Analyzing Security & Privacy Issues in Cloud Computing for Finance
VerifiedAdded on 2023/06/14
|16
|3933
|310
Report
AI Summary
This report examines the security and privacy challenges posed by cloud computing within the financial sector, highlighting the opportunities and flaws associated with its adoption. It reviews existing literature, identifying strengths and shortcomings of previous research, and points out gaps in current solutions. The core objective is to identify security and privacy challenges and propose potential measures to create a more secure financial environment. The paper emphasizes the criticality of addressing these issues due to the financial sector's significant impact on national GDP and growth, advocating for solutions that can adapt to the evolving nature of cloud technology, potentially through the integration of machine learning. The report utilizes a detailed methodology for data collection and analysis, culminating in a scheduled timeframe for the proposed research work.

Running head: CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY
ISSUES AND ITS SOLUTIONS
Name of the Student
Name of the University
Author Note
CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY
ISSUES AND ITS SOLUTIONS
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
Abstract:
Cloud computing is offering major challenges to the security & privacy and the proposed
paper will evaluate the significance and potential solution of the same in the finance sector.
The paper will introduce, the research topic and the objectives. Additionally, the devised
report will offer an insight into the steps and measures that will be taken to achieve the
proposed research work along with relevant literature review to earn an insight in the subject.
Finally, the paper has offered a scheduled time frame of the proposed work to conclude the
proposal.
Abstract:
Cloud computing is offering major challenges to the security & privacy and the proposed
paper will evaluate the significance and potential solution of the same in the finance sector.
The paper will introduce, the research topic and the objectives. Additionally, the devised
report will offer an insight into the steps and measures that will be taken to achieve the
proposed research work along with relevant literature review to earn an insight in the subject.
Finally, the paper has offered a scheduled time frame of the proposed work to conclude the
proposal.

2CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
Table of Contents
Background:...............................................................................................................................3
Aims & Objectives:....................................................................................................................3
Literature review:.......................................................................................................................4
Paper under review:................................................................................................................4
Justification over selection of papers:....................................................................................5
Strength:.................................................................................................................................6
Shortcomings:........................................................................................................................7
Methodology:.............................................................................................................................8
Data Collection...................................................................................................................9
Schedule:..................................................................................................................................14
Bibliography:............................................................................................................................16
Table of Contents
Background:...............................................................................................................................3
Aims & Objectives:....................................................................................................................3
Literature review:.......................................................................................................................4
Paper under review:................................................................................................................4
Justification over selection of papers:....................................................................................5
Strength:.................................................................................................................................6
Shortcomings:........................................................................................................................7
Methodology:.............................................................................................................................8
Data Collection...................................................................................................................9
Schedule:..................................................................................................................................14
Bibliography:............................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
Background:
Cloud computing (CC) has opened up different opportunities in different sectors and
one of such industry is financial industry. The discussed industry has greatly been benefited
by the introduction especially for the customers as they can now access different options
offered by the organisation while seating at their favourite location. The benefits enjoyed by
the customers is not the limited for CC’s benefit in the financial sector. The subject (financial
industry) are enjoying the benefits of proper utilisation of resources along with fast and less
effort consuming operation. However, the benefits do not come without it flaws and the
recent financial debacles due to CC are acting as evidence to the flaws. The flaws are
associated with security and privacy which is a major concern for the industry. The proposed
paper will attempt at citing some light on to the discussed challenges offered by the CC to the
subject and in the process contribute to the literary work on CC. The proposed paper will also
offer potential solutions to the identified challenges. The section following offers the aim and
objective that the proposed paper will pursue.
Literature review:
Reviewing the literary work of the past enables the author of the proposed research
work to earn a critical insight into the paper and also develops a platform for the research
work. The articles reviewed for the proposed paper will offer an insight into the Cloud
services and their role in financial industry which will further assist in the proposed research.
