Cloud Computing Page 1 of 46 1.0 Questions
VerifiedAdded on 2023/04/23
|46
|6158
|499
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

CLOUD COMPUTING
Page 1 of 46
Page 1 of 46
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
1.0 Question 1:.................................................................................................................................3
2.0 Question 2:.................................................................................................................................5
3.0 Question 3:.................................................................................................................................8
4.0 Question 4:...............................................................................................................................15
5.0 Question 5:...............................................................................................................................18
6.0 Question 6:...............................................................................................................................20
7.0 Question 7:...............................................................................................................................23
8.0 Question 8:...............................................................................................................................25
9.0 Question 9:...............................................................................................................................27
10.0 Question 10:...........................................................................................................................29
11.0 Question 11:...........................................................................................................................32
References:....................................................................................................................................35
Appendix:......................................................................................................................................40
Page 2 of 46
1.0 Question 1:.................................................................................................................................3
2.0 Question 2:.................................................................................................................................5
3.0 Question 3:.................................................................................................................................8
4.0 Question 4:...............................................................................................................................15
5.0 Question 5:...............................................................................................................................18
6.0 Question 6:...............................................................................................................................20
7.0 Question 7:...............................................................................................................................23
8.0 Question 8:...............................................................................................................................25
9.0 Question 9:...............................................................................................................................27
10.0 Question 10:...........................................................................................................................29
11.0 Question 11:...........................................................................................................................32
References:....................................................................................................................................35
Appendix:......................................................................................................................................40
Page 2 of 46
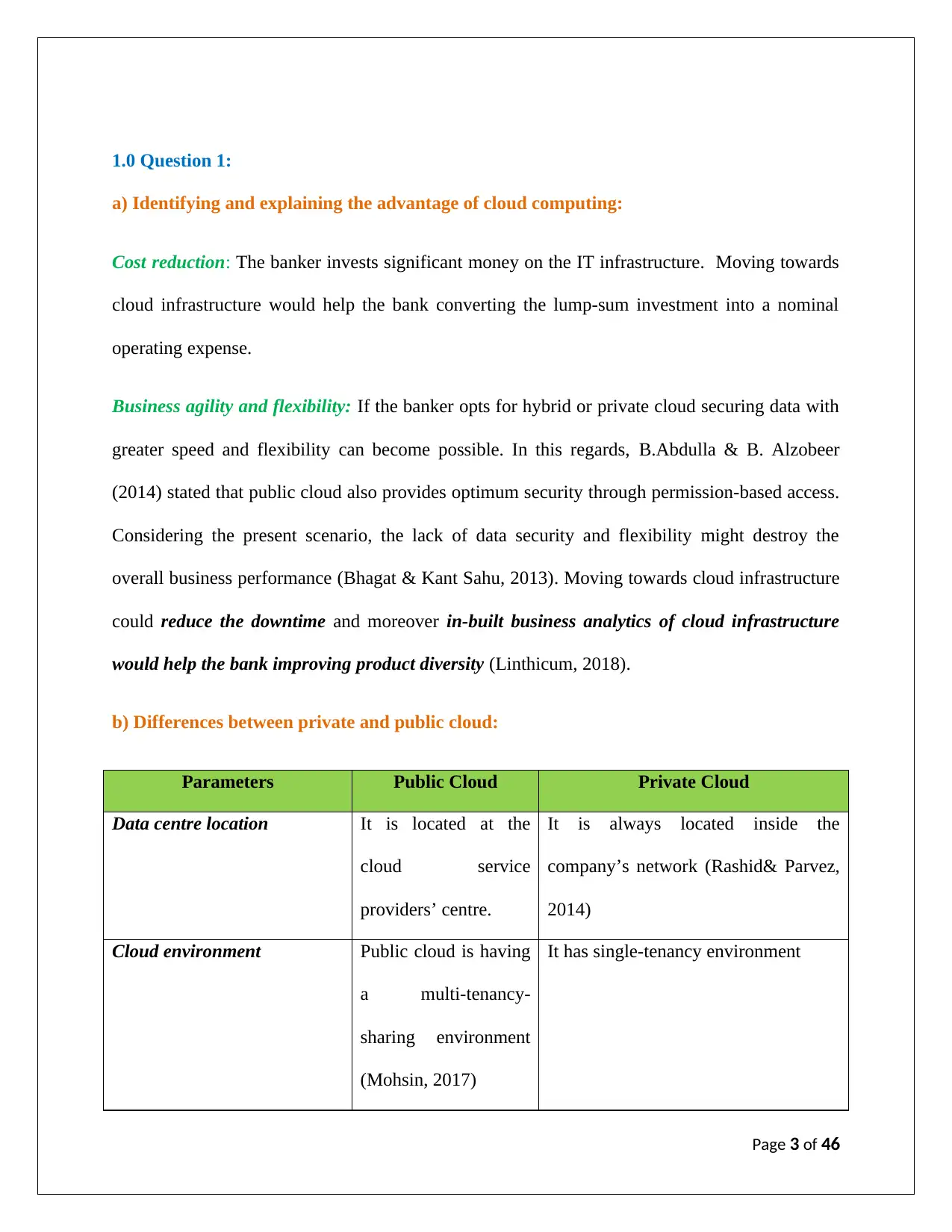
1.0 Question 1:
a) Identifying and explaining the advantage of cloud computing:
Cost reduction: The banker invests significant money on the IT infrastructure. Moving towards
cloud infrastructure would help the bank converting the lump-sum investment into a nominal
operating expense.
Business agility and flexibility: If the banker opts for hybrid or private cloud securing data with
greater speed and flexibility can become possible. In this regards, B.Abdulla & B. Alzobeer
(2014) stated that public cloud also provides optimum security through permission-based access.
Considering the present scenario, the lack of data security and flexibility might destroy the
overall business performance (Bhagat & Kant Sahu, 2013). Moving towards cloud infrastructure
could reduce the downtime and moreover in-built business analytics of cloud infrastructure
would help the bank improving product diversity (Linthicum, 2018).
b) Differences between private and public cloud:
Parameters Public Cloud Private Cloud
Data centre location It is located at the
cloud service
providers’ centre.
It is always located inside the
company’s network (Rashid& Parvez,
2014)
Cloud environment Public cloud is having
a multi-tenancy-
sharing environment
(Mohsin, 2017)
It has single-tenancy environment
Page 3 of 46
a) Identifying and explaining the advantage of cloud computing:
Cost reduction: The banker invests significant money on the IT infrastructure. Moving towards
cloud infrastructure would help the bank converting the lump-sum investment into a nominal
operating expense.
Business agility and flexibility: If the banker opts for hybrid or private cloud securing data with
greater speed and flexibility can become possible. In this regards, B.Abdulla & B. Alzobeer
(2014) stated that public cloud also provides optimum security through permission-based access.
Considering the present scenario, the lack of data security and flexibility might destroy the
overall business performance (Bhagat & Kant Sahu, 2013). Moving towards cloud infrastructure
could reduce the downtime and moreover in-built business analytics of cloud infrastructure
would help the bank improving product diversity (Linthicum, 2018).
b) Differences between private and public cloud:
Parameters Public Cloud Private Cloud
Data centre location It is located at the
cloud service
providers’ centre.
It is always located inside the
company’s network (Rashid& Parvez,
2014)
Cloud environment Public cloud is having
a multi-tenancy-
sharing environment
(Mohsin, 2017)
It has single-tenancy environment
Page 3 of 46
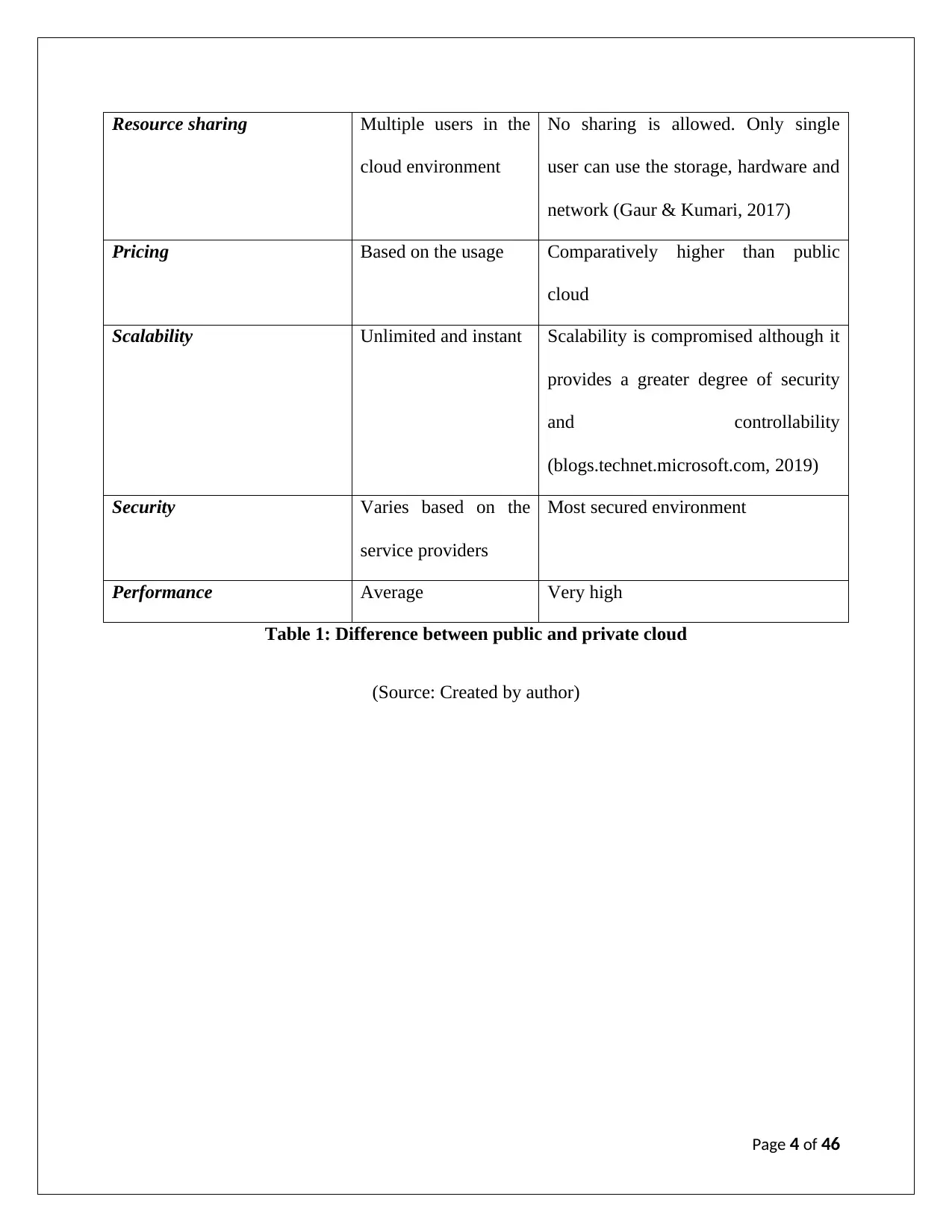
Resource sharing Multiple users in the
cloud environment
No sharing is allowed. Only single
user can use the storage, hardware and
network (Gaur & Kumari, 2017)
Pricing Based on the usage Comparatively higher than public
cloud
Scalability Unlimited and instant Scalability is compromised although it
provides a greater degree of security
and controllability
(blogs.technet.microsoft.com, 2019)
Security Varies based on the
service providers
Most secured environment
Performance Average Very high
Table 1: Difference between public and private cloud
(Source: Created by author)
Page 4 of 46
cloud environment
No sharing is allowed. Only single
user can use the storage, hardware and
network (Gaur & Kumari, 2017)
Pricing Based on the usage Comparatively higher than public
cloud
Scalability Unlimited and instant Scalability is compromised although it
provides a greater degree of security
and controllability
(blogs.technet.microsoft.com, 2019)
Security Varies based on the
service providers
Most secured environment
Performance Average Very high
Table 1: Difference between public and private cloud
(Source: Created by author)
Page 4 of 46
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2.0 Question 2:
a) Methods to implement the private cloud:
A solution architect would follow the steps mentioned herein to implement the private cloud:
Identifying purpose:
This step includes understanding the requirements of the business, security and operational
legislations.
Workload assessment:
As an architect, the most vital responsibility is to address the data load that will run on the
private cloud. Based on this assessment load will be distributed by means of data, application
and infrastructure (Prabha & Dhivya, 2016).
Defining the hardware:
Based on the software applications and existing data, the hardware system would be framed that
is capable of supporting the present requirement and the future need as well (Yamato, 2015).
Defining the software:
This step involves enquiring the client regarding the choice of software. The software is of two
types in private cloud named as ‘proprietary’ or ‘open’. “OpenStack” can be the primary choice
if the client is ready to move to the ‘open software solutions.
Network selection:
Page 5 of 46
a) Methods to implement the private cloud:
A solution architect would follow the steps mentioned herein to implement the private cloud:
Identifying purpose:
This step includes understanding the requirements of the business, security and operational
legislations.
Workload assessment:
As an architect, the most vital responsibility is to address the data load that will run on the
private cloud. Based on this assessment load will be distributed by means of data, application
and infrastructure (Prabha & Dhivya, 2016).
Defining the hardware:
Based on the software applications and existing data, the hardware system would be framed that
is capable of supporting the present requirement and the future need as well (Yamato, 2015).
Defining the software:
This step involves enquiring the client regarding the choice of software. The software is of two
types in private cloud named as ‘proprietary’ or ‘open’. “OpenStack” can be the primary choice
if the client is ready to move to the ‘open software solutions.
Network selection:
Page 5 of 46

