Cloud Computing for Small Businesses
VerifiedAdded on 2020/04/01
|15
|2948
|171
AI Summary
This assignment delves into the advantages and challenges of cloud computing for small and medium-sized enterprises (SMEs). It examines critical success factors influencing SME adoption of cloud services, highlighting specific examples and research findings. The analysis covers various aspects of cloud computing, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS), and their impact on SMEs' operations and growth.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
Cloud Computing
Assignment No.:
Student Name:
Student ID:
Student Email:
University Name:
Cloud Computing
Assignment No.:
Student Name:
Student ID:
Student Email:
University Name:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
Executive Summary
Webb's Store, the retail store in Australia has decided to migrate to the cloud. Various
aspects associated with cloud will be discussed in the report. Webb Store can be facilitated
by the advanced cloud solutions provided by Amazon. The risks, threats associated with
cloud platform has been detailed and as well as the risk mitigation has been detailed in the
report has been elaborated.
1 STUDENT NAME: , STUDENT ID:
Executive Summary
Webb's Store, the retail store in Australia has decided to migrate to the cloud. Various
aspects associated with cloud will be discussed in the report. Webb Store can be facilitated
by the advanced cloud solutions provided by Amazon. The risks, threats associated with
cloud platform has been detailed and as well as the risk mitigation has been detailed in the
report has been elaborated.
1 STUDENT NAME: , STUDENT ID:

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
Table of Contents
Introduction................................................................................................................................3
Question 1..................................................................................................................................3
1. Webb’s decision to migrate their MS SQL Server 2012 R2 database to IaaS instance.........3
1. a. Security deployment to protect this migration of database to IaaS instance...............3
1. b. Benefits and issues related to deployment of these security measures.......................4
Question 2..................................................................................................................................5
2. Risks associated with migrating database to the cloud with respect to-................................5
2. a. The database..................................................................................................................5
2. b. The IaaS infrastructure...................................................................................................6
2. c. Communications between Webb’s and their IaaS database in the cloud.....................6
Question 3..................................................................................................................................7
3. Webb’s consideration for the use of the Cloud for backup and possibly also for archival of
records........................................................................................................................................7
3. a. Risks associated to..........................................................................................................7
I. Backing up data to the Cloud..........................................................................................7
II. Storage of data in the Cloud..........................................................................................7
III. Retrieval of data from the cloud...................................................................................8
3. b. Webb’s use of a Cloud backup and its impact on the company and DR plan...............8
Question 4..................................................................................................................................8
4. Recommendations to Webb for protecting access to the following services that they want
to move to the Cloud..................................................................................................................8
4.a. Their IaaS infrastructure..................................................................................................8
4.b. Their Ms SQL Server 2012 R2 cloud instance..................................................................9
4.c. Their Cloud network infrastructure.................................................................................9
4.d. Their Cloud backup and restore infrastructure..............................................................9
Conclusion..................................................................................................................................9
References................................................................................................................................11
2 STUDENT NAME: , STUDENT ID:
Table of Contents
Introduction................................................................................................................................3
Question 1..................................................................................................................................3
1. Webb’s decision to migrate their MS SQL Server 2012 R2 database to IaaS instance.........3
1. a. Security deployment to protect this migration of database to IaaS instance...............3
1. b. Benefits and issues related to deployment of these security measures.......................4
Question 2..................................................................................................................................5
2. Risks associated with migrating database to the cloud with respect to-................................5
2. a. The database..................................................................................................................5
2. b. The IaaS infrastructure...................................................................................................6
2. c. Communications between Webb’s and their IaaS database in the cloud.....................6
Question 3..................................................................................................................................7
3. Webb’s consideration for the use of the Cloud for backup and possibly also for archival of
records........................................................................................................................................7
3. a. Risks associated to..........................................................................................................7
I. Backing up data to the Cloud..........................................................................................7
II. Storage of data in the Cloud..........................................................................................7
III. Retrieval of data from the cloud...................................................................................8
3. b. Webb’s use of a Cloud backup and its impact on the company and DR plan...............8
Question 4..................................................................................................................................8
4. Recommendations to Webb for protecting access to the following services that they want
to move to the Cloud..................................................................................................................8
4.a. Their IaaS infrastructure..................................................................................................8
4.b. Their Ms SQL Server 2012 R2 cloud instance..................................................................9
4.c. Their Cloud network infrastructure.................................................................................9
4.d. Their Cloud backup and restore infrastructure..............................................................9
Conclusion..................................................................................................................................9
References................................................................................................................................11
2 STUDENT NAME: , STUDENT ID:

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
Introduction
Webb's Store, the retail store in Australia has decided to move to the cloud. Various
aspects associated with cloud will be discussed in the report (Beck, Hao & Campan, 2017).