The critical literature review has been discussed in the following subsections:
Paper under review:
Article Author in-text link
On the relevance of security
risks for cloud adoption in
Lampe et al. (2013) Lampe, U., Wenge, O.,
Müller, A. and
Background:
Cloud computing (CC) has opened up different opportunities in different sectors and
one of such industry is financial industry. The discussed industry has greatly been benefited
by the introduction especially for the customers as they can now access different options
offered by the organisation while seating at their favourite location. The benefits enjoyed by
the customers is not the limited for CC’s benefit in the financial sector. The subject (financial
industry) are enjoying the benefits of proper utilisation of resources along with fast and less
effort consuming operation. However, the benefits do not come without it flaws and the
recent financial debacles due to CC are acting as evidence to the flaws. The flaws are
associated with security and privacy which is a major concern for the industry. The proposed
paper will attempt at citing some light on to the discussed challenges offered by the CC to the
subject and in the process contribute to the literary work on CC. The proposed paper will also
offer potential solutions to the identified challenges. The section following offers the aim and
objective that the proposed paper will pursue.
Literature review:
Reviewing the literary work of the past enables the author of the proposed research
work to earn a critical insight into the paper and also develops a platform for the research
work. The articles reviewed for the proposed paper will offer an insight into the Cloud
services and their role in financial industry which will further assist in the proposed research.
The critical literature review has been discussed in the following subsections:
Paper under review:
Article Author in-text link
On the relevance of security
risks for cloud adoption in
Lampe et al. (2013) Lampe, U., Wenge, O.,
Müller, A. and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
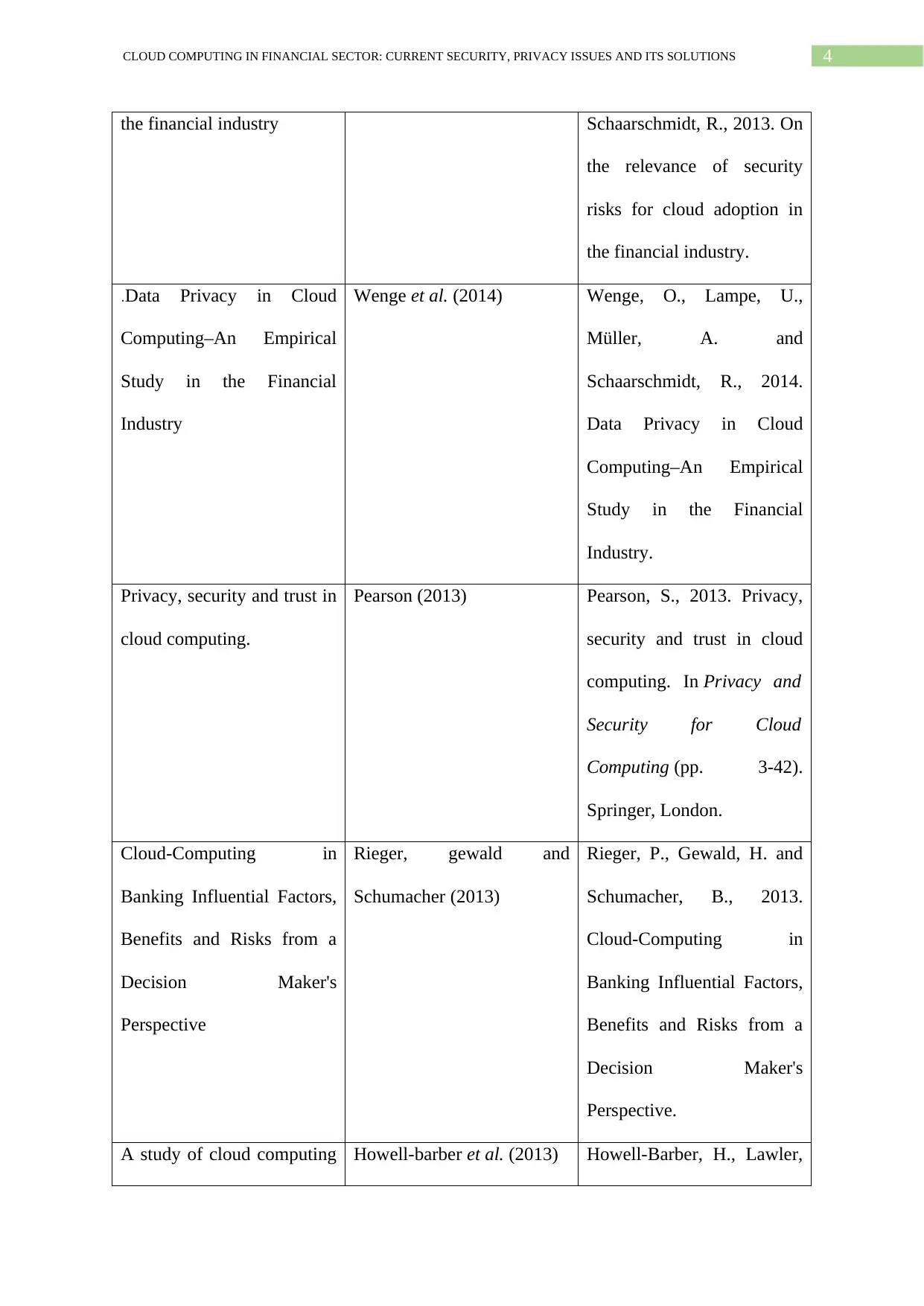
the financial industry Schaarschmidt, R., 2013. On
the relevance of security
risks for cloud adoption in
the financial industry.
