DTGOV Case Study: Cloud Computing Architecture & IT Redesign
VerifiedAdded on 2023/03/31
|13
|2334
|59
Case Study
AI Summary
This case study addresses the challenges faced by DTGOV, a public company seeking to improve its IT operations and business model. The solution recommends a hybrid cloud model incorporating dynamic scalability architecture and service load balancing to enhance customer satisfaction and performance. Key aspects discussed include the risks associated with hybrid cloud strategies, necessary information security steps (such as encryption and secure login functions), backup and disaster recovery planning, application resilience, and an operations checklist. The goal is to redesign DTGOV's IT operations to increase efficiency, minimize costs, and ease management burdens, leveraging services like AWS Lambda or Azure Functions, Containers, Data Services, and Cloud Edge capability and monitoring.

Running head: CLOUD COMPUTING ARCHITECTURE
CLOUD COMPUTING ARCHITECTURE
Name of the Student
Name of the University
Author Note
CLOUD COMPUTING ARCHITECTURE
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD COMPUTING ARCHITECTURE 1
Executive summary:
The purpose of this paper is to discuss the changes that DTGOV need to incorporate in the
business model and IT for improving the functionality of the organisation. The architectures
that are recommended for DTGOV are the dynamic scalability architecture and the service
load balancing. There are some major benefits of the architectures for helping the
organisation for improving the customer satisfaction as well as for improving its
performance. The implementation of the hybrid cloud model in the business model of them
that promises for improving the growth for the DTGOV.
Executive summary:
The purpose of this paper is to discuss the changes that DTGOV need to incorporate in the
business model and IT for improving the functionality of the organisation. The architectures
that are recommended for DTGOV are the dynamic scalability architecture and the service
load balancing. There are some major benefits of the architectures for helping the
organisation for improving the customer satisfaction as well as for improving its
performance. The implementation of the hybrid cloud model in the business model of them
that promises for improving the growth for the DTGOV.

2CLOUD COMPUTING ARCHITECTURE
Table of Contents
Introduction:...............................................................................................................................3
Discussion:.................................................................................................................................3
Risks of hybrid cloud strategy................................................................................................4
Information security steps and the controls...........................................................................5
Recommends that are to be included.....................................................................................6
Backup and disaster recovery.............................................................................................6
Application resilience:...........................................................................................................7
Operations checklist...............................................................................................................7
Conclusion:................................................................................................................................8
Table of Contents
Introduction:...............................................................................................................................3
Discussion:.................................................................................................................................3
Risks of hybrid cloud strategy................................................................................................4
Information security steps and the controls...........................................................................5
Recommends that are to be included.....................................................................................6
Backup and disaster recovery.............................................................................................6
Application resilience:...........................................................................................................7
Operations checklist...............................................................................................................7
Conclusion:................................................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD COMPUTING ARCHITECTURE
Introduction:
DTGOV is a public company that is having an autonomous structure for the
management and the company is having the flexibility to govern IT operations and structures.
At present, the company is supplying the IT infrastructure and services to the external public
sector organisations. The services that are provided by DTGOV is including the server
hosting and server co-location. Few consumers of DTGOV have outsources the operations,
maintenance as well as the application development to the DTGOV. The organisation is
understanding the present situation of it as well as stand in the in the world of IT has taken up
several protocols. The working of the company is gaining slowly completely as well as the
management of the organisation has been becoming so much hard for the company. It has
lead for mismanaging in the organisational system as well as the inflation of the costing. The
purpose of this paper is to discuss the changes that DTGOV need to incorporate in the
business model and IT for improving the functionality of the organisation. The architectures
that are recommended for DTGOV are the dynamic scalability architecture and the service
load balancing. There are some major benefits of the architectures for helping the
organisation for improving the customer satisfaction as well as for improving its
performance. The implementation of the hybrid cloud model in the business model of them
that promises for improving the growth for the DTGOV. The management has decided for
redesigning the operation of the IT as well as the organisational management model for
increasing the efficiency of the company and minimizing the costing as well as easing out the
work of the management.
Discussion:
At present, the organisations are becoming global organizations increasingly. The
organizations do not restrict themselves commonly in the business conducting in any of the
Introduction:
DTGOV is a public company that is having an autonomous structure for the
management and the company is having the flexibility to govern IT operations and structures.
