What is Cloud Computing Accounting Software
VerifiedAdded on 2022/07/28
|11
|2792
|35
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Q 1. What is Cloud computing accounting software and how does it work?
Accounting system is the series of tasks and records of an entity by which the transactions are
processed as a means of maintaining financial records. A good accounting system should provide
managerial reports, financial statements, reports prepared for outsiders and adequate information.
Holmesglen Hair Dressing Salon uses MYOB, Computerized accounting system yet their data are
not stored in the cloud system.
Please answer to the following questions. (300 words)
1) Describe what Cloud Accounting system is and how Clouding system is different from Desktop
based Accounting system.
2) Provide reasons to implement Cloud-based Accounting system for Holmesglen Hair Dressing
Salon in your own words
Type Answer here:
1) This is a system of electronic accounting which more or less resembles the traditional systems
of accounting. However, what spells out the difference is that the software programs are
located remotely in other servers. Any data has to be transmitted to the cloud for processing
before feedback is given. The end user does not have to install the software on their
computers. Access to such software is granted over the internet or alternatively through
networks. There is an offsite processing of data. End users from whatever location they are in
are in a position to remotely log in to the cloud and access the exact copy of the data they
require. There is a small fee charged by the provider of the application, based on use(Master,
2018).
2) Cloud based Accounting systems have over the years become very user friendly as the
developers have come up with means to make it compatible with specific user needs.
There are a lot of savings as far as storage space and costs are concerned. The salon
will be allocated a virtual storage space on the cloud
Data security is beefed up as the information is not stored physically. Tragedies like
infernos and even hardware failure do not lead to data loss as the data can be accessed
from any other device that can access the cloud(Mangiuc, 2017).
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
Accounting system is the series of tasks and records of an entity by which the transactions are
processed as a means of maintaining financial records. A good accounting system should provide
managerial reports, financial statements, reports prepared for outsiders and adequate information.
Holmesglen Hair Dressing Salon uses MYOB, Computerized accounting system yet their data are
not stored in the cloud system.
Please answer to the following questions. (300 words)
1) Describe what Cloud Accounting system is and how Clouding system is different from Desktop
based Accounting system.
2) Provide reasons to implement Cloud-based Accounting system for Holmesglen Hair Dressing
Salon in your own words
Type Answer here:
1) This is a system of electronic accounting which more or less resembles the traditional systems
of accounting. However, what spells out the difference is that the software programs are
located remotely in other servers. Any data has to be transmitted to the cloud for processing
before feedback is given. The end user does not have to install the software on their
computers. Access to such software is granted over the internet or alternatively through
networks. There is an offsite processing of data. End users from whatever location they are in
are in a position to remotely log in to the cloud and access the exact copy of the data they
require. There is a small fee charged by the provider of the application, based on use(Master,
2018).
2) Cloud based Accounting systems have over the years become very user friendly as the
developers have come up with means to make it compatible with specific user needs.
There are a lot of savings as far as storage space and costs are concerned. The salon
will be allocated a virtual storage space on the cloud
Data security is beefed up as the information is not stored physically. Tragedies like
infernos and even hardware failure do not lead to data loss as the data can be accessed
from any other device that can access the cloud(Mangiuc, 2017).
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Sharing of data and collaboration amongst various levels in the salon can be achieved
when cloud accounting is used. This in term is cost effective as software may not
necessarily have to be installed in individual end users for access
Time effectiveness. Cloud Accounting systems with regard to accessibility from
anyplace, can save a great deal of time whenever you have to do a task and you are
away from the office. Instead of waiting till you return, you can easily log in and do
what is require(Soni, Saluja & Vardia, 2018).
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
when cloud accounting is used. This in term is cost effective as software may not
necessarily have to be installed in individual end users for access
Time effectiveness. Cloud Accounting systems with regard to accessibility from
anyplace, can save a great deal of time whenever you have to do a task and you are
away from the office. Instead of waiting till you return, you can easily log in and do
what is require(Soni, Saluja & Vardia, 2018).
