An In-Depth Report on Cloud Computing and Virtualization Concepts
VerifiedAdded on 2024/05/29
|13
|1894
|248
Report
AI Summary
This report provides a comprehensive overview of cloud computing and virtualization, highlighting their combined impact on modern technology. It begins with an introduction to the necessity, feasibility, and pricing factors that drive the adoption of these technologies, emphasizing the shift towards online accessibility and cost-effectiveness. The report details various user access levels within a cloud-based system, including system administrators, teachers, and students, and outlines the types of data collected, such as personal information, income, and expenses. It further elaborates on the high-level processes involved in gathering, storing, accessing, and securing information within the system. The report also includes conceptual and process designs for a cloud-based system, illustrating the architecture with diagrams of user connections, network interfaces, and data flow, emphasizing security measures like firewalls and access management. The discussion covers the roles of gateway adapters, services, and event logs in ensuring data integrity and system security, referencing various sources to support its analysis of cloud computing and virtualization technologies.

Cloud Computing and Virtualisation
Cloud Computing
And
Virtualisation
1
Cloud Computing
And
Virtualisation
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing and Virtualisation
Summary
Cloud Computing [1] and Virtualization [2] both are futuristic technologies and when
combined together creates a deadly combination.
Cloud Computing is the usage of services such as – storage, software, networking, computing
resources over the Internet. Whereas, Virtualization is running multiple instances of an
application and making them available to multiple people or process using Virtual concept.
Virtualization runs multiple Operating Systems on a single physical Operating System and
shares hardware resources across all virtual Operating Systems and this is known as
Virtualization.
Virtualization achieved by using Virtual Machine in an isolated run time environment. So,
multiple virtual machines can run simultaneously on a single physical machine.
Cloud Computing takes Virtualization a one step ahead by making it available directly over
the internet rather than physically at premises. Using this mechanism, multiple people or
organizations can use same physical infrastructure on a shared basis.
1
Summary
Cloud Computing [1] and Virtualization [2] both are futuristic technologies and when
combined together creates a deadly combination.
Cloud Computing is the usage of services such as – storage, software, networking, computing
resources over the Internet. Whereas, Virtualization is running multiple instances of an
application and making them available to multiple people or process using Virtual concept.
Virtualization runs multiple Operating Systems on a single physical Operating System and
shares hardware resources across all virtual Operating Systems and this is known as
Virtualization.
Virtualization achieved by using Virtual Machine in an isolated run time environment. So,
multiple virtual machines can run simultaneously on a single physical machine.
Cloud Computing takes Virtualization a one step ahead by making it available directly over
the internet rather than physically at premises. Using this mechanism, multiple people or
organizations can use same physical infrastructure on a shared basis.
1

Cloud Computing and Virtualisation
Contents
Summary....................................................................................................................................1
Introduction................................................................................................................................3
User Access................................................................................................................................4
Data............................................................................................................................................5
Processes....................................................................................................................................7
....................................................................................................................................................7
Process Justification.................................................................................................................12
2
Contents
Summary....................................................................................................................................1
Introduction................................................................................................................................3
User Access................................................................................................................................4
Data............................................................................................................................................5
Processes....................................................................................................................................7
....................................................................................................................................................7
Process Justification.................................................................................................................12
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cloud Computing and Virtualisation
Introduction
Necessity, Feasibility and Pricing gave a rise to Cloud Computing [1] and Virtualization [2].
Due to a large number of consumers have an Internet Connection and prefer these things to
be available online. Due to the change in the consumer behaviour and perception, Cloud
Computing has taken a Leap.
Due to High Capital Expenditure, Maintenance Costs, High Physical Space Requirement,
gave a rose to Virtualization and combining this with Cloud Computing. This became a
fantastic combination, which addresses, Cost Factor, Easy and High Availability of
Resources over the Internet.
Virtualization used via utilizing Hypervisors. IT means multiple applications, Operating
Systems, can run on a single physical machine utilizing same System Hardware like CPU,
Memory, Disk Storage, etc. It also supports running multiple Operating systems concurrently
on a same physical server using Virtualization Software.
Majorly Virtualization is used to achieve Resources Utilization and now it is used for
Platforms.
And Cloud Computing makes these resources available on a shared basis to multiple users or
organizations. The platform, Infrastructure, Software are available On-Demand using
Platform as a Service, Infrastructure as a Service, and Software as a Service.
