Case Study: Cloud and IoT Security Challenges in MITS5004, 2020S1
VerifiedAdded on 2022/09/01
|11
|475
|26
Case Study
AI Summary
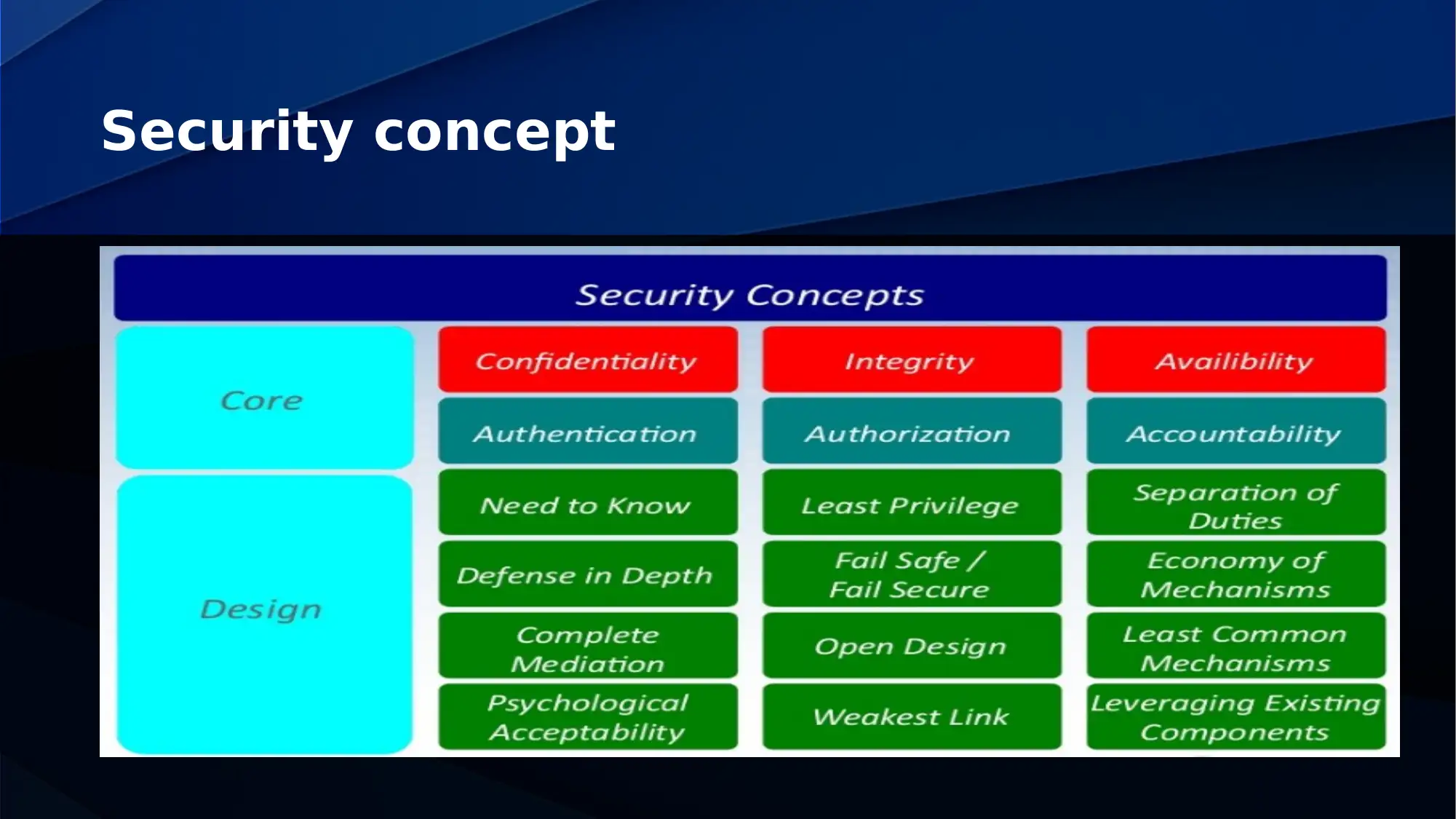
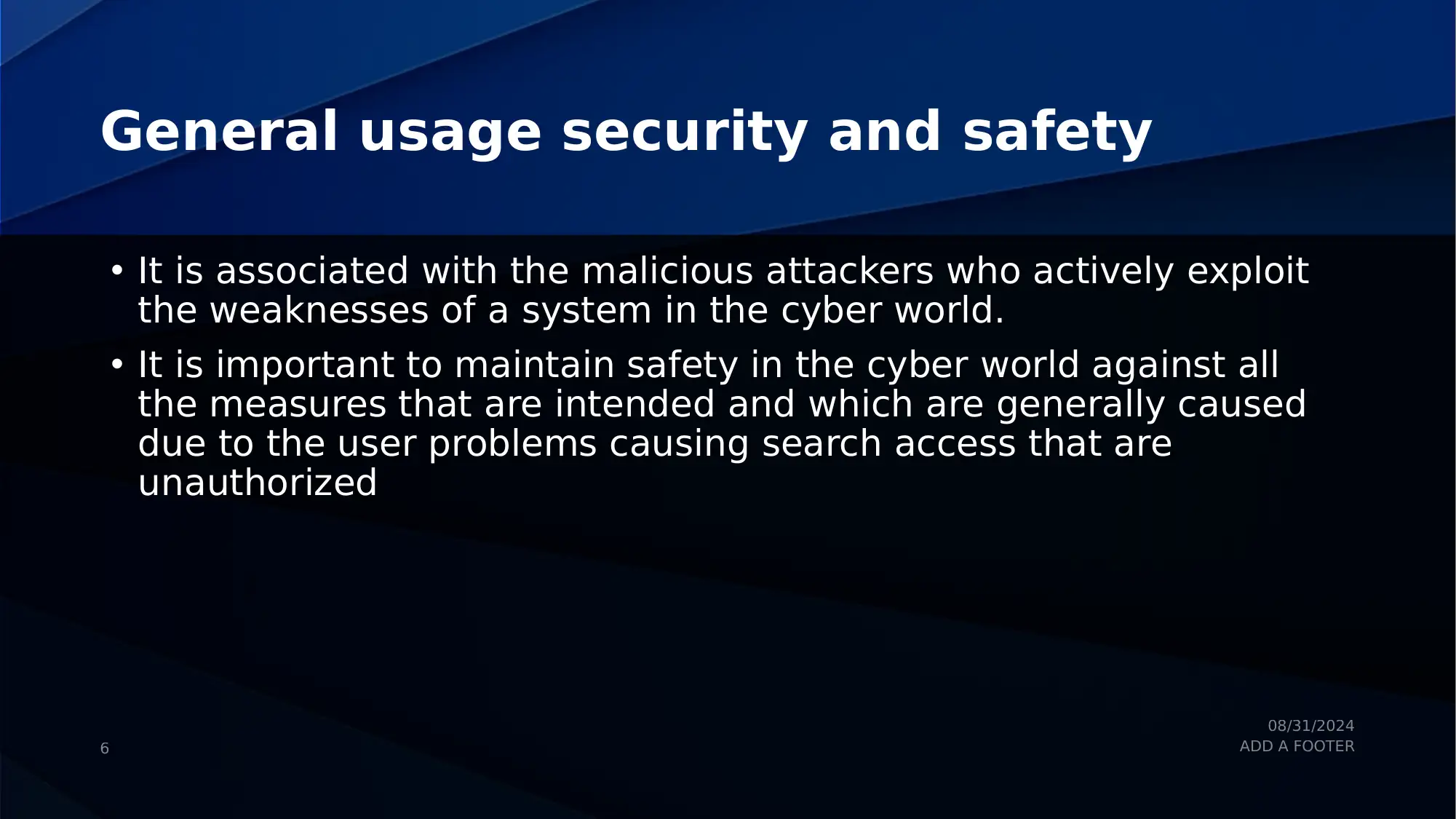
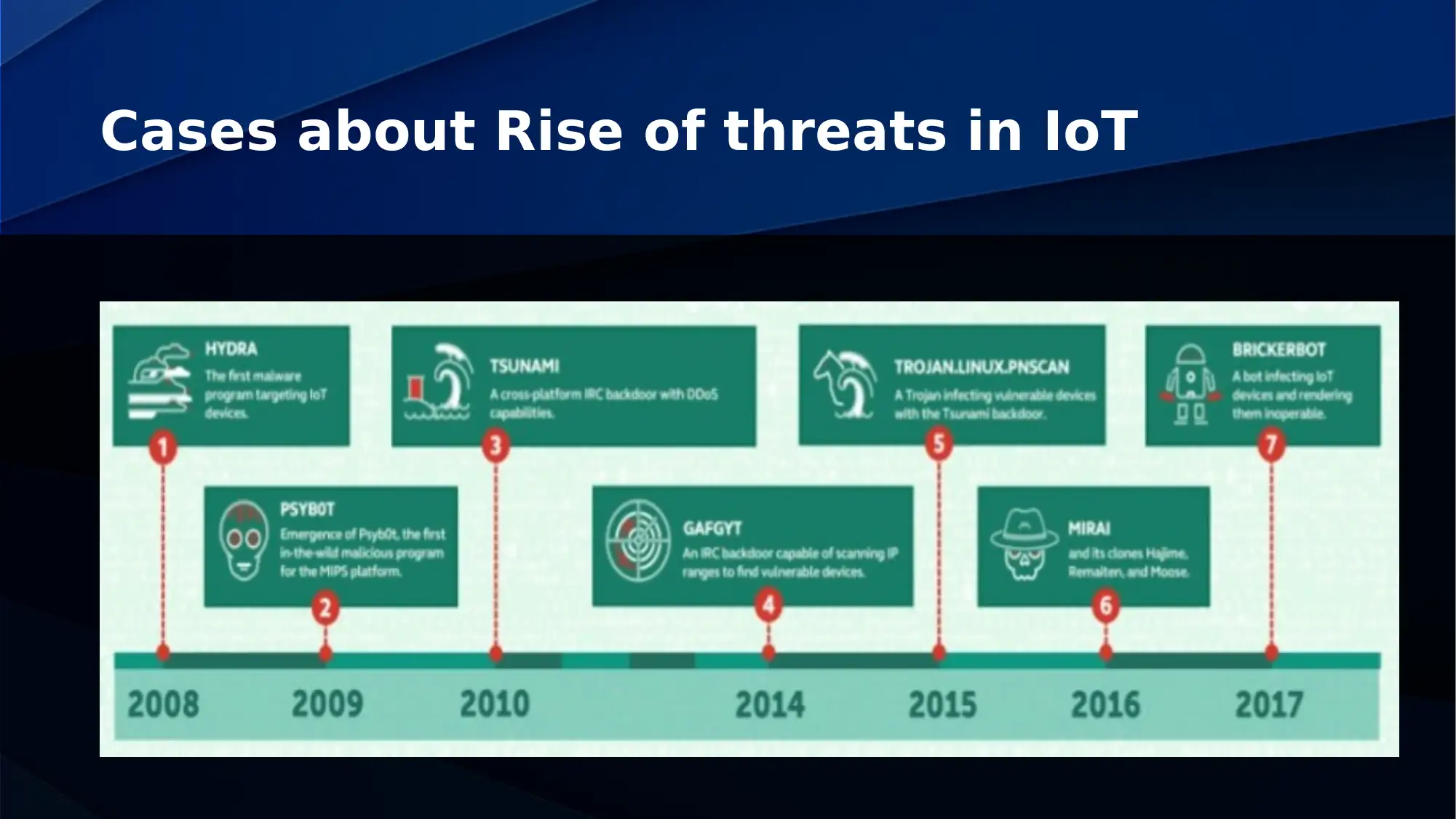
This assignment analyzes the security challenges associated with cloud computing and the Internet of Things (IoT). It explores the essence of cybersecurity, emphasizing multiple layers of security including physical, personal, operational, communication, and network security. The document discusses the importance of information security policies, awareness of cyber hygiene, and the need for proper training and technological enhancements. It addresses the vulnerabilities in IoT security, including design flaws, incompatibility issues, and the rise of various threats. Different types of IoT security attacks, such as physical, network, software, and encryption attacks, are also examined. The assignment provides a comprehensive overview of cloud and IoT security, offering valuable insights into the current landscape of cyber threats and security measures.
1 out of 11













![[object Object]](/_next/static/media/star-bottom.7253800d.svg)