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx

Q 2. A source document is the original record containing the details to substantiate a transaction
entered in an accounting system.
Please answer to the three following questions. (300 words)
1) Describe key characteristics of source documents and explain why the source
document is essential to the bookkeeping and accounting process.
2) Provide three example of source documents
3) Are photocopies of source documents legally acceptable?
Type Answer here:
1) Transaction date. Clearly indicates when the business transaction took place for record
keeping. The date enables keeping track of future transactions that may be required
such as warranties that are normally pegged to a particular period after the transaction
date after which it expires.
The names and contact details of persons involved in the transaction must be indicated.
This enables easy identification of whoever did the transaction whenever a claim is
being made, for example when receiving goods during delivery, a crosscheck can be
done between the name on the delivery note and that on the identification details of the
recipient.
A precise description of the products, whether goods or services should be included.
There value of the transaction in terms of amount of cash involved should be stated.
This is key in general accounting and maintenance of the financial records of a
company. This may be needed during routine procedures such as sales audits(Flaherty,
2017).
Double entry system allows for multiple copies of the same document, these may
include a customer copy and a copy for the service provider. The more the participants
in a business transaction, definitely, the more the number of copies that shall be require
as each party has to be entrusted with one.
Validation of the source documents by means of signage by all parties involved in the
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
entered in an accounting system.
Please answer to the three following questions. (300 words)
1) Describe key characteristics of source documents and explain why the source
document is essential to the bookkeeping and accounting process.
2) Provide three example of source documents
3) Are photocopies of source documents legally acceptable?
Type Answer here:
1) Transaction date. Clearly indicates when the business transaction took place for record
keeping. The date enables keeping track of future transactions that may be required
such as warranties that are normally pegged to a particular period after the transaction
date after which it expires.
The names and contact details of persons involved in the transaction must be indicated.
This enables easy identification of whoever did the transaction whenever a claim is
being made, for example when receiving goods during delivery, a crosscheck can be
done between the name on the delivery note and that on the identification details of the
recipient.
A precise description of the products, whether goods or services should be included.
There value of the transaction in terms of amount of cash involved should be stated.
This is key in general accounting and maintenance of the financial records of a
company. This may be needed during routine procedures such as sales audits(Flaherty,
2017).
Double entry system allows for multiple copies of the same document, these may
include a customer copy and a copy for the service provider. The more the participants
in a business transaction, definitely, the more the number of copies that shall be require
as each party has to be entrusted with one.
Validation of the source documents by means of signage by all parties involved in the
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx

transaction
For the case of sales, the related terms of sale have to be clearly stated; these may
include discounts and after sell services such delivery logistics(Hurloiu, Rusu &
Hurloiu, 2018).
2) Official Receipt
Invoice
Bank Statement
3) Yes, photocopies of the source documents can be accepted legally. However they have to be
an accurate copy of what is contained in the original document. They have to be consistent
and clear. This is recommended by the United States Internal Review Service(Stedman, 2019).
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
For the case of sales, the related terms of sale have to be clearly stated; these may
include discounts and after sell services such delivery logistics(Hurloiu, Rusu &
Hurloiu, 2018).
2) Official Receipt
Invoice
Bank Statement
3) Yes, photocopies of the source documents can be accepted legally. However they have to be
an accurate copy of what is contained in the original document. They have to be consistent
and clear. This is recommended by the United States Internal Review Service(Stedman, 2019).
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Q 3. The Privacy Act 1988 (the Privacy Act) contains 13 Australian Privacy Principles (APPs)
which regulate the way we collect, store, provide access to, use and disclose personal
information.
Please answer to the following questions. (300 words)
1) Explain APP 11
2) Provide two exceptions to this requirement.