3
Introduction
Necessity, Feasibility and Pricing gave a rise to Cloud Computing [1] and Virtualization [2].
Due to a large number of consumers have an Internet Connection and prefer these things to
be available online. Due to the change in the consumer behaviour and perception, Cloud
Computing has taken a Leap.
Due to High Capital Expenditure, Maintenance Costs, High Physical Space Requirement,
gave a rose to Virtualization and combining this with Cloud Computing. This became a
fantastic combination, which addresses, Cost Factor, Easy and High Availability of
Resources over the Internet.
Virtualization used via utilizing Hypervisors. IT means multiple applications, Operating
Systems, can run on a single physical machine utilizing same System Hardware like CPU,
Memory, Disk Storage, etc. It also supports running multiple Operating systems concurrently
on a same physical server using Virtualization Software.
Majorly Virtualization is used to achieve Resources Utilization and now it is used for
Platforms.
And Cloud Computing makes these resources available on a shared basis to multiple users or
organizations. The platform, Infrastructure, Software are available On-Demand using
Platform as a Service, Infrastructure as a Service, and Software as a Service.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing and Virtualisation
User Access
Different kinds of users that would access ABC’s Cloud-Based System [3] are:
1. System Administrators
2. System Engineers
3. Support or Administrative Staff
4. Teachers
5. Research Associates
6. Course Students
7. Network Administrator
8. Database Administrator
9. Security Administrator
10. Cloud Administrator
11. HR
12. Finance Team
Data
Different types of data ABC collects [4] are:
1. Students Personal Information like
a. Date of Birth,
b. Date of Joining,
c. Date of Admission,
4
User Access
Different kinds of users that would access ABC’s Cloud-Based System [3] are:
1. System Administrators
2. System Engineers
3. Support or Administrative Staff
4. Teachers
5. Research Associates
6. Course Students
7. Network Administrator
8. Database Administrator
9. Security Administrator
10. Cloud Administrator
11. HR
12. Finance Team
Data
Different types of data ABC collects [4] are:
1. Students Personal Information like
a. Date of Birth,
b. Date of Joining,
c. Date of Admission,
4

Cloud Computing and Virtualisation
d. Date of Relieving,
e. Date of Passing Course,
f. Date of Enrolment,
g. Permanent Address,
h. Communication Address,
i. National Identifier/Social Security Number/National Insurance Number
j. Driving License Number
k. Full Name
l. Gender
m. Personal Nationality
n. Student Record Date Created
o. Student Record Cease Date
p. VIP Identifier (Very Important Person)
q. Photo of Student Enrolled
r. Passport Information
s. Race or Ethnic Origin
t. Email Address
u. Mobile number
v. Religion
w. Sexual Orientation (Male/Female)
x. Biometric Data
y. Country of Residence
z. Pin or Zip Code
aa. Associated Person Information like Emergency Contact Name and Emergency
Contact Number
bb. Signatures
cc. Qualifications
dd. Age
ee. Credit Card Details
ff. Bank Account Information
gg. Bills/Invoices
hh. Account Number
ii. User ID
5
d. Date of Relieving,
e. Date of Passing Course,
f. Date of Enrolment,
g. Permanent Address,
h. Communication Address,
i. National Identifier/Social Security Number/National Insurance Number
j. Driving License Number
k. Full Name
l. Gender
m. Personal Nationality
n. Student Record Date Created
o. Student Record Cease Date
p. VIP Identifier (Very Important Person)
q. Photo of Student Enrolled
r. Passport Information
s. Race or Ethnic Origin
t. Email Address
u. Mobile number
v. Religion
w. Sexual Orientation (Male/Female)
x. Biometric Data
y. Country of Residence
z. Pin or Zip Code
aa. Associated Person Information like Emergency Contact Name and Emergency
Contact Number
bb. Signatures
cc. Qualifications
dd. Age
ee. Credit Card Details
ff. Bank Account Information
gg. Bills/Invoices
hh. Account Number
ii. User ID
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cloud Computing and Virtualisation
jj. Student Enrollment Number
kk. Course Name Enrolled
ll. Status (Active/InActive)
mm. Course Pass/Failed
nn. Health Information
2. Income and Expenses
3. Partnerships
Processes
Please see High-Level Processes [5] [6] involved in ABC.