.Data Privacy in Cloud
Computing–An Empirical
Study in the Financial
Industry
Wenge et al. (2014) Wenge, O., Lampe, U.,
Müller, A. and
Schaarschmidt, R., 2014.
Data Privacy in Cloud
Computing–An Empirical
Study in the Financial
Industry.
Privacy, security and trust in
cloud computing.
Pearson (2013) Pearson, S., 2013. Privacy,
security and trust in cloud
computing. In Privacy and
Security for Cloud
Computing (pp. 3-42).
Springer, London.
Cloud-Computing in
Banking Influential Factors,
Benefits and Risks from a
Decision Maker's
Perspective
Rieger, gewald and
Schumacher (2013)
Rieger, P., Gewald, H. and
Schumacher, B., 2013.
Cloud-Computing in
Banking Influential Factors,
Benefits and Risks from a
Decision Maker's
Perspective.
A study of cloud computing Howell-barber et al. (2013) Howell-Barber, H., Lawler,
the financial industry Schaarschmidt, R., 2013. On
the relevance of security
risks for cloud adoption in
the financial industry.
.Data Privacy in Cloud
Computing–An Empirical
Study in the Financial
Industry
Wenge et al. (2014) Wenge, O., Lampe, U.,
Müller, A. and
Schaarschmidt, R., 2014.
Data Privacy in Cloud
Computing–An Empirical
Study in the Financial
Industry.
Privacy, security and trust in
cloud computing.
Pearson (2013) Pearson, S., 2013. Privacy,
security and trust in cloud
computing. In Privacy and
Security for Cloud
Computing (pp. 3-42).
Springer, London.
Cloud-Computing in
Banking Influential Factors,
Benefits and Risks from a
Decision Maker's
Perspective
Rieger, gewald and
Schumacher (2013)
Rieger, P., Gewald, H. and
Schumacher, B., 2013.
Cloud-Computing in
Banking Influential Factors,
Benefits and Risks from a
Decision Maker's
Perspective.
A study of cloud computing Howell-barber et al. (2013) Howell-Barber, H., Lawler,

5CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
software-as-a-service (SaaS)
in financial firms
J., Desai, S. and Joseph, A.,
2013. A study of cloud
computing software-as-a-
service (SaaS) in financial
firms. Journal of
Information Systems
Applied Research, 6(3).
TABLE 1: REVIEWED ARTICLES
(Source: Created by Author)
Justification over selection of papers:
The articles have been selected because the subjects of the paper are either cloud
computing or technology in financial services or both. The reason for sticking to the articles
lays on the fact that both the subjects of proposed paper are involved in it. The first reviewed
article provides an insight into the relevance of security risk that cloud offers to the financial
industry on adoption. The second article has its similarity to the previous article, however,
unlike, the previous article the deemed article follows the privacy issue rather than security.
The third article can be stated as the integration of both the first and second article with an
additional factor of trust which will enable the author in understanding the perception of the
financial industry over adoption of the cloud services (one of the objectives of the proposed
paper). The fourth article is selected for reviewing because it discusses the factors responsible
for the risks of CC in financial industry along with the benefits and influential factors that
will assist in concluding the proposed paper. Finally, the fifth and final paper has taken an in
general approach of the CC in the subject. In conclusion, it can be stated that the reviewed
software-as-a-service (SaaS)
in financial firms
J., Desai, S. and Joseph, A.,
2013. A study of cloud
computing software-as-a-
service (SaaS) in financial
firms. Journal of
Information Systems
Applied Research, 6(3).
