Exploring Security Issues in IoT Cloud Computing & Countermeasures
VerifiedAdded on 2023/06/13
|14
|4648
|362
Annotated Bibliography
AI Summary
This annotated bibliography delves into the security challenges arising from the integration of cloud computing with the Internet of Things (IoT). It highlights the significance of cloud computing in IoT applications for data storage, processing, and transmission, while also addressing the emerging security issues and threats. The document reviews device security issues, authorization and authentication problems, device update challenges, secure communication concerns, data privacy and integrity issues, and cloud architecture vulnerabilities. It also covers in-cloud data protection, data encryption, identity management, scale management for IoT-Cloud, and denial of service attacks. The research identifies a gap in the existing literature, focusing on device-related security issues and neglecting user-related problems and the involvement of other technologies. The aim of the research is to provide a comprehensive analysis of security aspects with the involvement of cloud computing in IoT, and to present possible solutions and countermeasures based on qualitative research analysis and data collection. The bibliography concludes with a discussion of potential countermeasures and solutions, including device security measures, cloud security enhancements, and IoT security lifecycle management.
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Cloud Computing in IoT Security
Issues, Threats, and Countermeasures
4/18/2018
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Cloud Computing in IoT Security
Issues, Threats, and Countermeasures
4/18/2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing in IoT Security
Table of Contents
Introduction...........................................................................................................................................2
Significance of the Research..............................................................................................................2
Literature Review: Security Issues and Threats.................................................................................2
Device Security Issues...................................................................................................................2
Authorization & Authentication Issues..........................................................................................2
Device Updates for Security..........................................................................................................3
Secure Communication Issues.......................................................................................................3
Data Privacy & Integrity Issues.....................................................................................................3
Cloud Architecture Issues..............................................................................................................4
In-Cloud Data Protection Issues....................................................................................................4
Data Encryption Issues..................................................................................................................4
Identity Management Security Issues............................................................................................4
Scale Management for IoT-Cloud..................................................................................................5
Denial of Service & Distributed Denial of Service Attacks...........................................................5
Research Gap.....................................................................................................................................5
Aim of the Research..........................................................................................................................6
Materials & Methods.............................................................................................................................6
Discussion.............................................................................................................................................9
Set of Countermeasures & Solutions.................................................................................................9
Device Security.............................................................................................................................9
Securing the Cloud........................................................................................................................9
IoT Security Lifecycle Management............................................................................................10
Recommendations & Conclusion........................................................................................................10
References...........................................................................................................................................11
1
Table of Contents
Introduction...........................................................................................................................................2
Significance of the Research..............................................................................................................2
Literature Review: Security Issues and Threats.................................................................................2
Device Security Issues...................................................................................................................2
Authorization & Authentication Issues..........................................................................................2
Device Updates for Security..........................................................................................................3
Secure Communication Issues.......................................................................................................3
Data Privacy & Integrity Issues.....................................................................................................3
Cloud Architecture Issues..............................................................................................................4
In-Cloud Data Protection Issues....................................................................................................4
Data Encryption Issues..................................................................................................................4
Identity Management Security Issues............................................................................................4
Scale Management for IoT-Cloud..................................................................................................5
Denial of Service & Distributed Denial of Service Attacks...........................................................5
Research Gap.....................................................................................................................................5
Aim of the Research..........................................................................................................................6
Materials & Methods.............................................................................................................................6
Discussion.............................................................................................................................................9
Set of Countermeasures & Solutions.................................................................................................9
Device Security.............................................................................................................................9
Securing the Cloud........................................................................................................................9
IoT Security Lifecycle Management............................................................................................10
Recommendations & Conclusion........................................................................................................10
References...........................................................................................................................................11
1

Cloud Computing in IoT Security
Introduction
Internet of Things (IoT) is an inter-connection of the gadgets, devices, networks, algorithms,
databases, and codes to carry out specific activities for achieving a particular goal. The IoT-
based applications have gained a lot of popularity recently and are being used in a variety of
sectors and areas. Some of the industrial sectors that are the prime applicants of IoT include
healthcare sector, e-commerce, sales & marketing, banking and finance, commercial services,
and applications.
Significance of the Research
Cloud computing plays a significant role in the functioning of an IoT application. There are
huge clusters of data sets that are generated and processed by an IoT application on a daily
basis [1]. Cloud computing services and application provide a mechanism for storage,
processing, and transmission of these data sets. There are different pricing models on the
basis of the cloud delivery model that is selected. Economies of scale are one of the
mechanisms through which cloud can provide cost-effective solutions and benefits to the IoT
start-ups [2]. Virtual data storage along with the collaboration of varied components is made
possible by cloud computing. The sharing and allocation of the resources required by the
components in an IoT-based application is also handled by cloud services. There are several
benefits that cloud computing offers to IoT. However, there are certain security issues and
threats that have emerged with the involvement of cloud computing in IoT [3].
Literature Review: Security Issues and Threats
Device Security Issues
The number of devices connected in an IoT application has limits on the amount of data
storage or memory along with the processing capabilities that may be offered. These devices
shall operate on power saver modes when running on batteries. These constrained devices
cannot be protected with the aid of encryption as the execution of encryption and decryption
processes is not quick enough for secure data transmission [4]. There may be side channel
attacks, or power analysis attacks that may take place. There may also be issues of device loss
or stealing that may occur leading to compromise on security [5].
2
Introduction
Internet of Things (IoT) is an inter-connection of the gadgets, devices, networks, algorithms,
databases, and codes to carry out specific activities for achieving a particular goal. The IoT-
based applications have gained a lot of popularity recently and are being used in a variety of
sectors and areas. Some of the industrial sectors that are the prime applicants of IoT include
healthcare sector, e-commerce, sales & marketing, banking and finance, commercial services,
and applications.
Significance of the Research
Cloud computing plays a significant role in the functioning of an IoT application. There are
huge clusters of data sets that are generated and processed by an IoT application on a daily
basis [1]. Cloud computing services and application provide a mechanism for storage,
processing, and transmission of these data sets. There are different pricing models on the
basis of the cloud delivery model that is selected. Economies of scale are one of the
mechanisms through which cloud can provide cost-effective solutions and benefits to the IoT
start-ups [2]. Virtual data storage along with the collaboration of varied components is made
possible by cloud computing. The sharing and allocation of the resources required by the
components in an IoT-based application is also handled by cloud services. There are several
benefits that cloud computing offers to IoT. However, there are certain security issues and
threats that have emerged with the involvement of cloud computing in IoT [3].
