Challenges of Cyber Security on Business Performances
VerifiedAdded on 2021/06/18
|18
|3599
|35
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Crime Attack 1
Business Research
Challenges of Cyber Security on Business performances. A case study of medium
and large enterprises in Pakistan
Business Research
Challenges of Cyber Security on Business performances. A case study of medium
and large enterprises in Pakistan
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Crime Attack 2
Contents
Introduction......................................................................................................................................3
Project objective..............................................................................................................................4
Project scope....................................................................................................................................5
Literature review..............................................................................................................................6
Conclusion.....................................................................................................................................13
References......................................................................................................................................14
Appendix........................................................................................................................................16
Contents
Introduction......................................................................................................................................3
Project objective..............................................................................................................................4
Project scope....................................................................................................................................5
Literature review..............................................................................................................................6
Conclusion.....................................................................................................................................13
References......................................................................................................................................14
Appendix........................................................................................................................................16

Crime Attack 3
Introduction
There are various modern communities have reliant on cyberspace that provides valuable and
essential services for the functionalities of the environment and the human life along with the
challenges and threats. The field of cyber security focuses on preventing databases, networks and
programs from unlawful access or destruction. It is essential for this to have adequate knowledge
about the limitations, vulnerabilities and stability of ICT (Awan and Memon, 2016). The world
has changed rapidly due to the amendment in technology; this might need innovative and
effective involvement among developing countries at the different level of development. It has
become necessary for the developing countries to pay attention towards the cyber security issues.
Pakistan is one of them that facing challenges regarding cyber security. This research contributes
a clear overview of cyber security threats which may impact the business performance of small
and large enterprises of Pakistan. The project objective will be defined in a concise manner.
Furthermore, it concludes by providing some recommendations to the makers of cyber security
policy which can be implemented by the country to prevent the cyber boundaries.
Introduction
There are various modern communities have reliant on cyberspace that provides valuable and
essential services for the functionalities of the environment and the human life along with the
challenges and threats. The field of cyber security focuses on preventing databases, networks and
programs from unlawful access or destruction. It is essential for this to have adequate knowledge
about the limitations, vulnerabilities and stability of ICT (Awan and Memon, 2016). The world
has changed rapidly due to the amendment in technology; this might need innovative and
effective involvement among developing countries at the different level of development. It has
become necessary for the developing countries to pay attention towards the cyber security issues.
Pakistan is one of them that facing challenges regarding cyber security. This research contributes
a clear overview of cyber security threats which may impact the business performance of small
and large enterprises of Pakistan. The project objective will be defined in a concise manner.
Furthermore, it concludes by providing some recommendations to the makers of cyber security
policy which can be implemented by the country to prevent the cyber boundaries.

Crime Attack 4
Project objective
The project objective of the research is to find out the various factors which may influence the
cyber security of Pakistan’s small and large enterprises. The objectives are defined below:
To explore the essential services of small and large enterprises.
To evaluate the current threats and attacks in Pakistan by considering infector, infection
and infected by.
To investigate the cyber threat policies and cyber protection policies in Pakistan.
Project objective
The project objective of the research is to find out the various factors which may influence the
cyber security of Pakistan’s small and large enterprises. The objectives are defined below:
To explore the essential services of small and large enterprises.
To evaluate the current threats and attacks in Pakistan by considering infector, infection
and infected by.
To investigate the cyber threat policies and cyber protection policies in Pakistan.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Crime Attack 5
Project scope
The project scope is wide as it covers various factors regarding cyber security challenges and
policies in small and large enterprises of Pakistan. The project is firmed through various regular
authorities in the enterprises as it aims to present the specific knowledge about the cyber security
challenges and policies. The readers will get sufficient knowledge about the cyber security issues
in developing country and about the actions which have taken by the government of Pakistan to
prevent these concerns.
Project scope
The project scope is wide as it covers various factors regarding cyber security challenges and
policies in small and large enterprises of Pakistan. The project is firmed through various regular
authorities in the enterprises as it aims to present the specific knowledge about the cyber security
challenges and policies. The readers will get sufficient knowledge about the cyber security issues
in developing country and about the actions which have taken by the government of Pakistan to
prevent these concerns.

