Cloud Computing Security Solution: Project Proposal and Plan
VerifiedAdded on 2023/06/10
|12
|2602
|63
Project
AI Summary
This document presents a project proposal and plan for developing cloud computing-based security solutions. It includes an introduction to the problem domain, rationale, and justification for the research, which aims to investigate the role of cloud computing in designing and deploying security measures. The proposal outlines key research questions, a conceptual framework, and the methodology, which combines qualitative and quantitative approaches. Data collection methods include questionnaires, domain analysis, and interviews. The document addresses ethical considerations, compliance requirements, and data analysis techniques. A detailed project plan is provided, encompassing deliverables, a work breakdown structure (WBS), risk analysis, duration, and a timeline with a Gantt chart. The research intends to explore the potential of cloud computing to enhance overall security architecture and mitigate emerging security challenges.
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Cloud-Computing-based Security Solution
Project Proposal & Plan
8/4/2018
0
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Cloud-Computing-based Security Solution
Project Proposal & Plan
8/4/2018
0
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing-based Security Solution
Table of Contents
Title.......................................................................................................................................................2
Blog Entry.........................................................................................................................................2
Introduction...........................................................................................................................................2
Rationale............................................................................................................................................2
Problem Domain............................................................................................................................2
Purpose & Justification..................................................................................................................3
Sponsor or Supervisor Recommendation...........................................................................................3
Research Questions...........................................................................................................................3
Conceptual or Theoretical Framework..................................................................................................4
Materials & Methods.............................................................................................................................4
Research Methodology......................................................................................................................4
Data Collection Methods...................................................................................................................5
Ethical Issues.....................................................................................................................................5
Compliance Requirements.................................................................................................................5
Analysis of Data................................................................................................................................5
Project Plan...........................................................................................................................................6
Deliverables.......................................................................................................................................6
Work Breakdown Structure...............................................................................................................6
Risk Analysis.....................................................................................................................................7
Duration.............................................................................................................................................9
Timeline & Gantt chart......................................................................................................................9
References...........................................................................................................................................11
1
Table of Contents
Title.......................................................................................................................................................2
Blog Entry.........................................................................................................................................2
Introduction...........................................................................................................................................2
Rationale............................................................................................................................................2
Problem Domain............................................................................................................................2
Purpose & Justification..................................................................................................................3
Sponsor or Supervisor Recommendation...........................................................................................3
Research Questions...........................................................................................................................3
Conceptual or Theoretical Framework..................................................................................................4
Materials & Methods.............................................................................................................................4
Research Methodology......................................................................................................................4
Data Collection Methods...................................................................................................................5
Ethical Issues.....................................................................................................................................5
Compliance Requirements.................................................................................................................5
Analysis of Data................................................................................................................................5
Project Plan...........................................................................................................................................6
Deliverables.......................................................................................................................................6
Work Breakdown Structure...............................................................................................................6
Risk Analysis.....................................................................................................................................7
Duration.............................................................................................................................................9
Timeline & Gantt chart......................................................................................................................9
References...........................................................................................................................................11
1

Cloud Computing-based Security Solution
Title
Cloud Computing-based Security Solution
Blog Entry
Cloud is also being used as a primary medium for data storage and management. The latest
and emerging technologies are also making use of cloud computing as one of a partner
technology to achieve the aims and objectives. Thus, cloud computing is sure to have a great
role to play in the area of security as well. The research on the security solutions based on
cloud computing can enhance the overall security architecture. A combination of the two
approaches has been selected as the research methodology as the research aims and
objectives will be better achieved. The research will require qualitative aspect to explore the
security issues and utility of cloud computing in the area of security solutions. It will also be
needed to have statistics and numerical patterns for understanding the mitigation and control
that cloud computing may provide for enhancement of security. The information and data sets
required for carrying out the research will be gathered using the techniques as interviews,
domain analysis, and questionnaires. The automated data analytics tools will be used to
analyse the sets collected. The timeframe estimated for the research is 84 days. There will be
three primary phases in which the research will be carried out.
Introduction
Cloud computing is a form of computing that allows the users to access the computing
resources, such as databases, servers, networking, software packages, etc. over the cloud. The
cloud in this case is referred as the Internet. There are a lot of cloud computing applications
that the users and business organizations are utilizing all across the globe. One such
application of cloud computing is security. There are research and development activities that
are being carried out to understand and apply cloud computing in the area of security (Munir
& Palaniappan, 2013).
Rationale
Problem Domain
With the technological advancements taking place at a rapid scale, there are newer
technologies and applications that are being developed and deployed in the organizations.