The report will also highlight the risks, threats associated with the SQL database and risk
mitigation procedures will also be showcased in the report as well.
Question 1
1. Webb’s decision to migrate their MS SQL Server 2012 R2 database to IaaS instance
1. a. Security deployment to protect this migration of database to IaaS instance
Webb wants to migrate to the cloud and for this, they must be ready to face the issues
and consequences associated with it. The general issues associated with cloud are illicit
access to APIs, the virus, malware attack to the system and the database by the hacktivist
(Shufeng & Xu, 2012). That is why Webb must follow these principles to stay safe as well as
protected on the cloud platform.
Follow-through: The database administrators of the Webb Store must be
knowledgeable about all the files of the database and they mark them all so that the
administrators can recognise the files very easily that are stored in the database (Azam et
al., 2013). This approach can be convenient for them when trying to acquire those files for
future needs.
Security associated with network information: Certain policies must be established
for the customers and the employees and must limit them to use data from the database to
a considerable amount and not beyond that (Sadooghi et al., 2017).
3 STUDENT NAME: , STUDENT ID:
Introduction
Webb's Store, the retail store in Australia has decided to move to the cloud. Various
aspects associated with cloud will be discussed in the report (Beck, Hao & Campan, 2017).
The report will also highlight the risks, threats associated with the SQL database and risk
mitigation procedures will also be showcased in the report as well.
Question 1
1. Webb’s decision to migrate their MS SQL Server 2012 R2 database to IaaS instance
1. a. Security deployment to protect this migration of database to IaaS instance
Webb wants to migrate to the cloud and for this, they must be ready to face the issues
and consequences associated with it. The general issues associated with cloud are illicit
access to APIs, the virus, malware attack to the system and the database by the hacktivist
(Shufeng & Xu, 2012). That is why Webb must follow these principles to stay safe as well as
protected on the cloud platform.
Follow-through: The database administrators of the Webb Store must be
knowledgeable about all the files of the database and they mark them all so that the
administrators can recognise the files very easily that are stored in the database (Azam et
al., 2013). This approach can be convenient for them when trying to acquire those files for
future needs.
Security associated with network information: Certain policies must be established
for the customers and the employees and must limit them to use data from the database to
a considerable amount and not beyond that (Sadooghi et al., 2017).
3 STUDENT NAME: , STUDENT ID:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
Security Intelligence techniques and procedures: The defence system must be
checked and verified to find out any defect and fault and it is the duty of the Security
Intelligence to keep an eye on the defence system constantly (Dinh et al., 2013). Along with
that, they must apply proper cryptographic methods to embellish the security of the system
and the database.
1. b. Benefits and issues related to deployment of these security measures
Benefits of security -
i. Secured from the DDoS attack- The security and privacy can be well assured by the
cloud solutions, thus authentication can be guaranteed and along with that, the threat DDoS
can be mitigated as well.
ii. Security assurance of the information- The information residing within the
database and the system can be provided advanced cloud security solutions thus Webb can
stay protected from various kinds of threats (Varia & Mathew, 2014).
iii. Regulatory compliance- The financial data of the Webb Store along with the
customers' sensitive information like bank details, the customers' purchase records can be
managed in a secure manner with the help of cloud security solution.
iv. Probable solutions- The server that Webb is using can crash at any times and
Webb has the opportunity to scale back to diminish the heavy expenses when the cloud
traffic gets rectified (Dillon & Vossen, 2015).
v. Allowing 24x7 services- The cloud has the capability to cater 24x7 communication
services to the clients all day long.