Crime Attack 6
Literature review
The governments are in the way of revolutions of their key services to online services because of
increasing in the implementation of Internet-based services. There are number of firms that use
internet-based infrastructure to give their services to the customers because it helps them to attain
the objectives of the organization in an adequate manner. The use of internet-based services at
government level has enhanced the chances of damage systems security not from internal
sources but also from external sources. According to Reddy and Reddy, (2014), it has been found
that cyber terrorists are able to make availability, integrity or confidentiality attack on different
cyber services. The flexibility, security and consistency of the cyber assets of nation and services
of government are a huge challenge for not only organizations but also for the growing number
of serious attacks on confidential information. It is considered the most serious national security
and economic threats (Graham, Olson and Howard, 2016). As per the New York Times Report
malware is the hazardous software that hits Atomic Organization of Iran and nuclear facilities
before evading and causing chaos on the public web. It has been found from the report of
phishing campaign (APWG, 2013), has focused a huge variety of recipients at the time of
employing the Dyre/Dyreza banking malware, which objects sensitive user account credentials
and provides the captured data to malicious actors. It has been analyzed from the report that the
Dyreza banking malware brings new challenge for developed countries which mostly targets
senders, themes, payload and attachments. According to Elmaghraby and Losavio, (2014),
medium and large enterprises have a significant role in the development of the industrial,
economic and social of a country. These enterprises play an integral role in the growth of
technological innovation in Pakistan. Large and medium enterprises are one of the major sources
Literature review
The governments are in the way of revolutions of their key services to online services because of
increasing in the implementation of Internet-based services. There are number of firms that use
internet-based infrastructure to give their services to the customers because it helps them to attain
the objectives of the organization in an adequate manner. The use of internet-based services at
government level has enhanced the chances of damage systems security not from internal
sources but also from external sources. According to Reddy and Reddy, (2014), it has been found
that cyber terrorists are able to make availability, integrity or confidentiality attack on different
cyber services. The flexibility, security and consistency of the cyber assets of nation and services
of government are a huge challenge for not only organizations but also for the growing number
of serious attacks on confidential information. It is considered the most serious national security
and economic threats (Graham, Olson and Howard, 2016). As per the New York Times Report
malware is the hazardous software that hits Atomic Organization of Iran and nuclear facilities
before evading and causing chaos on the public web. It has been found from the report of
phishing campaign (APWG, 2013), has focused a huge variety of recipients at the time of
employing the Dyre/Dyreza banking malware, which objects sensitive user account credentials
and provides the captured data to malicious actors. It has been analyzed from the report that the
Dyreza banking malware brings new challenge for developed countries which mostly targets
senders, themes, payload and attachments. According to Elmaghraby and Losavio, (2014),
medium and large enterprises have a significant role in the development of the industrial,
economic and social of a country. These enterprises play an integral role in the growth of
technological innovation in Pakistan. Large and medium enterprises are one of the major sources

Crime Attack 7
to decrease poverty and enlarge economic renewable and social development (Gupta, Agrawal
and Yamaguchi, 2016).
There are many countries that deploy online services and one of them is Pakistan, in which most
of the organizations whether medium or large are deploying services of information technology
into their infrastructure along with the upper level of authorities are interesting to organize these
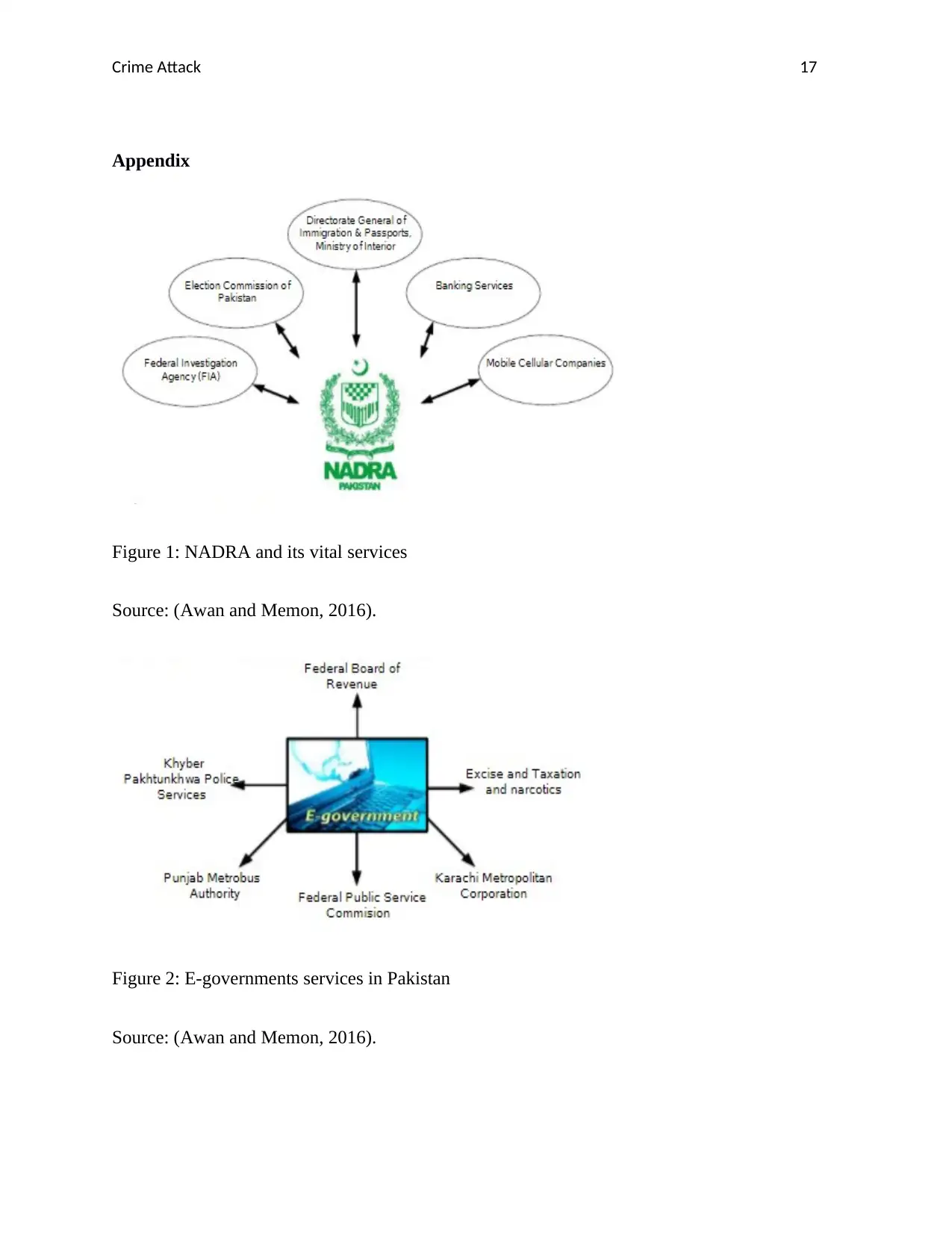
kinds of latest technology into their infrastructures. As per Awan and Memon, (2016), NADRA
(National Database and Registration Authority) is ID data base of Pakistan which is centralized.