Type Answer here:
1) A federal body or an organization ought to ensure that it has the capability to protect and
secure whatever form of confidential or personal information held by it from inappropriate
utilization, any loss of the information and access by parties that are not authorized. Such
parties must be denied not only the access rights but also, any modifications or dissemination
should be curtailed. Under special circumstances, the entity has the rights to delink the
information from any form of identifier or even destroy it completely. This mostly happens in
instances where the entity has exhausted the need for a given personal information
This clause cuts through the six key aspects of information. In the event that it is completely
impossible to destroy and make personal data completely irretrievable, an entity has to make
such information lack identity. It has to be delinked completely from the owner. This mostly
applies to electronic storage of information. These include, misuse, interference, loss,
unauthorized access, modification and disclosure. This guide is not only limited to the original
documents but also takes into consideration the likelihood that copies of a document with
personal data may have been reproduced for one reason or another. These too are governed by
APP 11(Azfar, Choo & Liu, 2016).
2) The requirement to under special circumstances destroy or de-identify personal
information does not apply to information that is in a Commonwealth record.
Such information can only be deemed fit for destruction upon consideration of the
Archives Act 1983(Mengmeng, 2018).
If a court of law or the Australian law requires some information, then an entity is not
tied to destroy or de-identify personal information. In this case destruction of the
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
which regulate the way we collect, store, provide access to, use and disclose personal
information.
Please answer to the following questions. (300 words)
1) Explain APP 11
2) Provide two exceptions to this requirement.
Type Answer here:
1) A federal body or an organization ought to ensure that it has the capability to protect and
secure whatever form of confidential or personal information held by it from inappropriate
utilization, any loss of the information and access by parties that are not authorized. Such
parties must be denied not only the access rights but also, any modifications or dissemination
should be curtailed. Under special circumstances, the entity has the rights to delink the
information from any form of identifier or even destroy it completely. This mostly happens in
instances where the entity has exhausted the need for a given personal information
This clause cuts through the six key aspects of information. In the event that it is completely
impossible to destroy and make personal data completely irretrievable, an entity has to make
such information lack identity. It has to be delinked completely from the owner. This mostly
applies to electronic storage of information. These include, misuse, interference, loss,
unauthorized access, modification and disclosure. This guide is not only limited to the original
documents but also takes into consideration the likelihood that copies of a document with
personal data may have been reproduced for one reason or another. These too are governed by
APP 11(Azfar, Choo & Liu, 2016).
2) The requirement to under special circumstances destroy or de-identify personal
information does not apply to information that is in a Commonwealth record.
Such information can only be deemed fit for destruction upon consideration of the
Archives Act 1983(Mengmeng, 2018).
If a court of law or the Australian law requires some information, then an entity is not
tied to destroy or de-identify personal information. In this case destruction of the
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
information becomes a legal trespass and therefore the entity has to uphold the law
despite the dictates of the APP11. After conclusion of legal procedure or after
permission by the law can such information be destroyed.
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
despite the dictates of the APP11. After conclusion of legal procedure or after
permission by the law can such information be destroyed.
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx

Q 4. Read the following and determine whether you are complying with the code of
conduct – Confidentiality or not.
Extract from TASA2009 Sn 30-10:
(6) Unless you have a legal duty to do so, you must not disclose any information relating to a client’s
affairs to a third party without your client’s permission.
Get Consent Before Providing Access to Information
You should not release any information to a third party without specific authority from the client. If
you do provide information to a third party without the authority of your client, whether knowingly or
unknowingly, this is a breach of the code of conduct and the client would be within their rights to
complain to the TPB.
In addition, you are most likely to be bound by the Privacy Act 1988. The Act is relevant for almost
all businesses, check the links below and if you are unsure whether the principles apply, you may
need to get advice from the Office of the Australian Information Commissioner—or simply assume
that the privacy principles apply to you.
Poppy George, one of your clients has a banana plantation in Kennedy, Queensland. Her company
was recently affected by unseasonal cyclonic weather. Your firm VPWC published an alert to
clients to call out a number of potential implications that companies need to consider.
