MITS4003 Database Systems: Data Security and Privacy in Cloud
VerifiedAdded on 2023/04/23
|7
|258
|265
Report
AI Summary
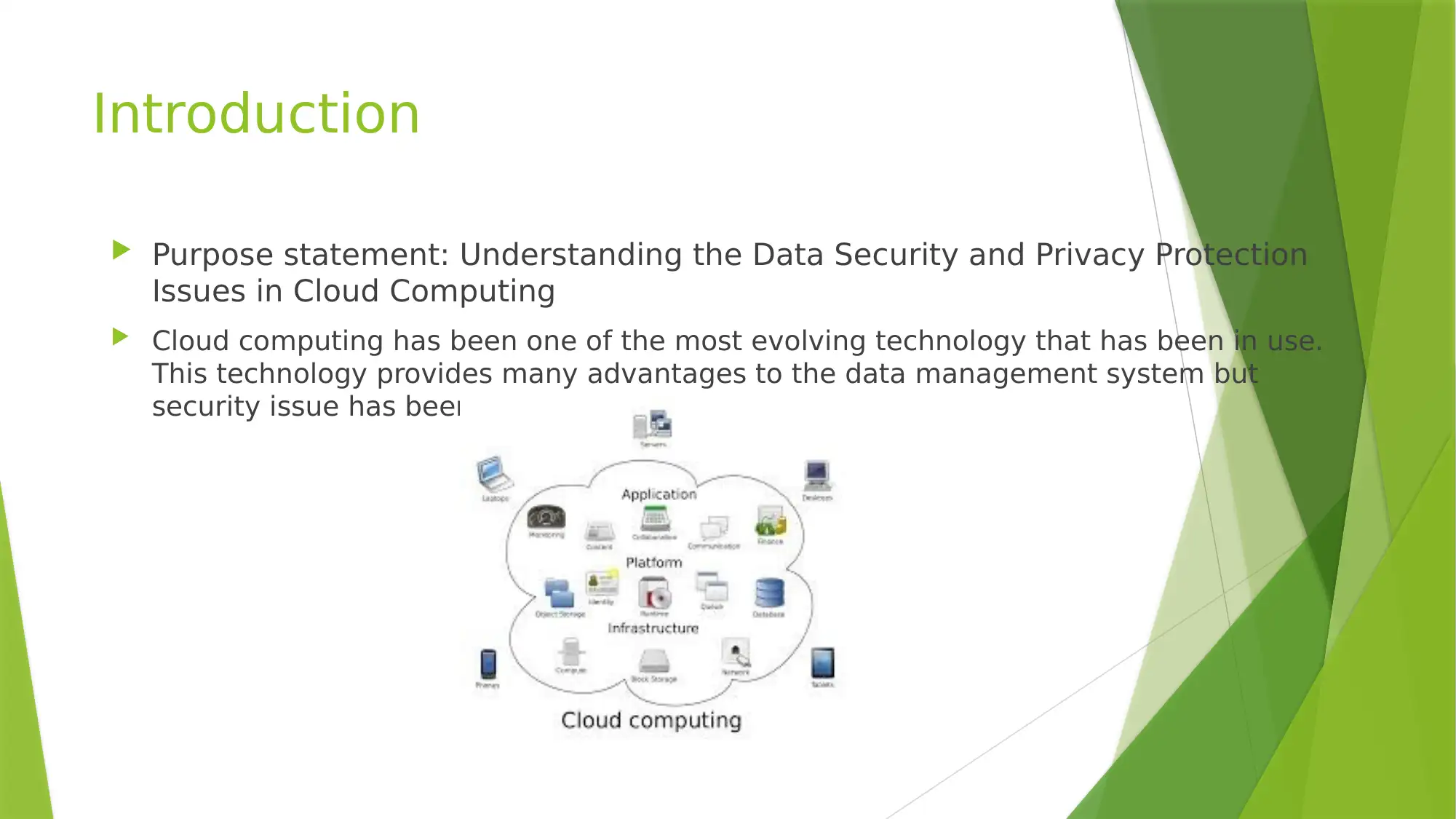
This report provides an overview of data security and privacy protection issues in cloud computing, highlighting the challenges and potential solutions. It identifies key issues such as security and privacy concerns, compliance requirements, privileged user access, data location tracking, and software security. The report also discusses security considerations across various stages of the data lifecycle, including generation, transfer, use, sharing, storage, archival, and destruction. The findings emphasize the importance of addressing these issues to ensure the secure and private implementation of databases in cloud environments, referencing Chen and Zhao's 2012 research on the subject.
1 out of 7













![[object Object]](/_next/static/media/star-bottom.7253800d.svg)