Cloud Computing Solution: Addressing Business Challenges for Fastfix
VerifiedAdded on 2023/01/12
|24
|5323
|93
Report
AI Summary
This report provides a comprehensive analysis of a cloud computing solution tailored for Fastfix, a business facing challenges in its operations. The report begins with an introduction to cloud computing, its evolution, and the specific problems faced by Fastfix, such as slow response times and inefficient business processes. It proposes cloud computing as a viable solution, highlighting its appropriateness by discussing features like resource pooling and improved functionalities. The architectural design for Fastfix's cloud implementation is detailed, followed by an examination of various deployment models, including private, public, community, and hybrid clouds, with a recommendation for the most suitable option. The report then explores service models such as IaaS, PaaS, and SaaS, explaining their applicability to Fastfix. Furthermore, it addresses data migration strategies, configuration with a CSP framework, and implementation using open-source tools. The report concludes with a discussion of potential security issues and ways to mitigate them, offering a complete overview of the cloud computing solution for Fastfix, supported by references to relevant sources.

Cloud Computing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.................................................................................................................................................3
Background of cloud and its evolution....................................................................................................3
Problem and solution...............................................................................................................................4
Appropriateness of solution.....................................................................................................................5
Architectural design.................................................................................................................................5
Deployment Model..................................................................................................................................7
Service Model..........................................................................................................................................8
Data Migration........................................................................................................................................9
Configuration of cloud with CSP framework........................................................................................10
Implementation of cloud platform using open source tool.....................................................................12
Probable solution to problems...............................................................................................................14
Security issues.......................................................................................................................................15
Ways to overcome issues.......................................................................................................................15
Conclusion.................................................................................................................................................16
References.................................................................................................................................................17
Introduction.................................................................................................................................................3
Background of cloud and its evolution....................................................................................................3
Problem and solution...............................................................................................................................4
Appropriateness of solution.....................................................................................................................5
Architectural design.................................................................................................................................5
Deployment Model..................................................................................................................................7
Service Model..........................................................................................................................................8
Data Migration........................................................................................................................................9
Configuration of cloud with CSP framework........................................................................................10
Implementation of cloud platform using open source tool.....................................................................12
Probable solution to problems...............................................................................................................14
Security issues.......................................................................................................................................15
Ways to overcome issues.......................................................................................................................15
Conclusion.................................................................................................................................................16
References.................................................................................................................................................17

Introduction
According to Microsoft, Cloud computing implies delivery of computing services which
includes database, networking, servers, intelligence, analytics and software over internet for
offering flexible resources, economies of scale and faster innovation (What is cloud computing?,
2020). Basically, it implies furnishing of on-demand computing services which varies from app
to storage along with processing power via internet as well as pay as you go basis. To understand
the concept of cloud computing Fastfix is taken into consideration which provides Matika tools
at minimum prices. They are from Bristol who are official distributors from 1990 and renders
online tools. This report comprises of history of cloud, description of problem, solution and its
relevance. Furthermore, it also includes service and deployment models along with data
migration. Along with this, some cloud computing solutions are also implemented that are
provided by cloud service providers and as open source tool. Certain issues along with their
solutions will also be discussed.
Background of cloud and its evolution
The type of computing which is dependent on shared computing resources instead of
personal devices or local servers for handling applications is referred to as cloud computing. The
rationale behind cloud computing is that in 1950s mainframe computing was utilized; they were
huge as well as expensive. For this reason, time sharing schedule were implemented that enabled
users to have access central mainframe systems via connected stations. It provided a shared
computational power and from here cloud computing started (Kumar and Kumar, 2013). In
1960’s, enhancement came in this when American computer scientist conceptualized the concept
of interconnected system of computers. In 1969, ARPANET (Advanced Research Projects
Agency Network) which permitted sharing of digital sources that are not present at physical
location. Virtual machine operating system was released by IBM in s1972 and in this way the
process of sharing data via online medium evolved by making use of internet.
