University Report: Cloud Computing Security with VPN Technologies
VerifiedAdded on 2023/02/01
|5
|1900
|39
Report
AI Summary
This report provides an overview of cloud computing security, with a specific focus on the role and application of Virtual Private Networks (VPNs). The report begins with an introduction to cloud computing and its increasing adoption in the market, highlighting the associated security challenges. It then delves into specific security issues faced by cloud computing, such as data breaches and vulnerabilities, particularly within public cloud environments. The core of the report examines VPN technology as a solution, explaining how VPNs encrypt data, create secure tunnels, and provide data confidentiality. It further illustrates the integration of VPNs with firewalls in cloud computing architectures, comparing scenarios with and without VPNs. The report also addresses VPN security issues and concludes by summarizing the benefits of VPNs in protecting data. Finally, the report suggests future research directions, potentially including other factors excluding VPN security, and provides a comprehensive list of references.

Cloud Computing Security with VPN
Name of the Student
Name of the University
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract: This report has focused on the
cloud computing with VPN. Cloud
computing gas been an important part for
business organization in the recent
market. However, security has been an
important problem in the cloud
computing. Various breaches have been
occurred in cloud computing. VPN has
been helping in encrypting data into
packets that provide proper security to
data transfer.
Keywords: Cloud Computing and VPN
I. Introduction
Cloud computing has been gaining a lot of
interest and competition in the market. The
service delivery model of cloud computing
has been helping a lot of companies and
users in the market. These advances in cloud
computing has been helping in maintaining a
keen approach in the development of
services with users. There have been several
benefits of cloud computing along with
some limitations. Security of data and
information has been the major issue in the
cloud computing. This report has focused on
security issues faced by cloud computing
and strategies for mitigation these issues
including use of VPN.
II. Securities issues for cloud computing
Cloud computing has been utilized by most
of the business organization in the market.
The demand of cloud computing has been
increased in the market with its beneficial
services provided to clients. Therefore, most
of the data and information have been stored
over cloud storage [1]. This create security
issues and treats of data and information.
The security in cloud computing has been
maintained over several platforms and
networks. Data security has been the most
important issue faced in the cloud
computing services. Hackers have been
targeting data stored over cloud database
over internet. The public cloud has been
most vulnerable to data security issue.
Public cloud refers to a model of cloud
computing that can be accessed by any user
over the cloud. Therefore, this model type
provide least security to data and
information stored over cloud storages.
III. Virtual Private Network (VPN)
Virtual private network (VPN) technology
has been providing a way of protection data
being transferred over the internet. VPN has
been a general term used in communication
network for using any combination of
technologies for securing a connection from
cyber issues. VPN helps in transmitting data
with the help of private connections [6].
Therefore, in case of pubic cloud, it helps in
transferring data in a secured and private
connection tunnels. Data used to be
encrypted in packet and added with a
header. The header node contains the
routing information that helps sender in
tracking data packet. VPN uses encryption
for providing data confidentiality. When
connection has been established, VPN uses
tunneling mechanism for encapsulating
encrypted data and information in a secure
tunnel. Packets have been passed over a
public network so that it becomes
unreadable without proper decryption keys
[7]. This help in securing data and
information over the cloud storages. VPN
has been providing information in a proper
manner. There has been regularly
performing message summary for ensuring
data check. VPN does not provide proper
user validation. Therefore, user has been
entering directly using private key for
obtaining entry into the network [4].
cloud computing with VPN. Cloud
computing gas been an important part for
business organization in the recent
market. However, security has been an
important problem in the cloud
computing. Various breaches have been
occurred in cloud computing. VPN has
been helping in encrypting data into
packets that provide proper security to
data transfer.
Keywords: Cloud Computing and VPN
I. Introduction
Cloud computing has been gaining a lot of
interest and competition in the market. The
service delivery model of cloud computing
has been helping a lot of companies and
users in the market. These advances in cloud
computing has been helping in maintaining a
keen approach in the development of
services with users. There have been several
benefits of cloud computing along with
some limitations. Security of data and
information has been the major issue in the
cloud computing. This report has focused on
security issues faced by cloud computing
and strategies for mitigation these issues
including use of VPN.
II. Securities issues for cloud computing
Cloud computing has been utilized by most
of the business organization in the market.
The demand of cloud computing has been
increased in the market with its beneficial
services provided to clients. Therefore, most
of the data and information have been stored
over cloud storage [1]. This create security
issues and treats of data and information.
The security in cloud computing has been
maintained over several platforms and
networks. Data security has been the most
important issue faced in the cloud
computing services. Hackers have been
targeting data stored over cloud database
over internet. The public cloud has been
most vulnerable to data security issue.
