BIT232 Systems Design & Development: ChemExec Design & Implementation
VerifiedAdded on 2023/06/03
|14
|3083
|405
Report
AI Summary
This report presents a system analysis and design for ChemExec, a pharmacy business aiming to computerize its operations to improve efficiency. The report includes a class diagram for use cases like 'Enter New Order,' 'Create Case Manifest,' and 'Record Order Fulfillment,' detailing attributes, behaviors, and navigation visibility. It also features a sequence diagram illustrating the order process and updates to the class diagram with additional classes like Facility and Employee. Security measures are outlined to prevent identity theft and phishing attacks, including encryption and firewalls. A database schema is proposed with seven tables, covering facility details, orders, payments, employees, and case manifests. The implementation strategy recommends a phased approach, and project management considerations address technical and organizational risks. This document provides a comprehensive overview of the proposed system and its development.

BIT232 Systems Design & Development
Assessment 2
Design refinement
Systems Design & Implementation Report
Assessment 2
Design refinement
Systems Design & Implementation Report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SYSTEM ANALYSIS REPORT FOR CHEMEXEC
PREPARED BY:
SUBMITTED TO:
PREPARED BY:
SUBMITTED TO:

Executive Summary
After years of using a combination of computerized and manual methods to man its operations,
ChemExec needs to computerize its operations. The failure to do so in the past years has led to
cumbersomeness brought about by the growth of the company and increase in its operations.
This inefficiency has resulted into losses for the company. The proposed system is intended to
help streamline order processing, delivery, billing and other management tasks. The existing
system has health facility employees deliver orders via telephone at all hours of the day, and then
ChemExec does delivery of the orders in two cycles, every twelve hours. The systems for taking
orders, billing and inventory are not integrated or synchronized. The new system should allow
the company’s clients to place orders via a web portal, and the employees to be able to process
them efficiently. More than that, the system should be able to manage the employees of the
company, monitor ranks and schedule shifts. This should simplify records of who was in charge
of assembling cases, delivery and supervision of the same. The system should also automate
actions such as generating case manifests and billing information. This kind of improved
efficiency should help in the growth of revenue for the organization as it will be easier to track
sales due to ease of generating reports, and therefore aid decision making by the company
executives. The separate spreadsheet and database applications will be consolidated into one
database application with appropriate interfaces for its users. This report covers the logical
design of the system in addition to security plans, project management and implementation
strategies that will be used during the entire system development life cycle.
After years of using a combination of computerized and manual methods to man its operations,
ChemExec needs to computerize its operations. The failure to do so in the past years has led to
cumbersomeness brought about by the growth of the company and increase in its operations.
This inefficiency has resulted into losses for the company. The proposed system is intended to
help streamline order processing, delivery, billing and other management tasks. The existing
system has health facility employees deliver orders via telephone at all hours of the day, and then
ChemExec does delivery of the orders in two cycles, every twelve hours. The systems for taking
orders, billing and inventory are not integrated or synchronized. The new system should allow
the company’s clients to place orders via a web portal, and the employees to be able to process
them efficiently. More than that, the system should be able to manage the employees of the
company, monitor ranks and schedule shifts. This should simplify records of who was in charge