Literature Review: Security Issues and Threats
Device Security Issues
The number of devices connected in an IoT application has limits on the amount of data
storage or memory along with the processing capabilities that may be offered. These devices
shall operate on power saver modes when running on batteries. These constrained devices
cannot be protected with the aid of encryption as the execution of encryption and decryption
processes is not quick enough for secure data transmission [4]. There may be side channel
attacks, or power analysis attacks that may take place. There may also be issues of device loss
or stealing that may occur leading to compromise on security [5].
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cloud Computing in IoT Security
Authorization & Authentication Issues
There are varied access points leading to emergence of varied points of failure with the
involvement of cloud computing in IoT. Authorization and authentication of the devices and
the cloud-based components emerges as an issue that leads to the presence of security
vulnerabilities [6]. There may be components or devices that may use weaker passwords or
poor access control mechanisms that may be utilized by the malevolent entities to give shape
to the security attacks. This may lead to the exposure of confidential data sets.
Device Updates for Security
The installation of updates and security patches is essential to ensure that the security of the
devices and the components is always maintained. The tracking of available updates in the
cloud-based medium becomes a challenge as there are numerous interfaces and components
involved. Missing out on the installation of a necessary security update may lead to the
emergence of a security attack [7]. There may also be certain devices or cloud-based
components that may demand enhanced downtime impacting overall performance of the
application [8].
Secure Communication Issues
The other set of security challenges that may be witnessed include communication issues
over the network and cloud services. Most of the messages that are transmitted between the
IoT devices and the cloud services or applications are not encrypted. These unsecure
messages and communication mechanisms lead to leakage and breaching of the data sets [9].
Data Privacy & Integrity Issues
It is necessary that the data sets that are transmitted over the cloud platforms, they are stored
and processed in a secure manner. The data privacy norms that are applied on the sensitive
data sets are separated from the IoT data payloads [10]. There may also be unwanted data and
information sets that shall be eliminated to ensure that the regulatory and legal policies are
complied. However, with the involvement of cloud networks, components, and services, there
are a number of privacy issues that crop up [11].
Some of the common data privacy issues include exposure of sensitive and confidential data
sets due to security attacks, such as malware attacks. These malicious codes may be injected
over a cloud network or a specific data set in the form of a virus, worm, Trojan Horses, Logic
bombs, ransomware, spyware, adware, etc. [12]. There are also a number of integrity issues
3
Authorization & Authentication Issues
There are varied access points leading to emergence of varied points of failure with the
involvement of cloud computing in IoT. Authorization and authentication of the devices and
the cloud-based components emerges as an issue that leads to the presence of security
vulnerabilities [6]. There may be components or devices that may use weaker passwords or
poor access control mechanisms that may be utilized by the malevolent entities to give shape
to the security attacks. This may lead to the exposure of confidential data sets.
Device Updates for Security
The installation of updates and security patches is essential to ensure that the security of the
devices and the components is always maintained. The tracking of available updates in the
cloud-based medium becomes a challenge as there are numerous interfaces and components
involved. Missing out on the installation of a necessary security update may lead to the
emergence of a security attack [7]. There may also be certain devices or cloud-based
components that may demand enhanced downtime impacting overall performance of the
application [8].
Secure Communication Issues
The other set of security challenges that may be witnessed include communication issues
over the network and cloud services. Most of the messages that are transmitted between the
IoT devices and the cloud services or applications are not encrypted. These unsecure
messages and communication mechanisms lead to leakage and breaching of the data sets [9].
Data Privacy & Integrity Issues
It is necessary that the data sets that are transmitted over the cloud platforms, they are stored
and processed in a secure manner. The data privacy norms that are applied on the sensitive
data sets are separated from the IoT data payloads [10]. There may also be unwanted data and
information sets that shall be eliminated to ensure that the regulatory and legal policies are
complied. However, with the involvement of cloud networks, components, and services, there
are a number of privacy issues that crop up [11].
Some of the common data privacy issues include exposure of sensitive and confidential data
sets due to security attacks, such as malware attacks. These malicious codes may be injected
over a cloud network or a specific data set in the form of a virus, worm, Trojan Horses, Logic
bombs, ransomware, spyware, adware, etc. [12]. There are also a number of integrity issues
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing in IoT Security
that include violation of digital signatures or employing checksums. There may be message
or media alteration issues or attacks that may be observed as well.
Cloud Architecture Issues
There may be three categories of cloud architecture that may be involved with the IoT
application viz. public, private, or hybrid cloud. The placement of the data sets on the cloud
architecture shall depend upon the category of the data and the type of the architecture
selected [13]. For instance, there are scenarios wherein confidential or sensitive data sets are
placed on public cloud. This leads to the exposure of the sensitive data to increased security
vulnerabilities and threats. The selection of the cloud architecture and model is important to
make sure that the security issues and threats are avoided [14].
In-Cloud Data Protection Issues
There are specific security protocols provided by the cloud service provider to prevent the
data transmission and leakage issues. These services are also provided to ensure that the data
is protected during processing and over the cloud as well. However, the service providers are
required to maintain the cloud properties, such as sharing of resources and multi-tenancy
architecture [15]. The business model is designed on the basis of economies of scale and this
often brings up security issues in terms of unsecure communication, data integrity and
privacy issues.
The extent of provider access on the data and information sets is also an issue that is observed
in the case of protection of the confidential and sensitive data sets.
Data Encryption Issues
The involvement of multiple cloud components, applications, and services bring up the need
to manage the security and data concerns using key management. However, management of
the security keys with cloud computing involved in IoT is an issues as the process is
complex. For instance, the data that is acquired from a location sensor in a cloud-based IoT
application may have relevance to numerous operations [16]. In case of authorised changes in
the application, all the keys are required to be revoked and new keys shall be issued.
Identity Management Security Issues
The users of the cloud-based IoT application have the primary interaction with the tenant’s
application which is further hosted by the cloud serve provider. There are further
considerations that are involved in an IoT application as there are a number of limitations
4
that include violation of digital signatures or employing checksums. There may be message
or media alteration issues or attacks that may be observed as well.