Now, you are having dinner with a friend and talking about issues going on with Poppy.
1) You are only talking about general issues a client is facing because of the disaster, and mostly
talked about how that impacts your role. (no names of clients or companies mentioned)
Would this be in breach of confidentiality? Clearly State Yes or No and explain why.
2) What if you mention the value and type of stock that the client holds? Also you’ve mentioned
names of Poppy and Poppy’s suppliers.
Would this be in breach of confidentiality? Clearly State Yes or No and explain why.
Type Answer here: (200 words)
1) No. This would not be a breach of confidentiality as no personal identifier information has
been exposed. It is therefore impossible for the third party to link the general issues to a
specific client. This therefore means that I have operated within the limits of the code of
conduct and I am not guilty of going against the set code of conduct(McKnight &
Linnenluecke, 2019).
2) Yes. This is a breach of confidentiality. No information about the client should be disclosed to
a third party without authority from the client or unless when compelled by the law. In this
instance there is no provision that has allowed me to disclose Poppy’s details to my friend as it
was just a general talk. The value of goods, Poppy’s name as well as the name of his suppliers
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
conduct – Confidentiality or not.
Extract from TASA2009 Sn 30-10:
(6) Unless you have a legal duty to do so, you must not disclose any information relating to a client’s
affairs to a third party without your client’s permission.
Get Consent Before Providing Access to Information
You should not release any information to a third party without specific authority from the client. If
you do provide information to a third party without the authority of your client, whether knowingly or
unknowingly, this is a breach of the code of conduct and the client would be within their rights to
complain to the TPB.
In addition, you are most likely to be bound by the Privacy Act 1988. The Act is relevant for almost
all businesses, check the links below and if you are unsure whether the principles apply, you may
need to get advice from the Office of the Australian Information Commissioner—or simply assume
that the privacy principles apply to you.
Poppy George, one of your clients has a banana plantation in Kennedy, Queensland. Her company
was recently affected by unseasonal cyclonic weather. Your firm VPWC published an alert to
clients to call out a number of potential implications that companies need to consider.
Now, you are having dinner with a friend and talking about issues going on with Poppy.
1) You are only talking about general issues a client is facing because of the disaster, and mostly
talked about how that impacts your role. (no names of clients or companies mentioned)
Would this be in breach of confidentiality? Clearly State Yes or No and explain why.
2) What if you mention the value and type of stock that the client holds? Also you’ve mentioned
names of Poppy and Poppy’s suppliers.
Would this be in breach of confidentiality? Clearly State Yes or No and explain why.
Type Answer here: (200 words)
1) No. This would not be a breach of confidentiality as no personal identifier information has
been exposed. It is therefore impossible for the third party to link the general issues to a
specific client. This therefore means that I have operated within the limits of the code of
conduct and I am not guilty of going against the set code of conduct(McKnight &
Linnenluecke, 2019).
2) Yes. This is a breach of confidentiality. No information about the client should be disclosed to
a third party without authority from the client or unless when compelled by the law. In this
instance there is no provision that has allowed me to disclose Poppy’s details to my friend as it
was just a general talk. The value of goods, Poppy’s name as well as the name of his suppliers
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

are very sensitive data that may be used maliciously if it has been disclosed whether
knowingly or unknowingly to a third party with ill intentions. This there is a grievous
violation of the code of conduct and therefore puts me in a vulnerable position with the law.
No legal authority had requested disclosure of the information and Poppy himself has not
specifically authorized disclosure of information to third parties.
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
knowingly or unknowingly to a third party with ill intentions. This there is a grievous
violation of the code of conduct and therefore puts me in a vulnerable position with the law.
No legal authority had requested disclosure of the information and Poppy himself has not
specifically authorized disclosure of information to third parties.