It has been sharing in passport offices, among banks, mobile networks, FBI (Federal Bureau of
Investigation) and Election Commission Departments and many more. It has been found that
NADRA is the only enterprise which has the responsibility of keeping information regarding
population. As per the report (Threat Track Security 2014), NADRA is considered as the top
most organization all over the world due to the usage of state of the art technologies for its
services. It has been found that at current time, the countries of Europe are using SCAP (Security
Content Automation Protocol) algorithm for National Vulnerability database which helps in data
automation of security management, vulnerability management and compliance (APWG 2013).
It has been observed that hackers are endeavoring to hack the sensitive information about the
country to hack the confidential information. NADRA might be targeted for cyber attackers to
increase the damage in its vital services and utilize them for illegal objectives.
According to Jang-Jaccard and Nepal, (2014), the access usage of social media sites is being the
cause for vulnerability of people towards the cybercrimes. It has been found that more than 3
billion users are active on social media sites. Pakistan’s government has initiated e-government
component for modernization which facilitates to develop the on-going stress by developing their
effectiveness and modifying to the pressure of latest society of information (Ben-Asher and
to decrease poverty and enlarge economic renewable and social development (Gupta, Agrawal
and Yamaguchi, 2016).
There are many countries that deploy online services and one of them is Pakistan, in which most
of the organizations whether medium or large are deploying services of information technology
into their infrastructure along with the upper level of authorities are interesting to organize these
kinds of latest technology into their infrastructures. As per Awan and Memon, (2016), NADRA
(National Database and Registration Authority) is ID data base of Pakistan which is centralized.
It has been sharing in passport offices, among banks, mobile networks, FBI (Federal Bureau of
Investigation) and Election Commission Departments and many more. It has been found that
NADRA is the only enterprise which has the responsibility of keeping information regarding
population. As per the report (Threat Track Security 2014), NADRA is considered as the top
most organization all over the world due to the usage of state of the art technologies for its
services. It has been found that at current time, the countries of Europe are using SCAP (Security
Content Automation Protocol) algorithm for National Vulnerability database which helps in data
automation of security management, vulnerability management and compliance (APWG 2013).
It has been observed that hackers are endeavoring to hack the sensitive information about the
country to hack the confidential information. NADRA might be targeted for cyber attackers to
increase the damage in its vital services and utilize them for illegal objectives.
According to Jang-Jaccard and Nepal, (2014), the access usage of social media sites is being the
cause for vulnerability of people towards the cybercrimes. It has been found that more than 3
billion users are active on social media sites. Pakistan’s government has initiated e-government
component for modernization which facilitates to develop the on-going stress by developing their
effectiveness and modifying to the pressure of latest society of information (Ben-Asher and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Crime Attack 8
Gonzalez, 2015). Government organizations which are considered as the large organization of
Pakistan are enabled due to effectiveness of e-government that provides rapid and effective
services to their constituents. There are various business and financial services such as Pakistan
stock exchanges, mobile banking, and online banking transactions, various financial services and
mobile and postal money services which are being used by medium and large enterprises in
Pakistan. It has been analyzed that capital markets are selling and purchasing the financial
markets for investment purpose that facilitates many organizations and government to empower
their amount by preventing them from various frauds (Sadeghi, Wachsmann and Waidner, 2015).
The literature review suggests that the cyber security issues can decrease the business
performance as it develops the fear in the mind of an employee of losing confidential data. There
are various threats of cyber attacks that hamper the goodwill of the enterprises whether it is large
or medium. The DDoS or Distributed Denial of Service attack is biggest challenge for thee
enterprises as it prevents various functions that perform at an efficient level. Generally, hackers
have a tendency to attack the single system and then utilize such process to attain access to
others systems that are linked to same server. Zargar, Joshi and Tipper (2013), stated that the
servers are not made for handling high volume of traffic that outcome in their failure along with
their security measures. In case of vulnerability of server, hackers take benefits and attack on
server to attain the confidential information. It has been found that BBC, Rio Olympics, DYN
are the illustrations that faced the DDoS attacks (Bisson, 2016).
