BallotOnline Cloud Migration: Risk Assessment and Compliance Strategy
VerifiedAdded on 2023/04/21
|16
|3217
|457
Report
AI Summary
This report provides a comprehensive risk assessment for BallotOnline's migration to the cloud, addressing potential security vulnerabilities, privacy concerns, and compliance requirements. It identifies key risks such as data breaches, lack of data integrity, and employee mismanagement, and proposes mitigation strategies aligned with NIST, FedRAMP, and ISO 31000 standards. The report also examines relevant security issues, applicable laws like the Help America Vote Act (HAVA), and geographic-specific compliance requirements in the US and EU. Furthermore, it includes a proposal for a compliance program, highlighting the roles of various employees and reviewing relevant literature to ensure a secure and compliant cloud environment for BallotOnline. The aim is to provide the company executives with a clear understanding of the challenges and solutions associated with transitioning to cloud infrastructure.

Running head: CLOUD COMPUTING RISK ASSESSMENT
CLOUD COMPUTING RISK ASSESSMENT
Name of the Student
Name of the University
Author note
CLOUD COMPUTING RISK ASSESSMENT
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
CLOUD COMPUTING RISK ASSESSMENT
Table of Contents
PART 1................................................................................................................................4
PART 2..............................................................................................................................10
Reference...........................................................................................................................15
CLOUD COMPUTING RISK ASSESSMENT
Table of Contents
PART 1................................................................................................................................4
PART 2..............................................................................................................................10
Reference...........................................................................................................................15

3
CLOUD COMPUTING RISK ASSESSMENT
Executive Summary
This report mainly focuses on discussing the security that must be implemented in the cloud
computing system. This report will discuss about the issues that are present in the usage of the
cloud computing system. This report will provide a risk analysis and risk management guidelines
that must be used in order to proclaim the management of the risk with the help of the risk
management guidelines. Potential privacy issues are also stated in the report. Security issues and
recommendations to mitigate the issues are also stated in this report. Proposal of the compliance
program will also be stated in this report.
CLOUD COMPUTING RISK ASSESSMENT
Executive Summary
This report mainly focuses on discussing the security that must be implemented in the cloud
computing system. This report will discuss about the issues that are present in the usage of the
cloud computing system. This report will provide a risk analysis and risk management guidelines
that must be used in order to proclaim the management of the risk with the help of the risk
management guidelines. Potential privacy issues are also stated in the report. Security issues and
recommendations to mitigate the issues are also stated in this report. Proposal of the compliance
