An Analysis of Security Challenges in 5G Network Systems
VerifiedAdded on 2022/09/02
|19
|4146
|17
Report
AI Summary
This report provides a comprehensive overview of the security challenges associated with 5G networks. It begins by introducing 5G technology and its features, including improvements in broadband, autonomous vehicles, public infrastructure safety, remote control devices, and healthcare applications. The report then delves into the security challenges that arise from 5G's increased connectivity and bandwidth, focusing on vulnerabilities in areas such as autonomous vehicles, healthcare, and IoT devices. These challenges include cyber-attacks, medical data breaches, and privacy concerns. The report also highlights the opportunities that 5G technology offers, and concludes by emphasizing the importance of addressing these security challenges to ensure the safe and reliable deployment of 5G networks. The report is a valuable resource for students studying telecommunications and cybersecurity, providing insights into the current and future landscape of 5G security.

Running head: - CHALLENGES IN 5G SECURITY
CHALLENGES IN 5G SECURITY
Name of the Student
Name of the University
Author Note
CHALLENGES IN 5G SECURITY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CHALLENGES IN 5G SECURITY
Table of Contents
1. Introduction:...........................................................................................................................2
2. 5G network technology:.........................................................................................................2
3. Features of 5G network:.........................................................................................................5
3.1. Improvement in broadband:............................................................................................6
3.2. Autonomous Vehicles:....................................................................................................6
3.3. Public infrastructure safety:............................................................................................7
3.4. Remote control device:...................................................................................................7
3.5. Healthcare:......................................................................................................................7
4. Security Challenges of 5G network:......................................................................................8
5. Opportunities in 5G network:...............................................................................................13
6. Conclusion:..........................................................................................................................15
7. References:...........................................................................................................................16
Table of Contents
1. Introduction:...........................................................................................................................2
2. 5G network technology:.........................................................................................................2
3. Features of 5G network:.........................................................................................................5
3.1. Improvement in broadband:............................................................................................6
3.2. Autonomous Vehicles:....................................................................................................6
3.3. Public infrastructure safety:............................................................................................7
3.4. Remote control device:...................................................................................................7
3.5. Healthcare:......................................................................................................................7
4. Security Challenges of 5G network:......................................................................................8
5. Opportunities in 5G network:...............................................................................................13
6. Conclusion:..........................................................................................................................15
7. References:...........................................................................................................................16

2CHALLENGES IN 5G SECURITY
1. Introduction:
5G specifically refers to the fifth generation of communications that are wireless
provisioning with the required amount of support to the field of cellular data networks. This
particular technology is considered to be the primary improvement of 4G technology that is
considered to be potentially capable enough to revolutionize the entire world that is
dependent on a daily basis upon the mobile networks1. In addition to this, the 5G technology
has been supposedly utilized IoT as a primary acceleration towards virtually acting as a boost
towards the telecommunication industry also upgrading the existing infrastructure. With the
usage of this technology and the relative implementation, it has been visibly identified that
the technology also has some major challenges in terms of security towards the existing
commodities of the digital world. This discussion primarily aims at introducing the 5G
network and identifies the challenges that the technology has a direct association2. Following
this, the report states the various features of 5G technology along with the opportunities that
shall be offered by this particular technology towards the digital world and the field of
business as well as manufacturing. Lastly, the discussion ends with a conclusion defining the
importance as well as the challenges that are associated with 5G networks in future.
2. 5G network technology:
5G is the telecommunication technology that is considered to be the fifth generation
of mobile networks that has been developed to act as a supporting hand towards the mobile
networks. This fifth generation technology is claimed to be a much awaited improvement to
the already existing technologies and as well promises to put forward a greater revolution
1 Gheisarnejad, Meysam, Mohammad-Hassan Khooban, and Tomislav Dragicevic. "The future 5G network
based secondary load frequency control in maritime microgrids." IEEE Journal of Emerging and Selected
Topics in Power Electronics (2019).
2 Osseiran, Afif, Jose F. Monserrat, and Patrick Marsch, eds. 5G mobile and wireless communications
technology. Cambridge University Press, 2016.