of assembling cases, delivery and supervision of the same. The system should also automate
actions such as generating case manifests and billing information. This kind of improved
efficiency should help in the growth of revenue for the organization as it will be easier to track
sales due to ease of generating reports, and therefore aid decision making by the company
executives. The separate spreadsheet and database applications will be consolidated into one
database application with appropriate interfaces for its users. This report covers the logical
design of the system in addition to security plans, project management and implementation
strategies that will be used during the entire system development life cycle.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Table of contents
Table of Contents
Executive Summary.....................................................................................................................................3
Table of contents.........................................................................................................................................4
Task 1: Class Diagram.................................................................................................................................5
Task 2:.........................................................................................................................................................5
Task 3: Security...........................................................................................................................................7
Task 4: Database Schema............................................................................................................................9
Task 5: Implementation of the system.......................................................................................................11
Task 6: Project Management.....................................................................................................................11
Technical Risk factors...........................................................................................................................11
BIBLIOGRAPHY...........................................................................................................................................13
Table of Contents
Executive Summary.....................................................................................................................................3
Table of contents.........................................................................................................................................4
Task 1: Class Diagram.................................................................................................................................5
Task 2:.........................................................................................................................................................5
Task 3: Security...........................................................................................................................................7
Task 4: Database Schema............................................................................................................................9
Task 5: Implementation of the system.......................................................................................................11
Task 6: Project Management.....................................................................................................................11
Technical Risk factors...........................................................................................................................11
BIBLIOGRAPHY...........................................................................................................................................13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
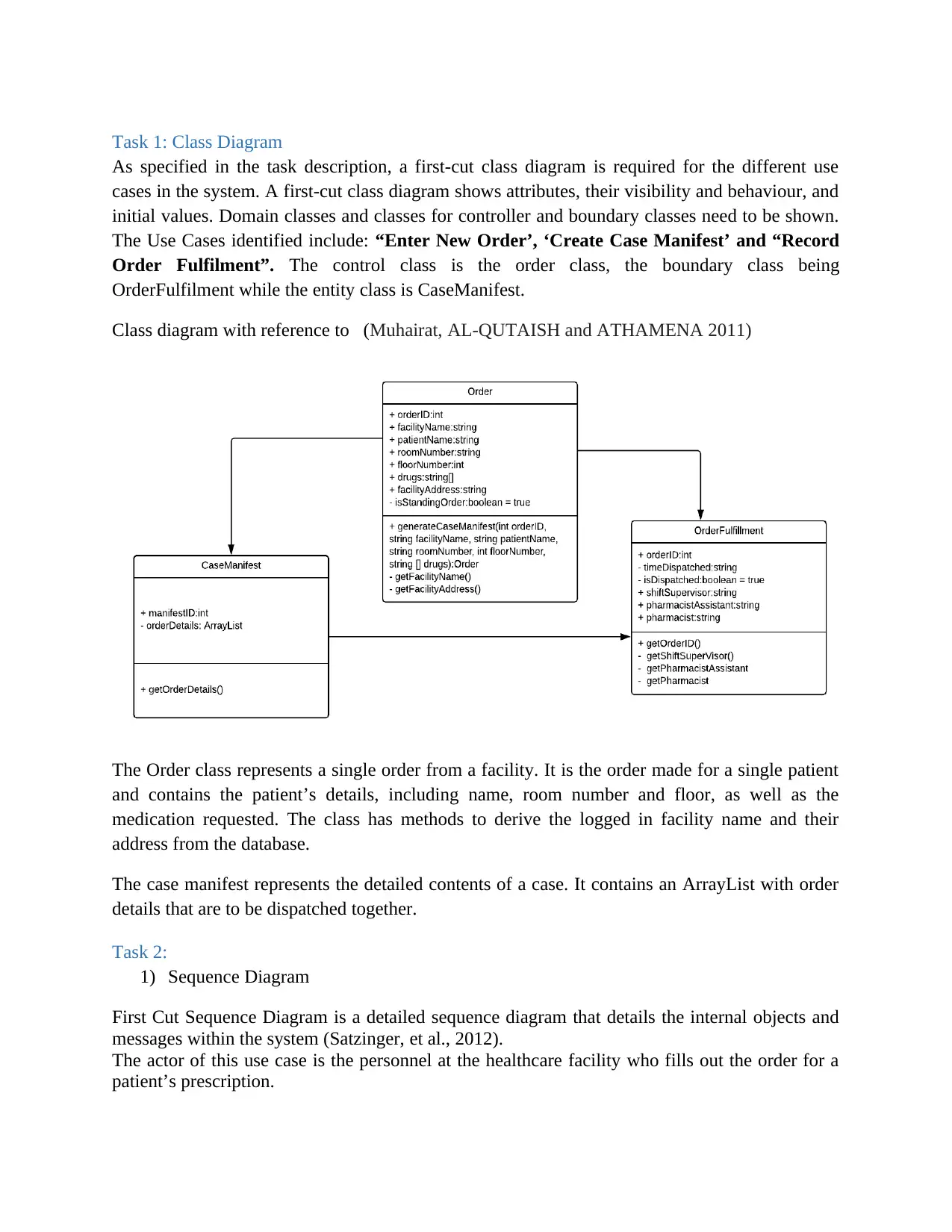
Task 1: Class Diagram
As specified in the task description, a first-cut class diagram is required for the different use
cases in the system. A first-cut class diagram shows attributes, their visibility and behaviour, and
initial values. Domain classes and classes for controller and boundary classes need to be shown.