At present, the company is supplying the IT infrastructure and services to the external public
sector organisations. The services that are provided by DTGOV is including the server
hosting and server co-location. Few consumers of DTGOV have outsources the operations,
maintenance as well as the application development to the DTGOV. The organisation is
understanding the present situation of it as well as stand in the in the world of IT has taken up
several protocols. The working of the company is gaining slowly completely as well as the
management of the organisation has been becoming so much hard for the company. It has
lead for mismanaging in the organisational system as well as the inflation of the costing. The
purpose of this paper is to discuss the changes that DTGOV need to incorporate in the
business model and IT for improving the functionality of the organisation. The architectures
that are recommended for DTGOV are the dynamic scalability architecture and the service
load balancing. There are some major benefits of the architectures for helping the
organisation for improving the customer satisfaction as well as for improving its
performance. The implementation of the hybrid cloud model in the business model of them
that promises for improving the growth for the DTGOV. The management has decided for
redesigning the operation of the IT as well as the organisational management model for
increasing the efficiency of the company and minimizing the costing as well as easing out the
work of the management.
Discussion:
At present, the organisations are becoming global organizations increasingly. The
organizations do not restrict themselves commonly in the business conducting in any of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CLOUD COMPUTING ARCHITECTURE
locations. It is the same situation with the DTGOV Company who have a thought for
expanding the business of them as well as increase the availability of the information for all
of the workers as well as the consumers of the organization.
Risks of hybrid cloud strategy
By the oversimplified definition, the hybrid cloud strategy could be characterized as
the mix of the both private as well as the public based cloud. The hybrid cloud is significantly
the powerful blend of the private as well as the open cloud which has been bound together by
either institutionalized or the restrictive innovation which helps in empowering the
compactness of that application as well as the information. This might be the blend of the
private based cloud that is placed inside the association with more than one suppliers of the
open cloud or the private cloud, which is facilitated on any of the premises of the outsider
with having more than suppliers of the open cloud. This has been seen that the
administrations of the open cloud neglects for meeting the IT as well as the necessities of the
matter of some of the business associations. Any condition of the mixture cloud might
associate in gathering the prerequisites. In a few techniques, the crossover cloud might be
considered, as the transitional stage like the endeavours gets ready to move dominant part of
the remaining tasks to the open mists. The open mists is developing to be progressively well
known lately. Denied of the keeping up of any server farm, open cloud significantly permits
the practically moment arrangement of the asset and the speedy scaling. The Amazon EC2
which is the result of Amazon that has progressively added to advancement of the open cloud
as well as this has been considered among all of the principal arrangement of the open cloud.
Besides, not exclusively the development of the cloud network is occurring yet number of
scrutinizes is essentially expanding. In particular, not exclusively in the term of the
information protection as well as the security, yet this is also considered in different themes
like the seller locking in, the accessibility, as well as the interoperability or the open cloud
locations. It is the same situation with the DTGOV Company who have a thought for
expanding the business of them as well as increase the availability of the information for all
of the workers as well as the consumers of the organization.
Risks of hybrid cloud strategy
By the oversimplified definition, the hybrid cloud strategy could be characterized as
the mix of the both private as well as the public based cloud. The hybrid cloud is significantly
the powerful blend of the private as well as the open cloud which has been bound together by
either institutionalized or the restrictive innovation which helps in empowering the
compactness of that application as well as the information. This might be the blend of the
private based cloud that is placed inside the association with more than one suppliers of the
open cloud or the private cloud, which is facilitated on any of the premises of the outsider
with having more than suppliers of the open cloud. This has been seen that the
administrations of the open cloud neglects for meeting the IT as well as the necessities of the
matter of some of the business associations. Any condition of the mixture cloud might
associate in gathering the prerequisites. In a few techniques, the crossover cloud might be
considered, as the transitional stage like the endeavours gets ready to move dominant part of
the remaining tasks to the open mists. The open mists is developing to be progressively well
known lately. Denied of the keeping up of any server farm, open cloud significantly permits
the practically moment arrangement of the asset and the speedy scaling. The Amazon EC2
which is the result of Amazon that has progressively added to advancement of the open cloud
as well as this has been considered among all of the principal arrangement of the open cloud.