Different network provisioning needs to be taken care of by the architect. How the network of
the client company will work on the private cloud needs to be addressed (Barona López, García
Villalba, Valdivieso Caraguay & López, 2015).
Security parameter:
Identity and access management (IAM) needs to be planned so that the right person can be given
the right to access the desired resources at the right time (Chu, Ouyang & Jang, 2012).
Defining governance:
The service governance model needs to be provided to the client firm to enable the required
control by every member.
Defining management tools:
Physical infrastructure, power supply and other parameters are to be implemented and monitored
regularly to avoid any discrepancies.
Final implementation:
This stage includes the staging of the private cloud, hardware and software in the data centre.
Testing and operations:
Test process needs to be defined to verify whether all requirements are met and plans are set for
the security issues, downtime or failure or not. Operations include monitoring the overall
security, governance, automation etc, which is known as CloudOps.
Page 6 of 46
the client company will work on the private cloud needs to be addressed (Barona López, García
Villalba, Valdivieso Caraguay & López, 2015).
Security parameter:
Identity and access management (IAM) needs to be planned so that the right person can be given
the right to access the desired resources at the right time (Chu, Ouyang & Jang, 2012).
Defining governance:
The service governance model needs to be provided to the client firm to enable the required
control by every member.
Defining management tools:
Physical infrastructure, power supply and other parameters are to be implemented and monitored
regularly to avoid any discrepancies.
Final implementation:
This stage includes the staging of the private cloud, hardware and software in the data centre.
Testing and operations:
Test process needs to be defined to verify whether all requirements are met and plans are set for
the security issues, downtime or failure or not. Operations include monitoring the overall
security, governance, automation etc, which is known as CloudOps.
Page 6 of 46

b) Monitoring and operating private cloud in System Centre:
The primary function is to coach the new engineer to get the complete structure of the cloud
computing monitored in the Microsoft system center. The main protocol is to provide high-end
security, a wide network connection in the system center (CHEN, QI & QI, 2013). The
generation of reports that is synchronized with system center will help the new engineer to
produce report fast and smoothly. The other process which will help to grab the new technology
is the easiness of the workflow, end to end configuration, creating different reports and
generation. The system center will help to manage the updates and auto recovery of files and the
implementation of service level management system could be easily understood by the new
engineers (Saha & Hossain, 2015).
Page 7 of 46
The primary function is to coach the new engineer to get the complete structure of the cloud
computing monitored in the Microsoft system center. The main protocol is to provide high-end
security, a wide network connection in the system center (CHEN, QI & QI, 2013). The
generation of reports that is synchronized with system center will help the new engineer to
produce report fast and smoothly. The other process which will help to grab the new technology
is the easiness of the workflow, end to end configuration, creating different reports and
generation. The system center will help to manage the updates and auto recovery of files and the
implementation of service level management system could be easily understood by the new
engineers (Saha & Hossain, 2015).
Page 7 of 46
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3.0 Question 3:
a) Different health checks and performance monitors available in System Centre:
Two different health checks and performance monitors are available such as ‘Health Monitors
for PORT-0.1’ and ‘Health Monitors for IF-30’
Figure 1: Health Monitors for PORT-0.1
(Source: Docs.microsoft.com, 2019)
Page 8 of 46
a) Different health checks and performance monitors available in System Centre:
Two different health checks and performance monitors are available such as ‘Health Monitors
for PORT-0.1’ and ‘Health Monitors for IF-30’
Figure 1: Health Monitors for PORT-0.1
(Source: Docs.microsoft.com, 2019)
Page 8 of 46
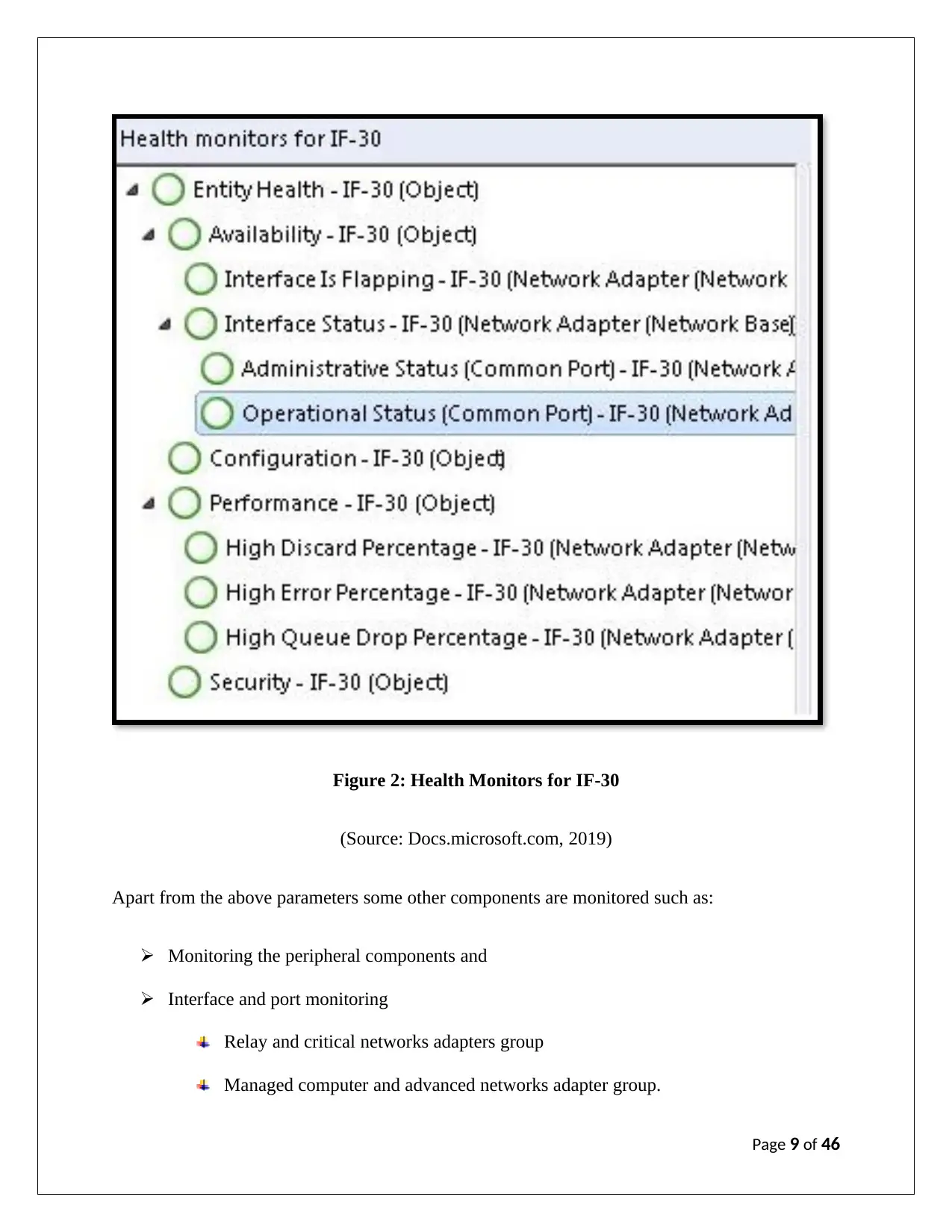
Figure 2: Health Monitors for IF-30
(Source: Docs.microsoft.com, 2019)
Apart from the above parameters some other components are monitored such as:
Monitoring the peripheral components and
Interface and port monitoring
Relay and critical networks adapters group
Managed computer and advanced networks adapter group.
Page 9 of 46
(Source: Docs.microsoft.com, 2019)
Apart from the above parameters some other components are monitored such as:
Monitoring the peripheral components and
Interface and port monitoring
Relay and critical networks adapters group
Managed computer and advanced networks adapter group.
Page 9 of 46