Cloud-Based System Design:
A) Conceptual Design for Cloud-based System Design [5] [6] [7]
6
ABC
Publishing
Information
Result
Accessing
Processing
Information
Securing
Information
Storing
Information
Updating
Information
Sharing
Gathering
Information
jj. Student Enrollment Number
kk. Course Name Enrolled
ll. Status (Active/InActive)
mm. Course Pass/Failed
nn. Health Information
2. Income and Expenses
3. Partnerships
Processes
Please see High-Level Processes [5] [6] involved in ABC.
Cloud-Based System Design:
A) Conceptual Design for Cloud-based System Design [5] [6] [7]
6
ABC
Publishing
Information
Result
Accessing
Processing
Information
Securing
Information
Storing
Information
Updating
Information
Sharing
Gathering
Information
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
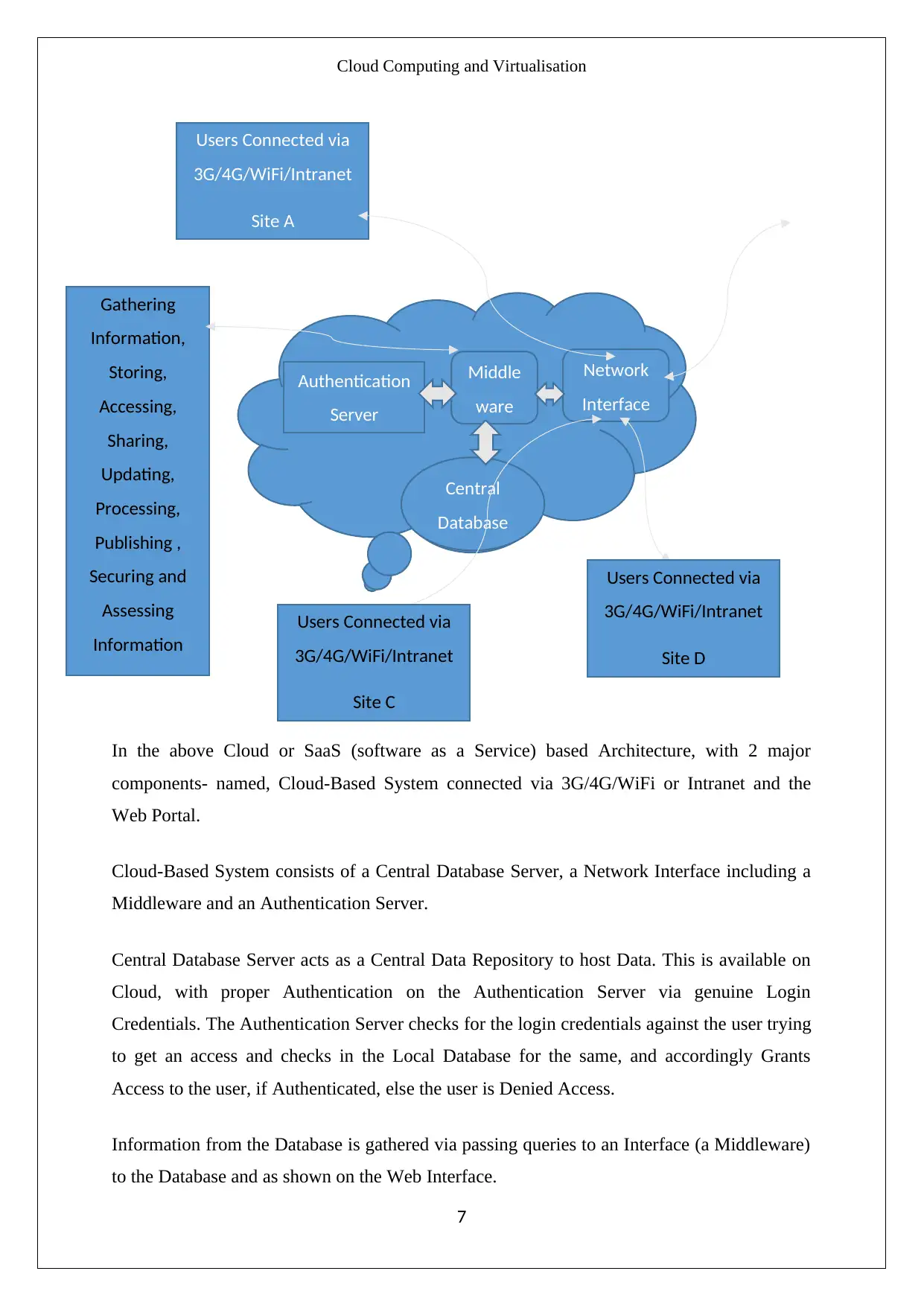
Cloud Computing and Virtualisation
In the above Cloud or SaaS (software as a Service) based Architecture, with 2 major
components- named, Cloud-Based System connected via 3G/4G/WiFi or Intranet and the
Web Portal.