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
Q 5. A system backup is the process of backing up the operating system, files and system-
specific useful/essential data. Backup is a process in which the state, files and data of a
computer system are duplicated to be used as a backup or data substitute when the
primary system data is corrupted, deleted or lost.
Create and describe an adequate backup procedure. You must address ALL of the
followings:
1) Who: Who / What team will manage the back up and maintain the system
2) How often: Schedule to make sure your system backup is up-to-date, you need to
create schedules to backup system
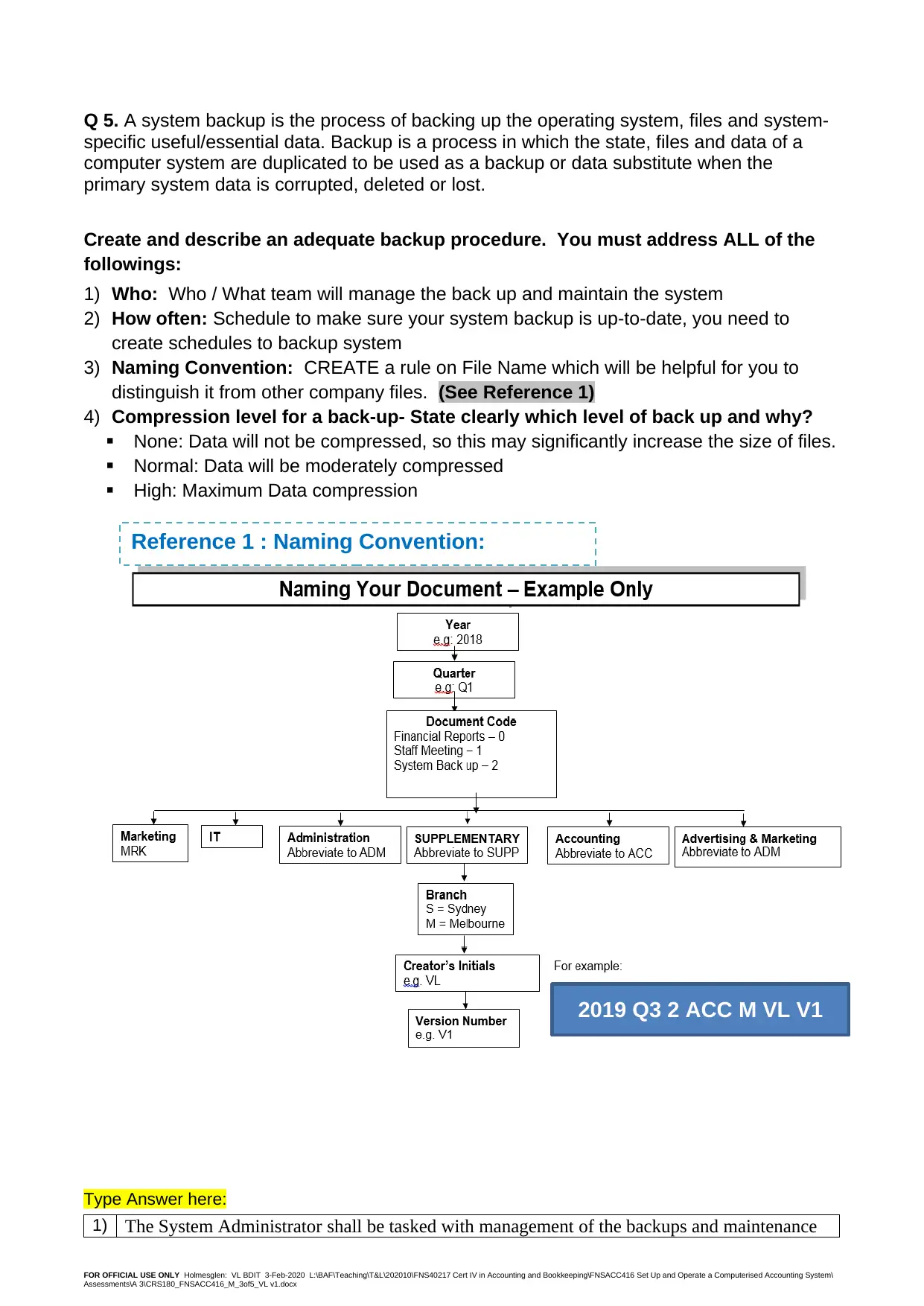
3) Naming Convention: CREATE a rule on File Name which will be helpful for you to
distinguish it from other company files. (See Reference 1)
4) Compression level for a back-up- State clearly which level of back up and why?