The business performance of the company is vital for the organization as it helps to increase the
revenues of thee enterprises. There are various impacts of cyber security challenges on the
business performance such as the economic cost of cyber attack, reputational damage and legal
consequences of cyber breach. It has been stated by Lohrke, Frownfelter-Lohrke and Ketchen Jr,
Gonzalez, 2015). Government organizations which are considered as the large organization of
Pakistan are enabled due to effectiveness of e-government that provides rapid and effective
services to their constituents. There are various business and financial services such as Pakistan
stock exchanges, mobile banking, and online banking transactions, various financial services and
mobile and postal money services which are being used by medium and large enterprises in
Pakistan. It has been analyzed that capital markets are selling and purchasing the financial
markets for investment purpose that facilitates many organizations and government to empower
their amount by preventing them from various frauds (Sadeghi, Wachsmann and Waidner, 2015).
The literature review suggests that the cyber security issues can decrease the business
performance as it develops the fear in the mind of an employee of losing confidential data. There
are various threats of cyber attacks that hamper the goodwill of the enterprises whether it is large
or medium. The DDoS or Distributed Denial of Service attack is biggest challenge for thee
enterprises as it prevents various functions that perform at an efficient level. Generally, hackers
have a tendency to attack the single system and then utilize such process to attain access to
others systems that are linked to same server. Zargar, Joshi and Tipper (2013), stated that the
servers are not made for handling high volume of traffic that outcome in their failure along with
their security measures. In case of vulnerability of server, hackers take benefits and attack on
server to attain the confidential information. It has been found that BBC, Rio Olympics, DYN
are the illustrations that faced the DDoS attacks (Bisson, 2016).
The business performance of the company is vital for the organization as it helps to increase the
revenues of thee enterprises. There are various impacts of cyber security challenges on the
business performance such as the economic cost of cyber attack, reputational damage and legal
consequences of cyber breach. It has been stated by Lohrke, Frownfelter-Lohrke and Ketchen Jr,

Crime Attack 9
(2016), that cyber attack can be the reason of financial loss due to confidential data and loss of
business contract that may lead the medium as well as large enterprises into adverse situation.
Trust is a vital element for maintaining the customer relationship. Cyber attacks can spoil the
image of the company in the point of view of outsiders as well as insiders which bring the issues
in the form of loss of customers, reduction in profits and loss of sales (Gai, Qiu, Sun and Zhao,
2016). The effect of reputational damage may affect the relationship with suppliers and other
third parties. Personal data should be managed by company in an effective manner to maintain
the relationship with customers as well as employees for the long period (Kim, Shin and Lee,
2009). Data protection and privacy laws should be implemented in the enterprises and if this data
is accidentally compromised, the company has to suffer with fined and regulatory sanctions
(Rasool, 2015).
Pakistan is developing country where execution of cyber services is under development so it is
vital for the enterprises of the country to secure confidential information on prior basis. Social
websites provide the comfort facilities to many users where user feel free to communicate with
each other in an effective manner but cyber criminals are targeting these social media sites for
the purpose of stealing personal information of the user involving locations. It has been found
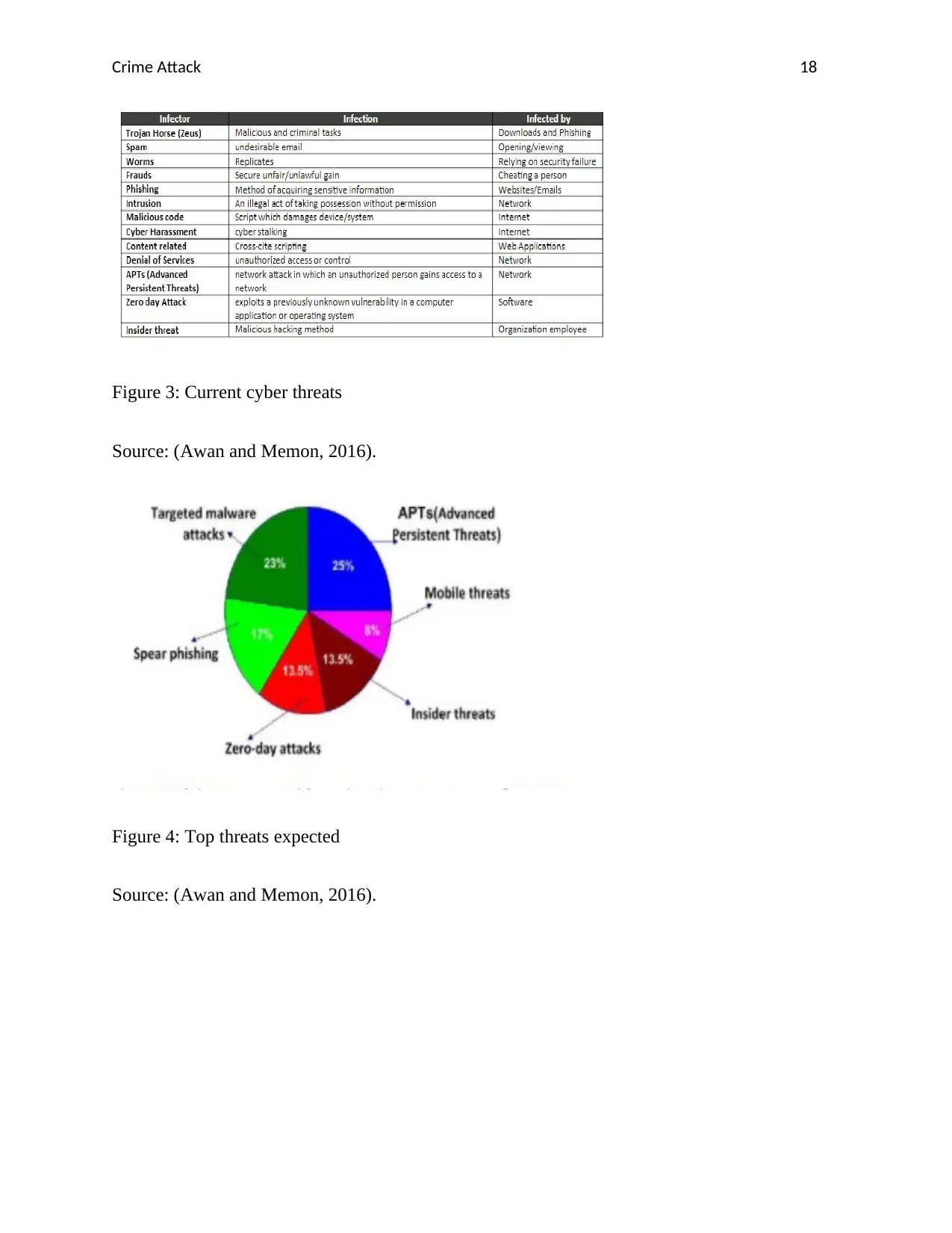
from the journal article of Awan and Memon, (2016), that the current cyber threats are Trojan
Horse, worms, fraud, phishing, Malicious code, cyber harassment, content relates, denial of
serves, zero day attack and insider threat. In the context of cyber threats and policies in Pakistan,
it has been analyzed that after thieving of confidential information by US National Security