Cloud-Based System consists of a Central Database Server, a Network Interface including a
Middleware and an Authentication Server.
Central Database Server acts as a Central Data Repository to host Data. This is available on
Cloud, with proper Authentication on the Authentication Server via genuine Login
Credentials. The Authentication Server checks for the login credentials against the user trying
to get an access and checks in the Local Database for the same, and accordingly Grants
Access to the user, if Authenticated, else the user is Denied Access.
Information from the Database is gathered via passing queries to an Interface (a Middleware)
to the Database and as shown on the Web Interface.
7
Users Connected via
3G/4G/WiFi/Intranet
Site A
Central
Database
Network
Interface
Middle
ware
Authentication
Server
Users Connected via
3G/4G/WiFi/Intranet
Site C
Users Connected via
3G/4G/WiFi/Intranet
Site D
Gathering
Information,
Storing,
Accessing,
Sharing,
Updating,
Processing,
Publishing ,
Securing and
Assessing
Information
In the above Cloud or SaaS (software as a Service) based Architecture, with 2 major
components- named, Cloud-Based System connected via 3G/4G/WiFi or Intranet and the
Web Portal.
Cloud-Based System consists of a Central Database Server, a Network Interface including a
Middleware and an Authentication Server.
Central Database Server acts as a Central Data Repository to host Data. This is available on
Cloud, with proper Authentication on the Authentication Server via genuine Login
Credentials. The Authentication Server checks for the login credentials against the user trying
to get an access and checks in the Local Database for the same, and accordingly Grants
Access to the user, if Authenticated, else the user is Denied Access.
Information from the Database is gathered via passing queries to an Interface (a Middleware)
to the Database and as shown on the Web Interface.
7
Users Connected via
3G/4G/WiFi/Intranet
Site A
Central
Database
Network
Interface
Middle
ware
Authentication
Server
Users Connected via
3G/4G/WiFi/Intranet
Site C
Users Connected via
3G/4G/WiFi/Intranet
Site D
Gathering
Information,
Storing,
Accessing,
Sharing,
Updating,
Processing,
Publishing ,
Securing and
Assessing
Information

Cloud Computing and Virtualisation
Middleware is hosted on Cloud to check for Web or Network traffic coming into the Interface
to facilitate the communication transactions between the Central Database and the Web
Portal. This Cloud-based Interface is equipped to handle queries coming in via 3G/4G, WiFi
or Intranet.
Simultaneously, it is equipped to handle multiple transactions at the same time.
Cloud-based Authentication Server, handles all the Authentication and Authorization for the
queries. Any Authenticated User as per the Role Based Access Policies (RBAC) can perform
operations like Storing, Searching, Updating, Accessing, Securing, Sharing, Transferring,
Publishing Information.
B) Process Design [6] [7]
8
Users
(Students/Staff/Teachers/Administrators)
Middleware is hosted on Cloud to check for Web or Network traffic coming into the Interface
to facilitate the communication transactions between the Central Database and the Web
Portal. This Cloud-based Interface is equipped to handle queries coming in via 3G/4G, WiFi
or Intranet.
Simultaneously, it is equipped to handle multiple transactions at the same time.
Cloud-based Authentication Server, handles all the Authentication and Authorization for the
queries. Any Authenticated User as per the Role Based Access Policies (RBAC) can perform
operations like Storing, Searching, Updating, Accessing, Securing, Sharing, Transferring,
Publishing Information.