b) Verifying the health checks for following components:
I. Operations Manager:
The system centre operation manager gathers data from the sources such as:
Event logs
Data files
Registry
Windows management instrumentation (WMI)
PowerShell and SQL queries from the specified server
The below steps are performed to configure the assessment through Operation console is:
Figure 3: Health check of operation manager
(Source: Docs.microsoft.com, 2019).
II. Virtual Machine Manager (VMM):
In order to check the health of Hyper-V server in Virtual Machine manager, the following tasks
are to be performed:
Page 10 of 46
I. Operations Manager:
The system centre operation manager gathers data from the sources such as:
Event logs
Data files
Registry
Windows management instrumentation (WMI)
PowerShell and SQL queries from the specified server
The below steps are performed to configure the assessment through Operation console is:
Figure 3: Health check of operation manager
(Source: Docs.microsoft.com, 2019).
II. Virtual Machine Manager (VMM):
In order to check the health of Hyper-V server in Virtual Machine manager, the following tasks
are to be performed:
Page 10 of 46
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
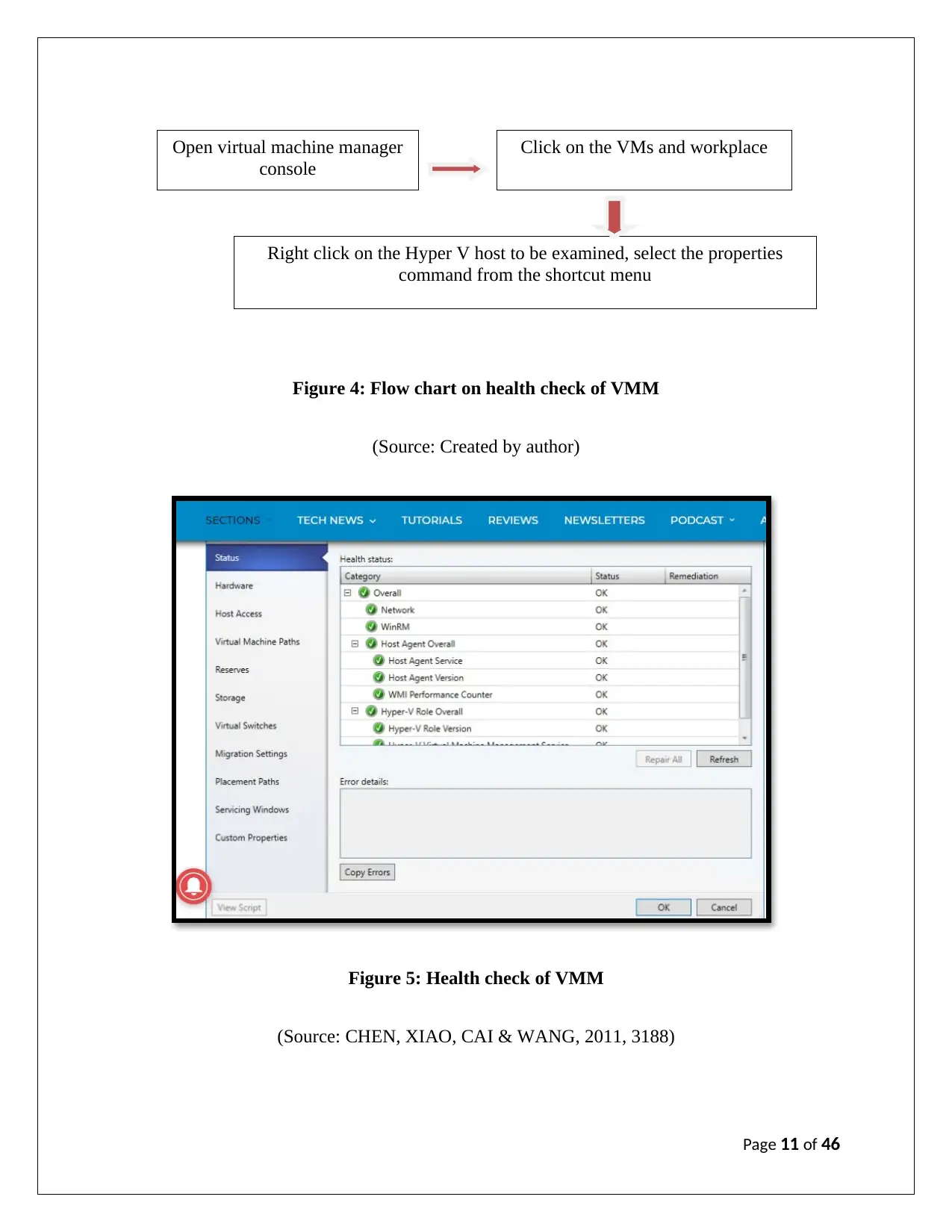
Open virtual machine manager
console
Click on the VMs and workplace
Right click on the Hyper V host to be examined, select the properties
command from the shortcut menu
Figure 4: Flow chart on health check of VMM
(Source: Created by author)
Figure 5: Health check of VMM
(Source: CHEN, XIAO, CAI & WANG, 2011, 3188)
Page 11 of 46
console
Click on the VMs and workplace
Right click on the Hyper V host to be examined, select the properties
command from the shortcut menu
Figure 4: Flow chart on health check of VMM
(Source: Created by author)
Figure 5: Health check of VMM
(Source: CHEN, XIAO, CAI & WANG, 2011, 3188)
Page 11 of 46
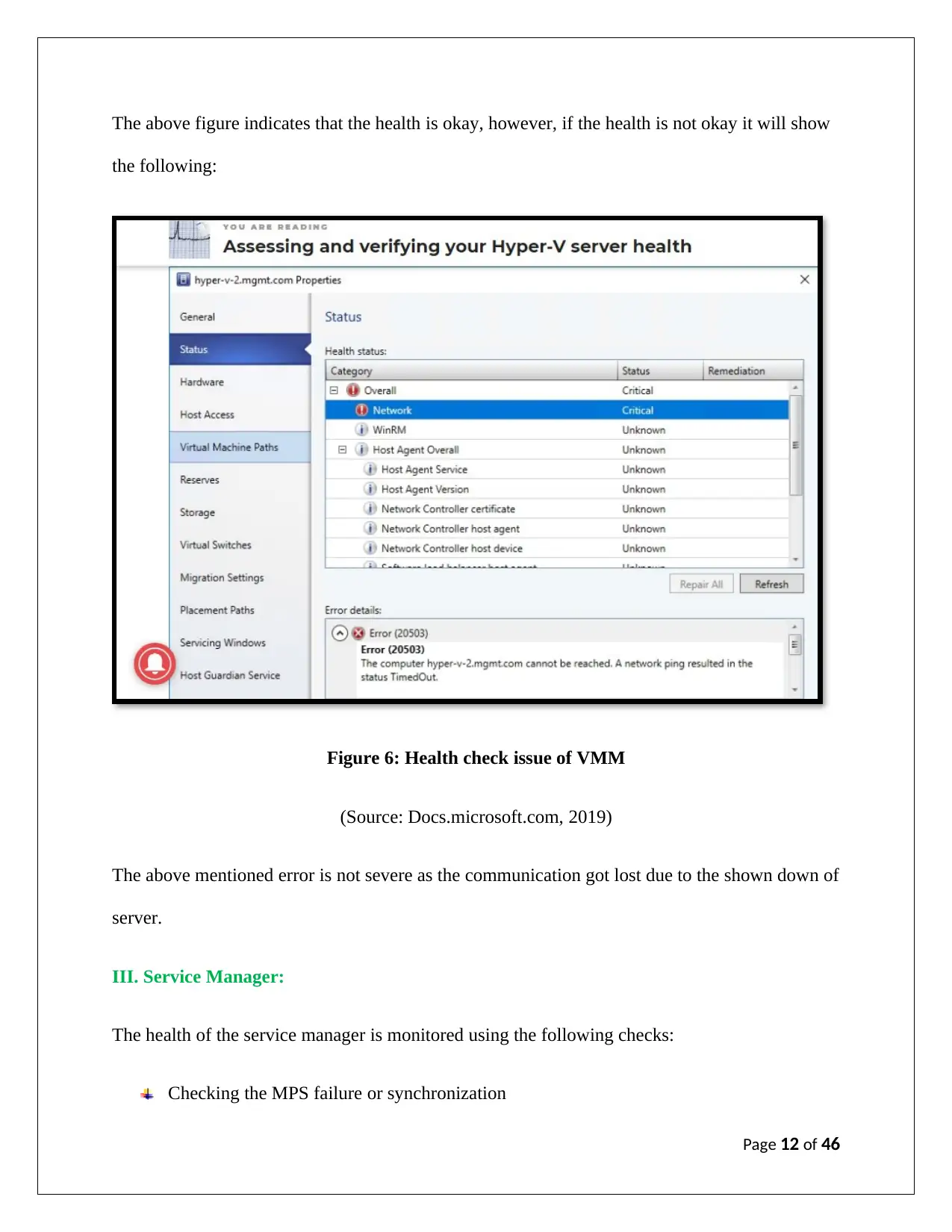
The above figure indicates that the health is okay, however, if the health is not okay it will show
the following:
Figure 6: Health check issue of VMM
(Source: Docs.microsoft.com, 2019)
The above mentioned error is not severe as the communication got lost due to the shown down of
server.
III. Service Manager:
The health of the service manager is monitored using the following checks:
Checking the MPS failure or synchronization
Page 12 of 46
the following:
Figure 6: Health check issue of VMM
(Source: Docs.microsoft.com, 2019)
The above mentioned error is not severe as the communication got lost due to the shown down of
server.
III. Service Manager:
The health of the service manager is monitored using the following checks:
Checking the MPS failure or synchronization
Page 12 of 46

Checking issues or workflows
Checking the SQL server to ensure Broker Service is enabled
Checking the grooming history to ensure CMDB clean-up
IV. Orchestrator:
‘Orchestrator Health Checker’ is installed and configured to verify the health status of
Orchestrator. After the installation, from the Audit menu, client those are connected to the run
book server along with existing issues can also be determined (GitHub.com, 2019).
V. Application Controller:
The operation basically expended over HTTP to indicate the UP or DOWN status of the
application. The return value of a health check is always a variable, but a nominal JSON
response, like {"status": "UP"}. The two-state defined process named readiness and liveness
covers the entire health check process of an application. A readiness probe indicates whether the
process is able to handle the requests, whereas, a liveness probe indicates which process needs to
be resumed (see exhibit 3, appendix).
VI. DPM Controller Health:
Data protection controller manager (DPM) health check retrieves all data about the DPM server.
It will display like the following:
DPM Information
DPM Disks (if exist)
DPM Libraries (if exist)
Page 13 of 46
Checking the SQL server to ensure Broker Service is enabled
Checking the grooming history to ensure CMDB clean-up
IV. Orchestrator:
‘Orchestrator Health Checker’ is installed and configured to verify the health status of
Orchestrator. After the installation, from the Audit menu, client those are connected to the run
book server along with existing issues can also be determined (GitHub.com, 2019).
V. Application Controller:
The operation basically expended over HTTP to indicate the UP or DOWN status of the
application. The return value of a health check is always a variable, but a nominal JSON
response, like {"status": "UP"}. The two-state defined process named readiness and liveness
covers the entire health check process of an application. A readiness probe indicates whether the
process is able to handle the requests, whereas, a liveness probe indicates which process needs to
be resumed (see exhibit 3, appendix).
VI. DPM Controller Health:
Data protection controller manager (DPM) health check retrieves all data about the DPM server.
It will display like the following:
DPM Information
DPM Disks (if exist)
DPM Libraries (if exist)
Page 13 of 46
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DPM Offsite ready tapes (if exist)
DPM Protection groups
DPM Last errors
After successful retrieval, the result is sent through email or HTML file. Scheduled repeat is
maintained to verify the DPM Controller Health (Gallery.technet.microsoft.com, 2019).
Page 14 of 46
DPM Protection groups
DPM Last errors
After successful retrieval, the result is sent through email or HTML file. Scheduled repeat is
maintained to verify the DPM Controller Health (Gallery.technet.microsoft.com, 2019).
Page 14 of 46

4.0 Question 4:
a1) Security issues of data stored in third-party data centres:
The physical orientation and control of the data centres in terms of the network
management and the storage space location.
Secured physical access to the storage area exclusively for the data center employees.
Network segmentation of the network management system and the data itself.
Disaster recovery policy of the data center service provider.
The frequency of upgrade patches to the security infrastructure.
The extent of multi-tenancy and security policies to the infrastructure.
a2) Category of controls to be implemented in cloud security architecture:
Deterrent controls: These controls are implemented as a warning to the cloud user for
possible adverse consequences.
Preventive control: These controls attempt to prevent any possible attack on the
system. For example strong identity management policies or steps to prevent DDoS
attack.
Detective controls: It detects anomalies and responds by initiating preventive or
corrective controls. Monitoring system and network security for intrusion detection
are some of the approaches (Hammer, Yazidi & Begnum, 2016).
Corrective controls: Such controls tend to restrict the effects of a security incident by
inhibiting the damage caused. For instance restoration of system backup as part of
disaster recovery (Kaur & Singh, 2015).
Page 15 of 46
a1) Security issues of data stored in third-party data centres:
The physical orientation and control of the data centres in terms of the network
management and the storage space location.
Secured physical access to the storage area exclusively for the data center employees.
Network segmentation of the network management system and the data itself.
Disaster recovery policy of the data center service provider.
The frequency of upgrade patches to the security infrastructure.
The extent of multi-tenancy and security policies to the infrastructure.
a2) Category of controls to be implemented in cloud security architecture:
Deterrent controls: These controls are implemented as a warning to the cloud user for
possible adverse consequences.
Preventive control: These controls attempt to prevent any possible attack on the
system. For example strong identity management policies or steps to prevent DDoS
attack.
Detective controls: It detects anomalies and responds by initiating preventive or
corrective controls. Monitoring system and network security for intrusion detection
are some of the approaches (Hammer, Yazidi & Begnum, 2016).
Corrective controls: Such controls tend to restrict the effects of a security incident by
inhibiting the damage caused. For instance restoration of system backup as part of
disaster recovery (Kaur & Singh, 2015).
Page 15 of 46