Agency (NSA), it has been recommended by the National Telecom & Information Technology
Security Board (NTISB) for preventing government, enterprises and their services from various
kinds of cyber attacks. It has been found from the report of APWG, (2013), that the cyber crimes
(2016), that cyber attack can be the reason of financial loss due to confidential data and loss of
business contract that may lead the medium as well as large enterprises into adverse situation.
Trust is a vital element for maintaining the customer relationship. Cyber attacks can spoil the
image of the company in the point of view of outsiders as well as insiders which bring the issues
in the form of loss of customers, reduction in profits and loss of sales (Gai, Qiu, Sun and Zhao,
2016). The effect of reputational damage may affect the relationship with suppliers and other
third parties. Personal data should be managed by company in an effective manner to maintain
the relationship with customers as well as employees for the long period (Kim, Shin and Lee,
2009). Data protection and privacy laws should be implemented in the enterprises and if this data
is accidentally compromised, the company has to suffer with fined and regulatory sanctions
(Rasool, 2015).
Pakistan is developing country where execution of cyber services is under development so it is
vital for the enterprises of the country to secure confidential information on prior basis. Social
websites provide the comfort facilities to many users where user feel free to communicate with
each other in an effective manner but cyber criminals are targeting these social media sites for
the purpose of stealing personal information of the user involving locations. It has been found
from the journal article of Awan and Memon, (2016), that the current cyber threats are Trojan
Horse, worms, fraud, phishing, Malicious code, cyber harassment, content relates, denial of
serves, zero day attack and insider threat. In the context of cyber threats and policies in Pakistan,
it has been analyzed that after thieving of confidential information by US National Security
Agency (NSA), it has been recommended by the National Telecom & Information Technology
Security Board (NTISB) for preventing government, enterprises and their services from various
kinds of cyber attacks. It has been found from the report of APWG, (2013), that the cyber crimes

Crime Attack 10
started to attack on various websites of Pakistan which entails number of confidential
information regarding security forces and the federal government. The business performance can
be affected due to several reasons such as political extremism, ethnic associations, extremisms,
unemployment and terrorism.
It has been from the articles of Lau, Xia and Ye, (2014), that Pakistan is most at risk of malicious
software cyber attacks worldwide. There are various kinds of malicious software that make
impossible for cyber security to be 100 percent efficient all the time. Cloud-based computing is
one of the examples which are utilized by many organizations in Pakistan. Whilst, it is most
effective and safe data hub but still, it has a potential risk of cyber attack (He, Maple, Watson,
Tiwari, Mehnen,Jin and Gabrys, 2016). However, there is a majority of companies in Pakistan
that face challenges of cyber attacks which can be reduced by keeping strengthen password
management to make sure that focused phishing attacks of third parties should be avoided. The
employees and customers are afraid to provide information about personal data to the companies
whether it is small or large due to hacktivism.
It has been analyzed that Pakistan has no policies and laws regarding cyber attacks that might
widely deal with the growing threat if cyber crimes. There is a lot of inadequacy in available
crime justice legal framework which is ill-equipped to handle the concerns of cyber attacks in a
sophisticated manner. This new age is being the cause of damage existing crimes while
conducted with the utilization of internet services. These provided opportunity to different
attackers of cyber crime to bring new kind of criminals and cyber crime like interference with
data and ICT system, hacking by adopting illegal access, frauds, illegal interception made by
civilians and utilization of malicious code viruses to the detective on ICT systems (Choo, 2011).
