The Department of Administrative Services for Cloud Computing Systems
Added on 2022-10-18
15 Pages4412 Words475 Views
Running head: CLOUD
COMPUTING
0
CLOUD COMPUTING
Name of the Student:
Name of the University:
Author Note:
COMPUTING
0
CLOUD COMPUTING
Name of the Student:
Name of the University:
Author Note:

CLOUD COMPUTING1
Introduction:
Cloud computing is one of the popular systems in the cloud platforms
network. There are many data moving operations, and applied enterprises are
there, cloud computing systems are one of them. DAS means The Department of
Administrative Services, which is provided with some works to the Australian
Government. These services are included in the human resources, payroll,
contract management, procurement, and personnel management. For this
service, DAS provides all departmental data. Basically, for this reason, the
government policies have changed, and this Administrative service department
moved a different approached called "Shared Services" (Ali, Khan & Vasilakos,
2015). The meaning of this service approach is DAS will identify a new type of
service for the WofG means the whole of Government. These applications are
very much suitable for H.R., including performance management. The application
Resources are provided to cloud database systems in the U.S. (California). This
database is replicated and also spread in different locations like Ireland, Dublin
(Ghazizadeh et al. , 2014). All data are configuring correctly, and this data mainly
uploaded, maintained and also processed in the application provider processing
center. This center is located in Bangalore, India. Every day in 12 AEST DAS
uploaded their employee data and first this data transferred in Bangalore after
that this data loaded and delivered secondarily in U.S., California. Human
Resources information and performance management source are always
accessible by the employees. They are still able to use the agency identification
card via DAS internet. Every agency's working directory creates an internal
identity, and this is used for the authorization and authentications internally.
Some characteristics are directly related to the cloud computing are client server
model, grid computing, fog computing, peer to peer, utility computing
(Aljawarneh, Alawneh & Jaradat, 2017). Virtualization is the most enabling
technology of cloud computing. Cloud computing architecture are depending on
some service models like SaaS , PaaS, IaaS. Virtual machines, load balancers,
networking storages are came under the IaaS. Similarly PaaS are related to the
webserver, development tools and database. Mainly it is the platform of the
cloud computing. Lastly email, communication, games, CRM are related to the
SaaS. Basically this models are arranged in a layers of cloud computing. The
architecture mainly systemized by some model architectures and mechanism.
Some benefits are cloud computing are speed, integration, business planning,
choice, low cost and elasticity.
Discussion:-
Introduction:
Cloud computing is one of the popular systems in the cloud platforms
network. There are many data moving operations, and applied enterprises are
there, cloud computing systems are one of them. DAS means The Department of
Administrative Services, which is provided with some works to the Australian
Government. These services are included in the human resources, payroll,
contract management, procurement, and personnel management. For this
service, DAS provides all departmental data. Basically, for this reason, the
government policies have changed, and this Administrative service department
moved a different approached called "Shared Services" (Ali, Khan & Vasilakos,
2015). The meaning of this service approach is DAS will identify a new type of
service for the WofG means the whole of Government. These applications are
very much suitable for H.R., including performance management. The application
Resources are provided to cloud database systems in the U.S. (California). This
database is replicated and also spread in different locations like Ireland, Dublin
(Ghazizadeh et al. , 2014). All data are configuring correctly, and this data mainly
uploaded, maintained and also processed in the application provider processing
center. This center is located in Bangalore, India. Every day in 12 AEST DAS
uploaded their employee data and first this data transferred in Bangalore after
that this data loaded and delivered secondarily in U.S., California. Human
Resources information and performance management source are always
accessible by the employees. They are still able to use the agency identification
card via DAS internet. Every agency's working directory creates an internal
identity, and this is used for the authorization and authentications internally.
Some characteristics are directly related to the cloud computing are client server
model, grid computing, fog computing, peer to peer, utility computing
(Aljawarneh, Alawneh & Jaradat, 2017). Virtualization is the most enabling
technology of cloud computing. Cloud computing architecture are depending on
some service models like SaaS , PaaS, IaaS. Virtual machines, load balancers,
networking storages are came under the IaaS. Similarly PaaS are related to the
webserver, development tools and database. Mainly it is the platform of the
cloud computing. Lastly email, communication, games, CRM are related to the
SaaS. Basically this models are arranged in a layers of cloud computing. The
architecture mainly systemized by some model architectures and mechanism.
Some benefits are cloud computing are speed, integration, business planning,
choice, low cost and elasticity.