a3) Requirements to limit data security:
Be conscious of the shared responsibilities of data security.
Must follow access and identity management best practices.
Granting limited access to application users.
Encryption of data at the physical level.
Authentication of software changes.
Involvement of the information security team throughout the application development
lifecycle.
Streamlining of acquiring permission to access data and application.
Logging of user and application activities for analysis.
Monitoring network activity to detect abnormalities (Salapura& Harper, 2018)
b) Assessment of selection criteria for cloud for an organization:
Private cloud infrastructure is dedicated to a single organization and can be managed internally
or by third-party depending on the hosting conditions. It is obvious that this kind of arrangement
decreases certain concerns of data privacy and security that arises out of the multi-tenancy in the
public cloud. Being dedicated to a single organization the extent of user access to the system is
limited which reduces the possibility of an attack on Private cloud (Shah, 2012). However it still
involves significant cost overhead to upgrade the architecture frequently thus, the private cloud
can only be opted to large enterprises with complex applications. Public cloud on the other hand,
has a flexible cost structure to suit a variety of organization sizes. It also has different security
considerations over the type of services opted for. However, the available cloud service
providers have dedicated teams to employ and monitor security policies throughout the
Page 16 of 46
Be conscious of the shared responsibilities of data security.
Must follow access and identity management best practices.
Granting limited access to application users.
Encryption of data at the physical level.
Authentication of software changes.
Involvement of the information security team throughout the application development
lifecycle.
Streamlining of acquiring permission to access data and application.
Logging of user and application activities for analysis.
Monitoring network activity to detect abnormalities (Salapura& Harper, 2018)
b) Assessment of selection criteria for cloud for an organization:
Private cloud infrastructure is dedicated to a single organization and can be managed internally
or by third-party depending on the hosting conditions. It is obvious that this kind of arrangement
decreases certain concerns of data privacy and security that arises out of the multi-tenancy in the
public cloud. Being dedicated to a single organization the extent of user access to the system is
limited which reduces the possibility of an attack on Private cloud (Shah, 2012). However it still
involves significant cost overhead to upgrade the architecture frequently thus, the private cloud
can only be opted to large enterprises with complex applications. Public cloud on the other hand,
has a flexible cost structure to suit a variety of organization sizes. It also has different security
considerations over the type of services opted for. However, the available cloud service
providers have dedicated teams to employ and monitor security policies throughout the
Page 16 of 46
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

infrastructure which tackles much of the overhead of businesses acquiring the cloud service
(Shyam & Manvi, 2015).
Page 17 of 46
(Shyam & Manvi, 2015).
Page 17 of 46

5.0 Question 5:
a) Strategies of System Centre Virtual Machine Manager (SCVMM):
In the Private Cloud system, all the organisation’s business resources have to be retained in an
infrastructure designed to support the IT infrastructure. The administrators have to deal with a
large number of virtual machines which may lead to virtual machine sprawl. So, the primary
strategy of SCVMM is to optimize the creation, deployment and management of virtual
machines.
With the virtualisation of machines, the network components of the cloud infrastructure have to
be controlled. Thus, the second strategy must be to manage the network devices like the
switches, routers and hubs that create LAN, VLAN and WAN, switch extension managers, MAC
address pools, ports etc.
The next strategy for SCVMM is to control data storage. The Storage Area Network is used in
private cloud which is used to connect the network storage to individual workstations and
assigned as local disks.
The final strategy should be to enable a group of computers to work as clusters in the overall
cloud infrastructure which provides high availability and scalability to the users (Rahma, Adji &
Widyawan, 2013).
b. Key features of Virtual Machine Manager:
The main role of a Virtual Machine Manager is to deploy virtual host machines used as servers
to manage the resources and information over a Private cloud infrastructure. Apart from
Page 18 of 46
a) Strategies of System Centre Virtual Machine Manager (SCVMM):
In the Private Cloud system, all the organisation’s business resources have to be retained in an
infrastructure designed to support the IT infrastructure. The administrators have to deal with a
large number of virtual machines which may lead to virtual machine sprawl. So, the primary
strategy of SCVMM is to optimize the creation, deployment and management of virtual
machines.
With the virtualisation of machines, the network components of the cloud infrastructure have to
be controlled. Thus, the second strategy must be to manage the network devices like the
switches, routers and hubs that create LAN, VLAN and WAN, switch extension managers, MAC
address pools, ports etc.
The next strategy for SCVMM is to control data storage. The Storage Area Network is used in
private cloud which is used to connect the network storage to individual workstations and
assigned as local disks.
The final strategy should be to enable a group of computers to work as clusters in the overall
cloud infrastructure which provides high availability and scalability to the users (Rahma, Adji &
Widyawan, 2013).
b. Key features of Virtual Machine Manager:
The main role of a Virtual Machine Manager is to deploy virtual host machines used as servers
to manage the resources and information over a Private cloud infrastructure. Apart from
Page 18 of 46

managing virtual hosts, it also enables the administrators to configure and manage pools of
infrastructure resources including the network, servers, storage and clusters. These resources
together are called as the fabric of Private cloud. The VMM combines the cloud infrastructure
and resources at a single place and allows the management with following key features:
Fabric management: VMM enables the individual components of a Private cloud fabric
to be managed via a single gateway as it is crucial to for the optimisation of the entire
cloud (Khanna& Rakesh, 2015). Resource management: Libraries of templates and profiles are a key feature of VMM that
allows the creation of virtual machines and scripts. It can dynamically balance the load
between servers to optimise the performance. It can also optimise power output resources
into the data centre’s environment (Kaushik, 2016). Cloud Management: This feature enables administrators to manage the holistic cloud
infrastructure including setting permission for users, altering quota parameters in private
cloud and enforce policies (Khaleel, 2018).
Page 19 of 46
infrastructure resources including the network, servers, storage and clusters. These resources
together are called as the fabric of Private cloud. The VMM combines the cloud infrastructure
and resources at a single place and allows the management with following key features:
Fabric management: VMM enables the individual components of a Private cloud fabric
to be managed via a single gateway as it is crucial to for the optimisation of the entire
cloud (Khanna& Rakesh, 2015). Resource management: Libraries of templates and profiles are a key feature of VMM that
allows the creation of virtual machines and scripts. It can dynamically balance the load
between servers to optimise the performance. It can also optimise power output resources
into the data centre’s environment (Kaushik, 2016). Cloud Management: This feature enables administrators to manage the holistic cloud
infrastructure including setting permission for users, altering quota parameters in private
cloud and enforce policies (Khaleel, 2018).
Page 19 of 46
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

6.0 Question 6:
i. Virtual Machine properties and available hardware options:
Managing VMM library: The library is a pool of file share acting as an inventory used to
deploy virtual machines and services.
Managing VMM host groups: The host groups are a logical entity that combines the
resources of the cloud fabric together. Once created, resources can be assigned and
configured to the groups.
Fabric > Servers > All Hosts > Create Host Group.
Managing infrastructure and update servers: VMM can be used to manage all the
infrastructure servers to support the cloud at the same place including library servers,
PXE servers, DNS, DHCP, Active Directory, IPAM servers etc.
Fabric > Servers > Infrastructure > Add Resources > Infrastructure Server / Update
Server.
Managing networking hardware: Following steps are taken to set up the networking
resources:-
Setup a logical network like IP subnets, VLNS, subnet/VLAN pairs
Creating VM networks
Setting up IP address pools
Adding a network virtualisation gateway
Creating port profiles
Configuring logical switches
Page 20 of 46
i. Virtual Machine properties and available hardware options:
Managing VMM library: The library is a pool of file share acting as an inventory used to
deploy virtual machines and services.
Managing VMM host groups: The host groups are a logical entity that combines the
resources of the cloud fabric together. Once created, resources can be assigned and
configured to the groups.
Fabric > Servers > All Hosts > Create Host Group.
Managing infrastructure and update servers: VMM can be used to manage all the
infrastructure servers to support the cloud at the same place including library servers,
PXE servers, DNS, DHCP, Active Directory, IPAM servers etc.
Fabric > Servers > Infrastructure > Add Resources > Infrastructure Server / Update
Server.
Managing networking hardware: Following steps are taken to set up the networking
resources:-
Setup a logical network like IP subnets, VLNS, subnet/VLAN pairs
Creating VM networks
Setting up IP address pools
Adding a network virtualisation gateway
Creating port profiles
Configuring logical switches
Page 20 of 46

Managing storage: Storages are other hardware options that are assigned to the virtual
host and clusters and can be managed under this property. It includes local, remote, block
and file-based storage.
Managing Scale-out file servers (SOFC): The SOFC file server can be managed via this
property that provides continuous availability and transparent failovers during a
downtime of nodes.
Managing virtual machines (VMs): This property allows the VMM to provision VMs in
the cloud fabric using cloning from an existing VM or creating from a template or virtual
hard disk.
Managing roles and accounts: This property can be used to manage roles and permission
defining allowable operations for the user profiles. Accounts act as containers for stored
user profiles.
ii. General settings of VMM that can be configured:
Adding a virtual adapter to a VM: It can be added by modifying a VMM hardware
profile.
Managing static memory on running VM: It helps in curbing the workload downtime.
Adding servicing window to a VM: Helps to maintain it outside the VMM console.
Creating production checkpoint for VM: It allows creating an image of the VM at an
instant of time which is used for system backups.
Configuring availability option for clustered VM: It ensures high availability and
resilience for VMs in a cluster.
Configuring resource throttling: The processor and memory throttling setting of VMM
optimise resource allocation and enhances the VM efficiency.
Page 21 of 46
host and clusters and can be managed under this property. It includes local, remote, block
and file-based storage.
Managing Scale-out file servers (SOFC): The SOFC file server can be managed via this
property that provides continuous availability and transparent failovers during a
downtime of nodes.
Managing virtual machines (VMs): This property allows the VMM to provision VMs in
the cloud fabric using cloning from an existing VM or creating from a template or virtual
hard disk.
Managing roles and accounts: This property can be used to manage roles and permission
defining allowable operations for the user profiles. Accounts act as containers for stored
user profiles.
ii. General settings of VMM that can be configured:
Adding a virtual adapter to a VM: It can be added by modifying a VMM hardware
profile.
Managing static memory on running VM: It helps in curbing the workload downtime.
Adding servicing window to a VM: Helps to maintain it outside the VMM console.
Creating production checkpoint for VM: It allows creating an image of the VM at an
instant of time which is used for system backups.
Configuring availability option for clustered VM: It ensures high availability and
resilience for VMs in a cluster.
Configuring resource throttling: The processor and memory throttling setting of VMM
optimise resource allocation and enhances the VM efficiency.
Page 21 of 46

Configuring virtual Non-Uniform Memory Access: These settings are used to close the
gap between processor speed and the memory access time in the cloud multiprocessor
environment.
Page 22 of 46
gap between processor speed and the memory access time in the cloud multiprocessor
environment.
Page 22 of 46
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

7.0 Question 7:
a) Steps to create private cloud from VMware resource pool:
Prerequisites (see exhibit 1, appendix):
The installation wizard is to be used so that the private cloud environment can be created.
The prerequisites are mentioned in appendix.
Procedure (mentioned step-by-step):
Configure the environment settings such as name, data center and password for a new
Private Cloud
Select the vRealize Suite Products to install in the private cloud environment
Configure Licensing and Accept the VMware License Agreement followed by entering
the license key (Suresh & Sakthivel, 2015).
Configure the whole infrastructure in detail at the time of creating an environment
Configure the Private Cloud Environment Details through the right configuration of
cluster, vCenter server, network, certificates and datastore
Configure vRealize Suite Products for its Installation in the private cloud
Finally verify and confirm the cloud environment setting to ensure accurate installation.
b) Increasing the capacity of private cloud:
Orchestration tool such as VMTurbo, VMWare, BMC, etc. can help in capacity planning. Sousa,
Moreira, Costa Filho & Machado (2018) also stated that a permutation of ITIL-aligned process
and automated tools can become useful in reducing the cost and improving the overall resource
Page 23 of 46
a) Steps to create private cloud from VMware resource pool:
Prerequisites (see exhibit 1, appendix):
The installation wizard is to be used so that the private cloud environment can be created.
The prerequisites are mentioned in appendix.
Procedure (mentioned step-by-step):
Configure the environment settings such as name, data center and password for a new
Private Cloud
Select the vRealize Suite Products to install in the private cloud environment
Configure Licensing and Accept the VMware License Agreement followed by entering
the license key (Suresh & Sakthivel, 2015).
Configure the whole infrastructure in detail at the time of creating an environment
Configure the Private Cloud Environment Details through the right configuration of
cluster, vCenter server, network, certificates and datastore
Configure vRealize Suite Products for its Installation in the private cloud
Finally verify and confirm the cloud environment setting to ensure accurate installation.
b) Increasing the capacity of private cloud:
Orchestration tool such as VMTurbo, VMWare, BMC, etc. can help in capacity planning. Sousa,
Moreira, Costa Filho & Machado (2018) also stated that a permutation of ITIL-aligned process
and automated tools can become useful in reducing the cost and improving the overall resource
Page 23 of 46

availability. In addition, having an exception can be considered as a significant element in the
capacity planning of private cloud. The steward also needs to put the process of freeing capacity
to redeploy the freed up capacity.
Page 24 of 46
capacity planning of private cloud. The steward also needs to put the process of freeing capacity
to redeploy the freed up capacity.
Page 24 of 46