Some of the popular technologies that are now being used as emerging and innovative
2
Title
Cloud Computing-based Security Solution
Blog Entry
Cloud is also being used as a primary medium for data storage and management. The latest
and emerging technologies are also making use of cloud computing as one of a partner
technology to achieve the aims and objectives. Thus, cloud computing is sure to have a great
role to play in the area of security as well. The research on the security solutions based on
cloud computing can enhance the overall security architecture. A combination of the two
approaches has been selected as the research methodology as the research aims and
objectives will be better achieved. The research will require qualitative aspect to explore the
security issues and utility of cloud computing in the area of security solutions. It will also be
needed to have statistics and numerical patterns for understanding the mitigation and control
that cloud computing may provide for enhancement of security. The information and data sets
required for carrying out the research will be gathered using the techniques as interviews,
domain analysis, and questionnaires. The automated data analytics tools will be used to
analyse the sets collected. The timeframe estimated for the research is 84 days. There will be
three primary phases in which the research will be carried out.
Introduction
Cloud computing is a form of computing that allows the users to access the computing
resources, such as databases, servers, networking, software packages, etc. over the cloud. The
cloud in this case is referred as the Internet. There are a lot of cloud computing applications
that the users and business organizations are utilizing all across the globe. One such
application of cloud computing is security. There are research and development activities that
are being carried out to understand and apply cloud computing in the area of security (Munir
& Palaniappan, 2013).
Rationale
Problem Domain
With the technological advancements taking place at a rapid scale, there are newer
technologies and applications that are being developed and deployed in the organizations.
Some of the popular technologies that are now being used as emerging and innovative
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cloud Computing-based Security Solution
techniques are Internet of Things (IoT), Artificial Intelligence, and Big Data. All of these
technologies make use of cloud computing to provide accessibility of the services to the
users. These technological applications are exposed to various forms of security challenges.
The cloud computing frameworks and applications shall be able to provide measures for the
enhancement of security as well (Sharma & Trivedi, 2014).
Purpose & Justification
The main purpose behind the research is to investigate and analyse the role of cloud-
computing to design, develop, and deploy security solutions (Shahid & Sharif, 2015).
There are a lot of applications of cloud in the current business environments as remote
working and tele-commuting has become a necessary for the organizations to mark a name at
the global platforms. Cloud is also being used as a primary medium for data storage and
management. The latest and emerging technologies are also making use of cloud computing
as one of a partner technology to achieve the aims and objectives. Thus, cloud computing is
sure to have a great role to play in the area of security as well. The research on the security
solutions based on cloud computing can enhance the overall security architecture.
Sponsor or Supervisor Recommendation
The supervisor for the research shall have the following skills.
Technical skills on the cloud computing norms, frameworks, architecture, and
applications.
Managerial skills to guide and motivate the research team and to manage the risks and
issues associated with the same.
Communication skills to provide adequate comments on every deliverable to clearly
put across the changes that shall be made.
Knowledge and experience on the security challenges, types of security risks that may
appear, and mitigation strategies that shall be utilized.
Research Questions
The research is being conducted with an aim to investigate and understand the role that cloud
computing plays in the area of security and the mechanisms of cloud that may be used to
design and provide security solutions. The research questions that will be answered upon the
completion are listed below.
3
techniques are Internet of Things (IoT), Artificial Intelligence, and Big Data. All of these
technologies make use of cloud computing to provide accessibility of the services to the
users. These technological applications are exposed to various forms of security challenges.
The cloud computing frameworks and applications shall be able to provide measures for the
enhancement of security as well (Sharma & Trivedi, 2014).
Purpose & Justification
The main purpose behind the research is to investigate and analyse the role of cloud-
computing to design, develop, and deploy security solutions (Shahid & Sharif, 2015).
There are a lot of applications of cloud in the current business environments as remote
working and tele-commuting has become a necessary for the organizations to mark a name at
the global platforms. Cloud is also being used as a primary medium for data storage and
management. The latest and emerging technologies are also making use of cloud computing
as one of a partner technology to achieve the aims and objectives. Thus, cloud computing is
sure to have a great role to play in the area of security as well. The research on the security
solutions based on cloud computing can enhance the overall security architecture.
Sponsor or Supervisor Recommendation
The supervisor for the research shall have the following skills.
Technical skills on the cloud computing norms, frameworks, architecture, and
applications.
Managerial skills to guide and motivate the research team and to manage the risks and
issues associated with the same.
Communication skills to provide adequate comments on every deliverable to clearly
put across the changes that shall be made.
Knowledge and experience on the security challenges, types of security risks that may
appear, and mitigation strategies that shall be utilized.
Research Questions
The research is being conducted with an aim to investigate and understand the role that cloud
computing plays in the area of security and the mechanisms of cloud that may be used to
design and provide security solutions. The research questions that will be answered upon the
completion are listed below.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing-based Security Solution
What are the technologies that are paired up with cloud computing and are being
used in the organizations?
What are the common security risks and challenges that come up?