program will also be stated in this report.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
CLOUD COMPUTING RISK ASSESSMENT
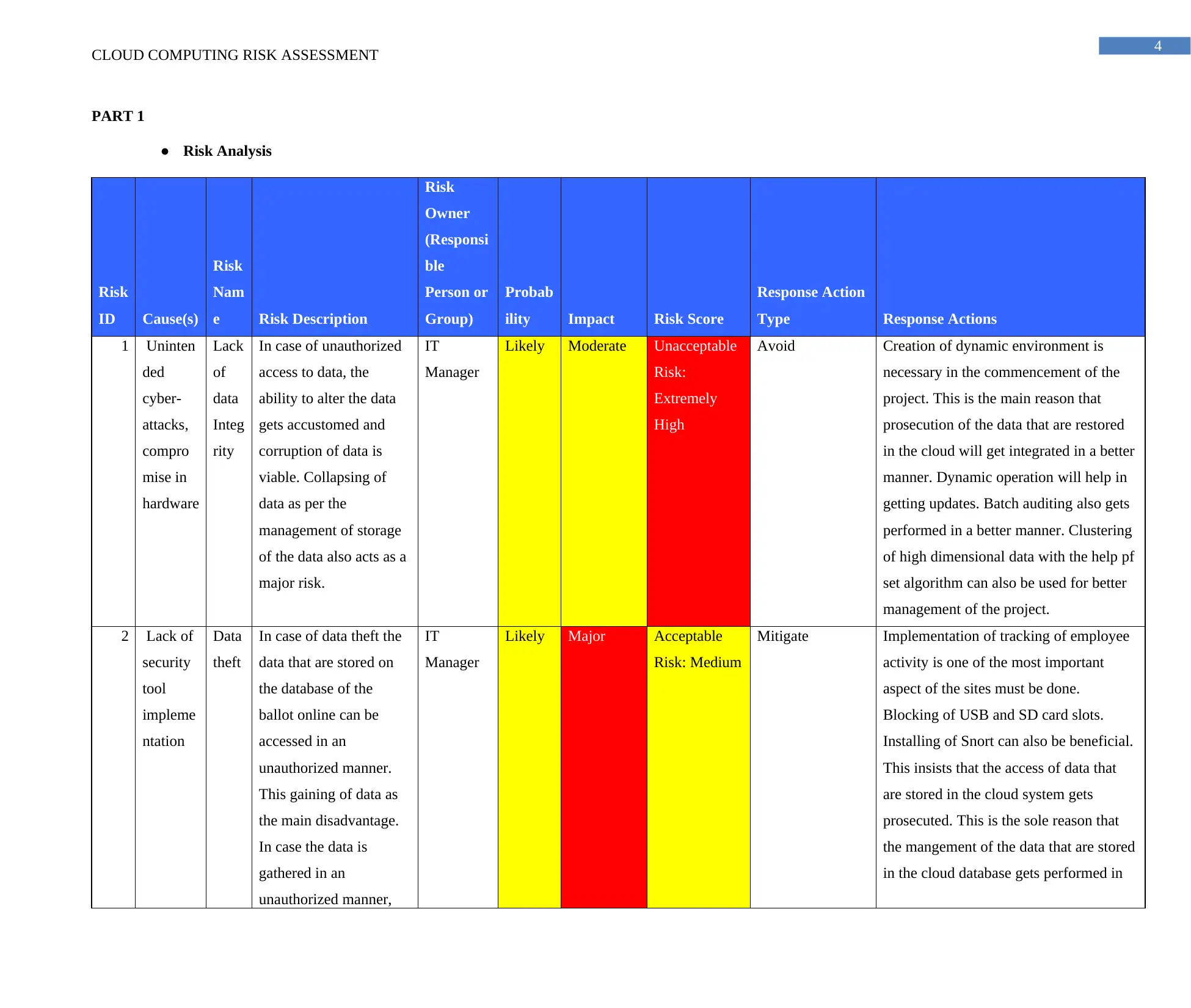
PART 1
● Risk Analysis
Risk
ID Cause(s)
Risk
Nam
e Risk Description
Risk
Owner
(Responsi
ble
Person or
Group)
Probab
ility Impact Risk Score
Response Action
Type Response Actions
1 Uninten
ded
cyber-
attacks,
compro
mise in
hardware
Lack
of
data
Integ
rity
In case of unauthorized
access to data, the
ability to alter the data
gets accustomed and
corruption of data is
viable. Collapsing of
data as per the
management of storage
of the data also acts as a
major risk.
IT
Manager
Likely Moderate Unacceptable
Risk:
Extremely
High
Avoid Creation of dynamic environment is
necessary in the commencement of the
project. This is the main reason that
prosecution of the data that are restored
in the cloud will get integrated in a better
manner. Dynamic operation will help in
getting updates. Batch auditing also gets
performed in a better manner. Clustering
of high dimensional data with the help pf
set algorithm can also be used for better
management of the project.
2 Lack of
security
tool
impleme
ntation
Data
theft
In case of data theft the
data that are stored on
the database of the
ballot online can be
accessed in an
unauthorized manner.
This gaining of data as
the main disadvantage.
In case the data is
gathered in an
unauthorized manner,
IT
Manager
Likely Major Acceptable
Risk: Medium
Mitigate Implementation of tracking of employee
activity is one of the most important
aspect of the sites must be done.
Blocking of USB and SD card slots.
Installing of Snort can also be beneficial.
This insists that the access of data that
are stored in the cloud system gets
prosecuted. This is the sole reason that
the mangement of the data that are stored
in the cloud database gets performed in
CLOUD COMPUTING RISK ASSESSMENT
PART 1
● Risk Analysis
Risk
ID Cause(s)
Risk
Nam
e Risk Description
Risk
Owner
(Responsi
ble
Person or
Group)
Probab
ility Impact Risk Score
Response Action
Type Response Actions
1 Uninten
ded
cyber-
attacks,
compro
mise in
hardware
Lack
of
data
Integ
rity
In case of unauthorized
access to data, the
ability to alter the data
gets accustomed and
corruption of data is
viable. Collapsing of
data as per the
management of storage
of the data also acts as a
major risk.
IT
Manager
Likely Moderate Unacceptable
Risk:
Extremely
High
Avoid Creation of dynamic environment is
necessary in the commencement of the
project. This is the main reason that
prosecution of the data that are restored
in the cloud will get integrated in a better
manner. Dynamic operation will help in
getting updates. Batch auditing also gets
performed in a better manner. Clustering
of high dimensional data with the help pf
set algorithm can also be used for better
management of the project.
2 Lack of
security
tool
impleme
ntation
Data
theft
In case of data theft the
data that are stored on
the database of the
ballot online can be
accessed in an
unauthorized manner.
This gaining of data as
the main disadvantage.
In case the data is
gathered in an
unauthorized manner,
IT
Manager
Likely Major Acceptable
Risk: Medium
Mitigate Implementation of tracking of employee
activity is one of the most important
aspect of the sites must be done.
Blocking of USB and SD card slots.
Installing of Snort can also be beneficial.