Discussion:-

CLOUD COMPUTING2
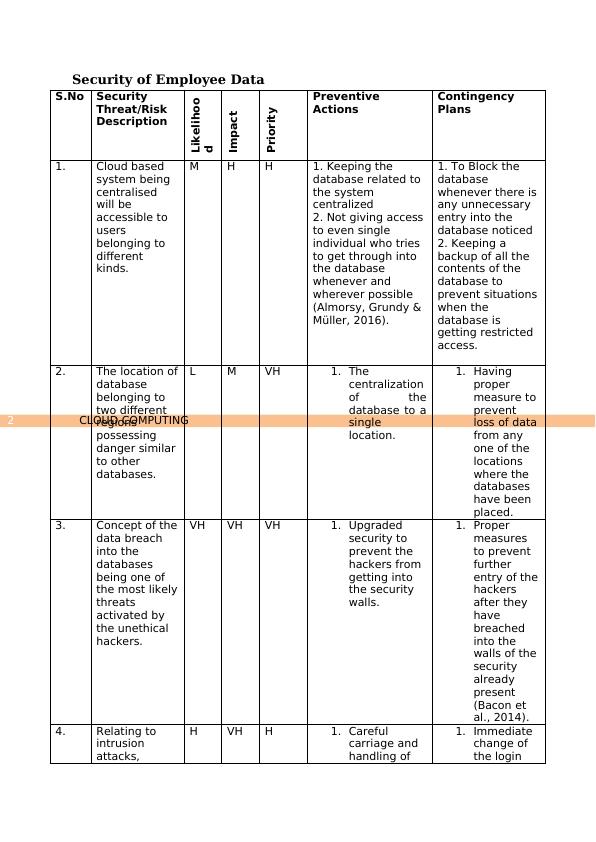
Security of Employee Data
S.No Security
Threat/Risk
Description
Likelihoo
d
Impact
Priority Preventive
Actions
Contingency
Plans
1. Cloud based
system being
centralised
will be
accessible to
users
belonging to
different
kinds.
M H H 1. Keeping the
database related to
the system
centralized
2. Not giving access
to even single
individual who tries
to get through into
the database
whenever and
wherever possible
(Almorsy, Grundy &
Müller, 2016).
1. To Block the
database
whenever there is
any unnecessary
entry into the
database noticed
2. Keeping a
backup of all the
contents of the
database to
prevent situations
when the
database is
getting restricted
access.
2. The location of
database
belonging to
two different
regions
possessing
danger similar
to other
databases.
L M VH 1. The
centralization
of the
database to a
single
location.
1. Having
proper
measure to
prevent
loss of data
from any
one of the
locations
where the
databases
have been
placed.
3. Concept of the
data breach
into the
databases
being one of
the most likely
threats
activated by
the unethical
hackers.
VH VH VH 1. Upgraded
security to
prevent the
hackers from
getting into
the security
walls.
1. Proper
measures
to prevent
further
entry of the
hackers
after they
have
breached
into the
walls of the
security
already
present
(Bacon et
al., 2014).
4. Relating to
intrusion
attacks,
H VH H 1. Careful
carriage and
handling of
1. Immediate
change of
the login
Security of Employee Data
S.No Security
Threat/Risk
Description
Likelihoo
d
Impact
Priority Preventive
Actions
Contingency
Plans
1. Cloud based
system being
centralised
will be
accessible to
users
belonging to
different
kinds.
M H H 1. Keeping the
database related to
the system
centralized
2. Not giving access
to even single
individual who tries
to get through into
the database
whenever and
wherever possible
(Almorsy, Grundy &
Müller, 2016).
1. To Block the
database
whenever there is
any unnecessary
entry into the
database noticed
2. Keeping a
backup of all the
contents of the
database to
prevent situations
when the
database is
getting restricted
access.
2. The location of
database
belonging to
two different
regions
possessing
danger similar
to other
databases.
L M VH 1. The
centralization
of the
database to a
single
location.
1. Having
proper
measure to
prevent
loss of data
from any
one of the
locations
where the
databases
have been
placed.
3. Concept of the
data breach
into the
databases
being one of
the most likely
threats
activated by
the unethical
hackers.
VH VH VH 1. Upgraded
security to
prevent the
hackers from
getting into
the security
walls.
1. Proper
measures
to prevent
further
entry of the
hackers
after they
have
breached
into the
walls of the
security
already
present
(Bacon et
al., 2014).