According to Microsoft, Cloud computing implies delivery of computing services which
includes database, networking, servers, intelligence, analytics and software over internet for
offering flexible resources, economies of scale and faster innovation (What is cloud computing?,
2020). Basically, it implies furnishing of on-demand computing services which varies from app
to storage along with processing power via internet as well as pay as you go basis. To understand
the concept of cloud computing Fastfix is taken into consideration which provides Matika tools
at minimum prices. They are from Bristol who are official distributors from 1990 and renders
online tools. This report comprises of history of cloud, description of problem, solution and its
relevance. Furthermore, it also includes service and deployment models along with data
migration. Along with this, some cloud computing solutions are also implemented that are
provided by cloud service providers and as open source tool. Certain issues along with their
solutions will also be discussed.
Background of cloud and its evolution
The type of computing which is dependent on shared computing resources instead of
personal devices or local servers for handling applications is referred to as cloud computing. The
rationale behind cloud computing is that in 1950s mainframe computing was utilized; they were
huge as well as expensive. For this reason, time sharing schedule were implemented that enabled
users to have access central mainframe systems via connected stations. It provided a shared
computational power and from here cloud computing started (Kumar and Kumar, 2013). In
1960’s, enhancement came in this when American computer scientist conceptualized the concept
of interconnected system of computers. In 1969, ARPANET (Advanced Research Projects
Agency Network) which permitted sharing of digital sources that are not present at physical
location. Virtual machine operating system was released by IBM in s1972 and in this way the
process of sharing data via online medium evolved by making use of internet.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Illustration 1: The History of the Cloud
AWS (Amazon Web Services) was brought within market in early 2000’s then in 2006
Amazon released EC2 (Elastic Compute Cloud) which allowed individuals as well as firms to
rent virtual systems by which firm like Fastfix can make use of their applications as well as
programs. From then there has been a explosive growth within cloud computing and it is being
widely used. Large firms like Adobe, Oracle, Microsoft, etc. are providing different options to
other organizations. There has to be a service level agreement (SLA) which takes place among
vendor and user. Along with this, service provider will be answerable to users if as per the
agreement services are not delivered to them.
Problem and solution
Fastfix provides their customers Matika tools which are supplied with UK Makita warranty
and they will also give UK VAT invoice when products are bought by them. This clearly
illustrates that firm provides authorized services but their customers and even employees goes
through certain problems. There is no instant response, lack of quick access and ineffectiveness
in business processes (Lee, 2012). These problems can be handled by cloud computing. The
reason behind this can be understood by taking some examples in this context, Google Assistant,
Alexa and Siri are cloud dependent bots which leverage computing capabilities to furnish
personalized customer experiences. Time which is needed for accessing services was more as
there was no centralized database that will enable to have delays within their project. This leads
AWS (Amazon Web Services) was brought within market in early 2000’s then in 2006
Amazon released EC2 (Elastic Compute Cloud) which allowed individuals as well as firms to
rent virtual systems by which firm like Fastfix can make use of their applications as well as
programs. From then there has been a explosive growth within cloud computing and it is being
widely used. Large firms like Adobe, Oracle, Microsoft, etc. are providing different options to
other organizations. There has to be a service level agreement (SLA) which takes place among
vendor and user. Along with this, service provider will be answerable to users if as per the
agreement services are not delivered to them.
Problem and solution
Fastfix provides their customers Matika tools which are supplied with UK Makita warranty
and they will also give UK VAT invoice when products are bought by them. This clearly
illustrates that firm provides authorized services but their customers and even employees goes
through certain problems. There is no instant response, lack of quick access and ineffectiveness
in business processes (Lee, 2012). These problems can be handled by cloud computing. The
reason behind this can be understood by taking some examples in this context, Google Assistant,
Alexa and Siri are cloud dependent bots which leverage computing capabilities to furnish
personalized customer experiences. Time which is needed for accessing services was more as
there was no centralized database that will enable to have delays within their project. This leads
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

to create a negative impact on organization as well as their productivity. This implies that instant
response and quick access to data will be attained by individuals depending upon whether they
are clients or employees. Chatbots have expanded computing power as well as capacity of cloud
as through this preferences about users are stored. That aids within furnishing quick response as
well as access.
