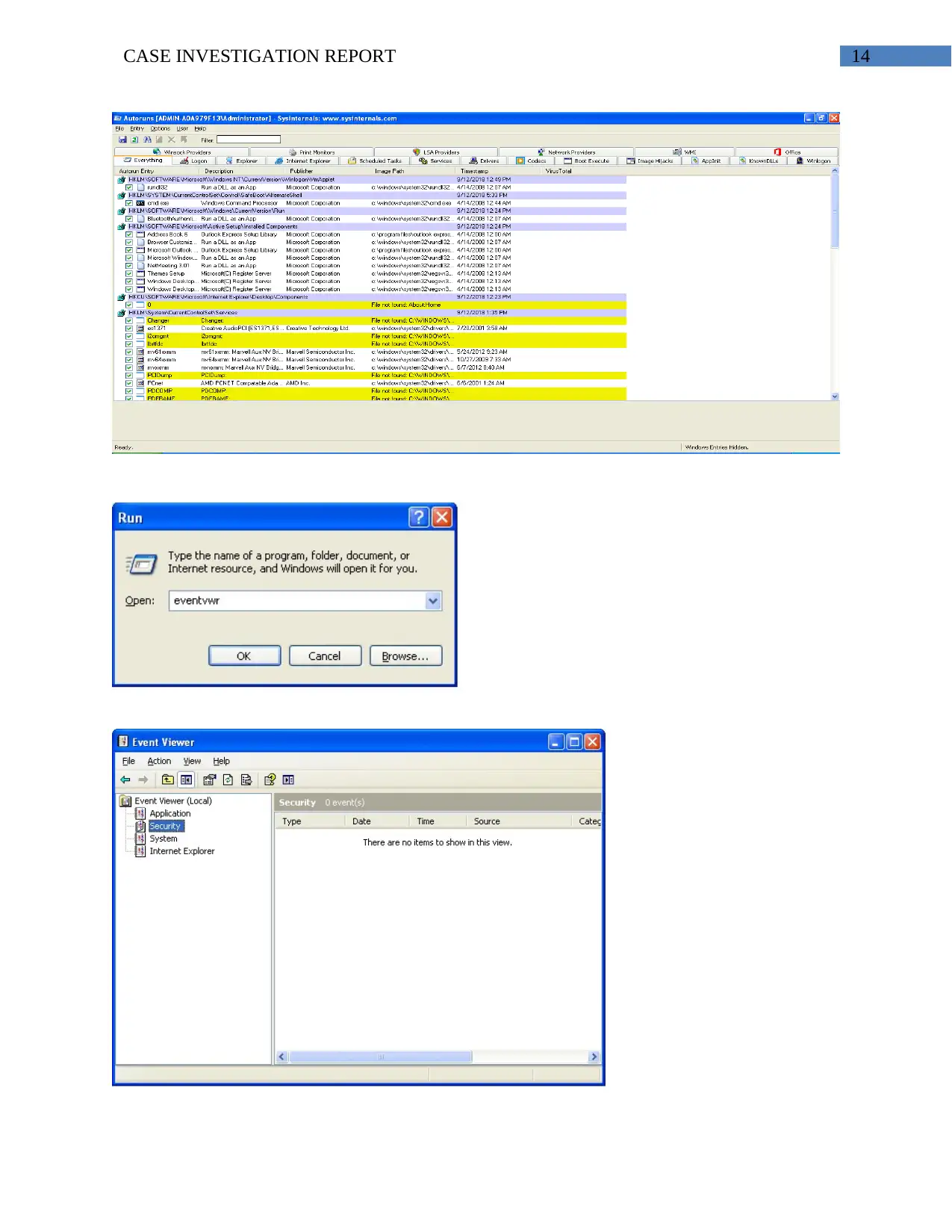
14CASE INVESTIGATION REPORT
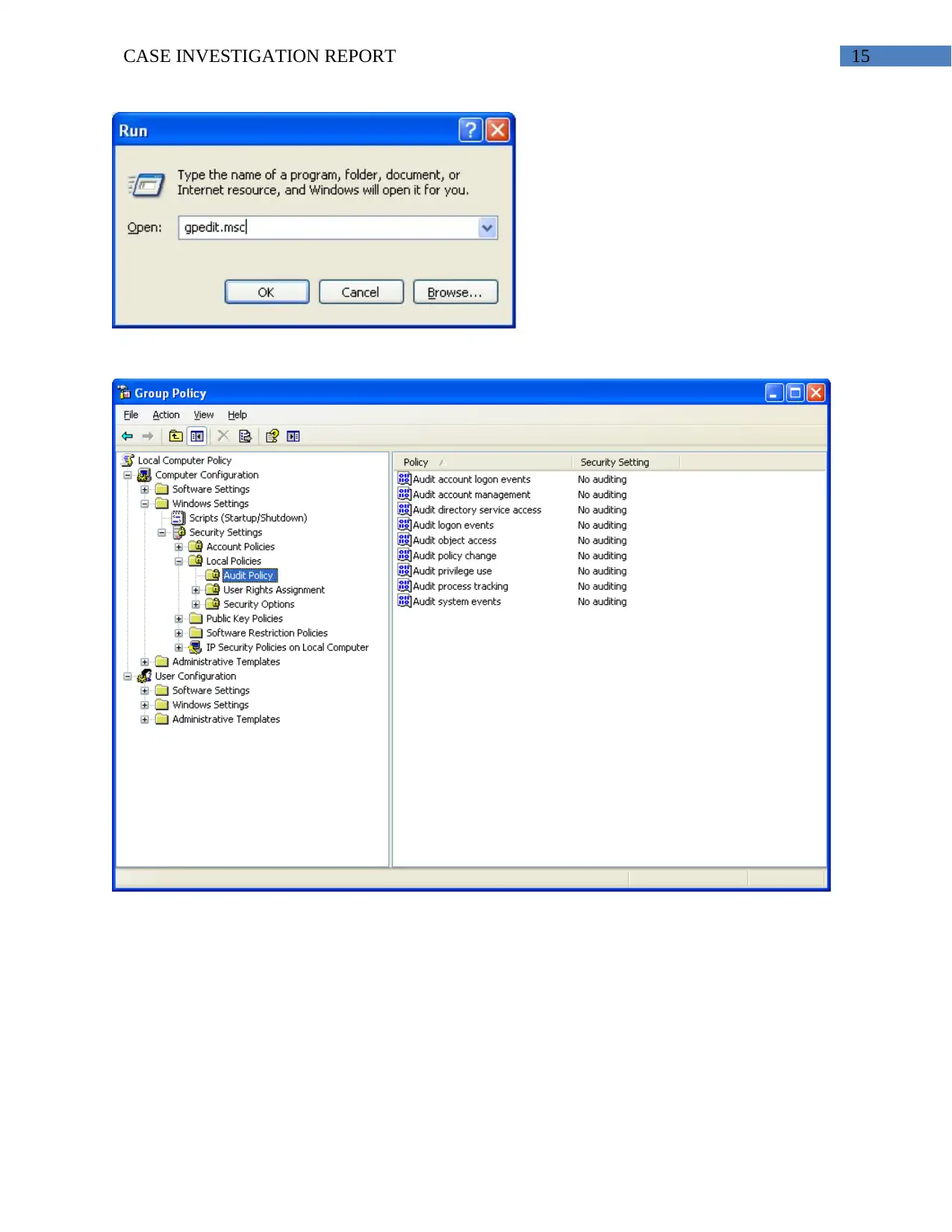
15CASE INVESTIGATION REPORT
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