4 STUDENT NAME: , STUDENT ID:
Security Intelligence techniques and procedures: The defence system must be
checked and verified to find out any defect and fault and it is the duty of the Security
Intelligence to keep an eye on the defence system constantly (Dinh et al., 2013). Along with
that, they must apply proper cryptographic methods to embellish the security of the system
and the database.
1. b. Benefits and issues related to deployment of these security measures
Benefits of security -
i. Secured from the DDoS attack- The security and privacy can be well assured by the
cloud solutions, thus authentication can be guaranteed and along with that, the threat DDoS
can be mitigated as well.
ii. Security assurance of the information- The information residing within the
database and the system can be provided advanced cloud security solutions thus Webb can
stay protected from various kinds of threats (Varia & Mathew, 2014).
iii. Regulatory compliance- The financial data of the Webb Store along with the
customers' sensitive information like bank details, the customers' purchase records can be
managed in a secure manner with the help of cloud security solution.
iv. Probable solutions- The server that Webb is using can crash at any times and
Webb has the opportunity to scale back to diminish the heavy expenses when the cloud
traffic gets rectified (Dillon & Vossen, 2015).
v. Allowing 24x7 services- The cloud has the capability to cater 24x7 communication
services to the clients all day long.
4 STUDENT NAME: , STUDENT ID:

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
vi. Costing- Webb do not have to spend heavy purchasing hardware, software and
application programs, even they do not have to spend money purchasing operating system
and also they do not have to worry about the updates and upgrades of the operating
system. They will have to pay a minimal amount to Amazon to hire their cloud platform
(Muthui & SISAT, 2013).
vii. Integrity- The data integrity highlights that the data should be stored safely and
securely and the cloud vendor must be loyal, thus, in this case, Amazon should take the
responsibility to provide advanced security solutions and data integrity solutions to the
Webb.
The primary issue is that Webb will have to pay the cloud vendor an annual revenue
or monthly revenue for hiring the cloud architecture framework (Muthui & SISAT, 2013).
The cloud architecture framework consists of latest hardware, latest software, latest
software programs and advanced security features. Webb needs it to conduct their business
activities in safe and secure manner.
5 STUDENT NAME: , STUDENT ID:
vi. Costing- Webb do not have to spend heavy purchasing hardware, software and
application programs, even they do not have to spend money purchasing operating system
and also they do not have to worry about the updates and upgrades of the operating
system. They will have to pay a minimal amount to Amazon to hire their cloud platform
(Muthui & SISAT, 2013).
vii. Integrity- The data integrity highlights that the data should be stored safely and
securely and the cloud vendor must be loyal, thus, in this case, Amazon should take the
responsibility to provide advanced security solutions and data integrity solutions to the
Webb.
The primary issue is that Webb will have to pay the cloud vendor an annual revenue
or monthly revenue for hiring the cloud architecture framework (Muthui & SISAT, 2013).
The cloud architecture framework consists of latest hardware, latest software, latest
software programs and advanced security features. Webb needs it to conduct their business
activities in safe and secure manner.
5 STUDENT NAME: , STUDENT ID:

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
Fig 1: SQL Server and its features
(Source: Tsai et al., 2014, pp-1-15)
Question 2
2. Risks associated with migrating database to the cloud with respect to-
2. a. The database
The risks associated with the database are-
Data breaches- Data breaches is a huge risk and threat for any organisation and
Webb Store is no exception. Due to the attack of the hacktivist Webb can lose reputation
and can lose the vital data and information. Even Webb can face severe loss for this data
breach.