TABLE 1: REVIEWED ARTICLES
(Source: Created by Author)
Justification over selection of papers:
The articles have been selected because the subjects of the paper are either cloud
computing or technology in financial services or both. The reason for sticking to the articles
lays on the fact that both the subjects of proposed paper are involved in it. The first reviewed
article provides an insight into the relevance of security risk that cloud offers to the financial
industry on adoption. The second article has its similarity to the previous article, however,
unlike, the previous article the deemed article follows the privacy issue rather than security.
The third article can be stated as the integration of both the first and second article with an
additional factor of trust which will enable the author in understanding the perception of the
financial industry over adoption of the cloud services (one of the objectives of the proposed
paper). The fourth article is selected for reviewing because it discusses the factors responsible
for the risks of CC in financial industry along with the benefits and influential factors that
will assist in concluding the proposed paper. Finally, the fifth and final paper has taken an in
general approach of the CC in the subject. In conclusion, it can be stated that the reviewed
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
articles are relevant to the proposed work and will assist in achieving the objectives and the
selection is justified.
Strength:
The strength of a reviewed article can be associated with anything from its offered
details to the structuring or the way it had paved for future researches. In case of the first
article, the strength of the article lays on the detailed nut, concussed information it has
offered. The detailing of the security threats offered by the article is vital and can be used to
derive the remedial measures for the same. Additionally, the paper is also good with
theoretical representation along with lack of practicality makes it easy to understand even for
the non-technical readers and is even capable of developing critical thinking about security
risks in the subject.
The second paper has its strength laying in the offering made by it. The paper has
offered a detail review over the privacy concerns that may arise post-adoption of the
discussed technology. The argument presented by the authors that financial sector should
focus more on the privacy issues rather than others because loss of private data will not only
threat the financial institution but also the enormous amount of customers associated with
them is a key strength of the paper.
The strength of the third article as well as the fourth article lays on the fact that they
have taken consideration of most of the factors that are relevant to the CC and the financial
services. Doing so, enables the readers to earn a collective idea about the subjects and can
even gather interest in them to pursue further researches on the subjects. Finally, the fifth
paper has its strength laying in the appropriate referencing and crediting that it has offered to
the sources of data collection along with choosing a much needed research topic which
enhances the reliability along with scope of the article.
articles are relevant to the proposed work and will assist in achieving the objectives and the
selection is justified.
Strength:
The strength of a reviewed article can be associated with anything from its offered
details to the structuring or the way it had paved for future researches. In case of the first
article, the strength of the article lays on the detailed nut, concussed information it has
offered. The detailing of the security threats offered by the article is vital and can be used to
derive the remedial measures for the same. Additionally, the paper is also good with
theoretical representation along with lack of practicality makes it easy to understand even for
the non-technical readers and is even capable of developing critical thinking about security
risks in the subject.
The second paper has its strength laying in the offering made by it. The paper has
offered a detail review over the privacy concerns that may arise post-adoption of the
discussed technology. The argument presented by the authors that financial sector should
focus more on the privacy issues rather than others because loss of private data will not only
threat the financial institution but also the enormous amount of customers associated with
them is a key strength of the paper.
The strength of the third article as well as the fourth article lays on the fact that they
have taken consideration of most of the factors that are relevant to the CC and the financial
services. Doing so, enables the readers to earn a collective idea about the subjects and can
even gather interest in them to pursue further researches on the subjects. Finally, the fifth
paper has its strength laying in the appropriate referencing and crediting that it has offered to
the sources of data collection along with choosing a much needed research topic which
enhances the reliability along with scope of the article.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
Shortcomings:
Though, the first paper has offered some prominent detail relevant to the security
threats offered by the cloud services in the financial industry, they seem less feasible because
the offered is more theoretical in nature than practical. The second paper is an interesting and
viable readable resource for the readers of cloud services however, the paper has been
developed on the secondary data that scholars have collected during their era. Additionally, it
is also known that cloud is a disruptive technology and is continuously changing, hence,
working on the secondary data does not seem feasible as the issues that were in past could
have been omitted in the current scenario or even the issues that were not associated with CC
in the past must have made their way in the current scenario. Hence, the reliability of the
reviewed article is in doubts.
No potential shortcoming has been identified in the third article because it is well-
structured and also offers detailed and knowledgeable facts that the readers need to know.