Besides, not exclusively the development of the cloud network is occurring yet number of
scrutinizes is essentially expanding. In particular, not exclusively in the term of the
information protection as well as the security, yet this is also considered in different themes
like the seller locking in, the accessibility, as well as the interoperability or the open cloud
5CLOUD COMPUTING ARCHITECTURE
conveys the characteristic dangers. Despite the fact that the hybrid mists covers the huge
offer and it likewise empowers the few chances, it involves the critical difficulties as well as
the problems that are needed to be considered as well as the best possible moderation plans
that are needed to be executed. Specially, because of the predominant developing nature,
there exist some difficulties of the mixture cloud methodology that are:
Cost: This challenge is the significant dangers that must be considered that is for the correct
execution of that cloud system in the association, as the framework of the hybrid cloud needs
both the neighborhood server farm just as the additional remote assets from the specialist
organization of cloud. It is regularly the most referenced advantage of the distributed
computing that the autonomy of the server farm do not hold fundamentally valid for the
hybrid conditions.
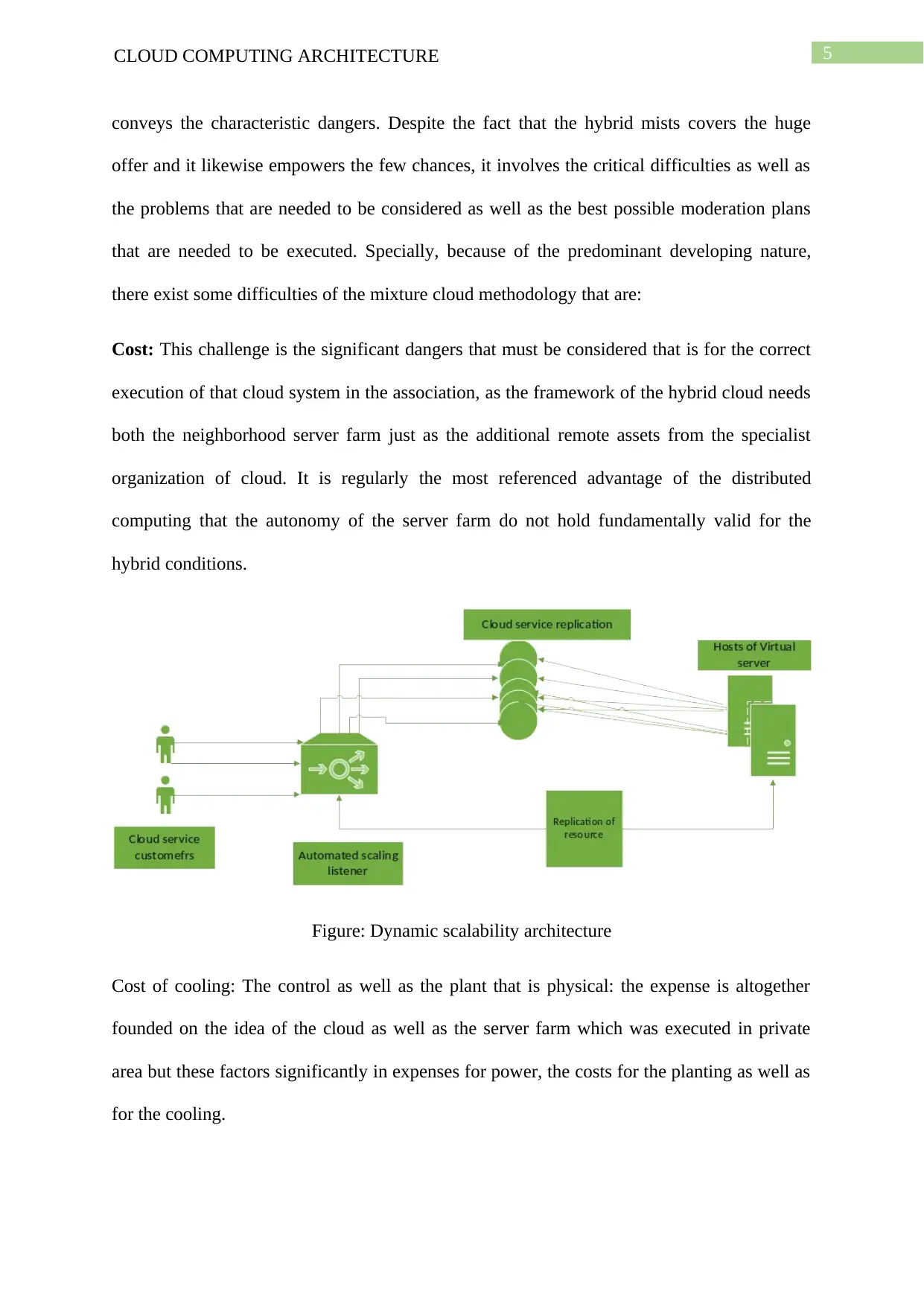
Figure: Dynamic scalability architecture
Cost of cooling: The control as well as the plant that is physical: the expense is altogether
founded on the idea of the cloud as well as the server farm which was executed in private
area but these factors significantly in expenses for power, the costs for the planting as well as
for the cooling.