The Use Cases identified include: “Enter New Order’, ‘Create Case Manifest’ and “Record
Order Fulfilment”. The control class is the order class, the boundary class being
OrderFulfilment while the entity class is CaseManifest.
Class diagram with reference to (Muhairat, AL-QUTAISH and ATHAMENA 2011)
The Order class represents a single order from a facility. It is the order made for a single patient
and contains the patient’s details, including name, room number and floor, as well as the
medication requested. The class has methods to derive the logged in facility name and their
address from the database.
The case manifest represents the detailed contents of a case. It contains an ArrayList with order
details that are to be dispatched together.
Task 2:
1) Sequence Diagram
First Cut Sequence Diagram is a detailed sequence diagram that details the internal objects and
messages within the system (Satzinger, et al., 2012).
The actor of this use case is the personnel at the healthcare facility who fills out the order for a
patient’s prescription.
As specified in the task description, a first-cut class diagram is required for the different use
cases in the system. A first-cut class diagram shows attributes, their visibility and behaviour, and
initial values. Domain classes and classes for controller and boundary classes need to be shown.
The Use Cases identified include: “Enter New Order’, ‘Create Case Manifest’ and “Record
Order Fulfilment”. The control class is the order class, the boundary class being
OrderFulfilment while the entity class is CaseManifest.
Class diagram with reference to (Muhairat, AL-QUTAISH and ATHAMENA 2011)
The Order class represents a single order from a facility. It is the order made for a single patient
and contains the patient’s details, including name, room number and floor, as well as the
medication requested. The class has methods to derive the logged in facility name and their
address from the database.
The case manifest represents the detailed contents of a case. It contains an ArrayList with order
details that are to be dispatched together.
Task 2:
1) Sequence Diagram
First Cut Sequence Diagram is a detailed sequence diagram that details the internal objects and
messages within the system (Satzinger, et al., 2012).
The actor of this use case is the personnel at the healthcare facility who fills out the order for a
patient’s prescription.
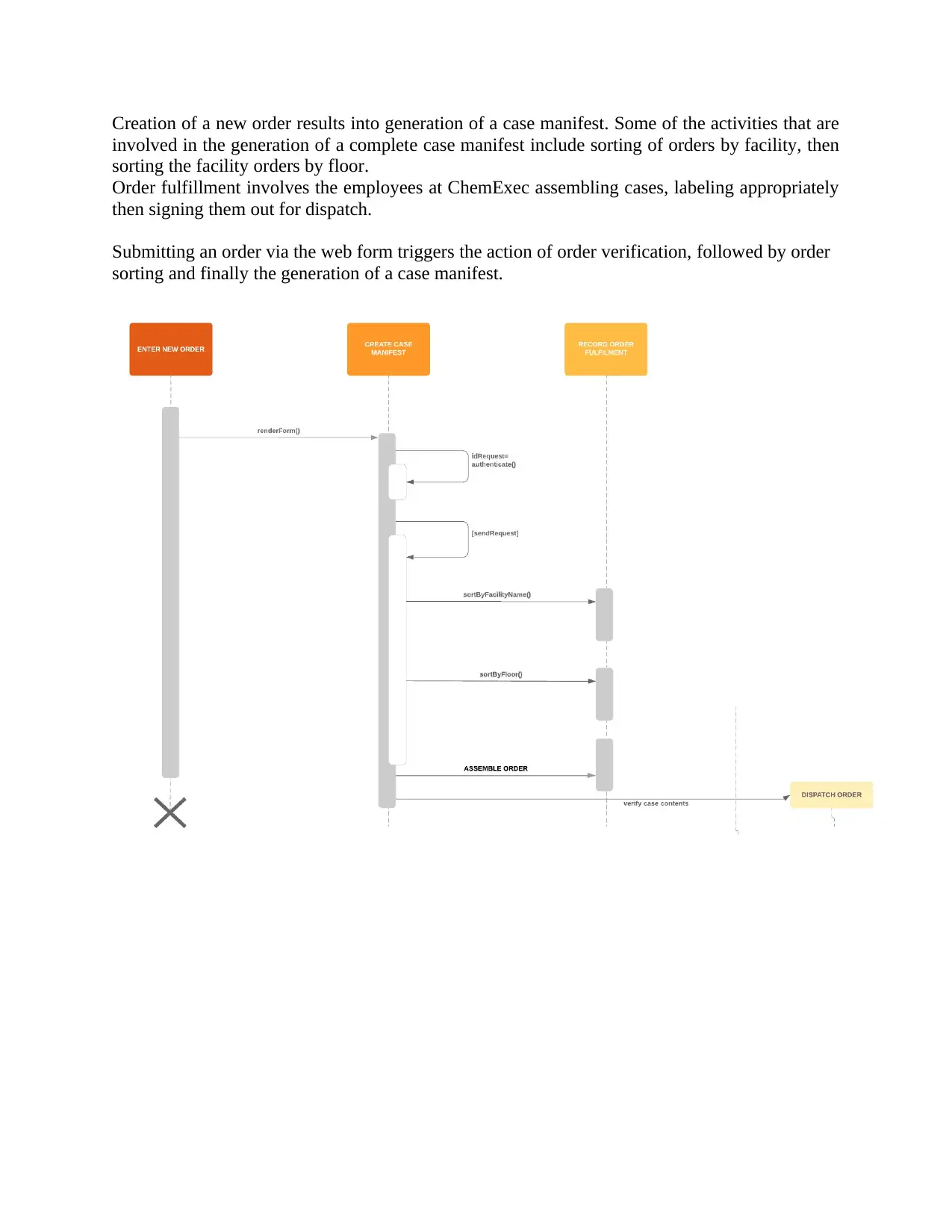
Creation of a new order results into generation of a case manifest. Some of the activities that are
involved in the generation of a complete case manifest include sorting of orders by facility, then
sorting the facility orders by floor.
Order fulfillment involves the employees at ChemExec assembling cases, labeling appropriately
then signing them out for dispatch.
Submitting an order via the web form triggers the action of order verification, followed by order