B) Process Design [6] [7]
8
Users
(Students/Staff/Teachers/Administrators)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
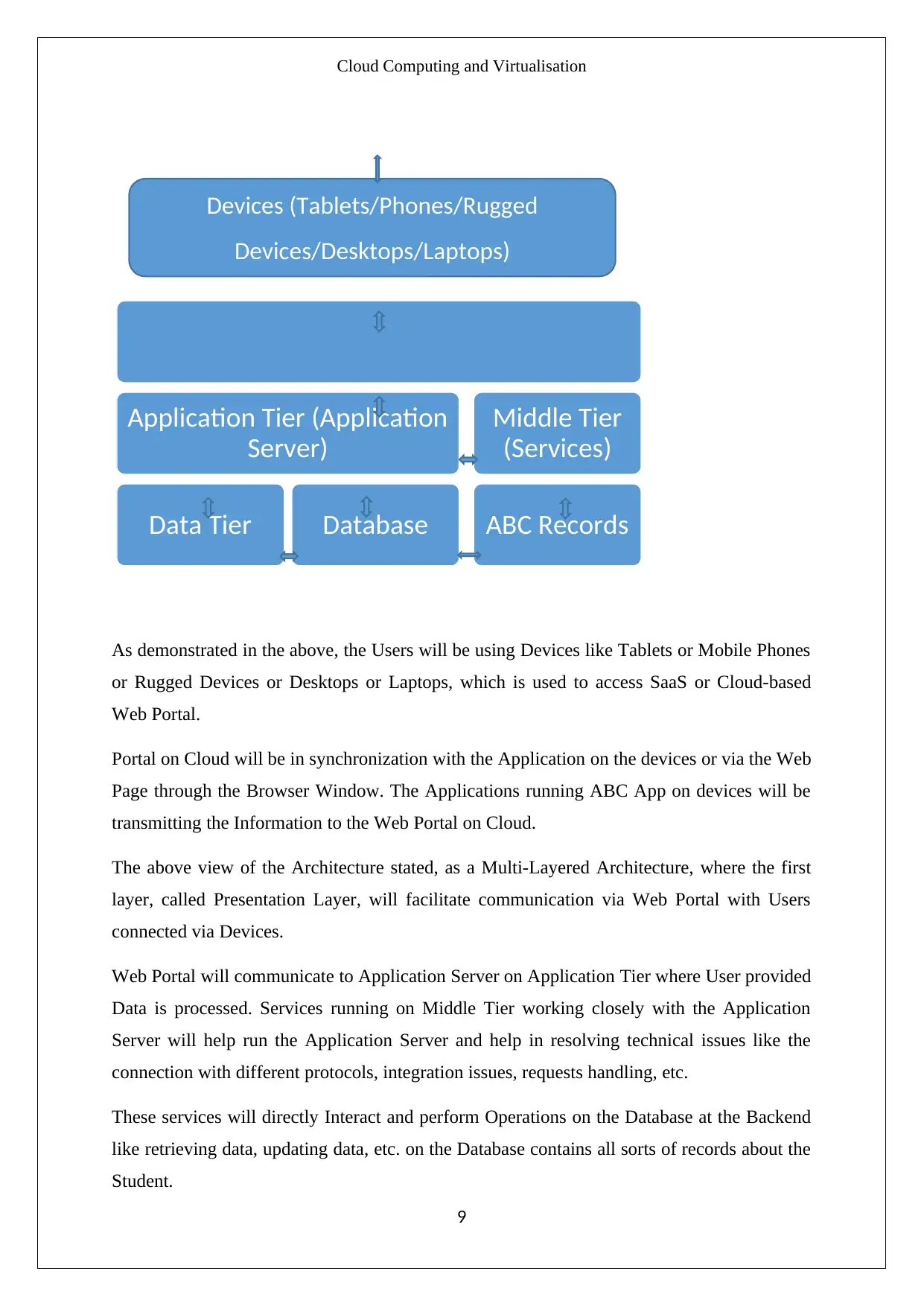
Cloud Computing and Virtualisation
As demonstrated in the above, the Users will be using Devices like Tablets or Mobile Phones
or Rugged Devices or Desktops or Laptops, which is used to access SaaS or Cloud-based
Web Portal.
Portal on Cloud will be in synchronization with the Application on the devices or via the Web
Page through the Browser Window. The Applications running ABC App on devices will be
transmitting the Information to the Web Portal on Cloud.
The above view of the Architecture stated, as a Multi-Layered Architecture, where the first
layer, called Presentation Layer, will facilitate communication via Web Portal with Users
connected via Devices.
Web Portal will communicate to Application Server on Application Tier where User provided
Data is processed. Services running on Middle Tier working closely with the Application
Server will help run the Application Server and help in resolving technical issues like the
connection with different protocols, integration issues, requests handling, etc.