1. Introduction:
5G specifically refers to the fifth generation of communications that are wireless
provisioning with the required amount of support to the field of cellular data networks. This
particular technology is considered to be the primary improvement of 4G technology that is
considered to be potentially capable enough to revolutionize the entire world that is
dependent on a daily basis upon the mobile networks1. In addition to this, the 5G technology
has been supposedly utilized IoT as a primary acceleration towards virtually acting as a boost
towards the telecommunication industry also upgrading the existing infrastructure. With the
usage of this technology and the relative implementation, it has been visibly identified that
the technology also has some major challenges in terms of security towards the existing
commodities of the digital world. This discussion primarily aims at introducing the 5G
network and identifies the challenges that the technology has a direct association2. Following
this, the report states the various features of 5G technology along with the opportunities that
shall be offered by this particular technology towards the digital world and the field of
business as well as manufacturing. Lastly, the discussion ends with a conclusion defining the
importance as well as the challenges that are associated with 5G networks in future.
2. 5G network technology:
5G is the telecommunication technology that is considered to be the fifth generation
of mobile networks that has been developed to act as a supporting hand towards the mobile
networks. This fifth generation technology is claimed to be a much awaited improvement to
the already existing technologies and as well promises to put forward a greater revolution
1 Gheisarnejad, Meysam, Mohammad-Hassan Khooban, and Tomislav Dragicevic. "The future 5G network
based secondary load frequency control in maritime microgrids." IEEE Journal of Emerging and Selected
Topics in Power Electronics (2019).
2 Osseiran, Afif, Jose F. Monserrat, and Patrick Marsch, eds. 5G mobile and wireless communications
technology. Cambridge University Press, 2016.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CHALLENGES IN 5G SECURITY
within the field of telecommunication and cellular networks with an additive usage of
Internet of Things (IoT)3. The adoption of this technology is already starting to take place
from the year of 2019 and have been virtually every individual telecommunication enterprises
belonging to this industry is making efforts to upgrade their existing infrastructure to offer all
of its customers with the upgraded features of 5G technology.
Figure-1: 5G-network technology
The frequency spectrum of this 5G has been separated into millimetre, low-band
waves and that of mid-band waves. The low-band makes use of similar range of frequency as
that of the previously existing 4G technology. 5G millimetre claims to be the fastest, having
can actual speed of 1-2 Gbit/s down4. The frequency of this 5G spectrum is above the count
of 24 GHz reaching until the count of 72 GHz that is above the high range of the frequency
band’s lower lying boundary.
3 Zhang, Haijun, et al. "Network slicing based 5G and future mobile networks: mobility, resource management,
and challenges." IEEE communications magazine 55.8 (2017): 138-145.
4 Singh, Rakesh Kumar, Deepika Bisht, and R. C. Prasad. "Development of 5G mobile network technology and
its architecture." International Journal of Recent Trends in Engineering & Research (IJRTER) 3.10 (2017): 196-
201.
within the field of telecommunication and cellular networks with an additive usage of
Internet of Things (IoT)3. The adoption of this technology is already starting to take place
from the year of 2019 and have been virtually every individual telecommunication enterprises
belonging to this industry is making efforts to upgrade their existing infrastructure to offer all
of its customers with the upgraded features of 5G technology.
Figure-1: 5G-network technology
The frequency spectrum of this 5G has been separated into millimetre, low-band
waves and that of mid-band waves. The low-band makes use of similar range of frequency as
that of the previously existing 4G technology. 5G millimetre claims to be the fastest, having
can actual speed of 1-2 Gbit/s down4. The frequency of this 5G spectrum is above the count
of 24 GHz reaching until the count of 72 GHz that is above the high range of the frequency
band’s lower lying boundary.
3 Zhang, Haijun, et al. "Network slicing based 5G and future mobile networks: mobility, resource management,
and challenges." IEEE communications magazine 55.8 (2017): 138-145.
4 Singh, Rakesh Kumar, Deepika Bisht, and R. C. Prasad. "Development of 5G mobile network technology and
its architecture." International Journal of Recent Trends in Engineering & Research (IJRTER) 3.10 (2017): 196-
201.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CHALLENGES IN 5G SECURITY
The service area of the 5G networks are particularly divided into smaller sized
geographical areas that are termed as cells. Analog signals put forward the representation of
sounds as well as images that are in digitized form within the telephone and are specifically
converted with the help of Analog to digital signal converter following which, are transmitted
in bits form. All of the existing 5G enabled working devices present within the cells carry out
the communication with the help of radio waves along with a provisioned helping hand from
the antenna as well as low power transceiver present within the cell itself5. These locally
existing antennas are specifically connected with the help of telephonic network as well as
the internet having the primary inclusion of an optical fibre consisting of high bandwidth or
with the existence of a wireless backhaul connection. Unlike the other existing cellular
networks, the mobile crossing over to one cell from one cell is handed over to the newly
existing cell of a different area in an automated manner.