sorting and finally the generation of a case manifest.
involved in the generation of a complete case manifest include sorting of orders by facility, then
sorting the facility orders by floor.
Order fulfillment involves the employees at ChemExec assembling cases, labeling appropriately
then signing them out for dispatch.
Submitting an order via the web form triggers the action of order verification, followed by order
sorting and finally the generation of a case manifest.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2) Update Class Diagram
Additional classes that can be included for these use cases include Facility and Employee. The
facility class will represent the details of the facility to which ChemExec is supplying medicine,
while the Employee class represents the ChemExec employee using the system. Employee has
the getCurrentShift() method which identifies the shift. Facility has the attributes of facilityID,
facilityAddress and deliveryArea. The method it uses is getdeliveryArea() which selects one of
the two delivery areas based on the address provided.
CastManifest class has getOrderDetails() which gets all the details of the orders made.
OrderFullfillment class has methods getOrderID which gets the Ids of the orders fulfilled,
getShiftSuperVisor() gets the supervisor of the shift when the order was fulfilled,
getPharmacist() and getPharmacistAssistant which get both the pharmacist and the pharmacist
assistant incharge.
Task 3: Security
The following are controls and security measures to be incorporated within the social networking
subsystem to curb identity theft, phishing attacks, and viruses.
Login credentials
Change login credentials from the factory default to a new username and a complex password
made up of letters, numbers and symbols (Munson, 2017). Unique login credentials for each user
Additional classes that can be included for these use cases include Facility and Employee. The
facility class will represent the details of the facility to which ChemExec is supplying medicine,
while the Employee class represents the ChemExec employee using the system. Employee has
the getCurrentShift() method which identifies the shift. Facility has the attributes of facilityID,
facilityAddress and deliveryArea. The method it uses is getdeliveryArea() which selects one of
the two delivery areas based on the address provided.
CastManifest class has getOrderDetails() which gets all the details of the orders made.
OrderFullfillment class has methods getOrderID which gets the Ids of the orders fulfilled,
getShiftSuperVisor() gets the supervisor of the shift when the order was fulfilled,
getPharmacist() and getPharmacistAssistant which get both the pharmacist and the pharmacist
assistant incharge.
Task 3: Security
The following are controls and security measures to be incorporated within the social networking
subsystem to curb identity theft, phishing attacks, and viruses.