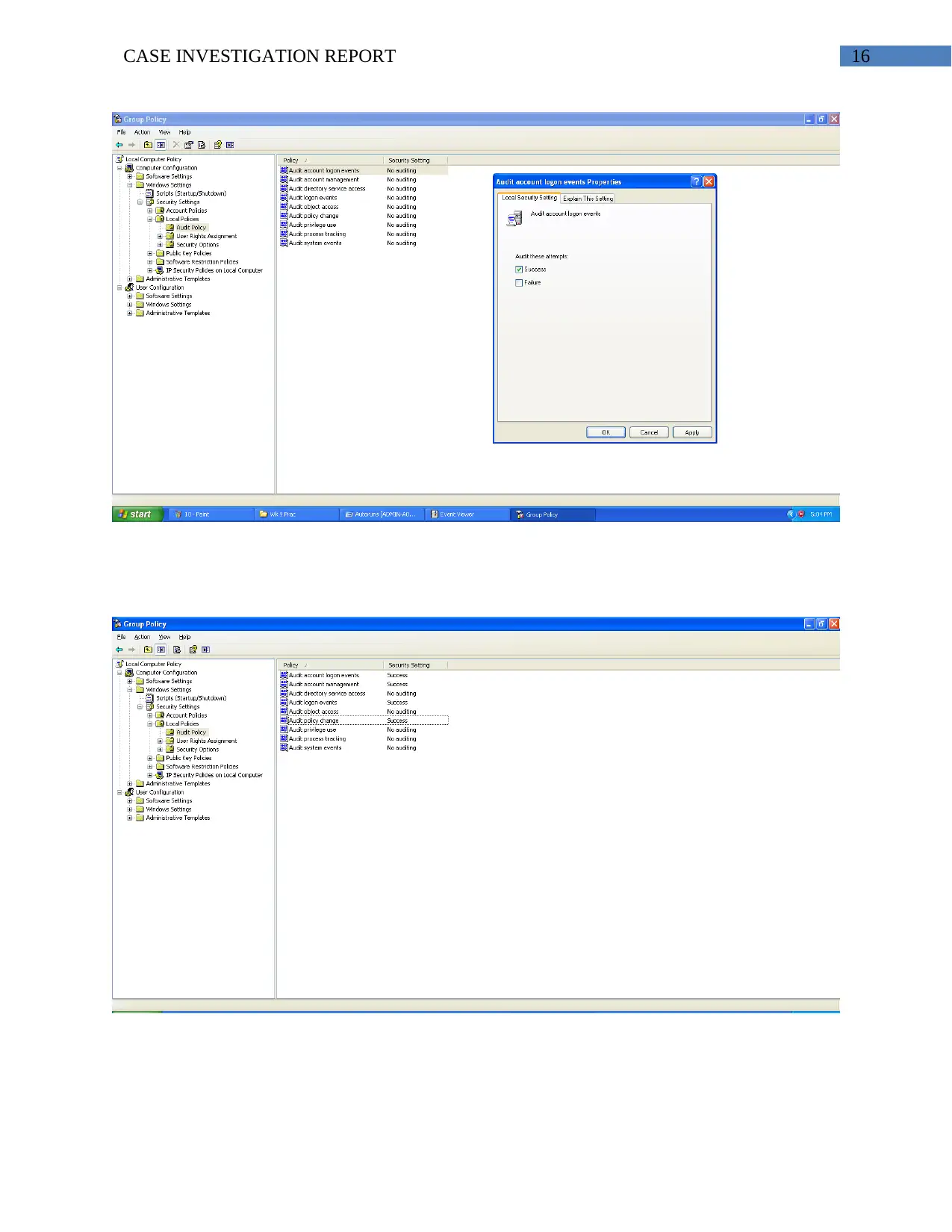
16CASE INVESTIGATION REPORT
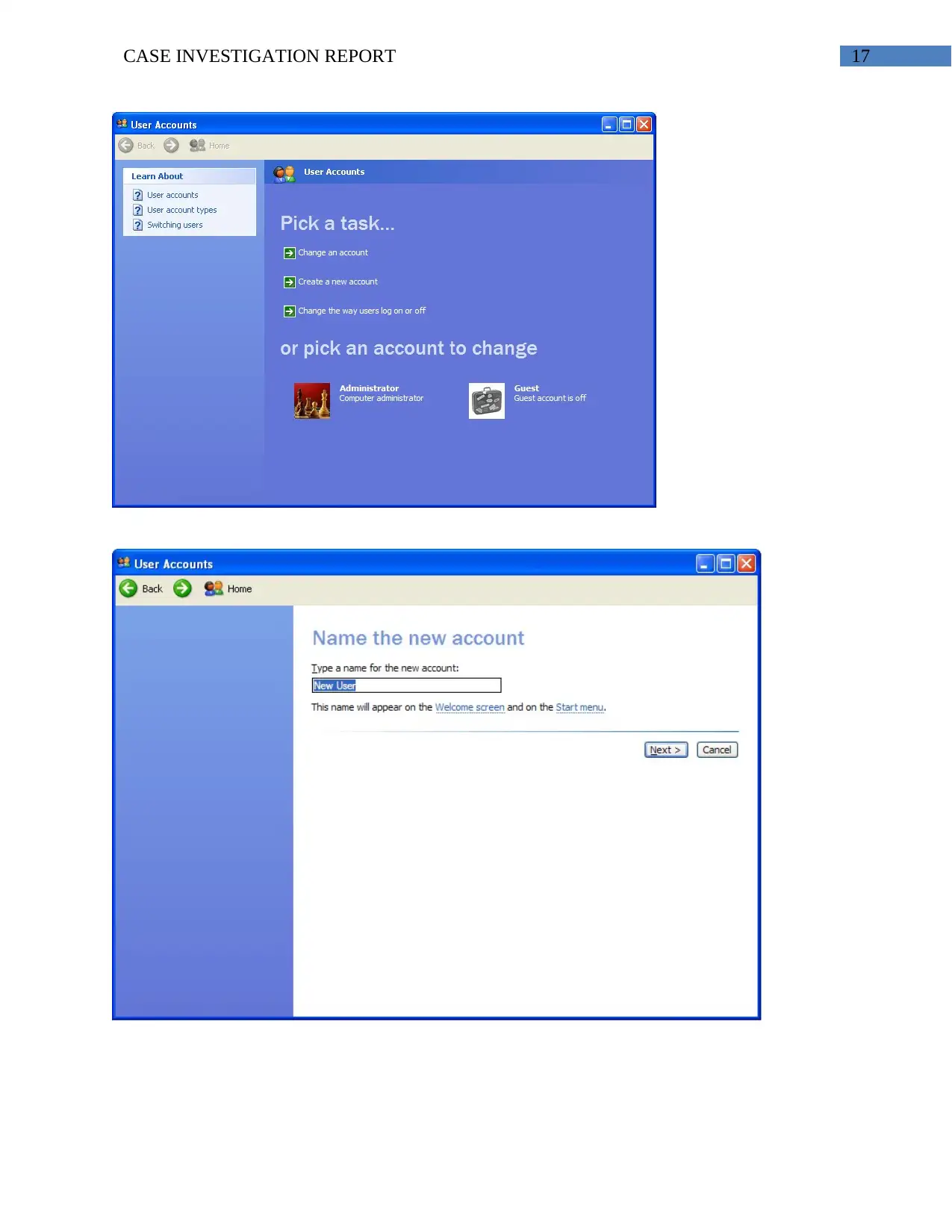
17CASE INVESTIGATION REPORT
18CASE INVESTIGATION REPORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
19CASE INVESTIGATION REPORT
1 out of 20
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