The existing legislation of Pakistan is not able to punish or entertain these issues in a significant
started to attack on various websites of Pakistan which entails number of confidential
information regarding security forces and the federal government. The business performance can
be affected due to several reasons such as political extremism, ethnic associations, extremisms,
unemployment and terrorism.
It has been from the articles of Lau, Xia and Ye, (2014), that Pakistan is most at risk of malicious
software cyber attacks worldwide. There are various kinds of malicious software that make
impossible for cyber security to be 100 percent efficient all the time. Cloud-based computing is
one of the examples which are utilized by many organizations in Pakistan. Whilst, it is most
effective and safe data hub but still, it has a potential risk of cyber attack (He, Maple, Watson,
Tiwari, Mehnen,Jin and Gabrys, 2016). However, there is a majority of companies in Pakistan
that face challenges of cyber attacks which can be reduced by keeping strengthen password
management to make sure that focused phishing attacks of third parties should be avoided. The
employees and customers are afraid to provide information about personal data to the companies
whether it is small or large due to hacktivism.
It has been analyzed that Pakistan has no policies and laws regarding cyber attacks that might
widely deal with the growing threat if cyber crimes. There is a lot of inadequacy in available
crime justice legal framework which is ill-equipped to handle the concerns of cyber attacks in a
sophisticated manner. This new age is being the cause of damage existing crimes while
conducted with the utilization of internet services. These provided opportunity to different
attackers of cyber crime to bring new kind of criminals and cyber crime like interference with
data and ICT system, hacking by adopting illegal access, frauds, illegal interception made by
civilians and utilization of malicious code viruses to the detective on ICT systems (Choo, 2011).
The existing legislation of Pakistan is not able to punish or entertain these issues in a significant
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Crime Attack 11
manner which may bring issues to the various enterprises of Pakistan. It is required for the
government of Pakistan to develop a comprehensively legal framework in against of unique
crimes. It has been suggested by Tanzanian delegation that Pakistan needs to make Cyber Crime
Unit (CCU) to handle cybercrimes and it requires enhancing an effective and liable legislation
and creating Computer Emergency Response Team (CERT) to help the execution.
It has been researched that Tanzania has lost approx $6 million due to non-care about the cyber
crimes which forced them to enhance CCUs and CERTs. The worthies of delegation described in
the discussion that the big amount of $445 billion is misplaced annually due to cyber crimes and
electronic thefts. Additionally, it has been observed that 800 million recorded data are hacked in
the developing countries. In this relation, Pakistan needs to describe the various policies
regarding controlling the crimes as well as the developed nations (APWG 2013). It has been
analyzed that Pakistan’s medium and large enterprises ar facing challenges in the context of
cyber crimes such as financial crimes, sale of illegal articles, email spoofing, forgery, trojan
attacks, internet time theft, password cracking, buffer overflow, worm attacks and many more.
On December 31, 2007, the president of Pakistan Pervej Musharraf broadcasted a law called )
2007 (Imam, 2012). It was the best gift for the nation because the cyber crime rate was increased
day by day. However, this bill was not passed by the Pakistan Parliament which is still pending.
It might be problematic that there are many systems in Pakistan which have become
computerized but no legal implications are taken place yet. There is no procedure to check the
things and no policies of punishment for criminals. Cellular companies of Pakistan are facing the
issues of cyber crimes, the public of nation is looted through email hackers and ‘African Lottery’
scams many people.
manner which may bring issues to the various enterprises of Pakistan. It is required for the
government of Pakistan to develop a comprehensively legal framework in against of unique
crimes. It has been suggested by Tanzanian delegation that Pakistan needs to make Cyber Crime
Unit (CCU) to handle cybercrimes and it requires enhancing an effective and liable legislation
and creating Computer Emergency Response Team (CERT) to help the execution.
It has been researched that Tanzania has lost approx $6 million due to non-care about the cyber
crimes which forced them to enhance CCUs and CERTs. The worthies of delegation described in
the discussion that the big amount of $445 billion is misplaced annually due to cyber crimes and
electronic thefts. Additionally, it has been observed that 800 million recorded data are hacked in
the developing countries. In this relation, Pakistan needs to describe the various policies
regarding controlling the crimes as well as the developed nations (APWG 2013). It has been
analyzed that Pakistan’s medium and large enterprises ar facing challenges in the context of
cyber crimes such as financial crimes, sale of illegal articles, email spoofing, forgery, trojan
attacks, internet time theft, password cracking, buffer overflow, worm attacks and many more.
On December 31, 2007, the president of Pakistan Pervej Musharraf broadcasted a law called )
2007 (Imam, 2012). It was the best gift for the nation because the cyber crime rate was increased
day by day. However, this bill was not passed by the Pakistan Parliament which is still pending.