This insists that the access of data that
are stored in the cloud system gets
prosecuted. This is the sole reason that
the mangement of the data that are stored
in the cloud database gets performed in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
CLOUD COMPUTING RISK ASSESSMENT
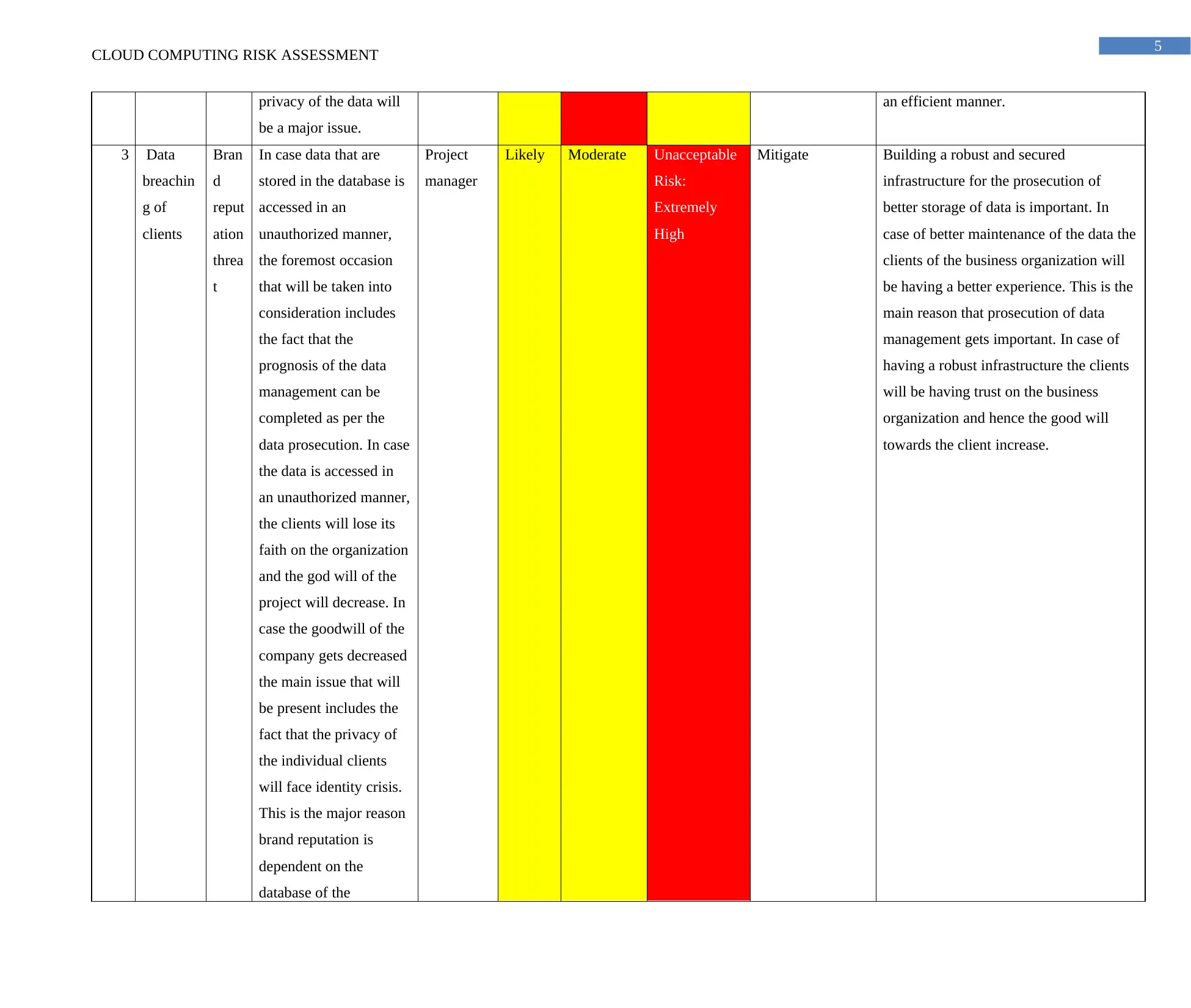
privacy of the data will
be a major issue.
an efficient manner.
3 Data
breachin
g of
clients
Bran
d
reput
ation
threa
t
In case data that are
stored in the database is
accessed in an
unauthorized manner,
the foremost occasion
that will be taken into
consideration includes
the fact that the
prognosis of the data
management can be
completed as per the
data prosecution. In case
the data is accessed in
an unauthorized manner,
the clients will lose its
faith on the organization
and the god will of the
project will decrease. In
case the goodwill of the
company gets decreased
the main issue that will
be present includes the
fact that the privacy of
the individual clients
will face identity crisis.
This is the major reason
brand reputation is
dependent on the
database of the
Project
manager
Likely Moderate Unacceptable
Risk:
Extremely
High
Mitigate Building a robust and secured
infrastructure for the prosecution of
better storage of data is important. In
case of better maintenance of the data the
clients of the business organization will
be having a better experience. This is the
main reason that prosecution of data
management gets important. In case of
having a robust infrastructure the clients
will be having trust on the business
organization and hence the good will
towards the client increase.
CLOUD COMPUTING RISK ASSESSMENT
privacy of the data will
be a major issue.
an efficient manner.
3 Data
breachin
g of
clients
Bran
d
reput
ation
threa
t
In case data that are
stored in the database is
accessed in an
unauthorized manner,
the foremost occasion
that will be taken into
consideration includes
the fact that the
prognosis of the data
management can be
completed as per the
data prosecution. In case
the data is accessed in
an unauthorized manner,
the clients will lose its
faith on the organization
and the god will of the
project will decrease. In
case the goodwill of the
company gets decreased
the main issue that will
be present includes the
fact that the privacy of
the individual clients
will face identity crisis.