What is the role of cloud computing in the area of security solutions?
Conceptual or Theoretical Framework
Conceptual Framework (Shahid & Sharif, 2015)
Conceptual framework for identity management solution using cloud computing has been
shown in the image above. It is one of the security solutions that may be implemented using
cloud computing as the technology.
Materials & Methods
Research Methodology
The methodology to be used for the research shall be a mix of qualitative and quantitative
methodologies. A combination of the two approaches has been selected as the research
methodology as the research aims and objectives will be better achieved. The research will
require qualitative aspect to explore the security issues and utility of cloud computing in the
area of security solutions. For this purpose, there will be a number of data collection
techniques utilized. The collected data will be sampled and then the analysis will be
performed (Yilmaz, 2013).
It will also be needed to have statistics and numerical patterns for understanding the
mitigation and control that cloud computing may provide for enhancement of security
(Hanson & Grimmer, 2007).
4
What are the technologies that are paired up with cloud computing and are being
used in the organizations?
What are the common security risks and challenges that come up?
What is the role of cloud computing in the area of security solutions?
Conceptual or Theoretical Framework
Conceptual Framework (Shahid & Sharif, 2015)
Conceptual framework for identity management solution using cloud computing has been
shown in the image above. It is one of the security solutions that may be implemented using
cloud computing as the technology.
Materials & Methods
Research Methodology
The methodology to be used for the research shall be a mix of qualitative and quantitative
methodologies. A combination of the two approaches has been selected as the research
methodology as the research aims and objectives will be better achieved. The research will
require qualitative aspect to explore the security issues and utility of cloud computing in the
area of security solutions. For this purpose, there will be a number of data collection
techniques utilized. The collected data will be sampled and then the analysis will be
performed (Yilmaz, 2013).
It will also be needed to have statistics and numerical patterns for understanding the
mitigation and control that cloud computing may provide for enhancement of security
(Hanson & Grimmer, 2007).
4

Cloud Computing-based Security Solution
Data Collection Methods
Questionnaires: The set of questions will be prepared for the business organizations
using emerging technologies and exposed to security risks and challenges. The
questionnaires will be so designed such that the required information regarding
applicability of cloud computing in the area of security could be obtained (Yousuf &
Asger, 2015).
Domain Analysis: The occurrence of security attacks and presence of security
challenges is not restricted to a specific domain. It may occur in an array of domains
and may have different patterns for each. Similarly, the use of cloud computing is
spread across several domains. The method will provide an analysis of each domain to
come up with domain related information.
Interviews: The one-on-one discussions will be possible in the interviews and these
will be organized for the business associates, analysts, end-users, and stakeholders.
Ethical Issues
There are different ethical theories that are present and the ethical principles shall be followed
as illustrated by each theory. The occurrence of security risks and attacks may violate these
theories. For example, theory of Consequentialism states that an activity shall not have any
negative consequences for any entity. The security challenges and occurrence of security
risks result in negative impacts for the users, data owners, and organizations. Thus, this
theory is violated as a result. Similarly, there are legal and regulatory policies that shall be
followed so that the theory of Deontology Ethics may be adhered to. The security attacks lead
to non-adherence to these rules and regulations causing further violation.
Compliance Requirements
The ethical theories and codes, such as ACS Code of Ethics, Theory of Consequentialism,
and Deontology Ethics shall be complied with. The compliance shall also be made for Data
Protection and Information Security laws.
Analysis of Data
The research methodologies as a mixture of qualitative and quantitative analysis will provide
huge clusters of data sets. The analysis shall be performed using advanced and automated
tools for data analysis.
5
Data Collection Methods
Questionnaires: The set of questions will be prepared for the business organizations
using emerging technologies and exposed to security risks and challenges. The
questionnaires will be so designed such that the required information regarding
applicability of cloud computing in the area of security could be obtained (Yousuf &
Asger, 2015).
Domain Analysis: The occurrence of security attacks and presence of security
challenges is not restricted to a specific domain. It may occur in an array of domains
and may have different patterns for each. Similarly, the use of cloud computing is
spread across several domains. The method will provide an analysis of each domain to
come up with domain related information.
Interviews: The one-on-one discussions will be possible in the interviews and these
will be organized for the business associates, analysts, end-users, and stakeholders.
Ethical Issues
There are different ethical theories that are present and the ethical principles shall be followed
as illustrated by each theory. The occurrence of security risks and attacks may violate these
theories. For example, theory of Consequentialism states that an activity shall not have any
negative consequences for any entity. The security challenges and occurrence of security
risks result in negative impacts for the users, data owners, and organizations. Thus, this
theory is violated as a result. Similarly, there are legal and regulatory policies that shall be
followed so that the theory of Deontology Ethics may be adhered to. The security attacks lead
to non-adherence to these rules and regulations causing further violation.