It might be problematic that there are many systems in Pakistan which have become
computerized but no legal implications are taken place yet. There is no procedure to check the
things and no policies of punishment for criminals. Cellular companies of Pakistan are facing the
issues of cyber crimes, the public of nation is looted through email hackers and ‘African Lottery’
scams many people.

Crime Attack 12
It has been found that the banking sector of Pakistan is increasing its dependence on cyber space
which increases the unsafe environment among people and their trust is losing on the banking
sector. It is vital for the different sectors of Pakistan to ensure their employees and customers
that their information is safe at the workplace (Rasool, 2015). Without the support of
government’s policies, it would not be possible for the enterprises of Pakistan to increase the
business performance. The economic stability and revenues of the company can be increased by
implementing the various policies regarding cyber crimes in Pakistan (Yan, Qian, Sharif and
Tipper, 2012).
It has been found that the banking sector of Pakistan is increasing its dependence on cyber space
which increases the unsafe environment among people and their trust is losing on the banking
sector. It is vital for the different sectors of Pakistan to ensure their employees and customers
that their information is safe at the workplace (Rasool, 2015). Without the support of
government’s policies, it would not be possible for the enterprises of Pakistan to increase the
business performance. The economic stability and revenues of the company can be increased by
implementing the various policies regarding cyber crimes in Pakistan (Yan, Qian, Sharif and
Tipper, 2012).

Crime Attack 13
Conclusion
From above discussion, it can be concluded that cyber crimes can decrease the performance of
the business and may lead the organizations into the adverse situation. With the support of
various authors, the discussion has been made on cyber security challenges in Pakistan. There are
many medium and large enterprises such as stock exchanges, mobile banking, financial
organizations and government sectors which can be influenced by Cyber attacks and decrease the
performance of the companies. It has been analyzed that there is no law and legislation regarding
cyber security attack in Pakistan which is threat in itself. It is recommended to the government of
Pakistan to implement significant policies regarding these concerns so that the business
performance of the company can be increased.
Conclusion
From above discussion, it can be concluded that cyber crimes can decrease the performance of
the business and may lead the organizations into the adverse situation. With the support of
various authors, the discussion has been made on cyber security challenges in Pakistan. There are
many medium and large enterprises such as stock exchanges, mobile banking, financial
organizations and government sectors which can be influenced by Cyber attacks and decrease the
performance of the companies. It has been analyzed that there is no law and legislation regarding
cyber security attack in Pakistan which is threat in itself. It is recommended to the government of
Pakistan to implement significant policies regarding these concerns so that the business
performance of the company can be increased.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Crime Attack 14
References
APWG, 2013. Phishing Trends Report for Q2 2013, APWG. Available at:
https://www.antiphishing.org/resources/apwg-reports/. Accessed on 29th April, 2018.
Awan, J. and Memon, S., 2016, January. Threats of cyber security and challenges for Pakistan.
In International Conference on Cyber Warfare and Security (p. 425). Academic Conferences
International Limited.
Ben-Asher, N. and Gonzalez, C., 2015. Effects of cyber security knowledge on attack
detection. Computers in Human Behavior, 48, pp.51-61.
Bisson, D., 2016. The 5 Most Significant DDoS Attacks of 2016. Available at:
https://www.tripwire.com/state-of-security/security-data-protection/cyber-security/5-significant-
ddos-attacks-2016/ Accessed on 28th April, 2018.
Choo, K.K.R., 2011. The cyber threat landscape: Challenges and future research
directions. Computers & Security, 30(8), pp.719-731.
Elmaghraby, A.S., and Losavio, M.M., 2014. Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of Advanced Research, vol. 5, no. 4, pp. 491-497.
Gai, K., Qiu, M., Sun, X. and Zhao, H., 2016, December. Security and privacy issues: A survey
on FinTech. In International Conference on Smart Computing and Communication (pp. 236-
247). Springer, Cham.
Graham, J., Olson, R. and Howard, R. eds., 2016. Cyber security essentials. CRC Press.
References
APWG, 2013. Phishing Trends Report for Q2 2013, APWG. Available at:
https://www.antiphishing.org/resources/apwg-reports/. Accessed on 29th April, 2018.
Awan, J. and Memon, S., 2016, January. Threats of cyber security and challenges for Pakistan.
In International Conference on Cyber Warfare and Security (p. 425). Academic Conferences
International Limited.
Ben-Asher, N. and Gonzalez, C., 2015. Effects of cyber security knowledge on attack
detection. Computers in Human Behavior, 48, pp.51-61.
Bisson, D., 2016. The 5 Most Significant DDoS Attacks of 2016. Available at:
https://www.tripwire.com/state-of-security/security-data-protection/cyber-security/5-significant-
ddos-attacks-2016/ Accessed on 28th April, 2018.
Choo, K.K.R., 2011. The cyber threat landscape: Challenges and future research
directions. Computers & Security, 30(8), pp.719-731.
Elmaghraby, A.S., and Losavio, M.M., 2014. Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of Advanced Research, vol. 5, no. 4, pp. 491-497.
Gai, K., Qiu, M., Sun, X. and Zhao, H., 2016, December. Security and privacy issues: A survey
on FinTech. In International Conference on Smart Computing and Communication (pp. 236-
247). Springer, Cham.