This is the major reason
brand reputation is
dependent on the
database of the
Project
manager
Likely Moderate Unacceptable
Risk:
Extremely
High
Mitigate Building a robust and secured
infrastructure for the prosecution of
better storage of data is important. In
case of better maintenance of the data the
clients of the business organization will
be having a better experience. This is the
main reason that prosecution of data
management gets important. In case of
having a robust infrastructure the clients
will be having trust on the business
organization and hence the good will
towards the client increase.
6
CLOUD COMPUTING RISK ASSESSMENT
organization
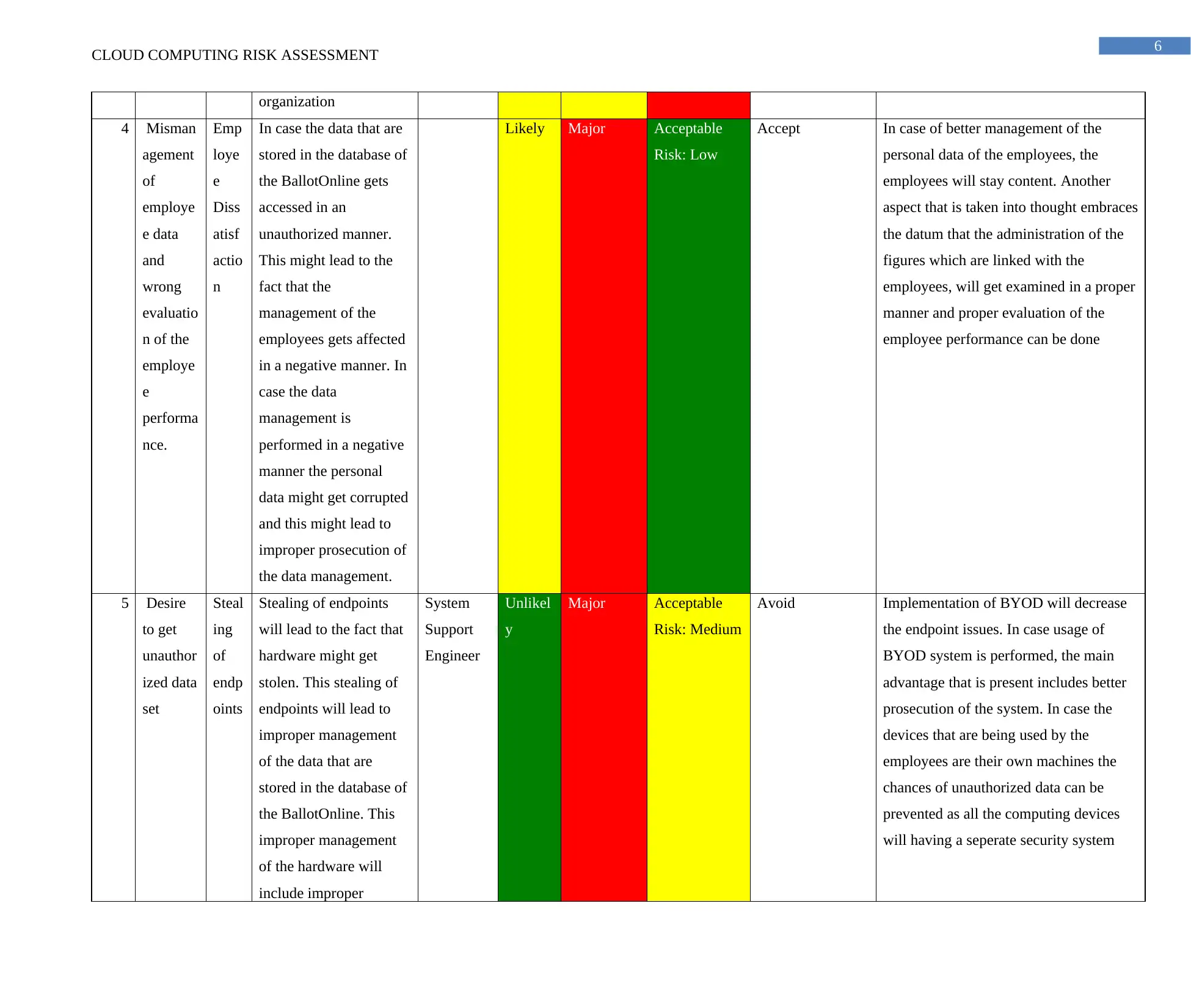
4 Misman
agement
of
employe
e data
and
wrong
evaluatio
n of the
employe
e
performa
nce.
Emp
loye
e
Diss
atisf
actio
n
In case the data that are
stored in the database of
the BallotOnline gets
accessed in an
unauthorized manner.
This might lead to the
fact that the
management of the
employees gets affected
in a negative manner. In
case the data
management is
performed in a negative
manner the personal
data might get corrupted
and this might lead to
improper prosecution of
the data management.