4. Relating to
intrusion
attacks,
H VH H 1. Careful
carriage and
handling of
1. Immediate
change of
the login
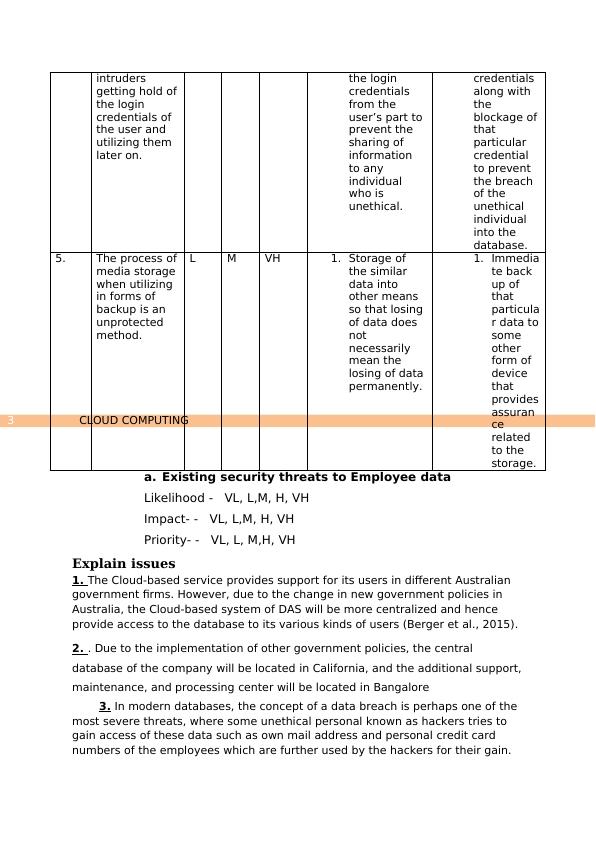
CLOUD COMPUTING3
intruders
getting hold of
the login
credentials of
the user and
utilizing them
later on.
the login
credentials
from the
user’s part to
prevent the
sharing of
information
to any
individual
who is
unethical.
credentials
along with
the
blockage of
that
particular
credential
to prevent
the breach
of the
unethical
individual
into the
database.
5. The process of
media storage
when utilizing
in forms of
backup is an
unprotected
method.
L M VH 1. Storage of
the similar
data into
other means
so that losing
of data does
not
necessarily
mean the
losing of data
permanently.
1. Immedia
te back
up of
that
particula
r data to
some
other
form of
device
that
provides
assuran
ce
related
to the
storage.
a. Existing security threats to Employee data
Likelihood - VL, L,M, H, VH
Impact- - VL, L,M, H, VH
Priority- - VL, L, M,H, VH
Explain issues
1. The Cloud-based service provides support for its users in different Australian
government firms. However, due to the change in new government policies in
Australia, the Cloud-based system of DAS will be more centralized and hence
provide access to the database to its various kinds of users (Berger et al., 2015).
2. . Due to the implementation of other government policies, the central
database of the company will be located in California, and the additional support,
maintenance, and processing center will be located in Bangalore
3. In modern databases, the concept of a data breach is perhaps one of the
most severe threats, where some unethical personal known as hackers tries to
gain access of these data such as own mail address and personal credit card
numbers of the employees which are further used by the hackers for their gain.
intruders
getting hold of
the login
credentials of
the user and
utilizing them
later on.
the login
credentials
from the
user’s part to
prevent the
sharing of
information
to any
individual
who is
unethical.
credentials
along with
the
blockage of
that
particular
credential
to prevent
the breach
of the
unethical
individual
into the
database.
5. The process of
media storage
when utilizing
in forms of
backup is an
unprotected
method.
L M VH 1. Storage of
the similar
data into
other means
so that losing
of data does
not
necessarily
mean the
losing of data
permanently.
1. Immedia
te back
up of
that
particula
r data to
some
other
form of
device
that
provides
assuran
ce
related
to the
storage.
a. Existing security threats to Employee data
Likelihood - VL, L,M, H, VH
Impact- - VL, L,M, H, VH
Priority- - VL, L, M,H, VH
Explain issues
1. The Cloud-based service provides support for its users in different Australian
government firms. However, due to the change in new government policies in
Australia, the Cloud-based system of DAS will be more centralized and hence
provide access to the database to its various kinds of users (Berger et al., 2015).
2. . Due to the implementation of other government policies, the central
database of the company will be located in California, and the additional support,
maintenance, and processing center will be located in Bangalore
3. In modern databases, the concept of a data breach is perhaps one of the
most severe threats, where some unethical personal known as hackers tries to
gain access of these data such as own mail address and personal credit card
numbers of the employees which are further used by the hackers for their gain.
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Cloud Computing.lg...
|13
|480
|79
Use of Cloud Computing in Regional Gardenslg...
|12
|665
|235
Migration of the Web Serverlg...
|17
|991
|89
Cloud Computing: Types, Advantages and Disadvantageslg...
|8
|1314
|485
Introduction to Cloud Computing (PDF)lg...
|13
|2656
|264
Cloud Computing: IAAS, SaaS, PaaS Models and AWS Implementationlg...
|9
|2112
|225