Account hijacking of customers and employees- Webb's database holds the
customers' personal and sensitive information, so there is a risk if those data get breached
6 STUDENT NAME: , STUDENT ID:
Fig 1: SQL Server and its features
(Source: Tsai et al., 2014, pp-1-15)
Question 2
2. Risks associated with migrating database to the cloud with respect to-
2. a. The database
The risks associated with the database are-
Data breaches- Data breaches is a huge risk and threat for any organisation and
Webb Store is no exception. Due to the attack of the hacktivist Webb can lose reputation
and can lose the vital data and information. Even Webb can face severe loss for this data
breach.
Account hijacking of customers and employees- Webb's database holds the
customers' personal and sensitive information, so there is a risk if those data get breached
6 STUDENT NAME: , STUDENT ID:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
then Webb will face severe loss (Tsai et al., 2014). This data breach generally occurs by
means of phishing, DDoS attacks.
Malware attack- The malware attack makes one’s system vulnerable and the
malware attack includes virus attack and worm attack.
2. b. The IaaS infrastructure
The risks correlated with IaaS Cloud are-
Misconfigure issues- Webb must use the latest hardware and software and latest
operating system and latest application programs so that Webb's architecture can comply
with the Amazon AWS cloud framework.
Threat issues- The IaaS framework elements that are responsive to risks and threats
can be predicted by the Remediate, Prioritize and Scan method (Manvi, & Shyam, 2014).
Shadow-IT- This Shadow-IT is basically the assets which have not been used for long.
In the case of Webb due to the advent of Amazon AWS, Webb will use the cloud server
provided by the cloud vendor, so the database server which they are utilising now will not
be used anymore. This unused database is the asset which they will not go to use in mere
future.
7 STUDENT NAME: , STUDENT ID:
then Webb will face severe loss (Tsai et al., 2014). This data breach generally occurs by
means of phishing, DDoS attacks.
Malware attack- The malware attack makes one’s system vulnerable and the
malware attack includes virus attack and worm attack.
2. b. The IaaS infrastructure
The risks correlated with IaaS Cloud are-
Misconfigure issues- Webb must use the latest hardware and software and latest
operating system and latest application programs so that Webb's architecture can comply
with the Amazon AWS cloud framework.
Threat issues- The IaaS framework elements that are responsive to risks and threats
can be predicted by the Remediate, Prioritize and Scan method (Manvi, & Shyam, 2014).
Shadow-IT- This Shadow-IT is basically the assets which have not been used for long.
In the case of Webb due to the advent of Amazon AWS, Webb will use the cloud server
provided by the cloud vendor, so the database server which they are utilising now will not
be used anymore. This unused database is the asset which they will not go to use in mere
future.