conveys the characteristic dangers. Despite the fact that the hybrid mists covers the huge
offer and it likewise empowers the few chances, it involves the critical difficulties as well as
the problems that are needed to be considered as well as the best possible moderation plans
that are needed to be executed. Specially, because of the predominant developing nature,
there exist some difficulties of the mixture cloud methodology that are:
Cost: This challenge is the significant dangers that must be considered that is for the correct
execution of that cloud system in the association, as the framework of the hybrid cloud needs
both the neighborhood server farm just as the additional remote assets from the specialist
organization of cloud. It is regularly the most referenced advantage of the distributed
computing that the autonomy of the server farm do not hold fundamentally valid for the
hybrid conditions.
Figure: Dynamic scalability architecture
Cost of cooling: The control as well as the plant that is physical: the expense is altogether
founded on the idea of the cloud as well as the server farm which was executed in private
area but these factors significantly in expenses for power, the costs for the planting as well as
for the cooling.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD COMPUTING ARCHITECTURE
Operational costs: The cloud-based environments involves the lower expenses of the
equipment activities because of the way in which the virtualisation was accomplished for the
server farms as well as there are critical dangers of the blackout, which might be moved
towards the outside suppliers. The real tasks costs related with the product the executives,
besides, wins comparative in the IaaS situations and it diminishes with the expansion inside
deliberation level.
Information security steps and the controls
As the organization is aiming to convey the IaaS an instance of the AWS, this is fundamental
for executing the examination that is extension; of the security, related problems that occur in
AWS based workspace. This might be seen that the serious problem of the AWS workspace
is the information ruptures as well as the problem is the developing worry for association
who could actualized the cloud that is in the organizations. The prescribed advances as well
as the controls which are needed to be incorporated into the business are as follows:
Encryption: As the majority of the information might be transmitted that is to the clients
utilizing the web, there existed the real prerequisite of encoding every one of the information
that must be sent by the web. The security arrangement for rehearsing the execution of the
encryption that is fundamentally significant for the association.
Recognizable proof of the dependable administrations: besides, this has been found
that the validation convention might be considered like the methodology for the personality.
This is significantly needed by the association to execute the correct steps of the security as
well as the controls that are for the best possible guaranteeing that the administrations which
have been taken from the specialist organizations are keeping up the information protection.
Secure login functions: There is the significant necessity of the use of the solid secret phrase
and the qualifications for picking up the powerful anticipation from a the unapproved access
Operational costs: The cloud-based environments involves the lower expenses of the
equipment activities because of the way in which the virtualisation was accomplished for the
server farms as well as there are critical dangers of the blackout, which might be moved
towards the outside suppliers. The real tasks costs related with the product the executives,
besides, wins comparative in the IaaS situations and it diminishes with the expansion inside
deliberation level.
Information security steps and the controls
As the organization is aiming to convey the IaaS an instance of the AWS, this is fundamental
for executing the examination that is extension; of the security, related problems that occur in
AWS based workspace. This might be seen that the serious problem of the AWS workspace
is the information ruptures as well as the problem is the developing worry for association
who could actualized the cloud that is in the organizations. The prescribed advances as well
as the controls which are needed to be incorporated into the business are as follows:
Encryption: As the majority of the information might be transmitted that is to the clients
utilizing the web, there existed the real prerequisite of encoding every one of the information
that must be sent by the web. The security arrangement for rehearsing the execution of the
encryption that is fundamentally significant for the association.
Recognizable proof of the dependable administrations: besides, this has been found
that the validation convention might be considered like the methodology for the personality.