There is ineffectiveness in the way services are being carried out by Fastfix as adequate
response is not provided to their customers (Modi and et. al, 2013). This denotes that there is a
need for relevant business processes that involves ERP (Enterprise Resource Planning) and CRM
(Customer Relationship Management). Marketo, Hubspot, Salesforce are instances of cloud
service providers. This method is efficient as well as cost effective for Fastfix as it will enable
them to manage their operations without any kind of hassle and security of critical business
resources. Along with this, it will enable firm within formulation of plans accordingly, monitor
overall activities carried out. This implies that cloud computing is an appropriate solution for an
organization.
Appropriateness of solution
As per the above discussion, it has been identified that cloud computing is an adequate
solution as it will allow firm to have amplified functionalities. It is a model that enables
ubiquitous, on-demand and convenient network access for computing resources, The
appropriateness of cloud computing can be understood by taking into account certain fact that it
will enable Fastfix to have resource pooling as this furnish services to various customers (Nabi,
Jamwal and Padmanbh, 2020). This will allow all stakeholders to have access to virtual
resources. Furthermore, the downtime will be low and updates are also compatible as well as
bugs can be fixed faster.
Architectural design
The technological model comprises of architecture on the basis of which entire model
carries their functions that will illustrate hierarchical view for describing technology. This will
illustrate the dependencies on which firm will work on (Neware and et. al, 2020). With respect to
Fastfix, the architectural design is illustrated below:
response and quick access to data will be attained by individuals depending upon whether they
are clients or employees. Chatbots have expanded computing power as well as capacity of cloud
as through this preferences about users are stored. That aids within furnishing quick response as
well as access.
There is ineffectiveness in the way services are being carried out by Fastfix as adequate
response is not provided to their customers (Modi and et. al, 2013). This denotes that there is a