Likely Major Acceptable
Risk: Low
Accept In case of better management of the
personal data of the employees, the
employees will stay content. Another
aspect that is taken into thought embraces
the datum that the administration of the
figures which are linked with the
employees, will get examined in a proper
manner and proper evaluation of the
employee performance can be done
5 Desire
to get
unauthor
ized data
set
Steal
ing
of
endp
oints
Stealing of endpoints
will lead to the fact that
hardware might get
stolen. This stealing of
endpoints will lead to
improper management
of the data that are
stored in the database of
the BallotOnline. This
improper management
of the hardware will
include improper
System
Support
Engineer
Unlikel
y
Major Acceptable
Risk: Medium
Avoid Implementation of BYOD will decrease
the endpoint issues. In case usage of
BYOD system is performed, the main
advantage that is present includes better
prosecution of the system. In case the
devices that are being used by the
employees are their own machines the
chances of unauthorized data can be
prevented as all the computing devices
will having a seperate security system
CLOUD COMPUTING RISK ASSESSMENT
organization
4 Misman
agement
of
employe
e data
and
wrong
evaluatio
n of the
employe
e
performa
nce.
Emp
loye
e
Diss
atisf
actio
n
In case the data that are
stored in the database of
the BallotOnline gets
accessed in an
unauthorized manner.
This might lead to the
fact that the
management of the
employees gets affected
in a negative manner. In
case the data
management is
performed in a negative
manner the personal
data might get corrupted
and this might lead to
improper prosecution of
the data management.
Likely Major Acceptable
Risk: Low
Accept In case of better management of the
personal data of the employees, the
employees will stay content. Another
aspect that is taken into thought embraces
the datum that the administration of the
figures which are linked with the
employees, will get examined in a proper
manner and proper evaluation of the
employee performance can be done
5 Desire
to get
unauthor
ized data
set
Steal
ing
of
endp
oints
Stealing of endpoints
will lead to the fact that
hardware might get
stolen. This stealing of
endpoints will lead to
improper management
of the data that are
stored in the database of
the BallotOnline. This
improper management
of the hardware will
include improper
System
Support
Engineer
Unlikel
y
Major Acceptable
Risk: Medium
Avoid Implementation of BYOD will decrease
the endpoint issues. In case usage of
BYOD system is performed, the main
advantage that is present includes better
prosecution of the system. In case the
devices that are being used by the
employees are their own machines the
chances of unauthorized data can be
prevented as all the computing devices
will having a seperate security system
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7
CLOUD COMPUTING RISK ASSESSMENT
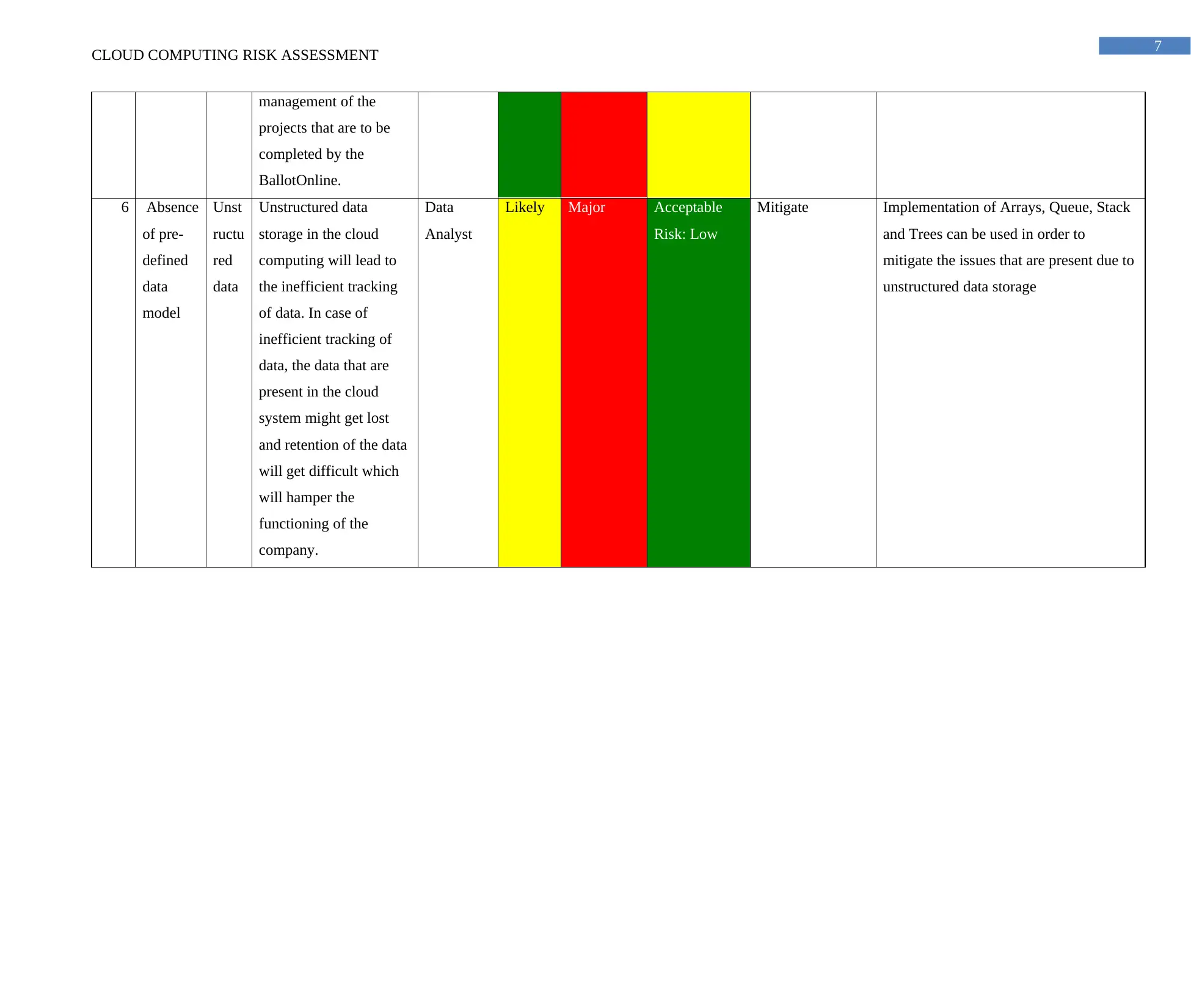
management of the
projects that are to be
completed by the
BallotOnline.