Hence, it can be stated that with the potential introduction of 5G networks, there is a
greater possibility of witnessing greater speed of downloads as well as uploads compared to
what was visible in the 4G LTE network. Latency as well as the time taken for the devices to
carry out communication with each other or with the wirelessly working networks will be
greatly reduced by this network as well.
Following this, the particular shift towards 5G from that of the traditional 4G will
greatly help the change within interaction on a daily basis within individuals. In addition to
the change in the way of interaction, 5G is also considered to be a primary contributor
towards introduction and improvement in autonomous vehicles. Such autonomous vehicles
with a potential helping hand from 5G shall provision the vehicles with the ability to carry
5 Yousaf, Faqir Zarrar, et al. "NFV and SDN—Key technology enablers for 5G networks." IEEE Journal on
Selected Areas in Communications 35.11 (2017): 2468-2478.
The service area of the 5G networks are particularly divided into smaller sized
geographical areas that are termed as cells. Analog signals put forward the representation of
sounds as well as images that are in digitized form within the telephone and are specifically
converted with the help of Analog to digital signal converter following which, are transmitted
in bits form. All of the existing 5G enabled working devices present within the cells carry out
the communication with the help of radio waves along with a provisioned helping hand from
the antenna as well as low power transceiver present within the cell itself5. These locally
existing antennas are specifically connected with the help of telephonic network as well as
the internet having the primary inclusion of an optical fibre consisting of high bandwidth or
with the existence of a wireless backhaul connection. Unlike the other existing cellular
networks, the mobile crossing over to one cell from one cell is handed over to the newly
existing cell of a different area in an automated manner.
Hence, it can be stated that with the potential introduction of 5G networks, there is a
greater possibility of witnessing greater speed of downloads as well as uploads compared to
what was visible in the 4G LTE network. Latency as well as the time taken for the devices to
carry out communication with each other or with the wirelessly working networks will be
greatly reduced by this network as well.
Following this, the particular shift towards 5G from that of the traditional 4G will
greatly help the change within interaction on a daily basis within individuals. In addition to
the change in the way of interaction, 5G is also considered to be a primary contributor
towards introduction and improvement in autonomous vehicles. Such autonomous vehicles
with a potential helping hand from 5G shall provision the vehicles with the ability to carry
5 Yousaf, Faqir Zarrar, et al. "NFV and SDN—Key technology enablers for 5G networks." IEEE Journal on
Selected Areas in Communications 35.11 (2017): 2468-2478.

5CHALLENGES IN 5G SECURITY
out communication with other autonomous vehicles6. Such communication can greatly allow
cars to provision other cars with the knowledge of road condition as well as offer with
information regarding performance to the automakers. Such vehicular interaction can act as a
major boon towards a great reduction of accidents that take place on road and lead to
unavoidable consequences.
Lastly, the introduction of 5G will provision the cities and other municipalities with
the allowance to operate with greater efficiency. In addition to this, the utility companies will
also have the added provision to monitor the usage, sensors notifying the public departments
regarding flooding of drains or streetlights going off. This can allow the municipalities to
quickly act towards the same and bring back normalized conditions.
With the increasing technologies and the relative amount of digitalization that 5G
promises to bring in, there is an increasing demand for an improvement in the healthcare
sector as well that is much evident from the 5G technology shall bring with itself7. Specific
growth and improvements in the services of telemedicine, physical therapy with the help of
AR as well as remote recovery that shall bring in a greater efficiency for the health related
services to save time and lives of millions belonging to the global digital age.
3. Features of 5G network:
With the introduction of 5G technology the following features are supposed to be
provisioned by this particular technology as a part of innovating the digitalized global world.
The features and functionalities of 5G technology has been briefly described in the following
section.
6 Blanco, Bego, et al. "Technology pillars in the architecture of future 5G mobile networks: NFV, MEC and
SDN." Computer Standards & Interfaces 54 (2017): 216-228.
7 Tian, Man-Wen, et al. "Research on Financial Technology Innovation and Application Based on 5G Network."
IEEE Access 7 (2019): 138614-138623.
out communication with other autonomous vehicles6. Such communication can greatly allow
cars to provision other cars with the knowledge of road condition as well as offer with
information regarding performance to the automakers. Such vehicular interaction can act as a
major boon towards a great reduction of accidents that take place on road and lead to
unavoidable consequences.