Compliance Requirements
The ethical theories and codes, such as ACS Code of Ethics, Theory of Consequentialism,
and Deontology Ethics shall be complied with. The compliance shall also be made for Data
Protection and Information Security laws.
Analysis of Data
The research methodologies as a mixture of qualitative and quantitative analysis will provide
huge clusters of data sets. The analysis shall be performed using advanced and automated
tools for data analysis.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cloud Computing-based Security Solution
Project Plan
Deliverables
Deliverable Name Description
Progress Reports The research work will be done in a series of numerous phases.
There shall be progress reports shared with the supervisor and
the management every week.
Research Proposal and
Plan
The document shall list out all the details of the planning and
analysis activities for the research and must also include the
timeline that shall be followed.
Data Analytics Document The name and description of the automated data analytics tool
along with the procedure followed shall be written. The results
and findings must be incorporated.
Review Report The comments of the supervisor on the research review and the
improvement areas & gaps identified shall be included in the
deliverable.
Research Presentation The research work will be considered as completed only when
the presentation will be given. It shall mark the closure of the
project.
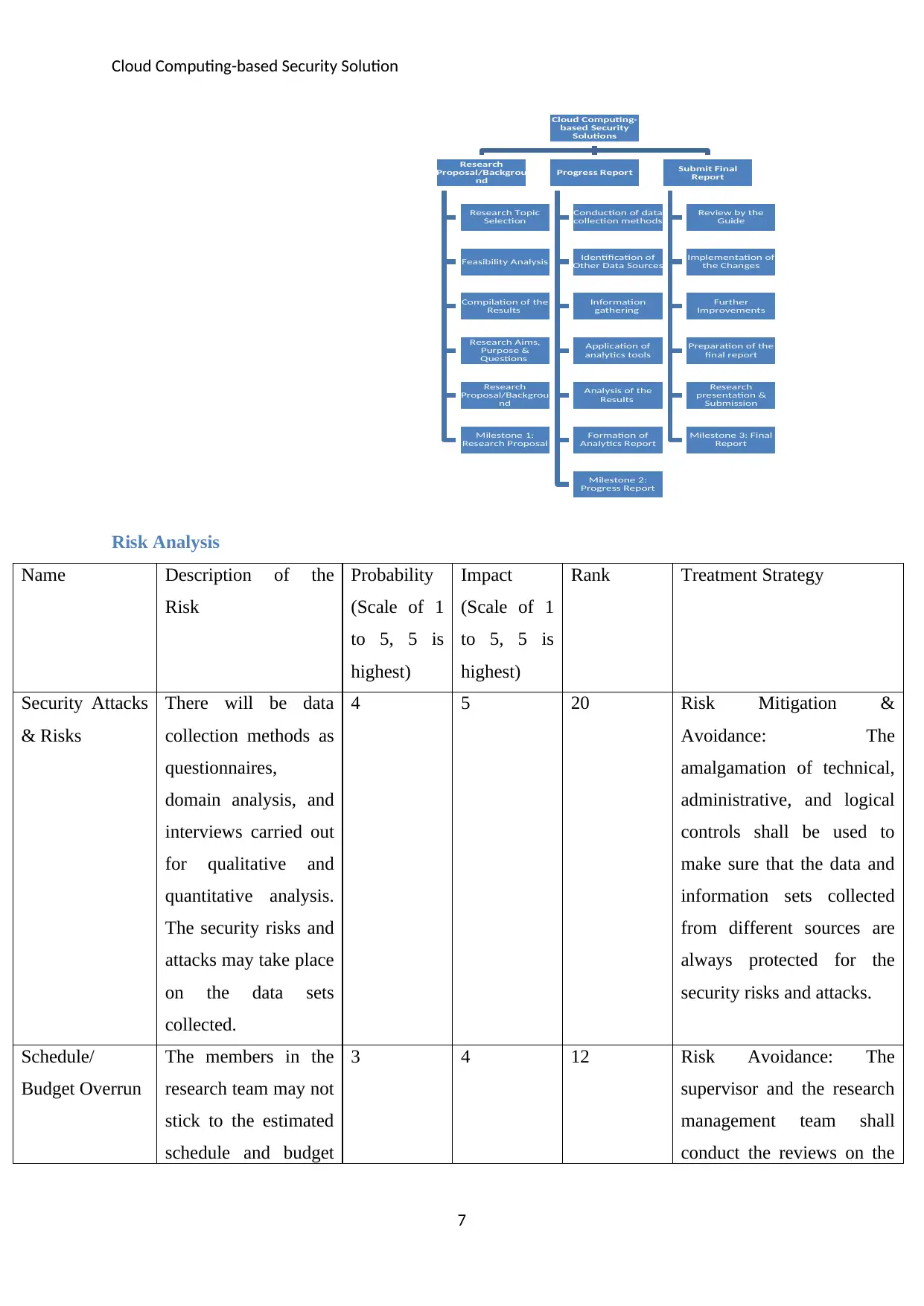
Work Breakdown Structure
The Work Breakdown Structure (WBS) of the research project has been shown in the
diagram below. It has three phases and these phases will be applied to carry out the research
tasks and activities. The aims and objectives of the research will be obtained by the
application of the research. A 3-level WBS of the research project is as illustrated below.