6 Absence
of pre-
defined
data
model
Unst
ructu
red
data
Unstructured data
storage in the cloud
computing will lead to
the inefficient tracking
of data. In case of
inefficient tracking of
data, the data that are
present in the cloud
system might get lost
and retention of the data
will get difficult which
will hamper the
functioning of the
company.
Data
Analyst
Likely Major Acceptable
Risk: Low
Mitigate Implementation of Arrays, Queue, Stack
and Trees can be used in order to
mitigate the issues that are present due to
unstructured data storage
CLOUD COMPUTING RISK ASSESSMENT
management of the
projects that are to be
completed by the
BallotOnline.
6 Absence
of pre-
defined
data
model
Unst
ructu
red
data
Unstructured data
storage in the cloud
computing will lead to
the inefficient tracking
of data. In case of
inefficient tracking of
data, the data that are
present in the cloud
system might get lost
and retention of the data
will get difficult which
will hamper the
functioning of the
company.
Data
Analyst
Likely Major Acceptable
Risk: Low
Mitigate Implementation of Arrays, Queue, Stack
and Trees can be used in order to
mitigate the issues that are present due to
unstructured data storage
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Summary of the risk
The risks that are present in the commencement of the scheme comprises the datum that
the organization of the data that are stored in the database of the cloud system is affected due to
lack of data integrity and data breaching. This data breaching from the database of a cloud
system might lead to decrease in the brand value of the BallotOnline. Hence the good will that is
built after so many tedious years might get affected in a negative manner. Employee satisfaction
is one of the main risk that is present in the origination of the development. In case the data
administration is not done in a proper manner, the employees working in the business
organization might get affected. Proper evaluation of the employee functioning can be done only
if the data that are stored are correct. Stealing endpoint and unstructured data presence can be
considered to be one of the major risk.
● Risk Management Guidelines Used
Guidelines that are appropriate for the BallotOnline organization includes usage of the
NIST Security and Privacy Controls: Fundamentals and Procedures, Federal Risk and
Authorization Management Program (FedRAMP), Risk Management with ISO 31000 and The
ISO 31000 Standard Risk Management: Principles and Guidelines. Usage of the ISO 31000
Standard Risk Management: Principles and Guidelines, the main advantage that is received
includes a better understanding of the risk management. Effective risk management strategies are
also stated in this guideline. Recommendations that are to be stated and this stated
recommendations are as per the framework of the organization. This section will also help in
understanding the technology that are needed to be used in order to implement the ISO3100
standard in the business organization.
● Potential Privacy Issues and Mitigation Measures
The risks that are present in the commencement of the scheme comprises the datum that
the organization of the data that are stored in the database of the cloud system is affected due to
lack of data integrity and data breaching. This data breaching from the database of a cloud
system might lead to decrease in the brand value of the BallotOnline. Hence the good will that is
built after so many tedious years might get affected in a negative manner. Employee satisfaction
is one of the main risk that is present in the origination of the development. In case the data
administration is not done in a proper manner, the employees working in the business
organization might get affected. Proper evaluation of the employee functioning can be done only
if the data that are stored are correct. Stealing endpoint and unstructured data presence can be
considered to be one of the major risk.
● Risk Management Guidelines Used
Guidelines that are appropriate for the BallotOnline organization includes usage of the
NIST Security and Privacy Controls: Fundamentals and Procedures, Federal Risk and
Authorization Management Program (FedRAMP), Risk Management with ISO 31000 and The
ISO 31000 Standard Risk Management: Principles and Guidelines. Usage of the ISO 31000
Standard Risk Management: Principles and Guidelines, the main advantage that is received
includes a better understanding of the risk management. Effective risk management strategies are
also stated in this guideline. Recommendations that are to be stated and this stated
recommendations are as per the framework of the organization. This section will also help in
understanding the technology that are needed to be used in order to implement the ISO3100
standard in the business organization.