The fourth article has its shortcoming laying in the limited size of the collected data. The
collected data for the paper were only from two banking industry of Germany. Additionally,
lack of literature review means that the paper has not collected secondary data which raises
the question over viability of the paper. The only identified drawback of the final reviewed
paper is its improper language.
Gaps in literature:
The review above cites that the CC in the financial industry has been researched at
times and by many scholars. However, the research questions of the proposed paper are still
unanswered and another potential gap that had been identified by reviewing the literary work
of the past on the subject of the paper is lack of adequate solution for CC in financial sector.
The reason for lack of adequate solution of the challenges that CC offers in the financial
sector is still in existence because cloud is a disruptive technology and is in its adolescence
Shortcomings:
Though, the first paper has offered some prominent detail relevant to the security
threats offered by the cloud services in the financial industry, they seem less feasible because
the offered is more theoretical in nature than practical. The second paper is an interesting and
viable readable resource for the readers of cloud services however, the paper has been
developed on the secondary data that scholars have collected during their era. Additionally, it
is also known that cloud is a disruptive technology and is continuously changing, hence,
working on the secondary data does not seem feasible as the issues that were in past could
have been omitted in the current scenario or even the issues that were not associated with CC
in the past must have made their way in the current scenario. Hence, the reliability of the
reviewed article is in doubts.
No potential shortcoming has been identified in the third article because it is well-
structured and also offers detailed and knowledgeable facts that the readers need to know.
The fourth article has its shortcoming laying in the limited size of the collected data. The
collected data for the paper were only from two banking industry of Germany. Additionally,
lack of literature review means that the paper has not collected secondary data which raises
the question over viability of the paper. The only identified drawback of the final reviewed
paper is its improper language.
Gaps in literature:
The review above cites that the CC in the financial industry has been researched at
times and by many scholars. However, the research questions of the proposed paper are still
unanswered and another potential gap that had been identified by reviewing the literary work
of the past on the subject of the paper is lack of adequate solution for CC in financial sector.
The reason for lack of adequate solution of the challenges that CC offers in the financial
sector is still in existence because cloud is a disruptive technology and is in its adolescence

8CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
stage which is witnessing major changes. Hence, an adequate solution for the discussed
challenges can only be that solution which is capable of upgrading itself with the upgrading
technology. One of the way to establish the deemed method is to induce machine learning in
CC. The deemed approach is one area which has not been explored and needs attention. The
proposed research may formulate path for further research on machine learning capabilities of
Cloud computing.
Statement of Problem:
The discussion above cites the vitality of the CC in the financial industry and have
also cited witness to the challenges that it offers. The problem becomes more significant
because financial sector is one of the most promising industry of a country’s GDP & growth
and if it remains at threat then the threats can be considered a threat for the nation and hence
they need to be mitigated. Hence, the deemed problem can be considered as one of the most
crucial problem and needs to be addressed in the minimum possible time.
Aims & Objectives:
Cloud services is one of the most discussed subject in today’s world of technology.
The benefits of the deemed subject have invited debate and so have the challenges. Hence,
inspired by the huge attention over the discussion over the author of the proposed paper was
motivated to pursue the deemed research work. Additionally, financial sector is a sector
which most of the individuals can relate to and are influenced if the former is suffering from
any challenges. Hence, the author attempted to research on the challenges of the financial
sector and attempts to mitigate them.
The core objective of the paper is to identify the security & privacy challenge offered
by the discussed technology to the subject. The problem statement above can be taken in
consideration to understand the vitality of the aim. The aim of the paper will act as a
stage which is witnessing major changes. Hence, an adequate solution for the discussed
challenges can only be that solution which is capable of upgrading itself with the upgrading
technology. One of the way to establish the deemed method is to induce machine learning in
CC. The deemed approach is one area which has not been explored and needs attention. The
proposed research may formulate path for further research on machine learning capabilities of
Cloud computing.
Statement of Problem:
The discussion above cites the vitality of the CC in the financial industry and have
also cited witness to the challenges that it offers. The problem becomes more significant
because financial sector is one of the most promising industry of a country’s GDP & growth
and if it remains at threat then the threats can be considered a threat for the nation and hence
they need to be mitigated. Hence, the deemed problem can be considered as one of the most
crucial problem and needs to be addressed in the minimum possible time.
Aims & Objectives:
Cloud services is one of the most discussed subject in today’s world of technology.