6
Project Plan
Deliverables
Deliverable Name Description
Progress Reports The research work will be done in a series of numerous phases.
There shall be progress reports shared with the supervisor and
the management every week.
Research Proposal and
Plan
The document shall list out all the details of the planning and
analysis activities for the research and must also include the
timeline that shall be followed.
Data Analytics Document The name and description of the automated data analytics tool
along with the procedure followed shall be written. The results
and findings must be incorporated.
Review Report The comments of the supervisor on the research review and the
improvement areas & gaps identified shall be included in the
deliverable.
Research Presentation The research work will be considered as completed only when
the presentation will be given. It shall mark the closure of the
project.
Work Breakdown Structure
The Work Breakdown Structure (WBS) of the research project has been shown in the
diagram below. It has three phases and these phases will be applied to carry out the research
tasks and activities. The aims and objectives of the research will be obtained by the
application of the research. A 3-level WBS of the research project is as illustrated below.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cloud Computing-based Security Solution
Risk Analysis
Name Description of the
Risk
Probability
(Scale of 1
to 5, 5 is
highest)
Impact
(Scale of 1
to 5, 5 is
highest)
Rank Treatment Strategy
Security Attacks
& Risks
There will be data
collection methods as
questionnaires,
domain analysis, and
interviews carried out
for qualitative and
quantitative analysis.
The security risks and
attacks may take place
on the data sets
collected.
4 5 20 Risk Mitigation &
Avoidance: The
amalgamation of technical,
administrative, and logical
controls shall be used to
make sure that the data and
information sets collected
from different sources are
always protected for the
security risks and attacks.
Schedule/
Budget Overrun
The members in the
research team may not
stick to the estimated
schedule and budget
3 4 12 Risk Avoidance: The
supervisor and the research
management team shall
conduct the reviews on the
7
Cloud Computing-
based Security
Solutions
Research
Proposal/Backgrou
nd
Research Topic
Selection
Feasibility Analysis
Compilation of the
Results
Research Aims,
Purpose &
Questions
Research
Proposal/Backgrou
nd
Milestone 1:
Research Proposal
Progress Report
Conduction of data
collection methods
Identification of
Other Data Sources
Information
gathering
Application of
analytics tools
Analysis of the
Results
Formation of
Analytics Report
Milestone 2:
Progress Report
Submit Final
Report
Review by the
Guide
Implementation of
the Changes
Further
Improvements
Preparation of the
final report
Research
presentation &
Submission
Milestone 3: Final
Report
Risk Analysis
Name Description of the
Risk
Probability
(Scale of 1
to 5, 5 is
highest)
Impact
(Scale of 1
to 5, 5 is
highest)
Rank Treatment Strategy
Security Attacks
& Risks
There will be data
collection methods as
questionnaires,
domain analysis, and
interviews carried out
for qualitative and
quantitative analysis.
The security risks and
attacks may take place
on the data sets
collected.
4 5 20 Risk Mitigation &
Avoidance: The
amalgamation of technical,
administrative, and logical
controls shall be used to
make sure that the data and
information sets collected
from different sources are
always protected for the
security risks and attacks.
Schedule/
Budget Overrun
The members in the
research team may not
stick to the estimated
schedule and budget
3 4 12 Risk Avoidance: The
supervisor and the research
management team shall
conduct the reviews on the
7
Cloud Computing-
based Security
Solutions
Research
Proposal/Backgrou
nd
Research Topic
Selection
Feasibility Analysis
Compilation of the
Results
Research Aims,
Purpose &
Questions
Research
Proposal/Backgrou
nd
Milestone 1:
Research Proposal
Progress Report
Conduction of data
collection methods
Identification of
Other Data Sources
Information
gathering
Application of
analytics tools
Analysis of the
Results
Formation of
Analytics Report
Milestone 2:
Progress Report
Submit Final
Report
Review by the
Guide
Implementation of
the Changes
Further
Improvements
Preparation of the
final report
Research
presentation &
Submission
Milestone 3: Final
Report
Cloud Computing-based Security Solution
values due to
occurrence of other
risks or changes in the
research scope.
variance in the estimated
and actual schedule and
budget levels.
Operational
Mistakes
The operational
mistakes during the
activities as data
collection or analysis
may occur.