These services will directly Interact and perform Operations on the Database at the Backend
like retrieving data, updating data, etc. on the Database contains all sorts of records about the
Student.
9
Application Tier (Application
Server)
Data Tier Database
Middle Tier
(Services)
ABC Records
Devices (Tablets/Phones/Rugged
Devices/Desktops/Laptops)
As demonstrated in the above, the Users will be using Devices like Tablets or Mobile Phones
or Rugged Devices or Desktops or Laptops, which is used to access SaaS or Cloud-based
Web Portal.
Portal on Cloud will be in synchronization with the Application on the devices or via the Web
Page through the Browser Window. The Applications running ABC App on devices will be
transmitting the Information to the Web Portal on Cloud.
The above view of the Architecture stated, as a Multi-Layered Architecture, where the first
layer, called Presentation Layer, will facilitate communication via Web Portal with Users
connected via Devices.
Web Portal will communicate to Application Server on Application Tier where User provided
Data is processed. Services running on Middle Tier working closely with the Application
Server will help run the Application Server and help in resolving technical issues like the
connection with different protocols, integration issues, requests handling, etc.
These services will directly Interact and perform Operations on the Database at the Backend
like retrieving data, updating data, etc. on the Database contains all sorts of records about the
Student.
9
Application Tier (Application
Server)
Data Tier Database
Middle Tier
(Services)
ABC Records
Devices (Tablets/Phones/Rugged
Devices/Desktops/Laptops)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
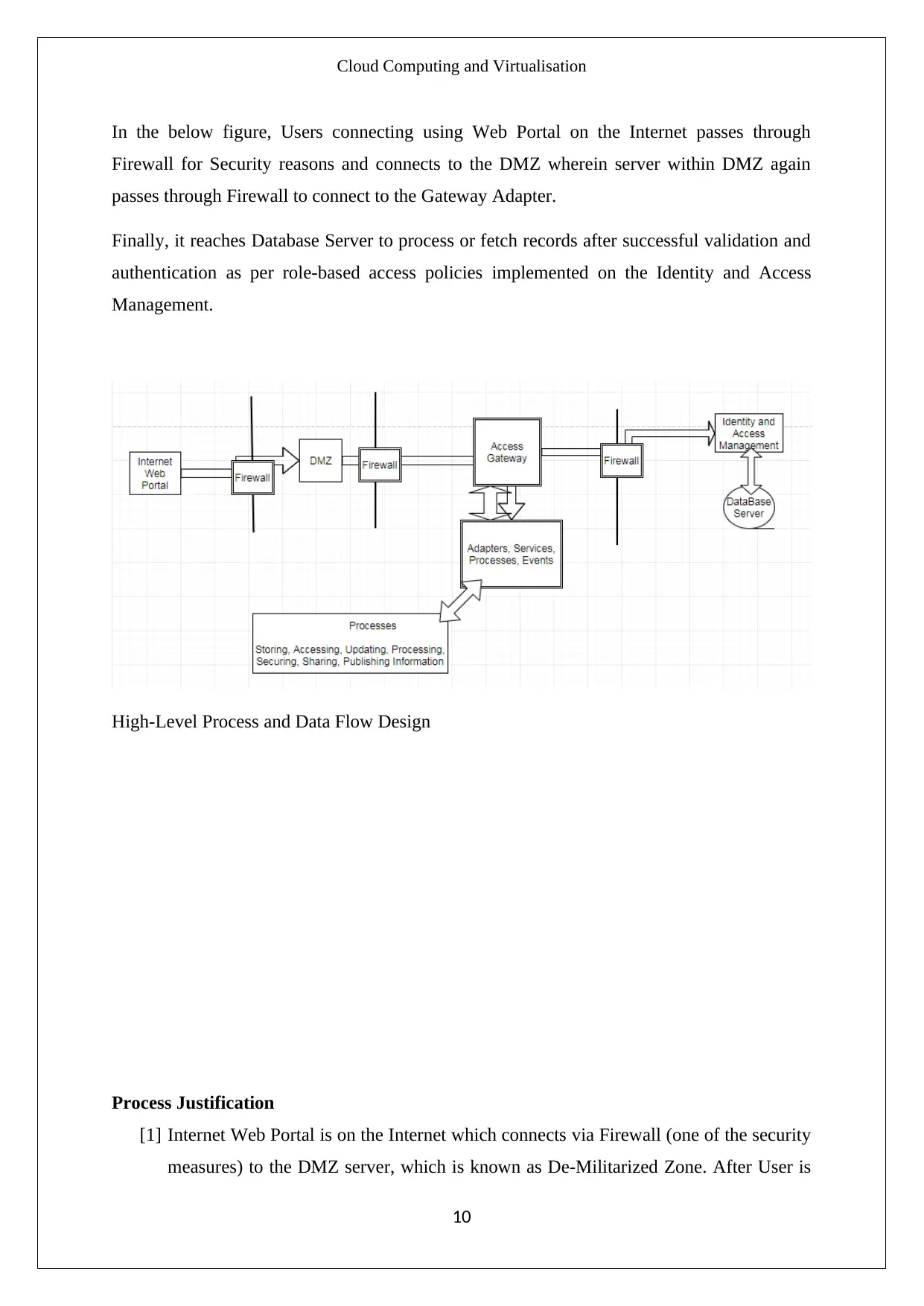
Cloud Computing and Virtualisation
In the below figure, Users connecting using Web Portal on the Internet passes through
Firewall for Security reasons and connects to the DMZ wherein server within DMZ again
passes through Firewall to connect to the Gateway Adapter.
Finally, it reaches Database Server to process or fetch records after successful validation and
authentication as per role-based access policies implemented on the Identity and Access
Management.
High-Level Process and Data Flow Design
Process Justification
[1] Internet Web Portal is on the Internet which connects via Firewall (one of the security
measures) to the DMZ server, which is known as De-Militarized Zone. After User is
10
In the below figure, Users connecting using Web Portal on the Internet passes through
Firewall for Security reasons and connects to the DMZ wherein server within DMZ again
passes through Firewall to connect to the Gateway Adapter.
Finally, it reaches Database Server to process or fetch records after successful validation and
authentication as per role-based access policies implemented on the Identity and Access
Management.