Cloud Architecture Issues
There may be three categories of cloud architecture that may be involved with the IoT
application viz. public, private, or hybrid cloud. The placement of the data sets on the cloud
architecture shall depend upon the category of the data and the type of the architecture
selected [13]. For instance, there are scenarios wherein confidential or sensitive data sets are
placed on public cloud. This leads to the exposure of the sensitive data to increased security
vulnerabilities and threats. The selection of the cloud architecture and model is important to
make sure that the security issues and threats are avoided [14].
In-Cloud Data Protection Issues
There are specific security protocols provided by the cloud service provider to prevent the
data transmission and leakage issues. These services are also provided to ensure that the data
is protected during processing and over the cloud as well. However, the service providers are
required to maintain the cloud properties, such as sharing of resources and multi-tenancy
architecture [15]. The business model is designed on the basis of economies of scale and this
often brings up security issues in terms of unsecure communication, data integrity and
privacy issues.
The extent of provider access on the data and information sets is also an issue that is observed
in the case of protection of the confidential and sensitive data sets.
Data Encryption Issues
The involvement of multiple cloud components, applications, and services bring up the need
to manage the security and data concerns using key management. However, management of
the security keys with cloud computing involved in IoT is an issues as the process is
complex. For instance, the data that is acquired from a location sensor in a cloud-based IoT
application may have relevance to numerous operations [16]. In case of authorised changes in
the application, all the keys are required to be revoked and new keys shall be issued.
Identity Management Security Issues
The users of the cloud-based IoT application have the primary interaction with the tenant’s
application which is further hosted by the cloud serve provider. There are further
considerations that are involved in an IoT application as there are a number of limitations
4

Cloud Computing in IoT Security
associated with these apps [17]. The components and things that are identified in the
application shall interact with the appropriate cloud service to maintain and adhere to the
security protocols. There are considerations that are involved in this process as well. For
instance, if a component classifies the data that needs to be transmitted to numerous
destinations, then the selection of the same is a complex process. This may bring up the
security concerns and threats [18].
Scale Management for IoT-Cloud
In the cloud-based IoT applications, there are a huge number of clients that the application
shall interact with. Also, there may be issues associated with data velocity, variety, and
volume. The cloud services that are involved shall efficiently manage the data loads and
volumes for preventing and avoiding the security issues [19]. The failure in maintaining the
scalability may lead to issues in the availability of data and application services. This comes
up as a major challenge as the cloud-enabled applications cannot completely rely on elasticity
of the services and applications.
System and data logs are necessary to ensure that all the components behave as per the
regulations and policies [20]. The processes of logging and auditing suffer from scalability
issues in cloud-based IoT applications that may enhance the likelihood of the emergence of
data availability concerns. The management of location of these logs also emerges as a
security consideration. The inefficient procedures involved may have an adverse implication
of the confidentiality, integrity, and availability of the IoT data and information sets [21].
Denial of Service & Distributed Denial of Service Attacks
The presence of cloud computing in IoT applications brings up the network traffic issues.
One of the primary issues that are witnessed is in terms of availability attacks on the services
[22]. There may be denial of service and distributed denial of service attacks that may emerge
as a result. There may be unwanted and garbage traffic that may be introduced by the
malevolent entities on the cloud that may disrupt the service continuity and gradually lead to
breakdown [23].
Research Gap
The researchers have primarily focussed on the device-related security issues and threats that
emerge due to vulnerabilities in cloud. There are several user-related problems, involvement
of other technologies, such as artificial intelligence, business intelligence, machine learning
5
associated with these apps [17]. The components and things that are identified in the
application shall interact with the appropriate cloud service to maintain and adhere to the
security protocols. There are considerations that are involved in this process as well. For
instance, if a component classifies the data that needs to be transmitted to numerous
destinations, then the selection of the same is a complex process. This may bring up the
security concerns and threats [18].
Scale Management for IoT-Cloud
In the cloud-based IoT applications, there are a huge number of clients that the application
shall interact with. Also, there may be issues associated with data velocity, variety, and
volume. The cloud services that are involved shall efficiently manage the data loads and
volumes for preventing and avoiding the security issues [19]. The failure in maintaining the
scalability may lead to issues in the availability of data and application services. This comes
up as a major challenge as the cloud-enabled applications cannot completely rely on elasticity
of the services and applications.
System and data logs are necessary to ensure that all the components behave as per the
regulations and policies [20]. The processes of logging and auditing suffer from scalability
issues in cloud-based IoT applications that may enhance the likelihood of the emergence of
data availability concerns. The management of location of these logs also emerges as a
security consideration. The inefficient procedures involved may have an adverse implication
of the confidentiality, integrity, and availability of the IoT data and information sets [21].
Denial of Service & Distributed Denial of Service Attacks
The presence of cloud computing in IoT applications brings up the network traffic issues.
One of the primary issues that are witnessed is in terms of availability attacks on the services
[22]. There may be denial of service and distributed denial of service attacks that may emerge
as a result. There may be unwanted and garbage traffic that may be introduced by the
malevolent entities on the cloud that may disrupt the service continuity and gradually lead to
breakdown [23].
Research Gap
The researchers have primarily focussed on the device-related security issues and threats that
emerge due to vulnerabilities in cloud. There are several user-related problems, involvement
of other technologies, such as artificial intelligence, business intelligence, machine learning
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cloud Computing in IoT Security
etc. that also lead to the development of newer security threats. These areas are not
researched extensively and gaps are found in association with the same.
Aim of the Research
The aim of the research is to cover all of the security aspects with the involvement of cloud
computing in IoT through qualitative research analysis and data collection. It also aims to
present the possible solutions and countermeasures that may be applied.
Materials & Methods
The data collection methods for qualitative research analysis are domain analysis,
observations, surveys, questionnaire, brainstorming, group discussions, and interviews.