2 3 6 Risk Avoidance: The
research team shall enhance
their skills by attending the
trainings and acquiring
knowledge about the best
practices that they shall
follow.
Quality Issues Non-compliance and
non-adherence to the
quality standards and
best practices set up
for the research
project.
1 5 5 Risk Avoidance: There shall
be reviews and audits
conducted at regular
intervals on the quality
standards and status to
identify the gaps in quality.
Ethical
Violations
Non-compliance and
non-adherence to the
ethical standards and
best practices set up
for the research
project.
2 5 10 Risk Avoidance: There shall
be reviews and audits
conducted at regular
intervals on the ethical
standards and status to
identify the gaps in the
same.
Legal
Obligations &
Punishments
Non-compliance and
non-adherence to the
legal standards and
best practices set up
for the research
project.
1 5 5 Risk Avoidance: There shall
be reviews and audits
conducted at regular
intervals on the legal
standards and status to
identify the gaps in the
same.
8
values due to
occurrence of other
risks or changes in the
research scope.
variance in the estimated
and actual schedule and
budget levels.
Operational
Mistakes
The operational
mistakes during the
activities as data
collection or analysis
may occur.
2 3 6 Risk Avoidance: The
research team shall enhance
their skills by attending the
trainings and acquiring
knowledge about the best
practices that they shall
follow.
Quality Issues Non-compliance and
non-adherence to the
quality standards and
best practices set up
for the research
project.
1 5 5 Risk Avoidance: There shall
be reviews and audits
conducted at regular
intervals on the quality
standards and status to
identify the gaps in quality.
Ethical
Violations
Non-compliance and
non-adherence to the
ethical standards and
best practices set up
for the research
project.
2 5 10 Risk Avoidance: There shall
be reviews and audits
conducted at regular
intervals on the ethical
standards and status to
identify the gaps in the
same.
Legal
Obligations &
Punishments
Non-compliance and
non-adherence to the
legal standards and
best practices set up
for the research
project.
1 5 5 Risk Avoidance: There shall
be reviews and audits
conducted at regular
intervals on the legal
standards and status to
identify the gaps in the
same.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cloud Computing-based Security Solution
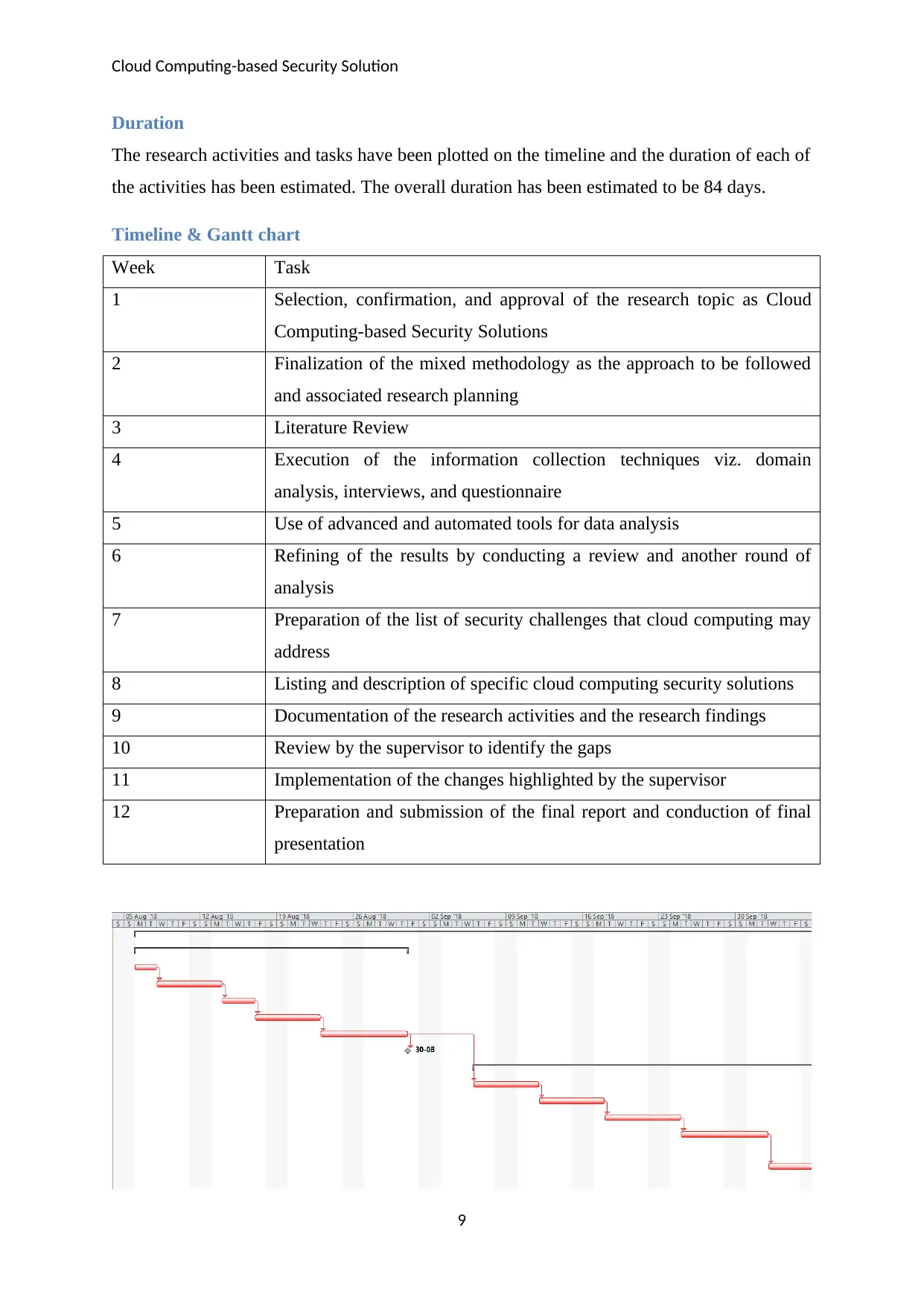
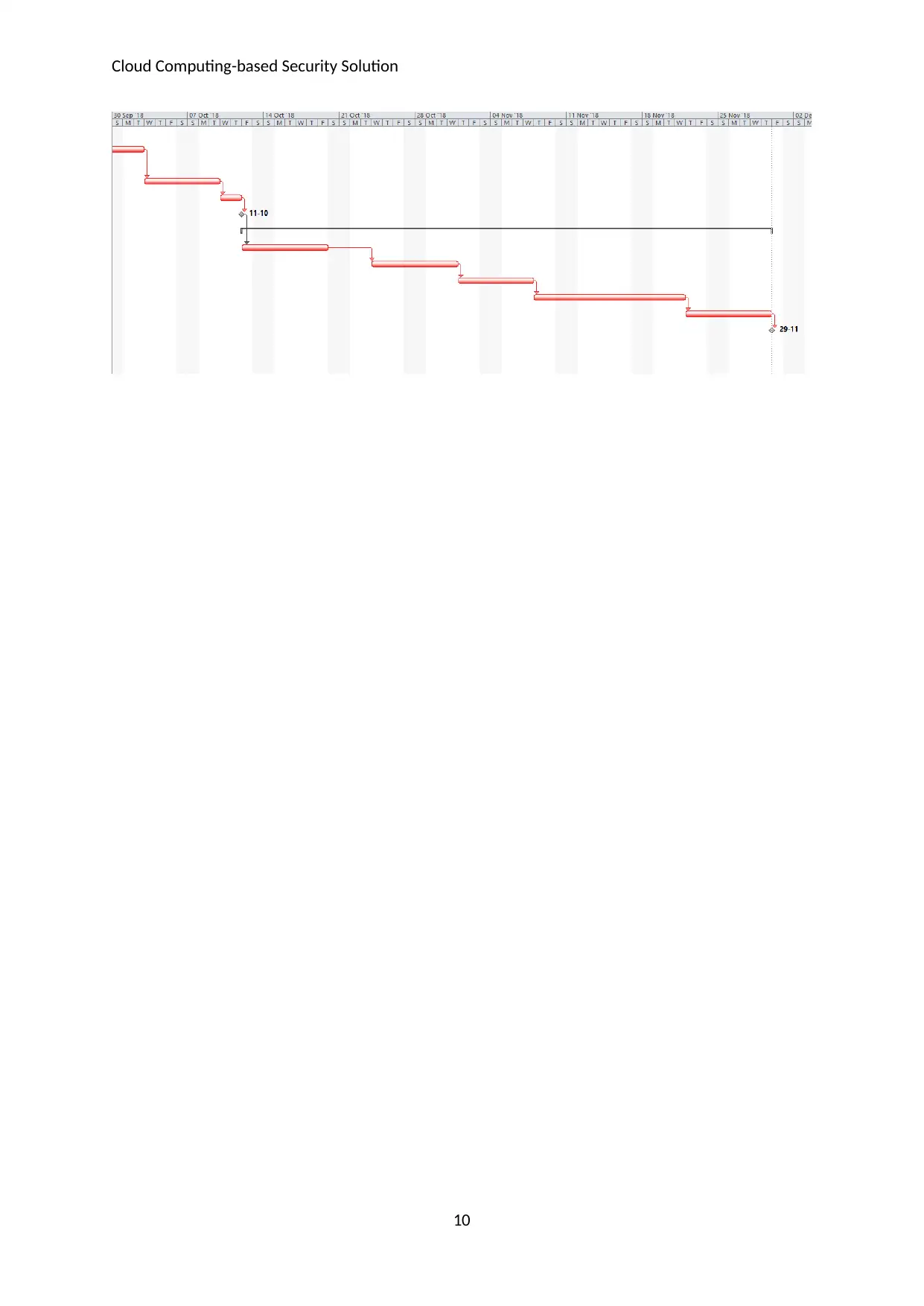
Duration
The research activities and tasks have been plotted on the timeline and the duration of each of
the activities has been estimated. The overall duration has been estimated to be 84 days.