Login credentials
Change login credentials from the factory default to a new username and a complex password
made up of letters, numbers and symbols (Munson, 2017). Unique login credentials for each user
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

will help prevent guessing or hacking of passwords and thus unauthorized logins to the system
and identity theft.
Encryption
Enable Access Point Encryption such as WPA or WPA2 to protect data sent over the network
(Munson, 2017). Encrypted data cannot be deciphered without the appropriate encryption key
and therefore will help prevent unauthorized recipients from accessing user information. One
way to do this is to only send data over secured networks.
Secure the 802.1X client settings
To prevent a man-in-the-middle attack, utilize server verification on the client side. This prevents
the client from passing the Wi-Fi login credentials to the RADIUS server until it verifies it’s
communicating with a legit server. (Singla, Singh and Choudhary 2017). In this type of attack,
an attacker sets up a faux Wi-Fi that an unsuspecting user will connect to using the correct
username and password. The attacker collects sensitive information by recording such logins.
Verifying that the client seeking to communicate with the server is authentic will prevent this
kind of attack
Use firewalls
Deploy two firewalls which will separate the intranet from the internet. These firewalls will filter
incoming and outgoing communication to validate that they are allowed. Firewalls will prevent
outgoing communication to malicious websites that may allow viruses into the intranet and
therefore the system. They also prevent spoofing and jamming attacks.
Filter Egress Traffic to protect intranet
This involves restricting addresses that local workstations in the intranet can access. It prevents
malicious programs from getting onto the host then ex-filtrating data to an attacker. This also
prevents erroneous exfiltration and exfiltration due to configuration errors in NetBIOS or DNS to
external parties. Detecting exfiltration is achievable through logging of network traffic activity.
Restrict traffic to allowed devices only
Switch on logging of devices and network activity. This allows for monitoring such that only
devices with appropriate IP range of company addresses can access the internal network
resources. This method prevents phishing attacks since requests such as password changes can be
verified by the system administrator before being affected.
and identity theft.
Encryption
Enable Access Point Encryption such as WPA or WPA2 to protect data sent over the network
(Munson, 2017). Encrypted data cannot be deciphered without the appropriate encryption key
and therefore will help prevent unauthorized recipients from accessing user information. One
way to do this is to only send data over secured networks.
Secure the 802.1X client settings
To prevent a man-in-the-middle attack, utilize server verification on the client side. This prevents
the client from passing the Wi-Fi login credentials to the RADIUS server until it verifies it’s
communicating with a legit server. (Singla, Singh and Choudhary 2017). In this type of attack,
an attacker sets up a faux Wi-Fi that an unsuspecting user will connect to using the correct
username and password. The attacker collects sensitive information by recording such logins.
Verifying that the client seeking to communicate with the server is authentic will prevent this
kind of attack
Use firewalls
Deploy two firewalls which will separate the intranet from the internet. These firewalls will filter
incoming and outgoing communication to validate that they are allowed. Firewalls will prevent
outgoing communication to malicious websites that may allow viruses into the intranet and
therefore the system. They also prevent spoofing and jamming attacks.
Filter Egress Traffic to protect intranet
This involves restricting addresses that local workstations in the intranet can access. It prevents
malicious programs from getting onto the host then ex-filtrating data to an attacker. This also
prevents erroneous exfiltration and exfiltration due to configuration errors in NetBIOS or DNS to
external parties. Detecting exfiltration is achievable through logging of network traffic activity.
Restrict traffic to allowed devices only
Switch on logging of devices and network activity. This allows for monitoring such that only
devices with appropriate IP range of company addresses can access the internal network
resources. This method prevents phishing attacks since requests such as password changes can be
verified by the system administrator before being affected.