Lastly, the introduction of 5G will provision the cities and other municipalities with
the allowance to operate with greater efficiency. In addition to this, the utility companies will
also have the added provision to monitor the usage, sensors notifying the public departments
regarding flooding of drains or streetlights going off. This can allow the municipalities to
quickly act towards the same and bring back normalized conditions.
With the increasing technologies and the relative amount of digitalization that 5G
promises to bring in, there is an increasing demand for an improvement in the healthcare
sector as well that is much evident from the 5G technology shall bring with itself7. Specific
growth and improvements in the services of telemedicine, physical therapy with the help of
AR as well as remote recovery that shall bring in a greater efficiency for the health related
services to save time and lives of millions belonging to the global digital age.
3. Features of 5G network:
With the introduction of 5G technology the following features are supposed to be
provisioned by this particular technology as a part of innovating the digitalized global world.
The features and functionalities of 5G technology has been briefly described in the following
section.
6 Blanco, Bego, et al. "Technology pillars in the architecture of future 5G mobile networks: NFV, MEC and
SDN." Computer Standards & Interfaces 54 (2017): 216-228.
7 Tian, Man-Wen, et al. "Research on Financial Technology Innovation and Application Based on 5G Network."
IEEE Access 7 (2019): 138614-138623.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CHALLENGES IN 5G SECURITY
3.1. Improvement in broadband:
Shifting over to 5G from the traditionally existing 4G technology will bring in an
effective change within the way of interaction on a regular basis. However, it can be stated
that this refers to an option for individuals if they want to keep using the mobile broadband.
Majority of the metropolitan cities make proper utilization of LTE capacity. In some
of the surrounding cities, users have already started experiencing slowdowns in their internet
or communication connectivity8. In regards to this, 5G specifically adds a huge amount of
spectrum in the bands that have still not been used in the traffic of the commercial broadband.
3.2. Autonomous Vehicles:
There is a considered expectation to visualise the increase of autonomous vehicles
with the introduction of 5G in and across the whole of United States. With the supposed
future that shall come in along with 5G, the autonomous vehicles are considered to carry out
communication with each other. Such communication shall be the likes of provisioning the
other vehicle regarding any information about the condition of the road as well as providing
the performance information to the owner and the automaker of the vehicle9. Along with this,
the vehicular communication will also save thousands of lives by letting the other vehicle let
know about braking and other things beforehand.
3.3. Public infrastructure safety:
5G network technology will provision with the allowance to the cities as well as the
municipalities to carry out the operation in a greater efficient manner. Companies that deal
with the various forms of utilities will have the provision to track the usage in a remote way10.
8 Tian, M. W., Wang, L., Yan, S. R., Tian, X. X., Liu, Z. Q., & Rodrigues, J. J. P. (2019). Research on Financial
Technology Innovation and Application Based on 5G Network. IEEE Access, 7, 138614-138623.
9 Sun, Songlin, et al. "An intelligent SDN framework for 5G heterogeneous networks." IEEE Communications
Magazine 53.11 (2015): 142-147.
10 Patel, Saurabh, Malhar Chauhan, and Kinjal Kapadiya. "5G: Future mobile technology-vision 2020."
International Journal of Computer Applications 54.17 (2012).
3.1. Improvement in broadband:
Shifting over to 5G from the traditionally existing 4G technology will bring in an
effective change within the way of interaction on a regular basis. However, it can be stated
that this refers to an option for individuals if they want to keep using the mobile broadband.
Majority of the metropolitan cities make proper utilization of LTE capacity. In some
of the surrounding cities, users have already started experiencing slowdowns in their internet
or communication connectivity8. In regards to this, 5G specifically adds a huge amount of
spectrum in the bands that have still not been used in the traffic of the commercial broadband.
3.2. Autonomous Vehicles:
There is a considered expectation to visualise the increase of autonomous vehicles
with the introduction of 5G in and across the whole of United States. With the supposed
future that shall come in along with 5G, the autonomous vehicles are considered to carry out
communication with each other. Such communication shall be the likes of provisioning the
other vehicle regarding any information about the condition of the road as well as providing
the performance information to the owner and the automaker of the vehicle9. Along with this,
the vehicular communication will also save thousands of lives by letting the other vehicle let
know about braking and other things beforehand.