need for relevant business processes that involves ERP (Enterprise Resource Planning) and CRM
(Customer Relationship Management). Marketo, Hubspot, Salesforce are instances of cloud
service providers. This method is efficient as well as cost effective for Fastfix as it will enable
them to manage their operations without any kind of hassle and security of critical business
resources. Along with this, it will enable firm within formulation of plans accordingly, monitor
overall activities carried out. This implies that cloud computing is an appropriate solution for an
organization.
Appropriateness of solution
As per the above discussion, it has been identified that cloud computing is an adequate
solution as it will allow firm to have amplified functionalities. It is a model that enables
ubiquitous, on-demand and convenient network access for computing resources, The
appropriateness of cloud computing can be understood by taking into account certain fact that it
will enable Fastfix to have resource pooling as this furnish services to various customers (Nabi,
Jamwal and Padmanbh, 2020). This will allow all stakeholders to have access to virtual
resources. Furthermore, the downtime will be low and updates are also compatible as well as
bugs can be fixed faster.
Architectural design
The technological model comprises of architecture on the basis of which entire model
carries their functions that will illustrate hierarchical view for describing technology. This will
illustrate the dependencies on which firm will work on (Neware and et. al, 2020). With respect to
Fastfix, the architectural design is illustrated below:
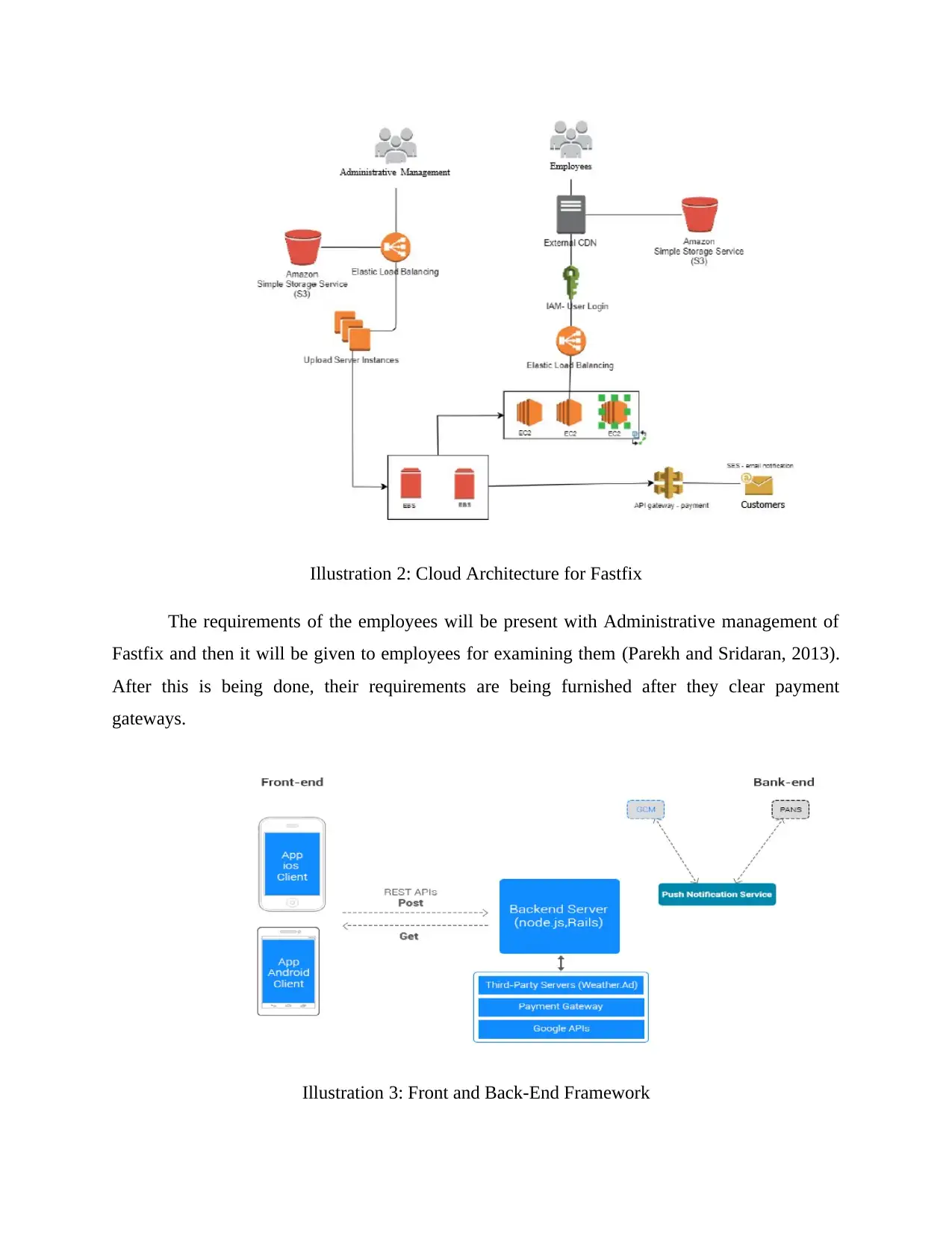
Illustration 2: Cloud Architecture for Fastfix
The requirements of the employees will be present with Administrative management of
Fastfix and then it will be given to employees for examining them (Parekh and Sridaran, 2013).
After this is being done, their requirements are being furnished after they clear payment
gateways.
Illustration 3: Front and Back-End Framework
The requirements of the employees will be present with Administrative management of
Fastfix and then it will be given to employees for examining them (Parekh and Sridaran, 2013).
After this is being done, their requirements are being furnished after they clear payment
gateways.