This is significantly needed by the association to execute the correct steps of the security as
well as the controls that are for the best possible guaranteeing that the administrations which
have been taken from the specialist organizations are keeping up the information protection.
Secure login functions: There is the significant necessity of the use of the solid secret phrase
and the qualifications for picking up the powerful anticipation from a the unapproved access
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CLOUD COMPUTING ARCHITECTURE
of the considerable number of work areas by any client where the important and delicate data
of the association has been put away.
Recommends that are to be included
Backup and disaster recovery
The uses of the association which have been facilitated into the haze of the specialist
organization involves the unmistakable need of the ability of the recuperation of the
information amid the circumstance of any calamity as well as this is needed to be broadly
associated with greater part of the reasons for the prerequisite connected with the area of the
distributed storage topographically, the recuperation focuses alongside the ideal opportunity
for the viable recuperation, which plays out the powerful checking of the physical closeness
of the locales of the debacle recuperation. Any viable system of catastrophe recuperation
predominantly incorporates the sort of the DR that is needed to be incorporated for the
affirming of the application re-establishing amid the circumstance of any fiasco.
The strategies alongside the properties that are a part of the AWS, which are needed
to be incorporated inside the BCP for the powerful usage of the proficient DR system,
incorporates:
Appropriate use of the Amazon Route R3 for dealing with the circumstance of the territorial
failover that may be founded on DNS.
of the considerable number of work areas by any client where the important and delicate data
of the association has been put away.
Recommends that are to be included
Backup and disaster recovery
The uses of the association which have been facilitated into the haze of the specialist
organization involves the unmistakable need of the ability of the recuperation of the
information amid the circumstance of any calamity as well as this is needed to be broadly
associated with greater part of the reasons for the prerequisite connected with the area of the
distributed storage topographically, the recuperation focuses alongside the ideal opportunity
for the viable recuperation, which plays out the powerful checking of the physical closeness
of the locales of the debacle recuperation. Any viable system of catastrophe recuperation
predominantly incorporates the sort of the DR that is needed to be incorporated for the
affirming of the application re-establishing amid the circumstance of any fiasco.
The strategies alongside the properties that are a part of the AWS, which are needed
to be incorporated inside the BCP for the powerful usage of the proficient DR system,
incorporates:
Appropriate use of the Amazon Route R3 for dealing with the circumstance of the territorial
failover that may be founded on DNS.

8CLOUD COMPUTING ARCHITECTURE
Figure: Resource pooling architecture:
Saved occasions of the Amazon EC2 could help in the holding the real limit of the DR in any
remote area.
Application resilience:
The usage of the mixture cloud is essentially significant for the organization for the different
reasons. The cloud based environments involves the lower expenses of the equipment
activities because of the way in which the virtualisation was accomplished for the server
farms as well as there are critical dangers of the blackout which might be moved towards the
outside suppliers. The real tasks costs related with the product the executives, besides, wins
comparative in the IaaS situations and it diminishes with the expansion inside deliberation
level.
Figure: Resource pooling architecture:
Saved occasions of the Amazon EC2 could help in the holding the real limit of the DR in any
remote area.