Public cloud refers to a model of cloud
computing that can be accessed by any user
over the cloud. Therefore, this model type
provide least security to data and
information stored over cloud storages.
III. Virtual Private Network (VPN)
Virtual private network (VPN) technology
has been providing a way of protection data
being transferred over the internet. VPN has
been a general term used in communication
network for using any combination of
technologies for securing a connection from
cyber issues. VPN helps in transmitting data
with the help of private connections [6].
Therefore, in case of pubic cloud, it helps in
transferring data in a secured and private
connection tunnels. Data used to be
encrypted in packet and added with a
header. The header node contains the
routing information that helps sender in
tracking data packet. VPN uses encryption
for providing data confidentiality. When
connection has been established, VPN uses
tunneling mechanism for encapsulating
encrypted data and information in a secure
tunnel. Packets have been passed over a
public network so that it becomes
unreadable without proper decryption keys
[7]. This help in securing data and
information over the cloud storages. VPN
has been providing information in a proper
manner. There has been regularly
performing message summary for ensuring
data check. VPN does not provide proper
user validation. Therefore, user has been
entering directly using private key for
obtaining entry into the network [4].
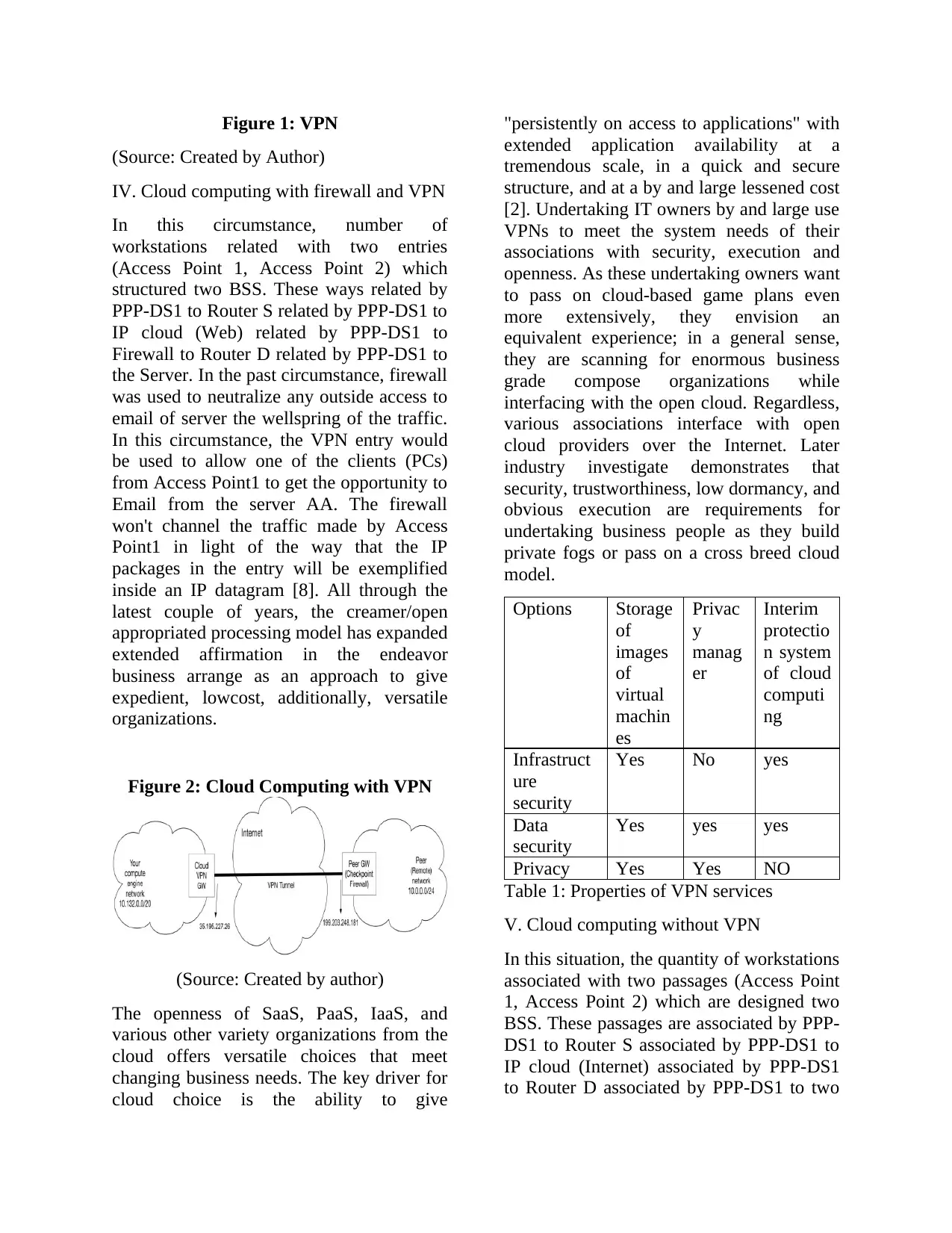
Figure 1: VPN
(Source: Created by Author)
IV. Cloud computing with firewall and VPN
In this circumstance, number of
workstations related with two entries
(Access Point 1, Access Point 2) which
structured two BSS. These ways related by
PPP-DS1 to Router S related by PPP-DS1 to
IP cloud (Web) related by PPP-DS1 to
Firewall to Router D related by PPP-DS1 to
the Server. In the past circumstance, firewall
was used to neutralize any outside access to
email of server the wellspring of the traffic.