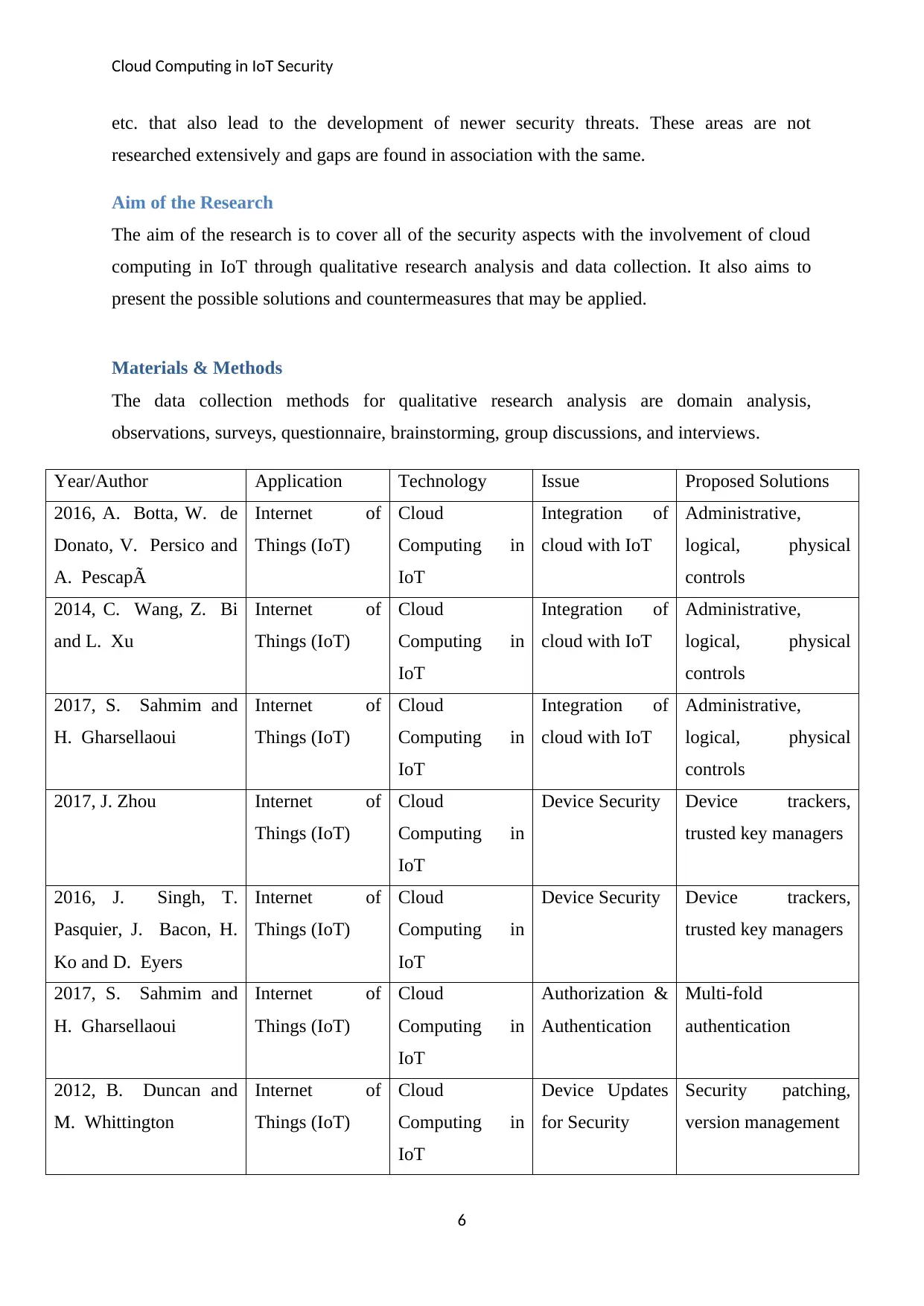
Year/Author Application Technology Issue Proposed Solutions
2016, A. Botta, W. de
Donato, V. Persico and
A. PescapÃ
Internet of
Things (IoT)
Cloud
Computing in
IoT
Integration of
cloud with IoT
Administrative,
logical, physical
controls
2014, C. Wang, Z. Bi
and L. Xu
Internet of
Things (IoT)
Cloud
Computing in
IoT
Integration of
cloud with IoT
Administrative,
logical, physical
controls
2017, S. Sahmim and
H. Gharsellaoui
Internet of
Things (IoT)
Cloud
Computing in
IoT
Integration of
cloud with IoT
Administrative,
logical, physical
controls
2017, J. Zhou Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Security Device trackers,
trusted key managers
2016, J. Singh, T.
Pasquier, J. Bacon, H.
Ko and D. Eyers
Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Security Device trackers,
trusted key managers
2017, S. Sahmim and
H. Gharsellaoui
Internet of
Things (IoT)
Cloud
Computing in
IoT
Authorization &
Authentication
Multi-fold
authentication
2012, B. Duncan and
M. Whittington
Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Updates
for Security
Security patching,
version management
6
etc. that also lead to the development of newer security threats. These areas are not
researched extensively and gaps are found in association with the same.
Aim of the Research
The aim of the research is to cover all of the security aspects with the involvement of cloud
computing in IoT through qualitative research analysis and data collection. It also aims to
present the possible solutions and countermeasures that may be applied.
Materials & Methods
The data collection methods for qualitative research analysis are domain analysis,
observations, surveys, questionnaire, brainstorming, group discussions, and interviews.
Year/Author Application Technology Issue Proposed Solutions
2016, A. Botta, W. de
Donato, V. Persico and
A. PescapÃ
Internet of
Things (IoT)
Cloud
Computing in
IoT
Integration of
cloud with IoT
Administrative,
logical, physical
controls
2014, C. Wang, Z. Bi
and L. Xu
Internet of
Things (IoT)
Cloud
Computing in
IoT
Integration of
cloud with IoT
Administrative,
logical, physical
controls
2017, S. Sahmim and
H. Gharsellaoui
Internet of
Things (IoT)
Cloud
Computing in
IoT
Integration of
cloud with IoT
Administrative,
logical, physical
controls
2017, J. Zhou Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Security Device trackers,
trusted key managers
2016, J. Singh, T.
Pasquier, J. Bacon, H.