8.0 Question 8:
Different aspects of multi-tenancy and typical expectations of clients of a multitenant
cloud:
As the chosen bank moves the infrastructure into a private cloud environment, the entire
accountability of constructing a multi-tenant architecture respite with the IT managers.
According to Das, Iyengar & Mueller (2018), the bank requires this multi tenancy aspect as the
cloud uses multi tenancy to share the essential software, services and IT resources in a most cost-
effective way. The process also offers high security to the entire cloud infrastructure of the bank
(Lakshmi & Begum, 2011). From the perspective of IT managers, the bank could adore the two
aspects of multi tenancy and those are as follows:
Internal: The chosen bank can treat its different departments as different and individual tenants.
It requires logical inaccessibility of the applications and structure while sharing the physical
infrastructure (Thomas, 2008).
External: This can be treated from the service provider’s end where each tenant means different
client company. Being a financial enterprise, the chosen bank needs a realistic infrastructure like
physical isolation to maintain the set of data.
The typical expectations of the clients in a multitenant cloud environment can be as follows:
Proper experience of using the dedicated cloud environment
Confident, secure and remote infrastructure
Conforms with the given protocols, principles and regulations
Cost-effective approach
Page 25 of 46
Different aspects of multi-tenancy and typical expectations of clients of a multitenant
cloud:
As the chosen bank moves the infrastructure into a private cloud environment, the entire
accountability of constructing a multi-tenant architecture respite with the IT managers.
According to Das, Iyengar & Mueller (2018), the bank requires this multi tenancy aspect as the
cloud uses multi tenancy to share the essential software, services and IT resources in a most cost-
effective way. The process also offers high security to the entire cloud infrastructure of the bank
(Lakshmi & Begum, 2011). From the perspective of IT managers, the bank could adore the two
aspects of multi tenancy and those are as follows:
Internal: The chosen bank can treat its different departments as different and individual tenants.
It requires logical inaccessibility of the applications and structure while sharing the physical
infrastructure (Thomas, 2008).
External: This can be treated from the service provider’s end where each tenant means different
client company. Being a financial enterprise, the chosen bank needs a realistic infrastructure like
physical isolation to maintain the set of data.
The typical expectations of the clients in a multitenant cloud environment can be as follows:
Proper experience of using the dedicated cloud environment
Confident, secure and remote infrastructure
Conforms with the given protocols, principles and regulations
Cost-effective approach
Page 25 of 46
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Accessible and adaptable
Figure 7: The multitenant Cloud design for the bank
(Source: Suresh & Sakthivel, 2015, 385)
Page 26 of 46
Figure 7: The multitenant Cloud design for the bank
(Source: Suresh & Sakthivel, 2015, 385)
Page 26 of 46

9.0 Question 9:
a) Elaborating the concept of service in a VMM and step involved in the creation of a
Service template:
i) Based on existing virtual hard disk or virtual machine template:
Virtual Machine Manager is a set of service refers to collecting virtual machines that are
installed together as a distinct object (LI, WO, HU, LI, WANG & HUAI, 2013). The steps are
mentioned in exhibit 4, appendix
ii) Using an existing virtual machine that is deployed on a host:
Please see exhibit 5, appendix
b) Analysing different properties of a service template that requires to be configured for a
multi-tier business:
Service Template contains one or more computer Tiers, which includes a single VM template.
However, Liu, Yang, Qu & Liu (2016) asserted that a VM template comprises with Hardware
Profile, Guest OS Profile and VHD presented in the library. A VM template also hasone or more
application deployments named MsDeploy, SQL DAC or Server App-V packages (Mukta,
2016).
Method to configure service template for a multi-tier business:
Step 1: Enable
Step 2: Configure terminal
Page 27 of 46
a) Elaborating the concept of service in a VMM and step involved in the creation of a
Service template:
i) Based on existing virtual hard disk or virtual machine template:
Virtual Machine Manager is a set of service refers to collecting virtual machines that are
installed together as a distinct object (LI, WO, HU, LI, WANG & HUAI, 2013). The steps are
mentioned in exhibit 4, appendix
ii) Using an existing virtual machine that is deployed on a host:
Please see exhibit 5, appendix
b) Analysing different properties of a service template that requires to be configured for a
multi-tier business:
Service Template contains one or more computer Tiers, which includes a single VM template.
However, Liu, Yang, Qu & Liu (2016) asserted that a VM template comprises with Hardware
Profile, Guest OS Profile and VHD presented in the library. A VM template also hasone or more
application deployments named MsDeploy, SQL DAC or Server App-V packages (Mukta,
2016).
Method to configure service template for a multi-tier business:
Step 1: Enable
Step 2: Configure terminal
Page 27 of 46

Step 3: Create service-template (template-name)
Step 4: Give absolute-timer minutes
Step 5: Access-group then access-list-name
Step 6: Provide description
Step 7: Redirect URL
Step 8: Create tag-name and vlan-id
Step 9: End
Step 10: Show service-template [template-name]
Page 28 of 46
Step 4: Give absolute-timer minutes
Step 5: Access-group then access-list-name
Step 6: Provide description
Step 7: Redirect URL
Step 8: Create tag-name and vlan-id
Step 9: End
Step 10: Show service-template [template-name]
Page 28 of 46
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10.0 Question 10:
i) Elaborating VMM profile and analysing the steps for Application profile using Telnet:
Telnet is a bidirectional interactive text-oriented communication protocol to offer
communication over the Internet that using a virtual terminal connection (Suresh & Sakthivel,
2015).
Step 1: Install Telnet
Step 2: Open command prompt
For Windows:
First select Start >Select Run or Search
Enter: cmd.exe
For OS X:
Select Utilities > Terminal
For Linux:
Open Terminal
Step 3: Enter the command: telnet <address><port> (see appendix)
Page 29 of 46
i) Elaborating VMM profile and analysing the steps for Application profile using Telnet:
Telnet is a bidirectional interactive text-oriented communication protocol to offer
communication over the Internet that using a virtual terminal connection (Suresh & Sakthivel,
2015).
Step 1: Install Telnet
Step 2: Open command prompt
For Windows:
First select Start >Select Run or Search
Enter: cmd.exe
For OS X:
Select Utilities > Terminal
For Linux:
Open Terminal
Step 3: Enter the command: telnet <address><port> (see appendix)
Page 29 of 46
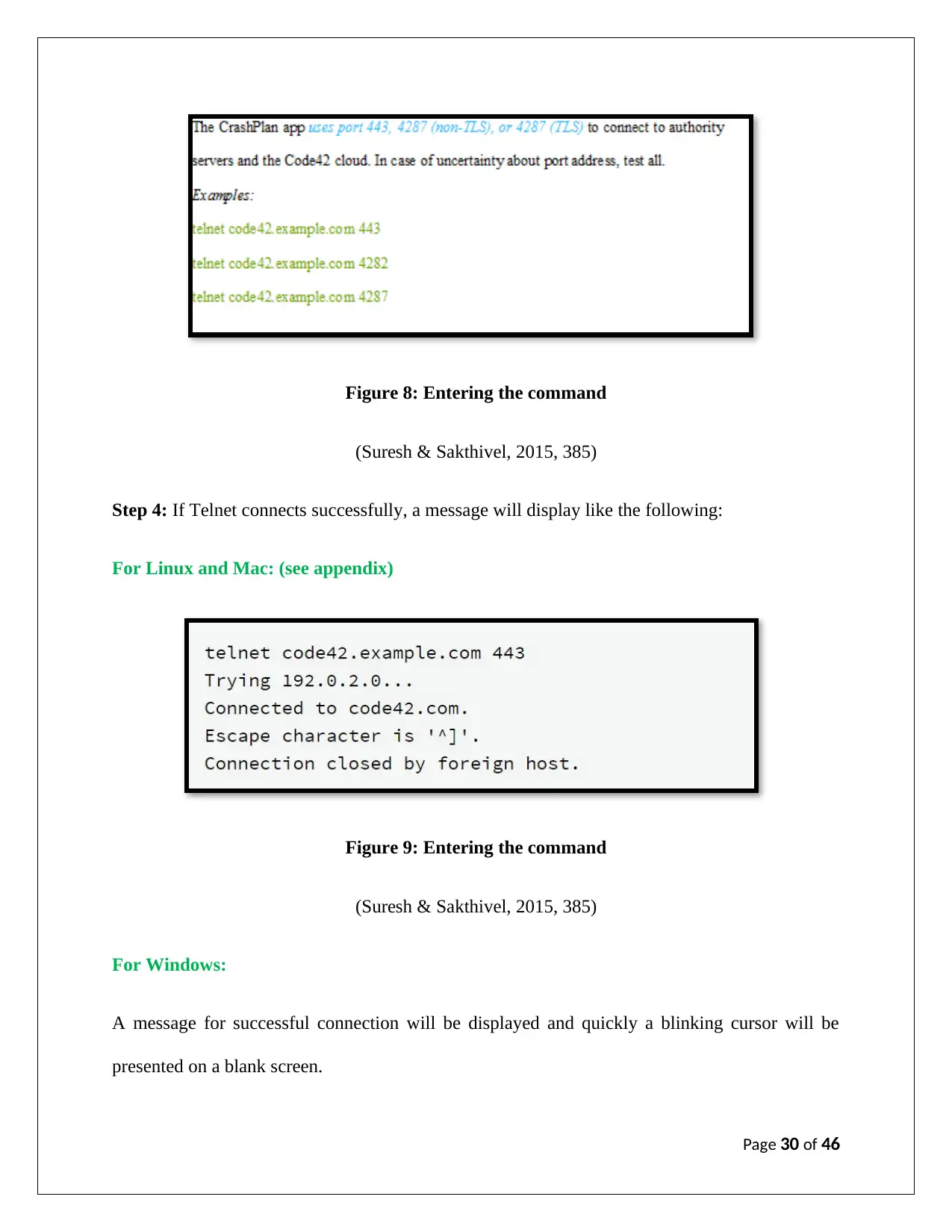
Figure 8: Entering the command
(Suresh & Sakthivel, 2015, 385)
Step 4: If Telnet connects successfully, a message will display like the following:
For Linux and Mac: (see appendix)
Figure 9: Entering the command
(Suresh & Sakthivel, 2015, 385)
For Windows:
A message for successful connection will be displayed and quickly a blinking cursor will be
presented on a blank screen.
Page 30 of 46
(Suresh & Sakthivel, 2015, 385)
Step 4: If Telnet connects successfully, a message will display like the following:
For Linux and Mac: (see appendix)
Figure 9: Entering the command
(Suresh & Sakthivel, 2015, 385)
For Windows:
A message for successful connection will be displayed and quickly a blinking cursor will be
presented on a blank screen.
Page 30 of 46