● Potential Privacy Issues and Mitigation Measures

9
CLOUD COMPUTING RISK ASSESSMENT
Privacy laws are distinct and separate for different countries. Similarly United States.
Californian uses the statutes of SB 1386. This section uses the prosecution of the personal
information protection as well as the CA Civil Code 1798.83. This code of privacy mitigation
issue comprises the statistic that the management of the development gets completed in a manner
that helps in better management of the data that are stored in the cloud of the BallotOnline.
Implementation of the Maryland Personal Information Protection Act (MPIPA) can also be
used in the projection of the data security that are stored in the cloud data base. Maryland
Personal Information Protection Act (MPIPA) helps in protection of the data the individual
employees of BallotOnline. This process protected the data as per the data that are disposed
and adopted as per the reasonable security process. This will help in preventing the
unauthorized data accessing.
● Relevant Security Issues
Relevant security issues that are present in the commencement of the sensitive and
proprietary data management. Keeping the data secretive is considered to be one of the major
threat to the processing of the entire system. Information traversing is considered to be one of the
major telecommunication landscaping as per the packet based internet protocol. Security issues
can be targeted in the Mobile cellular networks and wireless local networks are considered as per
the traditional landline networking process. Compromising of the firewall system can be
considered as a relevant security threat for the BallotOnline.
● Applicable Laws, Regulations, and Frameworks
Applicable laws that are to be implemented in order to project the management of the
system of BallotOnline includes implementation of the cyberspace law. Implementation of the
cyberspace law is one of the major projection of the substantive legal subjects. Section 202 of the
CLOUD COMPUTING RISK ASSESSMENT
Privacy laws are distinct and separate for different countries. Similarly United States.
Californian uses the statutes of SB 1386. This section uses the prosecution of the personal
information protection as well as the CA Civil Code 1798.83. This code of privacy mitigation
issue comprises the statistic that the management of the development gets completed in a manner
that helps in better management of the data that are stored in the cloud of the BallotOnline.
Implementation of the Maryland Personal Information Protection Act (MPIPA) can also be
used in the projection of the data security that are stored in the cloud data base. Maryland
Personal Information Protection Act (MPIPA) helps in protection of the data the individual
employees of BallotOnline. This process protected the data as per the data that are disposed
and adopted as per the reasonable security process. This will help in preventing the
unauthorized data accessing.
● Relevant Security Issues
Relevant security issues that are present in the commencement of the sensitive and
proprietary data management. Keeping the data secretive is considered to be one of the major
threat to the processing of the entire system. Information traversing is considered to be one of the
major telecommunication landscaping as per the packet based internet protocol. Security issues
can be targeted in the Mobile cellular networks and wireless local networks are considered as per
the traditional landline networking process. Compromising of the firewall system can be
considered as a relevant security threat for the BallotOnline.
● Applicable Laws, Regulations, and Frameworks
Applicable laws that are to be implemented in order to project the management of the
system of BallotOnline includes implementation of the cyberspace law. Implementation of the
cyberspace law is one of the major projection of the substantive legal subjects. Section 202 of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
CLOUD COMPUTING RISK ASSESSMENT
Help America Vote Act (HAVA) law is implemented to keep a check on the functioning of the
project completion. National Voter Registration Act of 1993 (NVRA) is also used in the
projection of the cloud computation implementation.
● Compliance Requirements
Geographic-specific compliance requirements for the United States and European
Union
Canadian and California specific laws are not always strict in nature. This is the main
reason that the different compliance issues arises. The EU protection is considered to be
paramount in nature. This contends the fact that the supervision of the venture gets completed
with better entity projection of the security laws as per the criminal and civil penalties. Protection
of the flow of the project will be prosecuted as per the management of the geographic isolation
of the IT infrastructure.
Election industry-specific compliance issues and data compliance requirements
The implementation of the Help America Vote Act 2002 is authorized in the prosecution
of the National Institute of Standard and Technology. Implementation of the Election Assistance
Commission provides the projection of the voting system related computer and provides security.
Providing voter privacy protection is also important.
PART 2
● Proposal for a Compliance Program
Introduction
Cloud computing has been acting as an integral part of today’s society. This ensures the
detail that the organization of the development gets achieved as per the management of the
compliance of program that is to be performed.
CLOUD COMPUTING RISK ASSESSMENT
Help America Vote Act (HAVA) law is implemented to keep a check on the functioning of the
project completion. National Voter Registration Act of 1993 (NVRA) is also used in the
projection of the cloud computation implementation.
● Compliance Requirements
Geographic-specific compliance requirements for the United States and European
Union
Canadian and California specific laws are not always strict in nature. This is the main
reason that the different compliance issues arises. The EU protection is considered to be
paramount in nature. This contends the fact that the supervision of the venture gets completed
with better entity projection of the security laws as per the criminal and civil penalties. Protection
of the flow of the project will be prosecuted as per the management of the geographic isolation
of the IT infrastructure.