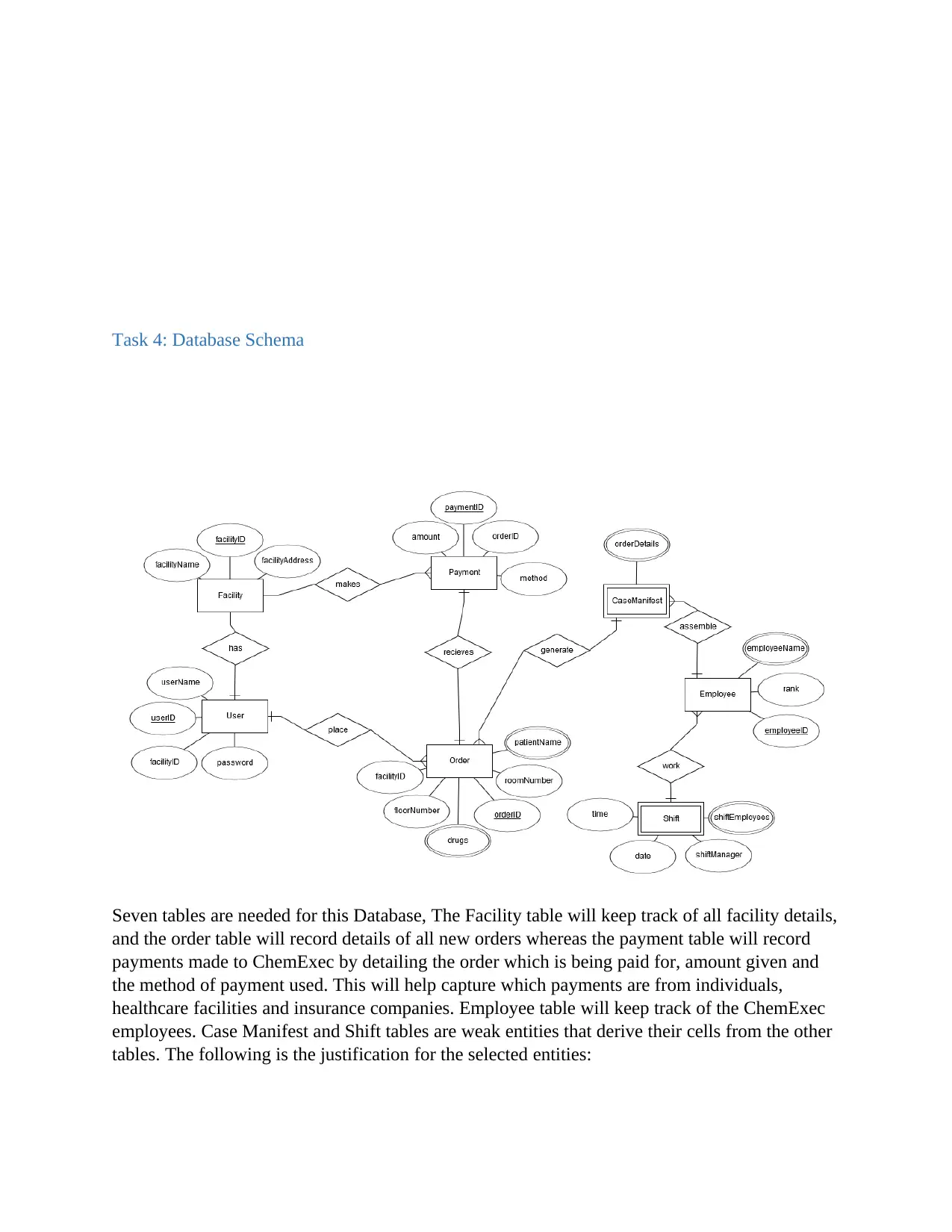
Task 4: Database Schema
Seven tables are needed for this Database, The Facility table will keep track of all facility details,
and the order table will record details of all new orders whereas the payment table will record
payments made to ChemExec by detailing the order which is being paid for, amount given and
the method of payment used. This will help capture which payments are from individuals,
healthcare facilities and insurance companies. Employee table will keep track of the ChemExec
employees. Case Manifest and Shift tables are weak entities that derive their cells from the other
tables. The following is the justification for the selected entities:
Seven tables are needed for this Database, The Facility table will keep track of all facility details,
and the order table will record details of all new orders whereas the payment table will record
payments made to ChemExec by detailing the order which is being paid for, amount given and
the method of payment used. This will help capture which payments are from individuals,
healthcare facilities and insurance companies. Employee table will keep track of the ChemExec
employees. Case Manifest and Shift tables are weak entities that derive their cells from the other
tables. The following is the justification for the selected entities:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Facility: The requirements document specifies that the health facility employees should be able
to place orders via a web portal. It is therefore needful to have an entity that keeps track of all
facilities registered with ChemExec, which results into normalization. This entity also provides
some measure of system security since it can be used to restrict the facilities making orders. The
primary key is facilityID and the only other details recorded are the facility name and address,
for the purpose of delivery.