ii) Configuration of SQL server profile using Telnet:
Step 1: Install Telnet client by opening Control Panel from the Start menu on Windows (see
appendix)
Step 2: Select program and features in the control panel (see appendix)
Step 3: Select Turn Windows features on or off (see appendix)
Step 4: Selectthe option Telnet Client (check this option)then press OK (see appendix)
Step 5:Enter telnet %host% %port% in the command prompt (%host% and %port% are the host
and port of SQL Server) (see appendix)
Step 6: Press Enter (it must call the SQL Server if the telnet could communicate with the
specified host and port). Then a blank dialog box will be opened to indicate that SQL Server is
connected.(see appendix)
Step 7: If it fails to make connection with SQL Server, there will be a failure message or
otherwise Configuration of SQL server profile will be successful (see appendix)
Page 31 of 46
Step 1: Install Telnet client by opening Control Panel from the Start menu on Windows (see
appendix)
Step 2: Select program and features in the control panel (see appendix)
Step 3: Select Turn Windows features on or off (see appendix)
Step 4: Selectthe option Telnet Client (check this option)then press OK (see appendix)
Step 5:Enter telnet %host% %port% in the command prompt (%host% and %port% are the host
and port of SQL Server) (see appendix)
Step 6: Press Enter (it must call the SQL Server if the telnet could communicate with the
specified host and port). Then a blank dialog box will be opened to indicate that SQL Server is
connected.(see appendix)
Step 7: If it fails to make connection with SQL Server, there will be a failure message or
otherwise Configuration of SQL server profile will be successful (see appendix)
Page 31 of 46
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
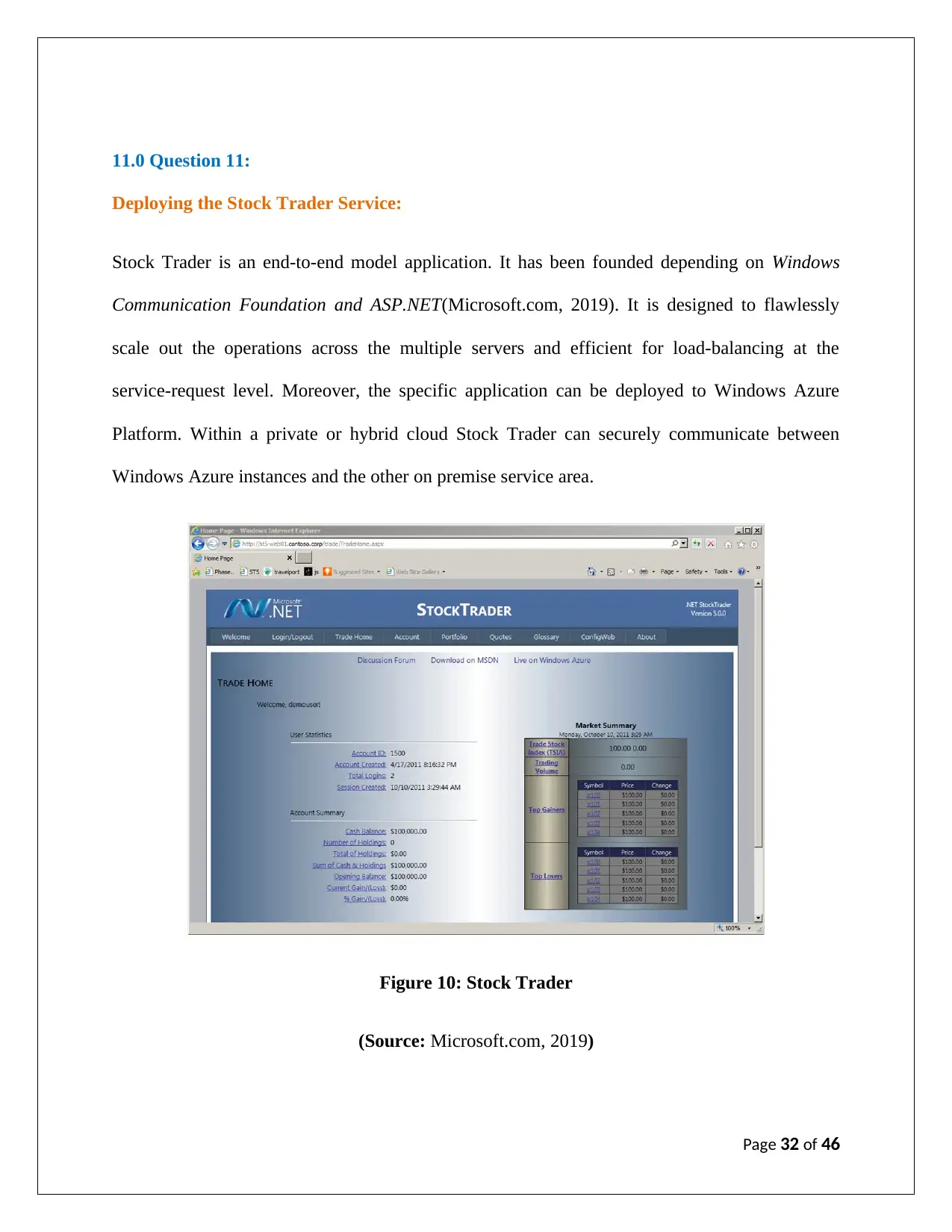
11.0 Question 11:
Deploying the Stock Trader Service:
Stock Trader is an end-to-end model application. It has been founded depending on Windows
Communication Foundation and ASP.NET(Microsoft.com, 2019). It is designed to flawlessly
scale out the operations across the multiple servers and efficient for load-balancing at the
service-request level. Moreover, the specific application can be deployed to Windows Azure
Platform. Within a private or hybrid cloud Stock Trader can securely communicate between
Windows Azure instances and the other on premise service area.
Figure 10: Stock Trader
(Source: Microsoft.com, 2019)
Page 32 of 46
Deploying the Stock Trader Service:
Stock Trader is an end-to-end model application. It has been founded depending on Windows
Communication Foundation and ASP.NET(Microsoft.com, 2019). It is designed to flawlessly
scale out the operations across the multiple servers and efficient for load-balancing at the
service-request level. Moreover, the specific application can be deployed to Windows Azure
Platform. Within a private or hybrid cloud Stock Trader can securely communicate between
Windows Azure instances and the other on premise service area.
Figure 10: Stock Trader
(Source: Microsoft.com, 2019)
Page 32 of 46

The Stock Trader application package can be downloaded easily from internet
(connect.microsoft.com, 2019) and contains application code, scripts, sysprepedvhd images, app-
v packages, and a service template for demonstrating the multi-tier application architecture and
its operations. An inclusive private cloud solution also includes its functional dependencies, level
of intelligence and VM templates which are useful for deploying Stock Trader. In order to
deploy Stock Trader as a service to a target private cloud the following hardware and software
specification are required.
Hardware requirement:
Figure 11: Hardware requirement
(Source: connect.microsoft.com, 2019)
Page 33 of 46
(connect.microsoft.com, 2019) and contains application code, scripts, sysprepedvhd images, app-
v packages, and a service template for demonstrating the multi-tier application architecture and
its operations. An inclusive private cloud solution also includes its functional dependencies, level
of intelligence and VM templates which are useful for deploying Stock Trader. In order to
deploy Stock Trader as a service to a target private cloud the following hardware and software
specification are required.
Hardware requirement:
Figure 11: Hardware requirement
(Source: connect.microsoft.com, 2019)
Page 33 of 46

Software requirements:
Figure 12: Software requirement
(Source: connect.microsoft.com, 2019)
Furthermore, the cloud implication is applicable to mostly a service provider to indicate the
capability to deploy, display, and manage an application with the 5-3-2 principle of cloud
computing.
Page 34 of 46
Figure 12: Software requirement
(Source: connect.microsoft.com, 2019)
Furthermore, the cloud implication is applicable to mostly a service provider to indicate the
capability to deploy, display, and manage an application with the 5-3-2 principle of cloud
computing.
Page 34 of 46
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References:
B.Abdulla, D., & B. Alzobeer, B. (2014). Analysis of Private Cloud Construction using
Microsoft Cloud Solution. International Journal Of Computer Applications, 99(1), 22-29.
doi: 10.5120/17338-7328
Barona López, L., García Villalba, L., Valdivieso Caraguay, Á., & López, D. (2015). Trends on
virtualisation with software defined networking and network function virtualisation. IET
Networks, 4(5), 255-263. doi: 10.1049/iet-net.2014.0117
Bhagat, A., & Kant Sahu, R. (2013). Cloud Data Security While using Third Party
Auditor. International Journal Of Computer Applications, 70(16), 9-13. doi:
10.5120/12149-7798
Blogs.technet.microsoft.com. (2019). What Gets Monitored with System Center Operations
Manager 2012 Network Monitoring. Retrieved from
https://blogs.technet.microsoft.com/momteam/2011/09/20/what-gets-monitored-with-
system-center-operations-manager-2012-network-monitoring/
CHEN, B., XIAO, N., CAI, Z., & WANG, Z. (2011). Prefetch Mechanism for On-Demand
Software Deployment in Virtual Machine Environments. Journal Of Software, 21(12),
3186-3198. doi: 10.3724/sp.j.1001.2010.03715
CHEN, L., QI, W., & QI, Y. (2013). Atmospheric monitoring network system based on cloud
computing. Journal Of Computer Applications, 32(5), 1415-1417. doi:
10.3724/sp.j.1087.2012.01415
Page 35 of 46
B.Abdulla, D., & B. Alzobeer, B. (2014). Analysis of Private Cloud Construction using
Microsoft Cloud Solution. International Journal Of Computer Applications, 99(1), 22-29.
doi: 10.5120/17338-7328
Barona López, L., García Villalba, L., Valdivieso Caraguay, Á., & López, D. (2015). Trends on
virtualisation with software defined networking and network function virtualisation. IET
Networks, 4(5), 255-263. doi: 10.1049/iet-net.2014.0117
Bhagat, A., & Kant Sahu, R. (2013). Cloud Data Security While using Third Party
Auditor. International Journal Of Computer Applications, 70(16), 9-13. doi:
10.5120/12149-7798
Blogs.technet.microsoft.com. (2019). What Gets Monitored with System Center Operations
Manager 2012 Network Monitoring. Retrieved from
https://blogs.technet.microsoft.com/momteam/2011/09/20/what-gets-monitored-with-
system-center-operations-manager-2012-network-monitoring/
CHEN, B., XIAO, N., CAI, Z., & WANG, Z. (2011). Prefetch Mechanism for On-Demand
Software Deployment in Virtual Machine Environments. Journal Of Software, 21(12),
3186-3198. doi: 10.3724/sp.j.1001.2010.03715
CHEN, L., QI, W., & QI, Y. (2013). Atmospheric monitoring network system based on cloud
computing. Journal Of Computer Applications, 32(5), 1415-1417. doi:
10.3724/sp.j.1087.2012.01415
Page 35 of 46