High-Level Process and Data Flow Design
Process Justification
[1] Internet Web Portal is on the Internet which connects via Firewall (one of the security
measures) to the DMZ server, which is known as De-Militarized Zone. After User is
10

Cloud Computing and Virtualisation
being Authenticated and Authorized from the DMZ Server it again passes via Firewall
(meant for greater Security) to the Access Gateway which in turn connects with
Adapters. Adapters connect with Services and Services initiates Events and events
initiates Processes in the background as and when called for.
Processes being triggered such as Storing information of a Student, Updating
Records, Publishing Records, etc. which in turn passes again via Gateway Adapters to
collect record from the Database only after conforming the authenticated users via
Identity and Access Management.
[2] Gateway Adapters have multiple roles. They serve as Encrypting and Decrypting
Agent for a Service and controls the behaviour of the processes requested for. They
also work as a mediator between Database and Processes called for. Events logs
generated via events actions are kept in the Database for Log Analysis for Security
Reasons. Even the Identity and Access Management System also keeps records of the
Authenticated and un-authorised users accessing the system including Timestamp.
Any Authenticated User as per the Role Based Access Policies (RBAC) can perform
operations like Storing, Searching, Updating, Accessing, Securing, Sharing,
Transferring, Publishing Information.
References
11
being Authenticated and Authorized from the DMZ Server it again passes via Firewall
(meant for greater Security) to the Access Gateway which in turn connects with
Adapters. Adapters connect with Services and Services initiates Events and events
initiates Processes in the background as and when called for.
Processes being triggered such as Storing information of a Student, Updating
Records, Publishing Records, etc. which in turn passes again via Gateway Adapters to
collect record from the Database only after conforming the authenticated users via
Identity and Access Management.
[2] Gateway Adapters have multiple roles. They serve as Encrypting and Decrypting
Agent for a Service and controls the behaviour of the processes requested for. They
also work as a mediator between Database and Processes called for. Events logs
generated via events actions are kept in the Database for Log Analysis for Security
Reasons. Even the Identity and Access Management System also keeps records of the
Authenticated and un-authorised users accessing the system including Timestamp.
Any Authenticated User as per the Role Based Access Policies (RBAC) can perform
operations like Storing, Searching, Updating, Accessing, Securing, Sharing,
Transferring, Publishing Information.
References
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