Order: The order entity records each unique order placed by assigning it a unique id, recording
the facility placing the order and the specifics which include the floor, room and patient to which
the order will be delivered.
Employee: This keeps a record of ChemExec employees in order to assist with shift management
and therefore efficiency and accountability.
Payment: This important entity keeps track of all the payments made for each order. An
allowance has been made to record mode of payment in order to track whether the payment was
made by an individual, a facility or an insurance company.
User: The users table is used for verifying logins for all authorized registered users. It records
usernames and passwords.
Case Manifest: This is an entity generated from a consolidation of orders every twelve hours. Its
multi-valued entity contains order details.
to place orders via a web portal. It is therefore needful to have an entity that keeps track of all
facilities registered with ChemExec, which results into normalization. This entity also provides
some measure of system security since it can be used to restrict the facilities making orders. The
primary key is facilityID and the only other details recorded are the facility name and address,
for the purpose of delivery.
Order: The order entity records each unique order placed by assigning it a unique id, recording
the facility placing the order and the specifics which include the floor, room and patient to which
the order will be delivered.
Employee: This keeps a record of ChemExec employees in order to assist with shift management
and therefore efficiency and accountability.
Payment: This important entity keeps track of all the payments made for each order. An
allowance has been made to record mode of payment in order to track whether the payment was
made by an individual, a facility or an insurance company.
User: The users table is used for verifying logins for all authorized registered users. It records
usernames and passwords.
Case Manifest: This is an entity generated from a consolidation of orders every twelve hours. Its
multi-valued entity contains order details.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 5: Implementation of the system
The recommended method for implementing the new system would be the phased
implementation strategy. This is where the new system is implemented in stages overtime, until
the entire system is in place.
Currently, many procedures within the organization such as order entry, billing, and inventory
management are done using both manual and computer-assisted methods. The programs
currently in use include Excel spreadsheets, an Access database, and old custom-developed
billing software running on personal computers.
Given that there are various different programs in use for different functions, implementing the
new system in phases is bound to produce the best results. Each old program can be replaced by
a module of the new system on separate dates. This would give the employees time to familiarize
well with this new module before moving on to the next implementation.
Other advantages of this method include that it puts less pressure on the development team, it is
less risky, since problems with a phased module affect only that section and not the entire system
and lastly, the development team can gain knowledge from the user interactions with the
implemented modules which they may use during the development of the other upcoming
modules.
Task 6: Project Management
Technical Risk factors
These arise from technological phenomena such as hardware or software failure or
incompatibility. Technical risks can be associated with the introduction of new technology (Van
Asselt and Renn 2011) or the acquisition of new hardware and software (Van Asselt and Renn
2011). Complex systems need higher levels of technical skills and technology employed. The
greater the project size, the higher the likelihood of a project failure. Furthermore, a project can
fail if it is too ambitious, such as needing to address cross-sector requirements, such as finance,
management, and distribution, even when given time and firm executive support. One way to
solve this is to use a phased approach (Warkentin, 2009). Breaking down the project into doable
parts helps address risks in small portions. However, the best method is to attempt to identify
risks earlier on and deploy the necessary factors needed to mitigate them.
Organizational Risk Issues
According to research, organizational risks such as hesitant senior management support to a
project and not involving the end-user during development are some of the risks that lead to
project failure or cancellation (Christensen, 2013). This risk occurs frequently and is of high
severity, because without the approval and support by the senior management, the project is
likely to fail completely. Moreover, not dedicating enough time towards the initial stages of
system leads to more issues during the testing period since the problem may not have been well
defined, leading to a product that the users do not accept, or one that does not meet user needs.
To mitigate this risk, development teams look out for known failure factors relating to planning
The recommended method for implementing the new system would be the phased
implementation strategy. This is where the new system is implemented in stages overtime, until
the entire system is in place.
Currently, many procedures within the organization such as order entry, billing, and inventory
management are done using both manual and computer-assisted methods. The programs
currently in use include Excel spreadsheets, an Access database, and old custom-developed
billing software running on personal computers.
Given that there are various different programs in use for different functions, implementing the
new system in phases is bound to produce the best results. Each old program can be replaced by
a module of the new system on separate dates. This would give the employees time to familiarize
well with this new module before moving on to the next implementation.