Chu, C., Ouyang, Y., & Jang, C. (2012). Secure data transmission with cloud computing in
heterogeneous wireless networks. Security And Communication Networks, 5(12), 1325-
1336. doi: 10.1002/sec.409
Das, A., Iyengar, A., & Mueller, F. (2018). KeyValueServe†: Design and performance analysis
of a multi-tenant data grid as a cloud service. Concurrency And Computation: Practice
And Experience, 30(14), e4424. doi: 10.1002/cpe.4424
Docs.microsoft.com. (2019). Install VMM. Retrieved from
https://docs.microsoft.com/en-us/system-center/vmm/install?view=sc-vmm-1807
Docs.microsoft.com. (2019). Optimize your System Center Operations Manager environment
with Azure Log Analytics. Retrieved from https://docs.microsoft.com/en-us/azure/azure-
monitor/insights/scom-assessment
Gallery.technet.microsoft.com. (2019). Script DPM Health Check. Retrieved from
https://gallery.technet.microsoft.com/scriptcenter/DPM-Health-Check-9628e68f
Gaur, R., & Kumari, U. (2017). Hybrid Intrusion Detection System for Private Cloud & Public
Cloud. Oriental Journal Of Computer Science And Technology, 10(2), 438-445. doi:
10.13005/ojcst/10.02.26
GitHub.com. (2019). sqdge/scorch. Retrieved from
https://github.com/sqdge/scorch/wiki/Orchestrator-Health-Checker
Hammer, H., Yazidi, A., & Begnum, K. (2016). An Inhomogeneous Hidden Markov Model for
Efficient Virtual Machine Placement in Cloud Computing Environments. Journal Of
Forecasting, 3(11), 132-156. doi: 10.1002/for.2441
Page 36 of 46
heterogeneous wireless networks. Security And Communication Networks, 5(12), 1325-
1336. doi: 10.1002/sec.409
Das, A., Iyengar, A., & Mueller, F. (2018). KeyValueServe†: Design and performance analysis
of a multi-tenant data grid as a cloud service. Concurrency And Computation: Practice
And Experience, 30(14), e4424. doi: 10.1002/cpe.4424
Docs.microsoft.com. (2019). Install VMM. Retrieved from
https://docs.microsoft.com/en-us/system-center/vmm/install?view=sc-vmm-1807
Docs.microsoft.com. (2019). Optimize your System Center Operations Manager environment
with Azure Log Analytics. Retrieved from https://docs.microsoft.com/en-us/azure/azure-
monitor/insights/scom-assessment
Gallery.technet.microsoft.com. (2019). Script DPM Health Check. Retrieved from
https://gallery.technet.microsoft.com/scriptcenter/DPM-Health-Check-9628e68f
Gaur, R., & Kumari, U. (2017). Hybrid Intrusion Detection System for Private Cloud & Public
Cloud. Oriental Journal Of Computer Science And Technology, 10(2), 438-445. doi:
10.13005/ojcst/10.02.26
GitHub.com. (2019). sqdge/scorch. Retrieved from
https://github.com/sqdge/scorch/wiki/Orchestrator-Health-Checker
Hammer, H., Yazidi, A., & Begnum, K. (2016). An Inhomogeneous Hidden Markov Model for
Efficient Virtual Machine Placement in Cloud Computing Environments. Journal Of
Forecasting, 3(11), 132-156. doi: 10.1002/for.2441
Page 36 of 46

Kaur, P., & Singh, J. (2015). Comprehensive Study of Cloud Resource Monitoring. International
Journal Of Private Cloud Computing Environment And Management, 2(1), 27-34. doi:
10.21742/ijpccem.2015.2.1.04
Kaushik, A. (2016). Analysis Of Cloud Based Multitenant Load Scaling. International Journal
Of Engineering And Computer Science, 4(15), 144-167. doi: 10.18535/ijecs/v5i11.85
Khaleel, M. (2018). Innovative Cloud-based Snooping Detection model in both Public and
Private Infrastructure. Journal Of Zankoy Sulaimani - Part A, 20(2), 43-52. doi:
10.17656/jzs.10723
Khanna, S., & Rakesh, N. (2015). Operations on Cloud Data (Classification and Data
Redundancy). International Journal Of Private Cloud Computing Environment And
Management, 2(2), 1-10. doi: 10.21742/ijpccem.2015.2.2.01
Lakshmi, V., & Begum, S. (2011). Security Issues & Controls in Cloud Computing. Indian
Journal Of Applied Research, 1(5), 38-40. doi: 10.15373/2249555x/feb2012/15
LI, B., WO, T., HU, C., LI, J., WANG, Y., & HUAI, J. (2013). Hidden OS Objects Correlated
Detection Technology Based on VMM. Journal Of Software, 24(2), 405-420. doi:
10.3724/sp.j.1001.2013.04265
Linthicum, D. (2018). Approaching Cloud Computing Performance. IEEE Cloud
Computing, 5(2), 33-36. doi: 10.1109/mcc.2018.022171665
Liu, S., Yang, Y., Qu, W., & Liu, Y. (2016). The business value of cloud computing: the
partnering agility perspective. Industrial Management & Data Systems, 116(6), 1160-
1177. doi: 10.1108/imds-09-2015-0376
Page 37 of 46
Journal Of Private Cloud Computing Environment And Management, 2(1), 27-34. doi:
10.21742/ijpccem.2015.2.1.04
Kaushik, A. (2016). Analysis Of Cloud Based Multitenant Load Scaling. International Journal
Of Engineering And Computer Science, 4(15), 144-167. doi: 10.18535/ijecs/v5i11.85
Khaleel, M. (2018). Innovative Cloud-based Snooping Detection model in both Public and
Private Infrastructure. Journal Of Zankoy Sulaimani - Part A, 20(2), 43-52. doi:
10.17656/jzs.10723
Khanna, S., & Rakesh, N. (2015). Operations on Cloud Data (Classification and Data
Redundancy). International Journal Of Private Cloud Computing Environment And
Management, 2(2), 1-10. doi: 10.21742/ijpccem.2015.2.2.01
Lakshmi, V., & Begum, S. (2011). Security Issues & Controls in Cloud Computing. Indian
Journal Of Applied Research, 1(5), 38-40. doi: 10.15373/2249555x/feb2012/15
LI, B., WO, T., HU, C., LI, J., WANG, Y., & HUAI, J. (2013). Hidden OS Objects Correlated
Detection Technology Based on VMM. Journal Of Software, 24(2), 405-420. doi:
10.3724/sp.j.1001.2013.04265
Linthicum, D. (2018). Approaching Cloud Computing Performance. IEEE Cloud
Computing, 5(2), 33-36. doi: 10.1109/mcc.2018.022171665
Liu, S., Yang, Y., Qu, W., & Liu, Y. (2016). The business value of cloud computing: the
partnering agility perspective. Industrial Management & Data Systems, 116(6), 1160-
1177. doi: 10.1108/imds-09-2015-0376
Page 37 of 46
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Microsoft.com. (2019). Download .NET StockTrader Sample Application from Official
Microsoft Download Center. Retrieved from
https://www.microsoft.com/en-in/download/details.aspx?id=26553
Mohsin, K. (2017). Cloud computing and security from single to multi cloud implement
calculator as use case. Global Sci-Tech, 9(4), 250. doi: 10.5958/2455-7110.2017.00034.9
Mukta. K. (2016). Cloud Computing for Rural Banking. International Journal Of Engineering
And Computer Science, 5(9), 23-44. doi: 10.18535/ijecs/v5i9.15
Prabha, S., & Dhivya, R. (2016). An Efficient Meta Scheduling based Virtual Consolidation for
Resource Sharing in Green Cloud. Bonfring International Journal Of Data Mining, 6(4),
39-45. doi: 10.9756/bijdm.8303
Rahma, F., Adji, T., & Widyawan, W. (2013). Scalability Analysis of KVM-Based Private Cloud
For Iaas. International Journal Of Cloud Computing And Services Science (IJ-
CLOSER), 2(4), 45-67. doi: 10.11591/closer.v2i4.4535
Rashid, A., & Parvez, J. (2014). Impact of Data-Centre And User-Base Location On Overall
Response-Time In A Cloud-Computing Environment. Transactions On Networks And
Communications, 2(4), 56-77. doi: 10.14738/tnc.24.358
Saha, S., & Hossain, M. (2015). Using Cloud Computing in Software Firm:A Strategy to
Improve Agility in the Current Financial Crisis. International Journal Of Distributed And
Cloud Computing, 3(2), 31-56. doi: 10.21863/ijdcc/2015.3.2.006
Salapura, V., & Harper, R. (2018). Virtual Machine Resiliency Management System for the
Cloud. IEEE Cloud Computing, 5(3), 55-64. doi: 10.1109/mcc.2018.032591617
Page 38 of 46
Microsoft Download Center. Retrieved from
https://www.microsoft.com/en-in/download/details.aspx?id=26553
Mohsin, K. (2017). Cloud computing and security from single to multi cloud implement
calculator as use case. Global Sci-Tech, 9(4), 250. doi: 10.5958/2455-7110.2017.00034.9
Mukta. K. (2016). Cloud Computing for Rural Banking. International Journal Of Engineering
And Computer Science, 5(9), 23-44. doi: 10.18535/ijecs/v5i9.15
Prabha, S., & Dhivya, R. (2016). An Efficient Meta Scheduling based Virtual Consolidation for
Resource Sharing in Green Cloud. Bonfring International Journal Of Data Mining, 6(4),
39-45. doi: 10.9756/bijdm.8303
Rahma, F., Adji, T., & Widyawan, W. (2013). Scalability Analysis of KVM-Based Private Cloud
For Iaas. International Journal Of Cloud Computing And Services Science (IJ-
CLOSER), 2(4), 45-67. doi: 10.11591/closer.v2i4.4535
Rashid, A., & Parvez, J. (2014). Impact of Data-Centre And User-Base Location On Overall
Response-Time In A Cloud-Computing Environment. Transactions On Networks And
Communications, 2(4), 56-77. doi: 10.14738/tnc.24.358
Saha, S., & Hossain, M. (2015). Using Cloud Computing in Software Firm:A Strategy to
Improve Agility in the Current Financial Crisis. International Journal Of Distributed And
Cloud Computing, 3(2), 31-56. doi: 10.21863/ijdcc/2015.3.2.006
Salapura, V., & Harper, R. (2018). Virtual Machine Resiliency Management System for the
Cloud. IEEE Cloud Computing, 5(3), 55-64. doi: 10.1109/mcc.2018.032591617
Page 38 of 46

Shah, D. (2012). Effective Security Controls and Contemporary Issues in Cloud
Computing. Global Journal For Research Analysis, 3(4), 35-37. doi:
10.15373/22778160/apr2014/12
Shyam, G., & Manvi, S. (2015). Modelling resource virtualisation concept in cloud computing
environment using finite state machines. International Journal Of Cloud
Computing, 4(3), 258. doi: 10.1504/ijcc.2015.071731
Sousa, F., Moreira, L., Costa Filho, J., & Machado, J. (2018). Predictive elastic replication for
multi-tenant databases in the cloud. Concurrency And Computation: Practice And
Experience, 30(16), e4437. doi: 10.1002/cpe.4437
Suresh, S., & Sakthivel, S. (2015). Workload Known VMM Scheduler for Server Consolidation
for Enterprise Cloud Data Center. Research Journal Of Applied Sciences, Engineering
And Technology, 9(5), 380-390. doi: 10.19026/rjaset.9.1417
Thomas, D. (2008). Enabling Application Agility - Software as A Service, Cloud Computing and
Dynamic Languages. The Journal Of Object Technology, 7(4), 29. doi:
10.5381/jot.2008.7.4.c3
Yamato, Y. (2015). Automatic system test technology of virtual machine software patch on IaaS
cloud. IEEJ Transactions On Electrical And Electronic Engineering, 10, S165-S167. doi:
10.1002/tee.22179
Page 39 of 46
Computing. Global Journal For Research Analysis, 3(4), 35-37. doi:
10.15373/22778160/apr2014/12
Shyam, G., & Manvi, S. (2015). Modelling resource virtualisation concept in cloud computing
environment using finite state machines. International Journal Of Cloud
Computing, 4(3), 258. doi: 10.1504/ijcc.2015.071731
Sousa, F., Moreira, L., Costa Filho, J., & Machado, J. (2018). Predictive elastic replication for
multi-tenant databases in the cloud. Concurrency And Computation: Practice And
Experience, 30(16), e4437. doi: 10.1002/cpe.4437
Suresh, S., & Sakthivel, S. (2015). Workload Known VMM Scheduler for Server Consolidation
for Enterprise Cloud Data Center. Research Journal Of Applied Sciences, Engineering
And Technology, 9(5), 380-390. doi: 10.19026/rjaset.9.1417
Thomas, D. (2008). Enabling Application Agility - Software as A Service, Cloud Computing and
Dynamic Languages. The Journal Of Object Technology, 7(4), 29. doi:
10.5381/jot.2008.7.4.c3
Yamato, Y. (2015). Automatic system test technology of virtual machine software patch on IaaS
cloud. IEEJ Transactions On Electrical And Electronic Engineering, 10, S165-S167. doi:
10.1002/tee.22179
Page 39 of 46