Application resilience:
The usage of the mixture cloud is essentially significant for the organization for the different
reasons. The cloud based environments involves the lower expenses of the equipment
activities because of the way in which the virtualisation was accomplished for the server
farms as well as there are critical dangers of the blackout which might be moved towards the
outside suppliers. The real tasks costs related with the product the executives, besides, wins
comparative in the IaaS situations and it diminishes with the expansion inside deliberation
level.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9CLOUD COMPUTING ARCHITECTURE
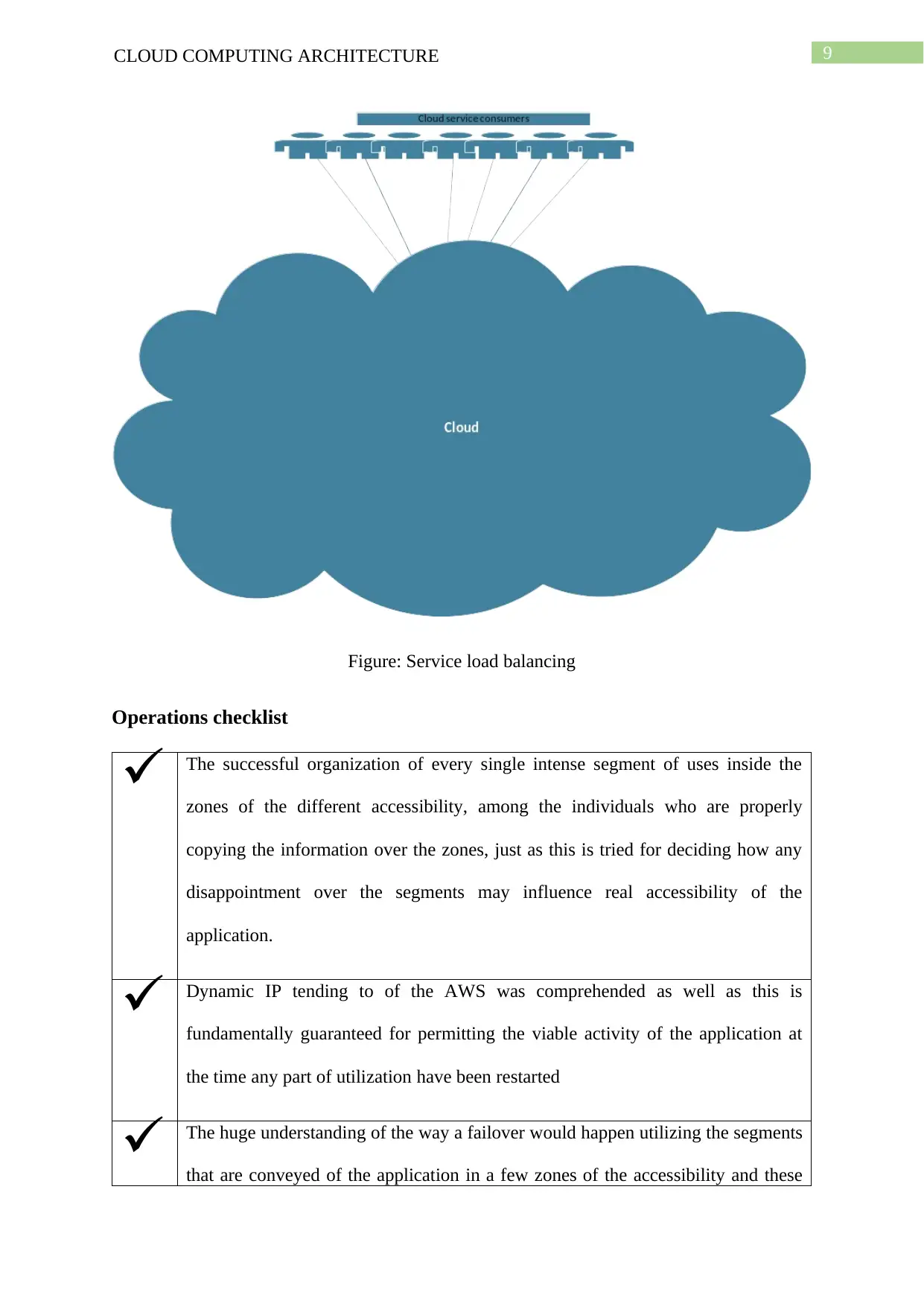
Figure: Service load balancing
Operations checklist
The successful organization of every single intense segment of uses inside the
zones of the different accessibility, among the individuals who are properly
copying the information over the zones, just as this is tried for deciding how any
disappointment over the segments may influence real accessibility of the
application.
Dynamic IP tending to of the AWS was comprehended as well as this is
fundamentally guaranteed for permitting the viable activity of the application at
the time any part of utilization have been restarted
The huge understanding of the way a failover would happen utilizing the segments
that are conveyed of the application in a few zones of the accessibility and these
Figure: Service load balancing
Operations checklist
The successful organization of every single intense segment of uses inside the
zones of the different accessibility, among the individuals who are properly
copying the information over the zones, just as this is tried for deciding how any
disappointment over the segments may influence real accessibility of the
application.
Dynamic IP tending to of the AWS was comprehended as well as this is
fundamentally guaranteed for permitting the viable activity of the application at
the time any part of utilization have been restarted
The huge understanding of the way a failover would happen utilizing the segments
that are conveyed of the application in a few zones of the accessibility and these
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CLOUD COMPUTING ARCHITECTURE
are using the Elastic Load Balancing or the outsider just as versatile IP addresses
wherever it is suitable.