Illustration 3: Front and Back-End Framework
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
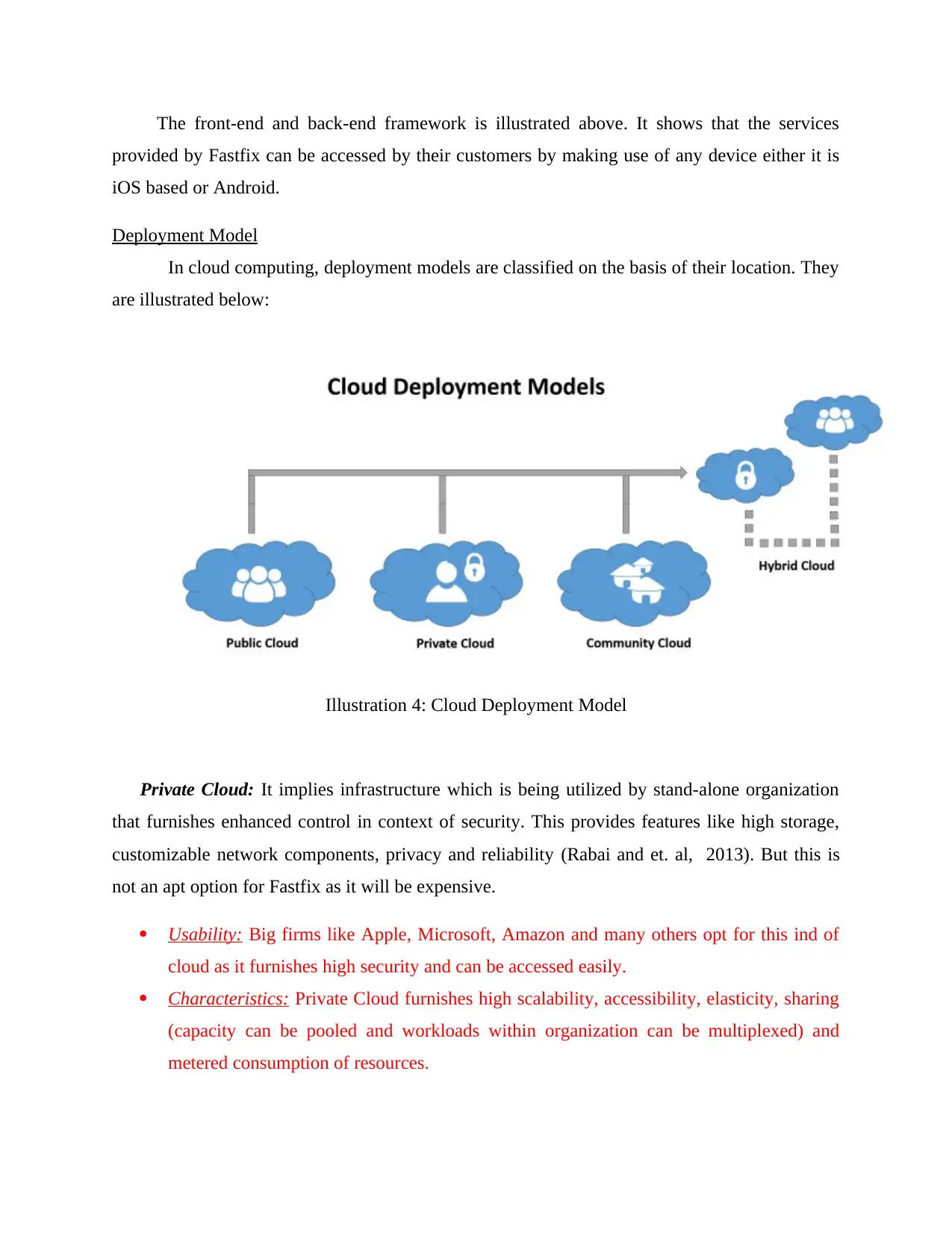
The front-end and back-end framework is illustrated above. It shows that the services
provided by Fastfix can be accessed by their customers by making use of any device either it is
iOS based or Android.
Deployment Model
In cloud computing, deployment models are classified on the basis of their location. They
are illustrated below:
Illustration 4: Cloud Deployment Model
Private Cloud: It implies infrastructure which is being utilized by stand-alone organization
that furnishes enhanced control in context of security. This provides features like high storage,
customizable network components, privacy and reliability (Rabai and et. al, 2013). But this is
not an apt option for Fastfix as it will be expensive.
Usability: Big firms like Apple, Microsoft, Amazon and many others opt for this ind of
cloud as it furnishes high security and can be accessed easily.
Characteristics: Private Cloud furnishes high scalability, accessibility, elasticity, sharing
(capacity can be pooled and workloads within organization can be multiplexed) and
metered consumption of resources.
provided by Fastfix can be accessed by their customers by making use of any device either it is
iOS based or Android.
Deployment Model
In cloud computing, deployment models are classified on the basis of their location. They
are illustrated below:
Illustration 4: Cloud Deployment Model
Private Cloud: It implies infrastructure which is being utilized by stand-alone organization
that furnishes enhanced control in context of security. This provides features like high storage,
customizable network components, privacy and reliability (Rabai and et. al, 2013). But this is
not an apt option for Fastfix as it will be expensive.