3.3. Public infrastructure safety:
5G network technology will provision with the allowance to the cities as well as the
municipalities to carry out the operation in a greater efficient manner. Companies that deal
with the various forms of utilities will have the provision to track the usage in a remote way10.
8 Tian, M. W., Wang, L., Yan, S. R., Tian, X. X., Liu, Z. Q., & Rodrigues, J. J. P. (2019). Research on Financial
Technology Innovation and Application Based on 5G Network. IEEE Access, 7, 138614-138623.
9 Sun, Songlin, et al. "An intelligent SDN framework for 5G heterogeneous networks." IEEE Communications
Magazine 53.11 (2015): 142-147.
10 Patel, Saurabh, Malhar Chauhan, and Kinjal Kapadiya. "5G: Future mobile technology-vision 2020."
International Journal of Computer Applications 54.17 (2012).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CHALLENGES IN 5G SECURITY
In addition to this, the sensors that shall be installed will notify the departments of the public
works regarding the breakdown and the municipalities can act in a quick manner to fix the
same.
3.4. Remote control device:
5G technology having the inclusion of a lower rate of latency, the heavy machinery
shall be controlled with the help of remote that has the capability to turn into a reality. With
the primary objective is to bring a reduction in the risk associated with the hazardous
environment, this remote control will allow the technicians with the ability to have the
control over the machinery from anywhere in the entire world.
3.5. Healthcare:
The Ultra-reliable low latency communications (URLLC) component that belongs to
the 5G technology will evidently bring a potential change within the field of healthcare. This
significant change will have a potential effect upon the field of telemedicine, physical therapy
with the use of AR, remote recovery as well as the precision surgery in the upcoming year of
the healthcare field.
Along with this, mMTC will also act a as a primary contributor towards the field of
healthcare and making it innovative and advanced for better treatment of the patients affected
with illness11. Hospitals will have the provision to put forward creation of huge sensor
networks for the monitoring of patients, prescribing of medicines as well as monitoring of the
subscriber for the insurance to determine proper treatment and the relative processes.
11 Iwamura, Mikio. "NGMN view on 5G architecture." 2015 IEEE 81st Vehicular Technology Conference (VTC
Spring). IEEE, 2015.
In addition to this, the sensors that shall be installed will notify the departments of the public
works regarding the breakdown and the municipalities can act in a quick manner to fix the
same.
3.4. Remote control device:
5G technology having the inclusion of a lower rate of latency, the heavy machinery
shall be controlled with the help of remote that has the capability to turn into a reality. With
the primary objective is to bring a reduction in the risk associated with the hazardous
environment, this remote control will allow the technicians with the ability to have the
control over the machinery from anywhere in the entire world.
3.5. Healthcare:
The Ultra-reliable low latency communications (URLLC) component that belongs to
the 5G technology will evidently bring a potential change within the field of healthcare. This
significant change will have a potential effect upon the field of telemedicine, physical therapy
with the use of AR, remote recovery as well as the precision surgery in the upcoming year of
the healthcare field.
Along with this, mMTC will also act a as a primary contributor towards the field of
healthcare and making it innovative and advanced for better treatment of the patients affected
with illness11. Hospitals will have the provision to put forward creation of huge sensor
networks for the monitoring of patients, prescribing of medicines as well as monitoring of the
subscriber for the insurance to determine proper treatment and the relative processes.
11 Iwamura, Mikio. "NGMN view on 5G architecture." 2015 IEEE 81st Vehicular Technology Conference (VTC
Spring). IEEE, 2015.

8CHALLENGES IN 5G SECURITY
Figure-2: 5G availability in United States
4. Security Challenges of 5G network:
5G networks allow with the provision of connectivity with multiple devices that also
puts forward an increase in the bandwidth over the existing LTE. This has potentially put
forward a creation of threat landscape from the previously existing networks. Challenges
related to security of the 5G network is supposed to be worked towards to safeguard the
invasion of privacy and stealing of information12. In regards to this, IoT that is a primary part
of 5G enabled network is considered to be the component that has the majority of the security
related risk. Devices having the inclusion of IoT are considered to be the hardware that are
mostly attacked accounting up to 78% of the malware detection and the relative events within
the service provider for communication in the year of 2018.
The upcoming 5G technology and the relative network carry the potential capability
to explode the existing vertical industries having enabled the creation of multiple array of
newer services that also have the primary requirement of different levels of security and
12 Kachhavay, Meenal G., and Ajay P. Thakare. "5G technology-evolution and revolution." International
Journal of Computer Science and Mobile Computing 3.3 (2014): 1080-1087.