None: Data will not be compressed, so this may significantly increase the size of files.
Normal: Data will be moderately compressed
High: Maximum Data compression
Type Answer here:
1) The System Administrator shall be tasked with management of the backups and maintenance
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
Reference 1 : Naming Convention:
2019 Q3 2 ACC M VL V1
specific useful/essential data. Backup is a process in which the state, files and data of a
computer system are duplicated to be used as a backup or data substitute when the
primary system data is corrupted, deleted or lost.
Create and describe an adequate backup procedure. You must address ALL of the
followings:
1) Who: Who / What team will manage the back up and maintain the system
2) How often: Schedule to make sure your system backup is up-to-date, you need to
create schedules to backup system
3) Naming Convention: CREATE a rule on File Name which will be helpful for you to
distinguish it from other company files. (See Reference 1)
4) Compression level for a back-up- State clearly which level of back up and why?
None: Data will not be compressed, so this may significantly increase the size of files.
Normal: Data will be moderately compressed
High: Maximum Data compression
Type Answer here:
1) The System Administrator shall be tasked with management of the backups and maintenance
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
Reference 1 : Naming Convention:
2019 Q3 2 ACC M VL V1

of the system(Zhang et al., 2017).
2) Regular backups are mandatory as no one can potentiate the time a threat to data integrity may
present.
Sensitive records such as payroll, financial records and employee records may require
monthly backups(Musembe & Mutula, 2019).
For reports and quarterly targets, it can be done on a quarterly basis.
3) The File Name should:
State the year
The quarter of the year(In the case of reports and quarterly targets)
Stat the month
State the department and branch
State the creator’s initials and version
For example, for the first version of a system backup of quarterly report done at the end of the
first quarter of 2019 by Don Joe in the Marketing Department in Sydney
2019 Q1 2 MRK S DJ V1
4) Normal level shall be used for documents as they do not take up too much space.
None is suited for database backups as they have the capability to be copied on
different servers as they are without compression to maintain quality of data(Malcher&
Kuhn, 2019).
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
2) Regular backups are mandatory as no one can potentiate the time a threat to data integrity may
present.
Sensitive records such as payroll, financial records and employee records may require
monthly backups(Musembe & Mutula, 2019).
For reports and quarterly targets, it can be done on a quarterly basis.
3) The File Name should:
State the year
The quarter of the year(In the case of reports and quarterly targets)
Stat the month
State the department and branch
State the creator’s initials and version
For example, for the first version of a system backup of quarterly report done at the end of the
first quarter of 2019 by Don Joe in the Marketing Department in Sydney
2019 Q1 2 MRK S DJ V1
4) Normal level shall be used for documents as they do not take up too much space.
None is suited for database backups as they have the capability to be copied on
different servers as they are without compression to maintain quality of data(Malcher&
Kuhn, 2019).
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References
Azfar, A., Choo, K. K. R., & Liu, L. (2016). An android communication app forensic
taxonomy. Journal of forensic sciences, 61(5), 1337-1350.
Flaherty, S. (2017). Bookkeeping in the Cloud: Advancements in Accounting Software (Doctoral
dissertation, Appalachian State University).
Hurloiu, L., Rusu, B., & Hurloiu, I. I. (2018). Modern perspectives of financial management
accounting approach in the current economy. EcoSoEn, (1-2), 81-86.