Election industry-specific compliance issues and data compliance requirements
The implementation of the Help America Vote Act 2002 is authorized in the prosecution
of the National Institute of Standard and Technology. Implementation of the Election Assistance
Commission provides the projection of the voting system related computer and provides security.
Providing voter privacy protection is also important.
PART 2
● Proposal for a Compliance Program
Introduction
Cloud computing has been acting as an integral part of today’s society. This ensures the
detail that the organization of the development gets achieved as per the management of the
compliance of program that is to be performed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
CLOUD COMPUTING RISK ASSESSMENT
Literature Review
Employees and their role
According to Islam, Manivannan & Zeadally (2016), Identification of the company
employees who will be having the oversight of the effective program includes the Cloud
platform provider, Adopter and the vendor. Tool providers are also the employees that are
projected as per the management of the cloud computing system. Project managers are the
employees who are one of the most important employees for implementation of the cloud
computing device. This system includes the fact that the management of the entire project is well
managed. Project managers will be responsible for better planning of the implementation of the
cloud computing of the business organization. Cloud platform providers are responsible for
providing the data storage platform. This data storage position is responsible for improved
administration of the mission. This is the chief motive that origination of the scheme will get
performed. The tool providers are responsible for implementing the tools that are required for
better prosecution of the projects that will be performed in a better manner with the help of better
integration of cloud computing system.
List of high level policy
According to Yimam & Fernandez (2016), Implementation of the HHS classification as
per the management of the federal government is performed and this is the goal that the
beginning of the project is performed as per the laws set. Implementation of HIPAA will be one
of the best policy that will get helped in better management of the project that are related to the
cybersecurity of the database. Implementation of the HITECH act along with the HIPAA can be
considered to be one of the best policy that is being used.
CLOUD COMPUTING RISK ASSESSMENT
Literature Review
Employees and their role
According to Islam, Manivannan & Zeadally (2016), Identification of the company
employees who will be having the oversight of the effective program includes the Cloud
platform provider, Adopter and the vendor. Tool providers are also the employees that are
projected as per the management of the cloud computing system. Project managers are the
employees who are one of the most important employees for implementation of the cloud
computing device. This system includes the fact that the management of the entire project is well
managed. Project managers will be responsible for better planning of the implementation of the
cloud computing of the business organization. Cloud platform providers are responsible for
providing the data storage platform. This data storage position is responsible for improved
administration of the mission. This is the chief motive that origination of the scheme will get
performed. The tool providers are responsible for implementing the tools that are required for
better prosecution of the projects that will be performed in a better manner with the help of better
integration of cloud computing system.
List of high level policy
According to Yimam & Fernandez (2016), Implementation of the HHS classification as
per the management of the federal government is performed and this is the goal that the
beginning of the project is performed as per the laws set. Implementation of HIPAA will be one
of the best policy that will get helped in better management of the project that are related to the
cybersecurity of the database. Implementation of the HITECH act along with the HIPAA can be
considered to be one of the best policy that is being used.

12
CLOUD COMPUTING RISK ASSESSMENT
List of training programs
According to Sen (2015), Training of the employees are very important in the prosecution
of the cloud computing implementation. Usage of the cloud computing system ensures the fact
that in case proper training is not provided to the employees of the organization, efficiency of the
task completion. In the initial stages theoretical training will be provided to the employees. With
the help of the theoretical training that will be provided, basic understanding of the terminologies
will be done. After completion of the theoretical training in hand practical training will be
provided to the employees of the organization. After completion of the in hand training,
assessment of the training will be performed. After checking the assessment result understanding
the improvement of the employees can be understood and hence the management of the project
can be understood.
Communication Channels
E-mail, phone calls, Official media are considered to be the communication channels that
might be used by the employees of the organization.
Dependencies
Output of the project is completely dependent on the designing of the project. This
designing of the project imbibes the fact that the completion of the project that implements cloud
computing gets performed in a better manner.
Time Constrain
Time constrain is one of the major aspect that will be taken into consideration. In case of
the completion of the project after the desired time, project failure can be expected. In case the
CLOUD COMPUTING RISK ASSESSMENT
List of training programs
According to Sen (2015), Training of the employees are very important in the prosecution
of the cloud computing implementation. Usage of the cloud computing system ensures the fact
that in case proper training is not provided to the employees of the organization, efficiency of the
task completion. In the initial stages theoretical training will be provided to the employees. With
the help of the theoretical training that will be provided, basic understanding of the terminologies
will be done. After completion of the theoretical training in hand practical training will be
provided to the employees of the organization. After completion of the in hand training,
assessment of the training will be performed. After checking the assessment result understanding
the improvement of the employees can be understood and hence the management of the project
can be understood.
Communication Channels
E-mail, phone calls, Official media are considered to be the communication channels that
might be used by the employees of the organization.
Dependencies
Output of the project is completely dependent on the designing of the project. This
designing of the project imbibes the fact that the completion of the project that implements cloud
computing gets performed in a better manner.
Time Constrain
Time constrain is one of the major aspect that will be taken into consideration. In case of
the completion of the project after the desired time, project failure can be expected. In case the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