Other advantages of this method include that it puts less pressure on the development team, it is
less risky, since problems with a phased module affect only that section and not the entire system
and lastly, the development team can gain knowledge from the user interactions with the
implemented modules which they may use during the development of the other upcoming
modules.
Task 6: Project Management
Technical Risk factors
These arise from technological phenomena such as hardware or software failure or
incompatibility. Technical risks can be associated with the introduction of new technology (Van
Asselt and Renn 2011) or the acquisition of new hardware and software (Van Asselt and Renn
2011). Complex systems need higher levels of technical skills and technology employed. The
greater the project size, the higher the likelihood of a project failure. Furthermore, a project can
fail if it is too ambitious, such as needing to address cross-sector requirements, such as finance,
management, and distribution, even when given time and firm executive support. One way to
solve this is to use a phased approach (Warkentin, 2009). Breaking down the project into doable
parts helps address risks in small portions. However, the best method is to attempt to identify
risks earlier on and deploy the necessary factors needed to mitigate them.
Organizational Risk Issues
According to research, organizational risks such as hesitant senior management support to a
project and not involving the end-user during development are some of the risks that lead to
project failure or cancellation (Christensen, 2013). This risk occurs frequently and is of high
severity, because without the approval and support by the senior management, the project is
likely to fail completely. Moreover, not dedicating enough time towards the initial stages of
system leads to more issues during the testing period since the problem may not have been well
defined, leading to a product that the users do not accept, or one that does not meet user needs.
To mitigate this risk, development teams look out for known failure factors relating to planning

and problem definition and deliberately avoid them as an incentive to prevent these factors of
project failure.
Resource Limitations
This is a problem of inadequate resources allocated to the project. The three crucial resources
needed during development are time, money and skilled personnel. The personnel need to
identify the system requirements and develop a requirement specification document, as well as a
budget outline. Once the team receives the necessary funding, they need to proceed to acquire
the technology and other resources needed for development.
Another resource required is the technology used. If the system specification details a technical
requirement that is not compatible with the technical resources provided, it hampers
development of the system.
Olawale and Sun (2010) stresses that organizations must always focus on balancing cost, time
and quality of a project design. Hwang and Gay 2013 advise that people, time, and money must
be allocated prior to the beginning of the project and then monitored throughout the system
development life cycle. Cost overruns are a great cause of a system project failure (Ameh,
Soyingbe and Odusami 2010).
Communication Risk
This is a factor that relates to sharing information between the project’s stakeholders.
Communication between vendors and clients is crucial especially from a management
perspective. When the team elements share information in a timely and concise manner, it makes
project management more efficient. Also, good management encourages better communication.
For this reason, when a problem arises, it can be managed in a timely manner. On the other hand,
lack of clearly outlined communication and management procedures has adverse consequences
such as poor product quality or termination of project. It is important that the appointed
communication persons between the teams have adequate knowledge of the project and a clear
understanding of the kind of information needed to bring the project to completion.
project failure.
Resource Limitations
This is a problem of inadequate resources allocated to the project. The three crucial resources
needed during development are time, money and skilled personnel. The personnel need to
identify the system requirements and develop a requirement specification document, as well as a
budget outline. Once the team receives the necessary funding, they need to proceed to acquire
the technology and other resources needed for development.
Another resource required is the technology used. If the system specification details a technical
requirement that is not compatible with the technical resources provided, it hampers
development of the system.
Olawale and Sun (2010) stresses that organizations must always focus on balancing cost, time
and quality of a project design. Hwang and Gay 2013 advise that people, time, and money must
be allocated prior to the beginning of the project and then monitored throughout the system
development life cycle. Cost overruns are a great cause of a system project failure (Ameh,
Soyingbe and Odusami 2010).
Communication Risk
This is a factor that relates to sharing information between the project’s stakeholders.
Communication between vendors and clients is crucial especially from a management
perspective. When the team elements share information in a timely and concise manner, it makes
project management more efficient. Also, good management encourages better communication.
For this reason, when a problem arises, it can be managed in a timely manner. On the other hand,
lack of clearly outlined communication and management procedures has adverse consequences
such as poor product quality or termination of project. It is important that the appointed
communication persons between the teams have adequate knowledge of the project and a clear
understanding of the kind of information needed to bring the project to completion.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