Malcher, M., & Kuhn, D. (2019). Configuring RMAN. In Pro Oracle Database 18c
Administration (pp. 693-732). Apress, Berkeley, CA.
Mangiuc, D. (2017). Accountants and the cloud–Involving the professionals. Accounting and
Management Information Systems, 16(1), 179-198.
Master, S. (2018). Cloud Accounting–The Game Changer In Digital Economy (No. 2018-28-15).
McKnight, B., & Linnenluecke, M. K. (2019). Patterns of firm responses to different types of natural
disasters. Business & Society, 58(4), 813-840.
Mengmeng, Y. E. (2018). The Study on Australian Archival legislation and Regulation System from
the Public Access Perspective. Archives Science Study, 32(1), 123-127.
Musembe, C. N., & Mutula, S. (2019, September). E-records security classification and access
controls in Moi University, Kenya. In Proceedings of 20th Annual IS Conference (Vol. 18, p.
143).
Soni, R., Saluja, R., & Vardia, S. (2018). Awareness and Adoption of Cloud Accounting Software:
An Empirical Research. IUP Journal of Accounting Research & Audit Practices, 17(2).
Stedman, J. C. (2019). Academic library reserves, photocopying, and the copyright law. College &
Research Libraries News, 39(9), 263-269.
Zhang, W., Lin, J., Xu, W., Fu, H., & Yang, G. (2017). Scstore: managing scientific computing
packages for hybrid system with containers. Tsinghua Science and Technology, 22(6), 675-
681.
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
Azfar, A., Choo, K. K. R., & Liu, L. (2016). An android communication app forensic
taxonomy. Journal of forensic sciences, 61(5), 1337-1350.
Flaherty, S. (2017). Bookkeeping in the Cloud: Advancements in Accounting Software (Doctoral
dissertation, Appalachian State University).
Hurloiu, L., Rusu, B., & Hurloiu, I. I. (2018). Modern perspectives of financial management
accounting approach in the current economy. EcoSoEn, (1-2), 81-86.
Malcher, M., & Kuhn, D. (2019). Configuring RMAN. In Pro Oracle Database 18c
Administration (pp. 693-732). Apress, Berkeley, CA.
Mangiuc, D. (2017). Accountants and the cloud–Involving the professionals. Accounting and
Management Information Systems, 16(1), 179-198.
Master, S. (2018). Cloud Accounting–The Game Changer In Digital Economy (No. 2018-28-15).
McKnight, B., & Linnenluecke, M. K. (2019). Patterns of firm responses to different types of natural
disasters. Business & Society, 58(4), 813-840.
Mengmeng, Y. E. (2018). The Study on Australian Archival legislation and Regulation System from
the Public Access Perspective. Archives Science Study, 32(1), 123-127.
Musembe, C. N., & Mutula, S. (2019, September). E-records security classification and access
controls in Moi University, Kenya. In Proceedings of 20th Annual IS Conference (Vol. 18, p.
143).
Soni, R., Saluja, R., & Vardia, S. (2018). Awareness and Adoption of Cloud Accounting Software:
An Empirical Research. IUP Journal of Accounting Research & Audit Practices, 17(2).
Stedman, J. C. (2019). Academic library reserves, photocopying, and the copyright law. College &
Research Libraries News, 39(9), 263-269.
Zhang, W., Lin, J., Xu, W., Fu, H., & Yang, G. (2017). Scstore: managing scientific computing
packages for hybrid system with containers. Tsinghua Science and Technology, 22(6), 675-
681.
FOR OFFICIAL USE ONLY Holmesglen: VL BDIT 3-Feb-2020 L:\BAF\Teaching\T&L\202010\FNS40217 Cert IV in Accounting and Bookkeeping\FNSACC416 Set Up and Operate a Computerised Accounting System\
Assessments\A 3\CRS180_FNSACC416_M_3of5_VL v1.docx
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