Figure-2: 5G availability in United States
4. Security Challenges of 5G network:
5G networks allow with the provision of connectivity with multiple devices that also
puts forward an increase in the bandwidth over the existing LTE. This has potentially put
forward a creation of threat landscape from the previously existing networks. Challenges
related to security of the 5G network is supposed to be worked towards to safeguard the
invasion of privacy and stealing of information12. In regards to this, IoT that is a primary part
of 5G enabled network is considered to be the component that has the majority of the security
related risk. Devices having the inclusion of IoT are considered to be the hardware that are
mostly attacked accounting up to 78% of the malware detection and the relative events within
the service provider for communication in the year of 2018.
The upcoming 5G technology and the relative network carry the potential capability
to explode the existing vertical industries having enabled the creation of multiple array of
newer services that also have the primary requirement of different levels of security and
12 Kachhavay, Meenal G., and Ajay P. Thakare. "5G technology-evolution and revolution." International
Journal of Computer Science and Mobile Computing 3.3 (2014): 1080-1087.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CHALLENGES IN 5G SECURITY
safeguarding13. In regards to this, some of the challenges in security that share a direct
association with the 5G technology are,
i) Autonomous vehicles- the threat that has a relation with the cyber-attacks that
occur within the automotive is expected to have a significant rise in the
autonomous vehicles in a wider aspect. As a safety procedure against this event
taking place, the National Highway Traffic Safety Administration is potentially
upgraded to take a step towards employing an approach for cyber security that
consists of multiple layers in regards to the technologies that provision the drivers
with required amount of assistance14.
ii) Healthcare- within the field of healthcare, the capabilities associated with 5G
provisions with a helping hand towards a faster transferring of large-sized files of
patients, remote surgery as well as monitoring over the patients with the use of
IoT devices among the other existing advances within the same field. In regards to
this, it can be stated that those existing advances within the field of healthcare as a
part of the 5G technology are in need of a greater as well as a stronger amount of
security15. Creation of risks that have the primary inclusion of medical identity
theft, medical management of data as well as invasion of the privacy that has a
relation to the health of an individual. Reports have stated that, in the year of
2018, the healthcare sector had been the target to 48% of the total breaches that
had occurred and caused by the cyber world. This also makes an addition to the
fact that potential growth of IoT will provisionally make the dealing and the
13 Hossain, Saddam. "5G wireless communication systems." American Journal of Engineering Research (AJER)
2.10 (2013): 344-353.
14 Parkvall, Stefan, et al. "NR: The new 5G radio access technology." IEEE Communications Standards
Magazine 1.4 (2017): 24-30.
15 Andrews, Jeffrey G., et al. "What will 5G be?." IEEE Journal on selected areas in communications 32.6
(2014): 1065-1082.
safeguarding13. In regards to this, some of the challenges in security that share a direct
association with the 5G technology are,
i) Autonomous vehicles- the threat that has a relation with the cyber-attacks that
occur within the automotive is expected to have a significant rise in the
autonomous vehicles in a wider aspect. As a safety procedure against this event
taking place, the National Highway Traffic Safety Administration is potentially
upgraded to take a step towards employing an approach for cyber security that
consists of multiple layers in regards to the technologies that provision the drivers
with required amount of assistance14.
ii) Healthcare- within the field of healthcare, the capabilities associated with 5G
provisions with a helping hand towards a faster transferring of large-sized files of
patients, remote surgery as well as monitoring over the patients with the use of
IoT devices among the other existing advances within the same field. In regards to
this, it can be stated that those existing advances within the field of healthcare as a
part of the 5G technology are in need of a greater as well as a stronger amount of
security15. Creation of risks that have the primary inclusion of medical identity
theft, medical management of data as well as invasion of the privacy that has a
relation to the health of an individual. Reports have stated that, in the year of
2018, the healthcare sector had been the target to 48% of the total breaches that
had occurred and caused by the cyber world. This also makes an addition to the
fact that potential growth of IoT will provisionally make the dealing and the
13 Hossain, Saddam. "5G wireless communication systems." American Journal of Engineering Research (AJER)
2.10 (2013): 344-353.
14 Parkvall, Stefan, et al. "NR: The new 5G radio access technology." IEEE Communications Standards
Magazine 1.4 (2017): 24-30.