In this circumstance, the VPN entry would
be used to allow one of the clients (PCs)
from Access Point1 to get the opportunity to
Email from the server AA. The firewall
won't channel the traffic made by Access
Point1 in light of the way that the IP
packages in the entry will be exemplified
inside an IP datagram [8]. All through the
latest couple of years, the creamer/open
appropriated processing model has expanded
extended affirmation in the endeavor
business arrange as an approach to give
expedient, lowcost, additionally, versatile
organizations.
Figure 2: Cloud Computing with VPN
(Source: Created by author)
The openness of SaaS, PaaS, IaaS, and
various other variety organizations from the
cloud offers versatile choices that meet
changing business needs. The key driver for
cloud choice is the ability to give
"persistently on access to applications" with
extended application availability at a
tremendous scale, in a quick and secure
structure, and at a by and large lessened cost
[2]. Undertaking IT owners by and large use
VPNs to meet the system needs of their
associations with security, execution and
openness. As these undertaking owners want
to pass on cloud-based game plans even
more extensively, they envision an
equivalent experience; in a general sense,
they are scanning for enormous business
grade compose organizations while
interfacing with the open cloud. Regardless,
various associations interface with open
cloud providers over the Internet. Later
industry investigate demonstrates that
security, trustworthiness, low dormancy, and
obvious execution are requirements for
undertaking business people as they build
private fogs or pass on a cross breed cloud
model.
Options Storage
of
images
of
virtual
machin
es
Privac
y
manag
er
Interim
protectio
n system
of cloud
computi
ng
Infrastruct
ure
security
Yes No yes
Data
security
Yes yes yes
Privacy Yes Yes NO
Table 1: Properties of VPN services
V. Cloud computing without VPN
In this situation, the quantity of workstations
associated with two passages (Access Point
1, Access Point 2) which are designed two
BSS. These passages are associated by PPP-
DS1 to Router S associated by PPP-DS1 to
IP cloud (Internet) associated by PPP-DS1
to Router D associated by PPP-DS1 to two
(Source: Created by Author)
IV. Cloud computing with firewall and VPN
In this circumstance, number of
workstations related with two entries
(Access Point 1, Access Point 2) which
structured two BSS. These ways related by
PPP-DS1 to Router S related by PPP-DS1 to
IP cloud (Web) related by PPP-DS1 to
Firewall to Router D related by PPP-DS1 to
the Server. In the past circumstance, firewall
was used to neutralize any outside access to
email of server the wellspring of the traffic.
In this circumstance, the VPN entry would
be used to allow one of the clients (PCs)
from Access Point1 to get the opportunity to
Email from the server AA. The firewall
won't channel the traffic made by Access
Point1 in light of the way that the IP
packages in the entry will be exemplified
inside an IP datagram [8]. All through the
latest couple of years, the creamer/open
appropriated processing model has expanded
extended affirmation in the endeavor
business arrange as an approach to give
expedient, lowcost, additionally, versatile
organizations.
Figure 2: Cloud Computing with VPN
(Source: Created by author)
The openness of SaaS, PaaS, IaaS, and
various other variety organizations from the
cloud offers versatile choices that meet
changing business needs. The key driver for
cloud choice is the ability to give
"persistently on access to applications" with
extended application availability at a
tremendous scale, in a quick and secure
structure, and at a by and large lessened cost
[2]. Undertaking IT owners by and large use
VPNs to meet the system needs of their
associations with security, execution and
openness. As these undertaking owners want
to pass on cloud-based game plans even
more extensively, they envision an
equivalent experience; in a general sense,
they are scanning for enormous business
grade compose organizations while
interfacing with the open cloud. Regardless,
various associations interface with open
cloud providers over the Internet. Later
industry investigate demonstrates that
security, trustworthiness, low dormancy, and
obvious execution are requirements for
undertaking business people as they build
private fogs or pass on a cross breed cloud
model.