7 STUDENT NAME: , STUDENT ID:
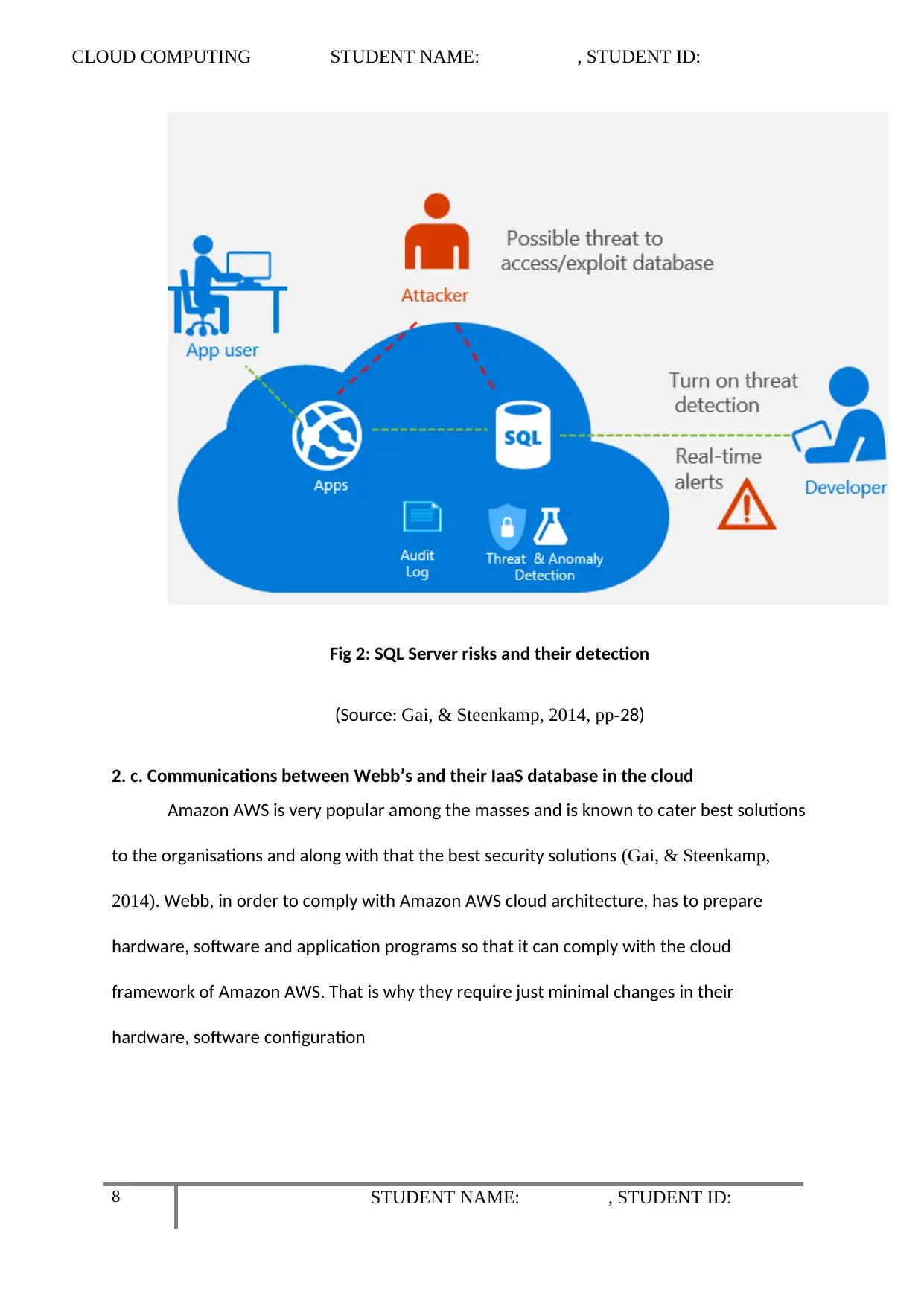
CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
Fig 2: SQL Server risks and their detection
(Source: Gai, & Steenkamp, 2014, pp-28)
2. c. Communications between Webb’s and their IaaS database in the cloud
Amazon AWS is very popular among the masses and is known to cater best solutions
to the organisations and along with that the best security solutions (Gai, & Steenkamp,
2014). Webb, in order to comply with Amazon AWS cloud architecture, has to prepare
hardware, software and application programs so that it can comply with the cloud
framework of Amazon AWS. That is why they require just minimal changes in their
hardware, software configuration
8 STUDENT NAME: , STUDENT ID:
Fig 2: SQL Server risks and their detection
(Source: Gai, & Steenkamp, 2014, pp-28)
2. c. Communications between Webb’s and their IaaS database in the cloud
Amazon AWS is very popular among the masses and is known to cater best solutions
to the organisations and along with that the best security solutions (Gai, & Steenkamp,
2014). Webb, in order to comply with Amazon AWS cloud architecture, has to prepare
hardware, software and application programs so that it can comply with the cloud
framework of Amazon AWS. That is why they require just minimal changes in their
hardware, software configuration
8 STUDENT NAME: , STUDENT ID:

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
Question 3
3. Webb’s consideration for the use of the Cloud for backup and possibly also for archival
of records
3. a. Risks associated to
I. Backing up data to the Cloud
The threats and the security risks associated with backup of data are-
i. A high bandwidth is required to both upload and downloads data from the web server, to
keep a backup of their server's data they need a strong bandwidth and thus Webb will have
to spend a lot for the fast bandwidth.