The benefits of the deemed subject have invited debate and so have the challenges. Hence,
inspired by the huge attention over the discussion over the author of the proposed paper was
motivated to pursue the deemed research work. Additionally, financial sector is a sector
which most of the individuals can relate to and are influenced if the former is suffering from
any challenges. Hence, the author attempted to research on the challenges of the financial
sector and attempts to mitigate them.
The core objective of the paper is to identify the security & privacy challenge offered
by the discussed technology to the subject. The problem statement above can be taken in
consideration to understand the vitality of the aim. The aim of the paper will act as a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
milestone in mitigating the discussed problem and offering a stability to CC based Financial
sector. The identification of the security & privacy challenge will ensure that a solution for
the problem that is capable of mitigating the discussed challenge.
The co-objective that the paper will pursue is identification of the potential measures that
can assist in tackling the identified challenges and in the process make a secure financial
environment. Identification of a problem is not sufficient as it may attract theoretical
solutions for the identified challenges. However, the feasibility of the solutions will stay
unclear unless they are researched over. The research will determine the limitation and
benefits of the proposed solution which the readers can adopt in real-world scenario
leveraging the research effort invested by the author(s). Hence, depending on the literature
review and the problem statement, the following research questions will be addressed by the
proposed research work.
What are the different types of uses of Cloud Computing in the business
organizations in Financial Sector?
What are the potential challenges of using Cloud Computing in Financial Sector?
What are the efficient strategies for mitigating the challenges of using Cloud
Computing in Financial Sector?
Can machine learning prove to be adequate solution for the security & privacy threat
for the CC based financial industries?
Methodology:
DATA COLLECTION
The proposed paper has adopted mixed methodology which will collect both the
primary and secondary data. It is also notable that the primary data will be quantitative data.
The secondary data will be from reviewing the literary work that had been done in the past
milestone in mitigating the discussed problem and offering a stability to CC based Financial
sector. The identification of the security & privacy challenge will ensure that a solution for
the problem that is capable of mitigating the discussed challenge.
The co-objective that the paper will pursue is identification of the potential measures that
can assist in tackling the identified challenges and in the process make a secure financial
environment. Identification of a problem is not sufficient as it may attract theoretical
solutions for the identified challenges. However, the feasibility of the solutions will stay
unclear unless they are researched over. The research will determine the limitation and
benefits of the proposed solution which the readers can adopt in real-world scenario
leveraging the research effort invested by the author(s). Hence, depending on the literature
review and the problem statement, the following research questions will be addressed by the
proposed research work.
What are the different types of uses of Cloud Computing in the business
organizations in Financial Sector?
What are the potential challenges of using Cloud Computing in Financial Sector?
What are the efficient strategies for mitigating the challenges of using Cloud
Computing in Financial Sector?
Can machine learning prove to be adequate solution for the security & privacy threat
for the CC based financial industries?
Methodology:
DATA COLLECTION
The proposed paper has adopted mixed methodology which will collect both the
primary and secondary data. It is also notable that the primary data will be quantitative data.
The secondary data will be from reviewing the literary work that had been done in the past
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
over the subject. While primary data will be collected by distributing a survey questionnaire
to the professionals who can associate themselves with the CC and financial industry as well.
The secondary data will be collected to develop platform for the research. It will assist in
justifying the findings that had been analysed from the primary data analysis. The primary
quantitative data will be collected to increase the size of the of the data.
Researches have been conducted in the past over the same topic and hence, reviewing
them would enable the author of proposed paper to understand the subject more appropriately
and based on the enhance understanding the questionnaire will be developed with
consideration of the research questions.
The reason for selecting primary quantitative data is based on the fact that CC is a
disruptive technology which is changing with time and hence, based on the previous statistics
new evaluation cannot be done. Additionally, the quantitative data is selected to increase the
size of data collected and take a global perception on the subject.
PHILOSOPHY
Interpretivism is the research philosophy that takes consideration of the factual data.
The factual data are those collected from scientific or other scholarly procedure and has been
selected as the research philosophy of the paper. The selection is based on the fact that CC is
a technological achievement and social factor does not have much in much in context for the
objective and hence, instead of positivism philosophy interpretivism has been adopted.