Ko and D. Eyers
Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Security Device trackers,
trusted key managers
2017, S. Sahmim and
H. Gharsellaoui
Internet of
Things (IoT)
Cloud
Computing in
IoT
Authorization &
Authentication
Multi-fold
authentication
2012, B. Duncan and
M. Whittington
Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Updates
for Security
Security patching,
version management
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cloud Computing in IoT Security
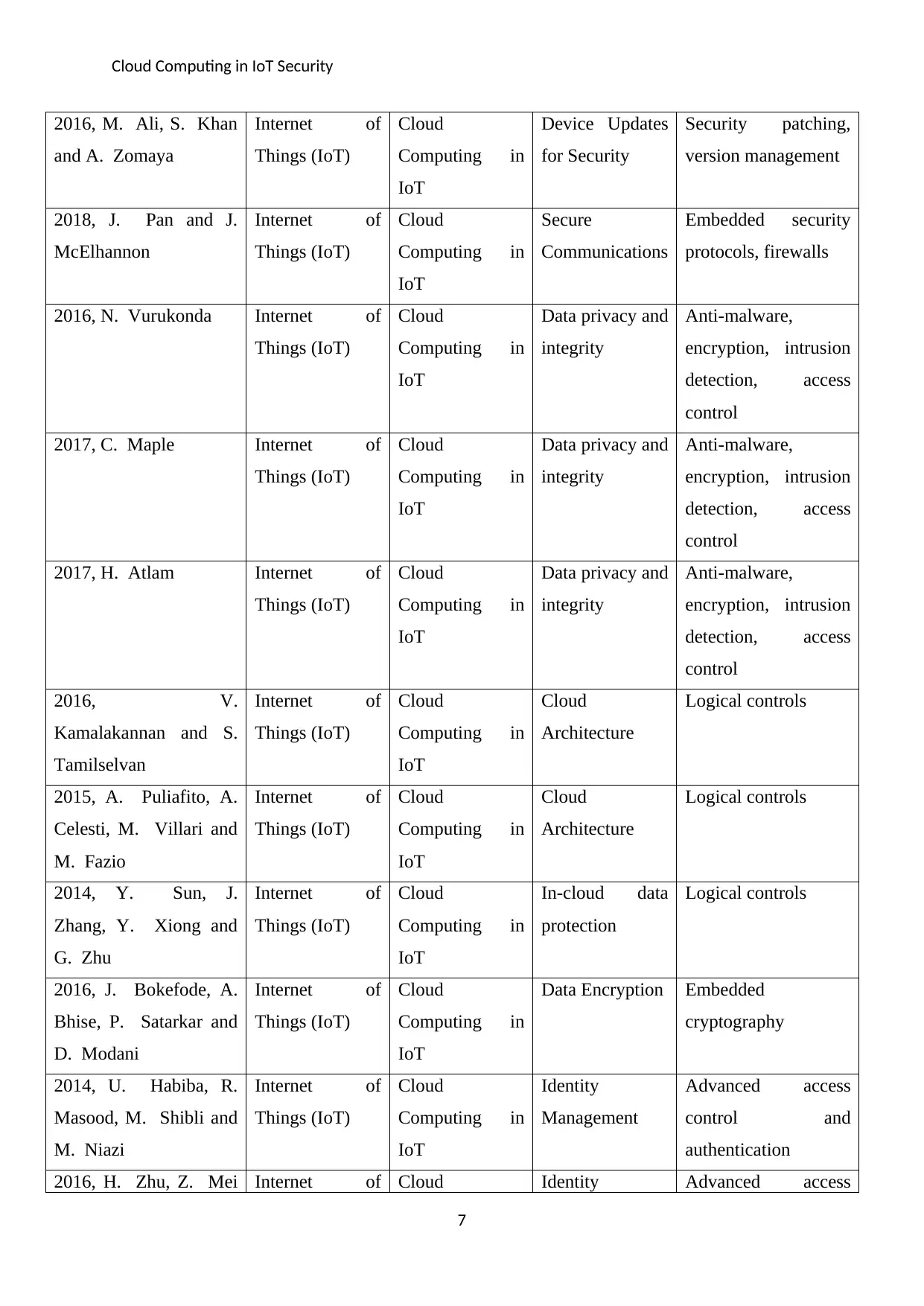
2016, M. Ali, S. Khan
and A. Zomaya
Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Updates
for Security
Security patching,
version management
2018, J. Pan and J.
McElhannon
Internet of
Things (IoT)
Cloud
Computing in
IoT
Secure
Communications
Embedded security
protocols, firewalls
2016, N. Vurukonda Internet of
Things (IoT)
Cloud
Computing in
IoT
Data privacy and
integrity
Anti-malware,
encryption, intrusion
detection, access
control
2017, C. Maple Internet of
Things (IoT)
Cloud
Computing in
IoT
Data privacy and
integrity
Anti-malware,
encryption, intrusion
detection, access
control
2017, H. Atlam Internet of
Things (IoT)
Cloud
Computing in
IoT
Data privacy and
integrity
Anti-malware,
encryption, intrusion
detection, access
control
2016, V.
Kamalakannan and S.
Tamilselvan
Internet of
Things (IoT)
Cloud
Computing in
IoT
Cloud
Architecture
Logical controls
2015, A. Puliafito, A.
Celesti, M. Villari and
M. Fazio
Internet of
Things (IoT)
Cloud
Computing in
IoT
Cloud
Architecture
Logical controls
2014, Y. Sun, J.
Zhang, Y. Xiong and
G. Zhu
Internet of
Things (IoT)
Cloud
Computing in
IoT
In-cloud data
protection
Logical controls
2016, J. Bokefode, A.
Bhise, P. Satarkar and
D. Modani
Internet of
Things (IoT)
Cloud
Computing in
IoT
Data Encryption Embedded
cryptography
2014, U. Habiba, R.
Masood, M. Shibli and
M. Niazi
Internet of
Things (IoT)
Cloud
Computing in
IoT
Identity
Management
Advanced access
control and
authentication
2016, H. Zhu, Z. Mei Internet of Cloud Identity Advanced access
7
2016, M. Ali, S. Khan
and A. Zomaya
Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Updates
for Security
Security patching,
version management
2018, J. Pan and J.