Usability: Big firms like Apple, Microsoft, Amazon and many others opt for this ind of
cloud as it furnishes high security and can be accessed easily.
Characteristics: Private Cloud furnishes high scalability, accessibility, elasticity, sharing
(capacity can be pooled and workloads within organization can be multiplexed) and
metered consumption of resources.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Illustration 5 Private Cloud
Advantages: It provides more possibilities for customizing cloud environment along with
high security as well as privacy of resources (as they are not shared with others).
Furthermore, greater control and enhanced reliability will be provided over servers.
Disadvantages: By usage of private cloud it will be more difficult to access data from
remote locations along with this it requires high investments within the infrastructure.
There will be operating expenses as firm will be liable for maintenance cost.
Public Cloud: This is offered for open public use on a network in which customers do not
possess control over physical location of infrastructure where users will pay per use. This will be
an apt option for Fastfix as firm need to pay on the basis of its usage and it provides features like
easy access for data, flexibility, scalability, 24/7 runtime, cost effectiveness and many others.
Usability: This is being used by individuals who need to have access to information or software
for having some results but security is not the major concern.
Advantages: It provides more possibilities for customizing cloud environment along with
high security as well as privacy of resources (as they are not shared with others).
Furthermore, greater control and enhanced reliability will be provided over servers.
Disadvantages: By usage of private cloud it will be more difficult to access data from
remote locations along with this it requires high investments within the infrastructure.
There will be operating expenses as firm will be liable for maintenance cost.
Public Cloud: This is offered for open public use on a network in which customers do not
possess control over physical location of infrastructure where users will pay per use. This will be
an apt option for Fastfix as firm need to pay on the basis of its usage and it provides features like
easy access for data, flexibility, scalability, 24/7 runtime, cost effectiveness and many others.
Usability: This is being used by individuals who need to have access to information or software
for having some results but security is not the major concern.
Characteristics: Public cloud provides users with metered pricing which impies that they
have to pay for services on the basis of how much they have used along with this it also
furnishes self-service management.
Illustration 6 Public Cloud
Advantages: Public cloud minimizes time involved within development, testing as well as
launching of new products. Furthermore, it provides cost effectiveness as there is no need
to make investments within infrastructure and payments have to be made with respect to
what is being used.
Disadvantages: Through the usage of public cloud there is high security risks as there are
vulnerabilities due to shared resources, network performance issues and lack of
customization.
Community Cloud: This is a shared firms that belongs to peculiar community like banks,
government organizations or commercial businesses (Rachana and Guruprasad, 2014). The
benefits provided by this are that it is cheap, easy to collaborate and share data. It won’t be an
have to pay for services on the basis of how much they have used along with this it also
furnishes self-service management.
Illustration 6 Public Cloud
Advantages: Public cloud minimizes time involved within development, testing as well as
launching of new products. Furthermore, it provides cost effectiveness as there is no need
to make investments within infrastructure and payments have to be made with respect to
what is being used.
Disadvantages: Through the usage of public cloud there is high security risks as there are
vulnerabilities due to shared resources, network performance issues and lack of
customization.
Community Cloud: This is a shared firms that belongs to peculiar community like banks,
government organizations or commercial businesses (Rachana and Guruprasad, 2014). The
benefits provided by this are that it is cheap, easy to collaborate and share data. It won’t be an
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

appropriate option for Fastfix due to some problems related with security, privacy and
performance.
Usability: It can be used by any organsiation but mostly small firms opt for this due to
minimized expenses as compared to other clouds. Furthermore, the resources can be
easily shared.
Characteristics: It furnishes firm with flexibility and scalability, availability of services
& reliability along with security and compliance. Community cloud furnishes improvised
services as per requirements of users.
Illustration 7: Community Cloud
Advantages: It provides cost effectiveness as cost is shared among community members
along with this it is easy to share as well as collaborate with others.
Disadvantages: There can be security issues as data is stored at one location which means
that it may be accessed by others who have opted for community cloud. Along with this,
there will be a restricted remote access.