Timeline & Gantt chart
Week Task
1 Selection, confirmation, and approval of the research topic as Cloud
Computing-based Security Solutions
2 Finalization of the mixed methodology as the approach to be followed
and associated research planning
3 Literature Review
4 Execution of the information collection techniques viz. domain
analysis, interviews, and questionnaire
5 Use of advanced and automated tools for data analysis
6 Refining of the results by conducting a review and another round of
analysis
7 Preparation of the list of security challenges that cloud computing may
address
8 Listing and description of specific cloud computing security solutions
9 Documentation of the research activities and the research findings
10 Review by the supervisor to identify the gaps
11 Implementation of the changes highlighted by the supervisor
12 Preparation and submission of the final report and conduction of final
presentation
9
Duration
The research activities and tasks have been plotted on the timeline and the duration of each of
the activities has been estimated. The overall duration has been estimated to be 84 days.
Timeline & Gantt chart
Week Task
1 Selection, confirmation, and approval of the research topic as Cloud
Computing-based Security Solutions
2 Finalization of the mixed methodology as the approach to be followed
and associated research planning
3 Literature Review
4 Execution of the information collection techniques viz. domain
analysis, interviews, and questionnaire
5 Use of advanced and automated tools for data analysis
6 Refining of the results by conducting a review and another round of
analysis
7 Preparation of the list of security challenges that cloud computing may
address
8 Listing and description of specific cloud computing security solutions
9 Documentation of the research activities and the research findings
10 Review by the supervisor to identify the gaps
11 Implementation of the changes highlighted by the supervisor
12 Preparation and submission of the final report and conduction of final
presentation
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cloud Computing-based Security Solution
10
10

Cloud Computing-based Security Solution
References
Hanson, D., & Grimmer, M. (2007). The mix of qualitative and quantitative research in major
marketing journals, 1993â€2002. European Journal Of Marketing, 41(1/2), 58-70.
doi: 10.1108/03090560710718111
Munir, K., & Palaniappan, S. (2013). Secure Cloud Architecture. Advanced Computing: An
International Journal, 4(1), 9-22. doi: 10.5121/acij.2013.4102
Shahid, M., & Sharif, M. (2015). Cloud Computing Security Models, Architectures, Issues
and Challenges: A Survey. The Smart Computing Review, 602-616. doi:
10.6029/smartcr.2015.06.010
Sharma, R., & Trivedi, R. (2014). Literature review: Cloud Computing –Security Issues,
Solution and Technologies. International Journal Of Engineering Research, 3(4),
221-225. doi: 10.17950/ijer/v3s4/408
Yilmaz, K. (2013). Comparison of Quantitative and Qualitative Research Traditions:
epistemological, theoretical, and methodological differences. European Journal Of
Education, 48(2), 311-325. doi: 10.1111/ejed.12014
Yousuf, M., & Asger, M. (2015). Comparison of Various Requirements Elicitation
Techniques. International Journal Of Computer Applications, 116(4), 8-15. doi:
10.5120/20322-2408
11
References
Hanson, D., & Grimmer, M. (2007). The mix of qualitative and quantitative research in major
marketing journals, 1993â€2002. European Journal Of Marketing, 41(1/2), 58-70.
doi: 10.1108/03090560710718111
Munir, K., & Palaniappan, S. (2013). Secure Cloud Architecture. Advanced Computing: An
International Journal, 4(1), 9-22. doi: 10.5121/acij.2013.4102
Shahid, M., & Sharif, M. (2015). Cloud Computing Security Models, Architectures, Issues
and Challenges: A Survey. The Smart Computing Review, 602-616. doi:
10.6029/smartcr.2015.06.010
Sharma, R., & Trivedi, R. (2014). Literature review: Cloud Computing –Security Issues,
Solution and Technologies. International Journal Of Engineering Research, 3(4),
221-225. doi: 10.17950/ijer/v3s4/408
Yilmaz, K. (2013). Comparison of Quantitative and Qualitative Research Traditions:
epistemological, theoretical, and methodological differences. European Journal Of
Education, 48(2), 311-325. doi: 10.1111/ejed.12014
Yousuf, M., & Asger, M. (2015). Comparison of Various Requirements Elicitation
Techniques. International Journal Of Computer Applications, 116(4), 8-15. doi:
10.5120/20322-2408
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