Graham, J., Olson, R. and Howard, R. eds., 2016. Cyber security essentials. CRC Press.

Crime Attack 15
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds., 2016. Handbook of research on modern
cryptographic solutions for computer and cyber security. IGI Global.
He, H., Maple, C., Watson, T., Tiwari, A., Mehnen, J., Jin, Y. and Gabrys, B., 2016, July. The
security challenges in the IoT enabled cyber-physical systems and opportunities for evolutionary
computing & other computational intelligence. In Evolutionary Computation (CEC), 2016 IEEE
Congress on(pp. 1015-1021). IEEE.
Imam, A. L., 2012. Cyber crime in Pakistan: Serious threat but no laws!. Available at: . Accessed
on: 28th April, 2018.
Jang-Jaccard, J. & Nepal, S. 2014. A survey of emerging threats in cybersecurity", Journal of
Computer and System Sciences, vol. 80, no. 5, pp. 973-993.
Kim, G., Shin, B. and Lee, H.G., 2009. Understanding dynamics between initial trust and usage
intentions of mobile banking. Information Systems Journal, 19(3), pp.283-311.
Lau, R.Y., Xia, Y. and Ye, Y., 2014. A probabilistic generative model for mining cybercriminal
networks from online social media. IEEE computational intelligence magazine, 9(1), pp.31-43.
Lohrke, F.T., Frownfelter-Lohrke, C. and Ketchen Jr, D.J., 2016. The role of information
technology systems in the performance of mergers and acquisitions. Business Horizons, 59(1),
pp.7-12.
Rasool, S., 2015. Cyber security threat in Pakistan: Causes, Challenges and Way
forward. International Scientific Online Journal, 12, pp.21-34.
Reddy, G.N. and Reddy, G.J., 2014. A Study of Cyber Security Challenges and its emerging
trends on latest technologies. arXiv preprint arXiv:1402.1842.
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds., 2016. Handbook of research on modern
cryptographic solutions for computer and cyber security. IGI Global.
He, H., Maple, C., Watson, T., Tiwari, A., Mehnen, J., Jin, Y. and Gabrys, B., 2016, July. The
security challenges in the IoT enabled cyber-physical systems and opportunities for evolutionary
computing & other computational intelligence. In Evolutionary Computation (CEC), 2016 IEEE
Congress on(pp. 1015-1021). IEEE.
Imam, A. L., 2012. Cyber crime in Pakistan: Serious threat but no laws!. Available at: . Accessed
on: 28th April, 2018.
Jang-Jaccard, J. & Nepal, S. 2014. A survey of emerging threats in cybersecurity", Journal of
Computer and System Sciences, vol. 80, no. 5, pp. 973-993.
Kim, G., Shin, B. and Lee, H.G., 2009. Understanding dynamics between initial trust and usage
intentions of mobile banking. Information Systems Journal, 19(3), pp.283-311.
Lau, R.Y., Xia, Y. and Ye, Y., 2014. A probabilistic generative model for mining cybercriminal
networks from online social media. IEEE computational intelligence magazine, 9(1), pp.31-43.
Lohrke, F.T., Frownfelter-Lohrke, C. and Ketchen Jr, D.J., 2016. The role of information
technology systems in the performance of mergers and acquisitions. Business Horizons, 59(1),
pp.7-12.
Rasool, S., 2015. Cyber security threat in Pakistan: Causes, Challenges and Way
forward. International Scientific Online Journal, 12, pp.21-34.
Reddy, G.N. and Reddy, G.J., 2014. A Study of Cyber Security Challenges and its emerging
trends on latest technologies. arXiv preprint arXiv:1402.1842.

Crime Attack 16
Sadeghi, A.R., Wachsmann, C. and Waidner, M., 2015. Security and privacy challenges in
industrial internet of things. In Proceedings of the 52nd annual design automation conference (p.
54). ACM.
Yan, Y., Qian, Y., Sharif, H. and Tipper, D., 2012. A survey on cyber security for smart grid
communications. IEEE Communications Surveys and tutorials, 14(4), pp.998-1010.
Sadeghi, A.R., Wachsmann, C. and Waidner, M., 2015. Security and privacy challenges in
industrial internet of things. In Proceedings of the 52nd annual design automation conference (p.
54). ACM.
Yan, Y., Qian, Y., Sharif, H. and Tipper, D., 2012. A survey on cyber security for smart grid
communications. IEEE Communications Surveys and tutorials, 14(4), pp.998-1010.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Crime Attack 17
Appendix
Figure 1: NADRA and its vital services
Source: (Awan and Memon, 2016).
Figure 2: E-governments services in Pakistan
Source: (Awan and Memon, 2016).
Appendix
Figure 1: NADRA and its vital services
Source: (Awan and Memon, 2016).
Figure 2: E-governments services in Pakistan
Source: (Awan and Memon, 2016).
Crime Attack 18
Figure 3: Current cyber threats
Source: (Awan and Memon, 2016).
Figure 4: Top threats expected
Source: (Awan and Memon, 2016).
Figure 3: Current cyber threats
Source: (Awan and Memon, 2016).
Figure 4: Top threats expected
Source: (Awan and Memon, 2016).
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