15 Andrews, Jeffrey G., et al. "What will 5G be?." IEEE Journal on selected areas in communications 32.6
(2014): 1065-1082.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10CHALLENGES IN 5G SECURITY
occurrences of the risks associated to cyber security more challenging as the 5G
network industry tries and makes way into the lives of human16.
iii) Smart homes- such smart homes that have been enabled by the technology off 5G
will specifically require to be safeguarded with greater as well as secure methods
of authentication like that of biometric identification, face and voice recognition
as well as the fingerprint technology that are installed into the door locks for
preventing the entry of trespassers17. In the year of 2019, a collective set of
breaches upon the Amazon’s camera for home setting had attracted the hackers
who had been able to get through to the cameras that had been installed within the
user’s home as well as the porches present on the front side.
In regards to such challenges that are associated with the increased usage of 5G
technology, the IoT devices and the relative sensors are in requirement of a more complex
authentication for the prevention of unauthorized access.
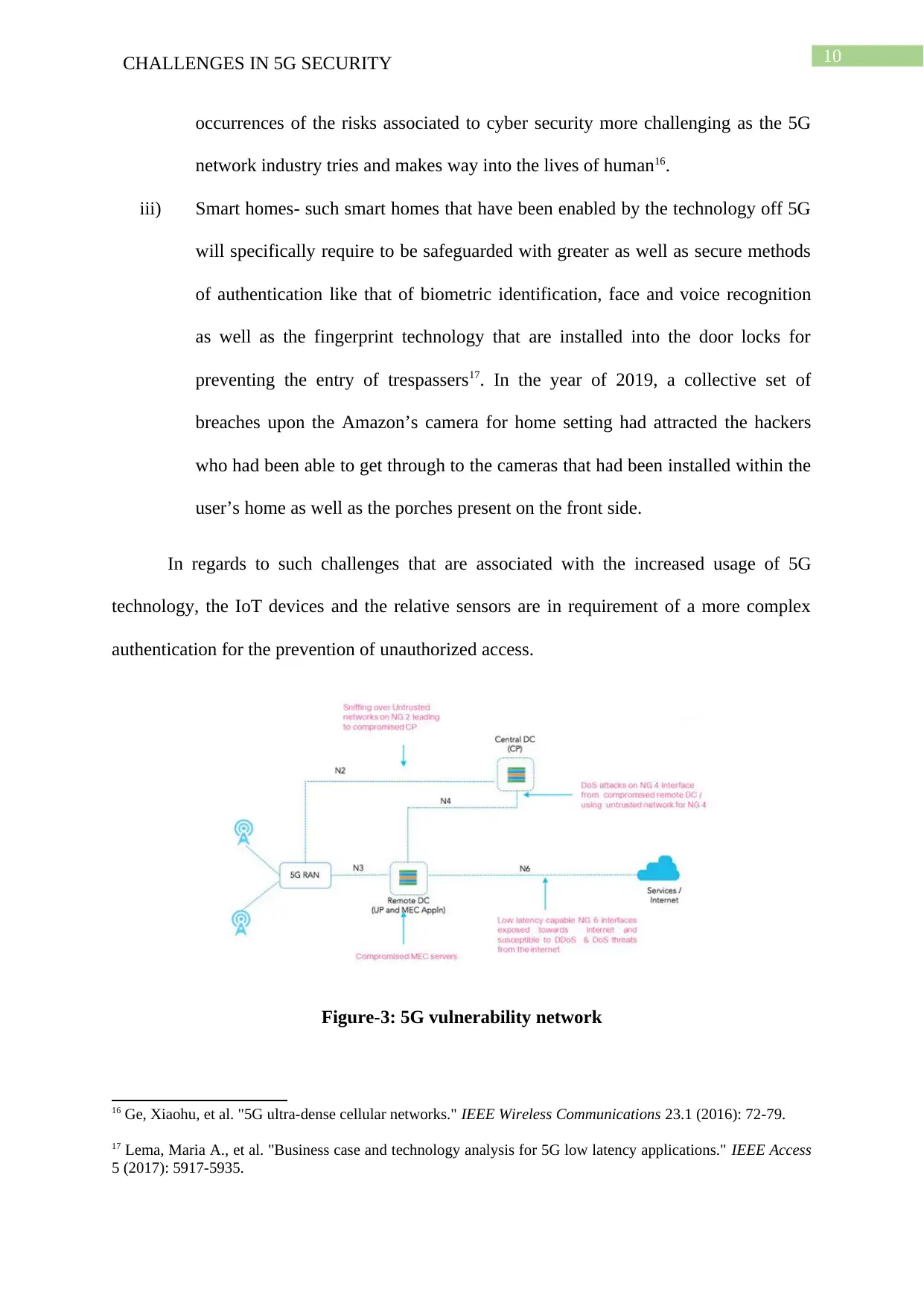
Figure-3: 5G vulnerability network
16 Ge, Xiaohu, et al. "5G ultra-dense cellular networks." IEEE Wireless Communications 23.1 (2016): 72-79.
17 Lema, Maria A., et al. "Business case and technology analysis for 5G low latency applications." IEEE Access
5 (2017): 5917-5935.
occurrences of the risks associated to cyber security more challenging as the 5G
network industry tries and makes way into the lives of human16.
iii) Smart homes- such smart homes that have been enabled by the technology off 5G
will specifically require to be safeguarded with greater as well as secure methods
of authentication like that of biometric identification, face and voice recognition
as well as the fingerprint technology that are installed into the door locks for
preventing the entry of trespassers17. In the year of 2019, a collective set of
breaches upon the Amazon’s camera for home setting had attracted the hackers
who had been able to get through to the cameras that had been installed within the
user’s home as well as the porches present on the front side.
In regards to such challenges that are associated with the increased usage of 5G
technology, the IoT devices and the relative sensors are in requirement of a more complex
authentication for the prevention of unauthorized access.
Figure-3: 5G vulnerability network
16 Ge, Xiaohu, et al. "5G ultra-dense cellular networks." IEEE Wireless Communications 23.1 (2016): 72-79.
17 Lema, Maria A., et al. "Business case and technology analysis for 5G low latency applications." IEEE Access
5 (2017): 5917-5935.

11CHALLENGES IN 5G SECURITY
With the technologies of cloud virtualization such as the likes of Software-defined
Networking (SDN) as well as the Network Functions Virtualization (NFV) have been waiting