The critical picking up of information in regards to the cases of the Amazon EBS
that could be upheld versus every one of the examples that could be store
sponsored has been done and most fitting stockpiling kind has been picked with
the best possible examination and increase the significant comprehension of
aftereffects of the information assurance, reinforcement and the recuperation.
Usage of CNAME records could be executed for the powerful mapping of the
DNS name of Elastic burden adjusting or pails of the Amazon S3.
Conclusion:
Thus, it can be concluded that the working of the company is gaining slowly completely as
well as the management of the organisation has been becoming so much hard for the
company. It has lead for mismanaging in the organisational system as well as the inflation of
the costing. The architectures that are recommended for DTGOV are the dynamic scalability
architecture and the service load balancing. There are some major benefits of the
architectures for helping the organisation for improving the customer satisfaction as well as
for improving its performance. The implementation of the hybrid cloud model in the business
model of them that promises for improving the growth for the DTGOV. The management has
decided for redesigning the operation of the IT as well as the organisational management
model for increasing the efficiency of the company and minimizing the costing as well as
easing out the work of the management.
are using the Elastic Load Balancing or the outsider just as versatile IP addresses
wherever it is suitable.
The critical picking up of information in regards to the cases of the Amazon EBS
that could be upheld versus every one of the examples that could be store
sponsored has been done and most fitting stockpiling kind has been picked with
the best possible examination and increase the significant comprehension of
aftereffects of the information assurance, reinforcement and the recuperation.
Usage of CNAME records could be executed for the powerful mapping of the
DNS name of Elastic burden adjusting or pails of the Amazon S3.
Conclusion:
Thus, it can be concluded that the working of the company is gaining slowly completely as
well as the management of the organisation has been becoming so much hard for the
company. It has lead for mismanaging in the organisational system as well as the inflation of
the costing. The architectures that are recommended for DTGOV are the dynamic scalability
architecture and the service load balancing. There are some major benefits of the
architectures for helping the organisation for improving the customer satisfaction as well as
for improving its performance. The implementation of the hybrid cloud model in the business
model of them that promises for improving the growth for the DTGOV. The management has
decided for redesigning the operation of the IT as well as the organisational management
model for increasing the efficiency of the company and minimizing the costing as well as
easing out the work of the management.

11CLOUD COMPUTING ARCHITECTURE
References:
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Carlin, S., & Curran, K. (2013). Cloud computing security. In Pervasive and Ubiquitous
Technology Innovations for Ambient Intelligence Environments (pp. 12-17). IGI
Global.
Hashizume, K., Rosado, D. G., Fernández-Medina, E., & Fernandez, E. B. (2013). An
analysis of security issues for cloud computing. Journal of internet services and
applications, 4(1), 5.
Khalil, I., Khreishah, A., & Azeem, M. (2014). Cloud computing security: A
survey. Computers, 3(1), 1-35.
Modi, C., Patel, D., Borisaniya, B., Patel, A., & Rajarajan, M. (2013). A survey on security
issues and solutions at different layers of Cloud computing. The journal of
supercomputing, 63(2), 561-592.
Pearson, S. (2013). Privacy, security and trust in cloud computing. In Privacy and security
for cloud computing (pp. 3-42). Springer, London.
References:
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Carlin, S., & Curran, K. (2013). Cloud computing security. In Pervasive and Ubiquitous
Technology Innovations for Ambient Intelligence Environments (pp. 12-17). IGI
Global.
Hashizume, K., Rosado, D. G., Fernández-Medina, E., & Fernandez, E. B. (2013). An
analysis of security issues for cloud computing. Journal of internet services and
applications, 4(1), 5.
Khalil, I., Khreishah, A., & Azeem, M. (2014). Cloud computing security: A
survey. Computers, 3(1), 1-35.
Modi, C., Patel, D., Borisaniya, B., Patel, A., & Rajarajan, M. (2013). A survey on security
issues and solutions at different layers of Cloud computing. The journal of
supercomputing, 63(2), 561-592.
Pearson, S. (2013). Privacy, security and trust in cloud computing. In Privacy and security
for cloud computing (pp. 3-42). Springer, London.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