ii. The sensitive personal data can be hacked or can be breached while the data is being
transacted (Manvi, & Shyam, 2014).
iii. The sudden breakdown of the server can also cost too much, there remains a high chance
for personal information loss also.
II. Storage of data in the Cloud
i. The chances are more for the data breach if gets transacted through the insecure network
which is not deciphered as well.
ii. The execution of the file must be done properly and also along with that file must be
processed and stored in the database well otherwise the sensitive information will get
breached and will get lost (Manvi, & Shyam, 2014).
III. Retrieval of data from the cloud
i. The high bandwidth is necessary to download files and to acquire files which are
absolutely necessary.
9 STUDENT NAME: , STUDENT ID:
Question 3
3. Webb’s consideration for the use of the Cloud for backup and possibly also for archival
of records
3. a. Risks associated to
I. Backing up data to the Cloud
The threats and the security risks associated with backup of data are-
i. A high bandwidth is required to both upload and downloads data from the web server, to
keep a backup of their server's data they need a strong bandwidth and thus Webb will have
to spend a lot for the fast bandwidth.
ii. The sensitive personal data can be hacked or can be breached while the data is being
transacted (Manvi, & Shyam, 2014).
iii. The sudden breakdown of the server can also cost too much, there remains a high chance
for personal information loss also.
II. Storage of data in the Cloud
i. The chances are more for the data breach if gets transacted through the insecure network
which is not deciphered as well.
ii. The execution of the file must be done properly and also along with that file must be
processed and stored in the database well otherwise the sensitive information will get
breached and will get lost (Manvi, & Shyam, 2014).
III. Retrieval of data from the cloud
i. The high bandwidth is necessary to download files and to acquire files which are
absolutely necessary.
9 STUDENT NAME: , STUDENT ID:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
ii. The information that has been downloaded from the web server may contain the
malware that is threatening and they must be checked and assured.
3. b. Webb’s use of a Cloud backup and its impact on the company and DR plan
The benefits that Webb is about to get-
i. The database of Webb can be improved to gain more throughputs and along with that
cost-effective service can be acquired from the cloud solutions.
ii. Amazon AWS caters the services to manage the database and also to update the
database; Webb Store does not have to consider the hardware and software maintenance
and the update (Sharma et al., 2017).
iii. Amazon is also famous to provide advanced cloud security solutions that are why Webb
can securely conduct their business activities peacefully.
They must have a disaster recovery plan ready for them, they must back up their
data in the external hard disk so that they can receive those files offline and do not require
an Internet connection. In that case, they do not have to worry about the security breaches
while they are conducting business activities offline.
10 STUDENT NAME: , STUDENT ID:
ii. The information that has been downloaded from the web server may contain the
malware that is threatening and they must be checked and assured.
3. b. Webb’s use of a Cloud backup and its impact on the company and DR plan
The benefits that Webb is about to get-
i. The database of Webb can be improved to gain more throughputs and along with that
cost-effective service can be acquired from the cloud solutions.
ii. Amazon AWS caters the services to manage the database and also to update the
database; Webb Store does not have to consider the hardware and software maintenance
and the update (Sharma et al., 2017).
iii. Amazon is also famous to provide advanced cloud security solutions that are why Webb
can securely conduct their business activities peacefully.
They must have a disaster recovery plan ready for them, they must back up their
data in the external hard disk so that they can receive those files offline and do not require
an Internet connection. In that case, they do not have to worry about the security breaches
while they are conducting business activities offline.