McElhannon
Internet of
Things (IoT)
Cloud
Computing in
IoT
Secure
Communications
Embedded security
protocols, firewalls
2016, N. Vurukonda Internet of
Things (IoT)
Cloud
Computing in
IoT
Data privacy and
integrity
Anti-malware,
encryption, intrusion
detection, access
control
2017, C. Maple Internet of
Things (IoT)
Cloud
Computing in
IoT
Data privacy and
integrity
Anti-malware,
encryption, intrusion
detection, access
control
2017, H. Atlam Internet of
Things (IoT)
Cloud
Computing in
IoT
Data privacy and
integrity
Anti-malware,
encryption, intrusion
detection, access
control
2016, V.
Kamalakannan and S.
Tamilselvan
Internet of
Things (IoT)
Cloud
Computing in
IoT
Cloud
Architecture
Logical controls
2015, A. Puliafito, A.
Celesti, M. Villari and
M. Fazio
Internet of
Things (IoT)
Cloud
Computing in
IoT
Cloud
Architecture
Logical controls
2014, Y. Sun, J.
Zhang, Y. Xiong and
G. Zhu
Internet of
Things (IoT)
Cloud
Computing in
IoT
In-cloud data
protection
Logical controls
2016, J. Bokefode, A.
Bhise, P. Satarkar and
D. Modani
Internet of
Things (IoT)
Cloud
Computing in
IoT
Data Encryption Embedded
cryptography
2014, U. Habiba, R.
Masood, M. Shibli and
M. Niazi
Internet of
Things (IoT)
Cloud
Computing in
IoT
Identity
Management
Advanced access
control and
authentication
2016, H. Zhu, Z. Mei Internet of Cloud Identity Advanced access
7
Cloud Computing in IoT Security
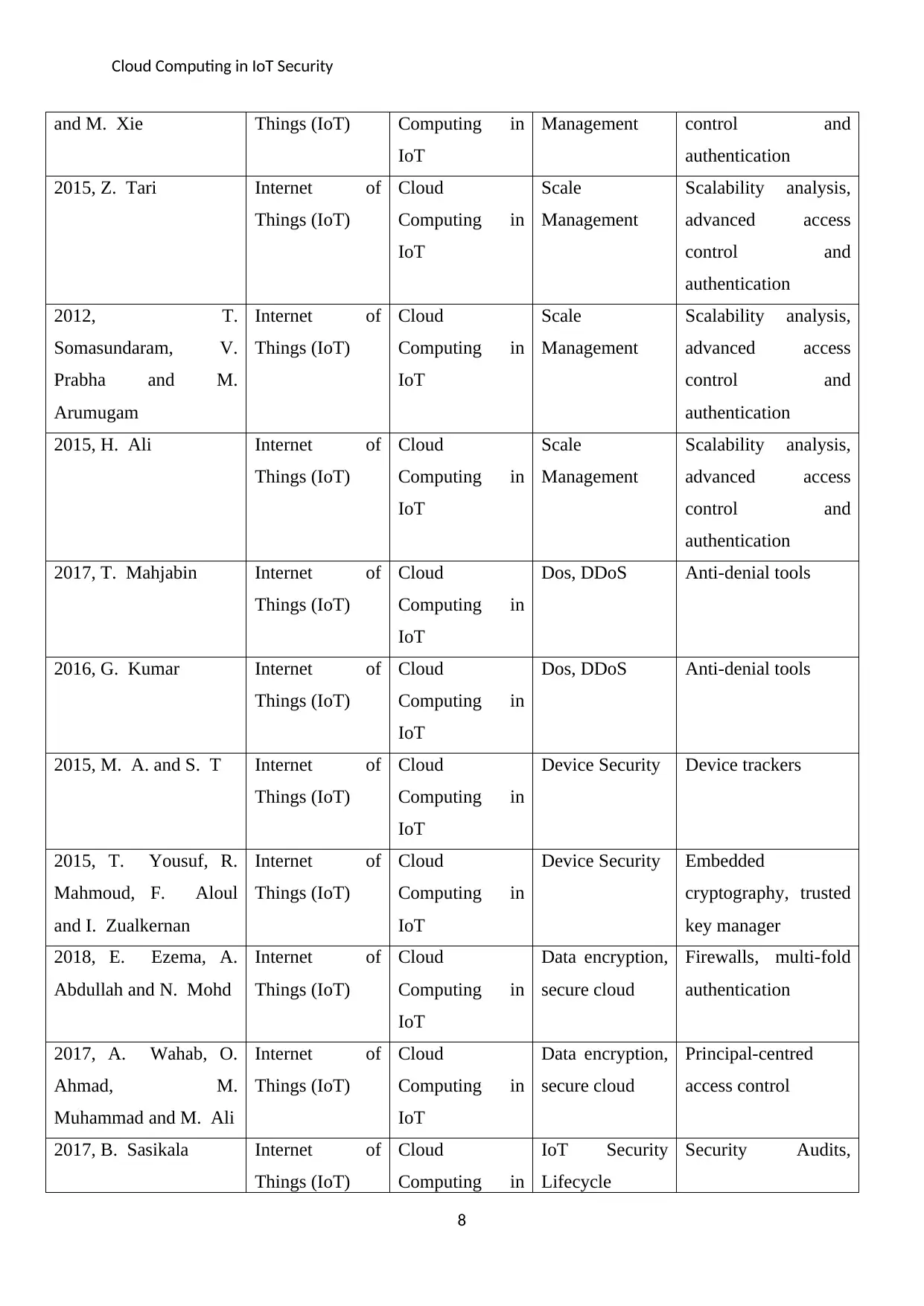
and M. Xie Things (IoT) Computing in
IoT
Management control and
authentication
2015, Z. Tari Internet of
Things (IoT)
Cloud
Computing in
IoT
Scale
Management
Scalability analysis,
advanced access
control and
authentication
2012, T.
Somasundaram, V.
Prabha and M.
Arumugam
Internet of
Things (IoT)
Cloud
Computing in
IoT
Scale
Management
Scalability analysis,
advanced access
control and
authentication
2015, H. Ali Internet of
Things (IoT)
Cloud
Computing in
IoT
Scale
Management
Scalability analysis,
advanced access
control and
authentication
2017, T. Mahjabin Internet of
Things (IoT)
Cloud
Computing in
IoT
Dos, DDoS Anti-denial tools
2016, G. Kumar Internet of
Things (IoT)
Cloud
Computing in
IoT
Dos, DDoS Anti-denial tools
2015, M. A. and S. T Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Security Device trackers
2015, T. Yousuf, R.