Hybrid Cloud: It incorporates public and private cloud but each entity remains individual. It
provides scalability, improvised security, flexibility, privacy, etc (Sharma and Trivedi, 2014).
performance.
Usability: It can be used by any organsiation but mostly small firms opt for this due to
minimized expenses as compared to other clouds. Furthermore, the resources can be
easily shared.
Characteristics: It furnishes firm with flexibility and scalability, availability of services
& reliability along with security and compliance. Community cloud furnishes improvised
services as per requirements of users.
Illustration 7: Community Cloud
Advantages: It provides cost effectiveness as cost is shared among community members
along with this it is easy to share as well as collaborate with others.
Disadvantages: There can be security issues as data is stored at one location which means
that it may be accessed by others who have opted for community cloud. Along with this,
there will be a restricted remote access.
Hybrid Cloud: It incorporates public and private cloud but each entity remains individual. It
provides scalability, improvised security, flexibility, privacy, etc (Sharma and Trivedi, 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
With reference to Fastfix, it will not be appropriate as it is SME and they do not need to split
their information into mission-critical and non-sensitive context.
Usability: The firms who have high operations and needs to have enhanced processing
power, they opt for hybrid cloud. This furnishes high scalability and agility which makes
it apt for these firms.
Characteristics: High agility is furnished as it comprises of integration of different clouds
and will furnish organizations with competitive edge. Along with this, it renders
unlimited scalability.
Illustration 8: Hybrid Cloud
Advantages: Hybrid cloud furnishes high flexibility as well as control as resources will
be allocated with respect to peculiar area, provides cost effectiveness and amplified
organizational agility.
Disadvantages: They need more maintenance which means that it can be costly for firm
along with this initial cost is also high and data as well as application integration is
challenging while implementing it.
their information into mission-critical and non-sensitive context.
Usability: The firms who have high operations and needs to have enhanced processing
power, they opt for hybrid cloud. This furnishes high scalability and agility which makes
it apt for these firms.
Characteristics: High agility is furnished as it comprises of integration of different clouds
and will furnish organizations with competitive edge. Along with this, it renders
unlimited scalability.
Illustration 8: Hybrid Cloud
Advantages: Hybrid cloud furnishes high flexibility as well as control as resources will
be allocated with respect to peculiar area, provides cost effectiveness and amplified
organizational agility.
Disadvantages: They need more maintenance which means that it can be costly for firm
along with this initial cost is also high and data as well as application integration is
challenging while implementing it.

Service Model
Cloud computing provides various services which can be explicated with respect to roles
played by them. They are as:
Infrastructure as a service: It implies outsourcing of physical infrastructure from third party
providers. In this, IT resources are with external servers which can be accessed by users through
usage of internet connection. IaaS enables firms like Fastfix to buy resources as per their
requirement instead of buying their own infrastructure. The benefits that are being provided by
this are improved flexibility, remote access, scalable, flexibility and many others (Singh, Jeong
and Park, 2016).
Usability: It is a advantageous to small or startup firms who have no budget for creation
of their own infrastructure, there is rapid growth of firm but demands are changeable and
unstable.
Characteristics: It furnishes organizations with automated administrative tasks, dynamic
scaling, platform virtualization technology along with graphical user interface and AAPI-
based access.
Illustration 9: Infrastructure as a Service
Cloud computing provides various services which can be explicated with respect to roles
played by them. They are as:
Infrastructure as a service: It implies outsourcing of physical infrastructure from third party
providers. In this, IT resources are with external servers which can be accessed by users through
usage of internet connection. IaaS enables firms like Fastfix to buy resources as per their
requirement instead of buying their own infrastructure. The benefits that are being provided by
this are improved flexibility, remote access, scalable, flexibility and many others (Singh, Jeong
and Park, 2016).
Usability: It is a advantageous to small or startup firms who have no budget for creation
of their own infrastructure, there is rapid growth of firm but demands are changeable and
unstable.
Characteristics: It furnishes organizations with automated administrative tasks, dynamic
scaling, platform virtualization technology along with graphical user interface and AAPI-
based access.
Illustration 9: Infrastructure as a Service
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