Options Storage
of
images
of
virtual
machin
es
Privac
y
manag
er
Interim
protectio
n system
of cloud
computi
ng
Infrastruct
ure
security
Yes No yes
Data
security
Yes yes yes
Privacy Yes Yes NO
Table 1: Properties of VPN services
V. Cloud computing without VPN
In this situation, the quantity of workstations
associated with two passages (Access Point
1, Access Point 2) which are designed two
BSS. These passages are associated by PPP-
DS1 to Router S associated by PPP-DS1 to
IP cloud (Internet) associated by PPP-DS1
to Router D associated by PPP-DS1 to two
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Servers (Server AA, Server BB) which
speaks to two divisions.
VI. VPN Security Issue
The motivation behind VPNs is to gain
admittance to normal sources. Considering
VPNs from client's perspective, they can be
seen as a point to point association among
PCs and servers. Another encryption
convention for information in VPN and an
administration key that in this VPN server is
a confided in one [9]. In this model VPN
server is a confided in one. In this technique,
Customer displays his solicitation to VPN
server and it appoints a key an incentive for
client. Consequently, client starts scrambling
information by utilizing this key and
propelled encryption standard AES
Furthermore, by RSA encryption calculation
can disentangle the coded data once more,
so we can say this technique has high
security. M.C. Nicalescu has displayed IP
versatile security in VPNs. At first AH, ESP
analyzed the characterized conventions in
IKE in IPsec-IETF engineering. In view of
these conventions, assurance against
forswearing of infections, sniff and the other
dynamic threats was talked about. This
paper built up this discourse to a vast
extension called "Web" [3]. In which the
utilization of secure burrowing as a primary
defensive component was tried. Take a
gander at the handling overhead from
utilizing Data Encryption Standard (DES)
(for secrecy) and Message Digest (MD5)
Secure Hash Calculation 1 (SHA-1) (for
validation security) in combination with
IPsec. Extends this investigation by
together thinking about the Advanced
Encryption Standard (AES).
Category Issues
Privacy issues Misuse of cloud
computing
Malicious insiders
Dynamic provision
Security issues Audit
Trust
Availability
Access
Table 2: Issues to cloud computing
VII. Conclusion
It can be concluded that cloud computing
has been helping business organization in
various ways. Because of the significance of
data security issue, this paper has focused on
investigation of various VPN encryption
strategies. Data security has been the most
important issue faced in the cloud
computing services. Hackers have been
targeting data stored over cloud database
over internet. The principle thoughts of
some VPN encryption strategies have been
presented. Later on, the combination or
blending between a portions of these
strategies can be connected to show signs of
improvement execution.
VIII. Future Work
This report has focused on cloud computing
security with the help of VPN. The future
research might focus on other factors
excluding VPN security.
IX. References
[1] He J, Dong M, Ota K, Fan M, Wang
G. NetSecCC: A scalable and fault-
tolerant architecture for cloud
computing security. Peer-to-Peer
Networking and Applications. 2016
Jan 1;9(1):67-81.
[2] Almorsy M, Grundy J, Müller I. An
analysis of the cloud computing
security problem. arXiv preprint
arXiv:1609.01107. 2016 Sep 5.
[3] Tesfamicael AD, Liu V, Foo E,
Caelli W. Modeling for performance
and security balanced trading
communication systems in the cloud.
In2017 IEEE 36th International
Performance Computing and
speaks to two divisions.
VI. VPN Security Issue
The motivation behind VPNs is to gain
admittance to normal sources. Considering
VPNs from client's perspective, they can be
seen as a point to point association among
PCs and servers. Another encryption
convention for information in VPN and an
administration key that in this VPN server is
a confided in one [9]. In this model VPN
server is a confided in one. In this technique,
Customer displays his solicitation to VPN
server and it appoints a key an incentive for
client. Consequently, client starts scrambling
information by utilizing this key and
propelled encryption standard AES
Furthermore, by RSA encryption calculation
can disentangle the coded data once more,
so we can say this technique has high
security. M.C. Nicalescu has displayed IP
versatile security in VPNs. At first AH, ESP
analyzed the characterized conventions in
IKE in IPsec-IETF engineering. In view of
these conventions, assurance against
forswearing of infections, sniff and the other
dynamic threats was talked about. This
paper built up this discourse to a vast
extension called "Web" [3]. In which the
utilization of secure burrowing as a primary
defensive component was tried. Take a
gander at the handling overhead from
utilizing Data Encryption Standard (DES)
(for secrecy) and Message Digest (MD5)
Secure Hash Calculation 1 (SHA-1) (for
validation security) in combination with
IPsec. Extends this investigation by
together thinking about the Advanced
Encryption Standard (AES).