10 STUDENT NAME: , STUDENT ID:

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
Fig 3: Securing Cloud Data
(Source: Manvi, & Shyam, 2014, pp-424-440)
Question 4
4. Recommendations to Webb for protecting access to the following services that they
want to move to the Cloud
4.a. Their IaaS infrastructure
Webb Store if adopt the Amazon's AWS cloud services can get the best features can
conduct their business activities in the agile and effective way. They can conduct the
business activities in agile and efficient. Plus, they do not have to pay heavily for the
software, they do not have to pay for the hardware (Dillon & Vossen, 2015. The existing
hardware and software must be compliant with the Amazon AWS and they have to make
11 STUDENT NAME: , STUDENT ID:
Fig 3: Securing Cloud Data
(Source: Manvi, & Shyam, 2014, pp-424-440)
Question 4
4. Recommendations to Webb for protecting access to the following services that they
want to move to the Cloud
4.a. Their IaaS infrastructure
Webb Store if adopt the Amazon's AWS cloud services can get the best features can
conduct their business activities in the agile and effective way. They can conduct the
business activities in agile and efficient. Plus, they do not have to pay heavily for the
software, they do not have to pay for the hardware (Dillon & Vossen, 2015. The existing
hardware and software must be compliant with the Amazon AWS and they have to make
11 STUDENT NAME: , STUDENT ID:

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
few changes to enjoy the Amazon AWS services. Amazon has a global value and a global
name and upon trusting Amazon they can get the desired output which they want.
4.b. Their Ms SQL Server 2012 R2 cloud instance
Amazon RDS for the SQL server furnish some outstanding features so that the Webb
can enhance the SQL database work activities to the utmost. The physical security must be
implemented to assure safety for the software components and the hardware components
from illegal access (Varia & Mathew, 2014). The digital certificate is equally beneficial for
ensuring database security.
4.c. Their Cloud network infrastructure
Amazon furnishes the smart business solutions and advanced security solutions. The
latest configuration system from Amazon has the capability to cater best security facilities to
Webb (Sharma et al., 2017). The latest configuration from Amazon is also helpful to provide
the solutions to run the cloud apps and performs the correlated cloud-based task with ease.
12 STUDENT NAME: , STUDENT ID:
few changes to enjoy the Amazon AWS services. Amazon has a global value and a global
name and upon trusting Amazon they can get the desired output which they want.
4.b. Their Ms SQL Server 2012 R2 cloud instance
Amazon RDS for the SQL server furnish some outstanding features so that the Webb
can enhance the SQL database work activities to the utmost. The physical security must be
implemented to assure safety for the software components and the hardware components
from illegal access (Varia & Mathew, 2014). The digital certificate is equally beneficial for
ensuring database security.
4.c. Their Cloud network infrastructure
Amazon furnishes the smart business solutions and advanced security solutions. The
latest configuration system from Amazon has the capability to cater best security facilities to
Webb (Sharma et al., 2017). The latest configuration from Amazon is also helpful to provide
the solutions to run the cloud apps and performs the correlated cloud-based task with ease.
12 STUDENT NAME: , STUDENT ID:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
Fig 4: Amazon AWS and its services
(Source: Muthui & SISAT, 2013)
4.d. Their Cloud backup and restore infrastructure
Webb’s data can be transmitted through the secure channel this secure channel is
responsible for controlling data breaches (Gai, & Steenkamp, 2014). Also, the secure
channel is responsible for defending the hacktivist. Amazon AWS cloud solutions have the
potential to provide these advantageous solutions.
Conclusion
It can be concluded from the above discourse that Webb can be facilitated by the
advanced cloud solutions provided by Amazon. The risks, threats associated with cloud
platform have been discussed and as well as the risk mitigation has been detailed in the
report have been detailed as well.