Mahmoud, F. Aloul
and I. Zualkernan
Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Security Embedded
cryptography, trusted
key manager
2018, E. Ezema, A.
Abdullah and N. Mohd
Internet of
Things (IoT)
Cloud
Computing in
IoT
Data encryption,
secure cloud
Firewalls, multi-fold
authentication
2017, A. Wahab, O.
Ahmad, M.
Muhammad and M. Ali
Internet of
Things (IoT)
Cloud
Computing in
IoT
Data encryption,
secure cloud
Principal-centred
access control
2017, B. Sasikala Internet of
Things (IoT)
Cloud
Computing in
IoT Security
Lifecycle
Security Audits,
8
and M. Xie Things (IoT) Computing in
IoT
Management control and
authentication
2015, Z. Tari Internet of
Things (IoT)
Cloud
Computing in
IoT
Scale
Management
Scalability analysis,
advanced access
control and
authentication
2012, T.
Somasundaram, V.
Prabha and M.
Arumugam
Internet of
Things (IoT)
Cloud
Computing in
IoT
Scale
Management
Scalability analysis,
advanced access
control and
authentication
2015, H. Ali Internet of
Things (IoT)
Cloud
Computing in
IoT
Scale
Management
Scalability analysis,
advanced access
control and
authentication
2017, T. Mahjabin Internet of
Things (IoT)
Cloud
Computing in
IoT
Dos, DDoS Anti-denial tools
2016, G. Kumar Internet of
Things (IoT)
Cloud
Computing in
IoT
Dos, DDoS Anti-denial tools
2015, M. A. and S. T Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Security Device trackers
2015, T. Yousuf, R.
Mahmoud, F. Aloul
and I. Zualkernan
Internet of
Things (IoT)
Cloud
Computing in
IoT
Device Security Embedded
cryptography, trusted
key manager
2018, E. Ezema, A.
Abdullah and N. Mohd
Internet of
Things (IoT)
Cloud
Computing in
IoT
Data encryption,
secure cloud
Firewalls, multi-fold
authentication
2017, A. Wahab, O.
Ahmad, M.
Muhammad and M. Ali
Internet of
Things (IoT)
Cloud
Computing in
IoT
Data encryption,
secure cloud
Principal-centred
access control
2017, B. Sasikala Internet of
Things (IoT)
Cloud
Computing in
IoT Security
Lifecycle
Security Audits,
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cloud Computing in IoT Security
IoT Management inspections
2015, J. Eom Internet of
Things (IoT)
Cloud
Computing in
IoT
Integration of
cloud with IoT
Administrative
controls
2018, G. Gupta Internet of
Things (IoT)
Cloud
Computing in
IoT
Integration of
cloud with IoT
Administrative
controls
Discussion
Set of Countermeasures & Solutions
There are three categories of countermeasures and solutions that shall be used.
Device Security
There shall be measures that shall be adopted for enhancing the device security in IoT
application. String authentication token shall be used for cellular application for encryption
and authentication of the data sets. There shall also be trackers included in the device to
monitor the same in case of loss [24]. These trackers shall also lock the security keys and
credentials in an automated manner. Embedded cryptographic tools shall be utilized for
enhanced authentication and identity management. A trusted key manager along with the IP
protection tools shall be integrated with the IoT devices for improved security [25].
Securing the Cloud
The cloud architecture and infrastructure shall be secured to maintain the security of the
application data and services. There are automated tools that have been developed in terms of
anti-malware and anti-denial tools. These tools shall be implemented in the cloud along with
the network-based intrusion detection and prevention applications. There shall also be
firewalls and multi-fold authentication measures implemented for improved access control
and management [26]. There are also data encryption algorithms and protocols that have been
defined to ensure the security of cloud.
The legal and regulatory compliance shall be assured with the certification of the cloud
service provider. The norms on data ownership, authority, and sharing shall be defined as
well. Sharing of the resources and information shall be controlled according to the policy and
9
IoT Management inspections
2015, J. Eom Internet of
Things (IoT)
Cloud
Computing in
IoT
Integration of
cloud with IoT
Administrative
controls
2018, G. Gupta Internet of
Things (IoT)
Cloud
Computing in
IoT
Integration of
cloud with IoT
Administrative
controls
Discussion
Set of Countermeasures & Solutions
There are three categories of countermeasures and solutions that shall be used.
Device Security
There shall be measures that shall be adopted for enhancing the device security in IoT
application. String authentication token shall be used for cellular application for encryption
and authentication of the data sets. There shall also be trackers included in the device to
monitor the same in case of loss [24]. These trackers shall also lock the security keys and
credentials in an automated manner. Embedded cryptographic tools shall be utilized for
enhanced authentication and identity management. A trusted key manager along with the IP
protection tools shall be integrated with the IoT devices for improved security [25].
Securing the Cloud
The cloud architecture and infrastructure shall be secured to maintain the security of the
application data and services. There are automated tools that have been developed in terms of
anti-malware and anti-denial tools. These tools shall be implemented in the cloud along with
the network-based intrusion detection and prevention applications. There shall also be
firewalls and multi-fold authentication measures implemented for improved access control
and management [26]. There are also data encryption algorithms and protocols that have been
defined to ensure the security of cloud.
The legal and regulatory compliance shall be assured with the certification of the cloud
service provider. The norms on data ownership, authority, and sharing shall be defined as
well. Sharing of the resources and information shall be controlled according to the policy and
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing in IoT Security
information regarding the same shall also be circulated [27]. Principal-centred access control
policies and mechanisms shall be utilized for secure data sharing and access.
IoT Security Lifecycle Management
The lifecycle of the security components shall be maintained across all the devices and cloud
components by adopting a scalable and long-term security strategy. There may be changes
that may be required to be done in the security strategies over time. These changes shall be
regularly identified and implemented with the mechanisms as security audits, review, and
inspection [28]. There may also be new devices added to the application and the lifecycle that
may bring up the need of managing secure firmware. There shall be enhanced management of
keys and token that shall be implemented. Trusted services hubs shall be utilized as central
interconnection platform on the application.