Category Issues
Privacy issues Misuse of cloud
computing
Malicious insiders
Dynamic provision
Security issues Audit
Trust
Availability
Access
Table 2: Issues to cloud computing
VII. Conclusion
It can be concluded that cloud computing
has been helping business organization in
various ways. Because of the significance of
data security issue, this paper has focused on
investigation of various VPN encryption
strategies. Data security has been the most
important issue faced in the cloud
computing services. Hackers have been
targeting data stored over cloud database
over internet. The principle thoughts of
some VPN encryption strategies have been
presented. Later on, the combination or
blending between a portions of these
strategies can be connected to show signs of
improvement execution.
VIII. Future Work
This report has focused on cloud computing
security with the help of VPN. The future
research might focus on other factors
excluding VPN security.
IX. References
[1] He J, Dong M, Ota K, Fan M, Wang
G. NetSecCC: A scalable and fault-
tolerant architecture for cloud
computing security. Peer-to-Peer
Networking and Applications. 2016
Jan 1;9(1):67-81.
[2] Almorsy M, Grundy J, Müller I. An
analysis of the cloud computing
security problem. arXiv preprint
arXiv:1609.01107. 2016 Sep 5.
[3] Tesfamicael AD, Liu V, Foo E,
Caelli W. Modeling for performance
and security balanced trading
communication systems in the cloud.
In2017 IEEE 36th International
Performance Computing and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Communications Conference
(IPCCC) 2017 Dec 10 (pp. 1-7).
IEEE.
[4] Pallas F, Günther J, Bermbach D.
Pick your choice in HBase: Security
or performance. In2016 IEEE
International Conference on Big
Data (Big Data) 2016 Dec 5 (pp.
548-554). IEEE.
[5] Jimenez JM, Diaz JR, Lloret J,
Romero O. MHCP: Multimedia
Hybrid Cloud Computing Protocol
and Architecture for Mobile Devices.
IEEE Network. 2019 Jan;33(1):106-
12.
[6] Singh M, Kant U, Gupta PK,
Srivastava VM. Cloud-Based
Predictive Intelligence and Its
Security Model. InPredictive
Intelligence Using Big Data and the
Internet of Things 2019 (pp. 128-
143). IGI Global.
[7] Jyothi KK, Reddy BI. Study on
Virtual Private Network (VPN),
VPN’s Protocols And Security.
[8] Masala GL, Ruiu P, Grosso E.
Biometric authentication and data
security in cloud computing.
InComputer and Network Security
Essentials 2018 (pp. 337-353).
Springer, Cham.
[9] Hu G, Yang Y, Li L. Education
Technology Cloud Platform
Framework Establishment and
Security. Journal of Computer and
Communications. 2016 May
19;4(07):7.
[10] Shankar R, Duraisamy S.
Different Service Models and
Deployment Models of Cloud
Computing: Challenges.
(IPCCC) 2017 Dec 10 (pp. 1-7).
IEEE.
[4] Pallas F, Günther J, Bermbach D.
Pick your choice in HBase: Security
or performance. In2016 IEEE
International Conference on Big
Data (Big Data) 2016 Dec 5 (pp.
548-554). IEEE.
[5] Jimenez JM, Diaz JR, Lloret J,
Romero O. MHCP: Multimedia
Hybrid Cloud Computing Protocol
and Architecture for Mobile Devices.
IEEE Network. 2019 Jan;33(1):106-
12.
[6] Singh M, Kant U, Gupta PK,
Srivastava VM. Cloud-Based
Predictive Intelligence and Its
Security Model. InPredictive
Intelligence Using Big Data and the
Internet of Things 2019 (pp. 128-
143). IGI Global.
[7] Jyothi KK, Reddy BI. Study on
Virtual Private Network (VPN),
VPN’s Protocols And Security.
[8] Masala GL, Ruiu P, Grosso E.
Biometric authentication and data
security in cloud computing.
InComputer and Network Security
Essentials 2018 (pp. 337-353).
Springer, Cham.
[9] Hu G, Yang Y, Li L. Education
Technology Cloud Platform
Framework Establishment and
Security. Journal of Computer and
Communications. 2016 May
19;4(07):7.
[10] Shankar R, Duraisamy S.
Different Service Models and
Deployment Models of Cloud
Computing: Challenges.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