APPROACH
Inductive and deductive are the most commonly known approach. While inductive
approach is used for scholarly work where a new tool or technique is inducted to counter a
situation, deductive approach are used when there is need of deducing some facts from a
scenario. However, there is a third approach known as remedial approach which deduces and
over the subject. While primary data will be collected by distributing a survey questionnaire
to the professionals who can associate themselves with the CC and financial industry as well.
The secondary data will be collected to develop platform for the research. It will assist in
justifying the findings that had been analysed from the primary data analysis. The primary
quantitative data will be collected to increase the size of the of the data.
Researches have been conducted in the past over the same topic and hence, reviewing
them would enable the author of proposed paper to understand the subject more appropriately
and based on the enhance understanding the questionnaire will be developed with
consideration of the research questions.
The reason for selecting primary quantitative data is based on the fact that CC is a
disruptive technology which is changing with time and hence, based on the previous statistics
new evaluation cannot be done. Additionally, the quantitative data is selected to increase the
size of data collected and take a global perception on the subject.
PHILOSOPHY
Interpretivism is the research philosophy that takes consideration of the factual data.
The factual data are those collected from scientific or other scholarly procedure and has been
selected as the research philosophy of the paper. The selection is based on the fact that CC is
a technological achievement and social factor does not have much in much in context for the
objective and hence, instead of positivism philosophy interpretivism has been adopted.
APPROACH
Inductive and deductive are the most commonly known approach. While inductive
approach is used for scholarly work where a new tool or technique is inducted to counter a
situation, deductive approach are used when there is need of deducing some facts from a
scenario. However, there is a third approach known as remedial approach which deduces and

11CLOUD COMPUTING IN FINANCIAL SECTOR: CURRENT SECURITY, PRIVACY ISSUES AND ITS SOLUTIONS
incudes both at the same time. It identifies the issues and offers remedial tools and techniques
at the same time.
The objective of the paper is to identify security & privacy issues due to CC in
financial sector which needs deductive objective. Another demand of the proposed paper is to
recommend potential measures for tackling the identified challenges which calls for inductive
approach. Hence, remedial approach is selected which takes account of both deduction and
induction at a particular instance.
DESIGN
Three types of research design are generally equipped and they are descriptive,
exploratory and explanatory. The proposed paper will equip the exploratory and explanatory
research design. Descriptive research design is used when there is need to describe a scenario
while explanatory design assists in explaining a scenario. Finally, the exploratory design is
equipped when there is need for exploring a scenario and explore remedial procedures.
The objective of the proposed paper demands the need of explaining the security &
privacy issues offered by CC in the financial sector and hence explanatory design will be
adopted. Additionally, the objective also raises the need for exploring the measures and tools
that can assist in tackling the identified security & privacy issues and hence, exploratory
design will be a part of the proposed research work. So, the research design of the paper is an
integrated form of explanatory and exploratory research design.
SAMPLING
Critical thinking and sampling tool (MS-Excel) will be the associated tools &
techniques which will assist in data sampling. Critical thinking will be equipped for the
secondary data while statistical tool will be used to evaluate and conclude on the collected
incudes both at the same time. It identifies the issues and offers remedial tools and techniques
at the same time.
The objective of the paper is to identify security & privacy issues due to CC in
financial sector which needs deductive objective. Another demand of the proposed paper is to
recommend potential measures for tackling the identified challenges which calls for inductive
approach. Hence, remedial approach is selected which takes account of both deduction and
induction at a particular instance.
DESIGN
Three types of research design are generally equipped and they are descriptive,
exploratory and explanatory. The proposed paper will equip the exploratory and explanatory
research design. Descriptive research design is used when there is need to describe a scenario
while explanatory design assists in explaining a scenario. Finally, the exploratory design is
equipped when there is need for exploring a scenario and explore remedial procedures.
The objective of the proposed paper demands the need of explaining the security &
privacy issues offered by CC in the financial sector and hence explanatory design will be
adopted. Additionally, the objective also raises the need for exploring the measures and tools
that can assist in tackling the identified security & privacy issues and hence, exploratory
design will be a part of the proposed research work. So, the research design of the paper is an
integrated form of explanatory and exploratory research design.
SAMPLING
Critical thinking and sampling tool (MS-Excel) will be the associated tools &
techniques which will assist in data sampling. Critical thinking will be equipped for the
secondary data while statistical tool will be used to evaluate and conclude on the collected
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