Recommendations & Conclusion
Apart from the security solutions and controls that are described above, there shall also be
administrative controls that shall be installed by the business organizations that provide IoT
applications and services based on cloud computing [29]. These administrative controls
include enhancement of security plans and policies, implementation of advanced access
control, use of automated tools for security audits and reviews, and monitoring of system
logs. There are several benefits that cloud computing offers to IoT. However, there are
certain security issues and threats that have emerged with the involvement of cloud
computing in IoT [30].
10
information regarding the same shall also be circulated [27]. Principal-centred access control
policies and mechanisms shall be utilized for secure data sharing and access.
IoT Security Lifecycle Management
The lifecycle of the security components shall be maintained across all the devices and cloud
components by adopting a scalable and long-term security strategy. There may be changes
that may be required to be done in the security strategies over time. These changes shall be
regularly identified and implemented with the mechanisms as security audits, review, and
inspection [28]. There may also be new devices added to the application and the lifecycle that
may bring up the need of managing secure firmware. There shall be enhanced management of
keys and token that shall be implemented. Trusted services hubs shall be utilized as central
interconnection platform on the application.
Recommendations & Conclusion
Apart from the security solutions and controls that are described above, there shall also be
administrative controls that shall be installed by the business organizations that provide IoT
applications and services based on cloud computing [29]. These administrative controls
include enhancement of security plans and policies, implementation of advanced access
control, use of automated tools for security audits and reviews, and monitoring of system
logs. There are several benefits that cloud computing offers to IoT. However, there are
certain security issues and threats that have emerged with the involvement of cloud
computing in IoT [30].
10

Cloud Computing in IoT Security
References
[1]A. Botta, W. de Donato, V. Persico and A. Pescapé, "Integration of Cloud computing
and Internet of Things: A survey", Future Generation Computer Systems, vol. 56, pp. 684-
700, 2016.
[2]C. Wang, Z. Bi and L. Xu, "IoT and Cloud Computing in Automation of Assembly
Modeling Systems", IEEE Transactions on Industrial Informatics, vol. 10, no. 2, pp. 1426-
1434, 2014.
[3]S. Sahmim and H. Gharsellaoui, "Privacy and Security in Internet-based Computing:
Cloud Computing, Internet of Things, Cloud of Things: a review", Procedia Computer
Science, vol. 112, pp. 1516-1522, 2017.
[4]J. Zhou, "Security and Privacy for Cloud-Based IoT: Challenges", IEEE Communications
Magazine, vol. 55, no. 1, pp. 26-33, 2017.
[5]J. Singh, T. Pasquier, J. Bacon, H. Ko and D. Eyers, "Twenty Security Considerations
for Cloud-Supported Internet of Things", IEEE Internet of Things Journal, vol. 3, no. 3, pp.
269-284, 2016.
[6]S. Sahmim and H. Gharsellaoui, "Privacy and Security in Internet-based Computing:
Cloud Computing, Internet of Things, Cloud of Things: a review", Procedia Computer
Science, vol. 112, pp. 1516-1522, 2017.
[7]B. Duncan and M. Whittington, "Cyber Security for Cloud and the Internet of Things:
How Can it be Achieved?", Engineering & Technology Reference, vol. 1, no. 1, 2012.
[8]M. Ali, S. Khan and A. Zomaya, "Security and Dependability of Cloud-Assisted Internet
of Things", IEEE Cloud Computing, vol. 3, no. 2, pp. 24-26, 2016.
[9]J. Pan and J. McElhannon, "Future Edge Cloud and Edge Computing for Internet of
Things Applications", IEEE Internet of Things Journal, vol. 5, no. 1, pp. 439-449, 2018.
[10]N. Vurukonda, "A Study on Data Storage Security Issues in Cloud Computing",
Procedia Computer Science, vol. 92, pp. 128-135, 2016.
[11]C. Maple, "Security and privacy in the internet of things", Journal of Cyber Policy, vol.
2, no. 2, pp. 155-184, 2017.
11
References
[1]A. Botta, W. de Donato, V. Persico and A. Pescapé, "Integration of Cloud computing
and Internet of Things: A survey", Future Generation Computer Systems, vol. 56, pp. 684-
700, 2016.
[2]C. Wang, Z. Bi and L. Xu, "IoT and Cloud Computing in Automation of Assembly
Modeling Systems", IEEE Transactions on Industrial Informatics, vol. 10, no. 2, pp. 1426-
1434, 2014.
[3]S. Sahmim and H. Gharsellaoui, "Privacy and Security in Internet-based Computing:
Cloud Computing, Internet of Things, Cloud of Things: a review", Procedia Computer
Science, vol. 112, pp. 1516-1522, 2017.
[4]J. Zhou, "Security and Privacy for Cloud-Based IoT: Challenges", IEEE Communications
Magazine, vol. 55, no. 1, pp. 26-33, 2017.
[5]J. Singh, T. Pasquier, J. Bacon, H. Ko and D. Eyers, "Twenty Security Considerations
for Cloud-Supported Internet of Things", IEEE Internet of Things Journal, vol. 3, no. 3, pp.
269-284, 2016.
[6]S. Sahmim and H. Gharsellaoui, "Privacy and Security in Internet-based Computing:
Cloud Computing, Internet of Things, Cloud of Things: a review", Procedia Computer
Science, vol. 112, pp. 1516-1522, 2017.
[7]B. Duncan and M. Whittington, "Cyber Security for Cloud and the Internet of Things:
How Can it be Achieved?", Engineering & Technology Reference, vol. 1, no. 1, 2012.
[8]M. Ali, S. Khan and A. Zomaya, "Security and Dependability of Cloud-Assisted Internet
of Things", IEEE Cloud Computing, vol. 3, no. 2, pp. 24-26, 2016.
[9]J. Pan and J. McElhannon, "Future Edge Cloud and Edge Computing for Internet of
Things Applications", IEEE Internet of Things Journal, vol. 5, no. 1, pp. 439-449, 2018.
[10]N. Vurukonda, "A Study on Data Storage Security Issues in Cloud Computing",
Procedia Computer Science, vol. 92, pp. 128-135, 2016.
[11]C. Maple, "Security and privacy in the internet of things", Journal of Cyber Policy, vol.
2, no. 2, pp. 155-184, 2017.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