13 STUDENT NAME: , STUDENT ID:
Fig 4: Amazon AWS and its services
(Source: Muthui & SISAT, 2013)
4.d. Their Cloud backup and restore infrastructure
Webb’s data can be transmitted through the secure channel this secure channel is
responsible for controlling data breaches (Gai, & Steenkamp, 2014). Also, the secure
channel is responsible for defending the hacktivist. Amazon AWS cloud solutions have the
potential to provide these advantageous solutions.
Conclusion
It can be concluded from the above discourse that Webb can be facilitated by the
advanced cloud solutions provided by Amazon. The risks, threats associated with cloud
platform have been discussed and as well as the risk mitigation has been detailed in the
report have been detailed as well.
13 STUDENT NAME: , STUDENT ID:

CLOUD COMPUTING STUDENT NAME: , STUDENT ID:
References
Azam, Abdollahzadehgan; Ab Razak Che Hussin; Gohary , Marjan Moshfegh Gohary &
Mahyar Amini (2013), The OrganizationalCritical Success Factors for Adopting Cloud
Computing in SMEs, Journal of Information Systems Research and Innovation (JISRI),
Volume 4, Issue 1, pp. 67-74.
Beck, M., Hao, W., & Campan, A. (2017, January). Accelerating the Mobile cloud: Using
Amazon Mobile Analytics and k-means clustering. In Computing and Communication
Workshop and Conference (CCWC), 2017 IEEE 7th Annual (pp. 1-7). IEEE.
Dillon, S., & Vossen, G. (2015). SaaS cloud computing in small and medium enterprises: A
comparison between Germany and New Zealand. International Journal of
Information Technology, Communications and Convergence, 3(2), 87-104.
Dinh, H. T., Lee, C., Niyato, D., & Wang, P. (2013). A survey of mobile cloud computing:
architecture, applications, and approaches. Wireless communications and mobile
computing, 13(18), 1587-1611.
Gai, K., & Steenkamp, A. (2014). A feasibility study of Platform-as-a-Service using cloud
computing for a global service organization. Journal of Information Systems Applied
Research, 7(3), 28.
Manvi, S. S., & Shyam, G. K. (2014). Resource management for Infrastructure as a Service
(IaaS) in cloud computing: A survey. Journal of Network and Computer
Applications, 41, 424-440.
Muthui, M., & SISAT, C. (2013). Amazon Web Services.
14 STUDENT NAME: , STUDENT ID:
References
Azam, Abdollahzadehgan; Ab Razak Che Hussin; Gohary , Marjan Moshfegh Gohary &
Mahyar Amini (2013), The OrganizationalCritical Success Factors for Adopting Cloud
Computing in SMEs, Journal of Information Systems Research and Innovation (JISRI),
Volume 4, Issue 1, pp. 67-74.
Beck, M., Hao, W., & Campan, A. (2017, January). Accelerating the Mobile cloud: Using
Amazon Mobile Analytics and k-means clustering. In Computing and Communication
Workshop and Conference (CCWC), 2017 IEEE 7th Annual (pp. 1-7). IEEE.
Dillon, S., & Vossen, G. (2015). SaaS cloud computing in small and medium enterprises: A
comparison between Germany and New Zealand. International Journal of
Information Technology, Communications and Convergence, 3(2), 87-104.
Dinh, H. T., Lee, C., Niyato, D., & Wang, P. (2013). A survey of mobile cloud computing:
architecture, applications, and approaches. Wireless communications and mobile
computing, 13(18), 1587-1611.
Gai, K., & Steenkamp, A. (2014). A feasibility study of Platform-as-a-Service using cloud
computing for a global service organization. Journal of Information Systems Applied
Research, 7(3), 28.
Manvi, S. S., & Shyam, G. K. (2014). Resource management for Infrastructure as a Service
(IaaS) in cloud computing: A survey. Journal of Network and Computer
Applications, 41, 424-440.
Muthui, M., & SISAT, C. (2013). Amazon Web Services.
14 STUDENT NAME: , STUDENT ID:
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