for the 5G networks. While, these functionalities also come along with the concerns of
security and safety. Since the presence of flexible, programmable nature as well as the open
nature of the SDN and the NFV that come forward with newer security threats18. For instance,
the network element belonging to a SDN such as the interfaces of management that can be
potentially used for the attacking of the SDN controller or might as well be the management
system and potentially bring down the proper working system as well.
Figure-4: 5G security network
In relation to the security, challenges and the relative concerns regarding the
safeguarding the 5G network the following five components of the network have been placed
forward to tackle such concerns of 5G security19. These are,
Presence of a secured edge- this puts forward the idea of ensuring the real-time
detection capability that shall be present at the edge. The respective network must
look for as well as stop the potential breaches before they potentially get successful to
reach the core of the network.
18 ZHANG, Ping, Y. Z. Tao, and Zhi ZHANG. "Survey of several key technologies for 5G." Journal on
Communications 37.7 (2016): 15-29.
19 Guey, Jiann-Ching, et al. "On 5G radio access architecture and technology [industry perspectives]." IEEE
Wireless Communications 22.5 (2015): 2-5.
With the technologies of cloud virtualization such as the likes of Software-defined
Networking (SDN) as well as the Network Functions Virtualization (NFV) have been waiting
for the 5G networks. While, these functionalities also come along with the concerns of
security and safety. Since the presence of flexible, programmable nature as well as the open
nature of the SDN and the NFV that come forward with newer security threats18. For instance,
the network element belonging to a SDN such as the interfaces of management that can be
potentially used for the attacking of the SDN controller or might as well be the management
system and potentially bring down the proper working system as well.
Figure-4: 5G security network
In relation to the security, challenges and the relative concerns regarding the
safeguarding the 5G network the following five components of the network have been placed
forward to tackle such concerns of 5G security19. These are,
Presence of a secured edge- this puts forward the idea of ensuring the real-time
detection capability that shall be present at the edge. The respective network must
look for as well as stop the potential breaches before they potentially get successful to
reach the core of the network.
18 ZHANG, Ping, Y. Z. Tao, and Zhi ZHANG. "Survey of several key technologies for 5G." Journal on
Communications 37.7 (2016): 15-29.
19 Guey, Jiann-Ching, et al. "On 5G radio access architecture and technology [industry perspectives]." IEEE
Wireless Communications 22.5 (2015): 2-5.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