Appendix:
Exhibit 1: Prerequisites:
Page 40 of 46
Exhibit 1: Prerequisites:
Page 40 of 46
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Page 41 of 46
Exhibit 2: Elaborating VMM profile and analysing the steps for Application profile using
Telnet:
Step 3:
Step 4:
Configuration of SQL server profile using Telnet:
Step 1:
Page 42 of 46
Telnet:
Step 3:
Step 4:
Configuration of SQL server profile using Telnet:
Step 1:
Page 42 of 46
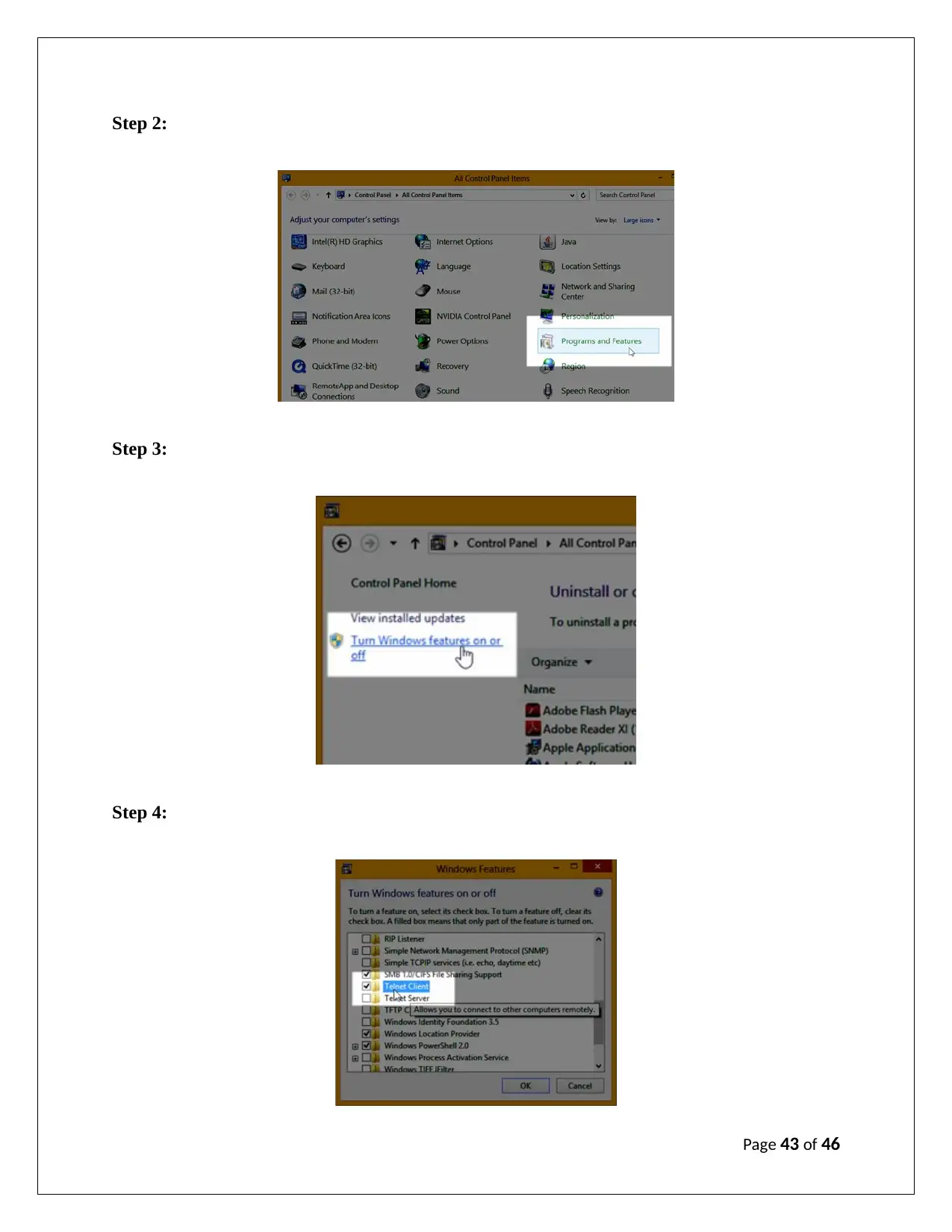
Step 2:
Step 3:
Step 4:
Page 43 of 46
Step 3:
Step 4:
Page 43 of 46
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
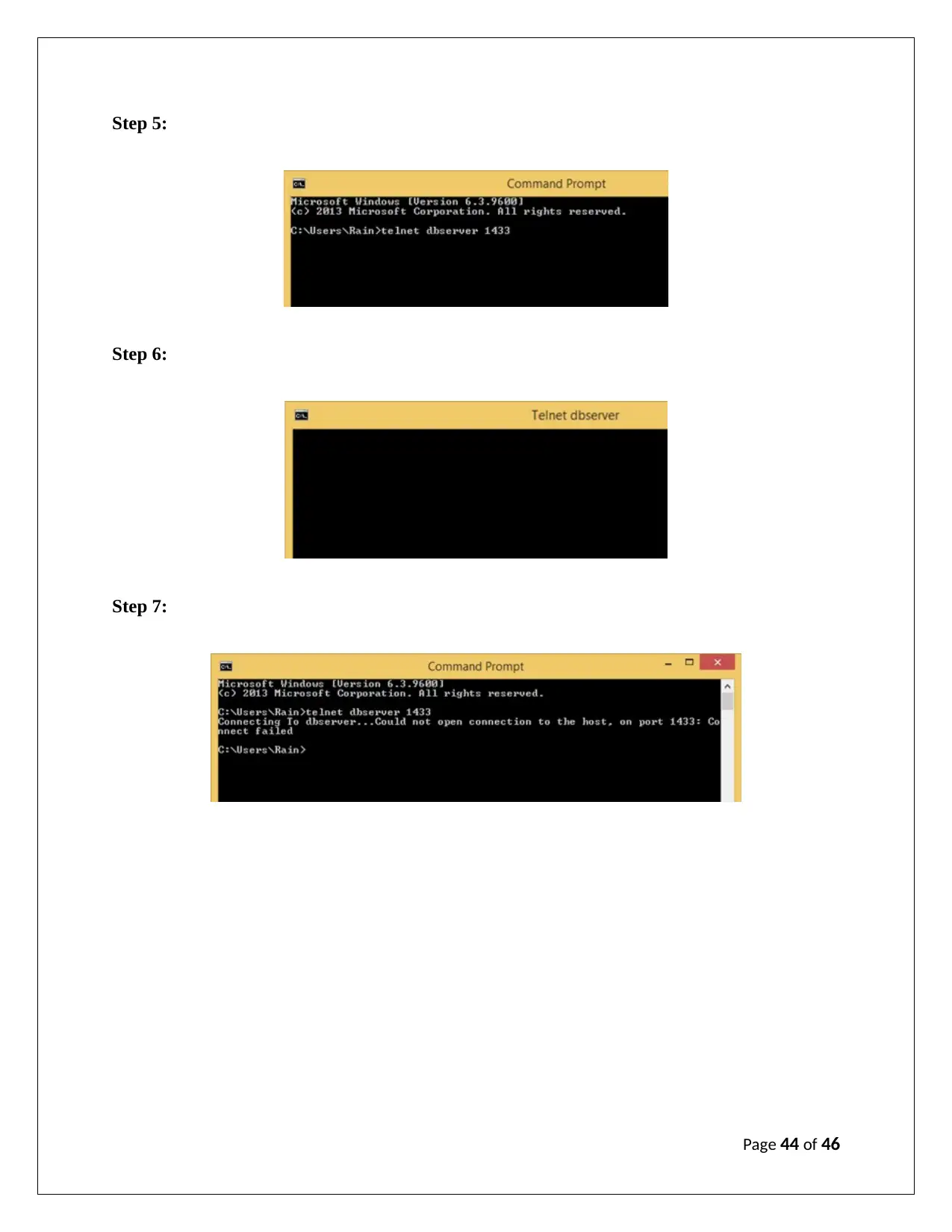
Step 5:
Step 6:
Step 7:
Page 44 of 46
Step 6:
Step 7:
Page 44 of 46
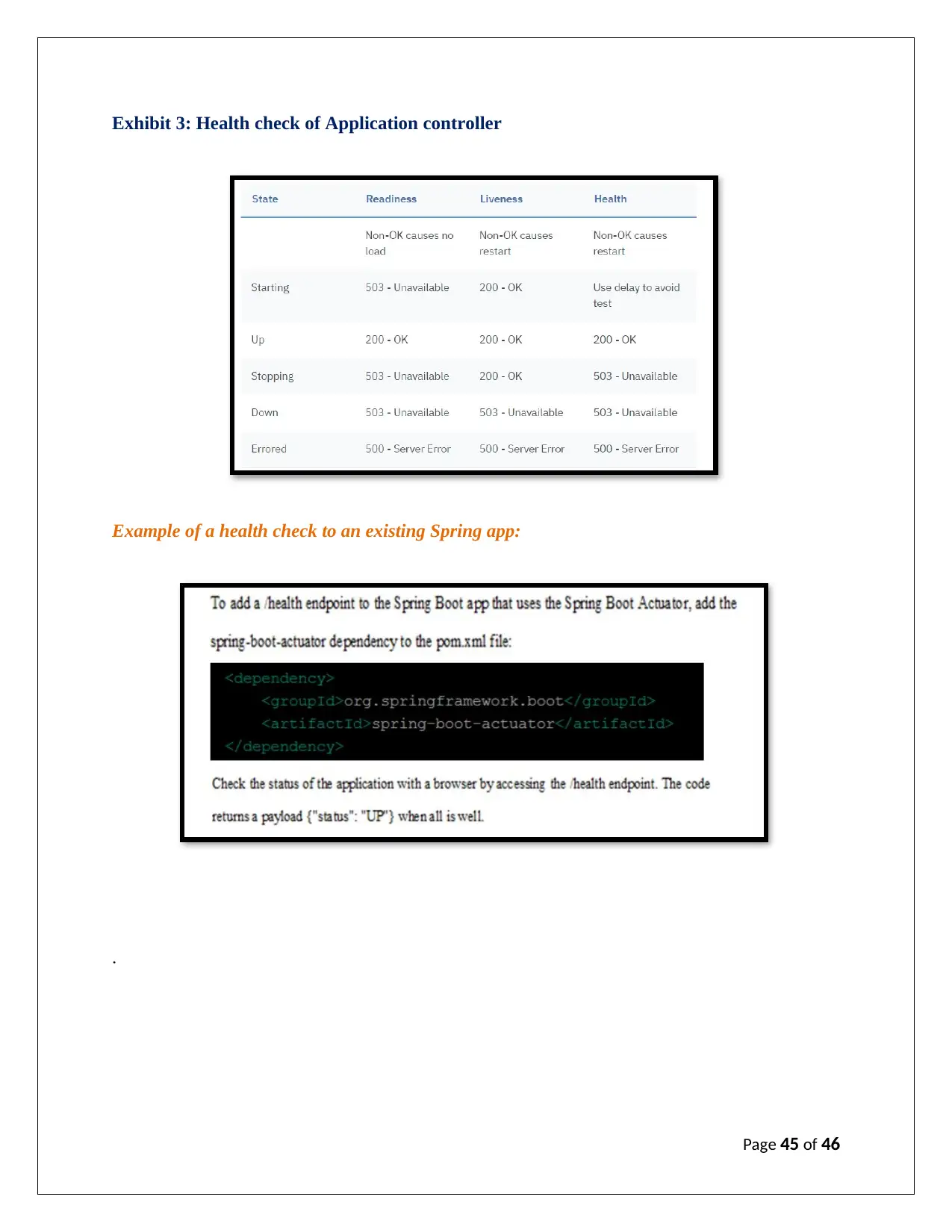
Exhibit 3: Health check of Application controller
Example of a health check to an existing Spring app:
.
Page 45 of 46
Example of a health check to an existing Spring app:
.
Page 45 of 46

Exhibit 4: The concept of service in a VMM and step involved in the creation of a Service
template: Based on existing virtual hard disk or virtual machine template:
Exhibit 4: The concept of service in a VMM and step involved in the creation of a Service
template: Using an existing virtual machine that is deployed on a host:
Page 46 of 46
template: Based on existing virtual hard disk or virtual machine template:
Exhibit 4: The concept of service in a VMM and step involved in the creation of a Service
template: Using an existing virtual machine that is deployed on a host:
Page 46 of 46
1 out of 46
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





